Urgent: Protect Against Active Exploitation of ProxyShell Vulnerabilities
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
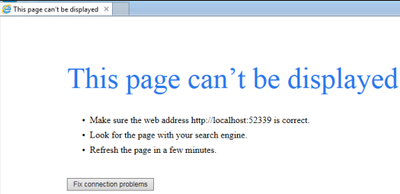
What is Page cannot be displayed?
There are certain scenarios in which when we try to browse a site hosted on IIS server, we end up getting Page cannot be displayed (PCBD) . There are several reasons for which we will eventually get PCBD , some of the reasons are :
In most of the scenarios the request doesn’t even reach to the IIS layer and fails before that . Here is a nice article explaining about layers of service that a request has to travel: https://techcommunity.microsoft.com/t5/iis-support-blog/iis-services-http-sys-w3svc-was-w3wp-oh-my/ba-p/287856
Generally, a PCBD error looks like below:

This blog will focus on list of steps which are going to be useful for troubleshooting these kinds of scenarios .Here, I have created a Flow chart:
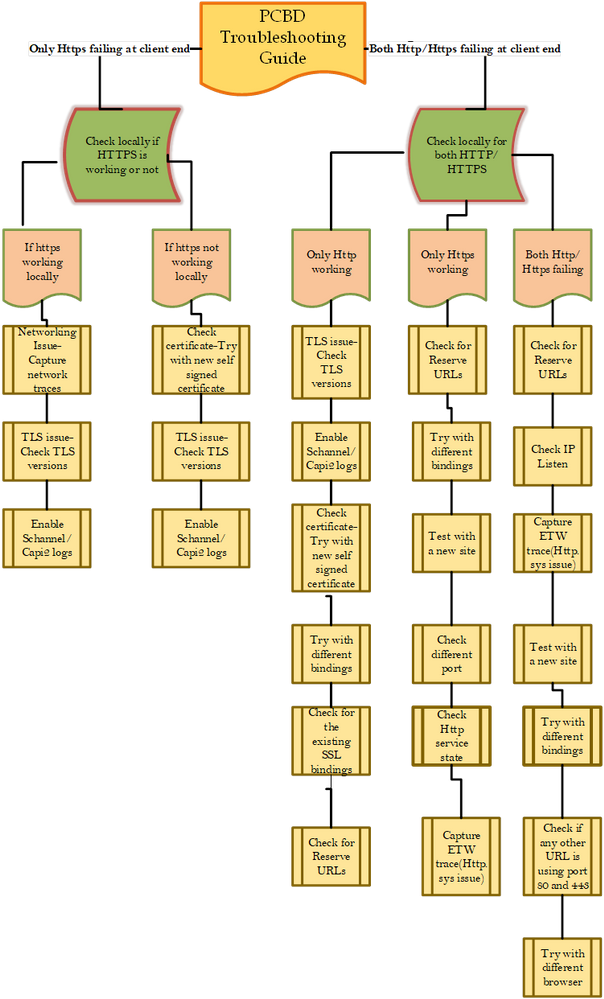
There are several steps in the flow chart which require data collection , just listing a few of them here:
Steps for capturing Schnannel logs and Capi2 logs :
Schannel Logs:
Logging options:
The default value for Schannel event logging is 0x0000 in Windows NT Server 4.0, which means that no Schannel events are logged. In Windows 2000 Server and Windows XP Professional, this value is set to 0x0001, which means that error messages are logged. Additionally, you can log multiple events by specifying the hexadecimal value that equates to the logging options that you want. For example, to log error messages (0x0001) and warnings (0x0002), set the value to 0x0003.
Value Description
0x0000 Do not log
0x0001 Log error messages
0x0002 Log warnings
0x0004 Log informational and success events
From https://support.microsoft.com/en-in/help/260729/how-to-enable-schannel-event-logging-in-iis
Capi2 Logs :
The CryptoAPI 2.0 Diagnostics is a feature available on Windows Server 2008+ that supports the trouble shooting of issues concerned with, for example: Certificate Chain Validation Certificate Store Operations Signature Verification
This article describes how to enable the CAPI2 Diagnostic, but for an in depth review of the capability, check here.
Enable CAPI2 logging by opening the Event Viewer and navigating to the Event Viewer (Local)Applications and Services LogsMicrosoftWindowsCAPI2 directory and expand it. You should see a view named Operational as illustrated in Figure 1.
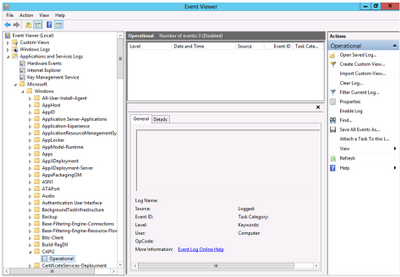
Figure 1, CAPI2 Diagnostics in Event Viewer
Next, right-click on the Operational view and click the Enable Log menu item as shown in Figure 2.
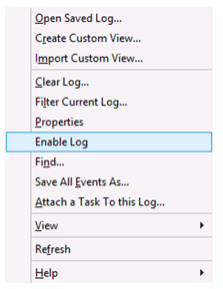
Figure 2, Enable CAPI2 Event Logging
Once enabled, any warnings or errors are logged into the viewer. Reproduce the problem you are experiencing and check if the issue is logged.
Command for checking Reserved URLs:
netsh http show urlacl
The above command lists DACLs (discretionary access control list ) for the specified reserved URL or all reserved URLs.
Command for checking Http.sys Service State:
netsh http show ServiceState
The above command shows snapshot of Http service .
Command for checking the IP Listen:
netsh http show iplisten
The above command lists all IP addresses in the IP listen list. The IP listen list is used to scope the list of addresses to which the HTTP service binds. “0.0.0.0” means any IPv4 address and “::” means any IPv6 address
Capturing Network trace –
To capture Network trace using Netmon tool…please check out this link : https://docs.microsoft.com/en-us/windows/client-management/troubleshoot-tcpip-netmon
Steps for capturing Http.sys ETW trace:
Capture a Perfview trace with IIS ETW providers. You can download Perfview from : https://github.com/microsoft/perfview/releases/tag/P2.0.71
Before starting the Pervfiew trace just run this command in admin command prompt (this captures http.sys traces), also start the other traces:
netsh trace start capture=yes overwrite=yes maxsize=2048 tracefile=c:minio_http.etl provider={DD5EF90A-6398-47A4-AD34-4DCECDEF795F} keywords=0xffffffffffffffff level=0xff provider={20F61733-57F1-4127-9F48-4AB7A9308AE2} keywords=0xffffffffffffffff level=0xff provider="Microsoft-Windows-HttpLog" keywords=0xffffffffffffffff level=0xff provider="Microsoft-Windows-HttpService" keywords=0xffffffffffffffff level=0xff provider="Microsoft-Windows-HttpEvent" keywords=0xffffffffffffffff level=0xff provider="Microsoft-Windows-Http-SQM-Provider" keywords=0xffffffffffffffff level=0xff
Make some 5-6 requests from client (http requests not https).. Once they fail, stop all of them, then run the below command to stop the command
netsh trace stop
This netsh trace will be saved on C drive with the name “minio_http.etl”..
Hope this one helps you.
Happy troubleshooting !!! :smiling_face_with_smiling_eyes:

This article is contributed. See the original author and article here.

A first look at Azure AD Conditional Access authentication context
Kenneth van Surksum is an Enterprise Mobility MVP from The Netherlands. Kenneth a works as a modern workplace consultant at Insight24 and is specialized in building modern workplace solutions on top of Microsoft 365. Kenneth is co-founder of the Windows Management User Group Netherlands (WMUG_NL), which was recently rebranded to the Workplace Ninja User Group Netherlands, and organizes (virtual) community meetings on a regular basis. Kenneth loves to speak about technical topics related to his daily work. Kenneth is Microsoft Certified Trainer (MCT) and has multiple certifications, he has received the MVP and VMware vExpert award multiple times. For more, check out Kenneth’s Twitter @kennethvs
Set up organizational Teams meeting backgrounds
Vesku Nopanen is a Principal Consultant in Office 365 and Modern Work and passionate about Microsoft Teams. He helps and coaches customers to find benefits and value when adopting new tools, methods, ways or working and practices into daily work-life equation. He focuses especially on Microsoft Teams and how it can change organizations’ work. He lives in Turku, Finland. Follow him on Twitter: @Vesanopanen

UNO PACKAGE: A NEW WAY TO UPDATE WINDOWS 10 AND WINDOWS SERVER 2019
Silvio Di Benedetto is founder and CEO at Inside Technologies. He is a Digital Transformation helper, and Microsoft MVP for Cloud Datacenter Management. Silvio is a speaker and author, and collaborates side-by-side with some of the most important IT companies including Microsoft, Veeam, Parallels, and 5nine to provide technical sessions. Follow him on Twitter @s_net.

Azure VM: Log in with RDP using Azure AD
George Chrysovalantis Grammatikos is based in Greece and is working for Tisski ltd. as an Azure Cloud Architect. He has more than 10 years’ experience in different technologies like BI & SQL Server Professional level solutions, Azure technologies, networking, security etc. He writes technical blogs for his blog “cloudopszone.com“, Wiki TechNet articles and also participates in discussions on TechNet and other technical blogs. Follow him on Twitter @gxgrammatikos.
Chris Hoard is a Microsoft Certified Trainer Regional Lead (MCT RL), Educator (MCEd) and Teams MVP. With over 10 years of cloud computing experience, he is currently building an education practice for Vuzion (Tier 2 UK CSP). His focus areas are Microsoft Teams, Microsoft 365 and entry-level Azure. Follow Chris on Twitter at @Microsoft365Pro and check out his blog here.

This article is contributed. See the original author and article here.

This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
The Advanced eDiscovery (Aed) section of this blog series is aimed at legal and HR officers who need to understand how to perform a basic investigation.
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through the use of Advanced eDiscovery.
It is presumed that you already data to search inside your tenant.
We will only step through a basic eDiscovery case (see the Use Case section).
This document does not cover any other aspect of Microsoft E5 Compliance, including:
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
It is also presumed you are using an existing Information Types (SIT) or a SIT you have created for your testing.
There are many use cases for Advanced eDiscovery. For the sake of simplicity, we will use the following: Your organization has a Human Resources investigation against a specific user.
If you have performed Part 1 of this blog series (creating a Sensitive Information Type), then you have everything you need. If you have not done that part of the blog, you will need to populate your test environment with test data for the steps to follow.
a. Note – the more you put in the description, the better for reporting later on. So, if you have received an email from HR, Legal, outside council, etc., you can cut and paste that information into the Case Description.
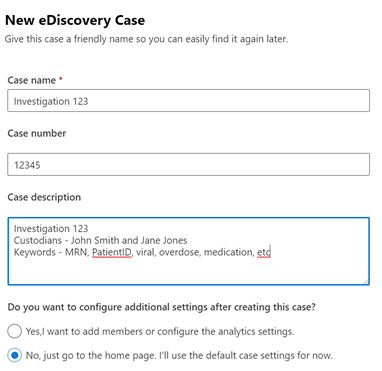
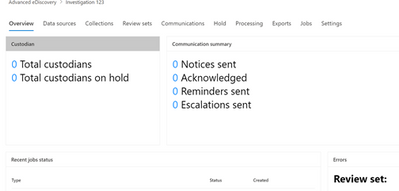
In this section, we will walk through the steps and flow to run a basic eDiscovery case:
There are 2 ways to indicate what data sources will be searched, custodian or location.
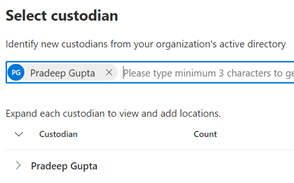
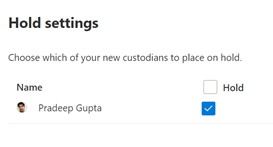
a . Note #1 – Any data location associated with that user will have a number 1 associated with it. If there is no number associated with the data location, then, the user is not determined to have any data in that location. Automatic Hold will be placed on locations where the user has data, per the 2nd step of the wizard.
b. Note #2 – When you edit a custodian, you can change or clear the setting in this screen.
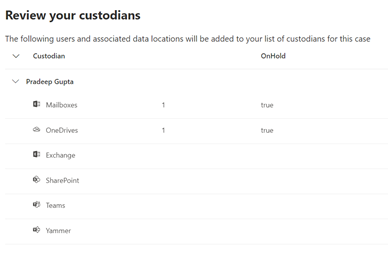
