This article is contributed. See the original author and article here.
Several federal initiatives such as CDM (Continuous Diagnostic and Mitigation) TIC (Trusted Internet Connection) are increasingly becoming similar, in that identical tools and approaches such as Zero Trust can be used to meet multiple federal mandates. This convergence provides an opportunity to reduce complexity while helping agencies improve their security posture and increase IT efficiency.
This blog is the fourth of a four-part series on meeting federal mandates with SaaS services, provides a deep dive on auditing and logging.
Previous blogs in the series have addressed various ways to manage and secure mobile devices, endpoints, and the Office 365 platform. In Part 4, we will focus on the various methods to audit and log activity. The cloud is ever changing, and Microsoft has published numerous announcements since the blog series started. One of which was the release of Microsoft Threat Protection (MTP), which helps unify auditing and querying of Microsoft’s security solutions.
There are several locations that activity logs can be found however for this post we will focus on three primary solutions.
Unified Audit Logs (UAL)
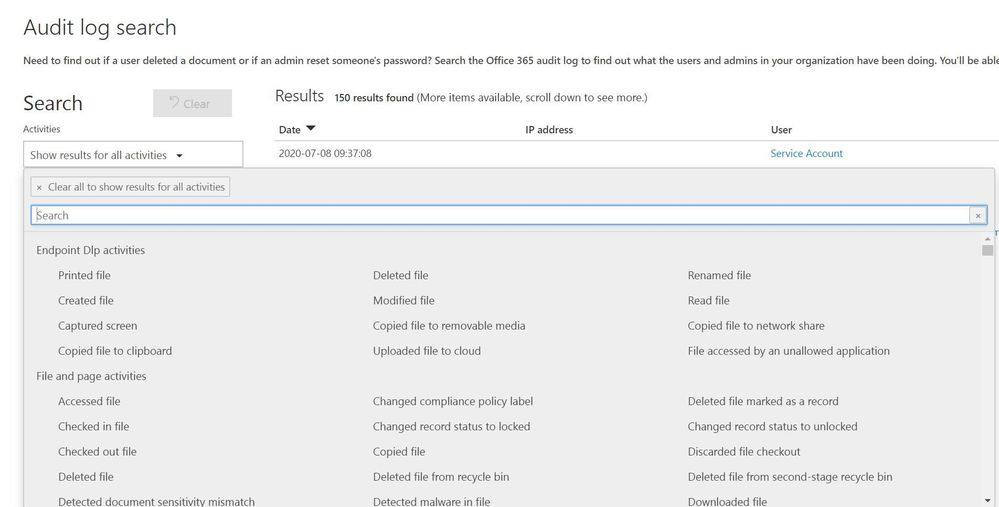
When an organization wants to gain insights into Office 365 activity the first location to be familiar with is the UAL located at https://protection.office.com/unifiedauditlog . The UAL provides organizations with a rich set of filters to search 100’s of Office 365 activities.
Figure 1: Unified Audit Log search interface
The UAL provides multiple ways to search the data using a graphical interface like the portal or a command line via Powershell, which allows organization to choose the right method for their needs. The UAL can assist organizations in understanding what data is accessed and by whom however, the UAL can only see activity that is hosted in Office 365 services such as: OneDrive, SharePoint Online, and Exchange Online. The UAL has no visibility into data once it leaves the platform, this is where other Microsoft security tools extend the organizations’ ability to continue to track data that has moved outside of Office 365.
Microsoft Threat Protection
Microsoft announced the release of Microsoft Threat Protection (MTP) at RSA this year. MTP is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Security teams understand modern attacks traverse many parts of infrastructure and the Microsoft Threat Protection suite protects:
- Endpoints with Microsoft Defender ATP - Microsoft Defender ATP is a unified endpoint platform for preventative protection, post-breach detection, automated investigation, and response.
- Email and collaboration with Office 365 ATP - Office 365 ATP safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
- Identities with Azure ATP and Azure AD Identity Protection - Azure ATP uses Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
- Applications with Microsoft Cloud App security - Microsoft Cloud App security is a comprehensive cross-SaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
Figure 2: Modern Threat Kill Chain
MTP will reduce the number of portals IT staff must utilize when securing their infrastructure, Microsoft’s goal is to move security related information to https://security.microsoft.com and provide a common method to search/query data. The first change in the initial release is the ability to utilize the advanced hunting language, Kusto Query Language (KQL). KQL has become the new query language for Microsoft security solutions and provides a rich set of capabilities, scalability, and speed.
The advanced hunting capabilities of MTP allows organizations to search across several data sets in a single interface and join queries together to gain rich insight. MTP should not be confused with a traditional SIEM. The focus of MTP is to unify Microsoft security solutions into a single location, not to aggregate 3rd party data. We will address the “3rd party data” scenario shortly.
