by Contributed | Dec 21, 2022 | Technology
This article is contributed. See the original author and article here.
I have already written a few articles on AKS, so feel free to have a look at them as I will not repeat what I’ve already written there. For the record, here are the links:
As a side note, this post is about how to harden ingress using Network Security Groups on top of internal network policies. Probably, 99% of the clusters worldwide are hardened using network policies only. If your organization is part of the last percent, and want to harden clusters further, this post is for you.
In AKS, ingress is used to let external components/callers interact with resources that are inside the cluster. Ingress is handled by an ingress controller. There are many of them: Nginx, Istio, Traefik, AGIC, etc. but whatever technology you choose, you will rely on a load balancer (LB) service to serve the traffic. When you instruct K8s to provision a service of type LB, it tells the Cloud provider (Microsoft in this case) to provision a LB service. This LB might be public facing or internal. The recommended approach is to provision an internal LB that is proxied by a Web Application Firewall (WAF) (Front Door+PLS or Application Gateway, or even any third party WAF). API traffic is also often proxied by a more specific API gateway.
The default behavior of a LB service in K8s, is to load balance the traffic twice:
- Firstly, at the level of the Azure LB, which will forward traffic to any healthy AKS node
- Secondly, at the level of K8s itself.
Because the Azure Load Balancer has no clue about the actual workload of the AKS cluster, it will blindly forward traffic to any “healthy” node, no matter what the pod density is. To prevent an imbalanced load balancing, K8s adds its own bits, to achieve a truly evenly distributed load balancing that considers the overall cluster capacity. While this sounds like the perfect thing on earth, it comes with two major caveats:
- K8s might add an extra hop between the Azure Load Balancer and the actual target, thus impacting latency.
- No matter whether there is an extra hop or not, K8s will source network address translation (SNAT) the source traffic, thus hiding the actual client IP. The ingress controller will therefore not be able to apply traffic restriction rules.
When you provision a LB service, for example, following the steps documented here, you will end up with a service, whose externalTrafficPolicy is set to Cluster. The Cluster mode takes care of the imbalanced load balancing. It performs the extra K8s bits to optimize load balancing and comes with the caveats described earlier.
This problem is known and documented so, why am I blogging about this? Well, this is because the load balancing algorithm that you choose at the level of the LB service, also has an impact on how you can restrict (or not) traffic that comes in, at the level of the Network Security Groups, and that is not something I could find guidance on.
If you do not want to restrict ingress traffic in any way, you can stop reading here, else, keep on reading.
Lab environment
Let us deep dive into the internals of AKS ingress with a concrete example.
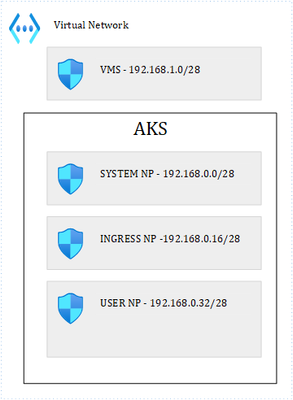
For this, let us use the following lab:

Where we have 1 VNET and 4 subnets. 3 subnets are used by the AKS cluster: 1 for the system node pool, 1 for ingress and the last one for user pods. I have labelled the Ingress and User node pools so that I can schedule pods accordingly. It is important to precise that our cluster is based on Kubenet, which adds a layer of complexity in terms of how networking works with K8s. The VM subnet holds our client VM, used to perform client calls to an API that is exposed through the ingress controller. Ultimately, we end up with this:
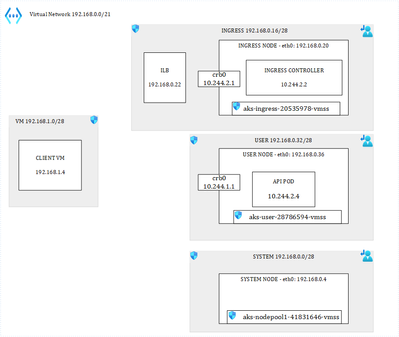
Load balancer with default behavior
I have provisioned the following LB service in AKS:
apiVersion: v1
kind: Service
metadata:
annotations:
meta.helm.sh/release-name: ingress-nginx
meta.helm.sh/release-namespace: ingress
service.beta.kubernetes.io/azure-load-balancer-health-probe-request-path: /healthz
service.beta.kubernetes.io/azure-load-balancer-internal: “true”
service.beta.kubernetes.io/azure-load-balancer-internal-subnet: ingress
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.5.1
helm.sh/chart: ingress-nginx-4.4.0
name: ingress-nginx-controller
namespace: ingress
spec:
allocateLoadBalancerNodePorts: true
externalTrafficPolicy: Cluster
internalTrafficPolicy: Cluster
ipFamilies:
– IPv4
ipFamilyPolicy: SingleStack
loadBalancerIP: 192.168.0.22
ports:
– appProtocol: http
name: http
nodePort: 31880
port: 80
protocol: TCP
targetPort: http
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
sessionAffinity: None
type: LoadBalancer
Notice the Azure-specific annotations at the top, telling Azure to provision an internal load balancer in a specific subnet, and with the /healthz endpoint for the health probe.
I’m only using HTTP but same logic applies to HTTPS. I have three nodes in the cluster:

I also have deployed one API and a few privileged containers, for later use:

Each privileged container runs on its corresponding node (one on the system node, one on the ingress node, and another one on the user node). The API runs on the user node. My ingress controller runs a single pod (for now) on the Ingress node:
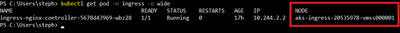
Lastly, I deployed the following ingress rule:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: weather
spec:
ingressClassName: nginx
rules:
– host: demoapi.eyskens.corp
http:
paths:
– path: /weatherforecast
pathType: Prefix
backend:
service:
name: simpleapi
port:
number: 8080
Upon the deployment of the K8s LB service, Azure creates its own LB service, which after a few minutes, shows the status of the health probe checks:
Each AKS node is being probed by the load balancer. So far so good, we can run our first API call from the client VM:
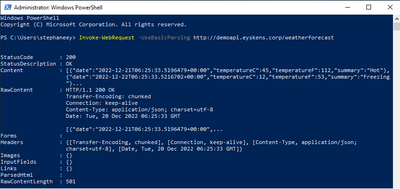
Our ingress controller sees the call and logs it:
192.168.0.4 – – [20/Dec/2022:06:25:33 +0000] “GET /weatherforecast HTTP/1.1” 200 513 “-“
“Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.17763.3770” 180
0.146 [default-simpleapi-8080] [] 10.244.1.5:8080 513 0.146 200
76e041740b70be9b36dd4fda52f97410
Everything works well until the security architect asks you how you control who can call this service…So, let us pretend that our client VM is the only one that can call the service. We could simply specify a rule at the level of the ingress controller itself. We know the IP of our VM so let’s give it a try:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: weather
annotations:
nginx.ingress.kubernetes.io/whitelist-source-range: 192.168.1.4
spec:
ingressClassName: nginx
rules:
– host: demoapi.eyskens.corp
http:
paths:
– path: /weatherforecast
pathType: Prefix
backend:
service:
name: simpleapi
port:
number: 8080
By adding a whitelist-source-range annotation. Surprise, we now we get a Forbidden response from our Client VM:

Looking at the NGINX logs reveals the problem:
…*24932 access forbidden by rule, client: 10.244.2.1, …
The client is 10.244.2.1 (crb0 of the ingress node) instead of our VM (192.168.1.4). Why is that? That is because of caveat number 2 described earlier. The Client IP is always hidden by the SNAT operation because the service is in Cluster mode. Well, is the client always 10.244.2.1? No, just run a few hundred queries from the same client VM, and you will notice things like this:
2022/12/20 07:03:45 [error] 98#98: *39317 access forbidden by rule, client: 10.244.2.1,
server: demoapi.eyskens.corp, request: “GET /weatherforecast HTTP/1.1”, host:
“demoapi.eyskens.corp”
2022/12/20 07:03:45 [error] 98#98: *39317 access forbidden by rule, client: 10.244.2.1,
server: demoapi.eyskens.corp, request: “GET /weatherforecast HTTP/1.1”, host:
“demoapi.eyskens.corp”
2022/12/20 07:03:48 [error] 98#98: *39361 access forbidden by rule, client: 192.168.0.36,
server: demoapi.eyskens.corp, request: “GET /weatherforecast HTTP/1.1”, host:
“demoapi.eyskens.corp”
We can see our CBR0 back, but also 192.168.0.36, which is the IP of our user node. Because you want to understand how things work internally, you decide to analyze traffic from the ingress node itself. You basically exec into the privileged container that is running on that node:
kubectl exec ingresspriv-5cfc6468c8-f8bjf -it — /bin/sh
Then, you go onto the node itself, and run a tcpdump:
chroot /host
tcpdump -i cbr0|grep weatherforecast
Where you can indeed see that traffic is coming from everywhere:
07:15:29.484576 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 14689:14845, ack 26227, win 16411, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.499647 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 14845:15001, ack 26506, win 16416, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.538515 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 15001:15157, ack 26785, win 16414, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.552183 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 15157:15313, ack 27064, win 16413, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.552630 IP aks-nodepool1-41831646-vmss000001.internal.cloudapp.net.24631 >
10.244.2.2.http: Flags [P.], seq 1:181, ack 1, win 16416, length 180: HTTP: GET
/weatherforecast HTTP/1.1
07:15:29.604062 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 15313:15469, ack 27343, win 16412, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.620439 IP aks-user-28786594-vmss000001.internal.cloudapp.net.35448 >
10.244.2.2.http: Flags [P.], seq 15469:15625, ack 27622, win 16411, length 156: HTTP:
GET /weatherforecast HTTP/1.1
07:15:29.637675 IP aks-nodepool1-41831646-vmss000001.internal.cloudapp.net.24631 >
10.244.2.2.http: Flags [P.], seq 181:337, ack 280, win 16414, length 156: HTTP: GET
/weatherforecast HTTP/1.1
07:15:29.666067 IP aks-nodepool1-41831646-vmss000001.internal.cloudapp.net.24631
This is plain normal: every single node of the cluster could be a potential client. So, no way to filter out traffic from the perspective of the ingress controller, with the Cluster mode.
Never mind, let us use the NSG instead of the ingress controller to restrict traffic to our VM only. That’s even better, let’s stop the illegal traffic sooner and not even hit our ingress controller. Naturally, you tell the security architect that you have a plan and come with the following NSG rules for the ingress NSG:
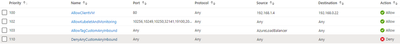
You basically allow the client VM to talk to the LB, and some system ports, but you deny everything else. You tell the security guy to relax about the “Any” destination since none of the internal cluster IPs is routable or visible to the outside world anyway (Kubenet), so only what is exposed through an ingress rule will be “visible”. For the two other subnets, you decide to be even more restrictive. You basically use the same rules as shown above, except for rule 100. You’re pretty sure it should be ok, and that no one else on earth but your client VM will ever be able to consume that API. Because you are a thoughtful person, you still decided to enable the NSG flow logs to make sure you capture traffic…in case you need to troubleshooting things later on.
So, you retry and you realize that a few queries go through while others are blocked, until every call from the client VM is going through again….What could be the culprit? First reaction is to look at the Azure Load Balancer itself and you’ll notice that it is not in a great shape anymore:
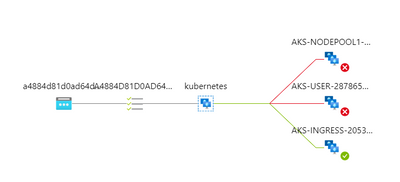
Why is that? It is because of the NSG that you defined at the level of the Ingress subnet, which broke it entirely, although you had authorized the AzureLoadBalancer tag. So, you decide to remove the NSG, wait a few minutes, and inspect again what comes into the CBR0 of the Ingress node, to figure it out from the inside:
tcpdump -i cbr0
This is what comes out of the dump:
08:36:46.835356 IP aks-user-28786594-vmss000001.internal.cloudapp.net.54259 >
10.244.2.2.http: Flags [P.], seq 199:395, ack 125, win 1024, length 196: HTTP: GET
/healthz HTTP/1.1
08:36:48.382720 IP aks-nodepool1-41831646-vmss000001.internal.cloudapp.net.8461 >
10.244.2.2.http: Flags [P.], seq 197:391, ack 125, win 16384, length 194: HTTP: GET
/healthz HTTP/1.1
You see that all nodes are directly probing the HEALTH endpoint on the ingress node…so the NSG rules described earlier are too restrictive. You start realizing that ruling AKS traffic with NSGs is a risky business…So, the non-ingress nodes are considered unhealthy by the Azure LB because they are unable to probe the ingress node. The ingress node is still considered healthy because it can probe itself and AzureLoadBalancer tag is allowed. That’s what explains the fact that ultimately, everything is going through because only the ingress node itself receives traffic, right from the LB and is already allowing the client VM. If you leave the cluster as is, you basically broke the built-in LB algorithm of K8s itself that protects against imbalanced traffic, plus you’ll keep getting calls from the other nodes trying to probe the ingress one. But because you want to optimize LB and avoid further issues, you add this rule to your ingress NSG:
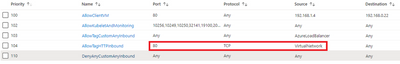
Where you basically allow every node to probe on port 80 (remember we only focus on HTTP). You can safely put Any as destination since the destination is the IP of the Ingress Pod, which you can’t guess in advance. After a few minutes, the Azure LB seems to be in a better shape:
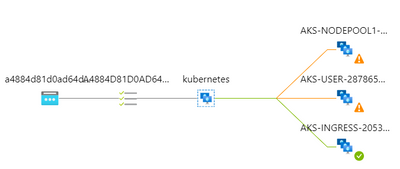
And yet a few minutes later, it’s all green again.
Now that you have restored the ingress, you’re back to square 1: some requests go through but not all. First, you checked the NSG flow logs of the User node pool and realized that you have such flow tuples that are blocked by the NSG:
[“1671521722,192.168.1.4,192.168.0.22,50326,80,T,I,D,B,,,,”]
Where you see that our client VM is trying to hit port 80 of our Azure Load Balancer…Wait, we said that the Cluster mode hides the original client IP, isn’t?? Yes that’s right but only from the inside, not from the outside. The NSGs still see the original IP….Ok, but why do I find these logs in the NSG of the user node?? Well, because each node of the cluster can potentially forward traffic to the destination…. So, it boils down to the following conclusion when using the Cluster mode:
- All nodes must be granted inbound access to the ingress node(s) for the health probes.
- Because each node is potentially forwarding the traffic itself, you must allow the callers (our VM in this case, an Application Gateway, an APIM in reality) in each subnet.
- You must accept de-facto cluster-wide node-level lateral movements to these endpoints/ports.
But what if the security architect cannot live with that? Let us explore the second option.
LB with externalTrafficPolicy set to Local.
The only thing needed to do is to switch the service’s externalTrafficPolicy to Local:
Type: LoadBalancer
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.0.58.7
IPs: 10.0.58.7
IP: 192.168.0.22
LoadBalancer Ingress: 192.168.0.22
Port: http 80/TCP
TargetPort: http/TCP
NodePort: http 31880/TCP
Endpoints: 10.244.2.2:80
Session Affinity: None
External Traffic Policy: Local
After a minute, you’ll notice this at the level of the Azure Load Balancer:
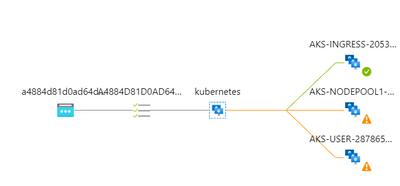
Don’t worry, this is the expected behavior. When you switch the K8s service to Local, K8s stops adding its own bits to the load balancing algorithm. The only way to prevent the Azure Load Balancer from sending traffic to a non-ingress-enabled node, is to mark these nodes as unhealthy. Any probe to the healthz endpoint will return a 503 answer from non-ingress-enabled nodes (example with the user node):
kubectl exec userpriv-5d879699c8-b2cww -it — /bin/sh
chroot /host
root@aks-user-28786594-vmss000001:/# curl -v http://localhost:31049/healthz
* Trying 127.0.0.1…
* TCP_NODELAY set
* Connected to localhost (127.0.0.1) port 31049 (#0)
> GET /healthz HTTP/1.1
> Host: localhost:31049
> User-Agent: curl/7.58.0
> Accept: */*
>
< HTTP/1.1 503 Service Unavailable
< Content-Type: application/json
< X-Content-Type-Options: nosniff
< Date: Tue, 20 Dec 2022 11:57:34 GMT
< Content-Length: 105
<
{
“service”: {
“namespace”: “ingress”,
“name”: “ingress-nginx-controller”
},
“localEndpoints”: 0
* Connection #0 to host localhost left intact
}root@aks-user-28786594-vmss000001:/#
While it will return a 200 on every ingress-enabled node. But what is it exactly an ingress-enabled node? It’s simply a node that is hosting an ingress controller pod. So, with this, you can control much better the ingress entry point, plus you can also directly use a whitelist-source-range annotation, and this time, the ingress controller will see the real client IP since there is no more SNAT happening.
You still must pay attention to where your ingress controller pods are running. Remember that I have dedicated one node pool in its own subnet for ingress and I have forced the pod scheduling on that node pool through a nodeSelector. Should I omit this, and scale my replicas to 3, I could end up with the following situation where AKS would schedule pods across nodes of different node pools:
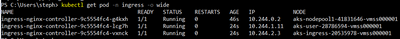
This would lead to a situation where nodes hosting an instance of the ingress controller would show up as healthy again at the level of the Azure Load Balancer. Therefore, you’d be hitting NSGs of subnets hosting those nodes…So, if you want to concentrate the ingress traffic to a single entry point, you need to:
- Dedicate a node pool with 1 or more nodes (more for HA) and enable Availability Zones for your ingress pods to run on.
- Make sure to force the pod scheduling of the ingress controller onto that node pool.
- Make sure you white list your clients (APIM, Application Gateway, etc.) at the level of the NSG of the ingress subnet. You do not need to white list other nodes because in Local mode, nodes do not probe the ingress node anymore. If you run a tcdump -i cbr0 on the ingress node, you’ll see only traffic from the node’s pod cidr itself.
Conclusion
Whether you are using Kubenet or CNI, ruling AKS ingress with Network Security Groups is not something you can improvise. Using the native load balancing algorithm (Cluster), you should end up with an optimized load balancing, but you must accept the fact that you have to live with lateral movements across the entire cluster. You can of course try to compensate with additional network policies but OS-level traffic would still be allowed (mind the container escape risk). Using the Local mode, you can control much better the incoming traffic, at the level of the NSGs as well as at the level of the ingress controller itself. You can run any number of ingress controller pods, as long as you scheduled them on identified nodes. The downside is that you might end up with an imbalanced traffic. This is a trade-off!
by Scott Muniz | Dec 19, 2022 | Security, Technology
This article is contributed. See the original author and article here.
| pacparser — pacparser |
A vulnerability classified as problematic was found in pacparser up to 1.3.x. Affected by this vulnerability is the function pacparser_find_proxy of the file src/pacparser.c. The manipulation of the argument url leads to buffer overflow. Attacking locally is a requirement. Upgrading to version 1.4.0 is able to address this issue. The name of the patch is 853e8f45607cb07b877ffd270c63dbcdd5201ad9. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-215443. |
2022-12-13 |
not yet calculated |
CVE-2019-25078
MISC
MISC
MISC
MISC |
| zhimengzhe — ibarn |
File upload vulnerability in function upload in action/Core.class.php in zhimengzhe iBarn 1.5 allows remote attackers to run arbitrary code via avatar upload to index.php. |
2022-12-15 |
not yet calculated |
CVE-2020-20588
MISC |
| netgate — multiple_products |
Cross Site Scripting (XSS) vulnerability in Netgate pf Sense 2.4.4-Release-p3 and Netgate ACME package 0.6.3 allows remote attackers to to run arbitrary code via the RootFolder field to acme_certificate_edit.php page of the ACME package. |
2022-12-15 |
not yet calculated |
CVE-2020-21219
MISC
MISC |
| easywebpack-cli — easywebpack-cli |
Directory Traversal vulnerability in easywebpack-cli before 4.5.2 allows attackers to obtain sensitive information via crafted GET request. |
2022-12-15 |
not yet calculated |
CVE-2020-24855
MISC |
| ibm — spectrum_protect_plus |
IBM Spectrum Protect Plus 10.1.0 through 10.1.12 discloses sensitive information due to unencrypted data being used in the communication flow between Spectrum Protect Plus vSnap and its agents. An attacker could obtain information using main in the middle techniques. IBM X-Force ID: 182106. |
2022-12-14 |
not yet calculated |
CVE-2020-4497
MISC
MISC |
| apache — zeppelin |
The improper Input Validation vulnerability in “”Move folder to Trash” feature of Apache Zeppelin allows an attacker to delete the arbitrary files. This issue affects Apache Zeppelin Apache Zeppelin version 0.9.0 and prior versions. |
2022-12-16 |
not yet calculated |
CVE-2021-28655
MISC |
| sourcecodester — online_grading_system |
A SQL injection vulnerability in Sourcecodester Online Grading System 1.0 allows remote attackers to execute arbitrary SQL commands via the uname parameter. |
2022-12-16 |
not yet calculated |
CVE-2021-31650
MISC |
| inikulin — replicator |
A deserialization issue discovered in inikulin replicator before 1.0.4 allows remote attackers to run arbitrary code via the fromSerializable function in TypedArray object. |
2022-12-15 |
not yet calculated |
CVE-2021-33420
MISC
MISC
MISC
MISC |
| hp — omen_gaming_hub_sdk |
Potential security vulnerabilities have been identified in an OMEN Gaming Hub SDK package which may allow escalation of privilege and/or denial of service. HP is releasing software updates to mitigate the potential vulnerabilities. |
2022-12-12 |
not yet calculated |
CVE-2021-3437
MISC |
| solarwinds — serv-u_ftp_server |
Common encryption key appears to be used across all deployed instances of Serv-U FTP Server. Because of this an encrypted value that is exposed to an attacker can be simply recovered to plaintext. |
2022-12-16 |
not yet calculated |
CVE-2021-35252
MISC
MISC
MISC |
| feehi_cms — feehi_cms |
Cross Site Scripting (XSS) vulnerability in Feehi CMS thru 2.1.1 allows attackers to run arbitrary code via the user name field of the login page. |
2022-12-15 |
not yet calculated |
CVE-2021-36572
MISC |
| hp — workstation_bios |
A potential security vulnerability has been identified in certain HP Workstation BIOS (UEFI firmware) which may allow arbitrary code execution. HP is releasing firmware mitigations for the potential vulnerability. |
2022-12-12 |
not yet calculated |
CVE-2021-3661
MISC |
| ruoyi — ruoyi |
Deserialization issue discovered in Ruoyi before 4.6.1 allows remote attackers to run arbitrary code via weak cipher in Shiro framework. |
2022-12-16 |
not yet calculated |
CVE-2021-38241
MISC |
| hp — multiple_products |
A potential security vulnerability has been identified in OMEN Gaming Hub and in HP Command Center which may allow escalation of privilege and/or denial of service. HP has released software updates to mitigate the potential vulnerability. |
2022-12-12 |
not yet calculated |
CVE-2021-3919
MISC |
| hp — multiple_products |
Certain HP Print products and Digital Sending products may be vulnerable to potential remote code execution and buffer overflow with use of Link-Local Multicast Name Resolution or LLMNR. |
2022-12-12 |
not yet calculated |
CVE-2021-3942
MISC |
| seacms — seacms |
An issue was discovered in /Upload/admin/admin_notify.php in Seacms 11.4 allows attackers to execute arbitrary php code via the notify1 parameter when the action parameter equals set. |
2022-12-15 |
not yet calculated |
CVE-2021-39426
MISC |
| 188jianzhan — 188jianzhan |
Cross site scripting vulnerability in 188Jianzhan 2.10 allows attackers to execute arbitrary code via the username parameter to /admin/reg.php. |
2022-12-15 |
not yet calculated |
CVE-2021-39427
MISC |
| eyoucms — eyoucms |
Cross Site Scripting (XSS) vulnerability in Users.php in eyoucms 1.5.4 allows remote attackers to run arbitrary code and gain escalated privilege via the filename for edit_users_head_pic. |
2022-12-15 |
not yet calculated |
CVE-2021-39428
MISC |
| rsfirewall — rsfirewall |
RSFirewall tries to identify the original IP address by looking at different HTTP headers. A bypass is possible due to the way it is implemented. |
2022-12-15 |
not yet calculated |
CVE-2021-4226
MISC |
| chbrown — rfc6902 |
A vulnerability classified as problematic has been found in chbrown rfc6902. This affects an unknown part of the file pointer.ts. The manipulation leads to improperly controlled modification of object prototype attributes (‘prototype pollution’). The exploit has been disclosed to the public and may be used. The name of the patch is c006ce9faa43d31edb34924f1df7b79c137096cf. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-215883. |
2022-12-15 |
not yet calculated |
CVE-2021-4245
N/A
N/A
N/A |
| roxlukas — lmeve |
A vulnerability was found in roxlukas LMeve and classified as critical. Affected by this issue is some unknown functionality of the component Login Page. The manipulation of the argument X-Forwarded-For leads to sql injection. The attack may be launched remotely. The name of the patch is 29e1ead3bb1c1fad53b77dfc14534496421c5b5d. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-216176. |
2022-12-17 |
not yet calculated |
CVE-2021-4246
N/A
N/A |
| hp — jumpstart |
A potential security vulnerability has been identified in the HP Jumpstart software, which might allow escalation of privilege. HP is recommending that customers uninstall HP Jumpstart and use myHP software. |
2022-12-12 |
not yet calculated |
CVE-2022-1038
MISC |
| google — android |
In multiple locations of NfcService.java, there is a possible disclosure of NFC tags due to a confused deputy. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-199291025 |
2022-12-16 |
not yet calculated |
CVE-2022-20199
MISC |
| google — android |
In onCreate of WifiDppConfiguratorActivity.java, there is a possible way for a guest user to add a WiFi configuration due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224772890 |
2022-12-16 |
not yet calculated |
CVE-2022-20503
MISC |
| google — android |
In multiple locations of DreamManagerService.java, there is a missing permission check. This could lead to local escalation of privilege and dismissal of system dialogs with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-225878553 |
2022-12-16 |
not yet calculated |
CVE-2022-20504
MISC |
| google — android |
In openFile of CallLogProvider.java, there is a possible permission bypass due to a path traversal error. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitationProduct: AndroidVersions: Android-13Android ID: A-225981754 |
2022-12-16 |
not yet calculated |
CVE-2022-20505
MISC |
| google — android |
In onCreate of WifiDialogActivity.java, there is a missing permission check. This could lead to local escalation of privilege from a guest user with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-226133034 |
2022-12-16 |
not yet calculated |
CVE-2022-20506
MISC |
| google — android |
In onMulticastListUpdateNotificationReceived of UwbEventManager.java, there is a possible arbitrary code execution due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-246649179 |
2022-12-16 |
not yet calculated |
CVE-2022-20507
MISC |
| google — android |
In onAttach of ConfigureWifiSettings.java, there is a possible way for a guest user to change WiFi settings due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-218679614 |
2022-12-16 |
not yet calculated |
CVE-2022-20508
MISC |
| google — android |
In mapGrantorDescr of MessageQueueBase.h, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-244713317 |
2022-12-16 |
not yet calculated |
CVE-2022-20509
MISC |
| google — android |
In getNearbyNotificationStreamingPolicy of DevicePolicyManagerService.java, there is a possible way to learn about the notification streaming policy of other users due to a permissions bypass. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-235822336 |
2022-12-16 |
not yet calculated |
CVE-2022-20510
MISC |
| google — android |
In getNearbyAppStreamingPolicy of DevicePolicyManagerService.java, there is a missing permission check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-235821829 |
2022-12-16 |
not yet calculated |
CVE-2022-20511
MISC |
| google — android |
In navigateUpTo of Task.java, there is a possible way to launch an intent handler with a mismatched intent due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-238602879 |
2022-12-16 |
not yet calculated |
CVE-2022-20512
MISC |
| google — android |
In decrypt_1_2 of CryptoPlugin.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-244569759 |
2022-12-16 |
not yet calculated |
CVE-2022-20513
MISC |
| google — android |
In acquireFabricatedOverlayIterator, nextFabricatedOverlayInfos, and releaseFabricatedOverlayIterator of Idmap2Service.cpp, there is a possible out of bounds write due to a use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-245727875 |
2022-12-16 |
not yet calculated |
CVE-2022-20514
MISC |
| google — android |
In onPreferenceClick of AccountTypePreferenceLoader.java, there is a possible way to retrieve protected files from the Settings app due to a confused deputy. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-220733496 |
2022-12-16 |
not yet calculated |
CVE-2022-20515
MISC |
| google — android |
In rw_t3t_act_handle_check_ndef_rsp of rw_t3t.cc, there is a possible out of bounds read due to an integer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224002331 |
2022-12-16 |
not yet calculated |
CVE-2022-20516
MISC |
| google — android |
In getMessagesByPhoneNumber of MmsSmsProvider.java, there is a possible access to restricted tables due to SQL injection. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224769956 |
2022-12-16 |
not yet calculated |
CVE-2022-20517
MISC |
| google — android |
In query of MmsSmsProvider.java, there is a possible access to restricted tables due to SQL injection. This could lead to local information disclosure with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224770203 |
2022-12-16 |
not yet calculated |
CVE-2022-20518
MISC |
google — android
|
In onCreate of AddAppNetworksActivity.java, there is a possible way for a guest user to configure WiFi networks due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224772678 |
2022-12-16 |
not yet calculated |
CVE-2022-20519
MISC |
| google — android |
In onCreate of various files, there is a possible tapjacking/overlay attack. This could lead to local escalation of privilege or denial of server with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-227203202 |
2022-12-16 |
not yet calculated |
CVE-2022-20520
MISC |
| google — android |
In sdpu_find_most_specific_service_uuid of sdp_utils.cc, there is a possible way to crash Bluetooth due to a missing null check. This could lead to local denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-227203684 |
2022-12-16 |
not yet calculated |
CVE-2022-20521
MISC |
| google — android |
In getSlice of ProviderModelSlice.java, there is a missing permission check. This could lead to local escalation of privilege from the guest user with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-227470877 |
2022-12-16 |
not yet calculated |
CVE-2022-20522
MISC |
| google — android |
In IncFs_GetFilledRangesStartingFrom of incfs.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-228222508 |
2022-12-16 |
not yet calculated |
CVE-2022-20523
MISC |
| google — android |
In compose of Vibrator.cpp, there is a possible arbitrary code execution due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-228523213 |
2022-12-16 |
not yet calculated |
CVE-2022-20524
MISC |
| google — android |
In enforceVisualVoicemailPackage of PhoneInterfaceManager.java, there is a possible leak of visual voicemail package name due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-229742768 |
2022-12-16 |
not yet calculated |
CVE-2022-20525
MISC |
| google — android |
In CanvasContext::draw of CanvasContext.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-229742774 |
2022-12-16 |
not yet calculated |
CVE-2022-20526
MISC |
| google — android |
In HalCoreCallback of halcore.cc, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure from the NFC firmware with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-229994861 |
2022-12-16 |
not yet calculated |
CVE-2022-20527
MISC |
| google — android |
In findParam of HevcUtils.cpp there is a possible out of bounds read due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-230172711 |
2022-12-16 |
not yet calculated |
CVE-2022-20528
MISC |
| google — android |
In multiple locations of WifiDialogActivity.java, there is a possible limited lockscreen bypass due to a logic error in the code. This could lead to local escalation of privilege in wifi settings with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-231583603 |
2022-12-16 |
not yet calculated |
CVE-2022-20529
MISC |
| google — android |
In strings.xml, there is a possible permission bypass due to a misleading string. This could lead to remote information disclosure of call logs with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-231585645 |
2022-12-16 |
not yet calculated |
CVE-2022-20530
MISC |
| google — android |
In placeCall of TelecomManager.java, there is a possible way to determine whether an app is installed, without query permissions, due to side channel information disclosure. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-231988638 |
2022-12-16 |
not yet calculated |
CVE-2022-20531
MISC |
| google — android |
In getSlice of WifiSlice.java, there is a possible way to connect a new WiFi network from the guest mode due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-232798363 |
2022-12-16 |
not yet calculated |
CVE-2022-20533
MISC |
| google — android |
In registerLocalOnlyHotspotSoftApCallback of WifiManager.java, there is a possible way to determine whether an app is installed, without query permissions, due to side channel information disclosure. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-233605242 |
2022-12-16 |
not yet calculated |
CVE-2022-20535
MISC |
| google — android |
In registerBroadcastReceiver of RcsService.java, there is a possible way to change preferred TTY mode due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-235100180 |
2022-12-16 |
not yet calculated |
CVE-2022-20536
MISC |
| google — android |
In createDialog of WifiScanModeActivity.java, there is a possible way for a Guest user to enable location-sensitive settings due to a missing permission check. This could lead to local escalation of privilege from the Guest user with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-235601169 |
2022-12-16 |
not yet calculated |
CVE-2022-20537
MISC |
| google — android |
In getSmsRoleHolder of RoleService.java, there is a possible way to determine whether an app is installed, without query permissions, due to side channel information disclosure. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-235601770 |
2022-12-16 |
not yet calculated |
CVE-2022-20538
MISC |
| google — android |
In parameterToHal of Effect.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege in the audio server with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-237291425 |
2022-12-16 |
not yet calculated |
CVE-2022-20539
MISC |
| google — android |
In SurfaceFlinger::doDump of SurfaceFlinger.cpp, there is possible arbitrary code execution due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-237291506 |
2022-12-16 |
not yet calculated |
CVE-2022-20540
MISC |
| google — android |
In phNxpNciHal_ioctl of phNxpNciHal.cc, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-238083126 |
2022-12-16 |
not yet calculated |
CVE-2022-20541
MISC |
| google — android |
In multiple locations, there is a possible display crash loop due to improper input validation. This could lead to local denial of service with system execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-238178261 |
2022-12-16 |
not yet calculated |
CVE-2022-20543
MISC |
| google — android |
In onOptionsItemSelected of ManageApplications.java, there is a possible bypass of profile owner restrictions due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-238745070 |
2022-12-16 |
not yet calculated |
CVE-2022-20544
MISC |
| google — android |
In bindArtworkAndColors of MediaControlPanel.java, there is a possible way to crash the phone due to improper input validation. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-239368697 |
2022-12-16 |
not yet calculated |
CVE-2022-20545
MISC |
| google — android |
In getCurrentConfigImpl of Effect.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-240266798 |
2022-12-16 |
not yet calculated |
CVE-2022-20546
MISC |
| google — android |
In multiple functions of AdapterService.java, there is a possible way to manipulate Bluetooth state due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-240301753 |
2022-12-16 |
not yet calculated |
CVE-2022-20547
MISC |
| google — android |
In setParameter of EqualizerEffect.cpp, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-240919398 |
2022-12-16 |
not yet calculated |
CVE-2022-20548
MISC |
| google — android |
In authToken2AidlVec of KeyMintUtils.cpp, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-242702451 |
2022-12-16 |
not yet calculated |
CVE-2022-20549
MISC |
| google — android |
In Multiple Locations, there is a possibility to launch arbitrary protected activities due to a confused deputy. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-242845514 |
2022-12-16 |
not yet calculated |
CVE-2022-20550
MISC |
| google — android |
In btif_a2dp_sink_command_ready of btif_a2dp_sink.cc, there is a possible out of bounds read due to a use after free. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-243922806 |
2022-12-16 |
not yet calculated |
CVE-2022-20552
MISC |
| google — android |
In onCreate of LogAccessDialogActivity.java, there is a possible way to bypass a permission check due to a tapjacking/overlay attack. This could lead to local escalation of privilege with System execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-244155265 |
2022-12-16 |
not yet calculated |
CVE-2022-20553
MISC |
| google — android |
In removeEventHubDevice of InputDevice.cpp, there is a possible OOB read due to a use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-245770596 |
2022-12-16 |
not yet calculated |
CVE-2022-20554
MISC |
| google — android |
In ufdt_get_node_by_path_len of ufdt_convert.c, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-246194233 |
2022-12-16 |
not yet calculated |
CVE-2022-20555
MISC |
| google — android |
In launchConfigNewNetworkFragment of NetworkProviderSettings.java, there is a possible way for the guest user to add a new WiFi network due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-246301667 |
2022-12-16 |
not yet calculated |
CVE-2022-20556
MISC |
| google — android |
In MessageQueueBase of MessageQueueBase.h, there is a possible out of bounds read due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-247092734 |
2022-12-16 |
not yet calculated |
CVE-2022-20557
MISC |
| google — android |
In registerReceivers of DeviceCapabilityListener.java, there is a possible way to change preferred TTY mode due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-236264289 |
2022-12-16 |
not yet calculated |
CVE-2022-20558
MISC |
| google — android |
In revokeOwnPermissionsOnKill of PermissionManager.java, there is a possible way to determine whether an app is installed, without query permissions, due to side channel information disclosure. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-219739967 |
2022-12-16 |
not yet calculated |
CVE-2022-20559
MISC |
| google — android |
Product: AndroidVersions: Android kernelAndroid ID: A-212623833References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20560
MISC |
| google — android |
In TBD of aud_hal_tunnel.c, there is a possible memory corruption due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-222162870References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20561
MISC |
| google — android |
In various functions of ap_input_processor.c, there is a possible way to record audio during a phone call due to a logic error in the code. This could lead to local information disclosure with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-231630423References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20562
MISC |
| google — android |
In TBD of ufdt_convert, there is a possible out of bounds read due to memory corruption. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242067561References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20563
MISC |
| google — android |
In _ufdt_output_strtab_to_fdt of ufdt_convert.c, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243798789References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20564
MISC |
| google — android |
In l2cap_chan_put of l2cap_core, there is a possible use after free due to improper locking. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-165329981References: Upstream kernel |
2022-12-16 |
not yet calculated |
CVE-2022-20566
MISC |
| google — android |
In pppol2tp_create of l2tp_ppp.c, there is a possible use after free due to a race condition. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-186777253References: Upstream kernel |
2022-12-16 |
not yet calculated |
CVE-2022-20567
MISC |
| google — android |
In (TBD) of (TBD), there is a possible way to corrupt kernel memory due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-220738351References: Upstream kernel |
2022-12-16 |
not yet calculated |
CVE-2022-20568
MISC |
| google — android |
In thermal_cooling_device_stats_update of thermal_sysfs.c, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege in the kernel with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-229258234References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20569
MISC |
| google — android |
Product: AndroidVersions: Android kernelAndroid ID: A-230660904References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20570
MISC |
| google — android |
In extract_metadata of dm-android-verity.c, there is a possible way to corrupt kernel memory due to a use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-234030265References: Upstream kernel |
2022-12-16 |
not yet calculated |
CVE-2022-20571
MISC |
| google — android |
In verity_target of dm-verity-target.c, there is a possible way to modify read-only files due to a missing permission check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-234475629References: Upstream kernel |
2022-12-16 |
not yet calculated |
CVE-2022-20572
MISC |
| google — android |
In sec_sysmmu_info of drm_fw.c, there is a possible out of bounds read due to improper input validation. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-237582191References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20574
MISC |
| google — android |
In read_ppmpu_info of drm_fw.c, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-237585040References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20575
MISC |
| google — android |
In externalOnRequest of rilapplication.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239701761References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20576
MISC |
| google — android |
In OemSimAuthRequest::encode of wlandata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241762281References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20577
MISC |
| google — android |
In RadioImpl::setGsmBroadcastConfig of ril_service_legacy.cpp, there is a possible stack clash leading to memory corruption. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243509749References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20578
MISC |
| google — android |
In RadioImpl::setCdmaBroadcastConfig of ril_service_legacy.cpp, there is a possible stack clash leading to memory corruption. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243510139References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20579
MISC |
| google — android |
In ufdt_do_one_fixup of ufdt_overlay.c, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243629453References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20580
MISC |
| google — android |
In the Pixel camera driver, there is a possible use after free due to a logic error in the code. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-245916120References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20581
MISC |
| google — android |
In ppmp_unprotect_mfcfw_buf of drm_fw.c, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-233645166References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20582
MISC |
| google — android |
In ppmp_unprotect_mfcfw_buf of drm_fw.c, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege in S-EL1 with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-234859169References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20583
MISC |
| google — android |
In page_number of shared_mem.c, there is a possible code execution in secure world due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238366009References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20584
MISC |
| google — android |
In valid_out_of_special_sec_dram_addr of drm_access_control.c, there is a possible EoP due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238716781References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20585
MISC |
| google — android |
In valid_out_of_special_sec_dram_addr of drm_access_control.c, there is a possible EoP due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238718854References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20586
MISC |
| google — android |
In ppmp_validate_wsm of drm_fw.c, there is a possible EoP due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238720411References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20587
MISC |
| google — android |
In sysmmu_map of sysmmu.c, there is a possible EoP due to a precondition check failure. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238785915References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20588
MISC |
| google — android |
In valid_va_secbuf_check of drm_access_control.c, there is a possible ID due to improper input validation. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238841928References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20589
MISC |
| google — android |
In valid_va_sec_mfc_check of drm_access_control.c, there is a possible information disclosure due to improper input validation. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238932493References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20590
MISC |
| google — android |
In ppmpu_set of ppmpu.c, there is a possible information disclosure due to a logic error in the code. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238939706References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20591
MISC |
| google — android |
In ppmp_validate_secbuf of drm_fw.c, there is a possible information disclosure due to improper input validation. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238976908References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20592
MISC |
| google — android |
In pop_descriptor_string of BufferDescriptor.h, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239415809References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20593
MISC |
| google — android |
In updateStart of WirelessCharger.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239567689References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20594
MISC |
| google — android |
In getWpcAuthChallengeResponse of WirelessCharger.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239700137References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20595
MISC |
| google — android |
In sendChunk of WirelessCharger.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239700400References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20596
MISC |
| google — android |
In ppmpu_set of ppmpu.c, there is a possible EoP due to an integer overflow. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243480506References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20597
MISC |
| google — android |
In sec_media_protect of media.c, there is a possible EoP due to an integer overflow. This could lead to local escalation of privilege of secure mode MFC Core with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242357514References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20598
MISC |
| google — android |
In Pixel firmware, there is a possible exposure of sensitive memory due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242332706References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20599
MISC |
| google — android |
In TBD of TBD, there is a possible out of bounds write due to memory corruption. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239847859References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20600
MISC |
| google — android |
Product: AndroidVersions: Android kernelAndroid ID: A-204541506References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20601
MISC |
| google — android |
Product: AndroidVersions: Android kernelAndroid ID: A-211081867References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20602
MISC |
| google — android |
In SetDecompContextDb of RohcDeCompContextOfRbId.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to remote code execution with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-219265339References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20603
MISC |
| google — android |
In SAECOMM_SetDcnIdForPlmn of SAECOMM_DbManagement.c, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure from a single device with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-230463606References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20604
MISC |
| google — android |
In SAECOMM_CopyBufferBytes of SAECOMM_Utility.c, there is a possible out of bounds read due to an incorrect bounds check. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-231722405References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20605
MISC |
| google — android |
In SAEMM_MiningCodecTableWithMsgIE of SAEMM_RadioMessageCodec.c, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-233230674References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20606
MISC |
| google — android |
In the Pixel cellular firmware, there is a possible out of bounds write due to a missing bounds check. This could lead to remote code execution with LTE authentication needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-238914868References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20607
MISC |
| google — android |
In Pixel cellular firmware, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239239246References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20608
MISC |
| google — android |
In Pixel cellular firmware, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-239240808References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20609
MISC |
| google — android |
In cellular modem firmware, there is a possible out of bounds read due to a missing bounds check. This could lead to remote code execution with LTE authentication needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-240462530References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-20610
MISC |
| qualcomm — snapdragon |
Memory corruption in Core due to improper configuration in boot remapper. |
2022-12-15 |
not yet calculated |
CVE-2022-22063
MISC |
| codex-team — editor.js |
Editor.js is a block-style editor with clean JSON output. Versions prior to 2.26.0 are vulnerable to Code Injection via pasted input. The processHTML method passes pasted input into wrapper’s innerHTML. This issue is patched in version 2.26.0. |
2022-12-15 |
not yet calculated |
CVE-2022-23474
MISC
MISC |
bigbluebutton — bigbluebutton
|
BigBlueButton is an open source web conferencing system. Versions prior to 2.4-rc-6 are vulnerable to Insertion of Sensitive Information Into Sent Data. The moderators-only webcams lock setting is not enforced on the backend, which allows an attacker to subscribe to viewers’ webcams, even when the lock setting is applied. (The required streamId was being sent to all users even with lock setting applied). This issue is fixed in version 2.4-rc-6. There are no workarounds. |
2022-12-17 |
not yet calculated |
CVE-2022-23488
MISC
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. Versions prior to 2.4.0 expose sensitive information to Unauthorized Actors. This issue affects meetings with polls, where the attacker is a meeting participant. Subscribing to the current-poll collection does not update the client UI, but does give the attacker access to the contents of the collection, which include the individual poll responses. This issue is patched in version 2.4.0. There are no workarounds. |
2022-12-16 |
not yet calculated |
CVE-2022-23490
MISC
MISC |
| informalsystems — tendermint-rs |
Tendermint is a high-performance blockchain consensus engine for Byzantine fault tolerant applications. Versions prior to 0.28.0 contain a potential attack via Improper Verification of Cryptographic Signature, affecting anyone using the tendermint-light-client and related packages to perform light client verification (e.g. IBC-rs, Hermes). The light client does not check that the chain IDs of the trusted and untrusted headers match, resulting in a possible attack vector where someone who finds a header from an untrusted chain that satisfies all other verification conditions (e.g. enough overlapping validator signatures) could fool a light client. The attack vector is currently theoretical, and no proof-of-concept exists yet to exploit it on live networks. This issue is patched in version 0.28.0. There are no workarounds. |
2022-12-15 |
not yet calculated |
CVE-2022-23507
MISC |
| flavorjones — loofah |
Loofah is a general library for manipulating and transforming HTML/XML documents and fragments, built on top of Nokogiri. Loofah < 2.19.1 contains an inefficient regular expression that is susceptible to excessive backtracking when attempting to sanitize certain SVG attributes. This may lead to a denial of service through CPU resource consumption. This issue is patched in version 2.19.1. |
2022-12-14 |
not yet calculated |
CVE-2022-23514
MISC
MISC |
flavorjones — loofah
|
Loofah is a general library for manipulating and transforming HTML/XML documents and fragments, built on top of Nokogiri. Loofah >= 2.1.0, < 2.19.1 is vulnerable to cross-site scripting via the image/svg+xml media type in data URIs. This issue is patched in version 2.19.1. |
2022-12-14 |
not yet calculated |
CVE-2022-23515
MISC
MISC
MISC |
| flavorjones — loofah |
Loofah is a general library for manipulating and transforming HTML/XML documents and fragments, built on top of Nokogiri. Loofah >= 2.2.0, < 2.19.1 uses recursion for sanitizing CDATA sections, making it susceptible to stack exhaustion and raising a SystemStackError exception. This may lead to a denial of service through CPU resource consumption. This issue is patched in version 2.19.1. Users who are unable to upgrade may be able to mitigate this vulnerability by limiting the length of the strings that are sanitized. |
2022-12-14 |
not yet calculated |
CVE-2022-23516
MISC |
helm — helm
|
Helm is a tool for managing Charts, pre-configured Kubernetes resources. Versions prior to 3.10.3 are subject to Uncontrolled Resource Consumption, resulting in Denial of Service. Input to functions in the _strvals_ package can cause a stack overflow. In Go, a stack overflow cannot be recovered from. Applications that use functions from the _strvals_ package in the Helm SDK can have a Denial of Service attack when they use this package and it panics. This issue has been patched in 3.10.3. SDK users can validate strings supplied by users won’t create large arrays causing significant memory usage before passing them to the _strvals_ functions. |
2022-12-15 |
not yet calculated |
CVE-2022-23524
MISC |
| helm — helm |
Helm is a tool for managing Charts, pre-configured Kubernetes resources. Versions prior to 3.10.3 are subject to NULL Pointer Dereference in the _repo_package. The _repo_ package contains a handler that processes the index file of a repository. For example, the Helm client adds references to chart repositories where charts are managed. The _repo_ package parses the index file of the repository and loads it into structures Go can work with. Some index files can cause array data structures to be created causing a memory violation. Applications that use the _repo_ package in the Helm SDK to parse an index file can suffer a Denial of Service when that input causes a panic that cannot be recovered from. The Helm Client will panic with an index file that causes a memory violation panic. Helm is not a long running service so the panic will not affect future uses of the Helm client. This issue has been patched in 3.10.3. SDK users can validate index files that are correctly formatted before passing them to the _repo_ functions. |
2022-12-15 |
not yet calculated |
CVE-2022-23525
MISC
MISC |
| helm — helm |
Helm is a tool for managing Charts, pre-configured Kubernetes resources. Versions prior to 3.10.3 are subject to NULL Pointer Dereference in the_chartutil_ package that can cause a segmentation violation. The _chartutil_ package contains a parser that loads a JSON Schema validation file. For example, the Helm client when rendering a chart will validate its values with the schema file. The _chartutil_ package parses the schema file and loads it into structures Go can work with. Some schema files can cause array data structures to be created causing a memory violation. Applications that use the _chartutil_ package in the Helm SDK to parse a schema file can suffer a Denial of Service when that input causes a panic that cannot be recovered from. Helm is not a long running service so the panic will not affect future uses of the Helm client. This issue has been patched in 3.10.3. SDK users can validate schema files that are correctly formatted before passing them to the _chartutil_ functions. |
2022-12-15 |
not yet calculated |
CVE-2022-23526
MISC
MISC |
| datadog — guarddog |
GuardDog is a CLI tool to identify malicious PyPI packages. Versions prior to v0.1.8 are vulnerable to arbitrary file write when scanning a specially-crafted remote PyPI package. Extracting files using shutil.unpack_archive() from a potentially malicious tarball without validating that the destination file path is within the intended destination directory can cause files outside the destination directory to be overwritten. This issue is patched in version 0.1.8. Potential workarounds include using a safer module, like zipfile, and validating the location of the extracted files and discarding those with malicious paths. |
2022-12-16 |
not yet calculated |
CVE-2022-23530
MISC
MISC
MISC |
| datadog — guarddog |
GuardDog is a CLI tool to identify malicious PyPI packages. Versions prior to 0.1.5 are vulnerable to Relative Path Traversal when scanning a specially-crafted local PyPI package. Running GuardDog against a specially-crafted package can allow an attacker to write an arbitrary file on the machine where GuardDog is executed due to a path traversal vulnerability when extracting the .tar.gz file of the package being scanned, which exists by design in the tarfile.TarFile.extractall function. This issue is patched in version 0.1.5. |
2022-12-17 |
not yet calculated |
CVE-2022-23531
MISC
MISC
MISC |
| wordpress — wordpress |
The Transposh WordPress Translation plugin for WordPress is vulnerable to unauthorized setting changes by unauthenticated users in versions up to, and including, 1.0.8.1. This is due to insufficient validation of settings on the ‘tp_translation’ AJAX action which makes it possible for unauthenticated attackers to bypass any restrictions and influence the data shown on the site. Please note this is a separate issue from CVE-2022-2461. Notes from the researcher: When installed Transposh comes with a set of pre-configured options, one of these is the “Who can translate” setting under the “Settings” tab. However, this option is largely ignored, if Transposh has enabled its “autotranslate” feature (it’s enabled by default) and the HTTP POST parameter “sr0” is larger than 0. This is caused by a faulty validation in “wp/transposh_db.php.” |
2022-12-15 |
not yet calculated |
CVE-2022-2536
MISC
MISC
MISC
MISC
MISC
MISC
MISC |
| broadcom — symantec_identity_governance_and_administration |
An unauthenticated user can access Identity Manager’s management console specific page URLs. However, the system doesn’t allow the user to carry out server side tasks without a valid web session. |
2022-12-16 |
not yet calculated |
CVE-2022-25626
MISC |
| broadcom — symantec_identity_governance_and_administration |
An authenticated administrator who has physical access to the environment can carry out Remote Command Execution on Management Console in Symantec Identity Manager 14.4 |
2022-12-16 |
not yet calculated |
CVE-2022-25627
MISC |
| broadcom — symantec_identity_governance_and_administration |
An authenticated user can perform XML eXternal Entity injection in Management Console in Symantec Identity Manager 14.4 |
2022-12-16 |
not yet calculated |
CVE-2022-25628
MISC |
| cyshield — multiple_products |
PAX Technology A930 PayDroid 7.1.1 Virgo V04.4.02 20211201 allows root privileged attackers to install an unsigned application by copying the APK to /data/app, setting the appropriate permissions and rebooting the device. |
2022-12-16 |
not yet calculated |
CVE-2022-26579
MISC |
| cyshield — multiple_products |
PAX Technology A930 PayDroid 7.1.1 Virgo V04.4.02 20211201 was discovered to be vulnerable to command injection. |
2022-12-16 |
not yet calculated |
CVE-2022-26580
MISC |
| cyshield — multiple_products |
The ADB daemon in PAX Technology A930 PayDroid 7.1.1 Virgo V04.4.02 20211201 allows the execution of the systool utility in production mode, allowing unauthenticated attackers to perform privileged actions. |
2022-12-16 |
not yet calculated |
CVE-2022-26581
MISC |
| cyshield — multiple_products |
The systool_server in PAX Technology A930 PayDroid 7.1.1 Virgo V04.4.02 20211201 fails to check for dollar signs or backticks in user supplied commands, leading to to arbitrary command execution as root. |
2022-12-16 |
not yet calculated |
CVE-2022-26582
MISC |
| lansweeper — lansweeper |
A directory traversal vulnerability exists in the TicketTemplateActions.aspx GetTemplateAttachment functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary file read. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-27498
MISC |
lansweeper — lansweeper
|
A stored cross-site scripting vulnerability exists in the HdConfigActions.aspx altertextlanguages functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary Javascript code injection. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-28703
MISC |
|
altair — hyperview_player
|
Altair HyperView Player versions 2021.1.0.27 and prior are vulnerable to the use of uninitialized memory vulnerability during parsing of H3D files. A DWORD is extracted from an uninitialized buffer and, after sign extension, is used as an index into a stack variable to increment a counter leading to memory corruption. |
2022-12-13 |
not yet calculated |
CVE-2022-2950
MISC |
|
altair — hyperview_player
|
Altair HyperView Player versions 2021.1.0.27 and prior are vulnerable to improper validation of array index vulnerability during processing of H3D files. A DWORD value from a PoC file is extracted and used as an index to write to a buffer, leading to memory corruption. |
2022-12-13 |
not yet calculated |
CVE-2022-2951
MISC |
| lansweeper — lansweeper |
A directory traversal vulnerability exists in the KnowledgebasePageActions.aspx ImportArticles functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary file read. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-29511
MISC |
| lansweeper — lansweeper |
A directory traversal vulnerability exists in the HelpdeskActions.aspx edittemplate functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary file upload. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-29517
MISC |
| delta_electronics — dopsoft |
Out-of-bounds Read vulnerability in Delta Electronics DOPSoft.This issue affects DOPSoft: All Versions. |
2022-12-16 |
not yet calculated |
CVE-2022-2966
MISC |
| ffmpeg — ffmpeg |
An issue was discovered in the FFmpeg through 3.0. vp3_decode_frame in libavcodec/vp3.c lacks check of the return value of av_malloc() and will cause the null pointer dereference, impacting confidentiality and availability. |
2022-12-16 |
not yet calculated |
CVE-2022-3109
MISC
MISC |
|
rockwell_automation — multiple_logix_controllers
|
A vulnerability exists in the Rockwell Automation controllers that allows a malformed CIP request to cause a major non-recoverable fault (MNRF) and a denial-of-service condition (DOS). |
2022-12-16 |
not yet calculated |
CVE-2022-3157
MISC |
| rockwell_automation — multiple_products |
Rockwell Automation was made aware that the webservers of the Micrologix 1100 and 1400 controllers contain a vulnerability that may lead to a denial-of-service condition. The security vulnerability could be exploited by an attacker with network access to the affected systems by sending TCP packets to webserver and closing it abruptly which would cause a denial-of-service condition for the web server application on the device |
2022-12-16 |
not yet calculated |
CVE-2022-3166
MISC |
|
vmware — multiple_products
|
VMware Workspace ONE Access and Identity Manager contain an authenticated remote code execution vulnerability. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 7.2. |
2022-12-14 |
not yet calculated |
CVE-2022-31700
MISC |
|
vmware — multiple_products
|
VMware Workspace ONE Access and Identity Manager contain a broken authentication vulnerability. VMware has evaluated the severity of this issue to be in the Moderate severity range with a maximum CVSSv3 base score of 5.3. |
2022-12-14 |
not yet calculated |
CVE-2022-31701
MISC |
|
vmware — multiple_products
|
VMware ESXi, Workstation, and Fusion contain a heap out-of-bounds write vulnerability in the USB 2.0 controller (EHCI). A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host. On ESXi, the exploitation is contained within the VMX sandbox whereas, on Workstation and Fusion, this may lead to code execution on the machine where Workstation or Fusion is installed. |
2022-12-14 |
not yet calculated |
CVE-2022-31705
MISC |
| vmware — vrealize_operations |
vRealize Operations (vROps) contains a privilege escalation vulnerability. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 7.2. |
2022-12-16 |
not yet calculated |
CVE-2022-31707
MISC |
| vmware — vrealize_operations |
vRealize Operations (vROps) contains a broken access control vulnerability. VMware has evaluated the severity of this issue to be in the Moderate severity range with a maximum CVSSv3 base score of 4.4. |
2022-12-16 |
not yet calculated |
CVE-2022-31708
MISC |
|
apache — bookkeeper_java_client
|
The Apache Bookkeeper Java Client (before 4.14.6 and also 4.15.0) does not close the connection to the bookkeeper server when TLS hostname verification fails. This leaves the bookkeeper client vulnerable to a man in the middle attack. The problem affects BookKeeper client prior to versions 4.14.6 and 4.15.1. |
2022-12-15 |
not yet calculated |
CVE-2022-32531
MISC |
| lansweeper — lansweeper |
A directory traversal vulnerability exists in the AssetActions.aspx addDoc functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary file upload. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-32573
MISC |
| lansweeper — lansweeper |
A cross-site scripting (xss) sanitization vulnerability bypass exists in the SanitizeHtml functionality of Lansweeper lansweeper 10.1.1.0. A specially-crafted HTTP request can lead to arbitrary Javascript code injection. An attacker can send an HTTP request to trigger this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-32763
MISC |
|
apple — ios
|
An issue existed with the file paths used to store website data. The issue was resolved by improving how website data is stored. This issue is fixed in iOS 16. An unauthorized user may be able to access browsing history. |
2022-12-15 |
not yet calculated |
CVE-2022-32833
MISC |
| apple — multiple_products |
An out-of-bounds write was addressed with improved input validation. This issue is fixed in iOS 15.6 and iPadOS 15.6, macOS Monterey 12.5, macOS Big Sur 11.6.8. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-32860
MISC
MISC
MISC |
| apple — ios |
An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. This issue is fixed in iOS 16. An app may be able to disclose kernel memory. |
2022-12-15 |
not yet calculated |
CVE-2022-32916
MISC |
|
apple — multiple_products
|
The issue was addressed with improved memory handling. This issue is fixed in macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-32942
MISC
MISC
MISC |
|
apple — multiple_products
|
The issue was addressed with improved bounds checks. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1. Shake-to-undo may allow a deleted photo to be re-surfaced without authentication. |
2022-12-15 |
not yet calculated |
CVE-2022-32943
MISC
MISC |
| apple — macos_ventura |
An access issue was addressed with additional sandbox restrictions on third-party apps. This issue is fixed in macOS Ventura 13. An app may be able to record audio with paired AirPods. |
2022-12-15 |
not yet calculated |
CVE-2022-32945
MISC |
| apple — multiple_products |
An out-of-bounds read was addressed with improved bounds checking. This issue is fixed in iOS 15.6 and iPadOS 15.6, macOS Monterey 12.5. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-32948
MISC
MISC |
| wordpress — wordpress |
The Corner Ad plugin for WordPress is vulnerable to Cross-Site Request Forgery in versions up to, and including, 1.0.56. This is due to missing or incorrect nonce validation on its corner_ad_settings_page function. This makes it possible for unauthenticated attackers to trigger the deletion of ads via forged request granted they can trick a site administrator into performing an action such as clicking on a link. |
2022-12-15 |
not yet calculated |
CVE-2022-3427
MISC
MISC
MISC |
|
emby_server — emby_server
|
In Emby Server 4.6.7.0, the playlist name field is vulnerable to XSS stored where it is possible to steal the administrator access token and flip or steal the media server administrator account. |
2022-12-16 |
not yet calculated |
CVE-2022-36223
MISC |
| hp — multiple_products |
A potential vulnerability has been identified in the system BIOS for certain HP PC products which may allow escalation of privileges and code execution. HP is releasing firmware updates to mitigate the potential vulnerability. |
2022-12-12 |
not yet calculated |
CVE-2022-37018
MISC |
| jumpsec — mutiny |
Mutiny 7.2.0-10788 suffers from Hardcoded root password. |
2022-12-16 |
not yet calculated |
CVE-2022-37832
MISC |
|
solarwinds — serv-u
|
This vulnerability happens in the web client versions 15.3.0 to Serv-U 15.3.1. This vulnerability affects the directory creation function. |
2022-12-16 |
not yet calculated |
CVE-2022-38106
MISC
MISC
MISC |
| logrocket — logrocket-oauth2-example |
logrocket-oauth2-example through 2020-05-27 allows SQL injection via the /auth/register username parameter. |
2022-12-14 |
not yet calculated |
CVE-2022-38488
MISC
MISC
MISC
MISC
MISC |
| micro_focus — groupwise_web |
A vulnerability has been identified in Micro Focus GroupWise Web in versions prior to 18.4.2. The GW Web component makes a request to the Post Office Agent that contains sensitive information in the query parameters that could be logged by any intervening HTTP proxies. |
2022-12-16 |
not yet calculated |
CVE-2022-38756
MISC |
| motorola — mobility_motorola |
Improper access control of bootloader function was discovered in Motorola Mobility Motorola e20 prior to version RONS31.267-38-8 allows attacker with local access to read partition or RAM data. |
2022-12-14 |
not yet calculated |
CVE-2022-3917
MISC |
| wordpress — wordpress |
The Motors WordPress plugin before 1.4.4 does not properly validate uploaded files for dangerous file types (such as .php) in an AJAX action, allowing an attacker to sign up on a victim’s WordPress instance, upload a malicious PHP file and attempt to launch a brute-force attack to discover the uploaded payload. |
2022-12-12 |
not yet calculated |
CVE-2022-3989
MISC |
| feehicms — feehicms |
Cross Site Scripting (XSS) vulnerability in FeehiCMS-2.1.1 allows remote attackers to run arbitrary code via the username field of the admin log in page. |
2022-12-15 |
not yet calculated |
CVE-2022-40000
MISC |
| feehicms — feehicms |
Cross Site Scripting (XSS) vulnerability in FeehiCMS-2.1.1 allows remote attackers to run arbitrary code via the title field of the create article page. |
2022-12-15 |
not yet calculated |
CVE-2022-40001
MISC |
| feehicms — feehicms |
Cross Site Scripting (XSS) vulnerability in FeehiCMS-2.1.1 allows remote attackers to run arbirtary code via the callback parameter to /cms/notify. |
2022-12-15 |
not yet calculated |
CVE-2022-40002
MISC |
| things_board — things_board |
Cross Site Scripting (XSS) vulnerability in Things Board 3.4.1 allows remote attackers to escalate privilege via crafted URL to the Audit Log. |
2022-12-15 |
not yet calculated |
CVE-2022-40004
MISC |
| feehicms — feehicms |
Cross Site Scripting (XSS) vulnerability in FeehiCMS 2.1.1 allows remote attackers to run arbitrary code via upload of crafted XML file. |
2022-12-15 |
not yet calculated |
CVE-2022-40373
MISC |
| satellite_server — satellite_server |
A blind site-to-site request forgery vulnerability was found in Satellite server. It is possible to trigger an external interaction to an attacker’s server by modifying the Referer header in an HTTP request of specific resources in the server. |
2022-12-16 |
not yet calculated |
CVE-2022-4130
MISC |
| netty — netty |
Netty project is an event-driven asynchronous network application framework. In versions prior to 4.1.86.Final, a StackOverflowError can be raised when parsing a malformed crafted message due to an infinite recursion. This issue is patched in version 4.1.86.Final. There is no workaround, except using a custom HaProxyMessageDecoder. |
2022-12-12 |
not yet calculated |
CVE-2022-41881
MISC |
| netty — netty |
Netty project is an event-driven asynchronous network application framework. In versions prior to 4.1.86.Final, when calling `DefaultHttpHeadesr.set` with an _iterator_ of values, header value validation was not performed, allowing malicious header values in the iterator to perform HTTP Response Splitting. This issue has been patched in version 4.1.86.Final. Integrators can work around the issue by changing the `DefaultHttpHeaders.set(CharSequence, Iterator)` call, into a `remove()` call, and call `add()` in a loop over the iterator of values. |
2022-12-13 |
not yet calculated |
CVE-2022-41915
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. Versions prior to 2.4.3, are subject to Insufficient Verification of Data Authenticity, resulting in Denial of Service. An attacker can make a Meteor call to `validateAuthToken` using a victim’s userId, meetingId, and an invalid authToken. This forces the victim to leave the conference, because the resulting verification failure is also observed and handled by the victim’s client. The attacker must be a participant in any meeting on the server. This issue is patched in version 2.4.3. There are no workarounds. |
2022-12-16 |
not yet calculated |
CVE-2022-41960
MISC
MISC
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. Versions prior to 2.4-rc-6 are subject to Ineffective user bans. The attacker could register multiple users, and join the meeting with one of them. When that user is banned, they could still join the meeting with the remaining registered users from the same extId. This issue has been fixed by improving permissions such that banning a user removes all users related to their extId, including registered users that have not joined the meeting. This issue is patched in versions 2.4-rc-6 and 2.5-alpha-1. There are no workarounds. |
2022-12-16 |
not yet calculated |
CVE-2022-41961
MISC
MISC
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. Versions prior to 2.4-rc-6, and 2.5-alpha-1 contain Incorrect Authorization for setting emoji status. A user with moderator rights can use the clear status feature to set any emoji status for other users. Moderators should only be able to set none as the status of other users. This issue is patched in 2.4-rc-6 and 2.5-alpha-1There are no workarounds. |
2022-12-16 |
not yet calculated |
CVE-2022-41962
MISC
MISC
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. Versions prior to 2.4.3 contain a whiteboard grace period that exists to handle delayed messages, but this grace period could be used by attackers to take actions in the few seconds after their access is revoked. The attacker must be a meeting participant. This issue is patched in version 2.4.3 an version 2.5-alpha-1 |
2022-12-16 |
not yet calculated |
CVE-2022-41963
MISC
MISC |
| bigbluebutton — bigbluebutton |
BigBlueButton is an open source web conferencing system. This vulnerability only affects release candidates of BigBlueButton 2.4. The attacker can start a subscription for poll results before starting an anonymous poll, and use this subscription to see individual responses in the anonymous poll. The attacker had to be a meeting presenter. This issue is patched in version 2.4.0. There are no workarounds. |
2022-12-16 |
not yet calculated |
CVE-2022-41964
MISC
MISC |
| contiki-ng — contiki-ng |
Contiki-NG is an open-source, cross-platform operating system for Next-Generation IoT devices. Versions prior to 4.9 contain a NULL Pointer Dereference in BLE L2CAP module. The Contiki-NG operating system for IoT devices contains a Bluetooth Low Energy stack. An attacker can inject a packet in this stack, which causes the implementation to dereference a NULL pointer and triggers undefined behavior. More specifically, while processing the L2CAP protocol, the implementation maps an incoming channel ID to its metadata structure. In this structure, state information regarding credits is managed through calls to the function input_l2cap_credit in the module os/net/mac/ble/ble-l2cap.c. Unfortunately, the input_l2cap_credit function does not check that the metadata corresponding to the user-supplied channel ID actually exists, which can lead to the channel variable being set to NULL before a pointer dereferencing operation is performed. The vulnerability has been patched in the “develop” branch of Contiki-NG, and will be included in release 4.9. Users can apply the patch in Contiki-NG pull request #2253 as a workaround until the new package is released. |
2022-12-16 |
not yet calculated |
CVE-2022-41972
MISC
MISC |
| poweriso — poweriso |
A memory corruption vulnerability exists in the VHD File Format parsing CXSPARSE record functionality of PowerISO PowerISO 8.3. A specially-crafted file can lead to an out-of-bounds write. A victim needs to open a malicious file to trigger this vulnerability. |
2022-12-16 |
not yet calculated |
CVE-2022-41992
MISC |
| pgadmin — pgadmin |
The pgAdmin server includes an HTTP API that is intended to be used to validate the path a user selects to external PostgreSQL utilities such as pg_dump and pg_restore. The utility is executed by the server to determine what PostgreSQL version it is from. Versions of pgAdmin prior to 6.17 failed to properly secure this API, which could allow an unauthenticated user to call it with a path of their choosing, such as a UNC path to a server they control on a Windows machine. This would cause an appropriately named executable in the target path to be executed by the pgAdmin server. |
2022-12-13 |
not yet calculated |
CVE-2022-4223
MISC
FEDORA |
| google — android |
In HexString2Value of util.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241231403References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42501
MISC |
| google — android |
In FacilityLock::Parse of simdata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241231970References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42502
MISC |
| google — android |
In ProtocolMiscBuilder::BuildSetLinkCapaReportCriteria of protocolmiscbuilder.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241231983References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42503
MISC |
| google — android |
In CallDialReqData::encodeCallNumber of callreqdata.cpp, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241232209References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42504
