This article is contributed. See the original author and article here.

Dear IT Pros,
Ransomware acts with accessing to the files, folders and encrypting them, to respond against it, we need to enable the Windows Defender feature named “Controlled Folder Access” – WDCFA and monitor the Windows Defender Guard Events in Windows Event Viewer. The best way is possibly collecting the related activities by Advanced Hunting features of Microsoft 365 Security or Defender for Endpoint.
Could we search for Event ID by running the advanced hunting query or not?
We will discuss the above topic today.
To View or change the list of protected folders
You can use the Windows Security app to view the list of folders that are protected by controlled folder access.
- On your Windows 10 device, open the Windows Security app.
- Select Virus & threat protection.
- Under Ransomware protection, select Manage ransomware protection.
- If controlled folder access is turned off, you’ll need to turn it on. Select protected folders.
- Do one of the following steps:
- To add a folder, select + Add a protected folder.
- To remove a folder, select it, and then select Remove.
Note
Windows system folders are protected by default, and you cannot remove them from the list.
Review controlled folder access events in Windows Event Viewer
The following table shows events related to controlled folder access:
Event ID | Description |
5007 | Event when settings are changed |
1124 | Audited controlled folder access event |
1123 | Blocked controlled folder access event |
You can review the Windows event log and look for events which were created when controlled folder access of Windows Defender had blocked (or reported in audit mode) an app ‘s activity of accessing to the related folders, steps to follow:
- Download the Evaluation Package and extract the file cfa-events.xml to an easily accessible location on the device.
Content of cfa-events.xml is shown in the following lines:
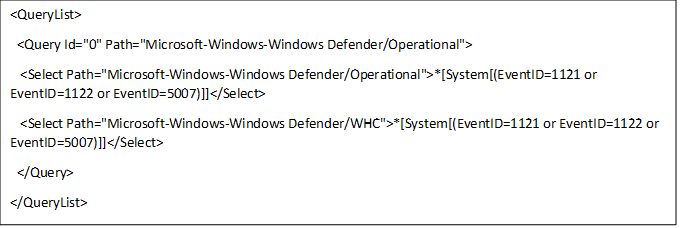
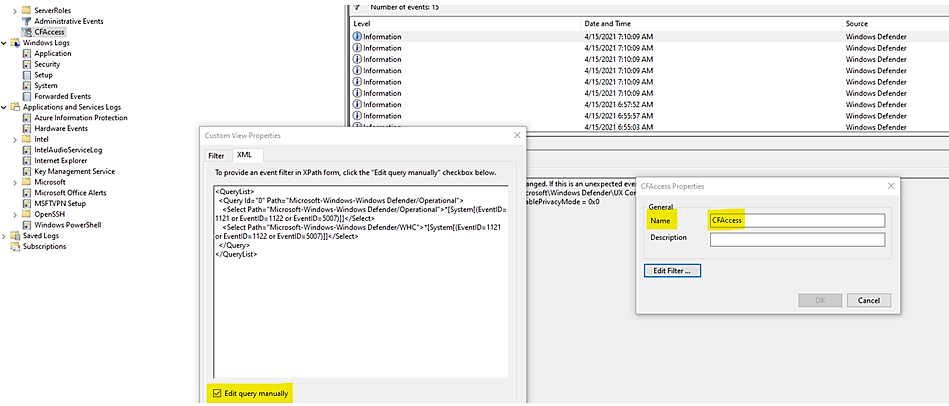
- Type Event viewer in the Start menu to open the Windows Event Viewer.
- On the left panel, under Actions, select Import custom view….
- Navigate to where you extracted cfa-events.xml and select it. Alternatively, copy the XML directly.
- Select OK.
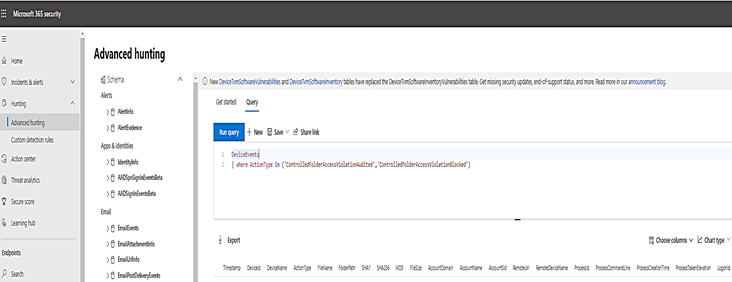
Review controlled folder access events in the Microsoft 365 Security.
M365 Security portal, advanced hunting provides detailed information of Windows Defender events as part of its alert investigation scenarios.
You can query Microsoft 365 Security data by using Advanced hunting. For Controlled Folder Access, if you are enable it audit mode, you can use advanced hunting to see how controlled folder access settings would affect your environment if they were enabled.
To query Controlled Folder Access Events by Powershell, :
DeviceEvents
| where ActionType in ('ControlledFolderAccessViolationAudited','ControlledFolderAccessViolationBlocked')
Advanced Hunting for Controlled Folder Access Events:
Query Table
WDAC- Windows Defender Application Control | DeviceEvents | where Timestamp > ago(7d) and ActionType startswith “AppControl” | summarize Machines=dcount(DeviceName) by ActionType | order by Machines desc |
Monthly report on Vulnerability | DeviceTvmSoftwareInventoryVulnerabilities | project DeviceName, SoftwareName, CveId, SoftwareVersion, VulnerabilitySeverityLevel | join (DeviceTvmSoftwareVulnerabilitiesKB | project AffectedSoftware, VulnerabilityDescription , CveId , CvssScore , IsExploitAvailable ) on CveId | project CveId , SoftwareName , SoftwareVersion , VulnerabilityDescription , VulnerabilitySeverityLevel, IsExploitAvailable , CvssScore | distinct SoftwareName , SoftwareVersion, CveId, VulnerabilityDescription , VulnerabilitySeverityLevel, IsExploitAvailable | sort by SoftwareName asc , SoftwareVersion |
WD-ASR Event | DeviceEvents | where ActionType == “AsrOfficeChildProcessAudited” and Timestamp > minTime | project BlockedProcess=FileName, ParentProcess=InitiatingProcessFileName, DeviceName, Timestamp |
WD-CFA Controlled Folder Access Event | DeviceEvents | where ActionType in (‘ControlledFolderAccessViolationAudited’,’ControlledFolderAccessViolationBlocked’) |
|
|
- We could not query by Event ID.
Until today, the built-in Defender for Endpoint sensor does not allow raw ETW access using Advanced Hunting nor forwards them.
- In Event Viewer, using XML to filter events related to Windows 10 Defender Guard,
the Event IDs are listed in the following Event Table:
Feature | Provider/source | Event ID | Description |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 1 | ACG audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 2 | ACG enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 3 | Do not allow child processes audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 4 | Do not allow child processes block |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 5 | Block low integrity images audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 6 | Block low integrity images block |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 7 | Block remote images audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 8 | Block remote images block |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 9 | Disable win32k system calls audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 10 | Disable win32k system calls block |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 11 | Code integrity guard audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 12 | Code integrity guard block |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 13 | EAF audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 14 | EAF enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 15 | EAF+ audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 16 | EAF+ enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 17 | IAF audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 18 | IAF enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 19 | ROP StackPivot audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 20 | ROP StackPivot enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 21 | ROP CallerCheck audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 22 | ROP CallerCheck enforce |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 23 | ROP SimExec audit |
Exploit protection | Security-Mitigations (Kernel Mode/User Mode) | 24 | ROP SimExec enforce |
Exploit protection | WER-Diagnostics | 5 | CFG Block |
Exploit protection | Win32K (Operational) | 260 | Untrusted Font |
Network protection | Windows Defender (Operational) | 5007 | Event when settings are changed |
Network protection | Windows Defender (Operational) | 1125 | Event when Network protection fires in Audit-mode |
Network protection | Windows Defender (Operational) | 1126 | Event when Network protection fires in Block-mode |
Attack surface reduction | Windows Defender (Operational) | 5007 | Event when settings are changed |
Attack surface reduction | Windows Defender (Operational) | 1122 | Event when rule fires in Audit-mode |
Attack surface reduction | Windows Defender (Operational) | 1121 | Event when rule fires in Block-mode |
- You could run the queries by using Microsoft 365 Security or Microsoft Defender for Endpoint.
I hope the information is useful, see you next time.
Reference:
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/controlled-folders?view=o365-worldwide
- https://www.verboon.info/2019/11/how-to-generate-a-monthly-defender-atp-threat-and-vulnerability-report/
- https://docs.microsoft.com/en-us/power-bi/report-server/configure-scheduled-refresh
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/run-advanced-query-sample-powershell?view=o365-worldwide.
- https://docs.microsoft.com/en-us/microsoft-365/enterprise/use-windows-powershell-to-create-reports-in-microsoft-365
- How to Automate PowerShell Scripts with Task Scheduler (netwrix.com)
- https://docs.microsoft.com/en-us/samples/browse/?products=mdatp
- https://github.com/microsoft/MicrosoftDefenderATP-PowerBI
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/api-power-bi?view=o365-worldwide
- https://docs.microsoft.com/en-us/power-bi/report-server/configure-scheduled-refresh
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments