by Contributed | Jun 17, 2021 | Technology
This article is contributed. See the original author and article here.
Today, we had a question from a customer asking if could be possible to connect to the Private Endpoint of Azure SQL DB or Synapse using Azure SQL External Tables.
The current answer is not, due to, as outbound connections for Azure SQL External Tables are executing from backend nodes that are outside of any private endpoint addressing space.
In this situation, there is not possible and won’t be available in a near future, as alternative, using Azure SQL Managed Instance that allows to use cross database queries among the database that belongs to the same instance or you could use Linked Server.
by Contributed | Jun 17, 2021 | Technology
This article is contributed. See the original author and article here.
This article was written by Future Kortor (@fkortor) and Bojan Magusic (@Bojan Magusic).
Intro
The purpose of this article is to empower organizations to understand the difference between Secure Score in Azure Security Center and Microsoft Secure Score in Microsoft 365 Security center. This article also touches briefly on the Identity Secure Score in the Azure AD Portal and Microsoft Secure Score for Devices in the Microsoft 365 Security center but going into details on these products is outside of the scope of this article.
Secure Score Functionality
As companies migrate more and more workloads to the cloud, it’s important to ensure that any resources in the public cloud are secured by adhering to industry standards and best practices. While companies might have existing solutions for their on-premises environment, security controls in the cloud differ from those on-premises. As no two company environments are the same, the question becomes where do you start with improving your security posture? What actions should you prioritize? Here is where Secure Score comes into play! The idea behind the Secure Score functionality isprovide you with a measurement that helps understand your current security posture as well as a list of actions you can take to improve your security posture. Secure Score, continuously assesses your environment. Meaning as you take actions to increase your security posture or deploy new resources, these changes will be reflected in your Secure Score. By implementing recommendations you’re adhering to best practices which will effectively increase the measurement and enhance
Depending on the workloads in question, you might be interested in having a measurement solely for your Microsoft SaaS workloads. On the other hand, you might be interested in a measurement for your PaaS and IaaS workloads in Azure (and even hybrid or multi-cloud scenarios). Hence, the need to have a different Secure Score for each scenario, which provides you a measurement for the specific type of cloud computing service that you are utilizing:
- Secure Score: applicable for PaaS, IaaS, hybrid and multi-cloud workloads.
- Microsoft Secure Score appliable for Microsoft SaaS workloads.
The table below aims to highlight the high-level difference between the two scores.
Service Models
|
Cloud Computing Service Provider
|
Category
|
Name of Secure Score Functionality
|
Administration Portal
|
SaaS
|
Microsoft 365
|
Identity, Devices and Apps
|
Microsoft Secure Score
|
Microsoft 365 Security Center
|
PaaS
|
Azure
|
Feature Coverage for Azure PaaS Services
|
Secure Score
|
Azure Security Center Dashboard
|
AWS
|
Provided by AWS Security Hub
|
GCP
|
Provided by GCP Security Command Center
|
IaaS
|
Azure
|
Supported Platforms
|
Secure Score
|
Azure Security Center dashboard
|
GCP, AWS
|
Supported Platforms
|
On-premise
|
Supported Platforms
|
Important Note: Microsoft 365 Secure Score is broken down further for each category (i.e. Identity Secure Score), however this falls out of scope of this article. More information on this topic can be found here.
Observation: With cloud adoption, identity has become the new perimeter – the control plane for your organization’s infrastructure, regardless of the type of cloud computing services that is being used (IaaS, PaaS, SaaS or even on-premises). Protecting your organization’s identities is key. Therefore, both scores place a high value on protecting your identities and enabling MFA. will have a positive impact on both scores. Beyond protecting identities, you can treat these two scores as separate.
Now, let’s dive into each one of these two scores!
Secure Score in Azure Security Center
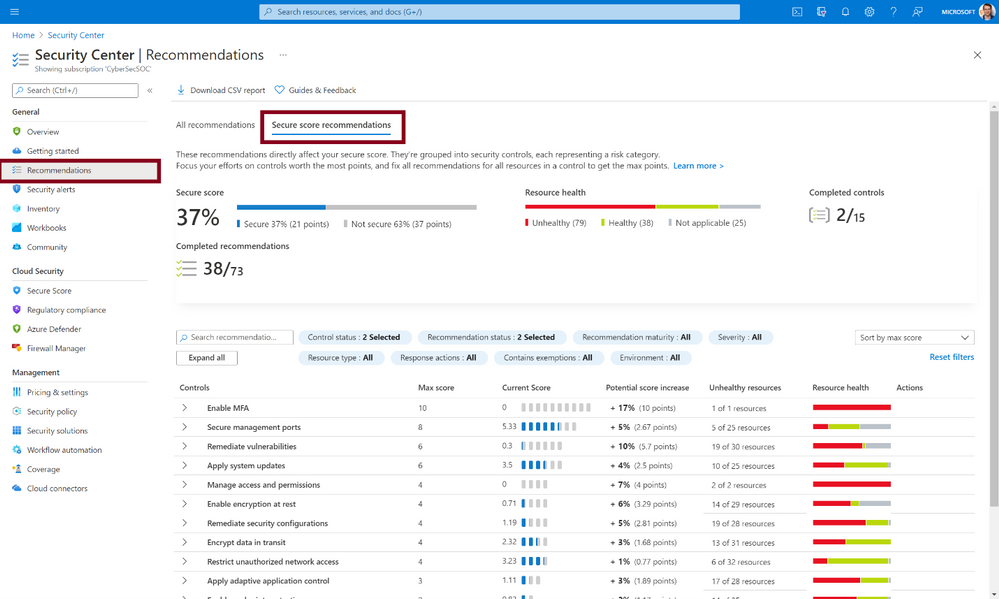
Secure Score is all about helping you improve your security posture with regards to your Azure resources (IaaS & PaaS) and even hybrid and multi-cloud workloads (i.e. AWS and GCP resources). When you select Secure Score in the Azure Security Center it shows you a list of security controls, where each security control has a list of recommendations. As you start addressing each one of those recommendations and you successfully address all the recommendations in a particular security control, your Secure Score will increase by a certain number of points (highlighted in the Potential score increase column). With your Secure Score increasing, your security posture will improve.

Figure 1: Secure Score in Azure Security Center Dashboard
Learn how Secure Score affects your governance.
Learn how to protect non-Azure resources.
Microsoft Secure Score in Microsoft 365 Security Center
Microsoft Secure Score is all about helping you improve your security posture with regards to Microsoft 365 services. The Microsoft Secure Score contains three distinct control and score categories:
- Identity (Azure Active Directory accounts and roles)
- Devices (Microsoft Defender for Endpoint)
- Apps (email and cloud apps, including Office 365 and Microsoft Cloud App Security)
At the time this was written, currently in Microsoft Secure Score there are recommendations for the following products:
- Microsoft 365 (including Exchange Online)
- Azure Active Directory
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Cloud App Security
- Microsoft Teams
Final Considerations:
The Secure Score functionality is all about helping you understand your current security posture and giving you a list of recommendations to proactively improve your security posture. Secure Score in Azure Security Center can help you understand how to improve the security posture of your Microsoft Azure IaaS and PaaS services (and even hybrid and multi-cloud). Microsoft Secure Score helps you understand how to improve your security posture when it comes to Identities, Devices and SaaS Applications in Microsoft 365. Both play a significant role in building a holistic security posture of your organization. Depending on how your organization is structured and which department (or team) is responsible for which workload, different teams and stakeholders might need to be involved to effectively improve the security posture of your organization. Hopefully, this article provides real value in understanding where you can find proactive guidance on how to improve your organizations security, depending on the workload in question. Remember, with each recommendation that you remediate, you are increasing your score and hardening your security defenses.
Reviewer:
@Yuri Diogenes, Principal PM
by Contributed | Jun 17, 2021 | Technology
This article is contributed. See the original author and article here.
Simulation Automations
The modern enterprise, of any size, faces a challenge that the logistics involved in planning a phishing simulation exercise are often laborious and time-consuming to implement. So to help address this we are pleased to announce some extra functionality in Attack Simulation Training that we feel will bring some added benefits in this space by:
- Helping move away from the traditional approach of running quarterly or annual simulations, to a more always on ‘educating’ model, by scheduling simulations to launch at a higher frequency (being mindful of simulation and training fatigue of course).
- Letting you schedule simulations up to a year in advance, so you decide the parameters of your simulations once in advance then you are good to go.
- Introducing some randomization elements around send times and dates to help combat the crowdsource effect that can occur when running large simulation exercises.
You can access the new functionality by selecting the “Simulation automations” tab within the main experience.

When you create a simulation automation, the experience walks you through a wizard experience just like creating a manual simulation, with the addition of a few new steps.
- Payload selection – Here we allow you to manually select what payloads you would like to be in scope for the simulations, or alternatively you can opt to randomize, where we will take a random payload from the available library and use that.
- Simulation schedule – Here, you get to decide if you would like a randomized schedule or a more predictable fixed schedule. What is the difference?
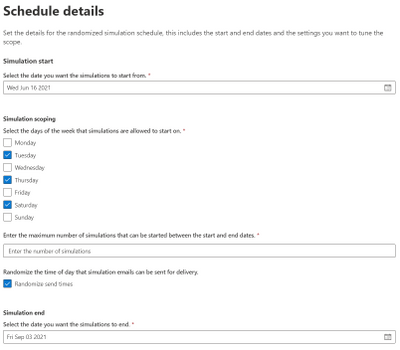
A randomized schedule lets you select a start date and end date, the days of the week you would like to be in scope for delivery and after how many simulation launches would you like the automation to stop.
Once the automation is enabled, the simulations will be launched on random days between the dates you have specified. You can also choose to randomize the send times (to negate the water cooler effect of users receiving simulation messages at the same time and chatting about it).
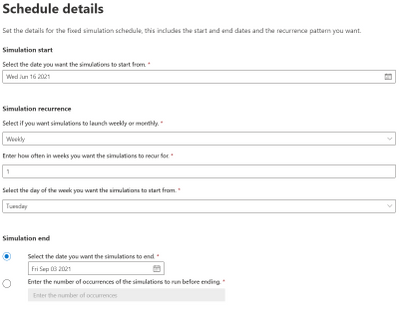
A fixed schedule allows you to run automations in a more controlled manner. We take the same approach – you specify a start date and end date – however this time you are prompted to enter the cadence, either weekly or monthly and the parameters of how often you would like them to launch.
For example, you can schedule an automation to run once a week for a period of 7 weeks starting every Monday, or you can also opt to end the simulations by a particular date or after a specific number of occurrences that you define.
Government Cloud and Regional Availability Updates
Attack Simulation Training is now live in GCC:
Starting 15 June 2021, Attack Simulation Training will be generally available in our Government Community Cloud. If your organization has Office 365 G5 GCC or Microsoft Defender for Office 365 (Plan 2) for Government, you can use Attack Simulation Training in Microsoft 365 Defender to run realistic attack scenarios in your organization as described here. Please note that the service is not yet available in GCC-High or DoD environments and this is part of our future roadmap.
Attack Simulation Training is now live in new regions:
Starting 16 June 2021, Attack Simulation Training will be generally available to tenants in Latin America, Brazil, and Switzerland that have Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2. For any guidance on running simulations, please start here. For frequently asked questions, please refer to our FAQ page.
We hope you find the enhancements useful as you continue your journey of end-user education and behavior change. If you have any comments or feedback be sure to let us know.

by Scott Muniz | Jun 17, 2021 | Security
This article was originally posted by the FTC. See the original article here.
 Instead of telling you a ghost story around a summer campfire, we have an all-too familiar tale to share: Myra’s grandson, Jon, is in Mexico for the summer. They video chat every week. One day, Myra gets a call from someone who says he’s Max, a friend of Jon’s: “He was arrested last night and needs $500 for bail.” Max says the police took Jon’s passport, so he’ll need another $700 to get it back. He says not to tell Jon’s parents or anyone else because Jon is embarrassed.
Instead of telling you a ghost story around a summer campfire, we have an all-too familiar tale to share: Myra’s grandson, Jon, is in Mexico for the summer. They video chat every week. One day, Myra gets a call from someone who says he’s Max, a friend of Jon’s: “He was arrested last night and needs $500 for bail.” Max says the police took Jon’s passport, so he’ll need another $700 to get it back. He says not to tell Jon’s parents or anyone else because Jon is embarrassed.
Myra is scared at first — but she’s heard a thing or two that makes her suspicious. So she thanks “Max” for his concern, hangs up, and calls Jon right away. Jon, it turns out, is on his way to class, not in jail. And “Max” is nothing but a scammer.
Family emergency scams like this try to scare people into sending money to help a loved one in trouble. The fraud can play out in many ways, but the hustle is the same: the caller lies, tries to scare you, and rushes you to pay so you don’t have time to think twice or check things out before you send money. And once you do that, you’ll never get it back.
To avoid family emergency scams:
- Resist the urge to act immediately — no matter how dramatic the story is.
- Call or message your loved one who (supposedly) contacted you. Even though the caller says not to. But use a number you know is right, not one the caller gives you.
- Never send cash, gift cards, cryptocurrency, or money transfers. Once the scammer gets the money, it’s gone!
If you spot this or any other scam, report it to the FTC at ReportFraud.ftc.gov.

Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.









Recent Comments