This article is contributed. See the original author and article here.
Azure Security Center monitors the security posture of your Azure resources. Today, organizations are extending their hybrid footprint and using additional public clouds. Security Center allows you to protect non-Azure resources located on-premises or on other cloud providers, from virtual machines, Kubernetes services and SQL resources.
To do so, those resources need to be connected to Azure by leveraging Azure Arc service – meaning that you can now manage and operate all your existing IT resources consistently and at-scale, wherever they reside, from Azure. You can also run Azure services anywhere, on-premises or in other public clouds, and take advantage of cloud benefits everywhere, such as scalability, fast deployment, and always up-to-date cloud innovation. Moreover, Azure Arc allows you to manage these resources like any other first citizen resource in Azure and benefit from additional capabilities, such as: non-Azure virtual machines connected to Azure Arc can benefit from capabilities such as patch management, RBAC roles, extension platform, tags and more.
Using Security Center and Azure Arc, you can also secure the 3 core scenarios which are offered today. In this blog post we will focus on the first one which is Azure Arc enabled servers.
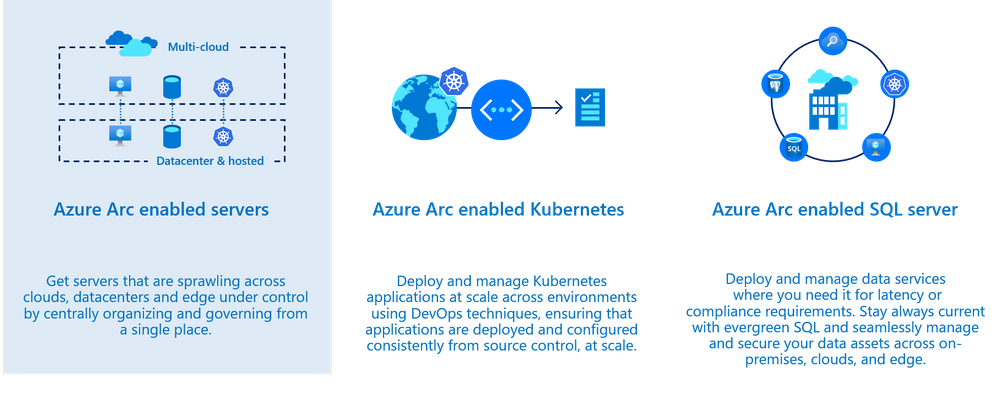
Onboarding non-Azure machines into Azure Arc provide you the ability to:
- Deploy virtual machine extension (such as Log Analytics agent, vulnerability assessment scanner, custom script extension and more)
- Enable guest configuration policies (Azure Policy)
- Use Security Center to improve the security posture such as misconfigured settings, missing system updates and more.
- Use Azure Defender for server capabilities such security alerts, vulnerability assessment, adaptive application controls, network hardening and more.
Prepare
Onboard machines as Azure Arc connected machines by installing the Hybrid Connected Machine agent on the target machine(s); this can be done by using a script or manually. Once a machine is onboarded, you will see it as Azure resource.
Before you onboard machines, please make sure to review these tasks:
- Make sure to review the supported operating system version as found here: Overview of the Connected Machine agent – Azure Arc | Microsoft Docs. If you still want to onboard a non-Azure machine but the target machine runs an OS version which is not supported by the agent yet, you can still onboard it by installing the Log Analytics agent directly on a machine.
- Ensure the target machines can communicate over the internet with the required URLs for the agent through a firewall or proxy server – proxy settings are set on the OS level.
All URLs used for communication are outbound and secured over TCP port 443 and can be found here.
Onboard
There are multiple ways to deploy the agent on a target machine as provided here: Connect hybrid machines to Azure from the Azure portal – Azure Arc | Microsoft Docs.
During the onboarding, you will be asked to onboard the resource to a subscription and a resource group you selected a subscription where Azure Defender for Servers plan is enabled.
To do so, navigate to Security Center Pricing and Settings page, and in the Servers row, click ON as shown the example below:

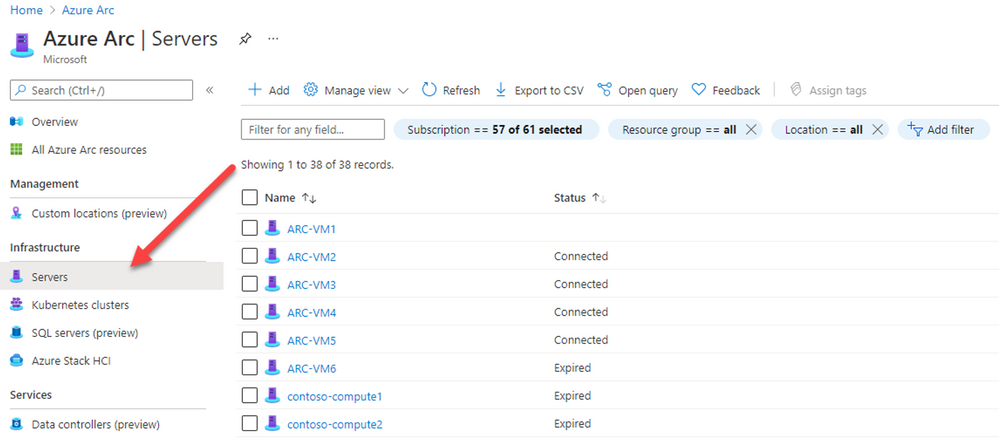
Once the machine is successfully onboarded, you will be able to see it listed on the Azure Arc blade.
In the Azure portal, search for Azure Arc service, then select Servers to see all the onboarded servers and their status, as shown in the example below:
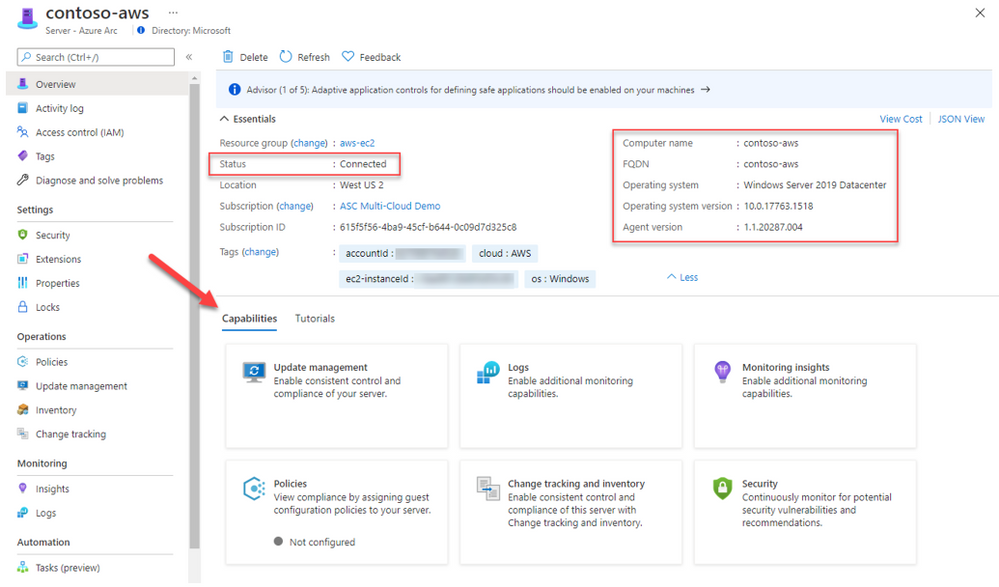
Selecting one of the onboarded machines, opens the resource blade. Here you can see the connectivity status, OS details and additional metadata.
Since it’s an ARM resource, you can assign tags, manage permissions using Azure RBAC and use additional capabilities such as policies, change tracking and inventory, patch management and security.
Secure
Projecting resources using Arc is a necessary step to ensure your machines are protected by Security Center. Like an Azure VM, you will need to deploy the Log Analytics agent on the target machine. To do so, you can use dedicated recommendations on Security Center recommendation list to deploy the Log Analytics agent; one for Azure Arc machines based on Linux and for Windows.
These recommendations offer you the Quick Fix approach to remediate it with a single click to trigger an installation of the Log Analytics agent.
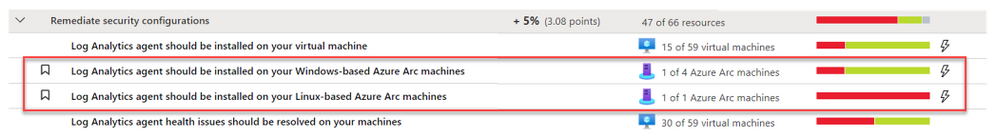
The agent is being deployed using the VM extension platform which is one of the advantages of using Arc. Once the Log analytics agent is installed and connected to a workspace used by Security Center, your machine will be ready to use and benefit of the variety of features which are available as part of the Azure Defender for Servers plan.