Figure 3: MTP Advanced Hunting interface
MTP aggregates several Microsoft security solutions together helping organizations identity attacks that span an entire kill chain. When creating custom detection rules MTP maps the detections to the MITRE ATT&CK framework. This helps security teams identify the type of techniques being used and can assist in breaking the attack chain.
Figure 4: MTP custom detection rule wizard
One of the challenges security teams often face is alert fatigue. This happens when security teams receive hundreds of individual alerts and may also be known as an alert storm. MTP automatically correlates alerts into incidents reducing the “noise” for security teams. In the incident below MTP has correlated 165 alerts, 15 devices, and 603 pieces of evidence into a single incident. This allows staff a single location to pivot across several entities and investigate an entire kill chain vs. “hunting down” individual alerts. MTP does an excellent job of aggregating the signal from the MTP stack but it is not a SIEM, this is where Azure Sentinel comes into the picture.
Figure 5: MTP Incident view zoomed in
Azure Sentinel
Microsoft released Azure Sentinel, a born in the cloud SIEM/SOAR which provides scalability and deep integration with a variety of vendors. Over time Azure Sentinel will be able to aggregate the data from MTP into a single location. Since Azure Sentinel was created as a cloud-first solution, the pace of new features evolves quickly and allows for massive scale and high performance.
Figure 6: Azure Sentinel capabilities overview
Azure Sentinel is built on top of the Log Analytics platform which means you use the same KQL language to query the data as with MTP. Since these tools share a common query language, this helps security teams easily move between tools and use a familiar experience.
Figure 7: Azure Sentinel advanced hunting
Hunting through raw data is valuable but, at times organizations need an easy way to visualize data. Azure Sentinel allows you to create workbooks from the data feeds you are receiving. Each connector has a default workbook that provides a data visualization. Organizations can edit or create custom views that meet their requirements.
Figure 8: Azure Sentinel workbook views
The biggest difference between MTP and Azure Sentinel is the ability to pull in 3rd party data and custom data sources. Azure Sentinel was designed to provide a single click experience when connecting Microsoft data sources like Office 365. This simplifies a task that often challenges security teams when attempting to connect various data sources. The list of first party and 3rd party connectors is always expanding at a cloud pace.
Azure Sentinel includes numerous Microsoft log sources at no additional cost to your organization for 90 days.
Figure 8: Azure Sentinel data connectors
Like MTP, Azure Sentinel maps threats to the MITRE ATT&CK framework and helps organizations hunt through data with many predefined queries written by Microsoft’s internal threat team Microsoft threat intelligence center (MSTIC). A challenge with data queries is once a data set is parsed and new data is added, its missed in a query. Azure Sentinel has a feature called live streaming that will parse any new data while the query is running so that security teams can identify possible indicators.
Figure 9: Azure Sentinel hunting
Azure Sentinel has integrated Juniper notebooks into the platform to allow analyst to store and share hunting repos. Juniper notebooks help security teams that use other scripting languages, and run queries to data sources, that maybe outside of Azure Sentinel. Microsoft also publishes a set of notebooks on GitHub located here that anyone can download and incorporate into their environment even if you do not use Azure Sentinel.
Figure 10: Azure Sentinel Juniper notebooks
At the heart of most SIEMs is incident management. Azure Sentinel provides a rich set of Playbooks and the ability to assign incidents to analysts and keep a history of comments with the incident. The incident view quickly allows security teams to view any entities involved with an alert and provide a graphical investigation view of the incident.
Figure 10: Azure Sentinel Incident view
Playbooks are considered a Security Orchestration And Response (SOAR) tool that can help organizations create, processes, and automate tasks. Playbooks have native connections into hundreds of applications and services allowing staff to connect alerts into Microsoft teams, Slack, or create tickets in ITSM solutions like ServiceNow. Playbooks are the corner stone for your SOC to automate processes to provide a consistent set of actions and remove many manual tasks.
Figure 11: Azure Sentinel Playbooks
Microsoft provides organizations several methods to audit and log data from various sources to include Office 365. In this post we focused on three main locations.
- Unified Access Log (UAL)
- Microsoft Threat Protection (MTP)
- Azure Sentinel
Each location provides a rich set of data that can be reviewed by security teams to help audit and secure an organization.
Blog Series links:
Part 1: Securing mobile: Designing SaaS service implementations to meet federal policy
Part 2: Securing the endpoint: designing SaaS service implementations to meet federal policy
Part 3: Securing the Platform: Designing SaaS service implementations to meet federal policy
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments