by Scott Muniz | Jun 22, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Building on secure productivity, today we announce the general availability of Safe Documents*, a new Microsoft 365 Apps feature that keeps enterprise users safe by verifying untrusted files on their behalf.
Safe Documents is a new feature that improves the existing Protected View experience. Although Protected View helps secure documents originating outside the organization, people too often exit the protection sandbox without considering if the document is safe – leaving their organizations vulnerable. To improve this trust promotion experience for Microsoft 365 Apps, Safe Documents takes away the guesswork by automatically verifying the document against the latest known risks and threat profiles before allowing users to leave the Protected View container.
Keeping Users Safe:
Safe Documents leverages the power of the Microsoft Intelligent Security Graph and brings it to the desktop. When an admin enables Safe Documents for their tenant, untrusted files that open in Protected View go through an additional flow where the document is uploaded and scanned by Microsoft Defender ATP. Learn more about how Microsoft is handling user data here.
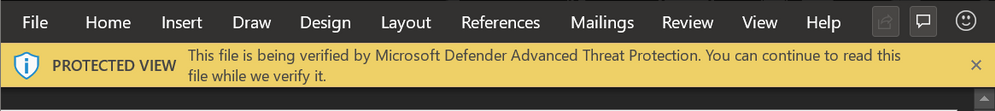
While a scan is in progress, Safe Documents will prevent users from exiting the Protected View container. Users are still able to access and read the document during this process but will be unable to make any edits until the scan has completed.
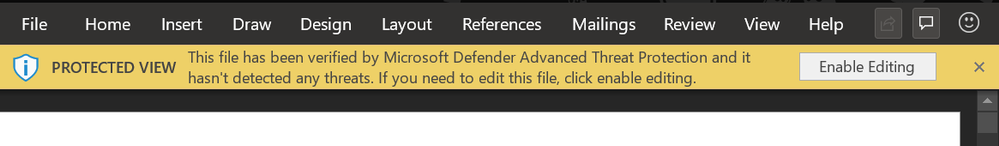
Once the file has been successfully scanned, users will be able to leave the Protected View container with confidence that their file is safe.
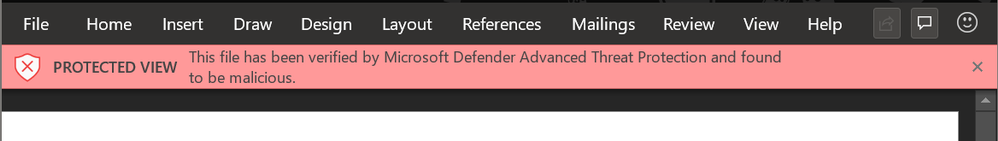
In case of a malicious file (above), users will be blocked from leaving the Protected View container. Admins can configure whether users can bypass and ‘Enable Editing’ for malicious scenarios in the Admin portal. Learn more about the user experience in this article.
Analytics for Admins:
In addition to providing these protections to enterprise users, we have also integrated features from Microsoft Defender Advanced Threat Protection – where admins can use the powerful Advanced Hunting feature, based on the Kusto query language, to get additional details in their tenants by using the DeviceEvents table and filtering for ActionType ‘SafeDocFileScan’.
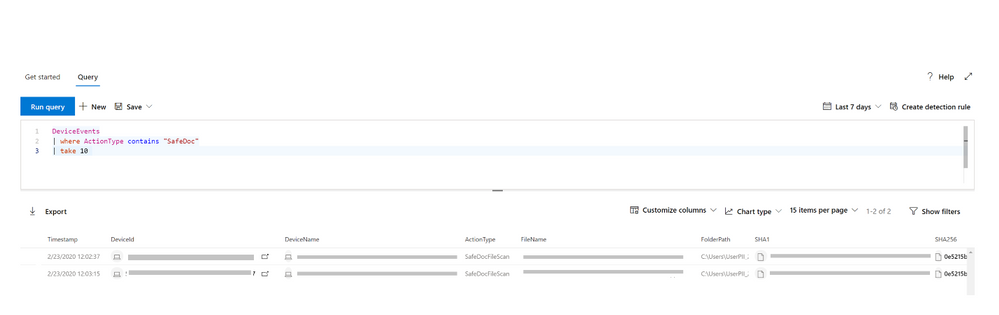
Details to get started with Advanced Hunting are available here. As we continue to receive feedback from customers, we will plan for additional functionality as we integrate with other features in the MDATP toolkit to provide greater visibility into these detections.
Enabling Safe Documents:
This feature is off by default and needs to be enabled by a Security Administrator. To turn on Safe Documents, the admin should navigate to the Security & Compliance center and go to Threat Management > Policy > ATP Safe Attachments where there will be settings to ‘Turn on Safe Documents for Office clients’ and another option to allow users to bypass protections if a file is malicious.

Thank you for those who joined us in the preview. We look forward to more of you enabling this protection and hearing feedback on how we can improve and evolve this solution.
* The Safe Documents feature is only available with a ‘Microsoft 365 E5’ or ‘Microsoft 365 E5 Security’ license for Commercial and Education customers on Windows clients.
by Scott Muniz | Jun 22, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Introduction
This is John Barbare and I am a Sr Premier Field Engineer at Microsoft focusing on all things in the Cybersecurity space. In this guide and tutorial, I will walk you through the steps of changing you background and adding image files to the library to have your own customized backgrounds when presenting using the Microsoft Teams video option.
Once you follow the steps and import the images, you will be ready to impress and show off your new backgrounds in the next meeting you present. Your imagination will have your co-workers wanting to know how exactly you had that “awesome and cool” background in the last video meeting. I will also go into details of how Microsoft secures Teams as I have lots of friends and family asking which is the best video collaboration application to use. Without further hesitation, let’s get started.
Adding the Images and accessing the folder
Let’s go ahead and access the folder by going to the start menu and typing run and then selecting it to open or by right clicking on the start menu and selecting “Run”.
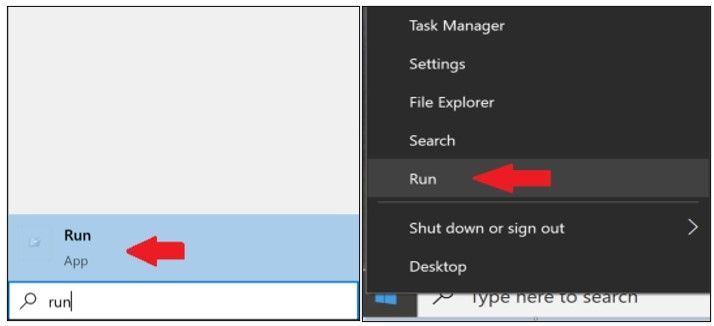
Type the following folder location in the “Run” window and then select ok.
File Path: %APPDATA%MicrosoftTeamsBackgroundsUploads
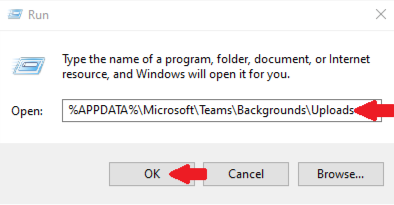
Once the folder opens, upload an image for your new background in Microsoft Teams.
Start uploading any type of image file that is supportable (I use .jpg and .png files) and make sure the image shows up in the folder.
Once all the files have been uploaded for your new background, go ahead and close out of Microsoft Teams and go into Task Manager and make sure it has been completely closed and End Task.

Once all instances of Microsoft Teams have been closed, go ahead and open back up Microsoft Teams on your Desktop. To test if it works, create a Microsoft Teams Video meeting/chat, or start a video chat with a co-worker. Once connected, click on the “Show Background Effects”. This will bring up all your images you placed in the folder along with the default ones.
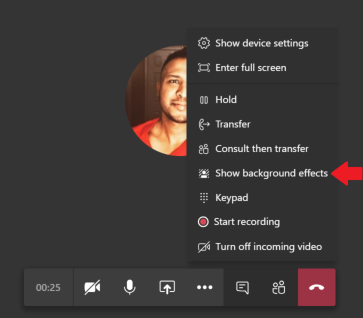
The image you placed in the folder will show up with the other images but will be below the rest of the default images.
Go ahead and select the new image and select “Apply and turn on video”.
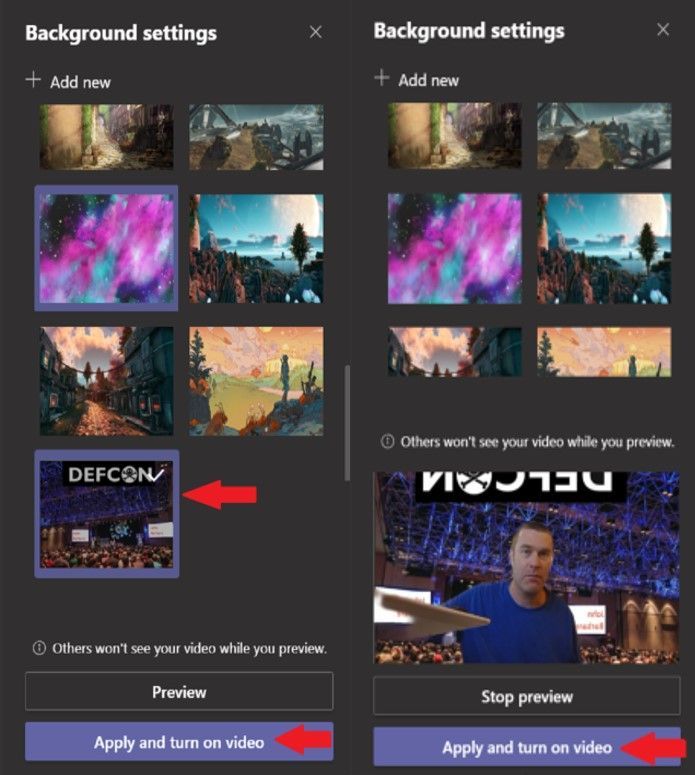
This concludes the tutorial of how to change your Microsoft Teams background using the video option. You will now have your new background with the picture of your choosing. Feel free to upload more pictures and change them whenever you have video meetings.
Security
Now that we have seen how to change your background in Microsoft Teams during a video call, let’s look at the security features and compliance that Microsoft Teams has built into the video and chat collaboration platform. Microsoft Teams is part of the Microsoft 365 (M365) service which follows all the security best practices and procedures that Microsoft has to offer. This includes the service-level security through defense-in-depth, customer controls within the service, security hardening, and operational best practices. When you log on and start a meeting, rest assured your network connection and communication is encrypted by default. The way Microsoft went about this approach was to require all servers to use certificates and by requiring OAUTH, TLS, Secure Real-Time Transport Protocol (SRTP), and other industry-standard encryption techniques, including 256-bit Advanced Encryption Standard (AES) encryption. To sum all this up, all Microsoft Teams data is protected on the network while you are having a business or personal video chat with a work colleague or friend.
Microsoft Cloud App Security
To see more of what is under the hood in terms of security, I like to check every single application using Microsoft Cloud App Security (MCAS) before I install it on my work, personal, and even my lab machines. MCAS is a multimode Cloud Access Security Broker (CASB) which provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all cloud services. MCAS lets me look at applications that have more than 80 risk factors, as well as leverage their security and compliance information submitted in Cloud Security Alliance and Security Trust Assurance and Risk or better known as CSA STAR.
The first thing I do is I log into https://www.portal.cloudappsecurity.com/ with my credentials and using two factor authentication (for licensing reference this link). Once authenticated, I click on the dropdown next to “Discover” on the left side and then select “Cloud app catalog”.
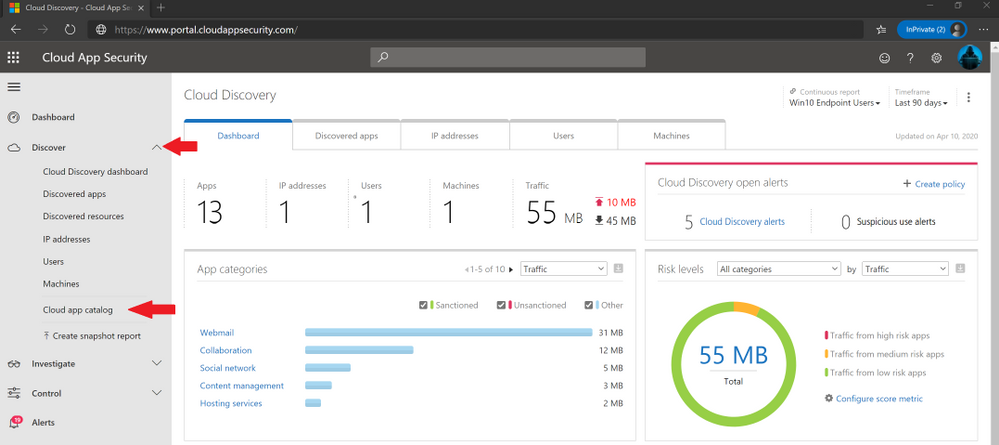
This will bring you to the Cloud app catalog page where you can search for every application that exists that Microsoft has and a plethora of other 3rd party applications.
Cloud app catalog
When the Cloud app catalog page is displayed, type “Teams” inside the “Apps” box and hit the enter key. Notice that different apps with the word Teams will be displayed.
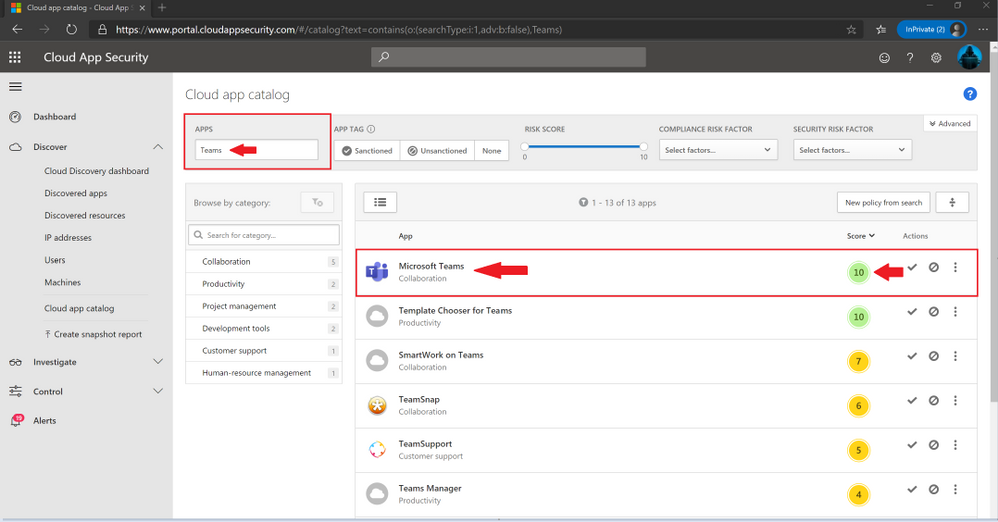
Microsoft Teams will be displayed first along with the score of 10 which tells me I am in rather good shape. Since I am always security minded about all things in the security and compliance realm, I will go ahead and click on the graphic and words displayed under “App” labeled “Microsoft Teams”.
Microsoft Teams Security
Once I land on the Microsoft Teams page in MCAS inside the Cloud app catalog, I get to see all the nuts and bolts of the security and compliance features along with legal data which shows me or anyone that Microsoft Teams is secure.
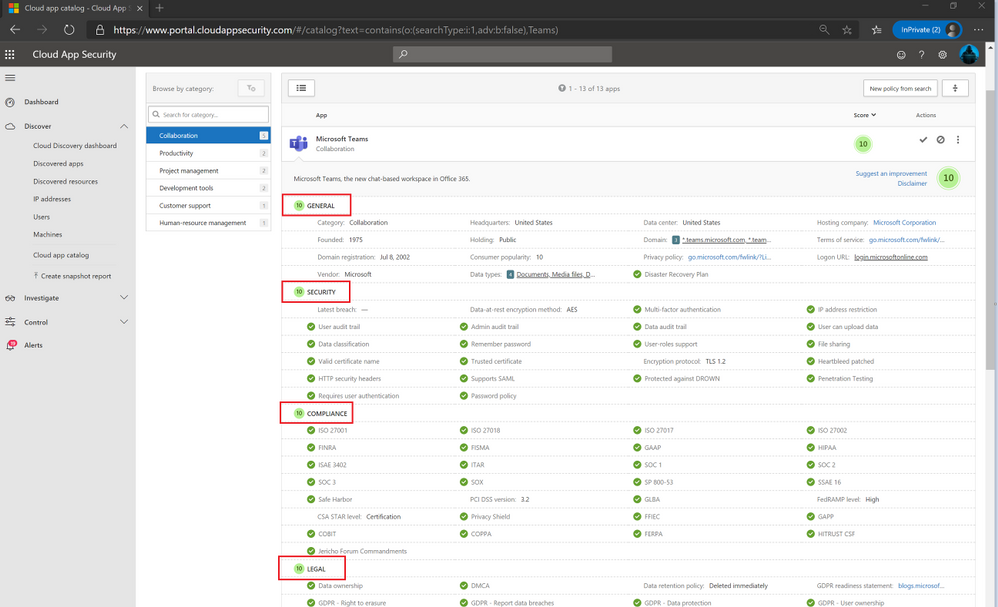
As you can see in each red box are the main sections which MCAS reports on for an application with either compliant (green check mark) or not compliant (red x mark) and then rates the application with an overall score (1-10) with 10 being the highest. In this case, Microsoft Teams scores a perfect 10. This security, data handling, and compliance information is intended to help organizations assess and manage risk in using these apps.
In the General section we get a brief overview of the company and where they are physically located at. Along with the domain name, URL for terms of services and privacy policy, and other data about the company that is valuable to me from a security perspective.
In the security section we can really dive into the encryption, certificates, penetration testing, multifactor authentication, password policy, and all the security measures a Cybersecurity professional like myself would decide whether its security worthy to be installed. Based off what I am seeing already, I know myself or any of my friends will be secure if/when they ask again about video conference calls and what I know.
In the compliance section we can see the national and international standards and publications that were used to make sure it meets the stringent compliance audits and if they are acceptable. Some of the main ones I have worked with in designing and getting large companies accredited inside different security realms have been the International Standards Organization (ISO) 27000 family of standards. The ISO 27000 helps organizations keep information assets secure and as you can see the various ISO 27000 standards are all compliant. Some of the other standards in the compliance section are ISAE, SOC 1 and 3, HIPAA, COBIT, and various other benchmarks to show your privacy and data are safe when collaborating or sharing various types of data, media, documents, etc.
In the legal section it goes over data ownership and if the company reports data breaches. Most of my cyber career I have worked in pre and post breach activities with large enterprises. Having a company that is transparent about any and all data breach activity shows Microsoft cares about its customer base.
Conclusion
If you are ever suspicious about an application, look it up in the Cloud app catalog in MCAS like I showed you in this blog. The more security information I can find about an application (especially all in one place) the more secure I feel and can let my friends and family know they are also.
Thanks for taking the time to read this article and I hope you had fun reading how to change your Teams video background while also showing you how secure Microsoft Teams is in security, compliance, and the legal aspects inside the application.
Thanks for reading and have a great Cybersecurity day!
by Scott Muniz | Jun 22, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Due to the ongoing concern of COVID-19 transmission the key focus for many organizations has been to provide a productive hybrid workplace environment where employees can work remotely, have an efficient method to report their wellness condition and get guidance before they return to their workplace. As crisis communication teams are working hard to update their employees with crucial information, from how to get tested for COVID-19 to what open workspaces will look like when returning to the office, we thought it would be useful to provide an update on some of the capabilities and solutions that may help to enable a safer return to work.
