by Scott Muniz | Nov 23, 2021 | Security
This article was originally posted by the FTC. See the original article here.
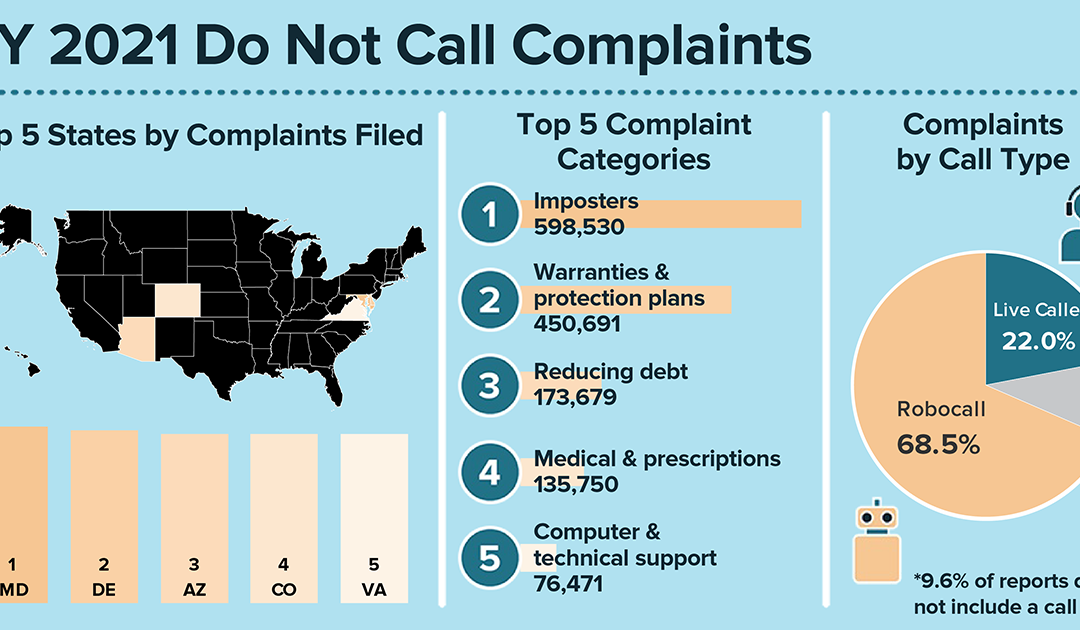
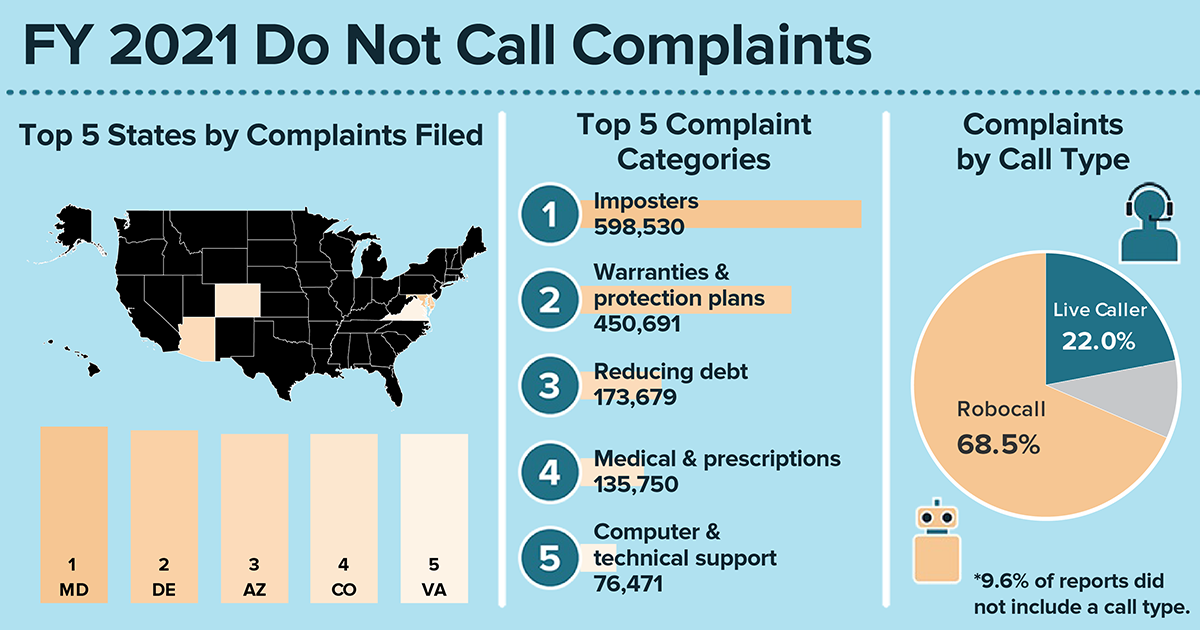 In the past 18 years of the National Do Not Call Registry, those of you signed up for the registry (244 million phone numbers right now) have reported millions upon millions of unwanted sales calls over the years. Here’s a quick look at what you’ve reported this year at DoNotCall.gov about the calls you’re getting:
In the past 18 years of the National Do Not Call Registry, those of you signed up for the registry (244 million phone numbers right now) have reported millions upon millions of unwanted sales calls over the years. Here’s a quick look at what you’ve reported this year at DoNotCall.gov about the calls you’re getting:
- The overwhelming majority of calls reported were robocalls — 68 percent of the 5 million calls you reported during the fiscal year ending October 2021 were robocalls. (If you answer the phone and hear a recorded message instead of a live person, it’s a robocall). Another 22 percent were live calls.
- The most common topic of the calls you reported was imposters, including calls from scammers pretending to be the Social Security Administration or IRS.
- The next most-reported topic — up by more than 175,000 from last year — was warranties and protection plans. Following that were calls about debt reduction, medical and prescription issues, and computers and technical support.
Learn more about these reports, including data for your state.
Your reports show what we all know — even if you’re on the registry, you’re still getting unwanted calls. Legitimate, law-abiding companies typically follow the Do Not Call rules. But scammers often ignore them. To get fewer calls, read about some steps you can take to block unwanted calls.
And please, keep reporting calls at DoNotCall.gov. The FTC and other law enforcement agencies analyze reports to identify and take action against the people responsible for illegal calls and scams. The FTC also takes the phone numbers you report and releases them each business day to help telecommunications carriers and other industry partners that are working on call-blocking and call-labeling solutions.
Learn more about blocking unwanted calls at ftc.gov/calls.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Nov 23, 2021 | Technology
This article is contributed. See the original author and article here.
Welcome to our new monthly blog series featuring the latest Security, Compliance, and Identity content updates on Microsoft Learn! This is our first post, and we’re highlighting recently released updates, including a new learning path we launched during Cybersecurity Awareness Month. Starting in January, we’ll highlight new learning paths, modules, and other content updates we make each month to give you the skills you need on your learning journey.
Read on to check out some of the latest updates from our Security, Compliance, and Identity portfolio.
Introduction to cybersecurity
Knowing the fundamentals of cybersecurity is a first step toward protecting against cyberthreats. Our new learning path—Describe the basic concepts of cybersecurity—delivers foundational knowledge about cybersecurity concepts including cryptography, authentication, and authorization, along with exploring ways to protect yourself and your business from cyberattacks.
AZ – 500: Microsoft Azure Security Technologies
This four-part series of learning paths will equip you with the knowledge you need to take Exam AZ-500.
This learning path will teach you how to secure Azure solutions with Azure Active Directory, implement hybrid identity, deploy Azure AD identity protection, and configure Azure AD privileged identity management.
This learning path will teach you how to lock down the infrastructure and network resources that are running in your Azure environment.
