by Contributed | Nov 30, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer got an issue that depending on the driver that they are using they are not able to see data in a specific column.
Sometimes, it is hard to debug the application or specify the driver to use to extract this data. In this Powershell command you could specify the driver and the provider to obtain this data.
Basically, you need to define the parameter of the connection and the provider to connect. In terms of provider you could use
- 1 – Driver: OLEDB – Provider: SQLOLEDB
- 2 – Driver: OLEDB – Provider: MSOLEDBSQL
- 3 – .Net SQL Client
- 4 – Driver: ADO – Provider: SQLOLEDB
- 5 – Driver: ADO – Provider: MSOLEDBSQL
Enjoy!
by Contributed | Nov 30, 2020 | Technology
This article is contributed. See the original author and article here.
Test Base for M365 recently changed one of the baseline tests it uses to validate applications against pre-released security updates. Previously, tests were executed using a ‘clean install’ approach. An application was installed on a clean virtual machine with an OS that was up-to-date with the latest cumulative update (LCU).
In the new sequence, termed the ‘in-place installation approach’, the application is installed on an in-market OS version that precedes the local cumulative update patch (the pre-released OS version) that we are testing against the application. This better mimics a use case of keeping existing users of apps productive and protected even when they receive platform upgrades for their devices.
The question we would like answered is, which test option works the best for all users? Would you prefer the clean install approach or the in-place installation approach?
A great metaphor is that of moving into a new home. Your home has a beautiful living area to be furnished, so you order a great couch. Would you rather take the couch out every time you clean the living area or would you get tools that do a great cleaning job while the couch remains where it is?
Taking the couch out represents a clean installation, where your application is fitted on a device for the first time. Leaving the couch in and using the right tools to tidy up is the in-place installation, where your application is already fitted on the device prior to whatever improvements being done on the device platform. Which brings more value to you?
We would very much like your feedback. Please comment below!
by Contributed | Nov 30, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
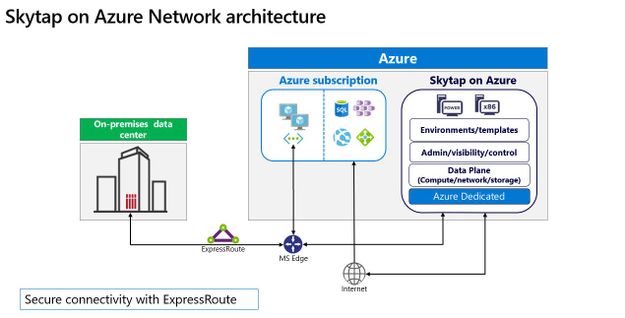
Cloud migration remains a crucial component for any organization in the transformation of their business, and Microsoft continues to focus on how best to support customers wherever they are in that journey. Microsoft works with partners like Skytap to unlock the power of Azure for customers relying on traditional on-premises application platforms.
Skytap on Azure is a cloud service purpose-built to natively run traditional IBM Power workloads in Azure. And we are excited to share that Skytap on Azure is available for purchase and provisioning directly through Azure Marketplace, further streamlining the experience for customers.
The migration of applications running on IBM Power to the cloud is often seen as a difficult and challenging move involving re-platforming. With Skytap on Azure, Microsoft brings the unique capabilities of IBM Power9 servers to Azure, directly integrating with Azure networking enabling Skytap to provide its platform with minimal connectivity latency to Azure native services.

Skytap has more than a decade of experience working with customers, such as Delphix, Schneider Electric, and Okta, and offering extensible application environments that are compatible with on-premises data centers; Skytap’s environments simplify migration and provide self-service access to develop, deploy, and accelerate innovation for complex applications.
“Until we started working with Skytap, we did not have a public cloud option for our IBM Power Systems customers that provided real value over their on-premise systems. Now, with Skytap on Azure we’re excited to offer true cloud capabilities like instant cloning, capacity on demand and pay-as-you-go options in the highly secure Azure environment,” said Daniel Magid, CEO of Eradani.

Skytap on Azure offers consumption-based pricing, on-demand access to compute and storage resources, and extensibility through RESTful APIs. With Skytap availability on Azure Marketplace customers can get started quickly, and at a low cost. Learn more about Skytap on Azure here, additionally take a look at the latest video from our Microsoft Product team here.
Skytap on Azure is available in the East US Azure region. Given the high level of interest we have seen already, we intend to expand availability to additional regions across Europe, the United States, and Asia Pacific. Stay tuned for more details on specific regional rollout availability.
Try Skytap on Azure today, available through the Azure Marketplace. Skytap on Azure is a Skytap first-party service delivered on Microsoft Azure’s global cloud infrastructure.
Published on behalf of the Microsoft Azure Dedicated and Skytap on Azure Team
by Contributed | Nov 30, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Azure Sentinel Logic Apps connector is the bridge between Sentinel and Playbooks, serving as the basis of incident automation scenarios. As we prepare for new Incident Trigger capabilities (coming soon), we have made some improvements to bring the most updated experience to playbooks users.
Note: existing playbooks should not be effected. For new playbooks, we recommend using the new actions.
Highlights:
- Operate on most up-to-date Incidents API
- New dynamic fields are now available
- Less work to accomplish incident changes
- Assign Owner ability in playbooks
- Format rich comments in a playbook
What’s new?
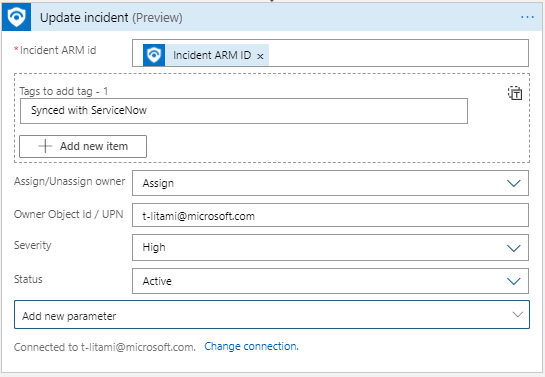
Update Incident: One action for all Incident properties configuration
Now it is simpler to update multiple properties at once for an incident. Identify the Incident you want to operate on and set new values for any field you want.
Update Incident replaces the actions: Change Incident Severity, Change Incident Status, Change Incident Title, Change Incident Description, Add/Remove Labels. They will still work in old playbooks, but eventually will be removed from the actions gallery for future use.

Assign Owner in playbooks
As part of new Update Incident, it is now possible to assign an owner to an incident in a playbook. For example, based on incident creation time and SecOps staffing information (for example, from a you can assign the incident to the right shift owners:
- Set Assign/Unassign owner to Assign
- Set Owner with the Object ID or User Principal Name.
Post Rich Comments with HTML editor
Recently, Azure Sentinel added support for HTML and Markdown for Incident Comments. Now, we added an HTML editor to the Add comment to Incident so you can format your comments.
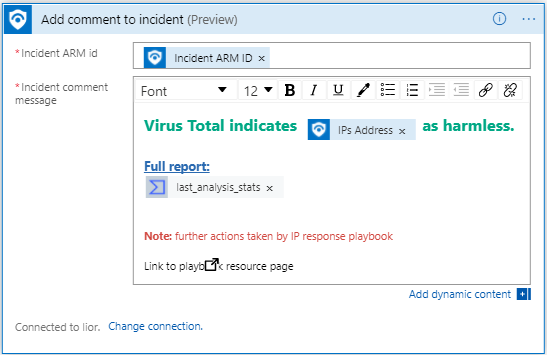
One identifier for working on Azure Sentinel Incidents
Previously, you had to supply 4 fields in order to identify the incident to update. New Update Incident and Add Comment to Incident require only one field (instead of 4) to identify the incident that meant to be changed: Incident ARM ID.
If your playbooks start with Azure Sentinel Alert trigger (When an Azure Sentinel Alert is Triggered), use Alert – Get Incident to retrieve this value.
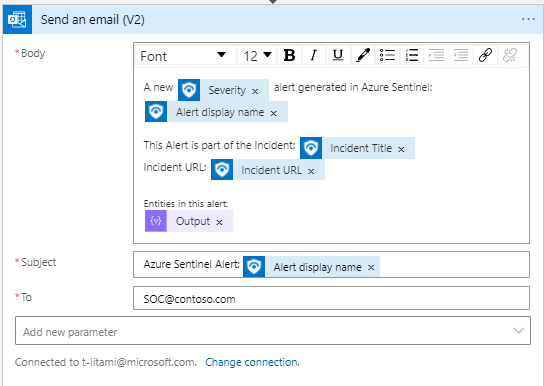
Get Incident: Now with most updated Sentinel API
Alert – Get Incident allows playbooks that start with Azure Sentinel Alert Trigger (When an alert is triggered) to reach the incident that holds the alert.
Now, new fields are available and are aligned to the Incident API.
For example, Incident URL can be included in an Email to the SOC shared mailbox or as part of a new ticket in Service Now, for easy access to the incident in the Azure Sentinel portal.
This action’s inputs have not changed, but the response became richer:
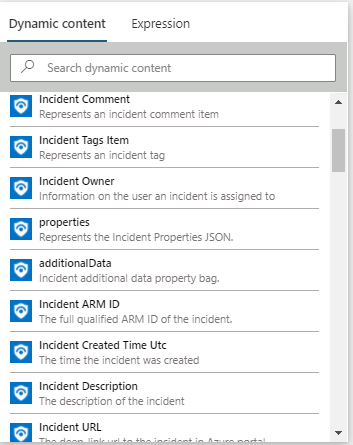
In addition, we supplied another action called Get Incident which allows you to identify incidents using the Incident ARM ID, so you can use any other Logic Apps trigger and still get Incident details. It returns the same Incident Schema. For example, if you work with another ticketing system which supports triggering Logic Apps, you can send the ARM ID as part of the request.
Get Entities: names change
As we prepare for our new Incident Trigger experience, when entities will be received both from incidents an alerts, we changed the name of the actions Alert – Get IPs/Accounts/URLs/Hosts/Filehashes to Entities – Get IPs/Accounts/URLs/Hosts/Filehashes.
Learn more
Azure Sentinel Connector documentation
by Scott Muniz | Nov 30, 2020 | Security
This article was originally posted by the FTC. See the original article here.
There’s a virtual “NO PARKING” sign planted smack in the middle of your credit report. It means that debt collectors can’t report your debt — or your supposed debt — to credit reporting agencies without first trying to check with you.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments