by Contributed | Dec 28, 2020 | Technology
This article is contributed. See the original author and article here.
Compute>Host groups
- Automatic host assignment for Azure dedicated host groups
Intune
- Updates to Microsoft Intune
Let’s look at each of these updates in greater detail.
Compute>Host groups
Automatic host assignment for Azure dedicated host groups
You can now simplify the deployment of Azure VMs in Dedicated Hosts by letting the platform select the host in the dedicated host group to which the VM will be deployed. Additionally, you can use Virtual Machine Scale Sets in conjunction with Dedicated Hosts. This will allow you to use scale sets across multiple dedicated hosts as part of a dedicated host group.
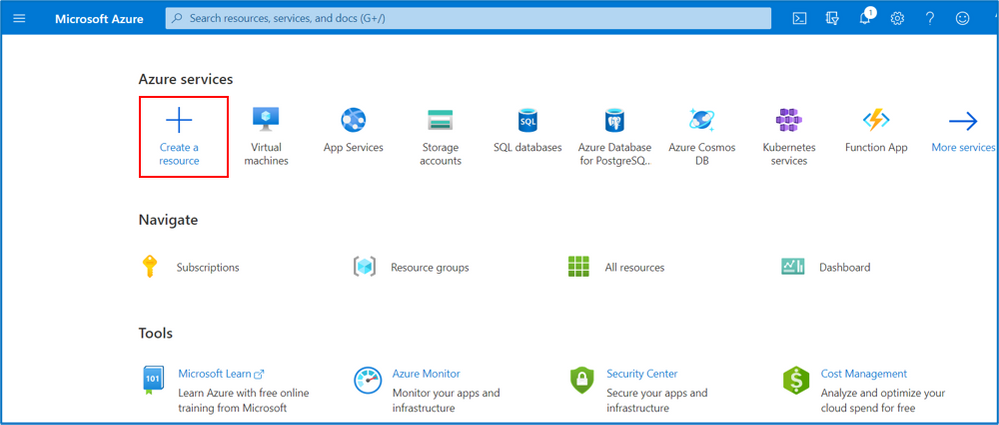
Step 1: Click “Create a resource”

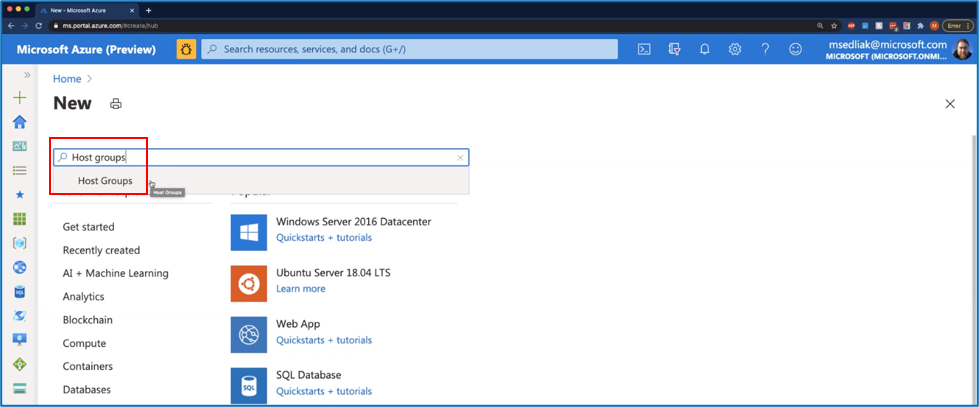
Step 2: Type in “Host groups” in the search box -> select “Host Groups” when it appears below the search box
Step 3: Click on the drop down arrow to the right of “Create” under “Host Groups” and select “Host Groups” from the drop down option

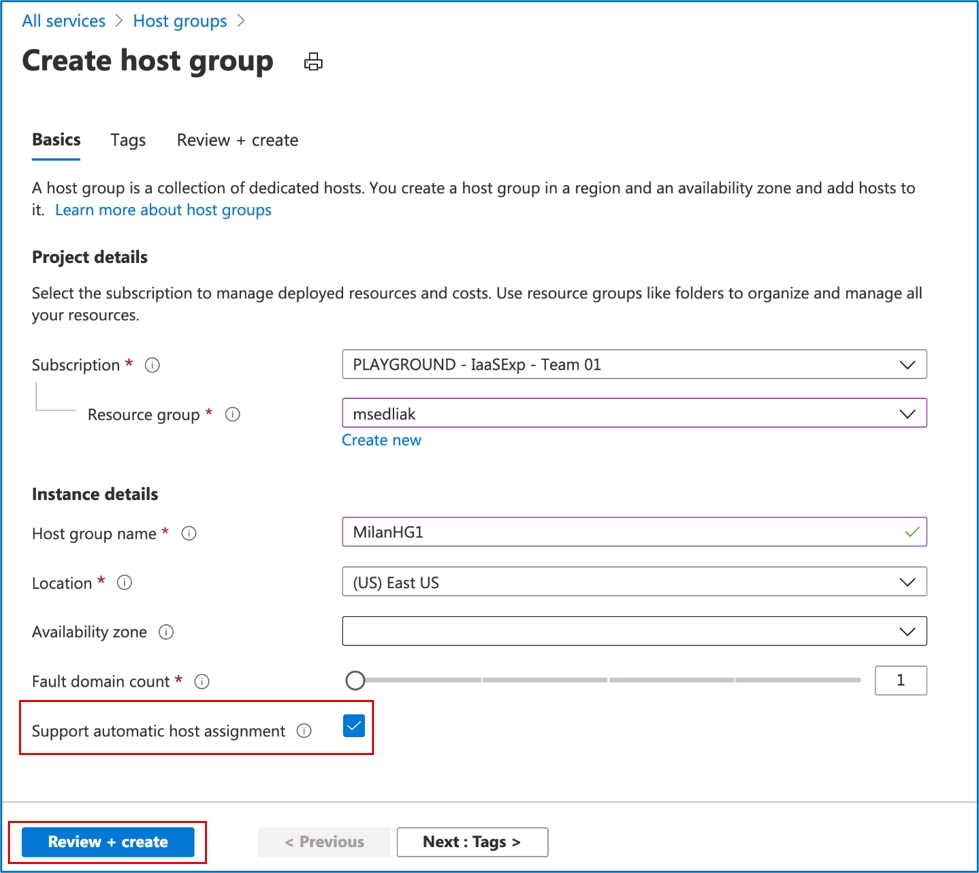
Step 4: Put in the required fields as marked with an * -> check the “Support automatic host assignment” box -> click on “Review + create”
Step 5: A preview of what will be created will appear -> click on “Create”

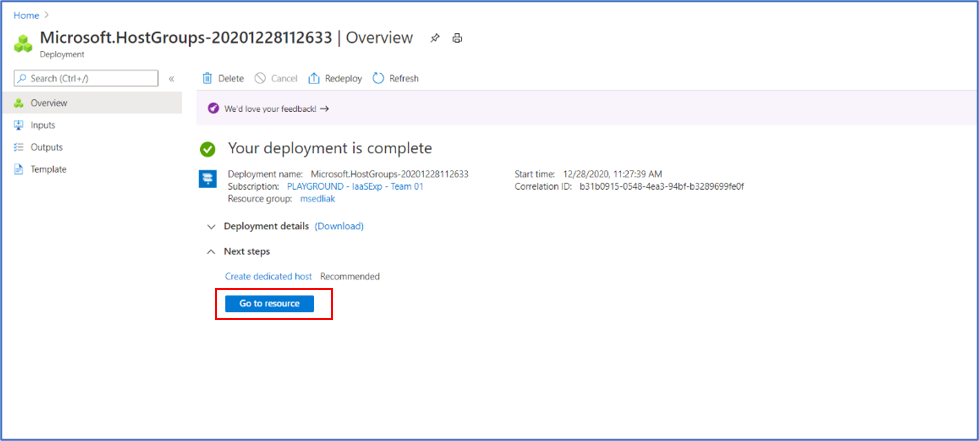
Step 6: When the host group deployment is complete, click “Go to resource” to open the host group so you can proceed to add a host
Step 7: Click on “Add host”
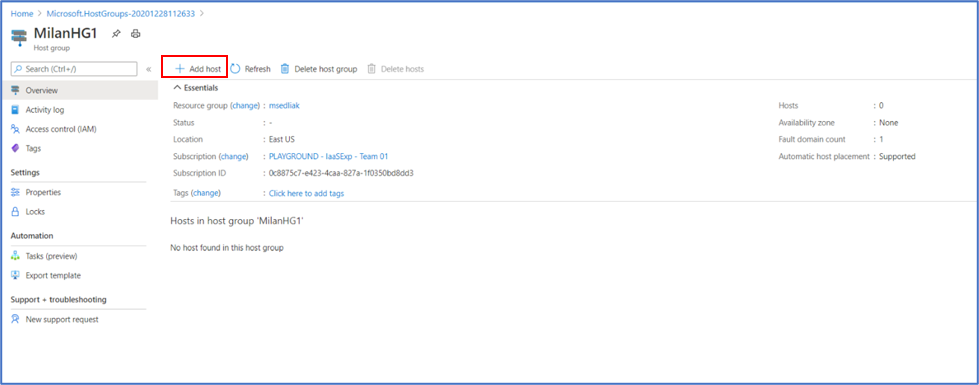
Step 8: Put in the required fields as marked with an *, making sure to select the same subscription ID and resource group as your host group -> click on “Review + create”
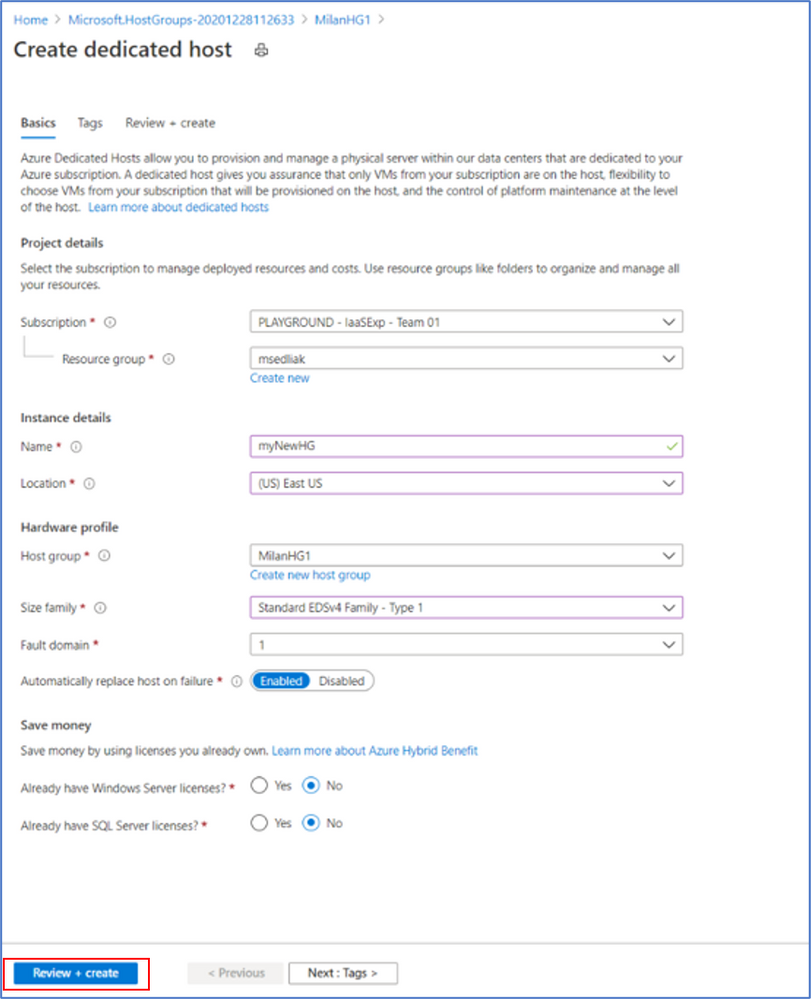
Step 9: A preview of what will be created will appear -> click on “Create”
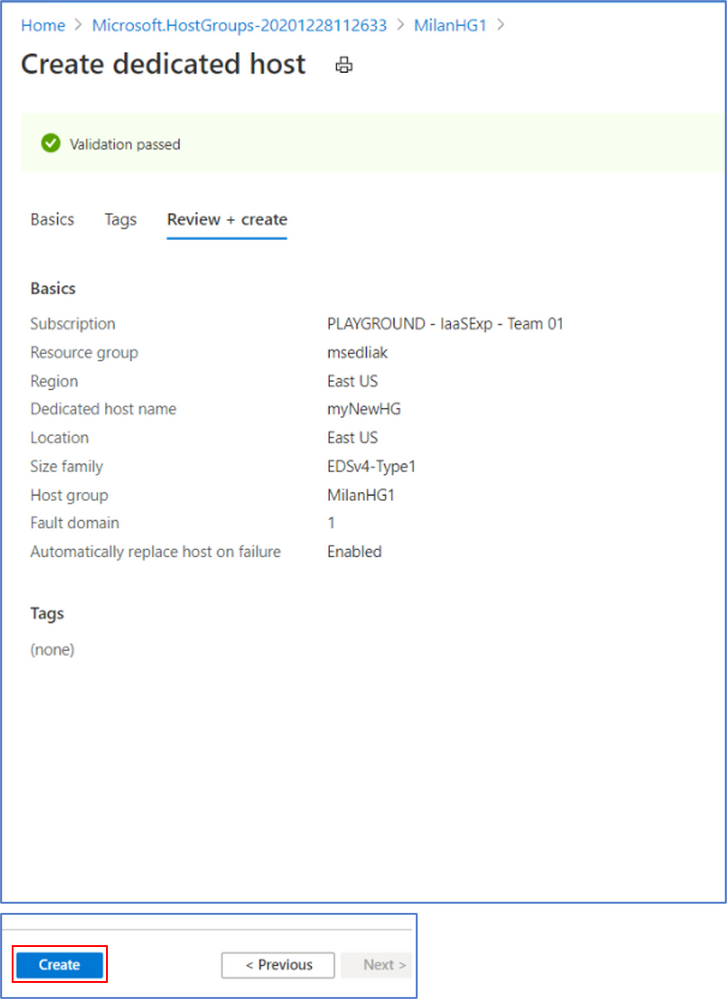
Step 10: Now that you have created a host group, you will need to create a Virtual Machine (or Virtual Machine Scale Set) to add to the host group.
- Click on “Create a resource” as in step 1 above
- Select “Compute” -> click on the “Virtual machine” icon
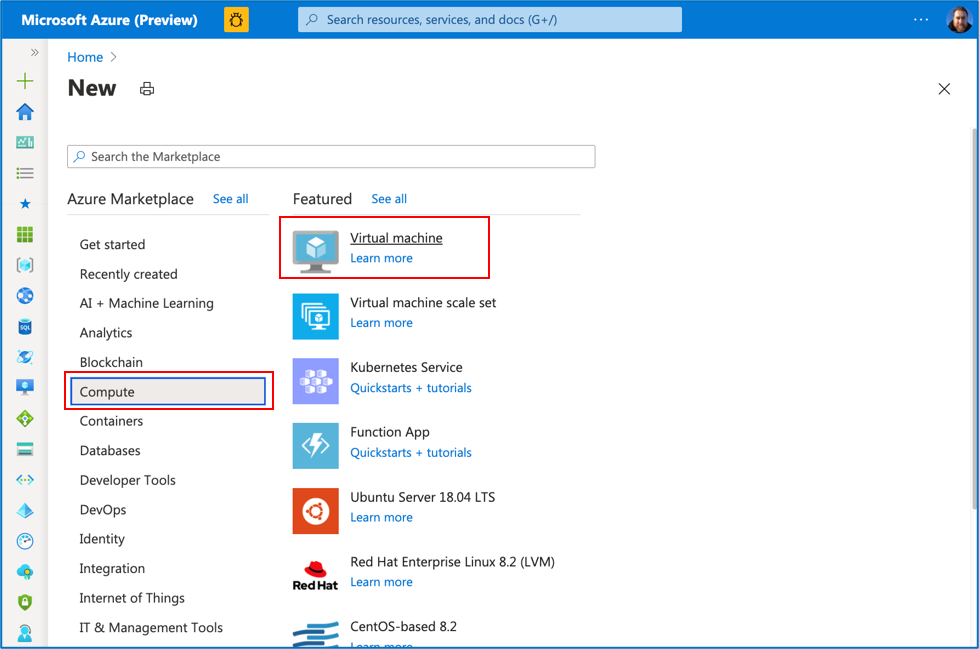
Step 11: Click “Create”

Step 12: Fill in all required information in the “Basics” tab
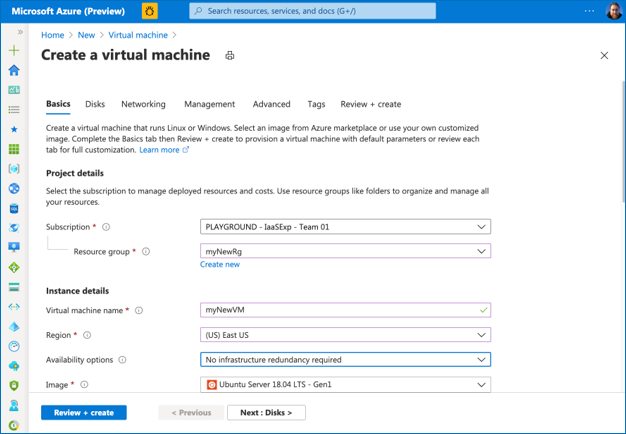
Step 13: Then click on the “Advanced” tab option
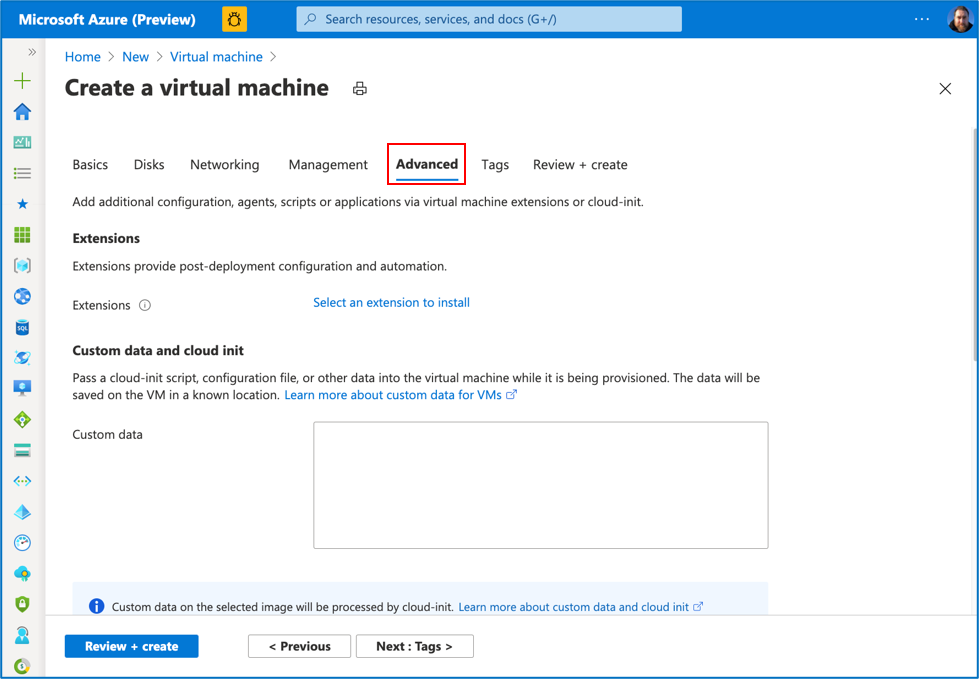
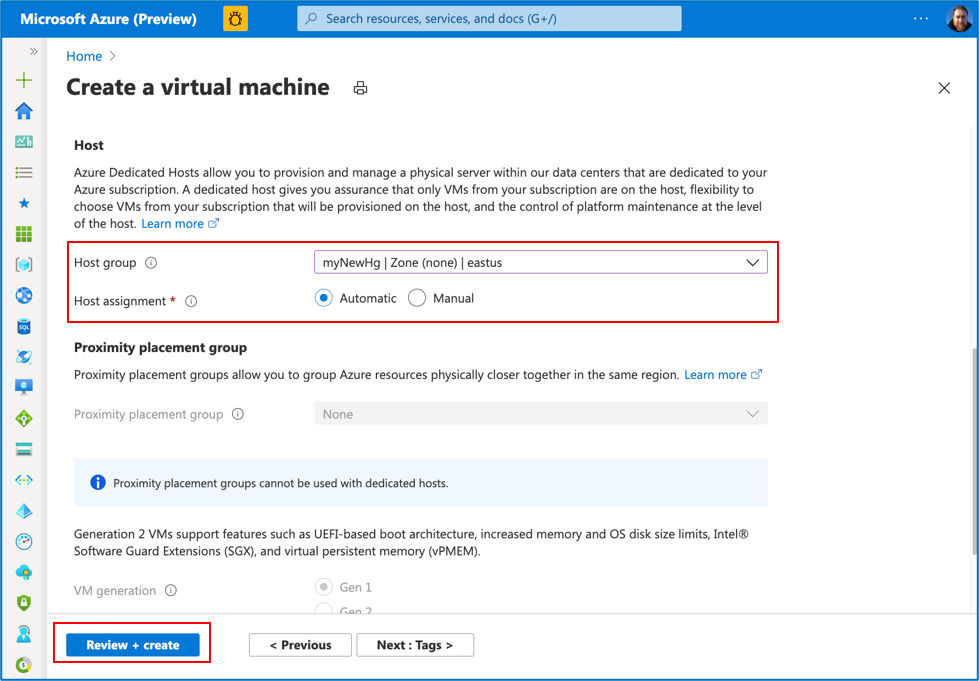
Step 14: Scroll down to the Host section:
- Select the Host group name from the drop down options
- Host assignment options will then appear; select “Automatic”
- Click on “Review + create”
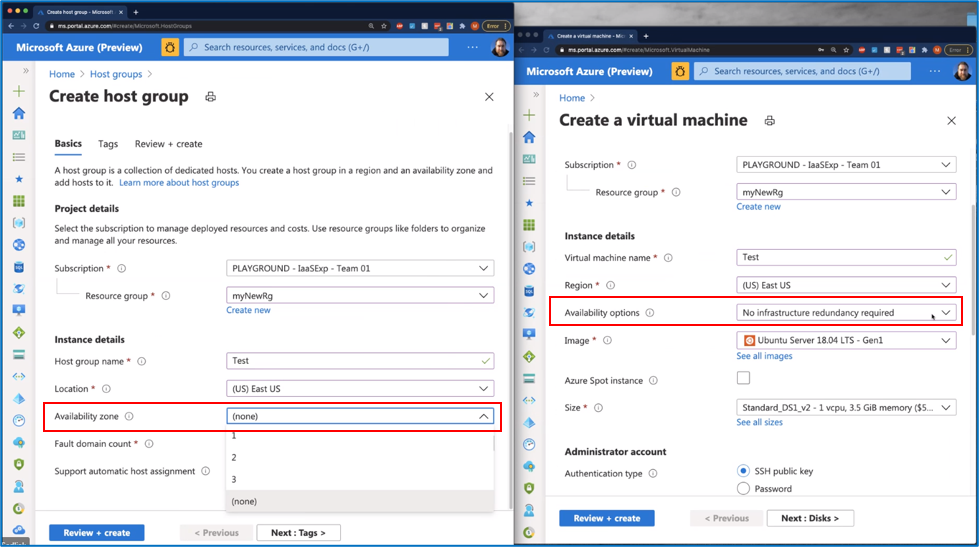
Important Notes:
- Make sure you use the same Subscription, Resource group, Region, and size Family as your dedicated host
- Due to the recent changes in the Create Virtual Machine experience, make sure that “Availability zone” in your Host group matches up with “Availability options” of your Virtual Machine (or Virtual Machine Scale Set). For example, if you use availability zone “1” in “Create a host group”, then select “Availability Zones” in “Availability options” and set “Availability zone” to “1”. However, if you use “(none)” in Availability zone in “Create host group”, then make sure you use “No infrastructure redundancy required” in Availability options in “Create a Virtual Machine”.
INTUNE
Updates to Microsoft Intune
The Microsoft Intune team has been hard at work on updates as well. You can find the full list of updates to Intune on the What’s new in Microsoft Intune page, including changes that affect your experience using Intune.
Azure portal “how to” video series
Have you checked out our Azure portal “how to” video series yet? The videos highlight specific aspects of the portal so you can be more efficient and productive while deploying your cloud workloads from the portal. Check out our most recently published videos:
Next steps
The Azure portal has a large team of engineers that wants to hear from you, so please keep providing us your feedback in the comments section below or on Twitter @AzurePortal.
Sign in to the Azure portal now and see for yourself everything that’s new. Download the Azure mobile app to stay connected to your Azure resources anytime, anywhere. See you next month!
by Contributed | Dec 28, 2020 | Technology
This article is contributed. See the original author and article here.
Introduction
A common ask from enterprise customers is the ability to monitor for the creation of Azure Subscriptions. This is not as easy as you might think so I wanted to walk you through a solution I’ve used to accomplish this. Below we will walk through creating an Azure Logic App that runs on a schedule and inserts the current subscriptions into Log Analytics. Once we have the data in Log Analytics we can either visualize new subscriptions or alert on them.
Step 1: Create a Service Principal
Our Logic App will utilize a Service Principal to query for the existing subscriptions. For this solution to work as intended you need to create a new Service Principal and then give them at least “Read” rights at your root Management Group.
If you’ve never created a service principal, you can follow this article:
Create an Azure AD app & service principal in the portal – Microsoft identity platform | Microsoft Docs
You’ll need the following information from the service principal:
- Application (client) id
- Tenant id
- Secret
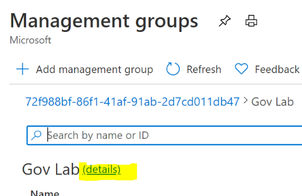
Once the service principal has been created you need to give it reader rights at the Management Group level.
Open the “Management Group” blade in the Azure portal. From the root Management Group click on the (details) link.

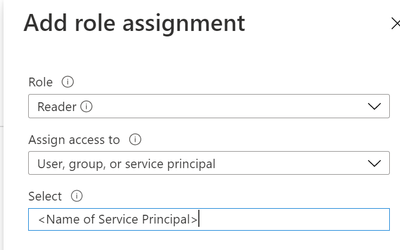
Click on “Access Control” | “Add” | “Add role assignment”

Grant the Service Principal the “Reader” role.
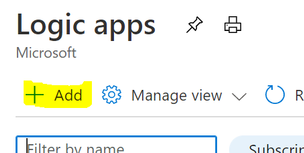
Step 2: Create the Logic App
In the Logic App blade click on “Add”
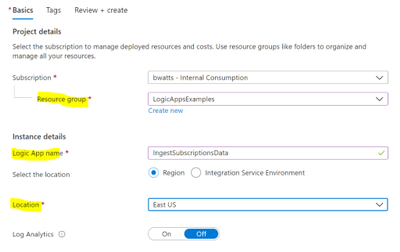
Fill in the required fields and create the Logic App.
In the Logic App Designer choose the “Recurrence” template.
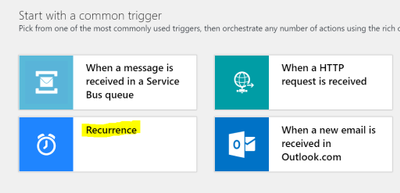
Configure the interval that you want to query for subscriptions. I chose to query every hour below. Then click on the “New step” button:
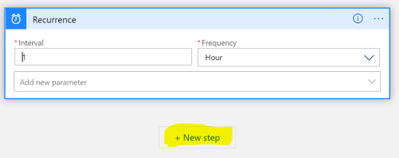
Search for “azure resource manager” and choose the “List subscriptions (preview)” action.
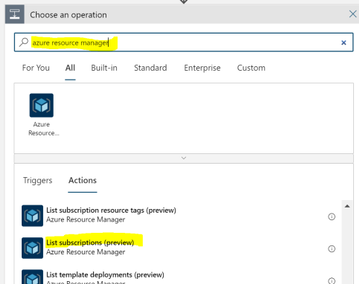
You want to connect with a service principal.
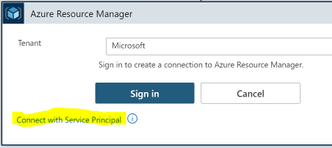
Fill in the information for your service principal (the “Connection Name” is just a display name):
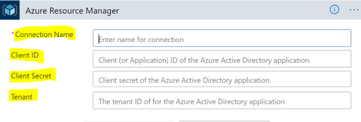
Note that this action doesn’t require any configuration besides setting up the connection. After configuring the service principal click on “New Step” and search for “Azure Log Analytics.” Choose the “Send Data (preview)” action.
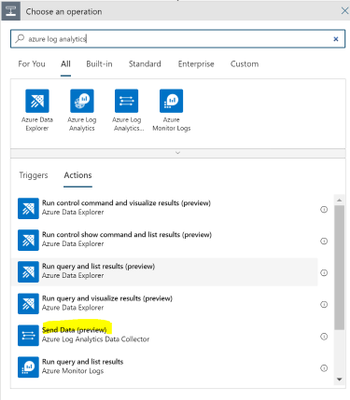
Connect to the Log Analytics workspace that you want to send the data to. You can get the workspace id and key within the Log Analytics blade in Azure:
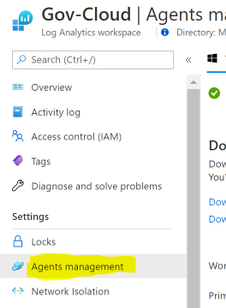
Once the connection is made to the Log Analytics Workspace you need to configure the connector:
- JSON Request Body: click in the box and then choose “Item” from the dynamic content
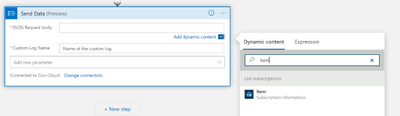
- Custom Log Name: Name of the log to be created in Log Analytics. Below I chose SubscriptionInventory
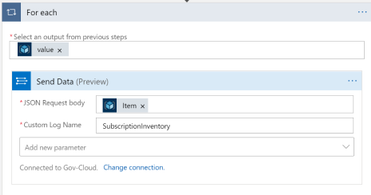
Note that when you choose “Item” it will put the “Send Data” action into a loop.
We can go ahead and save the Logic App and optionally run it to test the insertion of data into Log Analytics.
Step 3: Wait
This Logic App will need to run for a while before the data is useful. You can verify that the Logic App runs every hour and view the raw data in Log Analytics to verify everything is working.
Below is an example of viewing the table “SubscirptionInventory_CL” in Log Analytics
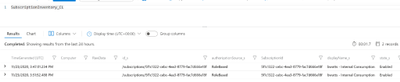
Step 4: Setting up Alerts
We will setup an alert for Subscriptions created in the last 4 hours.
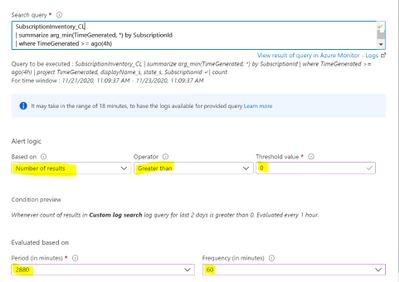
Below is the Kusto query we can use to find the subscriptions created in the last 4 hours:
SubscriptionInventory_CL
| summarize arg_min(TimeGenerated, *) by SubscriptionId
| where TimeGenerated >= ago(4h)
| project TimeGenerated, displayName_s, state_s, SubscriptionId
The key to this query is using the arg_min to get the first time we see the subscription added to log analytics. When we setup the alert we will look back a couple days and get the first occurrence of the subscription and then if the first occurrence is within the last 4 hours create an alert.
Now we are ready to create the alert within Azure Monitor. Open your Log Analytics Workspace and go to the Logs tab. Run the above query in Log Analytics and then click on “New alert rule”

**Note: I find this easier than going through Azure Monitor to create the alert because this selects your workspace and puts the correct query in the alert configuration.
You’ll see a red exclamation point next to the condition. Click on the condition to finish configuring the alert. Below are the parts you need to configure highlighted.
Now you just finish creating the alert. If you’ve never created an Azure Monitor Alert here is documentation to help you finish the process.
Create, view, and manage log alerts Using Azure Monitor – Azure Monitor | Microsoft Docs
**Note: Make sure you let the Logic App run for longer than the period you’re alerting on. In this example I’d need to let my Logic App run for at least 5 hours (4 hours is the alert threshold + 1 hour). The query relies on the history so if I run this before my Logic App has run long enough then it will trigger saying every subscription.
Step 5: Visualizing through Workbooks
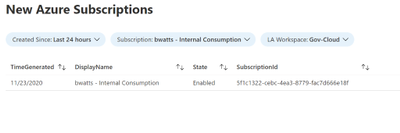
We can utilize a simple Azure Workbook to visualize the data in Log Analytics. The below workbook has the following parameters:
- Created Since: set this to show all the subscriptions created since this date
- Subscription: Filter down to the subscription that has the Log Analytics Workspace with the data
- LA Workspace: Select the Log Analytics workspace that you’re Logic App is putting data into
**Note: This workbook is assuming that the table name that your using is SubscriptionInventory_CL. If you’re using a different table name then you’ll need to modify the queries in the workbook.
Once you fill in the parameters there will be a simple table showing the day we detected the subscription, the display name, the state and the subscription id.
Open the Azure Monitor blade and go to the Workbook tab. Click on “New”
Click on the “Advanced Editor”
Replace the content from the following link:
https://raw.githubusercontent.com/bwatts64/Downloads/master/New_Subscriptions
Click on Apply:
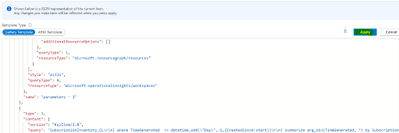
You can now verify that you’re able to visualize the data in Log Analytics. Once you’ve verified that click on “Save” to save the newly created workbook.

Summary
Monitoring new subscription creating in your Azure Tenant is a common ask by customers. Here we have utilized a Logic App to insert our subscription data into Log Analytics. From there we can both alert and visualize new subscriptions that are created in your environment.
by Contributed | Dec 28, 2020 | Technology
This article is contributed. See the original author and article here.
If you’re not already running your electronic design automation (EDA) backend workflows in the cloud, you’ve no doubt been seriously exploring options that would let you take advantage of the scale of cloud computing. One large hurdle for most cloud infrastructure architects has been getting tools, libraries, and datasets in to Azure from on-premises storage. The magnitude and complexity of data movement and other issues—such as securing your intellectual property (IP)—are challenging to many teams that could otherwise benefit from running EDA verification workloads on Azure high-performance computing (HPC) resources.
With the availability of the Azure HPC Cache service, and orchestration tools like Terraform from Hashicorp, it’s actually much easier than you may think to safely present your tools, libraries, IP design, and other data to large Azure HPC compute farms managed by Azure Cycle Cloud.
Use Azure HPC Cache for high throughput, low latency access to on-premises NAS
Azure HPC Cache is the pivotal service that brings together the high performance and low latency file access experience needed to be able to leverage Azure for efficiently running EDA backend tools that demand high processor clock rates and present considerable file I/O overhead. The intelligent-caching file service enables a hybrid-infrastructure environment, meaning that you can burst your EDA backend compute grid into Azure with reliably high-speed access to your on-premises network-attached storage (NAS) data. Azure HPC Cache eliminates the need to explicitly copy your tools, libraries, IP, and other proprietary information, from on-prem storage into the cloud or to permanently store it there. The cached copy can be destroyed and/or re-cached at essentially the press of the button.
Use Terraform to orchestrate infrastructure provisioning and management
The availability of new cloud orchestration tools like Hashicorp’s Terraform make it much simpler to deploy cloud resources. These tools work by letting you express your infrastructure as code (IaC) so that IT and cloud architects are do not have to continually reinvent the wheel to set up new or expanding cloud environments.
Hashicorp Terraform is one of the most common IaC tools—you may even already be using it to manage your on-premises infrastructure. It’s an open-source tool (downloadable from Hashicorp) that codifies infrastructure in modular configuration files that describe the topology of cloud resources. You can use it to simultaneously provision and manage both on-premises and cloud infrastructure, including Azure HPC Cache service instances. By helping you quickly, reliably, and precisely scale infrastructure up and down, IaC automation helps ensure that you’ll pay for resources only when you actually need and use them.
Use Azure CycleCloud for compute scalability, pay-for-only-what-you-use elasticity, and because it’s easier than you thought
The obvious advantages to using Azure include unlimited access to virtual machines (VMs) and CPU cores that let you scale out backend EDA workflow jobs as fast and as parallel as possible. Azure CycleCloud can connect to IBM LSF to manage the compute farm deployment in unison with your LSF job scheduling. The HPC Cache component lets you maintain control of your data while providing low-latency storage access to keep cloud computing CPU cores busily productive. With high-speed access to all required data, your queued-up verification jobs will run continuously, and you’ll minimize paying for idle cloud resources.
Summarizing the benefits, Azure HPC Cache and automation tools like Terraform let you more easily take advantage of cloud compute by:
- Providing high-speed access to on-premises data with scalability to support tens of thousands of cloud-based compute cores
- Minimizing complex data movement processes
- Streamlining provisioning and management for rapid deployment and to maintain the familiarity of existing workflows and processes—push-button deployment means electronic design architects don’t have to change what they’re used to doing
- Ensuring proprietary data does not linger in the cloud afer compute tasks are finished
Azure solutions truly democratize technology, making massive, on-demand compute resources accessible to EDA businesses of every size, from small designers to mid-size semiconductor manufacturers and the largest chip foundries. With access to tens of thousands of compute cores in Azure, companies can meet surge compute demand with the elasticity they need.
Use validated architectures
Lest you’re concerned about blazing new territory, be assured that EDA customers are already running many popular tool suites in Azure. And, they’ve validated those workloads against the HPC Cache. To give you an idea of results, for workloads running such tools as Ansys RedHawk-SC, Cadence Xcelium, Mentor Calibre DRC, Synopsys PrimeTime, and Synopsys TetraMAX, users report behavior and performance similar to or better than running the same backend workloads on their own datacenter infrastructure. Our Azure and HPC Cache teams also routinely work with EDA software tools vendors to optimize design solutions for Azure deployment.
Build on reference architectures
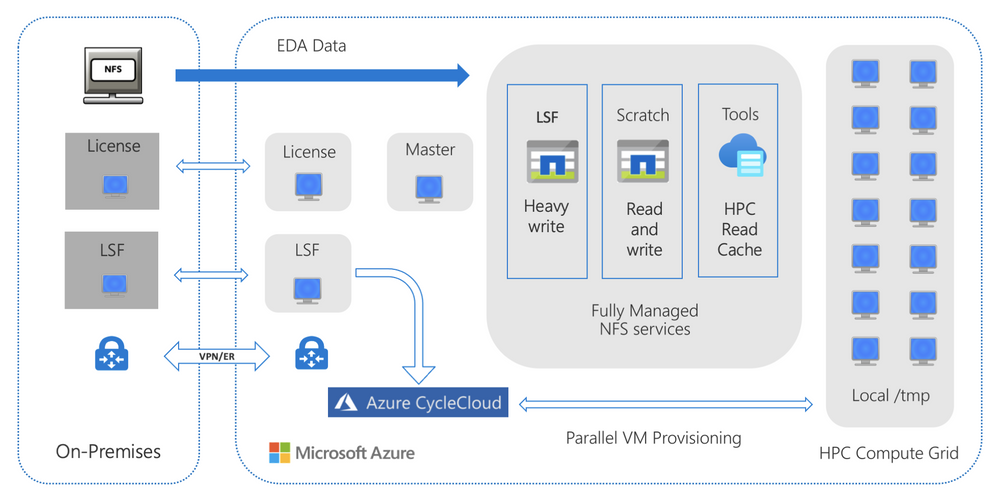
The reference architectures below illustrate how you can use HPC Cache for EDA workloads in both cloud-bursting (hybrid) and fully-on-Azure architectures.
 Figure 1. A general reference architecture for fully managed caching of on-premises NAS with the Azure HPC Cache service to burst verification workloads to Azure compute.
Figure 1. A general reference architecture for fully managed caching of on-premises NAS with the Azure HPC Cache service to burst verification workloads to Azure compute.
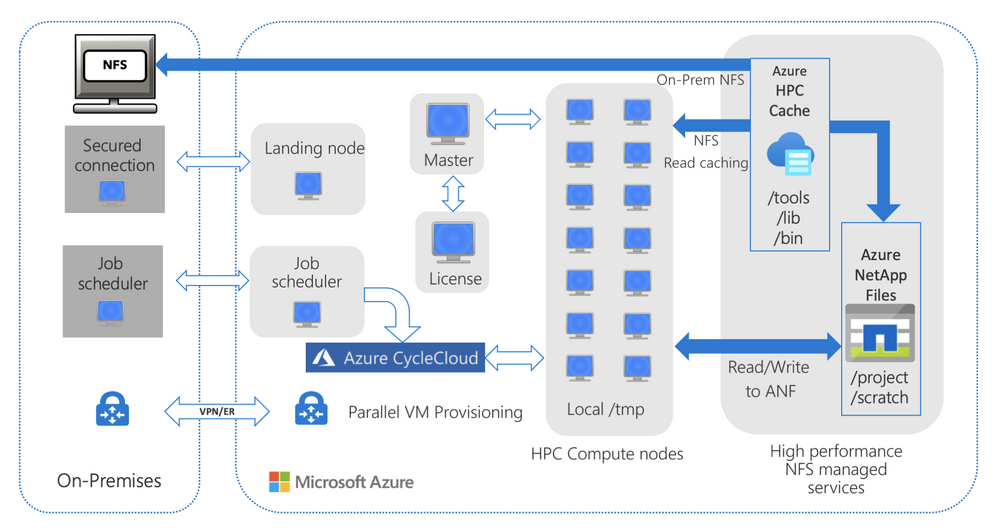 Figure 2. A general reference architecture with on-premises NAS and HPC Cache optimizing read access to tools and libraries hosted on-premises, and project data hosted on ANF.
Figure 2. A general reference architecture with on-premises NAS and HPC Cache optimizing read access to tools and libraries hosted on-premises, and project data hosted on ANF.
Access additional resources
Follow the links below for additional information about Azure HPC Cache and related tools and services.
Azure for EDA
https://azure.microsoft.com/en-us/solutions/high-performance-computing/silicon/#solutions
Infrastructure as Code
https://docs.microsoft.com/en-us/azure/devops/learn/what-is-infrastructure-as-code
Azure HPC Cache
https://azure.microsoft.com/en-us/services/hpc-cache/
Terraform with Azure
https://docs.microsoft.com/en-us/azure/terraform/terraform-overview
Azure CycleCloud LSF Connector
https://docs.microsoft.com/en-us/azure/cyclecloud/lsf
Terraform and HPC Cache
https://github.com/Azure/Avere/tree/main/src/terraform/examples/HPC%20Cache
As always, we appreciate your comments. If you need additional information about Azure HPC Cache services, you can visit our github page or message our team through the tech community.

by Contributed | Dec 28, 2020 | Technology
This article is contributed. See the original author and article here.

The end of #DevDecember is near, and we’re ready to kick off 2021. To help you mark the transition and start anew, we’ve created digital New Year postcards in three designs that you can adapt and share with fellow devs, friends, and family. Download the New Year cards on our #DevDecember homepage.

Before we hit send, let’s take one more look in the rearview mirror.
Each week, we asked for your #DevDecember thoughts, starting with the ways you grew this year as developer, and moving on to what communities had your back, what inspired you, and what projects and challenges you were most looking forward to in 2021. Check out what fellow devs shared.
Week 1: What helped us grow professionally
Beginner’s series to JavaScript
Taking your first steps toward mastering a new programming language is exciting, but it can also feel overwhelming. To help you get started with JavaScript, we’ve created short and easy-to-consume videos that break down the key concepts you need to know.
Start watching the series
Agrotech IoT workshop
Want to grow your professional IoT skills? Your first stop may be the garden. Get your hands dirty with a workshop on how to build an internet-connected device to gather soil moisture data that will tell you (by lighting up an LED) if a plant needs watering.
Start digging in
Bringing browser developer tools to Visual Studio Code
One of our favorite releases in 2020 was the Microsoft Edge Tools for VS Code extension, designed to simplify workflows. Connect to an existing browser instance, start a new one, or use a “headless” browser.
Explore the extension
Building a first “Power Apps” app
@JoeCamp13 built an app to track inventory entirely with Power Apps. His explanation of how he did it, is illustrated with screenshots so you can follow along.
Start the walkthrough
Week 2: How the community came together
Live coding community
Learn from the best on Twitch! Watch devs code live, and connect and ask questions in real time. Find out how joining Microsoft’s virtual community can speed up learning new skills and languages.
Watch an intro video on Twitch and live coding (25 min)
The ReadMe Project
Behind the open-source code used by millions of people are the unseen efforts of countless contributors, who put in long hours to build software, fix issues, and more. Meet some of the people making contributions, including veterans who find the teamwork required for open-source collaboration a natural fit.
Read their inspiring stories
Remote collaboration with Live Share in Visual Studio Code
With Live Share, you can instantly share your project with fellow developers. No need to clone a repo or set up the environment. It’s a one-stop, real-time collaboration tool for pairing, code reviews, technical interviews, boot camps, and more.
Watch a short video on how to set up Live Share (5 min)
From the open source cookbook
Cooking up code is a bit like developing food recipes. The more people who test your recipe, the more it’s likely to guarantee that what lands on your plate is what you intended.
Browse our crowdsourced cookbook with free code recipes
Week 3: What inspired us
IoT and Azure help with family chores
With everyone at home, dishes pile up faster, garbage accumulates, and chores must be done more frequently. To keep track in real time what chores need to be completed and by when, Scott Hanselman built an IoT solution, using sensors, a web-based heatmap, and notifications.
Check out how to build Chores IoT
The Developer Activity Book
Taking your mind off what you’re working on is sometimes the best way to get inspiration. The Developer Activity Book features family-friendly fun, including seven coloring pages, a crossword puzzle, a word search, and a logic puzzle.
Get the Developer Activity Book
2020 Imagine Cup World Championship
The Imagine Cup World Championship encourages students across the globe to innovate using Microsoft Azure. Finalist teams created technological solutions to tackle pressing global issues. Get inspired by their passion and the incredible projects they created.
Watch the recap (3 minutes)
Plastic Origins Project
Most of the plastic that ends up in the oceans comes from inland sources. In this episode of CodeStories, Seth Juarez shows how developers can use AI to address this problem by monitoring microplastic and tracking ocean-bound plastic waste.
Watch the video (13 minutes)
Week 4: Looking forward to new challenges
Microsoft Learn Student Ambassadors
In 2020, we launched the Microsoft Learn Student Ambassadors program, where students can join a global community of peers, connect with mentors, learn the skills they need to land a dream job, and make a difference. Applications are open year-round, and we will accept hundreds more Student Ambassadors in 2021.
Learn more about the program
Speed up development
What does it take to go from idea to development without detours? Best-in-class tools and product management are two of the things that boost velocity, a new McKinsey report found. Find out how to get stuff done faster in 2021 with this and other real-world strategies.
Read the McKinsey report on how to boost developer velocity
Learning to code
Intimidated by the idea of learning a new programming language? We’ve got a few ways to make it easier so 2021 is the year you make it happen. Download Visual Studio Code, then dive into tutorials and other resources that you can go through at your own pace.
Learn to program with Visual Studio Code
Predicting meteor showers using Python and VS Code
Shooting for the moon in 2021? This session may provide inspiration. Dr G explains what meteor showers are and how data science is used to predict these events. No coding experience required.
Watch the recorded live stream (50 min)
Finally, before we raise a glass, cup, or mug to 2021, we’d like to thank all of you who have shared #DevWithABev pictures during the month. We’ve discovered a few new beverages and flavors to sip  .
.
Here’s to new projects and new adventures! Happy New Year!
by Scott Muniz | Dec 28, 2020 | Security, Technology
This article is contributed. See the original author and article here.
| abb — symphony_+_historian |
In Symphony Plus Operations and Symphony Plus Historian, some services can be vulnerable to privilege escalation attacks. An unprivileged (but authenticated) user could execute arbitrary code and result in privilege escalation, depending on the user that the service runs as. |
2020-12-22 |
4.6 |
CVE-2020-24676
MISC
MISC |
| abb — symphony_plus_historian |
Vulnerabilities in the S+ Operations and S+ Historian web applications can lead to a possible code execution and privilege escalation, redirect the user somewhere else or download unwanted data. |
2020-12-22 |
6.5 |
CVE-2020-24677
MISC
MISC |
| abb — symphony_plus_historian |
An authenticated user might execute malicious code under the user context and take control of the system. S+ Operations or S+ Historian database is affected by multiple vulnerabilities such as the possibility to allow remote authenticated users to gain high privileges. |
2020-12-22 |
6.5 |
CVE-2020-24678
MISC
MISC |
| abb — symphony_plus_historian |
In S+ Operations and S+ Historian, the passwords of internal users (not Windows Users) are encrypted but improperly stored in a database. |
2020-12-22 |
4.6 |
CVE-2020-24680
MISC
MISC |
| advanced_comment_system_project — advanced_comment_system |
ACS Advanced Comment System 1.0 is affected by Directory Traversal via an advanced_component_system/index.php?ACS_path=..%2f URI. |
2020-12-23 |
5 |
CVE-2020-35598
MISC |
| apache — pulsar_manager |
In the Pulsar manager 0.1.0 version, malicious users will be able to bypass pulsar-manager’s admin, permission verification mechanism by constructing special URLs, thereby accessing any HTTP API. |
2020-12-18 |
4 |
CVE-2020-17520
MISC |
| apache — tomee |
If Apache TomEE 8.0.0-M1 – 8.0.3, 7.1.0 – 7.1.3, 7.0.0-M1 – 7.0.8, 1.0.0 – 1.7.5 is configured to use the embedded ActiveMQ broker, and the broker config is misconfigured, a JMX port is opened on TCP port 1099, which does not include authentication. CVE-2020-11969 previously addressed the creation of the JMX management interface, however the incomplete fix did not cover this edge case. |
2020-12-18 |
6.8 |
CVE-2020-13931
MLIST
MLIST
MISC |
| atlassian — crucible |
Affected versions of Atlassian Crucible allow remote attackers to impact the application’s availability via a Denial of Service (DoS) vulnerability in the file upload request feature of code reviews. The affected versions are before version 4.7.4, and from version 4.8.0 before 4.8.5. |
2020-12-21 |
4 |
CVE-2020-29447
MISC |
| bilanc — bilanc |
An issue was discovered in Programi Bilanc build 007 release 014 31.01.2020 and possibly below. It relies on broken encryption with a weak and guessable static encryption key. |
2020-12-23 |
5 |
CVE-2020-11719
MISC
FULLDISC |
| bilanc — bilanc |
An issue was discovered in Programi Bilanc build 007 release 014 31.01.2020 and below. Its software-update packages are downloaded via cleartext HTTP. |
2020-12-23 |
5.8 |
CVE-2020-11718
MISC
FULLDISC |
| bilanc — bilanc |
Programi Bilanc Build 007 Release 014 31.01.2020 supplies a .exe file containing several hardcoded credentials to different servers that allow remote attackers to gain access to the complete infrastructure including the website, update server, and external issue tracking tools. |
2020-12-21 |
5 |
CVE-2020-8995
FULLDISC
MISC |
| bitcoinsv — bitcoin_sv |
Bitcoin SV before 0.1.1 allows uncontrolled resource consumption when receiving sendheaders messages. |
2020-12-23 |
5 |
CVE-2018-1000892
MISC |
| bitcoinsv — bitcoin_sv |
Bitcoin SV before 0.1.1 allows uncontrolled resource consumption when receiving messages with invalid checksums. |
2020-12-23 |
5 |
CVE-2018-1000891
MISC |
| bitcoinsv — bitcoin_sv |
Bitcoin SV before 0.1.1 allows uncontrolled resource consumption when deserializing transactions. |
2020-12-23 |
5 |
CVE-2018-1000893
MISC |
| crk — business_platform |
CRK Business Platform <= 2019.1 allows reflected XSS via erro.aspx on ‘CRK’, ‘IDContratante’, ‘Erro’, or ‘Mod’ parameter. This is path-independent. |
2020-12-23 |
4.3 |
CVE-2020-13969
MISC |
| d-link — dsl2888a_firmware |
An issue was discovered on D-Link DSL-2888A devices with firmware prior to AU_2.31_V1.1.47ae55. Lack of authentication functionality allows an attacker to assign a static IP address that was once used by a valid user. |
2020-12-22 |
5.4 |
CVE-2020-24580
MISC
CONFIRM |
| d-link — dsl2888a_firmware |
An issue was discovered on D-Link DSL-2888A devices with firmware prior to AU_2.31_V1.1.47ae55. An unauthenticated attacker could bypass authentication to access authenticated pages and functionality. |
2020-12-22 |
5.8 |
CVE-2020-24579
MISC
CONFIRM |
| dbdeployer — dbdeployer |
DBdeployer is a tool that deploys MySQL database servers easily. In DBdeployer before version 1.58.2, users unpacking a tarball may use a maliciously packaged tarball that contains symlinks to files external to the target. In such scenario, an attacker could induce dbdeployer to write into a system file, thus altering the computer defenses. For the attack to succeed, the following factors need to contribute: 1) The user is logged in as root. While dbdeployer is usable as root, it was designed to run as unprivileged user. 2) The user has taken a tarball from a non secure source, without testing the checksum. When the tarball is retrieved through dbdeployer, the checksum is compared before attempting to unpack. This has been fixed in version 1.58.2. |
2020-12-21 |
4 |
CVE-2020-26277
MISC
CONFIRM |
| egavilanmedia — user_registration_&_login_system_with_admin_panel |
EgavilanMedia User Registration & Login System with Admin Panel 1.0 is affected by Cross Site Request Forgery (CSRF) to remotely gain privileges in the User Profile panel. An attacker can update any user’s account. |
2020-12-21 |
6 |
CVE-2020-35273
MISC
MISC |
| egavilanmedia — user_registration_and_login_system_with_admin_panel |
Cross Site Scripting (XSS) vulnerability via the ‘Full Name’ parameter in the User Registration section of User Registration & Login System with Admin Panel 1.0. |
2020-12-23 |
4.3 |
CVE-2020-35252
MISC |
| emerson — x-stream_enhanced_xegp_firmware |
Emerson Rosemount X-STREAM Gas AnalyzerX-STREAM enhanced XEGP, XEGK, XEFD, XEXF – all revisions, The affected products are vulnerable to improper authentication for accessing log and backup data, which could allow an attacker with a specially crafted URL to obtain access to sensitive information. |
2020-12-21 |
5 |
CVE-2020-27254
MISC |
| foxitsoftware — foxit_reader |
A use-after-free vulnerability exists in the JavaScript engine of Foxit Software’s PDF Reader, version 10.1.0.37527. A specially crafted PDF document can trigger the reuse of previously free memory which can lead to arbitrary code execution. An attacker needs to trick the user to open the malicious file to trigger this vulnerability. If the browser plugin extension is enabled, visiting a malicious site can also trigger the vulnerability. |
2020-12-22 |
6.8 |
CVE-2020-13570
MISC |
| foxitsoftware — foxit_reader |
A type confusion vulnerability exists in the JavaScript engine of Foxit Software’s Foxit PDF Reader, version 10.1.0.37527. A specially crafted PDF document can trigger an improper use of an object, resulting in memory corruption and arbitrary code execution. An attacker needs to trick the user to open the malicious file to trigger this vulnerability. If the browser plugin extension is enabled, visiting a malicious site can also trigger the vulnerability. |
2020-12-22 |
6.8 |
CVE-2020-13547
MISC |
| foxitsoftware — foxit_reader |
A use after free vulnerability exists in the JavaScript engine of Foxit Software’s Foxit PDF Reader, version 10.1.0.37527. A specially crafted PDF document can trigger reuse of previously free memory which can lead to arbitrary code execution. An attacker needs to trick the user to open the malicious file to trigger this vulnerability. If the browser plugin extension is enabled, visiting a malicious site can also trigger the vulnerability. |
2020-12-22 |
6.8 |
CVE-2020-13560
MISC |
| foxitsoftware — foxit_reader |
A use after free vulnerability exists in the JavaScript engine of Foxit Software’s Foxit PDF Reader, version 10.1.0.37527. A specially crafted PDF document can trigger reuse of previously free memory which can lead to arbitrary code execution. An attacker needs to trick the user to open the malicious file to trigger this vulnerability. If the browser plugin extension is enabled, visiting a malicious site can also trigger the vulnerability. |
2020-12-22 |
6.8 |
CVE-2020-13557
MISC |
| google — android |
An issue was discovered on LG mobile devices with Android OS 8.0, 8.1, 9.0, and 10 software. There is a WebView SSL error-handler vulnerability. The LG ID is LVE-SMP-200026 (December 2020). |
2020-12-18 |
4.6 |
CVE-2020-35554
MISC |
| google — android |
An issue was discovered on LG mobile devices with Android OS 10 software. When a dual-screen configuration is supported, the device does not lock upon disconnection of a call with the cover closed. The LG ID is LVE-SMP-200027 (December 2020). |
2020-12-18 |
4.4 |
CVE-2020-35555
MISC |
| hcltech — domino |
HCL Domino v9, v10, v11 is susceptible to an Information Disclosure vulnerability in XPages due to improper error handling of user input. An unauthenticated attacker could exploit this vulnerability to obtain information about the XPages software running on the Domino server. |
2020-12-22 |
5 |
CVE-2020-14270
MISC |
| hcltech — domino |
HCL Verse v10 and v11 is susceptible to a Stored Cross-Site Scripting (XSS) vulnerability due to improper handling of message content. An unauthenticated remote attacker could exploit this vulnerability using specially-crafted markup to execute script in a victim’s web browser within the security context of the hosting Web site and/or steal the victim’s cookie-based authentication credentials. |
2020-12-18 |
4.3 |
CVE-2020-4080
MISC |
| hcltech — hcl_inotes |
HCL iNotes is susceptible to a Tabnabbing vulnerability caused by improper sanitization of message content. A remote unauthenticated attacker could use this vulnerability to trick the end user into entering sensitive information such as credentials, e.g. as part of a phishing attack. |
2020-12-21 |
4.3 |
CVE-2020-14225
MISC |
| hcltech — hcl_inotes |
HCL iNotes v9, v10 and v11 is susceptible to a Stored Cross-Site Scripting (XSS) vulnerability due to improper handling of message content. An unauthenticated remote attacker could exploit this vulnerability using specially-crafted markup to execute script in a victim’s web browser within the security context of the hosting Web site and/or steal the victim’s cookie-based authentication credentials. |
2020-12-18 |
4.3 |
CVE-2020-14271
MISC |
| hcltechsw — hcl_client_application_access |
A vulnerability in the input parameter handling of HCL Client Application Access v9 could potentially be exploited by an authenticated attacker resulting in a stack buffer overflow. This could allow the attacker to crash the program or inject code into the system which would execute with the privileges of the currently logged in user. |
2020-12-22 |
6.5 |
CVE-2020-14231
MISC |
| hp — storeever_msl2024_firmware |
A potential security vulnerability has been identified in the HPE StoreEver MSL2024 Tape Library and HPE StoreEver 1/8 G2 Tape Autoloaders. The vulnerability could be remotely exploited to allow Cross-site Request Forgery (CSRF). |
2020-12-18 |
6.8 |
CVE-2020-7201
MISC |
| ibm — automation_workstream_services |
IBM Automation Workstream Services 19.0.3, 20.0.1, 20.0.2, IBM Business Automation Workflow 18.0, 19.0, and 20.0 and IBM Business Process Manager 8.6 could allow an authenticated user to obtain sensitive information or cuase a denial of service due to iimproper authorization checking. IBM X-Force ID: 189445. |
2020-12-21 |
5.5 |
CVE-2020-4794
XF
CONFIRM |
| ibm — financial_transaction_manager |
IBM Financial Transaction Manager 3.0.6 and 3.1.0 does not invalidate session after logout which could allow an authenticated user to impersonate another user on the system. IBM X-Force ID: 183328. |
2020-12-21 |
5.5 |
CVE-2020-4555
XF
CONFIRM
CONFIRM
CONFIRM
CONFIRM
CONFIRM
CONFIRM |
| ibm — mq |
IBM MQ 9.2 CD and LTS are vulnerable to a denial of service attack caused by an error processing connecting applications. IBM X-Force ID: 190833. |
2020-12-21 |
5 |
CVE-2020-4870
XF
CONFIRM
CONFIRM |
| ibm — planning_analytics |
IBM Planning Analytics 2.0 is vulnerable to cross-site request forgery which could allow an attacker to execute malicious and unauthorized actions transmitted from a user that the website trusts. IBM X-Force ID: 188898. |
2020-12-18 |
4.3 |
CVE-2020-4764
XF
CONFIRM |
| ibm — security_secret_server |
IBM Security Secret Server 10.6 could allow a remote attacker to obtain sensitive information, caused by the failure to properly enable HTTP Strict Transport Security. An attacker could exploit this vulnerability to obtain sensitive information using man in the middle techniques. IBM X-Force ID: 190045. |
2020-12-21 |
4.3 |
CVE-2020-4841
XF
CONFIRM |
| ibm — security_secret_server |
IBM Security Secret Server 10.6 stores potentially sensitive information in config files that could be read by an authenticated user. IBM X-Force ID: 190048. |
2020-12-21 |
4 |
CVE-2020-4843
XF
CONFIRM |
| ibm — security_secret_server |
IBM Security Secret Server 10.6 could allow a remote attacker to obtain sensitive information when a detailed technical error message is returned in the browser. This information could be used in further attacks against the system. IBM X-Force ID: 190046. |
2020-12-21 |
4 |
CVE-2020-4842
XF
CONFIRM |
| ibm — security_secret_server |
IBM Security Secret Server 10.6 could allow a remote attacker to conduct phishing attacks, using an open redirect attack. By persuading a victim to visit a specially crafted Web site, a remote attacker could exploit this vulnerability to spoof the URL displayed to redirect a user to a malicious Web site that would appear to be trusted. This could allow the attacker to obtain highly sensitive information or conduct further attacks against the victim. IBM X-Force ID: 190044. |
2020-12-21 |
5.8 |
CVE-2020-4840
XF
CONFIRM |
| jaws_project — jaws |
Jaws through 1.8.0 allows remote authenticated administrators to execute arbitrary code via crafted use of admin.php?reqGadget=Components&reqAction=InstallGadget&comp=FileBrowser and admin.php?reqGadget=FileBrowser&reqAction=Files to upload a .php file. NOTE: this is unrelated to the JAWS (aka Job Access With Speech) product. |
2020-12-23 |
6.5 |
CVE-2020-35656
MISC
MISC |
| jaws_project — jaws |
Jaws through 1.8.0 allows remote authenticated administrators to execute arbitrary code via crafted use of UploadTheme to upload a theme ZIP archive containing a .php file that is able to execute OS commands. NOTE: this is unrelated to the JAWS (aka Job Access With Speech) product. |
2020-12-23 |
6.5 |
CVE-2020-35657
MISC
MISC |
| jupyter — jupyter_server |
The Jupyter Server provides the backend (i.e. the core services, APIs, and REST endpoints) for Jupyter web applications like Jupyter notebook, JupyterLab, and Voila. In Jupyter Server before version 1.1.1, an open redirect vulnerability could cause the jupyter server to redirect the browser to a different malicious website. All jupyter servers running without a base_url prefix are technically affected, however, these maliciously crafted links can only be reasonably made for known jupyter server hosts. A link to your jupyter server may *appear* safe, but ultimately redirect to a spoofed server on the public internet. This same vulnerability was patched in upstream notebook v5.7.8. This is fixed in jupyter_server 1.1.1. If upgrade is not available, a workaround can be to run your server on a url prefix: “jupyter server –ServerApp.base_url=/jupyter/”. |
2020-12-21 |
5.8 |
CVE-2020-26275
MISC
CONFIRM
MISC |
| lantronix — xport_edge_firmware |
An information disclosure vulnerability exists in the Web Manager and telnet CLI functionality of Lantronix XPort EDGE 3.0.0.0R11, 3.1.0.0R9, 3.4.0.0R12 and 4.2.0.0R7. A specially crafted HTTP request can cause information disclosure. An attacker can sniff the network to trigger this vulnerability. |
2020-12-18 |
4.3 |
CVE-2020-13528
MISC |
| lantronix — xport_edge_firmware |
An authentication bypass vulnerability exists in the Web Manager functionality of Lantronix XPort EDGE 3.0.0.0R11, 3.1.0.0R9, 3.4.0.0R12 and 4.2.0.0R7. A specially crafted HTTP request can cause increased privileges. An attacker can send an HTTP request to trigger this vulnerability. |
2020-12-18 |
4 |
CVE-2020-13527
MISC |
| limitloginattempts — limit_login_attempts_reloaded |
LimitLoginAttempts.php in the limit-login-attempts-reloaded plugin before 2.17.4 for WordPress allows a bypass of (per IP address) rate limits because the X-Forwarded-For header can be forged. When the plugin is configured to accept an arbitrary header for the client source IP address, a malicious user is not limited to perform a brute force attack, because the client IP header accepts any arbitrary string. When randomizing the header input, the login count does not ever reach the maximum allowed retries. |
2020-12-21 |
5 |
CVE-2020-35590
MISC
MISC |
| malwarebytes — endpoint_protection |
In Malwarebytes Free 4.1.0.56, a symbolic link may be used delete an arbitrary file on the system by exploiting the local quarantine system. |
2020-12-22 |
6.6 |
CVE-2020-28641
CONFIRM
CONFIRM
MISC |
| mediawiki — mediawiki |
An issue was discovered in the SecurePoll extension for MediaWiki through 1.35.1. The non-admin vote list contains a full vote timestamp, which may provide unintended clues about how a voting process unfolded. |
2020-12-21 |
5 |
CVE-2020-35624
MISC
MISC |
| mediawiki — mediawiki |
An issue was discovered in the CasAuth extension for MediaWiki through 1.35.1. Due to improper username validation, it allowed user impersonation with trivial manipulations of certain characters within a given username. An ordinary user may be able to login as a “bureaucrat user” who has a similar username, as demonstrated by usernames that differ only in (1) bidirectional override symbols or (2) blank space. |
2020-12-21 |
5 |
CVE-2020-35623
MISC
MISC |
| mediawiki — mediawiki |
In MediaWiki before 1.35.1, the messages userrights-expiry-current and userrights-expiry-none can contain raw HTML. XSS can happen when a user visits Special:UserRights but does not have rights to change all userrights, and the table on the left side has unchangeable groups in it. (The right column with the changeable groups is not affected and is escaped correctly.) |
2020-12-18 |
5 |
CVE-2020-35475
FEDORA
MISC
MISC
DEBIAN |
| mediawiki — mediawiki |
An issue was discovered in the PushToWatch extension for MediaWiki through 1.35.1. The primary form did not implement an anti-CSRF token and therefore was completely vulnerable to CSRF attacks against onSkinAddFooterLinks in PushToWatch.php. |
2020-12-21 |
6.8 |
CVE-2020-35626
MISC
MISC |
| mediawiki — mediawiki |
In MediaWiki before 1.35.1, the combination of Html::rawElement and Message::text leads to XSS because the definition of MediaWiki:recentchanges-legend-watchlistexpiry can be changed onwiki so that the output is raw HTML. |
2020-12-18 |
4.3 |
CVE-2020-35474
FEDORA
MISC
MISC |
| mediawiki — mediawiki |
An issue was discovered in MediaWiki before 1.35.1. Missing users (accounts that don’t exist) and hidden users (accounts that have been explicitly hidden due to being abusive, or similar) that the viewer cannot see are handled differently, exposing sensitive information about the hidden status to unprivileged viewers. This exists on various code paths. |
2020-12-18 |
5 |
CVE-2020-35480
MLIST
FEDORA
MISC
MISC
DEBIAN |
| mediawiki — mediawiki |
MediaWiki before 1.35.1 blocks legitimate attempts to hide log entries in some situations. If one sets MediaWiki:Mainpage to Special:MyLanguage/Main Page, visits a log entry on Special:Log, and toggles the “Change visibility of selected log entries” checkbox (or a tags checkbox) next to it, there is a redirection to the main page’s action=historysubmit (instead of the desired behavior in which a revision-deletion form appears). |
2020-12-18 |
5 |
CVE-2020-35477
MLIST
FEDORA
MISC
MISC
DEBIAN |
| mediawiki — mediawiki |
MediaWiki before 1.35.1 allows XSS via BlockLogFormatter.php. Language::translateBlockExpiry itself does not escape in all code paths. For example, the return of Language::userTimeAndDate is is always unsafe for HTML in a month value. This affects MediaWiki 1.12.0 and later. |
2020-12-18 |
4.3 |
CVE-2020-35479
MLIST
FEDORA
MISC
MISC
DEBIAN |
| mediawiki — mediawiki |
MediaWiki before 1.35.1 allows XSS via BlockLogFormatter.php. MediaWiki:blanknamespace potentially can be output as raw HTML with SCRIPT tags via LogFormatter::makePageLink(). This affects MediaWiki 1.33.0 and later. |
2020-12-18 |
4.3 |
CVE-2020-35478
FEDORA
MISC
MISC |
| mediawiki — mediawiki |
An issue was discovered in the GlobalUsage extension for MediaWiki through 1.35.1. SpecialGlobalUsage.php calls WikiMap::makeForeignLink unsafely. The $page variable within the formatItem function was not being properly escaped, allowing for XSS under certain conditions. |
2020-12-21 |
4.3 |
CVE-2020-35622
MISC
MISC |
| mediawiki — mediawiki |
An issue was discovered in the Widgets extension for MediaWiki through 1.35.1. Any user with the ability to edit pages within the Widgets namespace could call any static function within any class (defined within PHP or MediaWiki) via a crafted HTML comment, related to a Smarty template. For example, a person in the Widget Editors group could use MediaWikiShellShell::command within a comment. |
2020-12-21 |
6.5 |
CVE-2020-35625
MISC
MISC |
| mersive — solstice_firmware |
** DISPUTED ** In Solstice Pod before 3.0.3, the firmware can easily be decompiled/disassembled. The decompiled/disassembled files contain non-obfuscated code. NOTE: it is unclear whether lack of obfuscation is directly associated with a negative impact, or instead only facilitates an attack technique. |
2020-12-23 |
5 |
CVE-2020-35587
MISC
MISC
MISC
MISC |
| mersive — solstice_pod_firmware |
