by Contributed | Apr 29, 2022 | Technology
This article is contributed. See the original author and article here.
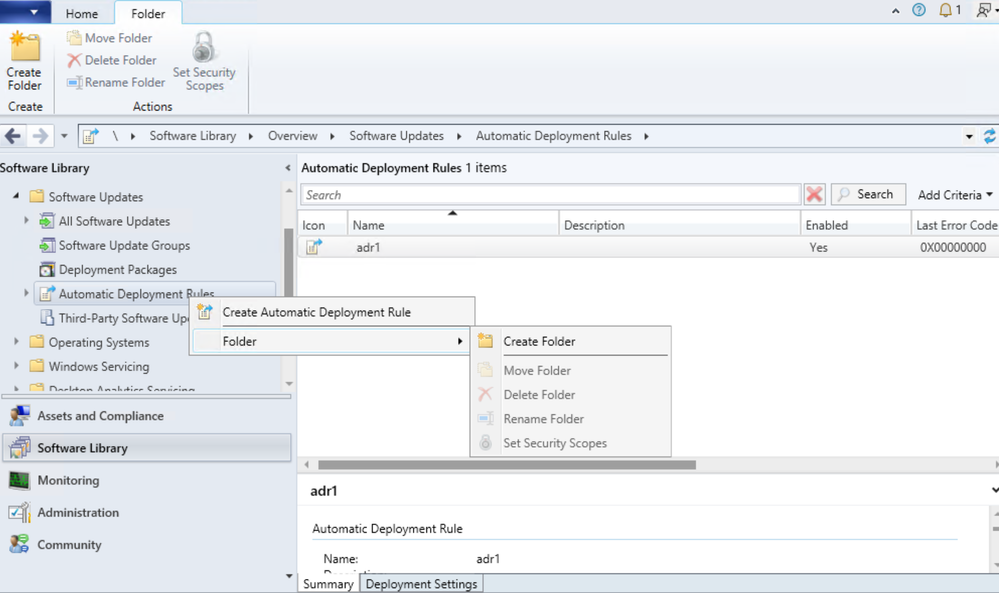
Update 2204 for the Technical Preview Branch of Microsoft Endpoint Configuration Manager has been released. In this release, administrators can now organize automatic deployment rules (ADR) using folders. This feature helps to enable better categorization and management of ADRs. Folder management is also supported with PowerShell Cmdlets.

This preview release also includes:
Administration Service Management option
When configuring Azure Services, a new option called Administration Service Management is now added for enhanced security. Selecting this option allows administrators to segment their admin privileges between cloud management gateway (CMG) and administration service. By enabling this option, access is restricted to only administration service endpoints. Configuration Management clients will authenticate to the site using Azure Active Directory.
Note:
Currently, the administration service management option can’t be used with CMG.
For more details and to view the full list of new features in this update, check out our Features in Configuration Manager technical preview version 2204 documentation.
Update 2204 for Technical Preview Branch is available in the Microsoft Endpoint Configuration Manager Technical Preview console. For new installations, the 2202 baseline version of Microsoft Endpoint Configuration Manager Technical Preview Branch is available on the Microsoft Evaluation Center. Technical Preview Branch releases give you an opportunity to try out new Configuration Manager features in a test environment before they are made generally available.
We would love to hear your thoughts about the latest Technical Preview! Send us feedback directly from the console.
Thanks,
The Configuration Manager team
Configuration Manager Resources:
Documentation for Configuration Manager Technical Previews
Try the Configuration Manager Technical Preview Branch
Documentation for Configuration Manager
Configuration Manager Forums
Configuration Manager Support
by Contributed | Apr 29, 2022 | Technology
This article is contributed. See the original author and article here.
The purpose of this series of articles is to describe some of the details of how High Availability works and how it is implemented in Azure SQL Managed Instance in both Service Tiers – General Purpose and Business Critical.
In this post, we shall introduce some of the high availability concepts and then dive into the details of the General Purpose service tier.
Introduction to High Availability
The goal of a high-availability solution is to mask the effects of a hardware or software failure and to maintain database availability so that the perceived downtime for users is minimized. In other words, high availability is about putting a set of technologies into place before a failure occurs to prevent the failure from affecting the availability of data.
The two main requirements around high availability are commonly known as RTO and RPO.
RTO – stands for Recovery Time Objective and is the maximum allowable downtime when a failure occurs. In other words, how much time it takes for your databases to be up and running.
RPO – stands for Recovery Point Objective and is the maximum allowable data-loss when a failure occurs. Of course, the ideal scenario is not to lose any data, but a more realistic (and also ideal) scenario is to not lose any committed data, also known as Zero Committed Data Loss.
In SQL Managed Instance the objective of the high availability architecture is to guarantee that your database is up and running 99.99% of the time (financially backed up by an SLA) minimizing the impact of maintenance operations (such as patching, upgrades, etc.) and outages (such as underlying hardware, software, or network failures) that might occur.
High Availability in the General Purpose service tier
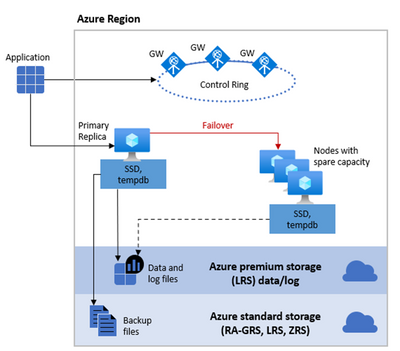
General Purpose service tier uses what is called the Standard Availability model. This architecture model is based on a separation of compute and storage. It relies on the high availability and reliability provided by the remote storage tier. This architecture is more suitable for budget-oriented business applications that can tolerate some performance degradation during maintenance activities.
The Standard Availability model includes two layers:
A stateless compute layer that runs the sqlservr.exe process and contains only transient and cached data, such as tempdb database, that resides on the attached SSD Disk, and memory structures such as the plan cache, the buffer pool, and columnstore pool that resides on memory.
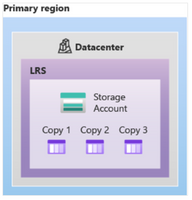
It also contains a stateful data layer where the user database data & log files reside in an Azure Blob storage. This type of repository has built-in data availability and redundancy features (Local Redundant Storage or LRS). It guarantees that every record in the log file or page in the data file will be preserved even if sqlservr.exe process crashes.

The behavior of this architecture is similar to an SQL Server FCI (SQL Server Failover Cluster Instance) but without all the complexity that we currently have on-premises or in an Azure SQL VM. In that scenario we would need to first create and configure a WSFC (Windows Server Failover Cluster) and then create an SQL Server FCI (SQL Server Failover Cluster Instance). All of this is done behind the curtains for you when you provision an Azure SQL Managed Instance, so you don’t need to worry about it. As you can see from the diagram on the picture above, we have a shared storage functionality (again like in an SQL Server FCI), in this case in Azure premium storage, and also we have a stateless node, operated by Azure Service Fabric. The stateless node not only initializes sqlservr.exe process but also monitors & controls the health of the node and, if necessary, performs the failover to another node from a pool of spare nodes.
All the technical aspects and fine-tuning of a cluster (i.e. quorum, lease, votes, network issues, avoiding split-brain, etc.) are covered & managed transparently by the Azure Service Fabric. The specific details of Azure Service Fabric go beyond the scope of this article, but you can find more information in the article Disaster recovery in Azure Service Fabric.
From the point of view of an application connected to an Azure SQL Managed Instance, you don’t have the concept of Listener (like in an Availability Groups implementation) or Virtual Name (like in an SQL Server FCI) – you connect to an endpoint via a Gateway. This is also an additional advantage since the Gateway is in charge of “redirecting” the connection to the Primary Node or a new Node in case of a Failover, so you don’t have to worry about changing the connection string or anything like that. Again, this is the same functionality that the Virtual Name or Listener provides, but more transparently to you. Also, notice in the Diagram above that we have redundancy on the Gateways to provide an additional level of availability.
Below is a diagram of the connection architecture, in this case using the Proxy connection type, which is the default:
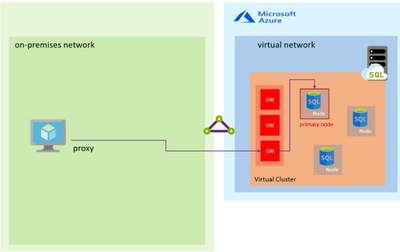
In the Proxy connection type, the TCP session is established using the Gateway and all subsequent packets flow through it.
Storage
Regarding Storage, we use the same concept of “Shared Storage” that is used in a FCI but with additional advantages. In a traditional FCI On-Prem the Storage becomes what is known as a “Single Point of Failure” meaning that if something happens with the Storage – your whole Cluster solution goes down. One of the possible ways customers could work around this problem is with “Block Replication” technologies of the Storage (SAN) Providers replicating this shared Storage to another Storage (typically between a long distance for DR purposes). In SQL Managed Instance we provide this redundancy, using Azure Premium Storage for Data and Log files, with Local Redundancy Storage (LRS) and also separating the Backup Files (following our Best Practices) in an Azure Standard Storage Account also making them redundant using RA-GRS (Read Access Geo Redundant Storage). To know more about redundancy of backups files take a look at the post on Configuring backup storage redundancy in Azure SQL.
For performance reasons, the tempdb database is kept local in an SSD where we provide 24 GB per each of the allocated CPU vCores.
The following diagram illustrates this storage architecture:
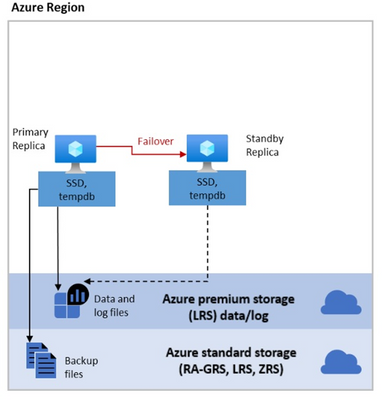
It is worth mentioning that Locally Redundant Storage (LRS) replicates your data three times within a single data center in the primary region. LRS provides at least 99.999999999% (11 nines) durability of objects over a given year.
To find out more about redundancy in Azure Storage please see the following article in Microsoft documentation – https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy.
Failover
The process of Failover is very straightforward and of course you can have either a “planned failover” – such as a user-initiated manual failover or a system-initiated failover taking place because of a database engine or operating system upgrade operation, and an “unplanned failover” taking place due to a failure detection (i.e. hardware, software, network failure, etc.).
Regarding an “unplanned” or an “unexpected” failover, when there are critical errors in the Azure SQL Managed Instance functioning, an API call is made to communicate the Azure Service Fabric that a Failover needs to happen. Of course, the same happens when other errors (like a faulty node) are detected. In this case, the Azure Service Fabric will move the stateless sqlservr.exe process to another stateless compute node with sufficient free capacity. Data in Azure Blob storage is not affected by the move, and the data/log files are attached to the newly initialized sqlservr.exe process. After that a Recovery Process on the Databases is initiated. This process guarantees 99.99% availability, but a heavy workload may experience some performance degradation during the transition since the new sqlservr.exe process starts with cold cache.
Since a Failover can occur unexpectedly, customer might need to determine if such event took place and for that purpose customer can determine the timestamp of the last Failover with the help of T-SQL as described in the article How-to determine the timestamp of the last SQL MI failover from the SQL MI how-to series.
Also, you could see the Failover event listed in the Activity Log using the Azure Portal.
Below is a diagram of the failover process:
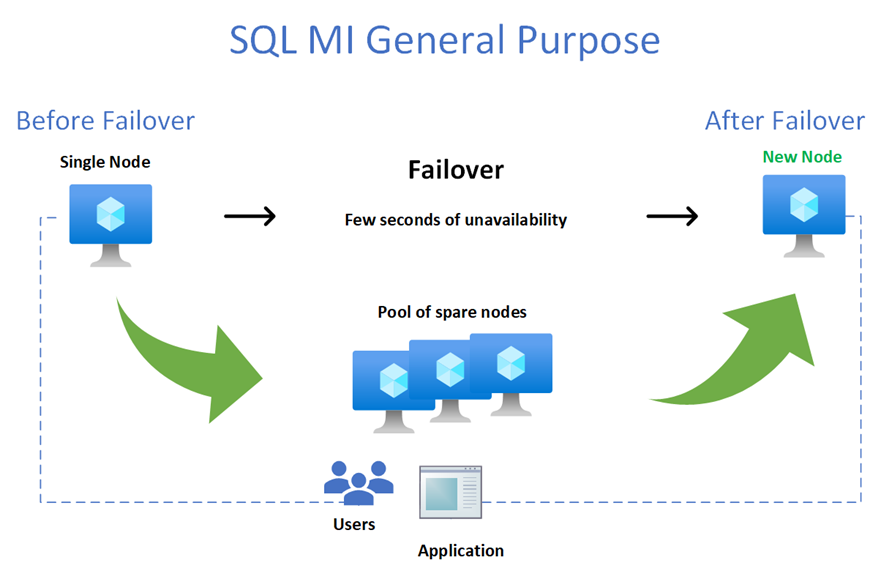
As you can see from the diagram, on the picture above, the Failover process will introduce a brief moment of unavailability while a new node from the Pool of spares nodes is allocated. In order to minimize the impact of a failover you would need to incorporate in your application a retry-logic. This is normally accomplished detecting the transient errors during a failover (4060, 40197, 40501, 40613, 49918, 49919, 49920, 11001) within a try-catch block of code, waiting a couple of seconds and then retrying the connection (re-connect). Alternatively, you could use the Microsoft.Data.SqlClient v3.0 Preview NuGet package in your application that have already incorporated a retry logic. To know more about this driver see the following article: Introducing Configurable Retry Logic in Microsoft.Data.SqlClient v3.0.0
Notice that that currently that only one failover call is allowed every 15 minutes.
In this article we have introduced the concepts of high availability and explained how it is implemented for the General Purpose service tier. In the second part of where we will cover High Availability in the Business Critical service tier.
by Contributed | Apr 28, 2022 | Technology
This article is contributed. See the original author and article here.
On November 10, 2020, we announced the first preview of Az.Tools.Predictor, a PowerShell module suggesting the Azure cmdlet to use with parameters and suggested values.
Today, we are announcing the general availability of Az.Tools.Predictor.
How it all started
During a study about a new module for Azure, I was surprised to see how difficult it was for the participant to find the correct cmdlet to use. Later, I was summarizing the learnings of the study, and though it would be great if we could have a solution that could help people finding the right cmdlet to use.
At the same time, we were starting to work on Predictive IntelliSense in PowerShell and after a couple of meetings with Jason Helmick, it became clear that this would be a great mechanism to address the challenge I had seen few days before by providing, in the command line, suggestions about cmdlet to use.
We quickly thought that some form of AI could help providing accurate recommendations so we involved Roshanak, Yevhen and Maoliang from our data science team to work with us on how we could build an engine that would provide recommendations for PowerShell cmdlets based on the user’s context.
Behind the scenes
Once a functional prototype was built, we wanted to confirm its usability before considering any public previews.
For our team usability is important, over time certain key combinations became a reflex and we knew that we had to fit in the existing memory muscle and become intuitive for PowerShell. For predictors to be successful, we organized several usability studies with prototypes of Az Predictors and addressed several improvements, like the color of the suggested text or the key combination to use to accept or navigate amongst predictions.
One of our initial prototypes was using the color scheme below, we wanted to have a clear color-based differentiation between typed characters and suggestions hoping this would help user navigate the suggestion. We worked with our design team to address the issue and evolve our design towards the current design.

