by Scott Muniz | Jul 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Several federal initiatives such as CDM (Continuous Diagnostic and Mitigation) TIC (Trusted Internet Connection) are increasingly becoming similar, in that identical tools and approaches such as Zero Trust can be used to meet multiple federal mandates. This convergence provides an opportunity to reduce complexity while helping agencies improve their security posture and increase IT efficiency.
This blog is the fourth of a four-part series on meeting federal mandates with SaaS services, provides a deep dive on auditing and logging.
Previous blogs in the series have addressed various ways to manage and secure mobile devices, endpoints, and the Office 365 platform. In Part 4, we will focus on the various methods to audit and log activity. The cloud is ever changing, and Microsoft has published numerous announcements since the blog series started. One of which was the release of Microsoft Threat Protection (MTP), which helps unify auditing and querying of Microsoft’s security solutions.
There are several locations that activity logs can be found however for this post we will focus on three primary solutions.
- Unified Access Logs (UAL)
- Microsoft Threat Protection
- Azure Sentinel
Unified Audit Logs (UAL)
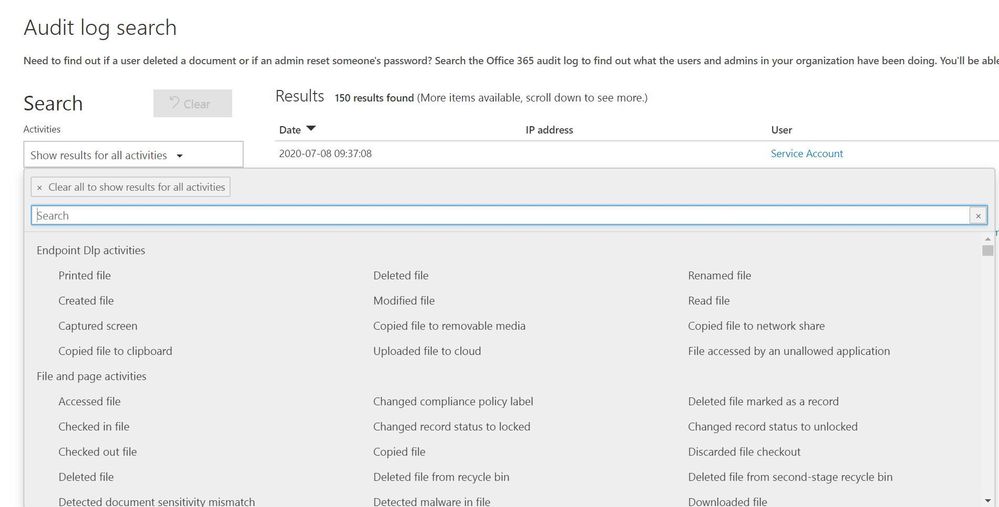
When an organization wants to gain insights into Office 365 activity the first location to be familiar with is the UAL located at https://protection.office.com/unifiedauditlog . The UAL provides organizations with a rich set of filters to search 100’s of Office 365 activities.
Figure 1: Unified Audit Log search interface
The UAL provides multiple ways to search the data using a graphical interface like the portal or a command line via Powershell, which allows organization to choose the right method for their needs. The UAL can assist organizations in understanding what data is accessed and by whom however, the UAL can only see activity that is hosted in Office 365 services such as: OneDrive, SharePoint Online, and Exchange Online. The UAL has no visibility into data once it leaves the platform, this is where other Microsoft security tools extend the organizations’ ability to continue to track data that has moved outside of Office 365.
Microsoft Threat Protection
Microsoft announced the release of Microsoft Threat Protection (MTP) at RSA this year. MTP is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Security teams understand modern attacks traverse many parts of infrastructure and the Microsoft Threat Protection suite protects:
- Endpoints with Microsoft Defender ATP - Microsoft Defender ATP is a unified endpoint platform for preventative protection, post-breach detection, automated investigation, and response.
- Email and collaboration with Office 365 ATP - Office 365 ATP safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
- Identities with Azure ATP and Azure AD Identity Protection - Azure ATP uses Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
- Applications with Microsoft Cloud App security - Microsoft Cloud App security is a comprehensive cross-SaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
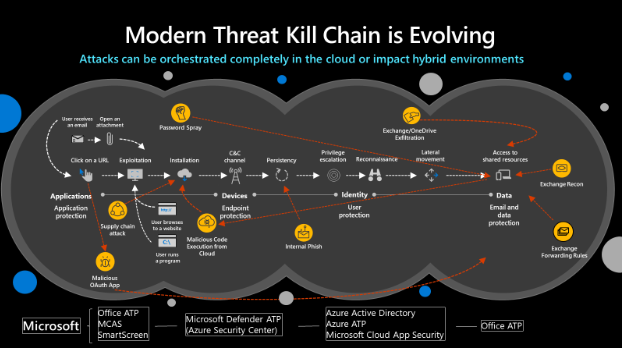
Figure 2: Modern Threat Kill Chain
MTP will reduce the number of portals IT staff must utilize when securing their infrastructure, Microsoft’s goal is to move security related information to https://security.microsoft.com and provide a common method to search/query data. The first change in the initial release is the ability to utilize the advanced hunting language, Kusto Query Language (KQL). KQL has become the new query language for Microsoft security solutions and provides a rich set of capabilities, scalability, and speed.
The advanced hunting capabilities of MTP allows organizations to search across several data sets in a single interface and join queries together to gain rich insight. MTP should not be confused with a traditional SIEM. The focus of MTP is to unify Microsoft security solutions into a single location, not to aggregate 3rd party data. We will address the “3rd party data” scenario shortly.
Figure 3: MTP Advanced Hunting interface
MTP aggregates several Microsoft security solutions together helping organizations identity attacks that span an entire kill chain. When creating custom detection rules MTP maps the detections to the MITRE ATT&CK framework. This helps security teams identify the type of techniques being used and can assist in breaking the attack chain.
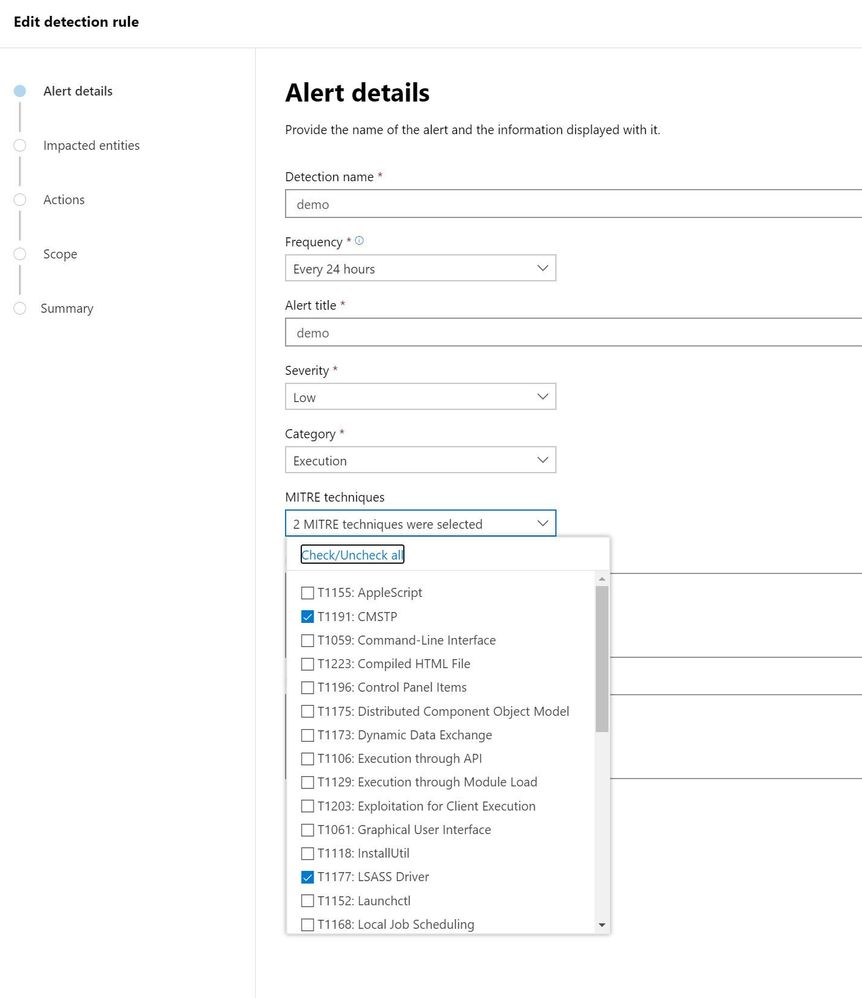
Figure 4: MTP custom detection rule wizard
One of the challenges security teams often face is alert fatigue. This happens when security teams receive hundreds of individual alerts and may also be known as an alert storm. MTP automatically correlates alerts into incidents reducing the “noise” for security teams. In the incident below MTP has correlated 165 alerts, 15 devices, and 603 pieces of evidence into a single incident. This allows staff a single location to pivot across several entities and investigate an entire kill chain vs. “hunting down” individual alerts. MTP does an excellent job of aggregating the signal from the MTP stack but it is not a SIEM, this is where Azure Sentinel comes into the picture.
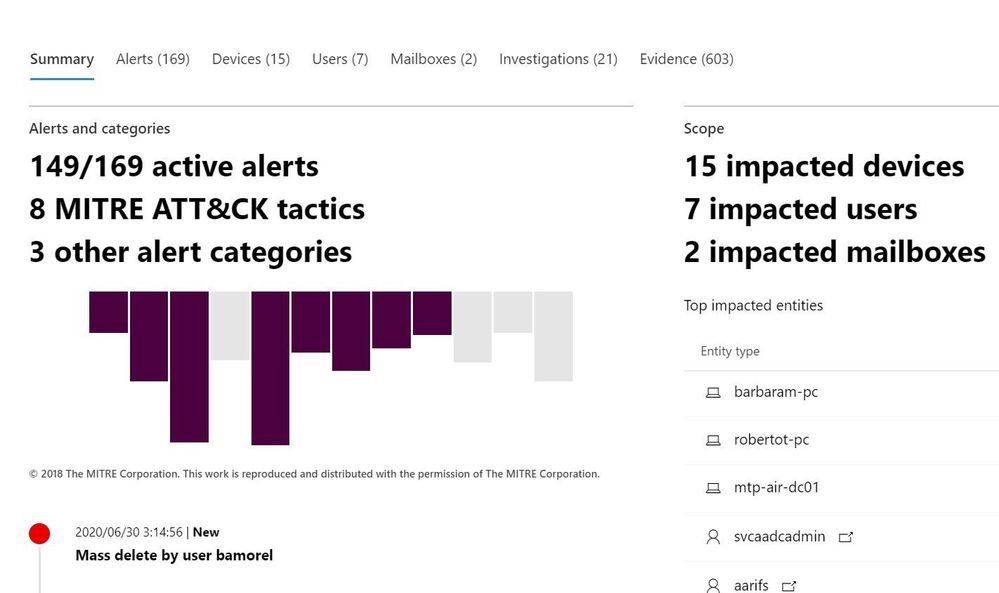
Figure 5: MTP Incident view zoomed in
Azure Sentinel
Microsoft released Azure Sentinel, a born in the cloud SIEM/SOAR which provides scalability and deep integration with a variety of vendors. Over time Azure Sentinel will be able to aggregate the data from MTP into a single location. Since Azure Sentinel was created as a cloud-first solution, the pace of new features evolves quickly and allows for massive scale and high performance.
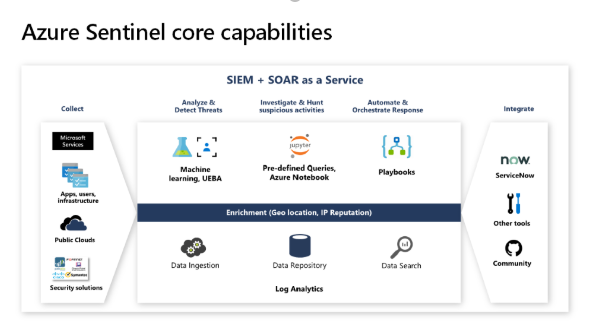
Figure 6: Azure Sentinel capabilities overview
Azure Sentinel is built on top of the Log Analytics platform which means you use the same KQL language to query the data as with MTP. Since these tools share a common query language, this helps security teams easily move between tools and use a familiar experience.
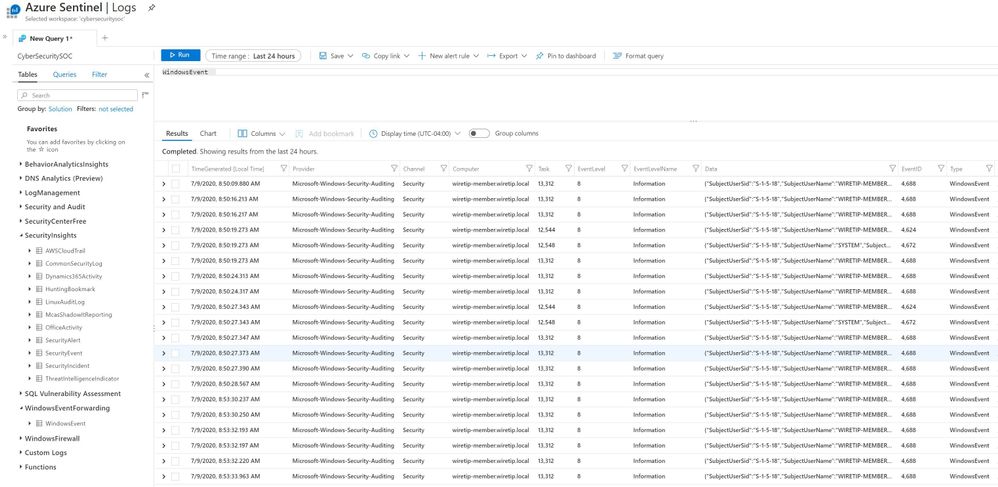
Figure 7: Azure Sentinel advanced hunting
Hunting through raw data is valuable but, at times organizations need an easy way to visualize data. Azure Sentinel allows you to create workbooks from the data feeds you are receiving. Each connector has a default workbook that provides a data visualization. Organizations can edit or create custom views that meet their requirements.
Figure 8: Azure Sentinel workbook views
The biggest difference between MTP and Azure Sentinel is the ability to pull in 3rd party data and custom data sources. Azure Sentinel was designed to provide a single click experience when connecting Microsoft data sources like Office 365. This simplifies a task that often challenges security teams when attempting to connect various data sources. The list of first party and 3rd party connectors is always expanding at a cloud pace.
Azure Sentinel includes numerous Microsoft log sources at no additional cost to your organization for 90 days.
Figure 8: Azure Sentinel data connectors
Like MTP, Azure Sentinel maps threats to the MITRE ATT&CK framework and helps organizations hunt through data with many predefined queries written by Microsoft’s internal threat team Microsoft threat intelligence center (MSTIC). A challenge with data queries is once a data set is parsed and new data is added, its missed in a query. Azure Sentinel has a feature called live streaming that will parse any new data while the query is running so that security teams can identify possible indicators.
Figure 9: Azure Sentinel hunting
Azure Sentinel has integrated Juniper notebooks into the platform to allow analyst to store and share hunting repos. Juniper notebooks help security teams that use other scripting languages, and run queries to data sources, that maybe outside of Azure Sentinel. Microsoft also publishes a set of notebooks on GitHub located here that anyone can download and incorporate into their environment even if you do not use Azure Sentinel.
Figure 10: Azure Sentinel Juniper notebooks
At the heart of most SIEMs is incident management. Azure Sentinel provides a rich set of Playbooks and the ability to assign incidents to analysts and keep a history of comments with the incident. The incident view quickly allows security teams to view any entities involved with an alert and provide a graphical investigation view of the incident.
Figure 10: Azure Sentinel Incident view
Playbooks are considered a Security Orchestration And Response (SOAR) tool that can help organizations create, processes, and automate tasks. Playbooks have native connections into hundreds of applications and services allowing staff to connect alerts into Microsoft teams, Slack, or create tickets in ITSM solutions like ServiceNow. Playbooks are the corner stone for your SOC to automate processes to provide a consistent set of actions and remove many manual tasks.
Figure 11: Azure Sentinel Playbooks
Microsoft provides organizations several methods to audit and log data from various sources to include Office 365. In this post we focused on three main locations.
- Unified Access Log (UAL)
- Microsoft Threat Protection (MTP)
- Azure Sentinel
Each location provides a rich set of data that can be reviewed by security teams to help audit and secure an organization.
Blog Series links:
Part 1: Securing mobile: Designing SaaS service implementations to meet federal policy
Part 2: Securing the endpoint: designing SaaS service implementations to meet federal policy
Part 3: Securing the Platform: Designing SaaS service implementations to meet federal policy
by Scott Muniz | Jul 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We have released a refresh to the MSIX Toolkit. The Toolkit has been updated with redistributables from the Windows 10, version 2004 SDK. In addition we have created easy to download individual .zip files for x86 and x64.
MSIX Toolkit is available on Github: https://github.com/microsoft/MSIX-Toolkit. Let us know what types of things you would like to see in future releases.
Thanks!
John Vintzel (@jvintzel)
Program Manager Lead, MSIX
by Scott Muniz | Jul 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
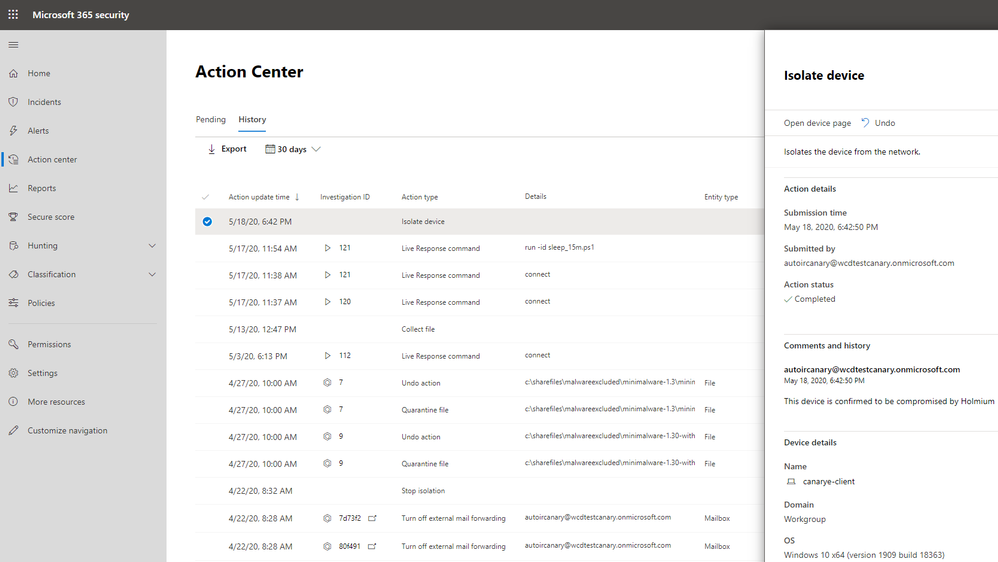
The results of current and past automatic investigations and remediation actions across your organization’s devices and mailboxes are visible in the Action center in Microsoft Threat Protection. The Action center provides a unified experience for remediation actions and an audit log. The Action center enables your security operations team to approve pending remediation actions and to remediate impacted assets. You can also review approved actions in an audit log. The Action center brings all this together across Microsoft Threat Protection security workloads, including Office 365 Advanced Threat Protection (Office 365 ATP) and Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
Furthermore, if you need to undo a remediation action that was taken by Microsoft Defender ATP, in most cases, you can do that in the Action center in Microsoft Threat Protection. The History tab tracks all remediation actions that were completed, and you can undo an action there.
But what about remediation actions that were taken manually or from an advanced hunting experience, such as isolating a device, or restricting app execution on a specific device? How do you view an audit log for those actions?
Suppose, for example, that in order to slow down the spread of ransomware, your security operations team decides to isolate all of the devices connected to specific subnet in your org. To take this action, you could use an advanced hunting custom detection with the predefined action, “Isolate device.” Such a custom detection might look like this:
DeviceNetworkEvents
| extend Subnet = extract(@”(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?).){3}”,0,LocalIP ) | where Subnet starts with “192.168.0.”
Or, maybe you use a slightly more advanced example with specific alert categories to view the list of devices, like this:
DeviceAlertEvents
| where Category in(“Credential access”, “Ransomware”) | join kind=leftouter(
DeviceNetworkEvents
| extend Subnet = extract(@”(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?).){3}”,0,LocalIP )
| where Subnet starts with “192.168.0.” )
, but how do you know which devices were isolated, and how do you undo device isolation if needed?
We’re happy to announce that you can now audit and undo manually taken actions in Microsoft Defender ATP in the Action center in Microsoft Threat Protection. This capability is in public preview now!
This capability provides you with one location to view an audit log of manually taken remediation actions that were performed in different portal experiences, such as the device page, file page, and advanced hunting. You can also undo certain actions, such as device isolation and app restriction, on the History tab in the Action center.
The full set of manual actions that are logged in the action center are :
- Collect investigation package
- Isolate device / Undo isolate device
- Offboard machine
- Release code execution
- Release from quarantine
- Request sample
- Restrict code execution / Undo restrict code execution
- Run antivirus scan
- Stop and quarantine
Want to see what this looks like? Here’s an example of an audit record showing device isolation:
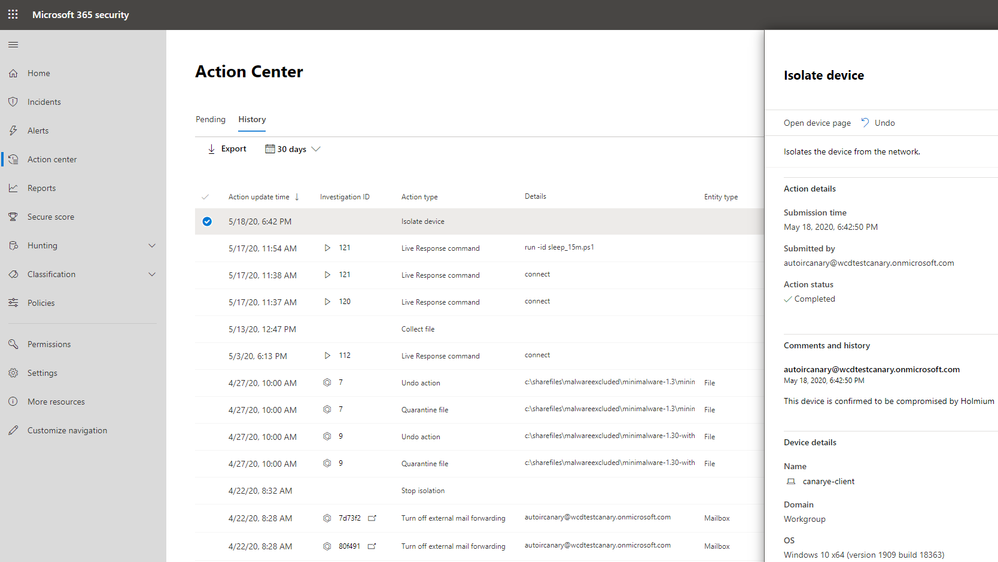
Here’s an example of undoing an action to isolate device:
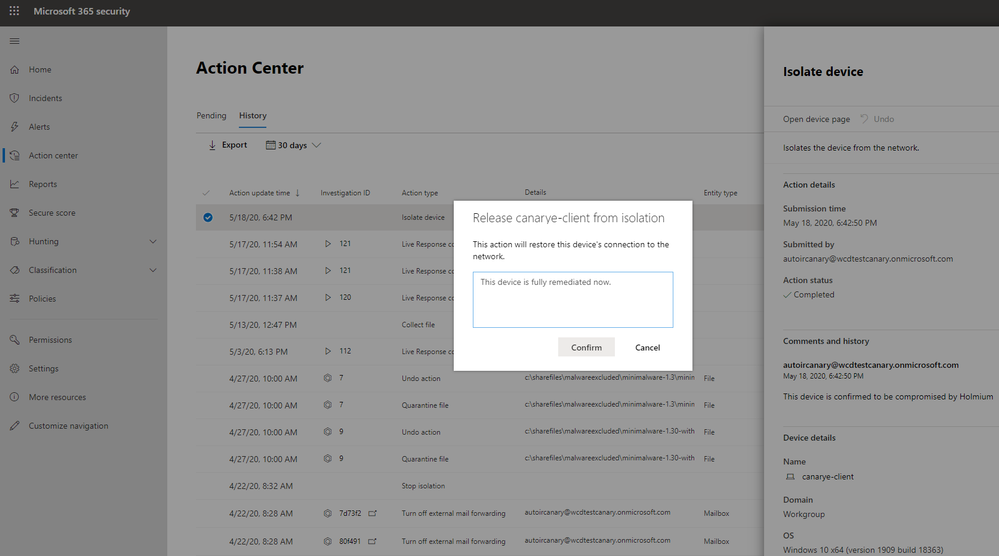
Make sure to opt in to preview features, and try it now!
Let us know what you think by leaving a comment below.
The Microsoft Threat Protection Team

by Scott Muniz | Jul 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Your task, should you choose to accept it: listen to the new “Tasks in Teams” Intrazone episode.
I’ll wait… just let me know when you’re done.
In this episode, Chris and I talk with Shin-Yi Lim (Senior PMM) and Howard Crow (Partner GPM) about Tasks in Teams. The new Tasks app brings a cohesive task management experience to Microsoft Teams, integrating personal tasks powered by Microsoft To Do and team tasks powered by Planner – all in one place. We dive into Microsoft tasks’ journey, task coherence, app integration, the use of AI, and the overall user experience.
Listen to podcast below.
Subscribe to The Intrazone podcast! And listen to episode 54 now + show links and more below.
 Intrazone guests – left-to-right, Shin-Yi Lim (senior product marketing manager) and Howard Crow (partner group product manager) – both focused on Planner & Tasks in Teams.
Intrazone guests – left-to-right, Shin-Yi Lim (senior product marketing manager) and Howard Crow (partner group product manager) – both focused on Planner & Tasks in Teams.
Links to important on-demand recordings and articles mentioned in this episode:
- Articles and sites
- Events
- Hosts and guests
Subscribe today!
Listen to the show! If you like what you hear, we’d love for you to Subscribe, Rate and Review it on iTunes or wherever you get your podcasts.
Be sure to visit our show page to hear all the episodes, access the show notes, and get bonus content. And stay connected to the SharePoint community blog where we’ll share more information per episode, guest insights, and take any questions from our listeners and SharePoint users (TheIntrazone@microsoft.com). We, too, welcome your ideas for future episodes topics and segments. Keep the discussion going in comments below; we’re hear to listen and grow.
Subscribe to The Intrazone podcast! And listen to episode 54 now.
Thanks for listening!
The SharePoint team wants you to unleash your creativity and productivity. And we will do this, together, one task at a time.
The Intrazone links
+ Listen to other Microsoft podcasts at aka.ms/microsoft/podcasts.
![Mark Kashman_1-1583812153608.jpeg Left to right [The Intrazone co-hosts]: Chris McNulty, director PMM (SharePoint, #ProjectCortex – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).](https://www.drware.com/wp-content/uploads/2020/07/large-471) Left to right [The Intrazone co-hosts]: Chris McNulty, director PMM (SharePoint, #ProjectCortex – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).
Left to right [The Intrazone co-hosts]: Chris McNulty, director PMM (SharePoint, #ProjectCortex – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).
 The Intrazone, a show about the Microsoft 365 intelligent intranet (aka.ms/TheIntrazone)
The Intrazone, a show about the Microsoft 365 intelligent intranet (aka.ms/TheIntrazone)
by Scott Muniz | Jul 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
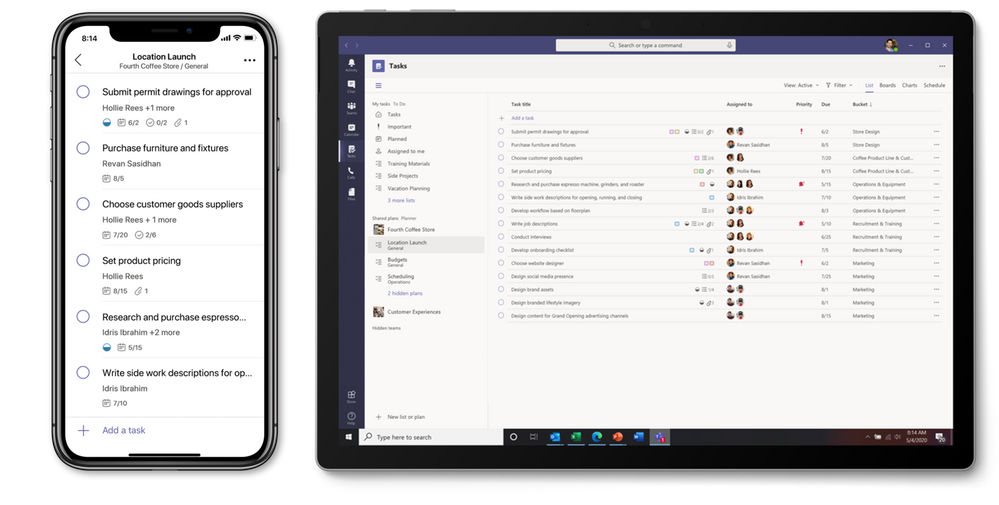
Tasks are the building blocks of our work. They help us keep track of what to do now and what needs to be done next. But tasks are hard to manage, especially when you have to flip between different places to see them all.
That’s why we’re thrilled to begin rolling out Tasks in Microsoft Teams, a coherent task management experience in your hub for teamwork. The new Tasks experience brings together Microsoft Planner and Microsoft To Do into Teams, giving you one place to manage your team plans and individual tasks.
We’re starting to roll out Tasks in Teams on desktop today to a small group of users, and that rollout will continue through September. The Tasks in Teams mobile experience will not be available until the desktop rollout is complete.
As a reminder from our announcement blog during Ignite last year, the Tasks in Teams experience comes as an app, which shows both Planner and To Do tasks, and as a tab, which is added to individual Teams channels and only shows Planner tasks. That blog also reiterated our commitment to Planner—and that’s still true today. We’re as dedicated to Planner as ever; in fact, there’s never been more momentum behind Planner because it powers key elements of the Tasks in Teams experience.
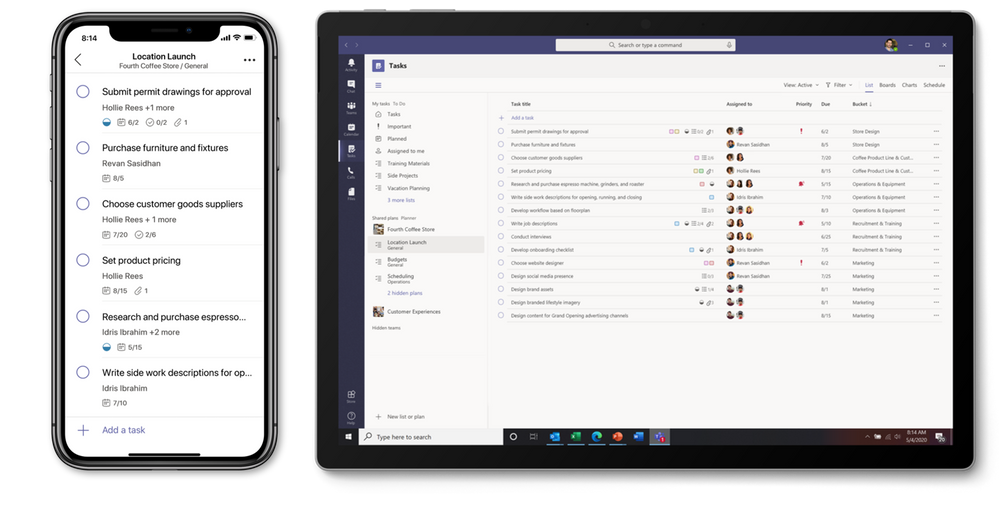
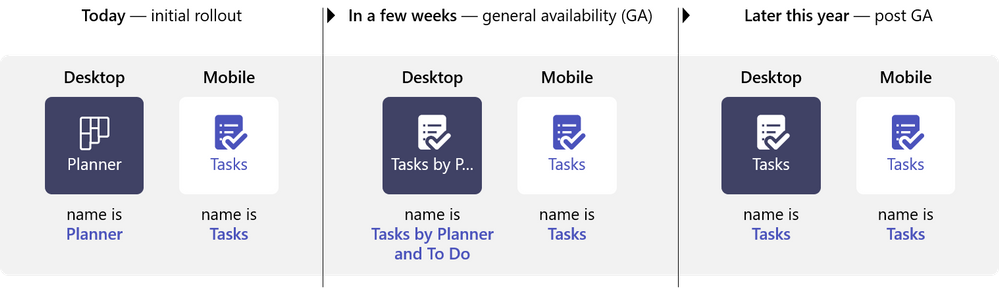
To get the Tasks in Teams app when it’s available, click the ellipses in the Teams left siderail and select Planner. No, that’s not a typo: as we roll out the new Planner experience in Teams desktop, the app name will initially remain Planner. It will then briefly change to Tasks by Planner and To Do. Finally, it’ll be simplified to Tasks. On Teams mobile clients, users will always see the app name as Tasks.
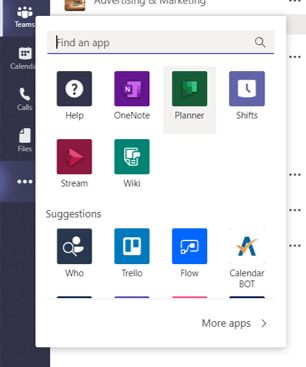
The above is true for the tab, too, which you can add by selecting the “+” icon at the top of a Teams channel.
We’ve devised this naming sequence on purpose to alleviate confusion among customers who miss our communications about this release. Nothing about the app’s functionality will change during this process; it only affects the name. Here’s a graphical representation of the sequence for reference.
If you’re not seeing the new Tasks experience after adding the app, hang tight. We’re enabling Tasks in Teams for customers little by little, and you will see it in the coming weeks. When it does appear, check out this support article first for tips on getting started. Government tenants will see the app and all its name changes but will not get the updated Tasks in Teams experience during this rollout. We’ll be in touch through Message Center when it becomes available.
We’ve made some exciting additions to the Tasks in Teams experience since the Ignite announcement. Here’s short summary of those changes, which are covered more extensively on our dedicated Microsoft Docs page.
- Task publishing lets companies create tasks at the corporate level and push those tasks to targeted teams across their Firstline Workforce. For example, leadership for a nationwide retailer can create tasks for an upcoming promotional campaign, send that list to all affected store locations, and then track progress against the assigned tasks. Store managers can easily assign tasks to individual employees, while Firstline Workers can see a simple prioritized list of those tasks on their personal or company-issued mobile device. As of now, task publishing is only available in private preview. If you’re interested in getting the private preview of task publishing for your organization, please fill out this form to nominate your company.
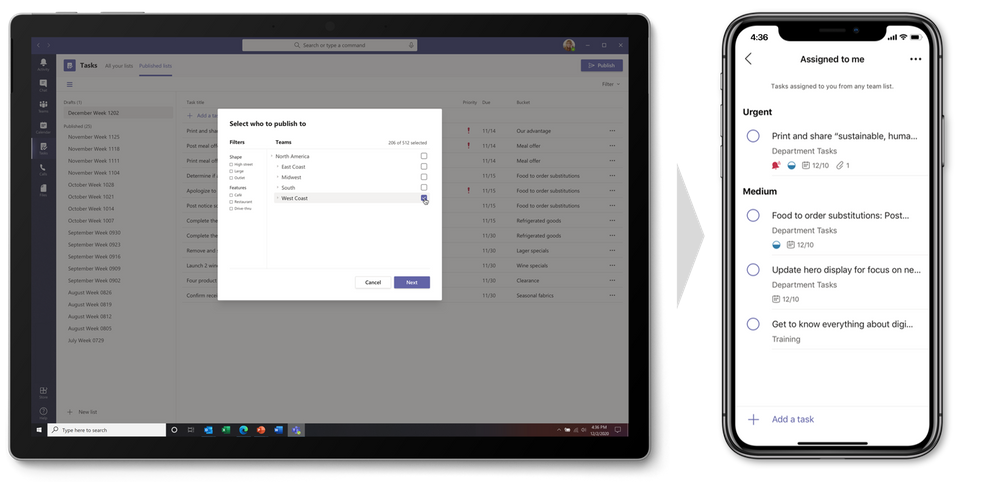
- Tasks in Teams is available in Teams desktop, web, and mobile clients. If Tasks in Teams is added in Teams on desktop, it’ll appear in the other two environments, too. The exception is guest users, who can access the Tasks tab but will only see the app on mobile.
- Both the Tasks in Teams app and tab include four views: the traditional Board, Charts, and Schedule views from Planner, plus the new Lists view. All four are available in the Teams desktop and web experiences, but only the List view is available on mobile.
- The new List view also comes with a new capability: edit multiple tasks at once. In both the desktop and web experiences, instead of making the same edits to each task individually, you can edit all affected tasks simultaneously. This feature supports changes for progress, priority, due date, and more depending on what task list you’re looking at.
- If you’re an IT admin, the Docs page includes steps for enabling or disabling Tasks in Teams for either your entire organization or specific users; setting a policy to automatically pin the Tasks app to the Teams siderail; and, hiding My tasks lists for users.
- You can use Graph API and Power Automate integrations for To Do and Planner to surface tasks created in other apps in Tasks in Teams. You can read more about these APIs on our respective Planner and To Do pages. Note, the existing To Do Graph API will soon get updated to a new one, which is currently in private preview. For Power Automate, you can easily build workflows that create tasks based on certain criteria (e.g., a task is created when a form is submitted with a specific response). There are lots of premade Power Automate templates for To Do and Planner here, just search for the product name.
Tasks in Teams is the first major step in building a more connected task management experience across Microsoft 365 apps. Outlook already syncs all tasks to To Do where you can manage more task details, and Office will soon support task assignments from @mentions in Word, Excel, and PowerPoint.
We’re calling this entire effort Tasks in Microsoft 365, and it revolves around three core principles: coherence, intelligence, and integration. It’s part of a larger collaborative work management initiative that we just launched last week at Microsoft Inspire. You can watch the 30-minute presentation video about that effort here.
To stay current on our progress, keep checking the Planner Tech Community. We also invite you to check out our new Tasks in Microsoft 365 webpage, where you can find more information and announcements about Microsoft’s connected tasks experience. If you have ideas or suggestions for improving this experience, drop us a line on Planner UserVoice.
AMA happening now! We’re hosting our second hour-long Ask Microsoft Anything (AMA) of the year right now, Tuesday, July 28 at 12 p.m. EST/9 a.m. PST. All the session details are here. Our last AMA was in April and the summary notes from that session are here. AMAs are your opportunity to engage with members of the Microsoft Planner team to ask us… well, anything. Come join us!






Recent Comments