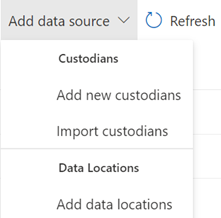
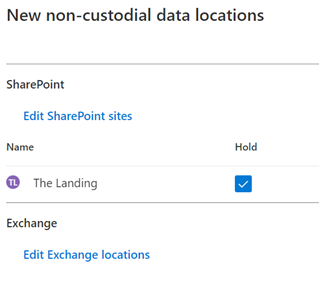
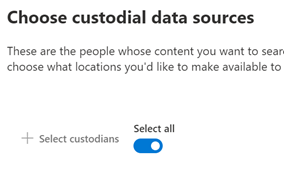
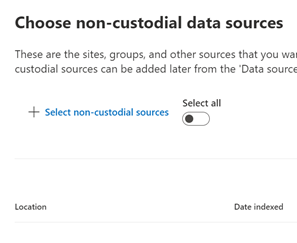
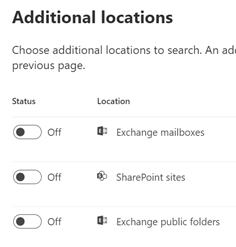
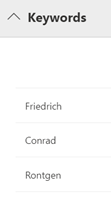
a. Note – A common initial search is to search a user or set of users and a date range. Then run a secondary search against a secondary search on a narrower data range, keywords, a subset of users, etc. In Advanced eDiscovery, we will do those sorts of searches in the Review Sets tab which is next.
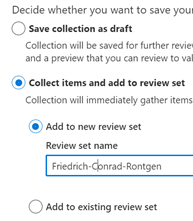
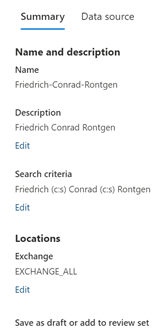
10. Next is Save Draft or Collection. Here you have the option to save this collection as a draft (meaning the data set is not officially placed on hold) or you can collect items into a review set. We will choose the latter (Collect items and add to review set), and I will add it to a new Review set.
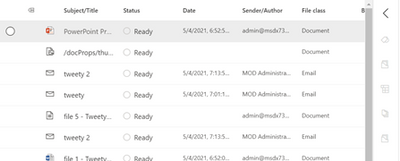
2. Let us take a tour of this interface. A ribbon across the top will show several options. Let us take a tour of this interface
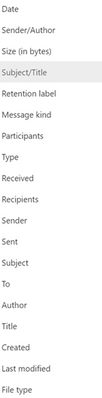
a. The first ribbon across the top will show several options to narrow your results by Keyword, Date, Sender/Author, Subject/Title, and/or Tags
b. The second ribbon allows for actions against the data in the Review Set: Overview (Summary), Analytics, Actions (download, report, redaction, etc), Tags (legal), and Manage (the collected data).
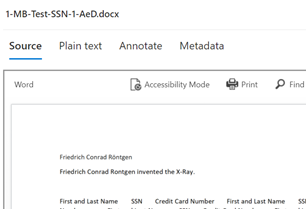
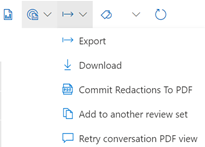
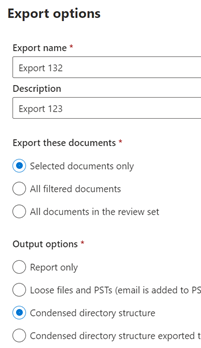
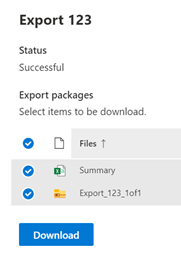
Note: This solution is a sample and may be used with Microsoft Compliance tools for dissemination of reference information only. This solution is not intended or made available for use as a replacement for professional and individualized technical advice from Microsoft or a Microsoft certified partner when it comes to the implementation of a compliance and/or advanced eDiscovery solution and no license or right is granted by Microsoft to use this solution for such purposes. This solution is not designed or intended to be a substitute for professional technical advice from Microsoft or a Microsoft certified partner when it comes to the design or implementation of a compliance and/or advanced eDiscovery solution and should not be used as such. Customer bears the sole risk and responsibility for any use. Microsoft does not warrant that the solution or any materials provided in connection therewith will be sufficient for any business purposes or meet the business requirements of any person or organization.
This article is contributed. See the original author and article here.
The Internet Systems Consortium (ISC) has released a security advisory that addresses a vulnerability affecting multiple versions of the ISC Berkeley Internet Name Domain (BIND). A remote attacker could exploit this vulnerability to cause a denial-of-service condition.
CISA encourages users and administrators to review ISC advisory CVE-2021-25218 and apply the necessary updates or workarounds.
Recent Comments