MISC |
| google — android |
In ProtocolMiscBuilder::BuildSetSignalReportCriteria of protocolmiscbuilder.cpp, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241232492References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42505
MISC |
| google — android |
In SimUpdatePbEntry::encode of simdata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241388399References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42506
MISC |
| google — android |
In ProtocolSimBuilder::BuildSimUpdatePb3gEntry of protocolsimbuilder.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241388774References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42507
MISC |
| google — android |
In ProtocolCallBuilder::BuildSendUssd of protocolcallbuilder.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241388966References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42508
MISC |
| google — android |
In CallDialReqData::encode of callreqdata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241544307References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42509
MISC |
| google — android |
In StringsRequestData::encode of requestdata.cpp, there is a possible out of bounds read due to improper input validation. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241762656References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42510
MISC |
| google — android |
In EmbmsSessionData::encode of embmsdata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241762712References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42511
MISC |
| google — android |
In VsimOperationDataExt::encode of vsimdata.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763050References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42512
MISC |
| google — android |
In ProtocolEmbmsBuilder::BuildSetSession of protocolembmsbuilder.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763204References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42513
MISC |
| google — android |
In ProtocolImsBuilder::BuildSetConfig of protocolimsbuilder.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763298References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42514
MISC |
| google — android |
In MiscService::DoOemSetRtpPktlossThreshold of miscservice.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763503References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42515
MISC |
| google — android |
In ProtocolSimBuilderLegacy::BuildSimGetGbaAuth of protocolsimbuilderlegacy.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763577References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42516
MISC |
| google — android |
In MiscService::DoOemSetTcsFci of miscservice.cpp, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-241763682References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42517
MISC |
| google — android |
In BroadcastSmsConfigsRequestData::encode of smsdata.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242536278References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42518
MISC |
| google — android |
In CdmaBroadcastSmsConfigsRequestData::encode of cdmasmsdata.cpp, there is a possible stack clash leading to memory corruption. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242540694References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42519
MISC |
| google — android |
In ServiceInterface::HandleRequest of serviceinterface.cpp, there is a possible use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242994270References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42520
MISC |
| google — android |
In encode of wlandata.cpp, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243130019References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42521
MISC |
| google — android |
In DoSetCarrierConfig of miscservice.cpp, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243130038References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42522
MISC |
| google — android |
In fillSetupDataCallInfo_V1_6 of ril_service_1_6.cpp, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243376893References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42523
MISC |
| google — android |
In sms_GetTpUdlIe of sms_PduCodec.c, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243401445References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42524
MISC |
| google — android |
In fillSetupDataCallInfo_V1_6 of ril_service_1_6.cpp, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243509750References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42525
MISC |
| google — android |
In ConvertUtf8ToUcs2 of radio_hal_utils.cpp, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-243509880References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42526
MISC |
| google — android |
In cd_SsParseMsg of cd_SsCodec.c, there is a possible crash due to a missing null check. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-244448906References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42527
MISC |
| google — android |
Product: AndroidVersions: Android kernelAndroid ID: A-235292841References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42529
MISC |
| google — android |
In Pixel firmware, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242331893References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42530
MISC |
| google — android |
In mmu_map_for_fw of gs_ldfw_load.c, there is a possible mitigation bypass due to Permissive Memory Allocation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-231500967References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42531
MISC |
| google — android |
In Pixel firmware, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-242332610References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42532
MISC |
| google — android |
In trusty_ffa_mem_reclaim of shared-mem-smcall.c, there is a possible privilege escalation due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-237838301References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42534
MISC |
| google — android |
In a query in MmsSmsProvider.java, there is a possible access to restricted tables due to SQL injection. This could lead to local information disclosure with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224770183 |
2022-12-16 |
not yet calculated |
CVE-2022-42535
MISC |
| google — android |
In phNxpNciHal_core_initialized of phNxpNciHal.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-231445184 |
2022-12-16 |
not yet calculated |
CVE-2022-42542
MISC |
| google — android |
In fdt_path_offset_namelen of fdt_ro.c, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-249998113References: N/A |
2022-12-16 |
not yet calculated |
CVE-2022-42543
MISC |
| google — android |
In getView of AddAppNetworksFragment.java, there is a possible way to mislead the user about network add requests due to improper input validation. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13Android ID: A-224545390 |
2022-12-16 |
not yet calculated |
CVE-2022-42544
MISC |
| apple — multiple_products |
An integer overflow was addressed with improved input validation. This issue is fixed in iOS 15.6 and iPadOS 15.6, macOS Monterey 12.5. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42805
MISC
MISC |
| apple — multiple_products |
A logic issue was addressed with improved checks. This issue is fixed in macOS Monterey 12.6.2, macOS Big Sur 11.7.2, macOS Ventura 13. An app may bypass Gatekeeper checks. |
2022-12-15 |
not yet calculated |
CVE-2022-42821
MISC
MISC
MISC |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs because the XkbCopyNames function left a dangling pointer to freed memory, resulting in out-of-bounds memory access on subsequent XkbGetKbdByName requests. This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions. |
2022-12-14 |
not yet calculated |
CVE-2022-4283
MISC
MISC
FEDORA
FEDORA |
| apple — multiple_products |
An issue existed in the parsing of URLs. This issue was addressed with improved input validation. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, watchOS 9.2. A remote user may be able to cause unexpected app termination or arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-42837
MISC
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42840
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A type confusion issue was addressed with improved checks. This issue is fixed in macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2. Processing a maliciously crafted package may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-42841
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. A remote user may be able to cause kernel code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-42842
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
This issue was addressed with improved data protection. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, watchOS 9.2. A user may be able to view sensitive user information. |
2022-12-15 |
not yet calculated |
CVE-2022-42843
MISC
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2. An app may be able to break out of its sandbox. |
2022-12-15 |
not yet calculated |
CVE-2022-42844
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. An app with root privileges may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42845
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2, iOS 15.7.2 and iPadOS 15.7.2. Parsing a maliciously crafted video file may lead to unexpected system termination. |
2022-12-15 |
not yet calculated |
CVE-2022-42846
MISC
MISC |
|
apple — macos_ventura
|
An out-of-bounds write issue was addressed with improved input validation. This issue is fixed in macOS Ventura 13.1. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42847
MISC |
| apple — multiple_products |
A logic issue was addressed with improved checks. This issue is fixed in iOS 16.2 and iPadOS 16.2, iOS 15.7.2 and iPadOS 15.7.2, tvOS 16.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42848
MISC
MISC
MISC |
| apple — multiple_products |
An access issue existed with privileged API calls. This issue was addressed with additional restrictions. This issue is fixed in iOS 16.2 and iPadOS 16.2, tvOS 16.2, watchOS 9.2. A user may be able to elevate privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42849
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42850
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2, tvOS 16.2. Parsing a maliciously crafted TIFF file may lead to disclosure of user information. |
2022-12-15 |
not yet calculated |
CVE-2022-42851
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may result in the disclosure of process memory. |
2022-12-15 |
not yet calculated |
CVE-2022-42852
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — macos_ventura |
An access issue was addressed with improved access restrictions. This issue is fixed in macOS Ventura 13.1. An app may be able to modify protected parts of the file system. |
2022-12-15 |
not yet calculated |
CVE-2022-42853
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in macOS Monterey 12.6.2, macOS Ventura 13.1. An app may be able to disclose kernel memory. |
2022-12-15 |
not yet calculated |
CVE-2022-42854
MISC
MISC |
| apple — multiple_products |
A logic issue was addressed with improved state management. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2. An app may be able to use arbitrary entitlements. |
2022-12-15 |
not yet calculated |
CVE-2022-42855
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A type confusion issue was addressed with improved state handling. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.1.2. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.1.. |
2022-12-15 |
not yet calculated |
CVE-2022-42856
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
Multiple issues were addressed by removing the vulnerable code. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, watchOS 9.2. An app may be able to bypass Privacy preferences. |
2022-12-15 |
not yet calculated |
CVE-2022-42859
MISC
MISC
MISC |
| apple — multiple_products |
This issue was addressed with improved checks. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2. An app may be able to break out of its sandbox. |
2022-12-15 |
not yet calculated |
CVE-2022-42861
MISC
MISC
MISC
MISC |
| apple — multiple_products |
This issue was addressed by removing the vulnerable code. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1. An app may be able to bypass Privacy preferences. |
2022-12-15 |
not yet calculated |
CVE-2022-42862
MISC
MISC |
| apple — multiple_products |
A memory corruption issue was addressed with improved state management. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-42863
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A race condition was addressed with improved state handling. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-42864
MISC
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
This issue was addressed by enabling hardened runtime. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, watchOS 9.2. An app may be able to bypass Privacy preferences. |
2022-12-15 |
not yet calculated |
CVE-2022-42865
MISC
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved handling of caches. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, watchOS 9.2. An app may be able to read sensitive location information. |
2022-12-15 |
not yet calculated |
CVE-2022-42866
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A use after free issue was addressed with improved memory management. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-42867
MISC
MISC
MISC
MISC
MISC |
|
trellix– endpoint_agent
|
Improper preservation of permissions vulnerability in Trellix Endpoint Agent (xAgent) prior to V35.31.22 on Windows allows a local user with administrator privileges to bypass the product protection to uninstall the agent via incorrectly applied permissions in the removal protection functionality. |
2022-12-16 |
not yet calculated |
CVE-2022-4326
MISC |
|
beijing_zed-3 — voip_simpliclty_asg
|
Beijing Zed-3 Technologies Co.,Ltd VoIP simpliclty ASG 8.5.0.17807 (20181130-16:12) is vulnerable to Cross Site Scripting (XSS). |
2022-12-15 |
not yet calculated |
CVE-2022-44235
MISC |
|
beijing_zed-3 — voip_simpliclty_asg
|
Beijing Zed-3 Technologies Co.,Ltd VoIP simpliclty ASG 8.5.0.17807 (20181130-16:12) has a Weak password vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-44236
MISC |
| m0ver — bible-online |
A vulnerability, which was classified as critical, has been found in m0ver bible-online. Affected by this issue is the function query of the file src/main/java/custom/application/search.java of the component Search Handler. The manipulation leads to sql injection. The name of the patch is 6ef0aabfb2d4ccd53fcaa9707781303af357410e. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-215444. |
2022-12-13 |
not yet calculated |
CVE-2022-4454
MISC
MISC |
| sproctor — php-calendar |
A vulnerability, which was classified as problematic, was found in sproctor php-calendar. This affects an unknown part of the file index.php. The manipulation of the argument $_SERVER[‘PHP_SELF’] leads to cross site scripting. It is possible to initiate the attack remotely. The name of the patch is a2941109b42201c19733127ced763e270a357809. It is recommended to apply a patch to fix this issue. The identifier VDB-215445 was assigned to this vulnerability. |
2022-12-13 |
not yet calculated |
CVE-2022-4455
MISC
MISC |
| falling-fruit — falling-fruit |
A vulnerability has been found in falling-fruit and classified as problematic. This vulnerability affects unknown code. The manipulation leads to cross site scripting. The attack can be initiated remotely. The name of the patch is 15adb8e1ea1f1c3e3d152fc266071f621ef0c621. It is recommended to apply a patch to fix this issue. VDB-215446 is the identifier assigned to this vulnerability. |
2022-12-13 |
not yet calculated |
CVE-2022-4456
MISC
MISC |
| wordpress — wordpress |
Unauth. SQL Injection vulnerability in Cryptocurrency Widgets Pack Plugin <=1.8.1 on WordPress. |
2022-12-15 |
not yet calculated |
CVE-2022-44588
MISC |
| samsung — samsung_tv |
The Samsung TV (2021 and 2022 model) smart remote control allows attackers to enable microphone access via Bluetooth spoofing when a user is activating remote control by pressing a button. This is fixed in xxx72510, E9172511 for 2021 models, xxxA1000, 4x2A0200 for 2022 models. |
2022-12-13 |
not yet calculated |
CVE-2022-44636
MISC
MISC |
| wordpress — wordpress |