Top scenarios that we have heard from organizations:
- Connecting employees with wellness resources
- Enabling employees to take personal accountability
- Empowering employees with remote work capability
- Morale events and building employee resilience
- Wellness verification and attestations to enter the workspace
- Limiting employees to work based on social distancing
- Wellness monitoring while entering the facilities
In the article below, we focus on a few topics that could help you enable a voluntary wellness check and attestation before entering the facilities, requesting a space at the facility, and wellness monitoring while entering the facility. Each organization is responsible for adhering to applicable privacy policies. Please refer to this article for Microsoft Privacy Principles for data collection and preserving privacy.
Employee & Volunteer Self-Screening
The process for returning onsite may vary based on geography, industry, vertical, and division. In some cases, it may feel more like turning a dial than flipping a switch. If your organization can continue working from home, Teams is a platform that lets team members collaborate and communicate from anywhere.
Some organizations may need a way to ease back into the workplace methodically, while some divisions of an organization may need employee onsite presence. In this case, organizations will need to prepare their facilities and employees for returning to the physical workplace. Therefore, it is critical to monitor employees for common COVID-19 symptoms and provide a simple way for affected employees to return to work once they have completed the required steps.
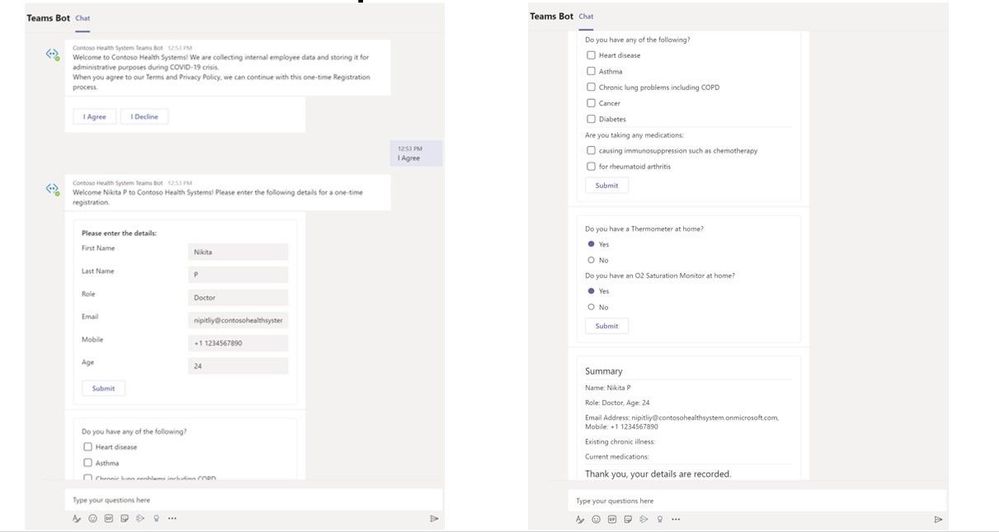
Teams has developed a solution template to quickly enable a few critical steps for returning to the workplace. We call it the “Back to Work” solution template, built on the Microsoft healthcare bot service and Azure API for FHIR. Please review the below images and this article for more in-depth information. This solution serves the dual purpose of acting as a wellness solution and attestation solution before employees return to work. Review this article for detailed instructions on how to use this solution.
In addition to above solution, we want to bring your attention to ProtectWell™, which can help employees determine whether they should return to work. Click here to learn more about this solution created in partnership between UnitedHealth Group and Microsoft.
Workplace Distancing & Space Reservation
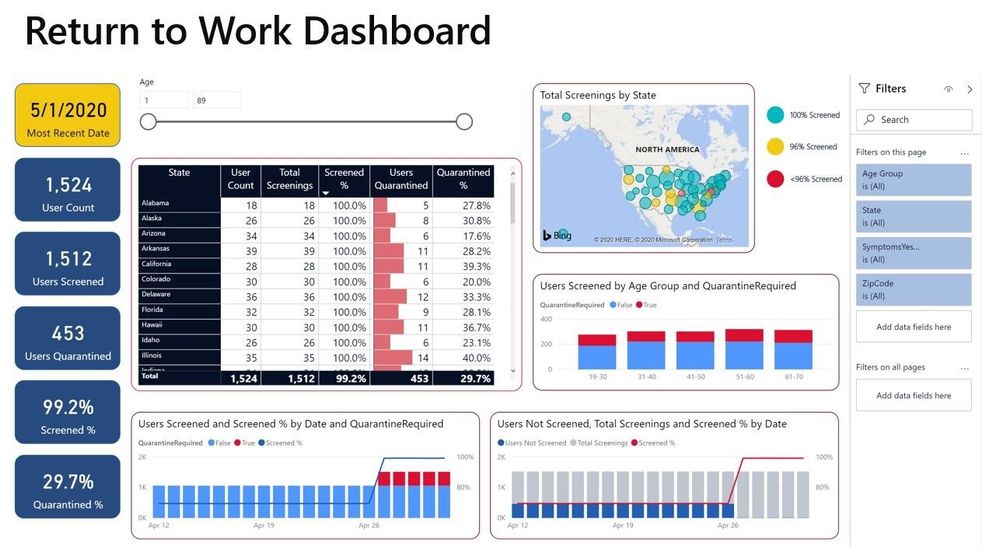
The pandemic needs a new way to think of rebuilding operations, modernize productivity platforms, and embrace these new technologies. The learnings will make organizations rethink how office buildings and shared spaces are designed and structured in the future. Organizations are developing a coordinated effort with a localized approach to limiting the number of people who could return to the workplace safely. The requirement to restrict people has created an additional burden on organizational leaders, particularly facilities and logistics division. The problem of space reservations and management can be solved using various solutions.
