by Contributed | Nov 28, 2022 | Technology
This article is contributed. See the original author and article here.
Microsoft Teams has been in extensive use for collaboration features such as IM, Teams meetings, 1:1 or group calls, files collaboration, etc., and has been explored by all organizations without any additional financial costs with existing Microsoft 365 licenses. This has been a boon to organizations for increasing productivity. However, one of the added functionalities of Microsoft Teams, which comes in handy, is to replace traditional telephone systems by enabling the Teams integrated Cloud telephone system that includes Calling Plans and PSTN Audio conferencing options for dial out and dial in capabilities—all without any additional on-premises PSTN infrastructure set up.
The Catch with Microsoft Teams Audio Conferencing Features
Availability across a given tenant is based on the initial data residence location (or organization billing address), and it must align with Microsoft 365 calling and conferencing features available for the given region. For Example, any M365 tenant initially set up with a billing address in India or China is devoid of Audio-conferencing Capabilities by design.
For a complete list of the latest M365 Audio Conferencing and Calling Plans region-wide availability, please Click here. This link is handy for all architect professionals while setting up new tenants to decide on an initial data residence location and to check on available MS Teams audio conferencing features. Owing to taxation regulations and compliance, the M365 tenant’s initial or billing location cannot be updated later, and the given tenant is devoid of the required features.
Microsoft Teams PSTN/calling and conferencing features can be categorized as follows:
- Dial out to domestic/telephone numbers for users enabled with the respective calling plans.
- Dial out from an Audio-Conferencing meeting to add someone else from anywhere in the world.
- Dial out from an Audio-Conferencing meeting to your mobile/office phone with the user logged into Microsoft Teams app.
- Dial in (Toll/Toll Free Numbers) and dial out capabilities to MS Teams meetings.
- Dial into a meeting using the service numbers or Toll-Free numbers enabled for given tenant.
Audio conferencing features for given users are based upon enablement of the given Audio-Conferencing licenses: as a part of Microsoft Business Voice, Microsoft Teams Phone standard, MS Teams phone with Calling, E5 license, or as an M365 Add-on license.
For leveraging and billing purposes of calling features across MS Teams, Microsoft has categorized all countries across the globe into two zones which is Zone A and another zone for rest of the countries not included in the aforementioned. For example, Albania, Argentina, Cayman Islands, Dubai, Egypt, Zimbabwe, Israel and many more. To access the update list of M365 Zone A countries please click here.
Microsoft Teams Audio conferencing licenses can be categorized in to 2 types:
- Pay per minute.
- Standard subscription per user
Audio conferencing pay per minute, which is only available as part of volume licensing, allows organizations to pay for all the Audio-Conferencing usage on a per-minute basis. All the inbound and outbound calls are charged based upon the standard pay per minute charges.
On the other end, Audio conferencing standard subscription license enables free dial in capabilities for toll numbers and 60 minutes per user a month for dial out to non-premium numbers in ANY of the Zone A countries. Thus, this license does not enable licensed users to place calls to any other non-Zone A countries within the pooled minutes. Those calls are separate, and any charges are counted against communication credits.
Minutes are pooled against an office 365 subscription are calculated at tenant-level and can be leveraged and shared by all the licensed users in the tenant. If a customer has purchased subscriptions for 500 Audio Conferencing licenses—with 400 users in the United States, 50 users in Australia, and 50 users in Dubai, then all 500 users share a pool of Audio-conferencing minutes. This is calculated as 500 users x 60 min = 30,000 minutes for conferencing dial-out minutes per calendar month. This may be used to place outbound calls to non-premium numbers in any of the Zone A countries. The minutes pooled for an Audio-Conferencing tenant is always based upon the licenses assigned to a user rather than total licenses available across the given tenant.
Call Charges are Calculated Against the Call Destination
The organizer’s country of residence, and the participant initiating the call, do not change the calling charges. Furthermore, calls placed between Zone A: non-Zone A and between non-Zone A: non-Zone A, they are always charged on a per minute basis against the Communication Credits rather than a minute pool for the tenant’s Audio-Conferencing.
To ease the burden of carrier calling charges and facilitate users struggling with internet connectivity, MS Teams Toll free conference number bridges the cost to the organization rather than the caller. All Toll-free conference calls are billed on a per minute basis in tenant Communication Credits and are never calculated against Audio-Conferencing minutes.
Communications Credits: Convenience to Pay for Audio-Conferencing and Calling Plan minutes
In laymen terms, these are a prepaid top-up amount across the tenant to be used for calls not included in Audio conferencing options.
Communication Credits Help Organizations Ensure Users Are Never Caught Without the Ability to:
- Add toll-free numbers to Audio-Conferencing meetings, auto attendants, call queues. (Toll Free Numbers are charged on a minute basis.)
- Dial out from an Audio-Conference meeting to add someone else from anywhere in the world or add your mobile or office phone in non-Zone A countries.
- Dial any international phone number when enabled only with Domestic Calling Plan subscriptions.
- Dial international phone numbers beyond what is included in a Domestic and International Calling Plan subscription.
- Dial out and pay per minute once the monthly minute allotment is exhausted.
- Dial out and pay per minute for all outgoing calls if you have a Pay-As-You-Go Calling Plan.
Communication Credits are specifically utilized for the below scenarios.
- Tenants enabled with Audio-Conferencing pay-per-minute.
- Enabling Toll-free Bridges across a given tenant, billed per minute.
- Dial-out calls exceeding Audio-Conferencing minutes per calendar month are billed per minute using Communications Credits at published rates to that destination.
- Dial-out calls to destinations not in the Zone A countries list are billed per minute using Communications Credits at the published rates to that given destination.
For users to leverage the Communication Credits across given Tenant, they are required to be assigned with Communication Credit license, which grant them access to the balance. The minimum amount of Communication Credit balance can be a minimum of $50. Setting up a toll-free number across a given tenant does require a positive Communication Credit.
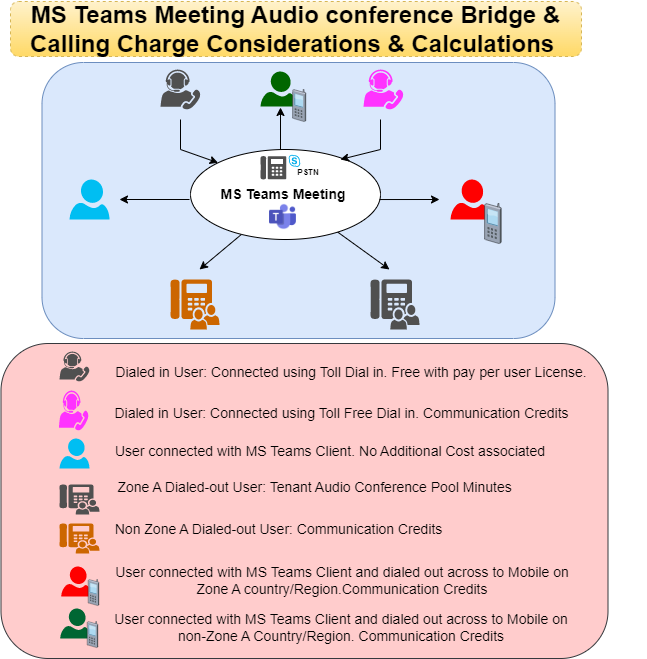
Below is a quick reference diagram to understand the various types of meeting participant types and how the MS Teams calling charges are applied.

With a subscription to pay per license, Audio-Conferencing Dial-in capabilities are considered free of cost with Toll number. Zone A dial out users are considered with Tenant pool minutes. Non-Zone A Dial out users and users with toll free dial in are charged per minute from Communication Credits.
With only Audio-Conferencing pay-per-minute licenses enabled, the dial in calls with a toll conference bridge and Zone A dial out users are charged against Communication Credits (owing to non-availability of any polled minutes). Toll free dial in users and Non-Zone A dial out users total against Communication Credits.
In conclusion, Toll Free and Calling capabilities to Non-Zone A countries can come with a hefty financial consideration; hence, proper planning and stringent controls in place are required for tracking MS Teams calling budgets to ensure a seamless experience for the required users.
Bio:
Sanjay Kumar Pendyala has a decade plus of experience across architecting, operations, and maintenance of Microsoft collaboration and cloud Technologies. Currently serving as an Infrastructure Architect with Cognizant Technology Solutions, Sanjay Kumar has a technical expertise across architecting and administration of SharePoint On-premises, Azure IAAS/PAAS, Microsoft 365 (Exchange Online, SharePoint Online, Teams, Azure AD, Yammer, Power Automate platform, Graph API automation), and he has been working for a few fortune 500 clients.
by Scott Muniz | Nov 28, 2022 | Security, Technology
This article is contributed. See the original author and article here.
| airbnb — optica |
A remote code execution (RCE) vulnerability in Optica allows unauthenticated attackers to execute arbitrary code via specially crafted JSON payloads. Specially crafted JSON payloads may lead to RCE (remote code execution) on the attacked system running Optica. The vulnerability was patched in v. 0.10.2, where the call to the function `oj.load` was changed to `oj.safe_load`. |
2022-11-23 |
not yet calculated |
CVE-2022-41875
CONFIRM
MISC
MISC |
| amasty — amasty_blog |
Amasty Blog 2.10.3 is vulnerable to Cross Site Scripting (XSS) via leave comment functionality. |
2022-11-23 |
not yet calculated |
CVE-2022-35500
MISC
MISC |
| amasty — amasty_blog_pro |
Stored Cross-site Scripting (XSS) exists in the Amasty Blog Pro 2.10.3 and 2.10.4 plugin for Magento 2 because of the duplicate post function. |
2022-11-23 |
not yet calculated |
CVE-2022-35501
MISC
MISC |
|
apache — dolphinscheduler
|
When using tasks to read config files, there is a risk of database password disclosure. We recommend you upgrade to version 2.0.6 or higher. |
2022-11-24 |
not yet calculated |
CVE-2022-26885
MISC |
| apache — multiple_products |
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability in Apache Airflow Pig Provider, Apache Airflow allows an attacker to control commands executed in the task execution context, without write access to DAG files. This issue affects Pig Provider versions prior to 4.0.0. It also impacts any Apache Airflow versions prior to 2.3.0 in case Pig Provider is installed (Pig Provider 4.0.0 can only be installed for Airflow 2.3.0+). Note that you need to manually install the Pig Provider version 4.0.0 in order to get rid of the vulnerability on top of Airflow 2.3.0+ version. |
2022-11-22 |
not yet calculated |
CVE-2022-40189
MISC
MISC |
| apache — multiple_products |
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability in Apache Airflow Hive Provider, Apache Airflow allows an attacker to execute arbtrary commands in the task execution context, without write access to DAG files. This issue affects Hive Provider versions prior to 4.1.0. It also impacts any Apache Airflow versions prior to 2.3.0 in case HIve Provider is installed (Hive Provider 4.1.0 can only be installed for Airflow 2.3.0+). Note that you need to manually install the HIve Provider version 4.1.0 in order to get rid of the vulnerability on top of Airflow 2.3.0+ version that has lower version of the Hive Provider installed). |
2022-11-22 |
not yet calculated |
CVE-2022-41131
MISC
MISC |
apache — multiple_products
|
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability in Apache Airflow Spark Provider, Apache Airflow allows an attacker to read arbtrary files in the task execution context, without write access to DAG files. This issue affects Spark Provider versions prior to 4.0.0. It also impacts any Apache Airflow versions prior to 2.3.0 in case Spark Provider is installed (Spark Provider 4.0.0 can only be installed for Airflow 2.3.0+). Note that you need to manually install the Spark Provider version 4.0.0 in order to get rid of the vulnerability on top of Airflow 2.3.0+ version that has lower version of the Spark Provider installed). |
2022-11-22 |
not yet calculated |
CVE-2022-40954
MISC
MISC |
|
apache –airflow_pinot_provider
|
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability in Apache Airflow Pinot Provider, Apache Airflow allows an attacker to control commands executed in the task execution context, without write access to DAG files. This issue affects Apache Airflow Pinot Provider versions prior to 4.0.0. It also impacts any Apache Airflow versions prior to 2.3.0 in case Apache Airflow Pinot Provider is installed (Apache Airflow Pinot Provider 4.0.0 can only be installed for Airflow 2.3.0+). Note that you need to manually install the Pinot Provider version 4.0.0 in order to get rid of the vulnerability on top of Airflow 2.3.0+ version. |
2022-11-22 |
not yet calculated |
CVE-2022-38649
MISC
MISC |
| artifex — mujs |
A logical issue in O_getOwnPropertyDescriptor() in Artifex MuJS 1.0.0 through 1.3.x before 1.3.2 allows an attacker to achieve Remote Code Execution through memory corruption, via the loading of a crafted JavaScript file. |
2022-11-23 |
not yet calculated |
CVE-2022-44789
MISC
MISC
CONFIRM |
| asith-eranga — isic_tour |
File upload vulnerability in asith-eranga ISIC tour booking through version published on Feb 13th 2018, allows attackers to upload arbitrary files via /system/application/libs/js/tinymce/plugins/filemanager/dialog.php and /system/application/libs/js/tinymce/plugins/filemanager/upload.php. |
2022-11-22 |
not yet calculated |
CVE-2022-30529
MISC
MISC |
| automotive_shop_management_system — automotive_shop_management_system |
Automotive Shop Management System v1.0 is vulnerable to Delete any file via /asms/classes/Master.php?f=delete_img. |
2022-11-23 |
not yet calculated |
CVE-2022-44280
MISC |
| automotive_shop_management_system — automotive_shop_management_system |
Automotive Shop Management System v1.0 was discovered to contain a SQL injection vulnerability via the id parameter at /asms/products/view_product.php. |
2022-11-25 |
not yet calculated |
CVE-2022-44858
MISC |
| automotive_shop_management_system — automotive_shop_management_system |
Automotive Shop Management System v1.0 was discovered to contain a SQL injection vulnerability via the id parameter at /asms/admin/products/manage_product.php. |
2022-11-25 |
not yet calculated |
CVE-2022-44859
MISC |
| automotive_shop_management_system — automotive_shop_management_system |
Automotive Shop Management System v1.0 was discovered to contain a SQL injection vulnerability via the id parameter at /admin/transactions/update_status.php. |
2022-11-25 |
not yet calculated |
CVE-2022-44860
MISC |
| backdrop_cms — backdrop_cms |
Backdrop CMS version 1.23.0 was discovered to contain a stored cross-site scripting (XSS) vulnerability via the Page content. |
2022-11-23 |
not yet calculated |
CVE-2022-42095
MISC
MISC
MISC
MISC
MISC |
| badaso — badaso |
Badaso version 2.6.3 allows an unauthenticated remote attacker to execute arbitrary code remotely on the server. This is possible because the application does not properly validate the data uploaded by users. |
2022-11-25 |
not yet calculated |
CVE-2022-41705
MISC
MISC |
|
basercms — basercms
|
BaserCMS is a content management system with a japanese language focus. In affected versions there is a cross-site scripting vulnerability on the management system of baserCMS. This is a vulnerability that needs to be addressed when the management system is used by an unspecified number of users. Users of baserCMS are advised to upgrade as soon as possible. There are no known workarounds for this vulnerability. |
2022-11-25 |
not yet calculated |
CVE-2022-39325
CONFIRM
MISC
MISC |
| bat-c2 — bat-c2 |
The web server of Hirschmann BAT-C2 before 09.13.01.00R04 allows authenticated command injection. This allows an authenticated attacker to pass commands to the shell of the system because the dir parameter of the FsCreateDir Ajax function is not sufficiently sanitized. The vendor’s ID is BSECV-2022-21. |
2022-11-25 |
not yet calculated |
CVE-2022-40282
MISC |
| boa — boa |
Boa 0.94.14rc21 is vulnerable to SQL Injection via username. |
2022-11-23 |
not yet calculated |
CVE-2022-44117
MISC |
| book_store_management_system — book_store_management_system |
Book Store Management System v1.0 was discovered to contain a cross-site scripting (XSS) vulnerability in /bsms_ci/index.php/book. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the book_title parameter. |
2022-11-25 |
not yet calculated |
CVE-2022-45225
MISC |
| bouncy_castle — bc-fja |
An issue was discovered in the FIPS Java API of Bouncy Castle BC-FJA before 1.0.2.4. Changes to the JVM garbage collector in Java 13 and later trigger an issue in the BC-FJA FIPS modules where it is possible for temporary keys used by the module to be zeroed out while still in use by the module, resulting in errors or potential information loss. NOTE: FIPS compliant users are unaffected because the FIPS certification is only for Java 7, 8, and 11. |
2022-11-21 |
not yet calculated |
CVE-2022-45146
MISC
CONFIRM |
|
churchinfo — churchinfo
|
CartView.php in ChurchInfo 1.3.0 allows attackers to achieve remote code execution through insecure uploads. This requires authenticated access tot he ChurchInfo application. Once authenticated, a user can add names to their cart, and compose an email. Uploading an attachment for the email stores the attachment on the site in the /tmp_attach/ folder where it can be accessed with a GET request. There are no limitations on files that can be attached, allowing for malicious PHP code to be uploaded and interpreted by the server. |
2022-11-23 |
not yet calculated |
CVE-2021-43258
MISC
MISC
MISC |
| codeigniter — codeigniter |
An access control issue in /Admin/dashboard.php of Record Management System using CodeIgniter v1.0 allows attackers to access and modify user data. |
2022-11-23 |
not yet calculated |
CVE-2022-41446
MISC
MISC
MISC
MISC |
| dedecmdv6 — dedecmdv6 |
dedecmdv6 v6.1.9 is vulnerable to Arbitrary file deletion via file_manage_control.php. |
2022-11-23 |
not yet calculated |
CVE-2022-43196
MISC |
|
dedecmdv6 — dedecmdv6
|
dedecmdv6 v6.1.9 is vulnerable to Remote Code Execution (RCE) via file_manage_control.php. |
2022-11-23 |
not yet calculated |
CVE-2022-44118
MISC |
|
dedecmdv6 — dedecmdv6
|
dedecmdv6 6.1.9 is vulnerable to SQL Injection. via sys_sql_query.php. |
2022-11-23 |
not yet calculated |
CVE-2022-44120
MISC |
| drachtio — drachtio-server |
drachtio-server 0.8.18 has a heap-based buffer over-read via a long Request-URI in an INVITE request. |
2022-11-26 |
not yet calculated |
CVE-2022-45909
MISC |
| etms — ondiskplayeragent |
Remote code execution vulnerability due to insufficient verification of URLs, etc. in OndiskPlayerAgent. A remote attacker could exploit the vulnerability to cause remote code execution by causing an arbitrary user to download and execute malicious code. |
2022-11-25 |
not yet calculated |
CVE-2022-41156
MISC |
| eyoom — eyoom_builder |
Remote code execution vulnerability can be achieved by using cookie values as paths to a file by this builder program. A remote attacker could exploit the vulnerability to execute or inject malicious code. |
2022-11-25 |
not yet calculated |
CVE-2022-41158
MISC |
| eyoucms — eyoucms |
A cross-site scripting (XSS) vulnerability in the Url parameter in /login.php of EyouCMS v1.6.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload. |
2022-11-23 |
not yet calculated |
CVE-2022-45280
MISC |
|
f-secure — endpoint_protection
|
In F-Secure Endpoint Protection for Windows and macOS before channel with Capricorn database 2022-11-22_07, the aerdl.dll unpacker handler crashes. This can lead to a scanning engine crash, triggerable remotely by an attacker for denial of service. |
2022-11-25 |
not yet calculated |
CVE-2022-38166
MISC |
| filecloud — filecloud |
FileCloud Versions 20.2 and later allows remote attackers to potentially cause unauthorized remote code execution and access to reported API endpoints via a crafted HTTP request. |
2022-11-23 |
not yet calculated |
CVE-2022-39833
CONFIRM
MISC |
| fortiguard_labs — multiple_products |
An improper access control vulnerability [CWE-284] in FortiManager 7.2.0, 7.0.0 through 7.0.3, 6.4.0 through 6.4.7, 6.2.0 through 6.2.9, 6.0.0 through 6.0.11 and FortiAnalyzer 7.2.0, 7.0.0 through 7.0.3, 6.4.0 through 6.4.8, 6.2.0 through 6.2.10, 6.0.0 through 6.0.12 may allow a remote and authenticated admin user assigned to a specific ADOM to access other ADOMs information such as device information and dashboard information. |
2022-11-25 |
not yet calculated |
CVE-2022-38377
MISC |
| frappe — frappe |
Frappe version 14.10.0 allows an external attacker to remotely obtain arbitrary local files. This is possible because the application does not correctly validate the information injected by the user in the import_file parameter. |
2022-11-25 |
not yet calculated |
CVE-2022-41712
MISC
MISC |
| github — enterprise_server |
CRITICAL: An improper neutralization of argument delimiters in a command vulnerability was identified in GitHub Enterprise Server that enabled remote code execution. To exploit this vulnerability, an attacker would need permission to create and build GitHub Pages using GitHub Actions. This vulnerability affected only version 3.7.0 of GitHub Enterprise Server and was fixed in version 3.7.1. This vulnerability was reported via the GitHub Bug Bounty program. |
2022-11-23 |
not yet calculated |
CVE-2022-23740
MISC |
| google — chrome |
Heap buffer overflow in GPU in Google Chrome prior to 107.0.5304.121 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. (Chromium security severity: High) |
2022-11-25 |
not yet calculated |
CVE-2022-4135
MISC
MISC |
| grails — grails_spring_security_core |
Grails Spring Security Core plugin is vulnerable to privilege escalation. The vulnerability allows an attacker access to one endpoint (i.e. the targeted endpoint) using the authorization requirements of a different endpoint (i.e. the donor endpoint). In some Grails framework applications, access to the targeted endpoint will be granted based on meeting the authorization requirements of the donor endpoint, which can result in a privilege escalation attack. This vulnerability has been patched in grails-spring-security-core versions 3.3.2, 4.0.5 and 5.1.1. Impacted Applications: Grails Spring Security Core plugin versions: 1.x 2.x >=3.0.0 <3.3.2 >=4.0.0 <4.0.5 >=5.0.0 <5.1.1 We strongly suggest that all Grails framework applications using the Grails Spring Security Core plugin be updated to a patched release of the plugin. Workarounds: Users should create a subclass extending one of the following classes from the `grails.plugin.springsecurity.web.access.intercept` package, depending on their security configuration: * `AnnotationFilterInvocationDefinition` * `InterceptUrlMapFilterInvocationDefinition` * `RequestmapFilterInvocationDefinition` In each case, the subclass should override the `calculateUri` method like so: “` @Override protected String calculateUri(HttpServletRequest request) { UrlPathHelper.defaultInstance.getRequestUri(request) } “` This should be considered a temporary measure, as the patched versions of grails-spring-security-core deprecates the `calculateUri` method. Once upgraded to a patched version of the plugin, this workaround is no longer needed. The workaround is especially important for version 2.x, as no patch is available version 2.x of the GSSC plugin. |
2022-11-23 |
not yet calculated |
CVE-2022-41923
CONFIRM
MISC
MISC |
|
h2 — database_engine
|
The web-based admin console in H2 Database Engine through 2.1.214 can be started via the CLI with the argument -webAdminPassword, which allows the user to specify the password in cleartext for the web admin console. Consequently, a local user (or an attacker that has obtained local access through some means) would be able to discover the password by listing processes and their arguments. NOTE: the vendor states “This is not a vulnerability of H2 Console … Passwords should never be passed on the command line and every qualified DBA or system administrator is expected to know that.” |
2022-11-23 |
not yet calculated |
CVE-2022-45868
MISC
MISC |
|
hewlett_packard_enterprise — netbatch-plus
|
A vulnerability in NetBatch-Plus software allows unauthorized access to the application. HPE has provided a workaround and fix. Please refer to HPE Security Bulletin HPESBNS04388 for details. |
2022-11-22 |
not yet calculated |
CVE-2022-37931
MISC |
| hitachi_energy — multiple_products |
An input validation vulnerability exists in the Monitor Pro interface of MicroSCADA Pro and MicroSCADA X SYS600. An authenticated user can launch an administrator level remote code execution irrespective of the authenticated user’s role. |
2022-11-21 |
not yet calculated |
CVE-2022-3388
MISC |
| hitachi_energy — pcm600 |
A vulnerability exists in the Intelligent Electronic Device (IED) Connectivity Package (ConnPack) credential storage function in Hitachi Energy’s PCM600 product included in the versions listed below, where IEDs credentials are stored in a cleartext format in the PCM600 database. An attacker who manages to get access to the exported backup file can exploit the vulnerability and obtain credentials of the IEDs. The credentials may be used to perform unauthorized modifications such as loading incorrect configurations, reboot the IEDs or cause a denial-of-service on the IEDs. |
2022-11-22 |
not yet calculated |
CVE-2022-2513
MISC |
|
human_resource_management_system — human_resource_management_system
|
Human Resource Management System v1.0.0 was discovered to contain a cross-site scripting (XSS) vulnerability. This vulnerability is triggered via a crafted payload injected into an authentication error message. |
2022-11-25 |
not yet calculated |
CVE-2022-45218
MISC
MISC |
|
insyde — insydeh20
|
An issue was discovered in Insyde InsydeH2O with kernel 5.0 through 5.5. A stack buffer overflow leads to arbitrary code execution in the SetupUtility driver on Intel platforms. An attacker can change the values of certain UEFI variables. If the size of the second variable exceeds the size of the first, then the buffer will be overwritten. This issue affects the SetupUtility driver of InsydeH2O. |
2022-11-22 |
not yet calculated |
CVE-2022-35407
MISC
MISC |
|
insyde — insydeh2o
|
An stack buffer overflow vulnerability leads to arbitrary code execution issue was discovered in Insyde InsydeH2O with kernel 5.0 through 5.5. If the attacker modifies specific UEFI variables, it can cause a stack overflow, leading to arbitrary code execution. The specific variables are normally locked (read-only) at the OS level and therefore an attack would require direct SPI modification. If an attacker can change the values of at least two variables out of three (SecureBootEnforce, SecureBoot, RestoreBootSettings), it is possible to execute arbitrary code. |
2022-11-21 |
not yet calculated |
CVE-2022-35897
MISC
MISC |
| insyde — insydeh2o |
In libarchive 3.6.1, the software does not check for an error after calling calloc function that can return with a NULL pointer if the function fails, which leads to a resultant NULL pointer dereference. NOTE: the discoverer cites this CWE-476 remark but third parties dispute the code-execution impact: “In rare circumstances, when NULL is equivalent to the 0x0 memory address and privileged code can access it, then writing or reading memory is possible, which may lead to code execution.” |
2022-11-22 |
not yet calculated |
CVE-2022-36227
MISC
MISC |
| insyde — insydeh2o |
An issue was discovered in Insyde InsydeH2O with kernel 5.0 through 5.5. A stack buffer overflow vulnerability in the MebxConfiguration driver leads to arbitrary code execution. Control of a UEFI variable under the OS can cause this overflow when read by BIOS code. |
2022-11-23 |
not yet calculated |
CVE-2022-36337
MISC
MISC |
| ipxe — ipxe |
A vulnerability was found in iPXE. It has been declared as problematic. This vulnerability affects the function tls_new_ciphertext of the file src/net/tls.c of the component TLS. The manipulation of the argument pad_len leads to information exposure through discrepancy. The name of the patch is 186306d6199096b7a7c4b4574d4be8cdb8426729. It is recommended to apply a patch to fix this issue. VDB-214054 is the identifier assigned to this vulnerability. |
2022-11-21 |
not yet calculated |
CVE-2022-4087
MISC
MISC |
|
iterm2 — iterm2
|
iTerm2 before 3.4.18 mishandles a DECRQSS response. |
2022-11-23 |
not yet calculated |
CVE-2022-45872
MISC |
| jeecg-boot — jeecg-boot |
Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/dict/queryTableData. |
2022-11-25 |
not yet calculated |
CVE-2022-45205
MISC
MISC |
| jeecg-boot — jeecg-boot |
Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/duplicate/check. |
2022-11-25 |
not yet calculated |
CVE-2022-45206
MISC
MISC |
| jeecg-boot — jeecg-boot |
Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component updateNullByEmptyString. |
2022-11-25 |
not yet calculated |
CVE-2022-45207
MISC
MISC |
| jeecg-boot — jeecg-boot |
Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/user/putRecycleBin. |
2022-11-25 |
not yet calculated |
CVE-2022-45208
MISC
MISC |
| jeecg-boot — jeecg-boot |
Jeecg-boot v3.4.3 was discovered to contain a SQL injection vulnerability via the component /sys/user/deleteRecycleBin. |
2022-11-25 |
not yet calculated |
CVE-2022-45210
MISC
MISC |
| jizhicms — jizhicms |
An issue was discovered in JIZHI CMS 1.9.4. There is a CSRF vulnerability that can add an admin account via index, /admin.php/Admin/adminadd.html |
2022-11-23 |
not yet calculated |
CVE-2021-29334
MISC |