We also evaluated if the information provided in the suggestions is helpful. Below is another of our early designs. By listening to our customers and observing how they are using the tool, we learned that showing cmdlets first then parameters and associated value samples was not as useful as showing the full line and not using more space in the terminal which is our current design.

During the last months we have done a few previews (read about preview 5) to stabilize the module as PowerShell and PS Readline which we depend on became stable. We have also improved our model based on the feedback we have collected and addressed issues reported.
Getting started
We would like to invite you to try the stable version of Az.Tools.Predictor.
To get started, follows these steps:
- Install or upgrade PowerShell v7.2
https://docs.microsoft.com/powershell/scripting/install/installing-powershell
- Install or upgrade PSReadline 2.2
Install-Module -Name PSReadLine -Force
- Install or upgrade Az.Tools.Predictor
Install-module -name Az.Tools.Predictor -Force
- Enable Az Predictor
Enable-AzPredictor -AllSession
Once installed, it is recommended that you restart your PowerShell sessions.
For more details, visit the Az Predictor documentation page: https://docs.microsoft.com/powershell/azure/az-predictor
Inline view mode (default)
Once enabled, the default view is the “inline view” as shown in the following screen capture:

This mode shows only one suggestion at a time. The suggestion can be accepted by pressing the right arrow or you can continue to type. The suggestion will dynamically adjust based on the text that you have typed.
You can accept the suggestion at any time then come back and edit the command that is on your prompt.
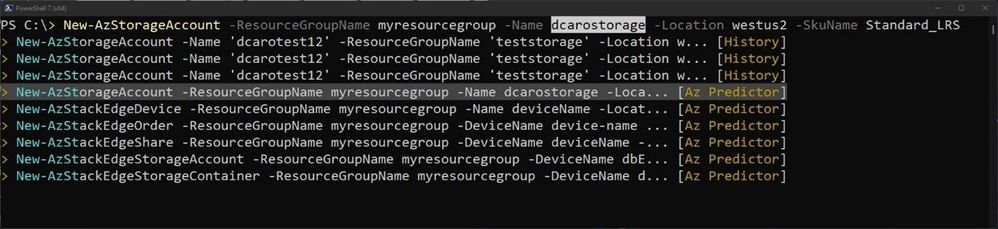
List view mode
This is my favorite mode!
Switch to this view either by using the “F2” function key on your keyboard or run the following command:
Set-PSReadLineOption -PredictionViewStyle ListView
This mode shows from your current prompt a list of possible matches for the command that you are typing. It combines suggestions from your local history and from Az Predictor.
Select a suggestion and then navigate through the parameter values with “Alt + A” to quickly fill replace the proposed values with yours.
Next steps
This is just the beginning of our journey to improving the usability of Azure PowerShell!
We will be carefully listening to every feedback that you send us:
We will share soon more about how we plan to expand this experience to other environments.
Credits
“It takes a village to raise a child” Az.Tools.Predictor is the result of the close collaboration of several teams distributed across continents and time zones working hard during the pandemic.
![MAR-10376640-1.v1 – IsaacWiper and HermeticWizard]()
by Scott Muniz | Apr 28, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Notification
This report is provided “as is” for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise.
This document is marked TLP:WHITE–Disclosure is not limited. Sources may use TLP:WHITE when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.cisa.gov/tlp.
Summary
Description
CISA received six files for analysis: five 32-bit Dynamic-link Library (DLL) files and one 32-bit executable file. These files have been identified as IsaacWiper and HermeticWizard. During analysis of HermeticWizard, another file was dropped and identified as HermeticWiper. The submitted files are designed to spread laterally through a network via Server Message Block (SMB) and Windows Management Instrumentation (WMI). These files attempt to overwrite the first 65536 bytes of data contained on the C: drive as well as any attached storage disks in order to render them useless to the victim user. The malware also creates a file and continuously writes to it until the disk runs out of free space and crashes. Upon reboot, the machine is no longer operable.
For a downloadable copy of IOCs, see: MAR-10376640-1.v1.stix.
Submitted Files (6)
13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033 (Cleaner.dll)
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b (exec_x32.dll)
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 (romance.dll)
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec (Wizard.dll)
abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f (Cleaner.dll)
afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a (Cleaner.exe)
Findings
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48
Tags
backdoortrojanwiperworm
Details
| Name |
romance.dll |
| Size |
348424 bytes |
| Type |
PE32 executable (DLL) (console) Intel 80386, for MS Windows |
| MD5 |
0959bf541d52b6e2915420442bf44ce8 |
| SHA1 |
ac5b6f16fc5115f0e2327a589246ba00b41439c2 |
| SHA256 |
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 |
| SHA512 |
b08ce87165b82db5a35353f9e42665fa9e736603b8e131e46501c0bbf4c830abbaba7bdbb5513af6201f19ba6741aa86b7cf736a8d92fef2c43a90383bf9ba68 |
| ssdeep |
6144:zB0WZ3twfUMDH34YslWeXEuS0dOIB9LcO1bJ/fKtn7eENm2eK7mnoUSgpAY8ODcV:lDRtSUMDH34DlWQEuS0UIzLR1NXKtn7f |
| Entropy |
6.683668 |
Antivirus
| Avira |
WORM/Agent.pjgwz |
| Bitdefender |
Trojan.GenericKD.48563945 |
| Cyren |
W32/Agent.XHXW-4345 |
| ESET |
Win32/Agent.OJC worm |
| Emsisoft |
MalCert-S.OE (A) |
| IKARUS |
Worm.Win32.Agent |
| K7 |
Trojan ( 0058f30e1 ) |
| Lavasoft |
Trojan.GenericKD.48563945 |
| McAfee |
Exploit-DcomRpc.c.gen |
| Quick Heal |
APEXCFC.Backdoor.Gen |
| Sophos |
Mal/BadCert-Gen |
| Symantec |
Trojan.KillDisk |
| Trend Micro |
Worm.Wi.A1D01B0A |
| Trend Micro HouseCall |
Worm.Wi.A1D01B0A |
| VirusBlokAda |
Worm.Hermetic |
| Zillya! |
Worm.Agent.Win32.99417 |
YARA Rules
- rule CISA_10376640_02 : trojan wiper worm HERMETICWIZARD
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-03-12”
Last_Modified = “20220413_1300”
Actor = “n/a”
Category = “Trojan Wiper Worm”
Family = “HERMETICWIZARD”
Description = “Detects Hermetic Wizard samples”
MD5_1 = “0959bf541d52b6e2915420442bf44ce8”
SHA256_1 = “5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48”
strings:
$s0 = { 70 00 69 00 70 00 65 00 5C 00 25 00 73 }
$s1 = { 6E 00 6D 00 61 00 6E 00 73 00 65 00 72 00 76 }
$s2 = { 73 61 6D 72 }
$s3 = { 62 72 6F 77 73 65 72 }
$s4 = { 6E 65 74 6C 6F 67 6F 6E }
$s5 = { 6C 73 61 72 70 63 }
$s6 = { 6E 74 73 76 63 73 }
$s7 = { 73 76 63 63 74 6C }
$s8 = { 73 74 61 72 74 20 63 6D 64 20 2F 63 20 22 70 69 6E 67 20 6C 6F 63 61 6C 68 6F 73 74 }
$s9 = { 67 00 75 00 65 00 73 00 74 }
$s10 = { 74 00 65 00 73 00 74 }
$s11 = { 75 00 73 00 65 00 72 }
$s12 = { 61 00 64 00 6D 00 69 00 6E 00 69 00 73 00 74 00 72 00 61 00 74 00 6F }
$s13 = { 51 00 61 00 7A 00 31 00 32 00 33 }
$s14 = { 51 00 77 00 65 00 72 00 74 00 79 00 31 00 32 }
$s15 = { 63 6D 64 20 2F 63 20 73 74 61 72 74 20 72 65 67 }
condition:
all of them
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2022-02-22 02:30:07-05:00 |
| Import Hash |
0802be27b58612f1b2648b8a57d1acfd |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| 6ca6e4584fdfe512c2567bc3df334540 |
header |
1024 |
2.665881 |
| 023be81d5f495e7428cde5d930ecf8ce |
.text |
286208 |
6.662690 |
| 5ed93c823af444567d6fac7c5b868db8 |
.rdata |
43008 |
5.287553 |
| d2ceb15c0042bf0981352c5e7af10677 |
.data |
3584 |
3.239415 |
| 84a3f07cc1f758d0993531a1da9e3f6a |
.reloc |
10752 |
6.623638 |
Packers/Compilers/Cryptors
Relationships
| 5a300f72e2… |
Contained_Within |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| 5a300f72e2… |
Dropped_By |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
Description
This application is a 32-bit DLL and has been identified as HermeticWizard. A filename is generated for the malware using the string ‘c%02X%02X%02X%02X%02X%02X’, which will create a random set of 12 characters, 6 hex bytes beginning with ‘c’. The purpose of the DLL is to spread to other machines over the SMB protocol to the Admin Share (IPC$). The malware attempts to authenticate through SMB using a set of hard-coded usernames and passwords.
–Begin Usernames–
guest
test
admin
user
root
administrator
manager
operator
–End Usernames–
–Begin Passwords–
123
Qaz123
Qwerty123
–End Passwords–
The malware is designed to use the command-line parameters below for execution:
–Begin command-line–
cmd /c start regsvr32.exe /s /i..<malicious DLL>
& start cmd /c “ping localhost -n 7 & wevtutil cl System
–End command-line–
Screenshots

Figure 1 – This screenshot shows the hard-coded usernames and passwords used to attempt authentication with the target machine.

Figure 2 – This screenshot shows the malware establishing a connection via the SMB protocol.
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b
Tags
backdoortrojanwiperworm
Details
| Name |
exec_x32.dll |
| Size |
122632 bytes |
| Type |
PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5 |
58d71fff346017cf8311120c69c9946a |
| SHA1 |
6b5958bfabfe7c731193adb96880b225c8505b73 |
| SHA256 |
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b |
| SHA512 |
315cc419f6ec600a345447b0f49e3de9f13c1e96d9bbc272f982204b1c7ec71cb3805f5ff7821da3e7944e327c22e5eba6f3c94b08c66b6e241395e1ea133ed1 |
| ssdeep |
3072:gnu7OIMtlhyAnF1bIoENm2eK7mnoUSgpAY8ODcDcm7cIsF4RO06loHGvJnuqO:g4OlhlzjENm2eK7mnoUSgpAY8ODcDcmT |
| Entropy |
6.646213 |
Antivirus
| AhnLab |
Trojan/Win.FoxBlade |
| Avira |
WORM/Agent.juikt |
| Bitdefender |
Trojan.GenericKD.39179683 |
| ESET |
Win32/Agent.OJC worm |
| Emsisoft |
MalCert-S.OE (A) |
| IKARUS |
Worm.Win32.Agent |
| K7 |
Trojan ( 00028d131 ) |
| Lavasoft |
Trojan.GenericKD.39179683 |
| Quick Heal |
APEXCFC.Backdoor.Gen |
| Sophos |
Mal/BadCert-Gen |
| Symantec |
Trojan.Gen.2 |
| Trend Micro |
Worm.Wi.A1D01B0A |
| Trend Micro HouseCall |
Worm.Wi.A1D01B0A |
| VirusBlokAda |
Trojan.Agent |
| Zillya! |
Worm.Agent.Win32.99414 |
YARA Rules
- rule CISA_10376640_03 : trojan wiper worm HERMETICWIZARD
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-03-13”
Last_Modified = “20220413_1300”
Actor = “n/a”
Category = “Trojan Wiper Worm”
Family = “HERMETICWIZARD”
Description = “Detects Hermetic Wizard samples”
MD5_1 = “58d71fff346017cf8311120c69c9946a”
SHA256_1 = “2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b”
strings:
$s0 = { 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F }
$s1 = { 5C 00 5C 00 25 00 73 00 5C 00 70 00 69 00 70 00 65 00 5C 00 25 00 73 }
$s2 = { 64 00 6C 00 6C 00 00 00 2D 00 69 }
$s3 = { 2D 00 68 00 00 00 00 00 2D 00 73 }
$s4 = { 2D 00 63 00 00 00 00 00 2D 00 61 }
$s5 = { 43 6F 6D 6D 61 6E 64 4C 69 6E 65 54 6F 41 72 67 76 57 }
condition:
all of them
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2022-02-22 02:23:15-05:00 |
| Import Hash |
0efd6cfc0613f20a06fa0746b2d5b8bc |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| 90d5fe0b84e27aef0c20e1f645feb2b0 |
header |
1024 |
2.713966 |
| 6e7013478def0b223ed6acb0a52fad70 |
.text |
81408 |
6.654914 |
| b63a5c496bdfc65b0a87074ddb5ea3ea |
.rdata |
29184 |
5.513656 |
| cd29db9b4e978a706ddf3195b7a6b9b9 |
.data |
2560 |
2.223270 |
| 463a2a119664cff0f6ea5941379a7700 |
.reloc |
4608 |
6.499252 |
Packers/Compilers/Cryptors
Relationships
| 2d29f9ca1d… |
Contained_Within |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| 2d29f9ca1d… |
Dropped_By |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
Description
This is a 32-bit DLL file. This DLL spreads laterally through the network via the WMI protocol. The malware copies a file over to the target machine for execution. This copied filename is generated using the string ‘c%02X%02X%02X%02X%02X%02X’ which will create a random set of 12 characters, 6 hex bytes beginning with ‘c’. The copied file has been identified as HermeticWizard. The malware identifies a running process with a desired authority and uses the token for impersonation to create a new process and service to launch the copied file.
–Begin command-line–
cmd /c start
regsvr32.exe /s /i <malicious DLL path>
–End command-line–
Screenshots

Figure 3 – This screenshot shows the malware authority type and impersonation.
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec
Tags
backdoortrojanworm
Details
| Name |
Wizard.dll |
| Size |
698632 bytes |
| Type |
PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5 |
517d2b385b846d6ea13b75b8adceb061 |
| SHA1 |
3c54c9a49a8ddca02189fe15fea52fe24f41a86f |
| SHA256 |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| SHA512 |
1de912f50b7f5cc2f4fcea7b6d3c84a39bd15d668122f50a9b11da66447ed99f456e86e006d0dfe7ab0fca7dc8e35efa7ff57959033463d94ef37e5705515430 |
| ssdeep |
12288:J4WCTqjtByJsZrjIYlkytnSg9hcr1DnDH2iRNL5tj1XUNgASK4CTfVf1WZ62PNTr:HGqRBRtnSEhMhDH2iRNL5tj1XUNgASKw |
| Entropy |
7.451862 |
Antivirus
| AhnLab |
Trojan/Win.FoxBlade |
| Antiy |
Trojan/Win32.Agent |
| Avira |
WORM/Agent.sejyu |
| Bitdefender |
Trojan.GenericKD.48550079 |
| ClamAV |
Win.Malware.HermeticWizard-9941571-0 |
| ESET |
Win32/Agent.OJC worm |
| Emsisoft |
MalCert-S.OE (A) |
| IKARUS |
Worm.Win32.Agent |
| K7 |
Trojan ( 0058f30e1 ) |
| Lavasoft |
Trojan.GenericKD.48550079 |
| McAfee |
Generic trojan.wh |
| NANOAV |
Trojan.Win32.TrjGen.jngwij |
| Quick Heal |
APEXCFC.Backdoor.Gen |
| Sophos |
Mal/BadCert-Gen |
| Symantec |
Trojan.Gen.MBT |
| TACHYON |
Trojan/W32.HermeticWizard.698632 |
| Trend Micro |
Worm.Wi.38D94AB0 |
| Trend Micro HouseCall |
Worm.Wi.38D94AB0 |
| VirusBlokAda |
BScope.Trojan.Agent |
| Zillya! |
Worm.Agent.Win32.99423 |
YARA Rules
- rule CISA_10376640_05 : trojan wiper worm HERMETICWIZARD
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-04-14”
Last_Modified = “20220414_1037”
Actor = “n/a”
Category = “Trojan Wiper Worm”
Family = “HERMETICWIZARD”
Description = “Detects Hermetic Wizard samples”
MD5_1 = “517d2b385b846d6ea13b75b8adceb061”
SHA256 = “a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec”
strings:
$s0 = { 57 69 7A 61 72 64 2E 64 6C 6C }
$s1 = { 69 6E 66 6C 61 74 65 }
$s2 = { 4D 61 72 6B 20 41 64 6C 65 72 }
condition:
all of them and filesize < 2000KB
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2022-02-22 03:07:17-05:00 |
| Import Hash |
e099d3524b6906cf8460b4e6db0b11f2 |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| 01185a4f21be653f13b885a655da2239 |
header |
1024 |
2.945954 |
| d7ed7d880b3eed5eae7787055766502c |
.text |
312832 |
6.633510 |
| 87728459f7938f00f8d53d0bd6e6a337 |
.rdata |
60416 |
5.802039 |
| 31b2ae0f6a40196c4bce89d36302d545 |
.data |
3584 |
2.914857 |
| d77cbf49cf473a8235a67912f0edd78f |
.rsrc |
304128 |
7.948029 |
| 32ec2dc9dc4b9fc8f96ac18835fea101 |
.reloc |
12800 |
6.692458 |
Packers/Compilers/Cryptors
Relationships
| a259e9b0ac… |
Contains |
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 |
| a259e9b0ac… |
Contains |
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b |
| a259e9b0ac… |
Dropped |
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 |
| a259e9b0ac… |
Dropped |
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b |
Description
This is a 32-bit DLL and has been identified as HermeticWizard. The original filename for the DLL is Wizard.dll. It is designed to use the command-line parameters below for execution:
–Begin command-line–
regsvr32.exe /s /i <malicious DLL path>
–End command-line–
The application contains three 32-bit encrypted binaries that are decrypted and installed into the current directory at runtime.
–Begin files–
%current directory%exec_x32.dll
%current directory%romance.dll
%current directory%<6 randomly generated alphanumerical characters>.ocx
–End files–
At runtime, it attempts to detect all active hosts on the victim’s network. It is capable of moving laterally across the network by actively scanning ranges of reachable IP version 4 addresses and ports. It is designed to create and connect to multiple name pipes.
Displayed below are the list of port numbers it attempts to connect to.
–Begin port numbers–
20
21
22
80
135
137
139
443
445
–End port numbers–
Once an active host (system) is found, it attempts to execute the command-line below to move to the reachable machine:
–Begin command–
“C:WindowsSystem32rundll32.exe %current directory%<6 randomly generated alphanumerical characters>.ocx #1 -s <path to Wizard.dll> – i <reachable system IP address>”
–End command–
It executes the file <6 randomly generated alphanumerical characters>.ocx binary to wipe the drive. This OLE Control Extension (OCX) file has been identified as HermeticWiper. The SHA256 of the OCX file is 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da. Note: Analysis of this file is included in MAR-10375867.r1.v1.WHITE.
Screenshots

Figure 4 – This screenshot shows the functionalities used to perform local network enumeration.
abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f
Tags
trojan
Details
| Name |
Cleaner.dll |
| Size |
11264 bytes |
| Type |
PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5 |
aa98b92e3320af7a1639de1bac6c17cc |
| SHA1 |
ad602039c6f0237d4a997d5640e92ce5e2b3bba3 |
| SHA256 |
abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f |
| SHA512 |
5549bdb658736c187c2d6493c82f46461dda728a0ec365833bf1987e9436a5f9e1a42cab68082af2640b5a10ab92aa9251095d3b453934d3ebeb211bfd42b212 |
| ssdeep |
192:bqSlxiV3BdNHxRvb8WZVPspRgssSt7NCphJHlHMjz5e:dnYx5RvYW3mQphJHVMjc |
| Entropy |
5.648075 |
Antivirus
| ESET |
a variant of Win32/KillMBR.NHP trojan |
| Trend Micro |
Trojan.9FABA348 |
| Trend Micro HouseCall |
Trojan.9FABA348 |
YARA Rules
- rule CISA_10376640_01 : trojan wiper ISAACWIPER
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-03-14”
Last_Modified = “20220418_1900”
Actor = “n/a”
Category = “Trojan Wiper”
Family = “ISAACWIPER”
Description = “Detects ISACC Wiper samples”
MD5_1 = “aa98b92e3320af7a1639de1bac6c17cc”
SHA256_1 = “abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f”
MD5_2 = “8061889aaebd955ba6fb493abe7a4de1”
SHA256_2 = “afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a”
MD5_3 = “ecce8845921a91854ab34bff2623151e”
SHA256_3 = “13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033”
strings:
$s0 = { 73 00 74 00 61 00 72 00 74 00 20 00 65 00 72 00 61 00 73 00 69 00 6E 00 67 }
$s1 = { 6C 00 6F 00 67 00 69 00 63 00 61 00 6C }
$s2 = { 46 00 41 00 49 00 4C 00 45 00 44 }
$s3 = { 5C 00 6C 00 6F 00 67 00 2E 00 74 00 78 00 74 }
$s4 = { 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F }
$s5 = {53 74 61 72 74 40 34}
$s6 = {3B 57 34 74 2D 6A}
$s7 = {43 6C 65 61 6E 65 72 2E}
condition:
all of ($s0,$s1,$s2,$s3,$s4) or all of ($s5,$s6,$s7)
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2021-10-19 10:17:30-04:00 |
| Import Hash |
8156382b4b0f02a7467108b32103b82a |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| 1e9e616d75f50f562b0d56edc472a8ea |
header |
1024 |
2.226630 |
| decfc792ded248587084a6329217380e |
.text |
7680 |
6.321812 |
| 99ec3d78dee2e180fa53da106a9a7540 |
.rdata |
1536 |
3.859100 |
| 9475a59226943a3ad422e18169989f66 |
.data |
512 |
0.020393 |
| 60a3ce8706953c03b2a4f22e43dccb26 |
.reloc |
512 |
2.886370 |
Description
Cleaner.dll is a 32-bit DLL which has been identified as a variant of the IsaacWiper. It attempts to overwrite the first 65536 bytes of data on the C: drive and on attached storage disks in order to render them useless to the victim user. The malware also overwrites the victim user’s files so they cannot be recovered. The data used to overwrite the disk drives and user files is random data that is generated via the Mersenne Twister algorithm.
Cleaner.dll also attempts to create a directory in the root directory of attached storage disks. The malware will then create a file within this newly created directory and attempt to fill it with random data, generated via the Mersenne Twister algorithm, in an effort to fill the drive up as another destructive method of rendering the storage device unusable to the victim user. The name of the folder created will begin with the letters “Tmd” and the remaining part of the folder name will be randomly generated alphanumerical characters. The filename created will begin with the letters “Tmf” and the remaining part of the filename will be randomly generated alphanumerical characters.
Displayed below is the format of the file installed:
–Begin file–
Filename: “C:’Tmd[4 randomly generated characters]Tmf[4 randomly generated alphanumerical characters].tmp”
Sample: “C:Tmd21D9.tmpTmf1E9E.tmp”
–End file–
Analysis indicates that the application fails to execute if the above tmp file already exists on the victim’s machine.
Screenshots

Figure 5 – This screenshot illustrates the malware overwriting the first 65536 bytes of the C: drive, or attached storage disk, using random encrypted data generated via the Mersenne Twister algorithm.

Figure 6 – This screenshot illustrates a sample file created by the malware. This malware will write random encrypted data to this file until the C: drive and attached storage devices runs out of space. This is just one method the malware utilizes in an attempt to corrupt the victim user’s machine.
afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a
Tags
trojan
Details
| Name |
Cleaner.exe |
| Size |
11264 bytes |
| Type |
PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5 |
8061889aaebd955ba6fb493abe7a4de1 |
| SHA1 |
e9b96e9b86fad28d950ca428879168e0894d854f |
| SHA256 |
afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a |
| SHA512 |
27874dca36c2ebe3ac240c3c6592093ef8cd09611ede1e16de22357bea35dfb70065c2545b6381a19198139b9591e2f4fe0f882483f418a9bd2e0c2f126a0b09 |
| ssdeep |
192:9ClgiV30I+0Kxn+rgRvb865VPkMsuW089mNCEFlggO4C6z5C:gmYLY5RvY6XW0ZQslggPC6 |
| Entropy |
5.628275 |
Antivirus
| Avira |
TR/Crypt.XPACK.Gen8 |
| ESET |
a variant of Win32/KillMBR.NHP trojan |
| Trend Micro |
Trojan.9FABA348 |
| Trend Micro HouseCall |
Trojan.9FABA348 |
YARA Rules
- rule CISA_10376640_01 : trojan wiper ISAACWIPER
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-03-14”
Last_Modified = “20220418_1900”
Actor = “n/a”
Category = “Trojan Wiper”
Family = “ISAACWIPER”
Description = “Detects ISACC Wiper samples”
MD5_1 = “aa98b92e3320af7a1639de1bac6c17cc”
SHA256_1 = “abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f”
MD5_2 = “8061889aaebd955ba6fb493abe7a4de1”
SHA256_2 = “afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a”
MD5_3 = “ecce8845921a91854ab34bff2623151e”
SHA256_3 = “13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033”
strings:
$s0 = { 73 00 74 00 61 00 72 00 74 00 20 00 65 00 72 00 61 00 73 00 69 00 6E 00 67 }
$s1 = { 6C 00 6F 00 67 00 69 00 63 00 61 00 6C }
$s2 = { 46 00 41 00 49 00 4C 00 45 00 44 }
$s3 = { 5C 00 6C 00 6F 00 67 00 2E 00 74 00 78 00 74 }
$s4 = { 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F }
$s5 = {53 74 61 72 74 40 34}
$s6 = {3B 57 34 74 2D 6A}
$s7 = {43 6C 65 61 6E 65 72 2E}
condition:
all of ($s0,$s1,$s2,$s3,$s4) or all of ($s5,$s6,$s7)
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2022-02-24 04:48:46-05:00 |
| Import Hash |
fd8214e8ca810e64eb947f522acbead7 |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| c1ecc108a6c84989eb4102d2d387c3cb |
header |
1024 |
2.235812 |
| 12bbe2ed84c503c161528eb9c65e06b7 |
.text |
7680 |
6.297084 |
| a84958d0a1ba6ccf7f68b0f082a1c656 |
.rdata |
1536 |
3.901725 |
| 9475a59226943a3ad422e18169989f66 |
.data |
512 |
0.020393 |
| 4c8100d03804167a977995936cfbf536 |
.reloc |
512 |
2.937988 |
Description
Cleaner.exe is a 32-bit executable file (EXE) which has been identified as another variant of the IsaacWiper. It can be executed immediately or has a sleep function for 15 minutes. When executed, it attempts to overwrite the first 65536 bytes of data contained on the C: drive and on attached storage disks in order to render them useless to the victim user. The malware also overwrites the victim user’s files so they cannot be recovered. The data used to overwrite the disk drives and user files is random data that is generated via the Mersenne Twister algorithm.
Cleaner.exe also attempts to create a directory in the root directory of attached storage disks. The malware will then create a file within this newly created directory and attempt to fill it with random data, generated via the Mersenne Twister algorithm, in an effort to fill the drive up as another destructive method of rendering the storage device unusable to the victim user. The name of the folder created will begin with the letters “Tmd” and the remaining part of the folder name will be randomly generated alphanumerical characters. The filename created will begin with the letters “Tmf” and the remaining part of the filename will be randomly generated alphanumerical characters.
Displayed below is the format of the file installed:
–Begin file–
Filename: “C:’Tmd[4 randomly generated characters]Tmf[4 randomly generated alphanumerical characters].tmp”
Sample: “C:Tmd21D9.tmpTmf1E9E.tmp”
–End file–
Analysis indicates that the application fails to execute if the above tmp file already exists on the victim’s machine.
Screenshots

Figure 7 – This screenshot illustrates the malware overwriting the first 65536 bytes of the C: drive, or attached storage disk, using random encrypted data generated via the Mersenne Twister algorithm.

Figure 8 – This screenshot illustrates a sample file created by the malware. This malware will write random encrypted data to this file until the C: drive and attached storage devices runs out of space. This is just one method the malware utilizes in an attempt to corrupt the victim user’s machine.