In Solstice Pod before 3.0.3, the web services allow users to connect to them over unencrypted channels via the Browser Look-in feature. An attacker suitably positioned to view a legitimate user’s network traffic could record and monitor their interactions with the web services and obtain any information the user supplies, including Administrator passwords and screen keys. |
2020-12-23 |
4.3 |
CVE-2020-35584
MISC
MISC
MISC |
| mersive — solstice_pod_firmware |
In Solstice Pod before 3.3.0 (or Open4.3), the screen key can be enumerated using brute-force attacks via the /lookin/info Solstice Open Control API because there are only 1.7 million possibilities. |
2020-12-23 |
5 |
CVE-2020-35585
MISC
MISC
MISC |
| mersive — solstice_pod_firmware |
In Solstice Pod before 3.3.0 (or Open4.3), the Administrator password can be enumerated using brute-force attacks via the /Config/service/initModel?password= Solstice Open Control API because there is no complexity requirement (e.g., it might be all digits or all lowercase letters). |
2020-12-23 |
5 |
CVE-2020-35586
MISC
MISC
MISC |
| miniweb_http_server_project — miniweb_http_server |
MiniWeb HTTP server 0.8.19 allows remote attackers to cause a denial of service (daemon crash) via a long name for the first parameter in a POST request. |
2020-12-21 |
5 |
CVE-2020-29596
MISC
MISC
MISC
MISC |
| mitel — 6873i_sip_firmware |
The Bluetooth handset of Mitel MiVoice 6873i, 6930, and 6940 SIP phones with firmware before 5.1.0.SP6 could allow an unauthenticated attacker within Bluetooth range to pair a rogue Bluetooth device when a phone handset loses connection, due to an improper pairing mechanism. A successful exploit could allow an attacker to eavesdrop on conversations. |
2020-12-18 |
4.8 |
CVE-2020-27639
MISC |
| mitel — businesscti_enterprise |
The chat window of Mitel BusinessCTI Enterprise (MBC-E) Client for Windows before 6.4.11 and 7.x before 7.0.3 could allow an attacker to gain access to user information by sending arbitrary code, due to improper input validation. A successful exploit could allow an attacker to view the user information and application data. |
2020-12-18 |
6.5 |
CVE-2020-27154
MISC |
| mitel — micollab |
The online help portal of Mitel MiCollab before 9.2 could allow an attacker to redirect a user to an unauthorized website by executing malicious script due to insufficient access control. |
2020-12-18 |
5.8 |
CVE-2020-27340
MISC |
| mitel — mivoice_6940_firmware |
The Bluetooth handset of Mitel MiVoice 6940 and 6930 MiNet phones with firmware before 1.5.3 could allow an unauthenticated attacker within Bluetooth range to pair a rogue Bluetooth device when a phone handset loses connection, due to an improper pairing mechanism. A successful exploit could allow an attacker to eavesdrop on conversations. |
2020-12-18 |
4.8 |
CVE-2020-27640
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in WEB server for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower has incorrectly implemented protections from session fixation, which may allow an attacker to gain access to a session and hijack it by stealing the user’s cookies. |
2020-12-23 |
6.8 |
CVE-2020-25198
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in web service for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower does not require users to have strong passwords. |
2020-12-23 |
5 |
CVE-2020-25153
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in WEB server for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower stores and transmits the credentials of third-party services in cleartext. |
2020-12-23 |
5 |
CVE-2020-25190
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in WEB server for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower allows sensitive information to be displayed without proper authorization. |
2020-12-23 |
5 |
CVE-2020-25192
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in WEB server for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower allows SSH/Telnet sessions, which may be vulnerable to brute force attacks to bypass authentication. |
2020-12-23 |
5 |
CVE-2020-25196
MISC |
| moxa — nport_iaw5000a-i/o_firmware |
The built-in WEB server for MOXA NPort IAW5000A-I/O firmware version 2.1 or lower has improper privilege management, which may allow an attacker with user privileges to perform requests with administrative privileges. |
2020-12-23 |
6.5 |
CVE-2020-25194
MISC |
| nagios — nagios_core |
There is a Cross Site Request Forgery (CSRF) vulnerability in Nagios Core 4.2.4. |
2020-12-23 |
6.8 |
CVE-2020-35269
MISC |
| niftypm — nifty-pm |
Nifty-PM CPE 2.3 is affected by stored HTML injection. The impact is remote arbitrary code execution. |
2020-12-21 |
4.3 |
CVE-2020-26049
MISC |
| odoo — odoo |
Improper access control in Odoo Community 13.0 and earlier and Odoo Enterprise 13.0 and earlier, allows remote authenticated users to modify translated terms, which may lead to arbitrary content modification on translatable elements. |
2020-12-22 |
4 |
CVE-2019-11786
MISC |
| odoo — odoo |
Improper access control in mail module (followers) in Odoo Community 13.0 and earlier and Odoo Enterprise 13.0 and earlier, allows remote authenticated users to obtain access to messages posted on business records there were not given access to, and subscribe to receive future messages. |
2020-12-22 |
4 |
CVE-2019-11785
MISC |
| odoo — odoo |
Improper access control in message routing in Odoo Community 12.0 and earlier and Odoo Enterprise 12.0 and earlier allows remote authenticated users to create arbitrary records via crafted payloads, which may allow privilege escalation. |
2020-12-22 |
4 |
CVE-2018-15645
MISC |
| odoo — odoo |
Improper access control in Odoo Community 14.0 and earlier and Odoo Enterprise 14.0 and earlier, allows remote authenticated users with access to contact management to modify user accounts, leading to privilege escalation. |
2020-12-22 |
4 |
CVE-2019-11782
MISC |
| odoo — odoo |
Improper access control in mail module (notifications) in Odoo Community 14.0 and earlier and Odoo Enterprise 14.0 and earlier, allows remote authenticated users to obtain access to arbitrary messages in conversations they were not a party to. |
2020-12-22 |
4 |
CVE-2019-11784
MISC |
| odoo — odoo |
Improper access control in mail module (channel partners) in Odoo Community 14.0 and earlier and Odoo Enterprise 14.0 and earlier, allows remote authenticated users to subscribe to arbitrary mail channels uninvited. |
2020-12-22 |
4 |
CVE-2019-11783
MISC |
| odoo — odoo |
Improper input validation in portal component in Odoo Community 12.0 and earlier and Odoo Enterprise 12.0 and earlier, allows remote attackers to trick victims into modifying their account via crafted links, leading to privilege escalation. |
2020-12-22 |
6.8 |
CVE-2019-11781
MISC |
| odoo — odoo |
Cross-site scripting (XSS) issue in attachment management in Odoo Community 14.0 and earlier and Odoo Enterprise 14.0 and earlier, allows remote attackers to inject arbitrary web script in the browser of a victim via a crafted link. |
2020-12-22 |
4.3 |
CVE-2018-15634
MISC |
| odoo — odoo |
Cross-site scripting (XSS) issue in “document” module in Odoo Community 11.0 and earlier and Odoo Enterprise 11.0 and earlier, allows remote attackers to inject arbitrary web script in the browser of a victim via crafted attachment filenames. |
2020-12-22 |
4.3 |
CVE-2018-15633
MISC |
| odoo — odoo |
A sandboxing issue in Odoo Community 11.0 through 13.0 and Odoo Enterprise 11.0 through 13.0, when running with Python 3.6 or later, allows remote authenticated users to execute arbitrary code, leading to privilege escalation. |
2020-12-22 |
6.5 |
CVE-2020-29396
MISC |
| online_marriage_registration_system_project — online_marriage_registration_system |
The Online Marriage Registration System 1.0 post parameter “searchdata” in the user/search.php request is vulnerable to Time Based Sql Injection. |
2020-12-21 |
6.5 |
CVE-2020-35151
MISC
MISC |
| onstove — stove |
A arbitrary code execution vulnerability exists in the way that the Stove client improperly validates input value. An attacker could execute arbitrary code when the user access to crafted web page. This issue affects: Smilegate STOVE Client 0.0.4.72. |
2020-12-18 |
6.8 |
CVE-2020-7838
MISC |
| openzaak — open_zaak |
Open Zaak is a modern, open-source data- and services-layer to enable zaakgericht werken, a Dutch approach to case management. In Open Zaak before version 1.3.3 the Cross-Origin-Resource-Sharing policy in Open Zaak is currently wide open – every client is allowed. This allows evil.com to run scripts that perform AJAX calls to known Open Zaak installations, and the browser will not block these. This was intended to only apply to development machines running on localhost/127.0.0.1. Open Zaak 1.3.3 disables CORS by default, while it can be opted-in through environment variables. The vulnerability does not actually seem exploitable because: a) The session cookie has a `Same-Site: Lax` policy which prevents it from being sent along in Cross-Origin requests. b) All pages that give access to (production) data are login-protected c) `Access-Control-Allow-Credentials` is set to `false` d) CSRF checks probably block the remote origin, since they’re not explicitly added to the trusted allowlist. |
2020-12-18 |
4.3 |
CVE-2020-26251
MISC
MISC
CONFIRM |
| opera — opera |
URLs using “javascript:” have the protocol removed when pasted into the address bar to protect users from cross-site scripting (XSS) attacks, but in certain circumstances this removal was not performed. This could allow users to be socially engineered to run an XSS attack against themselves. This vulnerability affects Opera for Android versions below 61.0.3076.56532. |
2020-12-23 |
4.3 |
CVE-2020-6159
MISC |
| oracle — cloud_infrastructure_identity_and_access_management |
Vulnerability in the Oracle Cloud Infrastructure Identity and Access Management product of Oracle Cloud Services. Easily exploitable vulnerability allows high privileged attacker with network access to compromise Oracle Cloud Infrastructure Identity and Access Management. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Cloud Infrastructure Identity and Access Management accessible data as well as unauthorized read access to a subset of Oracle Cloud Infrastructure Identity and Access Management accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Cloud Infrastructure Identity and Access Management. All affected customers were notified of CVE-2020-14874 by Oracle. CVSS 3.1 Base Score 4.7 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:L). |
2020-12-22 |
6.5 |
CVE-2020-14874
MISC |
| ovirt — ovirt-engine |
A flaw was found in ovirt-engine 4.4.3 and earlier allowing an authenticated user to read other users’ personal information, including name, email and public SSH key. |
2020-12-21 |
4 |
CVE-2020-35497
MISC |
| philips — hue_firmware |
Philips Hue is vulnerable to a Denial of Service attack. Sending a SYN flood on port tcp/80 will freeze Philips Hue’s hub and it will stop responding. The “hub” will stop operating and be frozen until the flood stops. During the flood, the user won’t be able to turn on/off the lights, and all of the hub’s functionality will be unresponsive. The cloud service also won’t work with the hub. |
2020-12-21 |
5 |
CVE-2018-7580
FULLDISC
MISC |
| postsrsd_prject — postsrsd |
srs2.c in PostSRSd before 1.10 allows remote attackers to cause a denial of service (CPU consumption) via a long timestamp tag in an SRS address. |
2020-12-20 |
5 |
CVE-2020-35573
MISC
MLIST |
| projectworlds — online_matrimonial_project |
Marital – Online Matrimonial Project In PHP version 1.0 suffers from an authenticated file upload vulnerability allowing remote attackers to gain remote code execution (RCE) on the Hosting web server via uploading a maliciously crafted PHP file. |
2020-12-23 |
6.5 |
CVE-2020-27397
MISC |
| rust-lang — async-h1 |
async-h1 is an asynchronous HTTP/1.1 parser for Rust (crates.io). There is a request smuggling vulnerability in async-h1 before version 2.3.0. This vulnerability affects any webserver that uses async-h1 behind a reverse proxy, including all such Tide applications. If the server does not read the body of a request which is longer than some buffer length, async-h1 will attempt to read a subsequent request from the body content starting at that offset into the body. One way to exploit this vulnerability would be for an adversary to craft a request such that the body contains a request that would not be noticed by a reverse proxy, allowing it to forge forwarded/x-forwarded headers. If an application trusted the authenticity of these headers, it could be misled by the smuggled request. Another potential concern with this vulnerability is that if a reverse proxy is sending multiple http clients’ requests along the same keep-alive connection, it would be possible for the smuggled request to specify a long content and capture another user’s request in its body. This content could be captured in a post request to an endpoint that allows the content to be subsequently retrieved by the adversary. This has been addressed in async-h1 2.3.0 and previous versions have been yanked. |
2020-12-21 |
5.8 |
CVE-2020-26281
MISC
CONFIRM |
| solarwinds — webhelpdesk |
SolarWinds Web Help Desk 12.7.0 allows CSV Injection, also known as Formula Injection, via a file attached to a ticket. |
2020-12-21 |
4 |
CVE-2019-16959
MISC
MISC
MISC |
| spamtitan — spamtitan |
SpamTitan before 7.09 allows attackers to tamper with backups, because backups are not encrypted. |
2020-12-23 |
5 |
CVE-2020-35658
MISC
MISC |
| spiceworks — spiceworks |
Host Header Injection in Spiceworks 7.5.7.0 allowing the attacker to render arbitrary links that point to a malicious website with poisoned Host header webpages. |
2020-12-18 |
5.8 |
CVE-2020-25901
MISC
MISC |
| steedos — steedos |
Steedos Platform through 1.21.24 allows NoSQL injection because the /api/collection/findone implementation in server/packages/steedos_base.js mishandles req.body validation, as demonstrated by MongoDB operator attacks such as an X-User-Id[$ne]=1 value. |
2020-12-23 |
6.5 |
CVE-2020-35666
MISC |
| subconverter_project — subconverter |
tindy2013 subconverter 0.6.4 has a /sub?target=%TARGET%&url=%URL%&config=%CONFIG% API endpoint that accepts an arbitrary %URL% value and launches a GET request for it, but does not consider that the external request target may indirectly redirect back to this original /sub endpoint. Thus, a request loop and a denial of service may occur. |
2020-12-20 |
5 |
CVE-2020-35579
MISC |
| tangro — business_workflow |
tangro Business Workflow before 1.18.1 requests a list of allowed filetypes from the server and restricts uploads to the filetypes contained in this list. However, this restriction is enforced in the browser (client-side) and can be circumvented. This allows an attacker to upload any file as an attachment to a workitem. |
2020-12-18 |
6.5 |
CVE-2020-26174
MISC
MISC |
| tangro — business_workflow |
In tangro Business Workflow before 1.18.1, an attacker can manipulate the value of PERSON in requests to /api/profile in order to change profile information of other users. |
2020-12-18 |
4 |
CVE-2020-26175
MISC
MISC |
| tangro — business_workflow |
Every login in tangro Business Workflow before 1.18.1 generates the same JWT token, which allows an attacker to reuse the token when a session is active. The JWT token does not contain an expiration timestamp. |
2020-12-18 |
6.4 |
CVE-2020-26172
MISC
MISC |
| tangro — business_workflow |
In tangro Business Workflow before 1.18.1, a user’s profile contains some items that are greyed out and thus are not intended to be edited by regular users. However, this restriction is only applied client-side. Manipulating any of the greyed-out values in requests to /api/profile is not prohibited server-side. |
2020-12-18 |
4 |
CVE-2020-26177
MISC
MISC |
| tangro — business_workflow |
An issue was discovered in tangro Business Workflow before 1.18.1. No (or broken) access control checks exist on the /api/document/<DocumentID>/attachments API endpoint. Knowing a document ID, an attacker can list all the attachments of a workitem, including their respective IDs. This allows the attacker to gather valid attachment IDs for workitems that do not belong to them. |
2020-12-18 |
4 |
CVE-2020-26176
MISC
MISC |
| tangro — business_workflow |
In tangro Business Workflow before 1.18.1, knowing an attachment ID, it is possible to download workitem attachments without being authenticated. |
2020-12-18 |
5 |
CVE-2020-26178
MISC
MISC |
| tangro — business_workflow |
In tangro Business Workflow before 1.18.1, the documentId of attachment uploads to /api/document/attachments/upload can be manipulated. By doing this, users can add attachments to workitems that do not belong to them. |
2020-12-18 |
4 |
CVE-2020-26171
MISC
MISC |
| tangro — business_workflow |
An incorrect access control implementation in Tangro Business Workflow before 1.18.1 allows an attacker to download documents (PDF) by providing a valid document ID and token. No further authentication is required. |
2020-12-18 |
4 |
CVE-2020-26173
MISC
MISC |
| tenable — tenable.sc |
In certain scenarios in Tenable.sc prior to 5.17.0, a scanner could potentially be used outside the user’s defined scan zone without a particular zone being specified within the Automatic Distribution configuration. |
2020-12-21 |
5 |
CVE-2020-5808
MISC |
| thingsboard — thingsboard |
ThingsBoard before v3.2 is vulnerable to Host header injection in password-reset emails. This allows an attacker to send malicious links in password-reset emails to victims, pointing to an attacker-controlled server. Lack of validation of the Host header allows this to happen. |
2020-12-18 |
6.8 |
CVE-2020-27687
MISC
MISC |
| tlslite-ng_project — tlslite-ng |
tlslite-ng is an open source python library that implements SSL and TLS cryptographic protocols. In tlslite-ng before versions 0.7.6 and 0.8.0-alpha39, the code that performs decryption and padding check in RSA PKCS#1 v1.5 decryption is data dependant. In particular, the code has multiple ways in which it leaks information about the decrypted ciphertext. It aborts as soon as the plaintext doesn’t start with 0x00, 0x02. All TLS servers that enable RSA key exchange as well as applications that use the RSA decryption API directly are vulnerable. This is patched in versions 0.7.6 and 0.8.0-alpha39. Note: the patches depend on Python processing the individual bytes in side-channel free manner, this is known to not the case (see reference). As such, users that require side-channel resistance are recommended to use different TLS implementations, as stated in the security policy of tlslite-ng. |
2020-12-21 |
5 |
CVE-2020-26263
MISC
MISC
MISC
CONFIRM
MISC
MISC |
| treck — ipv6 |
An issue was discovered in Treck IPv6 before 6.0.1.68. Improper Input Validation in the DHCPv6 client component allows an unauthenticated remote attacker to cause an Out of Bounds Read, and possibly a Denial of Service via adjacent network access. |
2020-12-22 |
4.8 |
CVE-2020-27338
CONFIRM |
| treck — ipv6 |
An issue was discovered in Treck IPv6 before 6.0.1.68. Improper input validation in the IPv6 component when handling a packet sent by an unauthenticated remote attacker could result in an out-of-bounds read of up to three bytes via network access. |
2020-12-22 |
5 |
CVE-2020-27336
CONFIRM |
| uncannyowl — tin_canny_reporting_for_learndash |
Multiple cross-site scripting (XSS) vulnerabilities in Uncanny Owl Tin Canny LearnDash Reporting before 3.4.4 allows authenticated remote attackers to inject arbitrary web script or HTML via the search_key GET Parameter in TinCan_Content_List_Table.php, message GET Parameter in licensing.php, tc_filter_group parameter in reporting-admin-menu.php, tc_filter_user parameter in reporting-admin-menu.php, tc_filter_course parameter in reporting-admin-menu.php, tc_filter_lesson parameter in reporting-admin-menu.php, tc_filter_module parameter in reporting-admin-menu.php, tc_filter_action parameter in reporting-admin-menu.php, tc_filter_data_range parameter in reporting-admin-menu.php, or tc_filter_data_range_last parameter in reporting-admin-menu.php. |
2020-12-23 |
4.3 |
CVE-2020-9439
MISC
MISC |
| uncannyowl — uncanny_groups_for_learndash |
Multiple cross-site scripting (XSS) vulnerabilities in Uncanny Groups for LearnDash before v3.7 allow authenticated remote attackers to inject arbitrary JavaScript or HTML via the ulgm_code_redeem POST Parameter in user-code-redemption.php, the ulgm_user_first POST Parameter in user-registration-form.php, the ulgm_user_last POST Parameter in user-registration-form.php, the ulgm_user_email POST Parameter in user-registration-form.php, the ulgm_code_registration POST Parameter in user-registration-form.php, the ulgm_terms_conditions POST Parameter in user-registration-form.php, the _ulgm_total_seats POST Parameter in frontend-uo_groups_buy_courses.php, the uncanny_group_signup_user_first POST Parameter in group-registration-form.php, the uncanny_group_signup_user_last POST Parameter in group-registration-form.php, the uncanny_group_signup_user_login POST Parameter in group-registration-form.php, the uncanny_group_signup_user_email POST Parameter in group-registration-form.php, the success-invited GET Parameter in frontend-uo_groups.php, the bulk-errors GET Parameter in frontend-uo_groups.php, or the message GET Parameter in frontend-uo_groups.php. |
2020-12-23 |
4.3 |
CVE-2020-35650
MISC
MISC |
| urve — urve |
An issue was discovered in URVE Build 24.03.2020. The password of an integration user account (used for the connection of the MS Office 365 Integration Service) is stored in cleartext in configuration files as well as in the database. The following files contain the password in cleartext: Profiles/urve/files/sql_db.backup, Server/data/pg_wal/000000010000000A000000DD, Server/data/base/16384/18617, and Server/data/base/17202/8708746. This causes the password to be displayed as cleartext in the HTML code as roomsreservationimport_password in /urve/roomsreservationimport/roomsreservationimport/update-HTML5. |
2020-12-23 |
5 |
CVE-2020-29550
FULLDISC
MISC
MISC |
| weiphp — weiphp |
WeiPHP 5.0 does not properly restrict access to pages, related to using POST. |
2020-12-18 |
5 |
CVE-2020-20299
MISC |
| wireshark — wireshark |
Buffer overflow in QUIC dissector in Wireshark 3.4.0 to 3.4.1 allows denial of service via packet injection or crafted capture file |
2020-12-21 |
5 |
CVE-2020-26422
CONFIRM
MISC
MISC |
| xinuos — openserver |
A reflected Cross-site scripting (XSS) vulnerability in Xinuo (formerly SCO) Openserver version 5 and 6 allows remote attackers to inject arbitrary web script or HTML tag via the parameter ‘section’. |
2020-12-18 |
4.3 |
CVE-2020-25495
MISC
MISC |
| zte — zxhn_e8810_firmware |
ZTE E8810/E8820/E8822 series routers have an MQTT DoS vulnerability, which is caused by the failure of the device to verify the validity of abnormal messages. A remote attacker could connect to the MQTT server and send an MQTT exception message to the specified device, which will cause the device to deny service. This affects:<ZXHN E8810, ZXHN E8820, ZXHN E8822><E8810 V1.0.26, E8810 V2.0.1, E8820 V1.1.3L, E8820 V2.0.13, E8822 V2.0.13> |
2020-12-21 |
5 |
CVE-2020-6881
MISC |
| zte — zxhn_e8810_firmware |
ZTE E8810/E8820/E8822 series routers have an information leak vulnerability, which is caused by hard-coded MQTT service access credentials on the device. The remote attacker could use this credential to connect to the MQTT server, so as to obtain information about other devices by sending specific topics. This affects:<ZXHN E8810, ZXHN E8820, ZXHN E8822><E8810 V1.0.26, E8810 V2.0.1, E8820 V1.1.3L, E8820 V2.0.13, E8822 V2.0.13> |
2020-12-21 |
5 |
CVE-2020-6882
MISC |




Recent Comments