The Mega Addons plugin for WordPress is vulnerable to authorization bypass due to a missing capability check on the vc_saving_data function in versions up to, and including, 4.2.7. This makes it possible for authenticated attackers, with subscriber-level permissions and above, to update the plugin’s settings. |
2022-12-14 |
not yet calculated |
CVE-2022-4501
MISC
MISC |
| codeprojects — expense_tracker |
A cross-site scripting (XSS) vulnerability in Expense Tracker 1.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Chat text field. |
2022-12-15 |
not yet calculated |
CVE-2022-45033
MISC |
| rainygao — docsys |
A vulnerability has been found in RainyGao DocSys and classified as critical. Affected by this vulnerability is an unknown functionality of the component com.DocSystem.controller.UserController#getUserImg. The manipulation leads to path traversal: ‘../filedir’. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-215851. |
2022-12-15 |
not yet calculated |
CVE-2022-4511
N/A
N/A |
| european_environment_agency — eionet.contreg |
A vulnerability, which was classified as problematic, has been found in European Environment Agency eionet.contreg. This issue affects some unknown processing. The manipulation of the argument searchTag/resourceUri leads to cross site scripting. The attack may be initiated remotely. Upgrading to version 2022-06-27T0948 is able to address this issue. The name of the patch is a120c2153e263e62c4db34a06ab96a9f1c6bccb6. It is recommended to upgrade the affected component. The identifier VDB-215885 was assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4513
N/A
N/A
N/A |
opencaching_deutschland — oc-server3
|
A vulnerability, which was classified as problematic, was found in Opencaching Deutschland oc-server3. Affected is an unknown function of the file htdocs/lang/de/ocstyle/varset.inc.php. The manipulation of the argument varvalue leads to cross site scripting. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. The name of the patch is 4bdd6a0e7b7760cea03b91812cbb80d7b16e3b5f. It is recommended to apply a patch to fix this issue. VDB-215886 is the identifier assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4514
N/A
N/A
N/A |
| wordpress — wordpress |
The WP User plugin for WordPress is vulnerable to Stored Cross-Site Scripting via its settings parameters in versions up to, and including, 7.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled. |
2022-12-15 |
not yet calculated |
CVE-2022-4519
MISC
MISC |
wso2 — carbon-registry
|
A vulnerability was found in WSO2 carbon-registry up to 4.8.11. It has been rated as problematic. Affected by this issue is some unknown functionality of the file components/registry/org.wso2.carbon.registry.search.ui/src/main/resources/web/search/advancedSearchForm-ajaxprocessor.jsp of the component Advanced Search. The manipulation of the argument mediaType/rightOp/leftOp/rightPropertyValue/leftPropertyValue leads to cross site scripting. The attack may be launched remotely. Upgrading to version 4.8.12 is able to address this issue. The name of the patch is 0c827cc1b14b82d8eb86117ab2e43c34bb91ddb4. It is recommended to upgrade the affected component. The identifier of this vulnerability is VDB-215900. |
2022-12-15 |
not yet calculated |
CVE-2022-4520
N/A
N/A
N/A
N/A |
| wso2 — carbon-registry |
A vulnerability classified as problematic has been found in WSO2 carbon-registry up to 4.8.7. This affects an unknown part of the component Request Parameter Handler. The manipulation of the argument parentPath/path/username/path/profile_menu leads to cross site scripting. It is possible to initiate the attack remotely. Upgrading to version 4.8.12 is able to address this issue. The name of the patch is 9f967abfde9317bee2cda469dbc09b57d539f2cc. It is recommended to upgrade the affected component. The identifier VDB-215901 was assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4521
N/A
N/A
N/A
N/A |
| calendarxp — calendarxp |
A vulnerability classified as problematic was found in CalendarXP up to 10.0.1. This vulnerability affects unknown code. The manipulation leads to cross site scripting. The attack can be initiated remotely. Upgrading to version 10.0.2 is able to address this issue. The name of the patch is e3715b2228ddefe00113296069969f9e184836da. It is recommended to upgrade the affected component. VDB-215902 is the identifier assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4522
N/A
N/A
N/A |
| vexim — vexim2 |
A vulnerability, which was classified as problematic, has been found in vexim2. This issue affects some unknown processing. The manipulation leads to cross site scripting. The attack may be initiated remotely. The name of the patch is 21c0a60d12e9d587f905cd084b2c70f9b1592065. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-215903. |
2022-12-15 |
not yet calculated |
CVE-2022-4523
N/A
N/A
N/A |
| roots — soil |
A vulnerability, which was classified as problematic, was found in Roots soil Plugin up to 4.1.0. Affected is the function language_attributes of the file src/Modules/CleanUpModule.php. The manipulation of the argument language leads to cross site scripting. It is possible to launch the attack remotely. Upgrading to version 4.1.1 is able to address this issue. The name of the patch is 0c9151e00ab047da253e5cdbfccb204dd423269d. It is recommended to upgrade the affected component. The identifier of this vulnerability is VDB-215904. |
2022-12-15 |
not yet calculated |
CVE-2022-4524
N/A
N/A
N/A
N/A |
| national_sleep_research_resource — sleepdata.org |
A vulnerability has been found in National Sleep Research Resource sleepdata.org up to 59.0.0.rc and classified as problematic. Affected by this vulnerability is an unknown functionality. The manipulation leads to cross site scripting. The attack can be launched remotely. Upgrading to version 59.0.0 is able to address this issue. The name of the patch is da44a3893b407087829b006d09339780919714cd. It is recommended to upgrade the affected component. The identifier VDB-215905 was assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4525
N/A
N/A
N/A |
| django-photologue — django-photologue |
A vulnerability was found in django-photologue up to 3.15.1 and classified as problematic. Affected by this issue is some unknown functionality of the file photologue/templates/photologue/photo_detail.html of the component Default Template Handler. The manipulation of the argument object.caption leads to cross site scripting. The attack may be launched remotely. Upgrading to version 3.16 is able to address this issue. The name of the patch is 960cb060ce5e2964e6d716ff787c72fc18a371e7. It is recommended to apply a patch to fix this issue. VDB-215906 is the identifier assigned to this vulnerability. |
2022-12-15 |
not yet calculated |
CVE-2022-4526
N/A
N/A
N/A |
| collective — collective.task |
A vulnerability was found in collective.task up to 3.0.9. It has been classified as problematic. This affects the function renderCell/AssignedGroupColumn of the file src/collective/task/browser/table.py. The manipulation leads to cross site scripting. It is possible to initiate the attack remotely. Upgrading to version 3.0.10 is able to address this issue. The name of the patch is 1aac7f83fa2c2b41d59ba02748912953461f3fac. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-215907. |
2022-12-15 |
not yet calculated |
CVE-2022-4527
N/A
N/A
N/A |
| exact_software — synergy_enterprise |
An arbitrary file upload vulnerability in the profile picture upload function of Exact Synergy Enterprise 267 before 267SP13 and Exact Synergy Enterprise 500 before 500SP6 allows attackers to execute arbitrary code via a crafted SVG file. |
2022-12-15 |
not yet calculated |
CVE-2022-45338
MISC |
| siemens — teamcenter_and_jt2go |
A vulnerability has been identified in JT2Go (All versions), Teamcenter Visualization V13.2 (All versions < V13.2.0.12), Teamcenter Visualization V13.3 (All versions = V13.3.0.8), Teamcenter Visualization V14.0 (All versions = V14.0.0.4), Teamcenter Visualization V14.1 (All versions < V14.1.0.6). The CCITT_G4Decode.dll contains an out of bounds read vulnerability when parsing a RAS file. An attacker can leverage this vulnerability to execute code in the context of the current process. (ZDI-CAN-19056) |
2022-12-13 |
not yet calculated |
CVE-2022-45484
CONFIRM |
| wordpress — wordpress |
The WP Shamsi plugin for WordPress is vulnerable to authorization bypass due to a missing capability check on the deactivate() function hooked via init() in versions up to, and including, 4.1.0. This makes it possible for unauthenticated attackers to deactivate arbitrary plugins on the site. This can be used to deactivate security plugins that aids in exploiting other vulnerabilities. |
2022-12-16 |
not yet calculated |
CVE-2022-4555
MISC
MISC |
| alinto — sogo |
A vulnerability was found in Alinto SOGo up to 5.7.1 and classified as problematic. Affected by this issue is the function _migrateMailIdentities of the file SoObjects/SOGo/SOGoUserDefaults.m of the component Identity Handler. The manipulation of the argument fullName leads to cross site scripting. The attack may be launched remotely. Upgrading to version 5.8.0 is able to address this issue. The name of the patch is efac49ae91a4a325df9931e78e543f707a0f8e5e. It is recommended to upgrade the affected component. The identifier of this vulnerability is VDB-215960. |
2022-12-16 |
not yet calculated |
CVE-2022-4556
MISC
MISC
MISC |
| alinto — sogo |
A vulnerability was found in Alinto SOGo up to 5.7.1. It has been classified as problematic. This affects an unknown part of the file SoObjects/SOGo/NSString+Utilities.m of the component Folder/Mail Handler. The manipulation leads to cross site scripting. It is possible to initiate the attack remotely. Upgrading to version 5.8.0 is able to address this issue. The name of the patch is 1e0f5f00890f751e84d67be4f139dd7f00faa5f3. It is recommended to upgrade the affected component. The identifier VDB-215961 was assigned to this vulnerability. |
2022-12-16 |
not yet calculated |
CVE-2022-4558
MISC
MISC
MISC |
| inex — ipx-manager |
A vulnerability was found in INEX IPX-Manager up to 6.2.0. It has been declared as problematic. This vulnerability affects unknown code of the file resources/views/customer/list.foil.php. The manipulation leads to cross site scripting. The attack can be initiated remotely. Upgrading to version 6.3.0 is able to address this issue. The name of the patch is bc9b14c6f70cccdb89b559e8bc3a7318bfe9c243. It is recommended to upgrade the affected component. VDB-215962 is the identifier assigned to this vulnerability. |
2022-12-16 |
not yet calculated |
CVE-2022-4559
MISC
MISC
MISC |
| joget — joget |
A vulnerability was found in Joget up to 7.0.32. It has been rated as problematic. This issue affects the function getInternalJsCssLib of the file wflow-core/src/main/java/org/joget/plugin/enterprise/UniversalTheme.java of the component wflow-core. The manipulation of the argument key leads to cross site scripting. The attack may be initiated remotely. Upgrading to version 8.0-BETA is able to address this issue. The name of the patch is ecf8be8f6f0cb725c18536ddc726d42a11bdaa1b. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-215963. |
2022-12-16 |
not yet calculated |
CVE-2022-4560
MISC
MISC
MISC |
| wikimedia — semanticdrilldown_extension |
A vulnerability classified as problematic has been found in SemanticDrilldown Extension. Affected is the function printFilterLine of the file includes/specials/SDBrowseDataPage.php of the component GET Parameter Handler. The manipulation of the argument value leads to cross site scripting. It is possible to launch the attack remotely. The name of the patch is 6e18cf740a4548166c1d95f6d3a28541d298a3aa. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-215964. |
2022-12-16 |
not yet calculated |
CVE-2022-4561
MISC
MISC |
| freedom_of_the_press — securedrop |
A vulnerability was found in Freedom of the Press SecureDrop. It has been rated as critical. Affected by this issue is some unknown functionality of the file gpg-agent.conf. The manipulation leads to symlink following. Local access is required to approach this attack. The name of the patch is b0526a06f8ca713cce74b63e00d3730618d89691. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-215972. |
2022-12-16 |
not yet calculated |
CVE-2022-4563
N/A
N/A
N/A |
| university_of_central_florida — materia |
A vulnerability classified as problematic has been found in University of Central Florida Materia up to 9.0.1-alpha1. This affects the function before of the file fuel/app/classes/controller/api.php of the component API Controller. The manipulation leads to cross-site request forgery. It is possible to initiate the attack remotely. Upgrading to version 9.0.2-alpha2 is able to address this issue. The name of the patch is af259115d2e8f17068e61902151ee8a9dbac397b. It is recommended to upgrade the affected component. The identifier VDB-215973 was assigned to this vulnerability. |
2022-12-16 |
not yet calculated |
CVE-2022-4564
N/A
N/A
N/A
N/A |
| dromara — hutool |
A vulnerability classified as problematic was found in Dromara HuTool up to 5.8.10. This vulnerability affects unknown code of the file cn.hutool.core.util.ZipUtil.java. The manipulation leads to resource consumption. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. Upgrading to version 5.8.11 is able to address this issue. It is recommended to upgrade the affected component. VDB-215974 is the identifier assigned to this vulnerability. |
2022-12-16 |
not yet calculated |
CVE-2022-4565
MISC
MISC |
| y_project — ruoyi |
A vulnerability, which was classified as critical, has been found in y_project RuoYi 4.7.5. This issue affects some unknown processing of the file com/ruoyi/generator/controller/GenController. The manipulation leads to sql injection. The name of the patch is 167970e5c4da7bb46217f576dc50622b83f32b40. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-215975. |
2022-12-16 |
not yet calculated |
CVE-2022-4566
MISC
MISC
MISC
MISC |
| openemr — openemr |
Improper Access Control in GitHub repository openemr/openemr prior to 7.0.0.2. |
2022-12-17 |
not yet calculated |
CVE-2022-4567
CONFIRM
MISC |
| ubi_reader — ubi_reader |
A vulnerability, which was classified as problematic, has been found in UBI Reader up to 0.8.0. Affected by this issue is the function ubireader_extract_files of the file ubireader/ubifs/output.py of the component UBIFS File Handler. The manipulation leads to path traversal. The attack may be launched remotely. Upgrading to version 0.8.5 is able to address this issue. The name of the patch is d5d68e6b1b9f7070c29df5f67fc060f579ae9139. It is recommended to upgrade the affected component. VDB-216146 is the identifier assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4572
MISC
MISC
MISC
MISC |
| sharp — multifunction_printers |
Command injection vulnerability in nw_interface.html in SHARP multifunction printers (MFPs)’s Digital Full-color Multifunctional System 202 or earlier, 120 or earlier, 600 or earlier, 121 or earlier, 500 or earlier, 402 or earlier, 790 or earlier, and Digital Multifunctional System (Monochrome) 200 or earlier, 211 or earlier, 102 or earlier, 453 or earlier, 400 or earlier, 202 or earlier, 602 or earlier, 500 or earlier, 401 or earlier allows remote attackers to execute arbitrary commands via unspecified vectors. |
2022-12-16 |
not yet calculated |
CVE-2022-45796
MISC |
| mind-map — mind-map |
A vulnerability was found in 1j01 mind-map and classified as problematic. This issue affects some unknown processing of the file app.coffee. The manipulation of the argument html leads to cross site scripting. The attack may be initiated remotely. The name of the patch is 9617e6084dfeccd92079ab4d7f439300a4b24394. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-216167. |
2022-12-17 |
not yet calculated |
CVE-2022-4581
N/A
N/A |
| starter-public-edition-4 — starter-public-edition-4 |
A vulnerability was found in starter-public-edition-4 up to 4.6.10. It has been classified as problematic. Affected is an unknown function. The manipulation leads to cross site scripting. It is possible to launch the attack remotely. Upgrading to version 4.6.11 is able to address this issue. The name of the patch is 2606983c20f6ea3430ac4b36b3d2e88aafef45da. It is recommended to upgrade the affected component. The identifier of this vulnerability is VDB-216168. |
2022-12-17 |
not yet calculated |
CVE-2022-4582
N/A
N/A
N/A |
| jlems — jlems |
A vulnerability was found in jLEMS. It has been declared as critical. Affected by this vulnerability is the function unpackJar of the file src/main/java/org/lemsml/jlems/io/util/JUtil.java. The manipulation leads to path traversal. The attack can be launched remotely. The name of the patch is 8c224637d7d561076364a9e3c2c375daeaf463dc. It is recommended to apply a patch to fix this issue. The identifier VDB-216169 was assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4583