Figure 9 – This screenshot show the executable’s sleep function.
13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033
Tags
backdoortrojanviruswiper
Details
| Name |
Cleaner.dll |
| Size |
224768 bytes |
| Type |
PE32 executable (DLL) (console) Intel 80386, for MS Windows |
| MD5 |
ecce8845921a91854ab34bff2623151e |
| SHA1 |
736a4cfad1ed83a6a0b75b0474d5e01a3a36f950 |
| SHA256 |
13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033 |
| SHA512 |
36fda34df70629d054a55823a3cc83f9599446b36576fbc86a6aac6564460789e8b141eeb168d3e4578f28182da874dd840e57b642af1a1a315dfe08a17b53e0 |
| ssdeep |
6144:pjU6yx1p7lvER8SPD/xzL0ruSSbAOfyV:Ju1pZvPuDF0ruSSbkV |
| Entropy |
6.612476 |
Antivirus
| AhnLab |
Trojan/Win.IsaacWiper |
| Avira |
TR/KillMBR.hlwrn |
| Bitdefender |
Trojan.GenericKD.39120112 |
| ClamAV |
Win.Malware.IsaacWiper-9940626-0 |
| Cyren |
W32/Killmbr.GBHG-3949 |
| ESET |
Win32/KillMBR.NHQ trojan |
| Emsisoft |
Trojan.GenericKD.39120112 (B) |
| IKARUS |
Virus.Wiper.Isaac |
| K7 |
Trojan ( 0058efff1 ) |
| Lavasoft |
Trojan.GenericKD.39120112 |
| McAfee |
RDN/Generic.dx |
| Quick Heal |
APEXCFC.Backdoor.Gen |
| Sophos |
Troj/Wiper-F |
| Symantec |
Trojan.Gen.MBT |
| Trend Micro |
Trojan.6050981D |
| Trend Micro HouseCall |
Trojan.6050981D |
| VirusBlokAda |
Trojan.Agentb |
| Zillya! |
Trojan.KillMBR.Win32.666 |
YARA Rules
- rule CISA_10376640_01 : trojan wiper ISAACWIPER
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10376640”
Date = “2022-03-14”
Last_Modified = “20220418_1900”
Actor = “n/a”
Category = “Trojan Wiper”
Family = “ISAACWIPER”
Description = “Detects ISACC Wiper samples”
MD5_1 = “aa98b92e3320af7a1639de1bac6c17cc”
SHA256_1 = “abf9adf2c2c21c1e8bd69975dfccb5ca53060d8e1e7271a5e9ef3b56a7e54d9f”
MD5_2 = “8061889aaebd955ba6fb493abe7a4de1”
SHA256_2 = “afe1f2768e57573757039a40ac40f3c7471bb084599613b3402b1e9958e0d27a”
MD5_3 = “ecce8845921a91854ab34bff2623151e”
SHA256_3 = “13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033”
strings:
$s0 = { 73 00 74 00 61 00 72 00 74 00 20 00 65 00 72 00 61 00 73 00 69 00 6E 00 67 }
$s1 = { 6C 00 6F 00 67 00 69 00 63 00 61 00 6C }
$s2 = { 46 00 41 00 49 00 4C 00 45 00 44 }
$s3 = { 5C 00 6C 00 6F 00 67 00 2E 00 74 00 78 00 74 }
$s4 = { 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F }
$s5 = {53 74 61 72 74 40 34}
$s6 = {3B 57 34 74 2D 6A}
$s7 = {43 6C 65 61 6E 65 72 2E}
condition:
all of ($s0,$s1,$s2,$s3,$s4) or all of ($s5,$s6,$s7)
}
ssdeep Matches
No matches found.
PE Metadata
| Compile Date |
2022-02-25 10:48:07-05:00 |
| Import Hash |
a4b162717c197e11b76a4d9bc58ea25d |
PE Sections
| MD5 |
Name |
Raw Size |
Entropy |
| 28378e0c1da3cce94aa72585f5559fc6 |
header |
1024 |
2.656680 |
| 06d63fddf89fae3948764028712c36d6 |
.text |
150528 |
6.676976 |
| 48f101db632bb445c21a10fd5501e343 |
.rdata |
60416 |
5.634639 |
| 5efc98798d0979e69e2a667fc20e3f24 |
.data |
4096 |
3.256171 |
| 9676f7c827fb9388358aaba3e4bd0cc6 |
.reloc |
8704 |
6.433076 |
Packers/Compilers/Cryptors
Description
This application is a 32-bit DLL which has been identified as another variant of the IsaacWiper. It attempts to overwrite the first 65536 bytes of data on the C: drive and on attached storage disks in order to render them useless to the victim user. The malware also overwrites the victim user’s files so they cannot be recovered. The data used to overwrite the disk drives and user files is random encrypted data that is generated via the Mersenne Twister algorithm.
The malware also attempts to create a directory in the root directory of attached storage disks. The malware will then create a file within this newly created directory and attempt to fill it with random encrypted data, generated via the Mersenne Twister algorithm, in an effort to fill the drive up as another destructive method of rendering the storage device unusable to the victim user. The name of the folder created will begin with the letters “Tmd” and the remaining part of the folder name will be random. The filename created will begin with the letters “Tmf” and the remaining part of the folder name will be random.
This malware creates a log file in the location C:ProgramDatalog.txt. This file logs the malware’s process of systematically corrupting the victim user storage disks. Illustrated below is sample data the malware recorded to its log file during runtime:
–Begin log.txt Data–
getting drives…
physical drives:
— system physical drive 0: PhysicalDrive0
logical drives:
— system logical drive: C:
— logical drive: D:
start erasing system physical drive…
system physical drive — FAILED
start erasing system logical drive C:
–End log.txt Data–
Screenshots

Figure 10 – This screenshot illustrates the malware logging the beginning of its attempt to corrupt the victim user’s storage device. This log data will be recorded within the log file named log.txt.

Figure 11 – This screenshot illustrates the malware overwriting the first 65536 bytes of an attached storage disk using random encrypted data generated via the Mersenne Twister algorithm.

Figure 12 – This screenshot illustrates a sample file created by the malware. This malware will write random encrypted data to this file until the C: drive and attached storage devices runs out of space. This is just one method the malware utilizes in an attempt to corrupt the victim user’s machine.
Relationship Summary
| 5a300f72e2… |
Contained_Within |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| 5a300f72e2… |
Dropped_By |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| 2d29f9ca1d… |
Contained_Within |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| 2d29f9ca1d… |
Dropped_By |
a259e9b0acf375a8bef8dbc27a8a1996ee02a56889cba07ef58c49185ab033ec |
| a259e9b0ac… |
Contains |
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 |
| a259e9b0ac… |
Contains |
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b |
| a259e9b0ac… |
Dropped |
5a300f72e221a228e3a36a043bef878b570529a7abc15559513ea07ae280bb48 |
| a259e9b0ac… |
Dropped |
2d29f9ca1d9089ba0399661bb34ba2fd8aba117f04678cd71856d5894aa7150b |
Recommendations
CISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization’s systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
- Maintain up-to-date antivirus signatures and engines.
- Keep operating system patches up-to-date.
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
- Enforce a strong password policy and implement regular password changes.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Disable unnecessary services on agency workstations and servers.
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
- Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
- Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
- Scan all software downloaded from the Internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, “Guide to Malware Incident Prevention & Handling for Desktops and Laptops”.
Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/
Document FAQ
What is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis.
What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis.
Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk.
Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA’s homepage at www.cisa.gov.




Recent Comments