This learning path will teach you how to deploy and secure Azure Key Vault, configure application security features, implement storage security, and configure and manage SQL database security.
This learning path will teach you how to configure and manage Azure monitor, enable, and manage Azure Security Center, and configure and monitor Azure Sentinel.
You can take Exam AZ-500: Microsoft Azure Security Technologies once you have completed the learning path to earn a certification.
Microsoft Endpoint Configuration Manager
Microsoft Endpoint Configuration Manager—which is part of Microsoft Endpoint Manager—helps you protect the on-premises devices, apps, and data that the people at your organization use to stay productive. Our newest module, Understand co-management using Microsoft Endpoint Configuration Manager, provides an in-depth look at how to enable co-management based on the implementation path that best suits your organization. You’ll also:
- Learn about the benefits of co-management
- Understand the co-management prerequisites
- Learn about paths to implement co-management
We’re excited to hear how you use these updated resources on your journey to certification!

by Scott Muniz | Nov 23, 2021 | Security
This article was originally posted by the FTC. See the original article here.
Giving Tuesday is a great time to show your gratitude by donating to help others. But you don’t want to give money to a fake charity or scammer (any day of the week).
Before you donate this Giving Tuesday ― and anytime you’re asked to give to charity:
- Research the cause or the organization. Search online for the name of the organization or cause with words like “review,” “scam,” or “complaint.” See if others have had good or bad experiences with the charity. Check out what charity watchdog groups say about that organization.
- Know that it’s ok to ask questions. If the request for a donation is over the phone, the caller should be able to answer critical questions. For example, how much of your donation will go to the program you want to help? Is the caller raising funds for a charity or for a Political Action Committee (PAC)? (Donations to PACs are NOT tax deductible.)
- Slow down. You don’t have to give over the phone, and anybody who pressures you might be someone you want to avoid giving to.
- Know who’s making the request. Don’t assume a request to donate is legitimate because a friend posted it on social media. Your friend might not personally know the charity or how it spends money. When you do your own research, double-check the exact name of the organization. Scammers will pick names or use website addresses that sound very similar to legitimate well-known charities.

This Giving Tuesday, and in this season of giving, consider starting with a plan for year-end donations. That way, you have time to do research, make your gifts, and tell anyone who asks that you’ve already given. Learn more at
ftc.gov/charity.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
![Pinning Records in Dynamics 365 CRM in Unified Interface [Quick Tip]](https://www.drware.com/wp-content/uploads/2021/03/cropped-cropped-21688204_10213848566435612_2978963762468624084_o.jpg)
by Priyesh Wagh | Nov 23, 2021 | Dynamics 365, Microsoft, Technology
Here’s how you can leverage Pinned Records in Dynamics 365 CRM.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Nov 22, 2021 | Technology
This article is contributed. See the original author and article here.
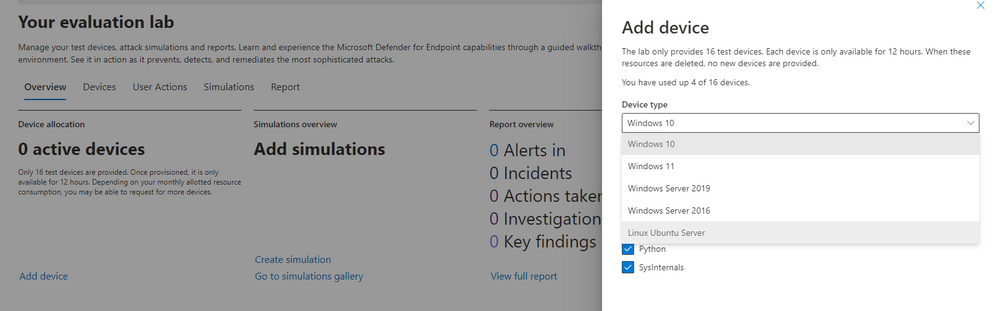
Microsoft Defender for Endpoint’s Evaluation Lab is an environment that allows security teams to seamlessly test their defense against threats. We are excited to share that the Evaluation Lab now supports adding Windows 11, Windows Server 2016, and Linux devices. In addition, we’d also like to announce a new partnership with Red Canary’s open-source simulation library, Atomic Red Team!
NOTE: Both updates are only available in the Microsoft 365 Defender portal at security.microsoft.com.
Expanded OS support
The evaluation lab now supports the following operating systems: Windows 10, Windows 11, Windows Server 2019, Windows Server 2016 and Linux (Ubuntu). To create a new device, simply select it within the “Add device” wizard. The new device will automatically be onboarded with no required additional steps.

Once created, you can connect to the device via RDP (Windows) or SSH (Linux). You can connect to a Linux device using any SSH client.
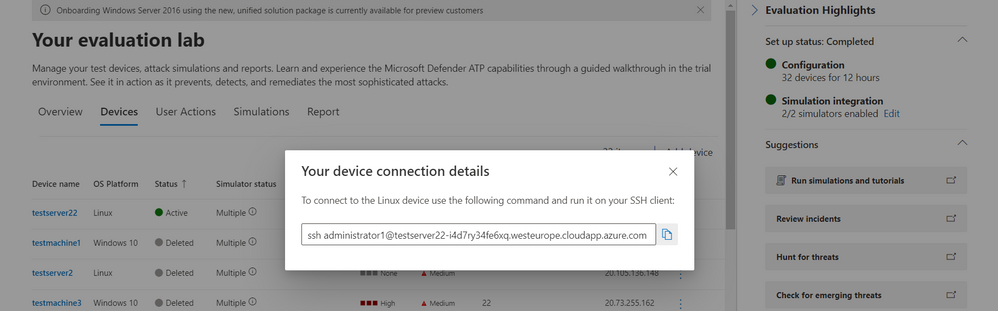
Atomic Red Team simulations
Powered by Red Canary, Atomic Red Team is an open-source library of tests that security teams can use to simulate adversarial activity in their environments. Atomic tests are simple – each test is mapped to a single MITRE ATT&CK® technique or sub-technique, most of them have no prerequisites, and many come with easy-to-use configuration and cleanup commands.
Evaluation Lab users can now use Atomic Red Team simulations to evaluate Microsoft Defender for Endpoint’s detection capabilities against both Windows and Linux threats. The simulations are provided as script files, so that security teams can choose to run them in the Evaluation lab or any other testing environment of their choice.
The first simulation, 2021 Threat Detection Report, executes tests according to Red Canary’s latest report of top Windows techniques associated with confirmed threats, as compiled from roughly 20,000 confirmed threats detected across customer environments.
The second simulation, Linux techniques, is a collection of simple tests compiled to allow security teams to evaluate Microsoft Defender for Endpoint’s detection capabilities against common Linux persistence, discovery, and defense evasion techniques.
We’re looking forward to you trying out the Evaluation Lab updates. Let us know your thoughts and feedback in the comments below or through the feedback tool in the portal!

 In the past 18 years of the National Do Not Call Registry, those of you signed up for the registry (244 million phone numbers right now) have reported millions upon millions of unwanted sales calls over the years. Here’s a quick look at what you’ve reported this year at DoNotCall.gov about the calls you’re getting:
In the past 18 years of the National Do Not Call Registry, those of you signed up for the registry (244 million phone numbers right now) have reported millions upon millions of unwanted sales calls over the years. Here’s a quick look at what you’ve reported this year at DoNotCall.gov about the calls you’re getting:


![Pinning Records in Dynamics 365 CRM in Unified Interface [Quick Tip]](https://www.drware.com/wp-content/uploads/2021/03/cropped-cropped-21688204_10213848566435612_2978963762468624084_o.jpg)




Recent Comments