| jizhicms — jizhicms |
Jizhicms v2.3.3 was discovered to contain a SQL injection vulnerability via the /Member/memberedit.html component. |
2022-11-23 |
not yet calculated |
CVE-2022-44140
MISC |
| jizhicms — jizhicms |
Jizhicms v2.3.3 was discovered to contain a SQL injection vulnerability via the /index.php/admins/Fields/get_fields.html component. |
2022-11-23 |
not yet calculated |
CVE-2022-45278
MISC |
| keylime — keylime |
A vulnerability was found in keylime. This security issue happens in some circumstances, due to some improperly handled exceptions, there exists the possibility that a rogue agent could create errors on the verifier that stopped attestation attempts for that host leaving it in an attested state but not verifying that anymore. |
2022-11-22 |
not yet calculated |
CVE-2022-3500
MISC
MISC |
| knime — analytics_platform |
A directory traversal vulnerability in the ZIP archive extraction routines of KNIME Analytics Platform 3.2.0 and above can result in arbitrary files being overwritten on the user’s system. This vulnerability is also known as ‘Zip-Slip’. An attacker can create a KNIME workflow that, when being opened by a user, can overwrite arbitrary files that the user has write access to. It’s not necessary to execute the workflow, opening the workflow is sufficient. The user will notice that something is wrong because an error is being reported but only after the files have already been written. This can impact data integrity (file contents are changed) or cause errors in other software (vital files being corrupted). It can even lead to remote code execution if executable files are being replaced and subsequently executed by the user. In all cases the attacker has to know the location of files on the user’s system, though. |
2022-11-24 |
not yet calculated |
CVE-2022-44749
MISC |
|
knime — server
|
A directory traversal vulnerability in the ZIP archive extraction routines of KNIME Server since 4.3.0 can result in arbitrary files being overwritten on the server’s file system. This vulnerability is also known as ‘Zip-Slip’. An attacker can create a KNIME workflow that, when being uploaded, can overwrite arbitrary files that the operating system user running the KNIME Server process has write access to. The user must be authenticated and have permissions to upload files to KNIME Server. This can impact data integrity (file contents are changed) or cause errors in other software (vital files being corrupted). It can even lead to remote code execution if executable files are being replaced and subsequently executed by the KNIME Server process user. In all cases the attacker has to know the location of files on the server’s file system, though. Note that users that have permissions to upload workflows usually also have permissions to run them on the KNIME Server and can therefore already execute arbitrary code in the context of the KNIME Executor’s operating system user. There is no workaround to prevent this vulnerability from being exploited. Updates to fixed versions 4.13.6, 4.14.3, or 4.15.3 are advised. |
2022-11-24 |
not yet calculated |
CVE-2022-44748
MISC |
| librenms — librenms/librenms |
A user is able to enable their own account if it was disabled by an admin while the user still holds a valid session. Moreover, the username is not properly sanitized in the admin user overview. This enables an XSS attack that enables an attacker with a low privilege user to execute arbitrary JavaScript in the context of an admin’s account. |
2022-11-20 |
not yet calculated |
CVE-2022-4068
MISC
CONFIRM |
| libxml2 — libxml2 |
An issue was discovered in libxml2 before 2.10.3. When parsing a multi-gigabyte XML document with the XML_PARSE_HUGE parser option enabled, several integer counters can overflow. This results in an attempt to access an array at a negative 2GB offset, typically leading to a segmentation fault. |
2022-11-23 |
not yet calculated |
CVE-2022-40303
MISC
MISC |
| libxml2 — libxml2 |
An issue was discovered in libxml2 before 2.10.3. Certain invalid XML entity definitions can corrupt a hash table key, potentially leading to subsequent logic errors. In one case, a double-free can be provoked. |
2022-11-23 |
not yet calculated |
CVE-2022-40304
MISC
MISC
MISC |
| linux — linux_kernel |
An issue was discovered in the Linux kernel through 6.0.9. drivers/media/dvb-core/dvbdev.c has a use-after-free, related to dvb_register_device dynamically allocating fops. |
2022-11-25 |
not yet calculated |
CVE-2022-45884
MISC
MISC |
| linux — linux_kernel |
An issue was discovered in the Linux kernel through 6.0.9. drivers/media/dvb-core/dvb_frontend.c has a race condition that can cause a use-after-free when a device is disconnected. |
2022-11-25 |
not yet calculated |
CVE-2022-45885
MISC
MISC |
| linux — linux_kernel |
An issue was discovered in the Linux kernel through 6.0.9. drivers/media/dvb-core/dvb_net.c has a .disconnect versus dvb_device_open race condition that leads to a use-after-free. |
2022-11-25 |
not yet calculated |
CVE-2022-45886
MISC
MISC |
| linux — linux_kernel |
An issue was discovered in the Linux kernel through 6.0.9. drivers/media/usb/ttusb-dec/ttusb_dec.c has a memory leak because of the lack of a dvb_frontend_detach call. |
2022-11-25 |
not yet calculated |
CVE-2022-45887
MISC
MISC |
| linux — linux_kernel |
An issue was discovered in the Linux kernel through 6.0.9. drivers/char/xillybus/xillyusb.c has a race condition and use-after-free during physical removal of a USB device. |
2022-11-25 |
not yet calculated |
CVE-2022-45888
MISC |
| manage_engine — manage_engine |
Zoho ManageEngine ServiceDesk Plus versions 13010 and prior are vulnerable to authenticated command injection. This can be exploited by high-privileged users. |
2022-11-23 |
not yet calculated |
CVE-2022-40770
MISC
MISC |
manage_engine — manage_engine
|
Zoho ManageEngine ServiceDesk Plus versions 13010 and prior are vulnerable to an XML External Entity attack that leads to Information Disclosure. |
2022-11-23 |
not yet calculated |
CVE-2022-40771
MISC
MISC |
manage_engine — manage_engine
|
Zoho ManageEngine ServiceDesk Plus versions 13010 and prior are vulnerable to a validation bypass that allows users to access sensitive data via the report module. |
2022-11-23 |
not yet calculated |
CVE-2022-40772
MISC
MISC |
| mcafee — total_protection |
McAfee Total Protection prior to version 16.0.49 contains an uncontrolled search path element vulnerability due to the use of a variable pointing to a subdirectory that may be controllable by an unprivileged user. This may have allowed the unprivileged user to execute arbitrary code with system privileges. |
2022-11-23 |
not yet calculated |
CVE-2022-43751
MISC
MISC |
|
microweber — microweber
|
Microweber version 1.3.1 allows an unauthenticated user to perform an account takeover via an XSS on the ‘select-file’ parameter. |
2022-11-25 |
not yet calculated |
CVE-2022-0698
MISC
MISC |
|
microweber — microweber
|
Microweber v1.2.15 was discovered to allow attackers to perform an account takeover via a host header injection attack. |
2022-11-22 |
not yet calculated |
CVE-2022-33012
MISC
MISC
MISC
MISC |
| mitsubishi electric — multiple_products |
Improper Input Validation vulnerability in Mitsubishi Electric GOT2000 Series GT27 model FTP server versions 01.39.000 and prior, Mitsubishi Electric GOT2000 Series GT25 model FTP server versions 01.39.000 and prior and Mitsubishi Electric GOT2000 Series GT23 model FTP server versions 01.39.000 and prior allows a remote authenticated attacker to cause a Denial of Service condition by sending specially crafted command. |
2022-11-24 |
not yet calculated |
CVE-2022-40266
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Password vulnerability in Mitsubishi Electric GX Works3 all versions allows an unauthenticated attacker to disclose sensitive information. As a result, unauthorized users may view or execute programs illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29825
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Cleartext Storage of Sensitive Information vulnerability in Mitsubishi Electric GX Works3 versions 1.086Q and prior allows a remote unauthenticated attacker to disclose sensitive information. As a result, unauthorized users may view or execute programs illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29826
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Cryptographic Key vulnerability in Mitsubishi Electric GX Works3 all versions allows a remote unauthenticated attacker to disclose sensitive information. As a result, unauthorized users may view or execute programs illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29827
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Cryptographic Key vulnerability in Mitsubishi Electric GX Works3 all versions allows a remote unauthenticated attacker to disclose sensitive information. As a result, unauthorized users may view or execute programs illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29828
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Cryptographic Key vulnerability in Mitsubishi Electric GX Works3 all versions allows a remote unauthenticated attacker to disclose sensitive information . As a result, unauthorized users may view or execute programs illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29829
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Cryptographic Key vulnerability in Mitsubishi Electric GX Works3 all versions allows a remote unauthenticated attacker to disclose or tamper with sensitive information. As a result, unauthorized users may obtain information about project files illegally. |
2022-11-25 |
not yet calculated |
CVE-2022-29830
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Use of Hard-coded Password vulnerability in Mitsubishi Electric Corporation GX Works3 versions 1.015R and later allows a remote unauthorized attacker to obtain information about the project file for MELSEC safety CPU modules. |
2022-11-25 |
not yet calculated |
CVE-2022-29831
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Cleartext Storage of Sensitive Information in Memory vulnerability in Mitsubishi Electric Corporation GX Works3 versions 1.015R and later allows a remote unauthorized attacker to disclose sensitive information. As a result, unauthorized users could obtain information about the project file for MELSEC safety CPU modules. |
2022-11-25 |
not yet calculated |
CVE-2022-29832
MISC
MISC |
|
mitsubishi_electric — gx_works3
|
Insufficiently Protected Credentials vulnerability in Mitsubishi Electric Corporation GX Works3 versions 1.015R and later allows a remote unauthorized attacker to disclose sensitive information. As a result, unauthorized users could access to MELSEC safety CPU modules illgally. |
2022-11-25 |
not yet calculated |
CVE-2022-29833
MISC
MISC |
| mitsubishi_electric — multiple_products |
Cleartext Storage of Sensitive Information vulnerability in Mitsubishi Electric GX Works3 all versions and Mitsubishi Electric MX OPC UA Module Configurator-R all versions allows a remote unauthenticated attacker to disclose sensitive information. As a result, unauthorized users can gain unauthorized access to the CPU module and the OPC UA server module. |
2022-11-25 |
not yet calculated |
CVE-2022-25164
MISC
MISC |
| moodle — moodle |
A blind Server-Side Request Forgery (SSRF) vulnerability was found in Moodle. This flaw exists due to insufficient validation of user-supplied input in LTI provider library. The library does not utilise Moodle’s inbuilt cURL helper, which resulted in a blind SSRF risk. An attacker can send a specially crafted HTTP request and trick the application to initiate requests to arbitrary systems. This vulnerability allows a remote attacker to perform SSRF attacks. |
2022-11-25 |
not yet calculated |
CVE-2022-45152
MISC
MISC
MISC |
| mpxj– mpxj |
MPXJ is an open source library to read and write project plans from a variety of file formats and databases. On Unix-like operating systems (not Windows or macos), MPXJ’s use of `File.createTempFile(..)` results in temporary files being created with the permissions `-rw-r–r–`. This means that any other user on the system can read the contents of this file. When MPXJ is reading a schedule file which requires the creation of a temporary file or directory, a knowledgeable local user could locate these transient files while they are in use and would then be able to read the schedule being processed by MPXJ. The problem has been patched, MPXJ version 10.14.1 and later includes the necessary changes. Users unable to upgrade may set `java.io.tmpdir` to a directory to which only the user running the application has access will prevent other users from accessing these temporary files. |
2022-11-25 |
not yet calculated |
CVE-2022-41954
CONFIRM
MISC |
| nextcloud — nextcloud_desktop |
Nexcloud desktop is the Desktop sync client for Nextcloud. An attacker can inject arbitrary HyperText Markup Language into the Desktop Client application in the notifications. It is recommended that the Nextcloud Desktop client is upgraded to 3.6.1. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-39331
MISC
MISC
CONFIRM |
| nextcloud — nextcloud_desktop |
Nexcloud desktop is the Desktop sync client for Nextcloud. An attacker can inject arbitrary HyperText Markup Language into the Desktop Client application via user status and information. It is recommended that the Nextcloud Desktop client is upgraded to 3.6.1. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-39332
MISC
MISC
CONFIRM |
| nextcloud — nextcloud_desktop |
Nexcloud desktop is the Desktop sync client for Nextcloud. An attacker can inject arbitrary HyperText Markup Language into the Desktop Client application. It is recommended that the Nextcloud Desktop client is upgraded to 3.6.1. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-39333
MISC
CONFIRM
MISC |
| nextcloud — nextcloud_desktop |
Nextcloud desktop is the desktop sync client for Nextcloud. Versions prior to 3.6.1 would incorrectly trust invalid TLS certificates. A Man-in-the-middle attack is possible in case a user can be made running a nextcloudcmd CLI command locally. It is recommended that the Nextcloud Desktop client is upgraded to 3.6.1. There are no known workarounds for this vulnerability. |
2022-11-25 |
not yet calculated |
CVE-2022-39334
MISC
CONFIRM
MISC
MISC |
| nextcloud — security-advisories |
user_oidc is an OpenID Connect user backend for Nextcloud. Versions prior to 1.2.1 did not properly validate discovery urls which may lead to a stored cross site scripting attack vector. The impact is limited due to the restrictive CSP that is applied on this endpoint. Additionally this vulnerability has only been shown to be exploitable in the Safari web browser. This issue has been addressed in version 1.2.1. Users are advised to upgrade. Users unable to upgrade should urge their users to avoid using the Safari web browser. |
2022-11-25 |
not yet calculated |
CVE-2022-39338
CONFIRM
MISC
MISC |
| nextcloud — security-advisories |
user_oidc is an OpenID Connect user backend for Nextcloud. In versions prior to 1.2.1 sensitive information such as the OIDC client credentials and tokens are sent in plain text of HTTP without TLS. Any malicious actor with access to monitor user traffic may have been able to compromise account security. This issue has been addressed in in user_oidc v1.2.1. Users are advised to upgrade. Users unable to upgrade may use https to access Nextcloud. Set an HTTPS discovery URL in the provider settings (in Nextcloud OIDC admin settings). |
2022-11-25 |
not yet calculated |
CVE-2022-39339
MISC
MISC
CONFIRM |
| nextcloud — security-advisories |
Nextcloud server is an open source personal cloud server. Affected versions of nextcloud server did not properly limit user display names which could allow a malicious users to overload the backing database and cause a denial of service. It is recommended that the Nextcloud Server is upgraded to 22.2.10, 23.0.7 or 24.0.3. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-39346
CONFIRM
MISC
MISC |
| nextcloud — security-advisories |
Nextcould talk android is the android OS implementation of the nextcloud talk chat system. In affected versions the receiver is not protected by broadcastPermission allowing malicious apps to monitor communication. It is recommended that the Nextcloud Talk Android is upgraded to 14.1.0. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-41926
MISC
CONFIRM
MISC |
|
nxp — multiple_products
|
An information-disclosure vulnerability exists on select NXP devices when configured in Serial Download Protocol (SDP) mode: i.MX RT 1010, i.MX RT 1015, i.MX RT 1020, i.MX RT 1050, i.MX RT 1060, i.MX 6 Family, i.MX 7Dual/Solo, i.MX 7ULP, i.MX 8M Quad, i.MX 8M Mini, and Vybrid. In a device security-enabled configuration, memory contents could potentially leak to physically proximate attackers via the respective SDP port in cold and warm boot attacks. (The recommended mitigation is to completely disable the SDP mode by programming a one-time programmable eFUSE. Customers can contact NXP for additional information.) |
2022-11-18 |
not yet calculated |
CVE-2022-45163
MISC
MISC
MISC |
|
octopus_deploy — octopus_server
|
In affected versions of Octopus Server it is possible for target discovery to print certain values marked as sensitive to log files in plaint-text in when verbose logging is enabled. |
2022-11-25 |
not yet calculated |
CVE-2022-2721
MISC |
| orchard — orchard_cms |
Orchardproject Orchard CMS 1.10.3 is vulnerable to Cross Site Scripting (XSS). When a low privileged user such as an author or publisher, injects a crafted html and javascript payload in a blog post, leading to full admin account takeover or privilege escalation when the malicious blog post is loaded in the victim’s browser. |
2022-11-25 |
not yet calculated |
CVE-2022-37720
MISC
MISC
MISC |
| paddlepaddle — paddlepaddle |
In PaddlePaddle before 2.4, paddle.audio.functional.get_window is vulnerable to code injection because it calls eval on a user-supplied winstr. This may lead to arbitrary code execution. |
2022-11-26 |
not yet calculated |
CVE-2022-45908
MISC
MISC |
| pgjdbc — pgjdbc |
pgjdbc is an open source postgresql JDBC Driver. In affected versions a prepared statement using either `PreparedStatement.setText(int, InputStream)` or `PreparedStatemet.setBytea(int, InputStream)` will create a temporary file if the InputStream is larger than 2k. This will create a temporary file which is readable by other users on Unix like systems, but not MacOS. On Unix like systems, the system’s temporary directory is shared between all users on that system. Because of this, when files and directories are written into this directory they are, by default, readable by other users on that same system. This vulnerability does not allow other users to overwrite the contents of these directories or files. This is purely an information disclosure vulnerability. Because certain JDK file system APIs were only added in JDK 1.7, this this fix is dependent upon the version of the JDK you are using. Java 1.7 and higher users: this vulnerability is fixed in 4.5.0. Java 1.6 and lower users: no patch is available. If you are unable to patch, or are stuck running on Java 1.6, specifying the java.io.tmpdir system environment variable to a directory that is exclusively owned by the executing user will mitigate this vulnerability. |
2022-11-23 |
not yet calculated |
CVE-2022-41946
MISC
CONFIRM |
| phpgurukul — blood_donor_management_system |
PHPGurukul Blood Donor Management System 1.0 does not properly restrict access to admin/dashboard.php, which allows attackers to access all data of users, delete the users, add and manage Blood Group, and Submit Report. |
2022-11-25 |
not yet calculated |
CVE-2022-38813
MISC
MISC
MISC
MISC |
| pyro — pyrocms |
PyroCMS 3.9 is vulnerable to a stored Cross Site Scripting (XSS_ when a low privileged user such as an author, injects a crafted html and javascript payload in a blog post, leading to full admin account takeover or privilege escalation. |
2022-11-25 |
not yet calculated |
CVE-2022-37721
MISC
MISC |
| pytorch — pytorch |
In PyTorch before trunk/89695, torch.jit.annotations.parse_type_line can cause arbitrary code execution because eval is used unsafely. |
2022-11-26 |
not yet calculated |
CVE-2022-45907
MISC
MISC |
| qmpaas — qmpaas/leadshop |
Dangerous method exposed which can lead to RCE in qmpass/leadshop v1.4.15 allows an attacker to control the target host by calling any function in leadshop.php via the GET method. |
2022-11-24 |
not yet calculated |
CVE-2022-4136
CONFIRM
MISC |
| qpress — qpress |
qpress before PierreLvx/qpress 20220819 and before version 11.3, as used in Percona XtraBackup and other products, allows directory traversal via ../ in a .qp file. |
2022-11-23 |
not yet calculated |
CVE-2022-45866
MISC
MISC
MISC
MISC
MISC |
|
qs — qs
|
qs before 6.10.3, as used in Express before 4.17.3 and other products, allows attackers to cause a Node process hang for an Express application because an __ proto__ key can be used. In many typical Express use cases, an unauthenticated remote attacker can place the attack payload in the query string of the URL that is used to visit the application, such as a[__proto__]=b&a[__proto__]&a[length]=100000000. The fix was backported to qs 6.9.7, 6.8.3, 6.7.3, 6.6.1, 6.5.3, 6.4.1, 6.3.3, and 6.2.4 (and therefore Express 4.17.3, which has “deps: qs@6.9.7” in its release description, is not vulnerable). |
2022-11-26 |
not yet calculated |
CVE-2022-24999
MISC
CONFIRM
CONFIRM |
| rizalafani — cms-php |
SQL Injection vulnerability in function get_user in login_manager.php in rizalafani cms-php v1. |
2022-11-23 |
not yet calculated |
CVE-2021-35284
MISC |
| sanitization_management_system — sanitization_management_system |
Sanitization Management System v1.0 is vulnerable to SQL Injection via /php-sms/admin/?page=user/manage_user&id=. |
2022-11-23 |
not yet calculated |
CVE-2022-44278
MISC |
| schneider_electric — multiple_products |
A CWE-269: Improper Privilege Management vulnerability exists that could cause a denial of service of the Ethernet communication of the controller when sending a specific request over SNMP. Affected products: Modicon M340 CPUs(BMXP34* versions prior to V3.40), Modicon M340 X80 Ethernet Communication modules:BMXNOE0100 (H), BMXNOE0110 (H), BMXNOR0200H RTU(BMXNOE* all versions)(BMXNOR* versions prior to v1.7 IR24) |
2022-11-22 |
not yet calculated |
CVE-2022-0222
CONFIRM |
|
schneider_electric — multiple_products
|
A CWE-191: Integer Underflow (Wrap or Wraparound) vulnerability exists that could cause a denial of service of the controller due to memory access violations when using the Modbus TCP protocol. Affected products: Modicon M340 CPU (part numbers BMXP34*)(V3.40 and prior), Modicon M580 CPU (part numbers BMEP* and BMEH*)(V3.22 and prior), Legacy Modicon Quantum/Premium(All Versions), Modicon Momentum MDI (171CBU*)(All Versions), Modicon MC80 (BMKC80)(V1.7 and prior) |
2022-11-22 |
not yet calculated |
CVE-2022-37301
CONFIRM |
| seiko_epson_corporation — multiple_products |
The WebConfig functionality of Epson TM-C3500 and TM-C7500 devices with firmware version WAM31500 allows authentication bypass. |
2022-11-25 |
not yet calculated |
CVE-2022-36133
MISC
MISC |
| silverstripe — multiple_products |
Silverstripe silverstripe/framework through 4.11.0, silverstripe/assets through 1.11.0, and silverstripe/asset-admin through 1.11.0 allow XSS. |
2022-11-23 |
not yet calculated |
CVE-2022-38724
MISC
MISC
MISC
MISC |
| silverstripe — silverstripe/cms |
Silverstripe silverstripe/cms through 4.11.0 allows XSS. |
2022-11-23 |
not yet calculated |
CVE-2022-37421
MISC
MISC
MISC
MISC |
| silverstripe — silverstripe/framework |
Silverstripe silverstripe/framework through 4.11 allows XSS (issue 1 of 2) via JavaScript payload to the href attribute of a link by splitting a javascript URL with white space characters. |
2022-11-23 |
not yet calculated |
CVE-2022-37429
MISC
MISC
MISC
MISC |
| silverstripe — silverstripe/framework |
Silverstripe silverstripe/framework through 4.11 allows XSS vulnerability via href attribute of a link (issue 2 of 2). |
2022-11-23 |
not yet calculated |
CVE-2022-37430
MISC
MISC
MISC
MISC |
|
silverstripe — silverstripe/framework
|
Silverstripe silverstripe/framework through 4.11 allows XSS (issue 1 of 3) via remote attackers adding a Javascript payload to a page’s meta description and get it executed in the versioned history compare view. |
2022-11-23 |
not yet calculated |
CVE-2022-38145
MISC
MISC
MISC
MISC |
|
silverstripe — silverstripe/framework
|
Silverstripe silverstripe/framework through 4.11 allows XSS (issue 3 of 3). |
2022-11-23 |
not yet calculated |
CVE-2022-38147
MISC
MISC
MISC
MISC |
| solarwinds — ets |
The application fails to prevent users from connecting to it over unencrypted connections. An attacker able to modify a legitimate user’s network traffic could bypass the application’s use of SSL/TLS encryption and use the application as a platform for attacks against its users. |
2022-11-23 |
not yet calculated |
CVE-2021-35246
MISC
MISC
MISC |
| solarwinds — sem |
This vulnerability discloses build and services versions in the server response header. |
2022-11-23 |
not yet calculated |
CVE-2022-38113
MISC
MISC |
| solarwinds — sem |
This vulnerability occurs when a web server fails to correctly process the Content-Length of POST requests. This can lead to HTTP request smuggling or XSS. |
2022-11-23 |
not yet calculated |
CVE-2022-38114
MISC
MISC |
| solarwinds — sem |
Insecure method vulnerability in which allowed HTTP methods are disclosed. E.g., OPTIONS, DELETE, TRACE, and PUT |
2022-11-23 |
not yet calculated |
CVE-2022-38115
MISC
MISC |
| sourcecodester — billing_system_project |
Billing System Project v1.0 was discovered to contain a SQL injection vulnerability via the orderId parameter at fetchOrderData.php. |
2022-11-22 |
not yet calculated |
CVE-2022-43212
MISC
MISC |
| sourcecodester — billing_system_project |
Billing System Project v1.0 was discovered to contain a SQL injection vulnerability via the id parameter at editorder.php. |
2022-11-23 |
not yet calculated |
CVE-2022-43213
MISC
MISC |
sourcecodester — canteen_management_system
|
A vulnerability was found in SourceCodester Canteen Management System. It has been classified as problematic. This affects the function query of the file food.php. The manipulation of the argument product_name leads to cross site scripting. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-214359. |
2022-11-25 |
not yet calculated |
CVE-2022-4091
MISC
MISC |
| spatie — browsershot |
Browsershot version 3.57.2 allows an external attacker to remotely obtain arbitrary local files. This is possible because the application does not validate the URL protocol passed to the Browsershot::url method. |
2022-11-25 |
not yet calculated |
CVE-2022-41706
MISC
MISC |
| spatie — browsershot |
Browsershot version 3.57.2 allows an external attacker to remotely obtain arbitrary local files. This is possible because the application does not validate that the HTML content passed to the Browsershot::html method does not contain URL’s that use the file:// protocol. |
2022-11-25 |
not yet calculated |
CVE-2022-43983
MISC
MISC |
| spatie — browsershot |
Browsershot version 3.57.3 allows an external attacker to remotely obtain arbitrary local files. This is possible because the application does not validate that the JS content imported from an external source passed to the Browsershot::html method does not contain URLs that use the file:// protocol. |
2022-11-25 |
not yet calculated |
CVE-2022-43984
MISC
MISC |
| stock_management_system — stock_management_system |
A vulnerability was found in rickxy Stock Management System and classified as critical. Affected by this issue is some unknown functionality of the file /pages/processlogin.php. The manipulation of the argument user/password leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-214322 is the identifier assigned to this vulnerability. |
2022-11-24 |
not yet calculated |
CVE-2022-4088
MISC
MISC |
| stock_management_system — stock_management_system |
A vulnerability was found in rickxy Stock Management System. It has been declared as problematic. This vulnerability affects unknown code of the file /pages/processlogin.php. The manipulation of the argument user leads to cross site scripting. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-214324. |
2022-11-24 |
not yet calculated |
CVE-2022-4089
MISC
MISC |
| stock_management_system — stock_management_system |
A vulnerability was found in rickxy Stock Management System and classified as problematic. This issue affects some unknown processing of the file us_transac.php?action=add. The manipulation leads to cross-site request forgery. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-214331. |
2022-11-24 |
not yet calculated |
CVE-2022-4090
MISC
MISC |
| super-xray — super-xray |
super-xray is a vulnerability scanner (xray) GUI launcher. In version 0.1-beta, the URL is not filtered and directly spliced ??into the command, resulting in a possible RCE vulnerability. Users should upgrade to super-xray 0.2-beta. |
2022-11-21 |
not yet calculated |
CVE-2022-41945
CONFIRM
MISC |
| super-xray — super-xray |
super-xray is a web vulnerability scanning tool. Versions prior to 0.7 assumed trusted input for the program config which is stored in a yaml file. An attacker with local access to the file could exploit this and compromise the program. This issue has been addressed in commit `4d0d5966` and will be included in future releases. Users are advised to upgrade. There are no known workarounds for this issue. |
2022-11-25 |
not yet calculated |
CVE-2022-41958
MISC
CONFIRM |
|
systemd — systemd
|
systemd 250 and 251 allows local users to achieve a systemd-coredump deadlock by triggering a crash that has a long backtrace. This occurs in parse_elf_object in shared/elf-util.c. The exploitation methodology is to crash a binary calling the same function recursively, and put it in a deeply nested directory to make its backtrace large enough to cause the deadlock. This must be done 16 times when MaxConnections=16 is set for the systemd/units/systemd-coredump.socket file. |
2022-11-23 |
not yet calculated |
CVE-2022-45873
MISC
MISC
MISC |
| tailscale — tailscale |
A vulnerability identified in the Tailscale Windows client allows a malicious website to reconfigure the Tailscale daemon `tailscaled`, which can then be used to remotely execute code. In the Tailscale Windows client, the local API was bound to a local TCP socket, and communicated with the Windows client GUI in cleartext with no Host header verification. This allowed an attacker-controlled website visited by the node to rebind DNS to an attacker-controlled DNS server, and then make local API requests in the client, including changing the coordination server to an attacker-controlled coordination server. An attacker-controlled coordination server can send malicious URL responses to the client, including pushing executables or installing an SMB share. These allow the attacker to remotely execute code on the node. All Windows clients prior to version v.1.32.3 are affected. If you are running Tailscale on Windows, upgrade to v1.32.3 or later to remediate the issue. |
2022-11-23 |
not yet calculated |
CVE-2022-41924
CONFIRM
MISC
MISC |
| tailscale — tailscale |
A vulnerability identified in the Tailscale client allows a malicious website to access the peer API, which can then be used to access Tailscale environment variables. In the Tailscale client, the peer API was vulnerable to DNS rebinding. This allowed an attacker-controlled website visited by the node to rebind DNS for the peer API to an attacker-controlled DNS server, and then making peer API requests in the client, including accessing the node’s Tailscale environment variables. An attacker with access to the peer API on a node could use that access to read the node’s environment variables, including any credentials or secrets stored in environment variables. This may include Tailscale authentication keys, which could then be used to add new nodes to the user’s tailnet. The peer API access could also be used to learn of other nodes in the tailnet or send files via Taildrop. All Tailscale clients prior to version v1.32.3 are affected. Upgrade to v1.32.3 or later to remediate the issue. |
2022-11-23 |
not yet calculated |
CVE-2022-41925
CONFIRM
MISC
MISC |
|
technitium_software — dns_server
|
An issue was discovered in Technitium DNS Server through 8.0.2 that allows variant V1 of unintended domain name resolution. A revoked domain name can still be resolvable for a long time, including expired domains and taken-down malicious domains. The effects of an exploit would be widespread and highly impactful, because the exploitation conforms to de facto DNS specifications and operational practices, and overcomes current mitigation patches for “Ghost” domain names. |
2022-11-21 |
not yet calculated |
CVE-2022-30257
MISC |
|
technitium_software — dns_server
|
An issue was discovered in Technitium DNS Server through 8.0.2 that allows variant V2 of unintended domain name resolution. A revoked domain name can still be resolvable for a long time, including expired domains and taken-down malicious domains. The effects of an exploit would be widespread and highly impactful, because the exploitation conforms to de facto DNS specifications and operational practices, and overcomes current mitigation patches for “Ghost” domain names. |
2022-11-21 |
not yet calculated |
CVE-2022-30258
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function form_fast_setting_wifi_set. |
2022-11-21 |
not yet calculated |
CVE-2022-44171
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function R7WebsSecurityHandler. |
2022-11-21 |
not yet calculated |
CVE-2022-44172
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.05 is vulnerable to Buffer Overflow via function formSetDeviceName. |
2022-11-21 |
not yet calculated |
CVE-2022-44174
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function formSetMacFilterCfg. |
2022-11-21 |
not yet calculated |
CVE-2022-44175
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function fromSetRouteStatic. |
2022-11-21 |
not yet calculated |
CVE-2022-44176
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function formWifiWpsStart. |
2022-11-21 |
not yet calculated |
CVE-2022-44177
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow. via function formWifiWpsOOB. |
2022-11-21 |
not yet calculated |
CVE-2022-44178
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function addWifiMacFilter. |
2022-11-21 |
not yet calculated |
CVE-2022-44180
MISC |
|
tenda — ac18
|
Tenda AC18 V15.03.05.19 is vulnerable to Buffer Overflow via function formSetWifiGuestBasic. |
2022-11-21 |
not yet calculated |
CVE-2022-44183
MISC |
|
tiny_file_manager — tiny_file_manager
|
Tiny File Manager version 2.4.8 allows an unauthenticated remote attacker to execute arbitrary code remotely on the server. This is possible because the application is vulnerable to CSRF, processes uploaded files server-side (instead of just returning them for download), and allows unauthenticated users to access uploaded files. |
2022-11-25 |
not yet calculated |
CVE-2022-23044
MISC
MISC |
| tiny_file_manager — tiny_file_manager |
Tiny File Manager version 2.4.8 allows an unauthenticated remote attacker to execute arbitrary code remotely on the server. This is possible because the application is vulnerable to CSRF, processes uploaded files server-side (instead of just returning them for download), and allows unauthenticated users to access uploaded files. |
2022-11-25 |
not yet calculated |
CVE-2022-45475
MISC
MISC |
| tiny_file_manager — tiny_file_manager |
Tiny File Manager version 2.4.8 allows an unauthenticated remote attacker to execute arbitrary code remotely on the server. This is possible because the application is vulnerable to CSRF, processes uploaded files server-side (instead of just returning them for download), and allows unauthenticated users to access uploaded files. |
2022-11-25 |
not yet calculated |
CVE-2022-45476
MISC
MISC |
|
totolink — a7100ru
|
TOTOlink A7100RU V7.4cu.2313_B20191024 was discovered to contain a command injection vulnerability via the port parameter in the setting/setOpenVpnClientCfg function. |
2022-11-25 |
not yet calculated |
CVE-2022-44843
MISC |
|
totolink — a7100ru
|
TOTOlink A7100RU V7.4cu.2313_B20191024 was discovered to contain a command injection vulnerability via the pass parameter in the setting/setOpenVpnCfg function. |
2022-11-25 |
not yet calculated |
CVE-2022-44844
MISC |
| tu6ge — oss-rs |
aliyun-oss-client is a rust client for Alibaba Cloud OSS. Users of this library will be affected, the incoming secret will be disclosed unintentionally. This issue has been patched in version 0.8.1. |
2022-11-22 |
not yet calculated |
CVE-2022-39397
MISC
CONFIRM |
| vim — vim/vim |
The target’s backtrace indicates that libc has detected a heap error or that the target was executing a heap function when it stopped. This could be due to heap corruption, passing a bad pointer to a heap function such as free(), etc. Since heap errors might include buffer overflows, use-after-free situations, etc. they are generally considered exploitable. |
2022-11-25 |
not yet calculated |
CVE-2022-4141
CONFIRM
MISC |
| vmware — open-vm-tools |
An issue was discovered in open-vm-tools 2009.03.18-154848. Local users can gain privileges via a symlink attack on /tmp files if vmware-user-suid-wrapper is setuid root and the ChmodChownDirectory function is enabled. |
2022-11-23 |
not yet calculated |
CVE-2009-1142
MISC
MISC |
| vmware — open-vm-tools |
An issue was discovered in open-vm-tools 2009.03.18-154848. Local users can bypass intended access restrictions on mounting shares via a symlink attack that leverages a realpath race condition in mount.vmhgfs (aka hgfsmounter). |
2022-11-23 |
not yet calculated |
CVE-2009-1143
MISC
MISC |
| wbce — wbce_cms |
A cross-site scripting (XSS) vulnerability in the Search Settings module of WBCE CMS v1.5.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the No Results field. |
2022-11-25 |
not yet calculated |
CVE-2022-45036
MISC |
| wbce — wbce_cms |
A cross-site scripting (XSS) vulnerability in /admin/users/index.php of WBCE CMS v1.5.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Display Name field. |
2022-11-25 |
not yet calculated |
CVE-2022-45037
MISC |
| wbce — wbce_cms |
A cross-site scripting (XSS) vulnerability in /admin/settings/save.php of WBCE CMS v1.5.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Website Footer field. |
2022-11-25 |
not yet calculated |
CVE-2022-45038
MISC |
| wbce — wbce_cms |
An arbitrary file upload vulnerability in the Server Settings module of WBCE CMS v1.5.4 allows attackers to execute arbitrary code via a crafted PHP file. |
2022-11-25 |
not yet calculated |
CVE-2022-45039
MISC |
| wbce — wbce_cms |
A cross-site scripting (XSS) vulnerability in /admin/pages/sections_save.php of WBCE CMS v1.5.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Name Section field. |
2022-11-25 |
not yet calculated |
CVE-2022-45040
MISC |
| web_based_quiz_system — web_based_quiz_system |
Web Based Quiz System v1.0 transmits user passwords in plaintext during the authentication process, allowing attackers to obtain users’ passwords via a bruteforce attack. |
2022-11-25 |
not yet calculated |
CVE-2022-44411
MISC |
| webcash — serp_server |
A specific file on the sERP server if Kyungrinara(ERP solution) has a fixed password with the SYSTEM authority. This vulnerability could allow attackers to leak or steal sensitive information or execute malicious commands. |
2022-11-25 |
not yet calculated |
CVE-2022-41157
MISC |
| wger — wger |
Improper Restriction of Excessive Authentication Attempts in GitHub repository wger-project/wger prior to 2.2. |
2022-11-24 |
not yet calculated |
CVE-2022-2650
CONFIRM
MISC |
|
wind_river — vxworks
|
An issue was discovered in Wind River VxWorks 6.9 and 7, that allows a specifically crafted packet sent by a Radius server, may cause Denial of Service during the IP Radius access procedure. |
2022-11-25 |
not yet calculated |
CVE-2022-38767
MISC
MISC |
| wordpress — wordpress |
The Betheme theme for WordPress is vulnerable to PHP Object Injection in versions up to, and including, 26.5.1.4 via deserialization of untrusted input supplied via the import, mfn-items-import-page, and mfn-items-import parameters passed through the mfn_builder_import, mfn_builder_import_page, importdata, importsinglepage, and importfromclipboard functions. This makes it possible for authenticated attackers, with contributor level permissions and above to inject a PHP Object. The additional presence of a POP chain would make it possible for attackers to execute code, retrieve sensitive data, delete files, etc.. |
2022-11-21 |
not yet calculated |
CVE-2022-3861
MISC
MISC
MISC |
| wordpress — wordpress |
Multiple Cross-Site Request Forgery vulnerabilities in All-In-One Security (AIOS) – Security and Firewall (WordPress plugin) <= 5.1.0 on WordPress. |
2022-11-22 |
not yet calculated |
CVE-2022-44737
MISC |
|
wordpress — wordpress
|
Auth. (subscriber+) Stored Cross-Site Scripting (XSS) in Muffingroup Betheme theme <= 26.6.1 on WordPress. |
2022-11-22 |
not yet calculated |
CVE-2022-45363
MISC |
| xwiki — xwiki-platform |