N/A
N/A
N/A |
| axiomatic — bento4 |
A vulnerability was found in Axiomatic Bento4. It has been rated as critical. Affected by this issue is some unknown functionality of the component mp42aac. The manipulation leads to heap-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-216170 is the identifier assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4584
N/A
N/A
N/A |
| opencaching_deutschland — oc-server3 |
A vulnerability classified as problematic has been found in Opencaching Deutschland oc-server3. This affects an unknown part of the file htdocs/templates2/ocstyle/start.tpl of the component Cookie Handler. The manipulation of the argument usercountryCode leads to cross site scripting. It is possible to initiate the attack remotely. The name of the patch is c720f2777a452186c67ef30db3679dd409556544. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-216171. |
2022-12-17 |
not yet calculated |
CVE-2022-4585
N/A
N/A
N/A |
opencaching_deutschland — oc-server3
|
A vulnerability classified as problematic was found in Opencaching Deutschland oc-server3. This vulnerability affects unknown code of the file htdocs/templates2/ocstyle/cachelists.tpl of the component Cachelist Handler. The manipulation of the argument name_filter/by_filter leads to cross site scripting. The attack can be initiated remotely. The name of the patch is a9f79c7da78cd24a7ef1d298e6bc86006972ea73. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-216172. |
2022-12-17 |
not yet calculated |
CVE-2022-4586
N/A
N/A
N/A |
| opencaching_deutschland — oc-server3 |
A vulnerability, which was classified as problematic, has been found in Opencaching Deutschland oc-server3. This issue affects some unknown processing of the file htdocs/templates2/ocstyle/login.tpl of the component Login Page. The manipulation of the argument username leads to cross site scripting. The attack may be initiated remotely. The name of the patch is 3296ebd61e7fe49e93b5755d5d7766d6e94a7667. It is recommended to apply a patch to fix this issue. The identifier VDB-216173 was assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4587
N/A
N/A
N/A |
| boston_sleep — slice |
A vulnerability, which was classified as problematic, was found in Boston Sleep slice up to 84.2.0. Affected is an unknown function of the component Layout Handler. The manipulation leads to cross site scripting. It is possible to launch the attack remotely. Upgrading to version 85.0.0 is able to address this issue. The name of the patch is 6523bb17d889e2ab13d767f38afefdb37083f1d0. It is recommended to upgrade the affected component. VDB-216174 is the identifier assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4588
N/A
N/A
N/A |
cyface — terms_and_conditions_module
|
A vulnerability has been found in cyface Terms and Conditions Module up to 2.0.10 and classified as problematic. Affected by this vulnerability is the function returnTo of the file termsandconditions/views.py. The manipulation leads to open redirect. The attack can be launched remotely. Upgrading to version 2.0.11 is able to address this issue. The name of the patch is 03396a1c2e0af95e12a45c5faef7e47a4b513e1a. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-216175. |
2022-12-17 |
not yet calculated |
CVE-2022-4589
N/A
N/A
N/A
N/A |
| mschaef — toto |
A vulnerability was found in mschaef toto up to 1.4.20. It has been classified as problematic. This affects an unknown part of the component Todo List Handler. The manipulation leads to cross site scripting. It is possible to initiate the attack remotely. Upgrading to version 1.4.21 is able to address this issue. The name of the patch is fdc825ac5249f40683377e8a526a06cdc6870125. It is recommended to upgrade the affected component. The identifier VDB-216177 was assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4590
N/A
N/A
N/A |
| mschaef — toto |
A vulnerability was found in mschaef toto up to 1.4.20. It has been declared as problematic. This vulnerability affects unknown code of the component Email Parameter Handler. The manipulation leads to cross site scripting. The attack can be initiated remotely. Upgrading to version 1.4.21 is able to address this issue. The name of the patch is 1f27f37c1a06f54a76971f70eaa6139dc139bdf9. It is recommended to upgrade the affected component. VDB-216178 is the identifier assigned to this vulnerability. |
2022-12-17 |
not yet calculated |
CVE-2022-4591
N/A
N/A
N/A |
| siemens — multiple_products |
A vulnerability has been identified in APOGEE PXC Series (BACnet) (All versions < V3.5.5), APOGEE PXC Series (P2 Ethernet) (All versions < V2.8.20), TALON TC Series (BACnet) (All versions < V3.5.5). A low privilege authenticated attacker with network access to the integrated web server could download sensitive information from the device containing user account credentials. |
2022-12-13 |
not yet calculated |
CVE-2022-45937
CONFIRM |
| alist — alist |
Alist v3.4.0 is vulnerable to Directory Traversal, |
2022-12-15 |
not yet calculated |
CVE-2022-45969
MISC |
| tenda — ac15 |
Tenda AC15 V15.03.06.23 is vulnerable to Buffer Overflow via function formSetClientState. |
2022-12-16 |
not yet calculated |
CVE-2022-46109
MISC |
| aerocms — aerocms |
In AeroCms v0.0.1, there is an arbitrary file upload vulnerability at /admin/posts.php?source=edit_post , through which we can upload webshell and control the web server. |
2022-12-16 |
not yet calculated |
CVE-2022-46135
MISC |
| aerocms — aerocms |
AeroCMS v0.0.1 is vulnerable to Directory Traversal. The impact is: obtain sensitive information (remote). The component is: AeroCMS v0.0.1. |
2022-12-16 |
not yet calculated |
CVE-2022-46137
MISC |
| siemens — scalance |
Affected devices use a weak encryption scheme to encrypt the debug zip file. This could allow an authenticated attacker to decrypt the contents of the file and retrieve debug information about the system. |
2022-12-13 |
not yet calculated |
CVE-2022-46140
CONFIRM |
| siemens — scalance |
Affected devices store the CLI user passwords encrypted in flash memory. Attackers with physical access to the device could retrieve the file and decrypt the CLI user passwords. |
2022-12-13 |
not yet calculated |
CVE-2022-46142
CONFIRM |
| siemens — scalance |
Affected devices do not check the TFTP blocksize correctly. This could allow an authenticated attacker to read from an uninitialized buffer that potentially contains previously allocated data. |
2022-12-13 |
not yet calculated |
CVE-2022-46143
CONFIRM |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs becuase the swap handler for the XTestFakeInput request of the XTest extension may corrupt the stack if GenericEvents with lengths larger than 32 bytes are sent through a the XTestFakeInput request. This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions. This issue does not affect systems where client and server use the same byte order. |
2022-12-14 |
not yet calculated |
CVE-2022-46340
MISC
MISC
FEDORA
FEDORA |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs because the handler for the XIPassiveUngrab request accesses out-of-bounds memory when invoked with a high keycode or button code. This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions. |
2022-12-14 |
not yet calculated |
CVE-2022-46341
MISC
MISC
FEDORA
FEDORA |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs because the handler for the XvdiSelectVideoNotify request may write to memory after it has been freed. This issue can lead to local privileges elevation on systems where the X se |
2022-12-14 |
not yet calculated |
CVE-2022-46342
MISC
MISC
FEDORA
FEDORA |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs because the handler for the ScreenSaverSetAttributes request may write to memory after it has been freed. This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions. |
2022-12-14 |
not yet calculated |
CVE-2022-46343
MISC
MISC
FEDORA
FEDORA |
| x.org — x.org |
A vulnerability was found in X.Org. This security flaw occurs because the handler for the XIChangeProperty request has a length-validation issues, resulting in out-of-bounds memory reads and potential information disclosure. This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions. |
2022-12-14 |
not yet calculated |
CVE-2022-46344
MISC
MISC
FEDORA
FEDORA |
| mbed_tls — mbed_tls |
An issue was discovered in Mbed TLS before 2.28.2 and 3.x before 3.3.0. An adversary with access to precise enough information about memory accesses (typically, an untrusted operating system attacking a secure enclave) can recover an RSA private key after observing the victim performing a single private-key operation, if the window size (MBEDTLS_MPI_WINDOW_SIZE) used for the exponentiation is 3 or smaller. |
2022-12-15 |
not yet calculated |
CVE-2022-46392
MISC
MISC |
| mbed_tls — mbed_tls |
An issue was discovered in Mbed TLS before 2.28.2 and 3.x before 3.3.0. There is a potential heap-based buffer overflow and heap-based buffer over-read in DTLS if MBEDTLS_SSL_DTLS_CONNECTION_ID is enabled and MBEDTLS_SSL_CID_IN_LEN_MAX > 2 * MBEDTLS_SSL_CID_OUT_LEN_MAX. |
2022-12-15 |
not yet calculated |
CVE-2022-46393
MISC
MISC
MISC |
| atos — unify |
A command injection vulnerability has been identified in Atos Unify OpenScape 4000 Assistant and Unify OpenScape 4000 Manager (8 before R2.22.18, 10 before 0.28.13, and 10 R1 before R1.34.4) that may allow an unauthenticated attacker to upload arbitrary files and achieve administrative access to the system. |
2022-12-13 |
not yet calculated |
CVE-2022-46404
MISC
MISC |
| totolink — a7100ru |
TOTOlink A7100RU V7.4cu.2313_B20191024 was discovered to contain a command injection vulnerability via the wscDisabled parameter in the setting/setWiFiSignalCfg function. |
2022-12-15 |
not yet calculated |
CVE-2022-46631
MISC |
| totolink — a7100ru |
TOTOlink A7100RU V7.4cu.2313_B20191024 was discovered to contain a command injection vulnerability via the wscDisabled parameter in the setting/setWiFiWpsCfg function. |
2022-12-15 |
not yet calculated |
CVE-2022-46634
MISC |
| rockwell_automation — micrologix_controllers |
Rockwell Automation was made aware of a vulnerability by a security researcher from Georgia Institute of Technology that the MicroLogix 1100 and 1400 controllers contain a vulnerability that may give an attacker the ability to accomplish remote code execution. The vulnerability is an unauthenticated stored cross-site scripting vulnerability in the embedded webserver. The payload is transferred to the controller over SNMP and is rendered on the homepage of the embedded website. |
2022-12-16 |
not yet calculated |
CVE-2022-46670
MISC |
| apple — multiple_products |
A race condition was addressed with additional validation. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-46689
MISC
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
An out-of-bounds write issue was addressed with improved input validation. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, watchOS 9.2. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-46690
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A memory consumption issue was addressed with improved memory handling. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46691
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A logic issue was addressed with improved state management. This issue is fixed in Safari 16.2, tvOS 16.2, iCloud for Windows 14.1, iOS 15.7.2 and iPadOS 15.7.2, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may bypass Same Origin Policy. |
2022-12-15 |
not yet calculated |
CVE-2022-46692
MISC
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
An out-of-bounds write issue was addressed with improved input validation. This issue is fixed in tvOS 16.2, iCloud for Windows 14.1, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing a maliciously crafted file may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46693
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
An out-of-bounds write issue was addressed with improved input validation. This issue is fixed in iOS 16.2 and iPadOS 16.2, iOS 15.7.2 and iPadOS 15.7.2, tvOS 16.2, watchOS 9.2. Parsing a maliciously crafted video file may lead to kernel code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46694
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. This issue is fixed in tvOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Visiting a website that frames malicious content may lead to UI spoofing. |
2022-12-15 |
not yet calculated |
CVE-2022-46695
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A memory corruption issue was addressed with improved input validation. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46696
MISC
MISC
MISC
MISC
MISC |
| apple — macos |
An out-of-bounds access issue was addressed with improved bounds checking. This issue is fixed in macOS Ventura 13.1. An app may be able to execute arbitrary code with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-46697
MISC |
| apple — ios_and_ipados |
A logic issue was addressed with improved checks. This issue is fixed in Safari 16.2, tvOS 16.2, iCloud for Windows 14.1, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may disclose sensitive user information. |
2022-12-15 |
not yet calculated |
CVE-2022-46698
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A memory corruption issue was addressed with improved state management. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46699
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
A memory corruption issue was addressed with improved input validation. This issue is fixed in Safari 16.2, tvOS 16.2, macOS Ventura 13.1, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. Processing maliciously crafted web content may lead to arbitrary code execution. |
2022-12-15 |
not yet calculated |
CVE-2022-46700
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved bounds checks. This issue is fixed in iOS 16.2 and iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2. Connecting to a malicious NFS server may lead to arbitrary code execution with kernel privileges. |
2022-12-15 |
not yet calculated |
CVE-2022-46701
MISC
MISC
MISC |
| apple — multiple_products |
The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2. An app may be able to disclose kernel memory. |
2022-12-15 |
not yet calculated |
CVE-2022-46702
MISC |
| zabbix — web_service_report_generation |
Arbitrary file read vulnerability exists in Zabbix Web Service Report Generation, which listens on the port 10053. The service does not have proper validation for URL parameters before reading the files. |
2022-12-15 |
not yet calculated |
CVE-2022-46768
CONFIRM |
| apache — zeppelin |
An Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) vulnerability in Apache Zeppelin allows logged-in users to execute arbitrary javascript in other users’ browsers. This issue affects Apache Zeppelin before 0.8.2. Users are recommended to upgrade to a supported version of Zeppelin. |
2022-12-16 |
not yet calculated |
CVE-2022-46870
MISC |
| netgear — nighthawk |
The “puhttpsniff” service, which runs by default, is susceptible to command injection due to improperly sanitized user input. An unauthenticated attacker on the same network segment as the router can execute arbitrary commands on the device without authentication. |
2022-12-16 |
not yet calculated |
CVE-2022-47208
MISC |
| netgear — nighthawk |
A support user exists on the device and appears to be a backdoor for Technical Support staff. The default password for this account is “support” and cannot be changed by a user via any normally accessible means. |
2022-12-16 |
not yet calculated |
CVE-2022-47209
MISC |
| netgear — nighthawk |
The default console presented to users over telnet (when enabled) is restricted to a subset of commands. Commands issued at this console, however, appear to be fed directly into a system call or other similar function. This allows any authenticated user to execute arbitrary commands on the device. |
2022-12-16 |
not yet calculated |
CVE-2022-47210
MISC |
| sick — sick_sim2000st |
Password recovery vulnerability in SICK SIM2000ST Partnumber 2086502 with firmware version = 1.13.4 as soon as possible (available in SICK Support Portal). |
2022-12-16 |
not yet calculated |
CVE-2022-47377
MISC |
| typo3 — typo3 |
An issue was discovered in the fe_change_pwd (aka Change password for frontend users) extension before 2.0.5, and 3.x before 3.0.3, for TYPO3. The extension fails to revoke existing sessions for the current user when the password has been changed. |
2022-12-14 |
not yet calculated |
CVE-2022-47406
MISC |









Recent Comments