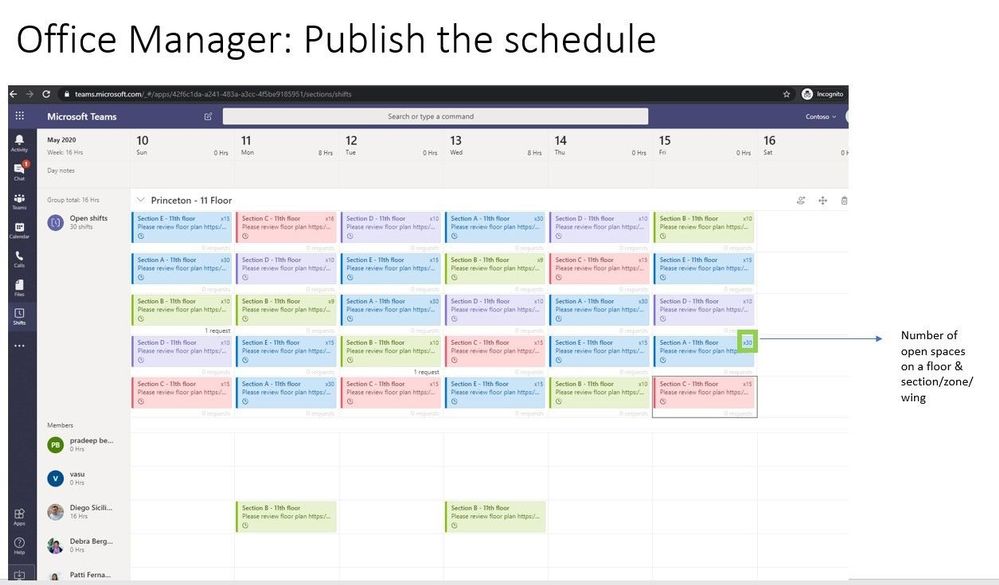
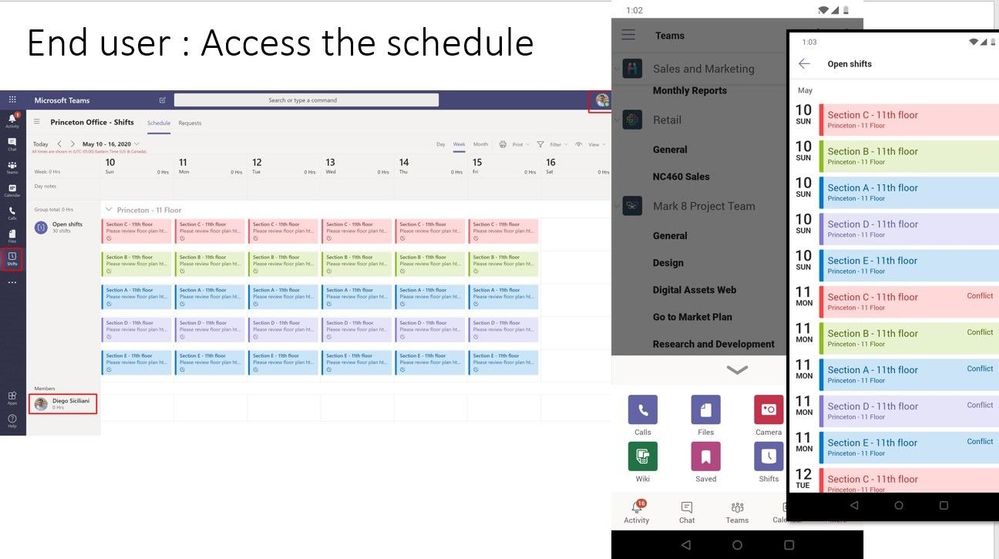
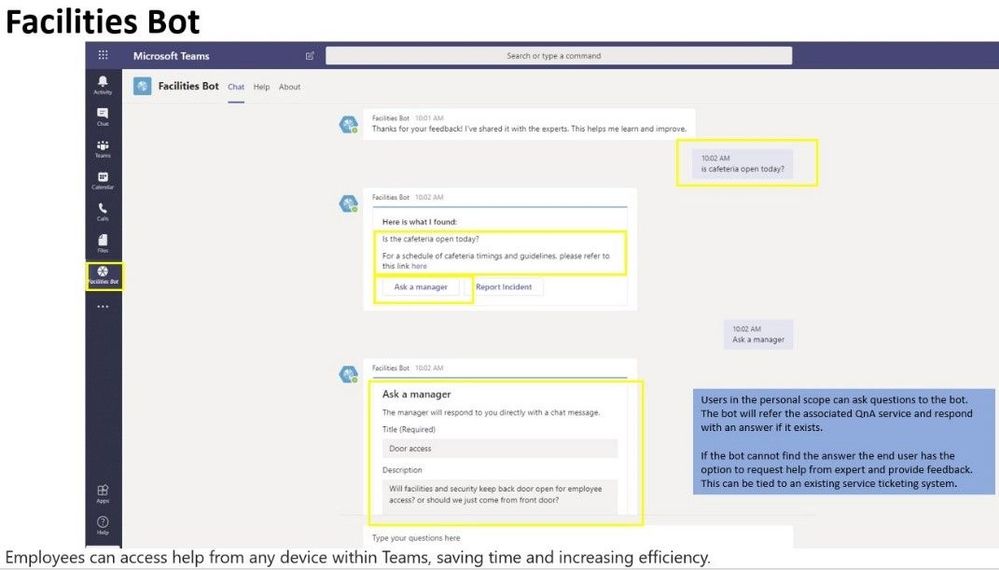
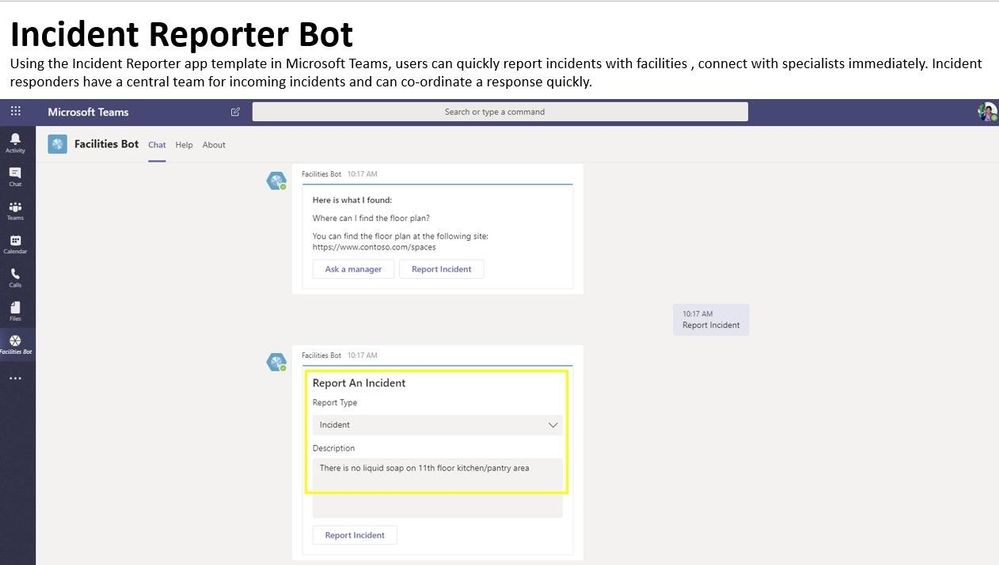
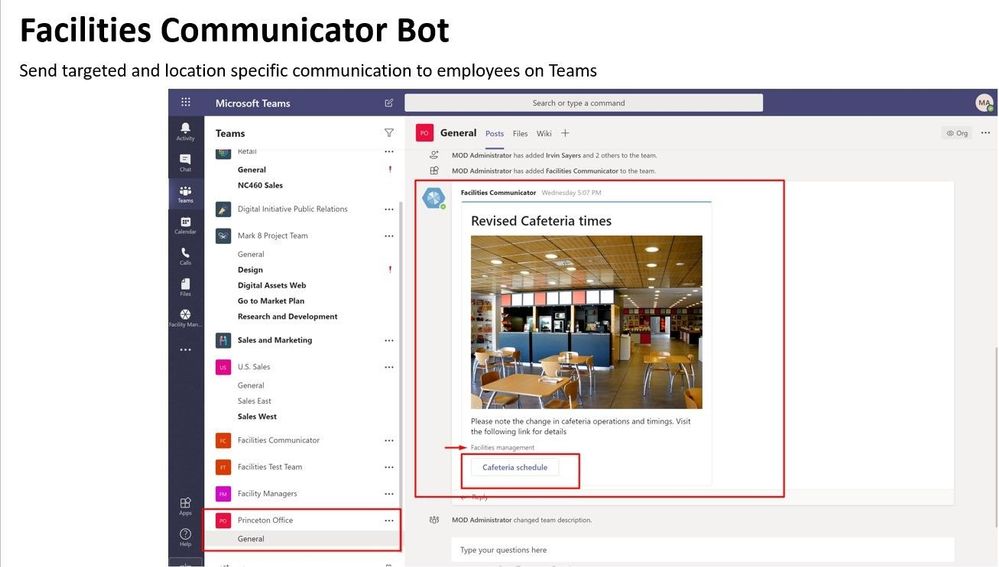
In this article, we address this scenario using Shifts in Teams and facility bots. Customers can utilize Shifts to publish open space availability to employees, allowing them to reserve spaces before they return to the workplace. To enable facility managers or departmental admins further, IT can deploy focused facility bots that send daily guidance to employees, provide a solution for topical Q&A and incident reporting capabilities.
Key features include:
- Office managers share available spaces to the employees based on location or floor, where employees reserve spaces on a first-come, first-served basis, or after approval.
- Office managers let the department admins manage open spaces, approval requests, send location-specific communications, and list suggested activities while employees are onsite.
- Employees can swap their spaces via mobile devices in case they cannot visit the office.
- Employees can interact with office managers and report any incidents that need attention.
- Facilities bot can help answer questions and engage an internal expert as needed.
Shifts in Teams is part of all Microsoft 365 enterprise SKUs and works across desktop, browser, and mobile platforms. IT departments can use Graph API or Power Automate to connect to Shifts for advanced scenarios. For example, only allocating the space after the employee has interacted with the health assessment bot, sending relevant data to the facility’s security system, and internal reporting systems.
- You can review this link, which has videos on how to enable and utilize the solution. We are working on providing additional guidance on how to address this scenario which we will publish in the coming weeks.
Data obtained from systems such as Employee & Volunteer self-screening bot or Shifts may help you manage events that need some attention. It is important to note that people need to be in control of their data and be empowered with information that explains how their data will be collected and used. Click here to learn more about preserving privacy while addressing COVID-19.
Sensor Based Wellness Monitoring
Organizations may be mandated by local jurisdiction to implement temperature checks before employees are permitted to report to the workplace, and our partners have built various solutions and devices on Microsoft technologies to address these industry and regional requirements. These solutions perform temperature checks with facial recognition, a less invasive method, and securely store this information in the cloud or your organization’s existing platforms. To find out more, please reach out to your Microsoft account team to get details of the partners in your region.
Summary
We hope these suggestions will help your organization be connected, productive, and have a safer workplace return experience. These solutions can be connected or independent with the option to extend it to fit your custom needs, giving your organization a starting point.
The public data presented by various health organizations clarify that the situation is still fragile. We continue to hear great stories from customers about how employees have built resilience, going above and beyond, and adapting in meaningful ways.
This global pandemic is a difficult and emotional time for many. So do take time to reach out to others, build employee resilience, and guard against isolation. Our Remote Work Fun handout can provide way to keep people connected when some have returned to the workplace and others remain remote. Using modern applications like Microsoft Teams can allow us to be productive and invest in our well being.
by Scott Muniz | Jun 22, 2020 | Uncategorized
This article is contributed. See the original author and article here.
If a web browser starts loading the web page but it never finishes loading it, check if there is an iframe in the page. If there is, try testing the page after removing the iframe.
In the case I worked on, these were the symptoms of the issue:
- There is an HTML page hosted in IIS. There is an iframe for a PowerApps in this page
- It works on
- Chrome and Edge browsers in the server
- Edge browser in the client (http)
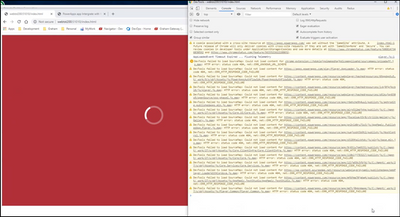
- It doesn’t work on (screenshot is below)
- Chrome and Edge Chromium browsers in the client (http)
- The page loads Chrome and Edge Chromium in the client if we access them via https
- F12 Developer Tools shows “A cookie associated with a cross-site resource at X was set without the “SameSite” attribute.” error
The root cause of this issue is the SameSite cookie changes. Chrome and Chrome based browsers had an update that changed how they interpret SameSite cookie.
The best solution would be enforcing the setting cookieSameSite = None in the PowerApps. However, there is no way of doing it at the time of this post. The only option left is that using the site through HTTPS all the time.
by Scott Muniz | Jun 22, 2020 | Uncategorized
This article is contributed. See the original author and article here.
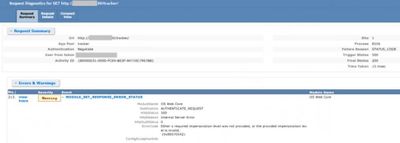
In a case I worked on, the page was displaying “The page cannot be displayed because an internal server error has occured” error if the user accesses the root folder of the application. There were no issues if they enter the full path.
Failed Request Tracing log:
“Either a required impersonation level was not provided, or the provided impersonation level is invalid (0x80070542)”
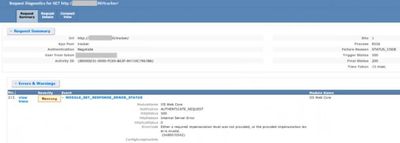
This error occurs if the service account doesn’t have “Impersonate a client after authentication” Permission.
Follow to steps below to solve this issue:
- Go to Start > Settings > Control Panel > Administrative Tools > Local Security Policies
- Expand Local Policies and select User Rights Assignment
- In the right pane, double-click Impersonate a client after authentication
- In the Security Policy Setting dialog box, click Add User or Group
- In the Select Users, Computers or Groups dialog box, type IIS_IUSRS
- Select Check Names and verify that the name is correct







Recent Comments