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. The application allows anyone with view access to modify any page of the wiki by importing a crafted XAR package. The problem has been patched in XWiki 14.6RC1, 14.6 and 13.10.8. As a workaround, setting the right of the page Filter.WebHome and making sure only the main wiki administrators can view the application installed on main wiki or edit the page and apply the changed described in commit fb49b4f. |
2022-11-22 |
not yet calculated |
CVE-2022-41937
MISC
MISC
CONFIRM |
xwiki — xwiki-platform
|
XWiki Platform is vulnerable to Cross-Site Request Forgery (CSRF) that may allow attackers to delete or rename tags without needing any confirmation. The problem has been patched in XWiki 13.10.7, 14.4.1 and 14.5RC1. Workarounds: It’s possible to patch existing instances directly by editing the page Main.Tags and add this kind of check, in the code for renaming and for deleting: “` #if (!$services.csrf.isTokenValid($request.get(‘form_token’))) #set ($discard = $response.sendError(401, “Wrong CSRF token”)) #end “` |
2022-11-23 |
not yet calculated |
CVE-2022-41927
MISC
CONFIRM |
xwiki — xwiki-platform
|
XWiki Platform vulnerable to Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’) in AttachmentSelector.xml. The issue can also be reproduced by inserting the dangerous payload in the `height` or `alt` macro properties. This has been patched in versions 13.10.7, 14.4.2, and 14.5. The issue can be fixed on a running wiki by updating `XWiki.AttachmentSelector` with the versions below: – 14.5-rc-1+: https://github.com/xwiki/xwiki-platform/commit/eb15147adf94bddb92626f862c1710d45bcd64a7#diff-e1513599ab698991f6cbba55d38f3f464432ced8d137a668b1f7618c7e747e23 – 14.4.2+: https://github.com/xwiki/xwiki-platform/commit/c02f8eb1f3c953d124f2c097021536f8bc00fa8d#diff-e1513599ab698991f6cbba55d38f3f464432ced8d137a668b1f7618c7e747e23 – 13.10.7+: https://github.com/xwiki/xwiki-platform/commit/efd0df0468d46149ba68b66660b93f31b6318515#diff-e1513599ab698991f6cbba55d38f3f464432ced8d137a668b1f7618c7e747e23 |
2022-11-23 |
not yet calculated |
CVE-2022-41928
CONFIRM
MISC |
xwiki — xwiki-platform
|
org.xwiki.platform:xwiki-platform-oldcore is missing authorization in User#setDisabledStatus, which may allow an incorrectly authorized user with only Script rights to enable or disable a user. This operation is meant to only be available for users with admin rights. This problem has been patched in XWiki 13.10.7, 14.4.2 and 14.5RC1. |
2022-11-23 |
not yet calculated |
CVE-2022-41929
CONFIRM
MISC
MISC |
xwiki — xwiki-platform
|
org.xwiki.platform:xwiki-platform-user-profile-ui is missing authorization to enable or disable users. Any user (logged in or not) with access to the page XWiki.XWikiUserProfileSheet can enable or disable any user profile. This might allow to a disabled user to re-enable themselves, or to an attacker to disable any user of the wiki. The problem has been patched in XWiki 13.10.7, 14.5RC1 and 14.4.2. Workarounds: The problem can be patched immediately by editing the page `XWiki.XWikiUserProfileSheet` in the wiki and by performing the changes contained in https://github.com/xwiki/xwiki-platform/commit/5be1cc0adf917bf10899c47723fa451e950271fa. |
2022-11-23 |
not yet calculated |
CVE-2022-41930
MISC
MISC
CONFIRM |
xwiki — xwiki-platform
|
xwiki-platform-icon-ui is vulnerable to Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’). Any user with view rights on commonly accessible documents including the icon picker macro can execute arbitrary Groovy, Python or Velocity code in XWiki due to improper neutralization of the macro parameters of the icon picker macro. The problem has been patched in XWiki 13.10.7, 14.5 and 14.4.2. Workarounds: The [patch](https://github.com/xwiki/xwiki-platform/commit/47eb8a5fba550f477944eb6da8ca91b87eaf1d01) can be manually applied by editing `IconThemesCode.IconPickerMacro` in the object editor. The whole document can also be replaced by the current version by importing the document from the XAR archive of a fixed version as the only changes to the document have been security fixes and small formatting changes. |
2022-11-23 |
not yet calculated |
CVE-2022-41931
MISC
MISC
CONFIRM |
xwiki — xwiki-platform
|
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. It’s possible to make XWiki create many new schemas and fill them with tables just by using a crafted user identifier in the login form. This may lead to degraded database performance. The problem has been patched in XWiki 13.10.8, 14.6RC1 and 14.4.2. Users are advised to upgrade. There are no known workarounds for this issue. |
2022-11-23 |
not yet calculated |
CVE-2022-41932
MISC
CONFIRM |
xwiki — xwiki-platform
|
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. When the `reset a forgotten password` feature of XWiki was used, the password was then stored in plain text in database. This only concerns XWiki 13.1RC1 and newer versions. Note that it only concerns the reset password feature available from the “Forgot your password” link in the login view: the features allowing a user to change their password, or for an admin to change a user password are not impacted. This vulnerability is particularly dangerous in combination with other vulnerabilities allowing to perform data leak of personal data from users, such as GHSA-599v-w48h-rjrm. Note that this vulnerability only concerns the users of the main wiki: in case of farms, the users registered on subwiki are not impacted thanks to a bug we discovered when investigating this. The problem has been patched in version 14.6RC1, 14.4.3 and 13.10.8. The patch involves a migration of the impacted users as well as the history of the page, to ensure no password remains in plain text in the database. This migration also involves to inform the users about the possible disclosure of their passwords: by default, two emails are automatically sent to the impacted users. A first email to inform about the possibility that their password have been leaked, and a second email using the reset password feature to ask them to set a new password. It’s also possible for administrators to set some properties for the migration: it’s possible to decide if the user password should be reset (default) or if the passwords should be kept but only hashed. Note that in the first option, the users won’t be able to login anymore until they set a new password if they were impacted. Note that in both options, mails will be sent to users to inform them and encourage them to change their passwords. |
2022-11-23 |
not yet calculated |
CVE-2022-41933
MISC
MISC
MISC
CONFIRM
MISC |
xwiki — xwiki-platform
|
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. Any user with view rights on commonly accessible documents including the menu macro can execute arbitrary Groovy, Python or Velocity code in XWiki leading to full access to the XWiki installation due to improper escaping of the macro content and parameters of the menu macro. The problem has been patched in XWiki 14.6RC1, 13.10.8 and 14.4.3. The patch (commit `2fc20891`) for the document `Menu.MenuMacro` can be manually applied or a XAR archive of a patched version can be imported. The menu macro was basically unchanged since XWiki 11.6 so on XWiki 11.6 or later the patch for version of 13.10.8 (commit `59ccca24a`) can most likely be applied, on XWiki version 14.0 and later the versions in XWiki 14.6 and 14.4.3 should be appropriate. |
2022-11-23 |
not yet calculated |
CVE-2022-41934
CONFIRM
MISC
MISC
MISC
MISC |
xwiki — xwiki-platform
|
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. Users without the right to view documents can deduce their existence by repeated Livetable queries. The issue has been patched in XWiki 14.6RC1, 13.10.8, and 14.4.3, the response is not properly cleaned up of obfuscated entries. As a workaround, The patch for the document `XWiki.LiveTableResultsMacros` can be manually applied or a XAR archive of a patched version can be imported, on versions 12.10.11, 13.9-rc-1, and 13.4.4. There are no known workarounds for this issue. |
2022-11-23 |
not yet calculated |
CVE-2022-41935
CONFIRM
MISC
MISC |
xwiki — xwiki-platform
|
XWiki Platform is a generic wiki platform offering runtime services for applications built on top of it. The `modifications` rest endpoint does not filter out entries according to the user’s rights. Therefore, information hidden from unauthorized users are exposed though the `modifications` rest endpoint (comments and page names etc). Users should upgrade to XWiki 14.6+, 14.4.3+, or 13.10.8+. Older versions have not been patched. There are no known workarounds. |
2022-11-22 |
not yet calculated |
CVE-2022-41936
CONFIRM
MISC
MISC |
yiisoft — yii
|
`yiisoft/yii` before version 1.1.27 are vulnerable to Remote Code Execution (RCE) if the application calls `unserialize()` on arbitrary user input. This has been patched in 1.1.27. |
2022-11-23 |
not yet calculated |
CVE-2022-41922
CONFIRM
MISC |
| yjcms — yjcms |
An issue in the /index/user/user_edit.html component of YJCMS v1.0.9 allows unauthenticated attackers to obtain the Administrator account password. |
2022-11-23 |
not yet calculated |
CVE-2022-45276
MISC |
| yoroi — fusiondirectory |
Fusiondirectory 1.3 suffers from Improper Session Handling. |
2022-11-22 |
not yet calculated |
CVE-2022-36179
MISC
MISC |
| yoroi — fusiondirectory |
Fusiondirectory 1.3 is vulnerable to Cross Site Scripting (XSS) via /fusiondirectory/index.php?message=[injection], /fusiondirectory/index.php?message=invalidparameter&plug={Injection], /fusiondirectory/index.php?signout=1&message=[injection]&plug=106. |
2022-11-22 |
not yet calculated |
CVE-2022-36180
MISC
MISC |
| zte — mf286r |
There is a SQL injection vulnerability in ZTE MF286R. Due to insufficient validation of the input parameters of the phonebook interface, an authenticated attacker could use the vulnerability to execute arbitrary SQL injection. |
2022-11-22 |
not yet calculated |
CVE-2022-39066
MISC |
|
zte — mf286r
|
There is a buffer overflow vulnerability in ZTE MF286R. Due to lack of input validation on parameters of the wifi interface, an authenticated attacker could use the vulnerability to perform a denial of service attack. |
2022-11-22 |
not yet calculated |
CVE-2022-39067
MISC |
|
zte — pon_olt
|
There is an access control vulnerability in some ZTE PON OLT products. Due to improper access control settings, remote attackers could use the vulnerability to log in to the device and execute any operation. |
2022-11-22 |
not yet calculated |
CVE-2022-39070
MISC |


Recent Comments