by Contributed | Mar 9, 2022 | Technology
This article is contributed. See the original author and article here.
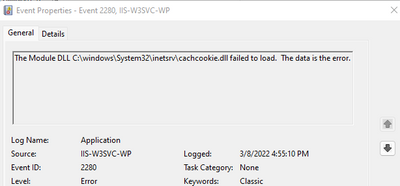
Recently I had a case were several servers had the dlls loaded in IIS that resembled names that sounded like IIS modules but were proven to be nonstandard modules. cachcookie.dll and anon_auth.dll were detected by the customer as malicious and thus removed by their antivirus software.
The problem is if they are deleted without removing the references in IIS when it tries to start the W3WP.exe, it will fail because module not found.

Here is an example of how to then remove the module reference using PowerShell.
Remove-WebConfigurationProperty -pspath ‘MACHINE/WEBROOT/APPHOST’ -filter “system.webServer/globalModules” -name “.” -AtElement @{name=’CookieCacheModule’}
Remove-WebConfigurationProperty -pspath ‘MACHINE/WEBROOT/APPHOST’ -filter “system.webServer/modules” -name “.” -AtElement @{name=’CookieCacheModule’}
With these two along with stopping/starting IIS and checking of the presence of the file we were able to streamline the process of fixing the issue.
Within the example you may change the “name=’CookieCacheModule'” to match the module you are targeting for removal.
Once removed the W3WP.EXE was started and begin to process requests as expected.
by Scott Muniz | Mar 9, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA, the Federal Bureau of Investigation (FBI), the National Security Agency (NSA), and the United States Secret Service (USSS) have re-released an advisory on Conti ransomware. Conti cyber threat actors remain active and reported Conti ransomware attacks against U.S. and international organizations have risen to more than 1,000.
CISA, the FBI, NSA, and the USSS encourage organizations to review AA21-265A: Conti Ransomware, which includes new indicators of compromise, for more information. See Shields Up and StopRansomware.gov for ways to respond against disruptive cyber activity.
by Scott Muniz | Mar 8, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Adobe has released security updates to address vulnerabilities in multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the following Adobe Security Bulletins and apply the necessary updates.
by Scott Muniz | Mar 8, 2022 | Security, Technology
This article is contributed. See the original author and article here.
SAP has released security updates to address vulnerabilities affecting multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the SAP Security Notes for March 2022 and apply the necessary updates.

by Scott Muniz | Mar 8, 2022 | Security, Technology
This article is contributed. See the original author and article here.

Official websites use .gov
A .gov website belongs to an official government organization in the United States.

Secure .gov websites use HTTPS
A
lock ( )
) or
https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.


Recent Comments