On Security Center’s asset inventory, you can filter Arc resources by using the filters located on the upper section, for example: select “servers – azure arc”. Unlike Azure VMs, Arc connected machines are presented in purple as you can see below.
For each resource you can see the agent monitoring alongside with the current security recommendations:
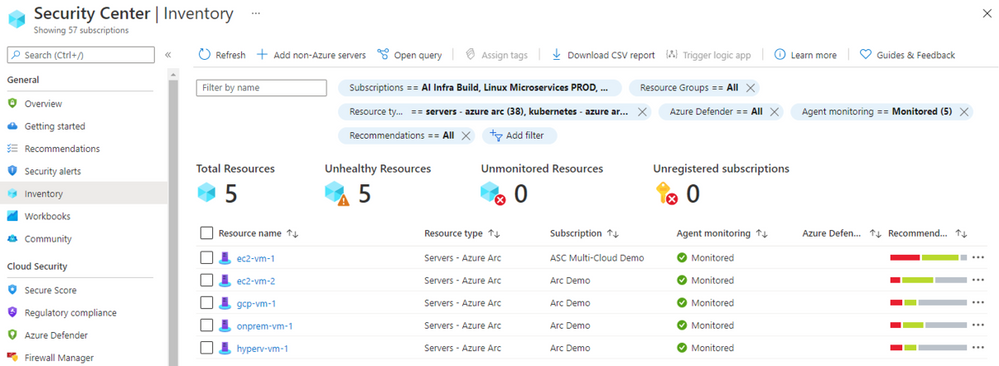
You can distinguish between the different resource by the icon:

The security alert below was triggered by Azure Defender from a virtual machine onboarded to Azure Arc and located on other cloud vendor:

Deploying our integrated vulnerability assessment solution on non-Azure machine is included with the Azure Defender for servers plan and provide you a visibility for all vulnerabilities found on the target resource including the remediation steps:
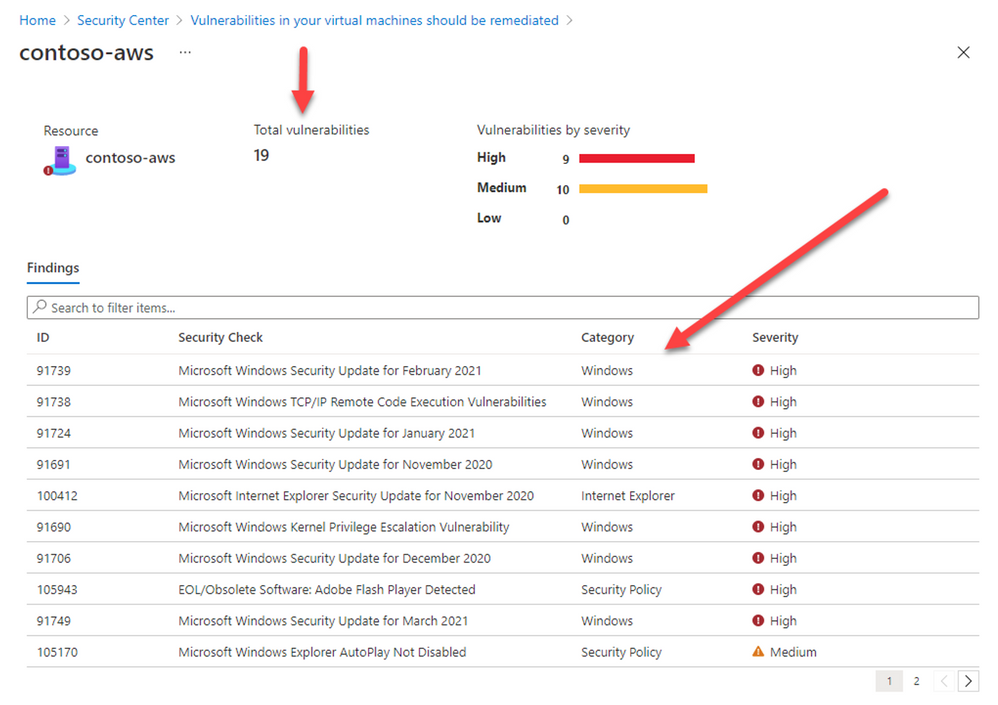
Hope you enjoyed learning on how Security Center and Azure Arc can protect your non-Azure resources located anywhere ![]()
Reviewers:
@Yuri Diogenes, Principal Program Manager, ASC CxE
Future Kortor, Program Manager, ASC CxE
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments