This article is contributed. See the original author and article here.
Before we start, please not that if you want to see a table of contents for all the sections of this blog and their various Purview topics, you can locate the in the following link:
Microsoft Purview- Paint By Numbers Series (Part 0) – Overview – Microsoft Tech Community
Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Information Protection section of this blog series is aimed at Security and Compliance officers who need to properly label data, encrypt it where needed.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through.
We will be covering the recommendation of labels for new files and emails based on the Sensitive Information Type within those files and emails.
It is presumed that you already have a Sensitive Information Type that you want to use in your Information Protection policy. For the purposes of this document, I will be using a previously created Data Classification called “Recommended_Label_Contoso_medicine”. The keyword I am tracking within that data classifier is “Contoso_medicine”. I am doing this to avoid labeling any files by accident by using an out-of-the-box classifier. For information on how you create your own data classifier, refer back to “Part 1 – Sensitivity Information Types” of this blog series.
This document is only meant to be an introduction to the topic of multiple Sensitivity labels. Always refer back to official Microsoft documentation or your Microsoft account team for the latest information.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Purview, including:
- Data Classification
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Data Lifecycle Management (retention and disposal)
- Records Management (retention and disposal)
- eDiscovery
- Insider Risk Management (IRM)
- Priva
- Advanced Audit
- Microsoft Cloud App Security (MCAS)
- Information Barriers
- Communications Compliance
- Licensing
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
For details on licensing (ie. which components and functions of Purview are in E3 vs E5) you will need to contact your Microsoft Security Specialist, Account Manager, or certified partner.
We will not be covering the auto-labeling of data at rest. That will be covered in another blog post and those auto-labeling policies should not be done until after you have locked down your Sensitivity labeling of all “net new” data.
Overview of Document
- Create a recommended Sensitivity Label
- Create a recommended Sensitivity labeling policy
- Verify that the user is prompted to apply the specific Sensitivity Label to a new file
- Verify that the user is prompted to apply the specific Sensitivity Label to a new email
Use Case
- The prompting of users to apply a Sensitivity Label when sensitive data is detected within a new file or email.
Definitions
- Sensitivity Label – a metadata tag
- Publish Label – making the metadata tag available to your tenant
- Policy – The monitoring and applying of Sensitivity labels through the Microsoft tenant
Notes
- Types of labels:
- Automatic labels are applied to data at rest in Exchange mailboxes, SharePoint/Teams sites and users’ OneDrives.
- Default labels are applied to data upon creation (and based on what is in the file/email).
- Recommended labels do not label data, but appear when a specific piece of Sensitive Information Type (ex. Contoso_Medicine) are added to a file/email. It is up to the user to apply or not apply the recommended label.
Pre-requisites
- You have read Parts 0, 1 and 2 of this blog series
- You have a Sensitive Information Type (SIT) that will be tied to this automatic label.
Part 1 – Create a Recommended Sensitivity label
We will first set up our recommended label.
- Give the label a name and description (and color marker, if you wish). Then click Next.
- For the Scope, select Items and be sure that Files and Emails are selected. Then click Next.
- Under the Items section of the wizard, select Apply or remove encryption and Apply content marking, then click Next.
- We now arrive at Encryption. Click Configure encryption settings.
- Assign Permissions now or let users decide? and chose Let users assign permissions when they apply the label.
- For the purpose of this blog, under In Outlook, enforce one of the following restrictions -> Do Not Forward.
- We want this label to be applied to MS Office related workloads. So, select In Word, Powerpoint, and Excel, prompt users to specify permissions.
- Click for Apply content watermarking, I like to use the header option as it is the easiest because it is at the top of each electronic page. I will be using this watermark – “Contoso Medicine (Blog Recommended Label)”.
- Next, we will Enable auto-labeling for files and emails.
- At the top of this page, for the Content contains, we will select the SIT that we created previously. In my case, I am using the “Recommended_Label_Contoso_medicine”. The keyword I am tracking within that data classifier is “Contoso_medicine”.
- At the bottom of this page, for the When content matches these conditions select Recommend that the users apply the label.
- Note – this is the proverbial switch that needs to be flipped for a label to enable Recommend vs. Automatic vs Default labels.
- We also want to provide an explanation in Word, Excel, etc. for the users. So in the field Display this message to users when the label is applied, type the message you want your user to see when the label is recommended. Then click Next.
- On the protection settings for Groups and Sites, we will not be enabling anything as they are not applicable for this label and policy. Accept the defaults and click Next.
- On the schematized data assets, we will leave this at the default of Off. Click Next.
- Review your label and click Create Label.
- Accept the defaults and then click Done and then Create Policy and then Close.
- You are now ready to publish your policy.
Part 2 – Publish your Recommended Sensitivity label
We will now publish your label to your tenant.
- On the left click on Information protection -> Label policies.
- Click Publish label to start the publication wizard.
- On the first step of the wizard, click Choose sensitivity labels to publish.
- Select your recommended above label and click Add.
- Note – you can publish (or republish) 1, many or all your labels in a Publish label wizard.
- Click Next.
- In the next step of the wizard, you can assign a specific administrative team to manage this policy. We will not be doing that in this blog. Click Next.
- Next, you can decide who will see the published label. I will be using the default of all Users and groups, but I recommend you only use your own test user accounts here to limit the who will be seeing this label.
- Under Policy Settings, you can leave all of these boxes blank. I will leave the first 3 boxes blankc and enter a URL into the last box (Provide users with a link to a customer help page). When you are ready, click Next.
- On Default settings for documents, we will not be selecting any Default labels. Accept the default and click Next.
- On Default settings for emails, leave things as the default of Same as docuemtn. Click Next.
- On Default settings for meetings and calendar events, leave things as the default of None. Click Next.
- On Default settings for Power BI content, leave things as the default of None. Click Next.
- Now give your policy a name and description and click Next.
- Tk Review your settings. When you are satisfied, click Submit and Done.
- You are not ready to start the testing phase of this blog.
Note – it can take 24-48 hours for labels and policies to replicated within a tenant.
Part 3 – Test Recommended label on new file
Before we start our file and email tests, remember that labels and policies can take a while to replicate throughout your tenant. One hour is usually a good amount of time to wait, but it might be quicker or slow to populate based on several variables in your tenant we will not cover at this time.
- Open Word, Excel or PowerPoint
- Create a New File.
- Type in the Sensitive Information Type that you have associated with your recommended Sensitivity label. I am using the compound word “contoso_medicine”.
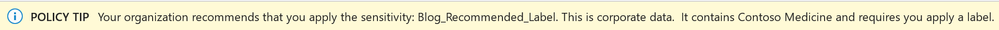
- When you do, you will see a Policy Tip bar appear at the top of your document. Here is an example.
- Here is a magnification of the left side above.
- Here is a magnification of the left side above.
- This is the end of the file testing.
Part 4 – Test Recommended label on new email
We will now test this recommended label against a newly created email.
- Open Outlook.
- Create a New Email.
- Type in the Sensitive Information Type that you have associated with your recommended Sensitivity label. I am using the compound word “contoso_medicine”.
- When you do, you will see a Policy Tip bar appear at the top of your document. Here is an example.
- Here is a magnification of the left side above.
- Here is a magnification of the left side above.
- This is the end of the email testing.
You have now reached the end of this blog entry.
Appendix and Links
Note: This solution is a sample and may be used with Microsoft Compliance tools for dissemination of reference information only. This solution is not intended or made available for use as a replacement for professional and individualized technical advice from Microsoft or a Microsoft certified partner when it comes to the implementation of a compliance and/or advanced eDiscovery solution and no license or right is granted by Microsoft to use this solution for such purposes. This solution is not designed or intended to be a substitute for professional technical advice from Microsoft or a Microsoft certified partner when it comes to the design or implementation of a compliance and/or advanced eDiscovery solution and should not be used as such. Customer bears the sole risk and responsibility for any use. Microsoft does not warrant that the solution or any materials provided in connection therewith will be sufficient for any business purposes or meet the business requirements of any person or organization.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.






Recent Comments