This article is contributed. See the original author and article here.
This installment is part of a broader series to keep you up to date with the latest features in Azure Sentinel. The installments will be bite-sized to enable you to easily digest the new content.
*Note, this post will be updated with more information at a later time.
When it comes to investigating incidents within a Security Operation Center (SOC), valuable time can be measured in a matter of seconds. SOC Analysts tremendously benefit when there is a variety of data available within a convenient location while investigating an incident. Azure Sentinel strives to deliver such an experience. In an effort to achieve this, Azure Sentinel is now offering Entity Insights, which is now in Public Preview!
This new Entity Insights feature will allow for valuable information, such as trends and actions over a time period, to be present while investigating an incident. In order for Insights to be present within the investigation, the following data sources are needed:
- Syslog
- Security Events
- Audit Logs
- Sign-in Logs
- Office Activity
These data types provide a variety of Insights for the accounts and hosts. A few examples of the insights are:
- Actions on Accounts
- Group Additions
- Events Cleared (by user, on host)
- Process Execution
- Process Rarity
- Sign-In Activity
- and more.
Entity Insights performs queries for each Entity to pull in the relevant information. These Insights are the same as the Insights within Entity Analytics (also in Public Preview). The main difference between the two locations is the time period used, in which Entity Insights uses a period around the time of the alert instead of the current time. In the future, all Insights will be posted on the Azure Sentinel GitHub (coming soon).
How to Use:
Entity Analytics can be found within the Investigation Graph. The requirement for the information to appear is to choose an incident that includes a User or Host entity that contains logs for the data types listed above.
When in the Investigation Graph, click on an Entity within the graph. There is an option for ‘Insights’ that will be available on the right side of the screen. When selected, queries will be performed on the Entity and any result that appears will be shown.
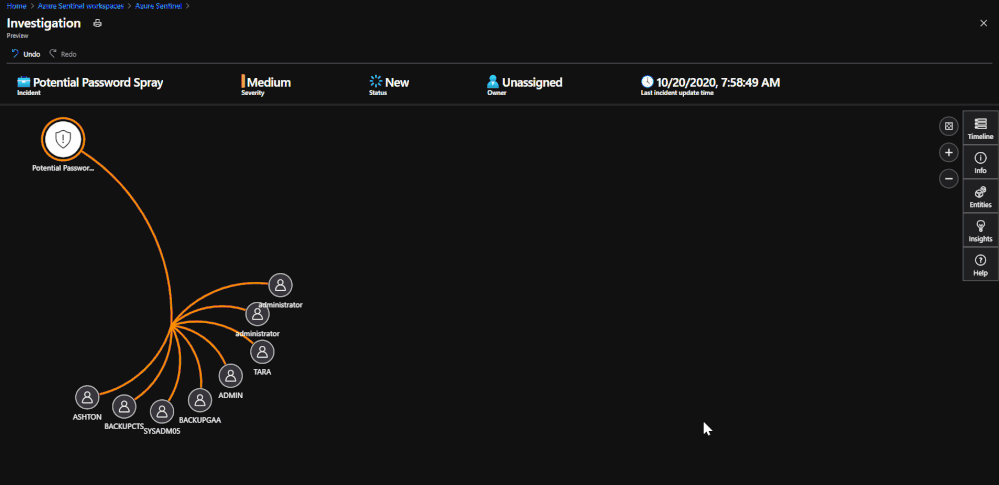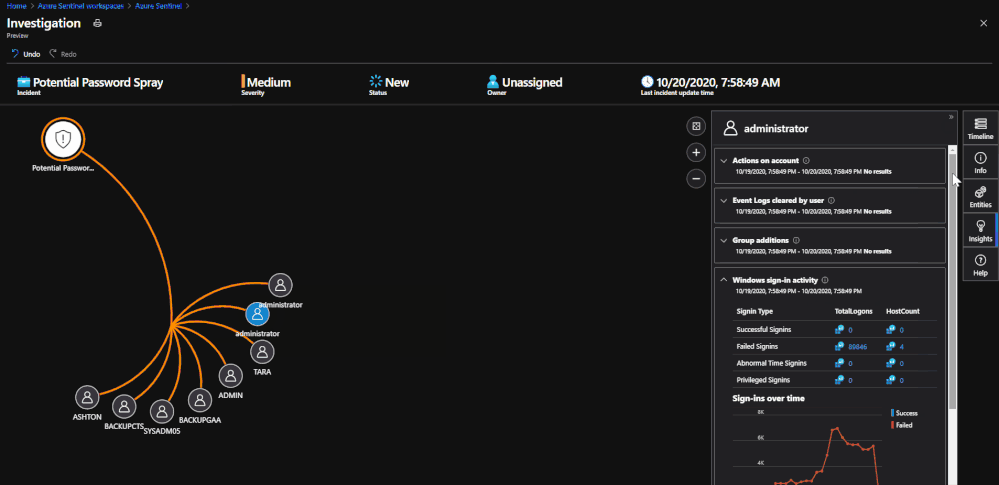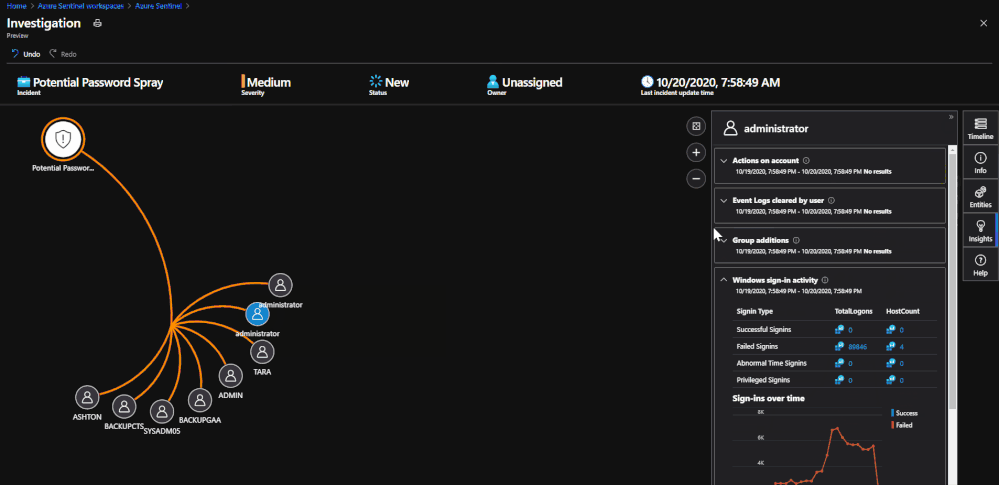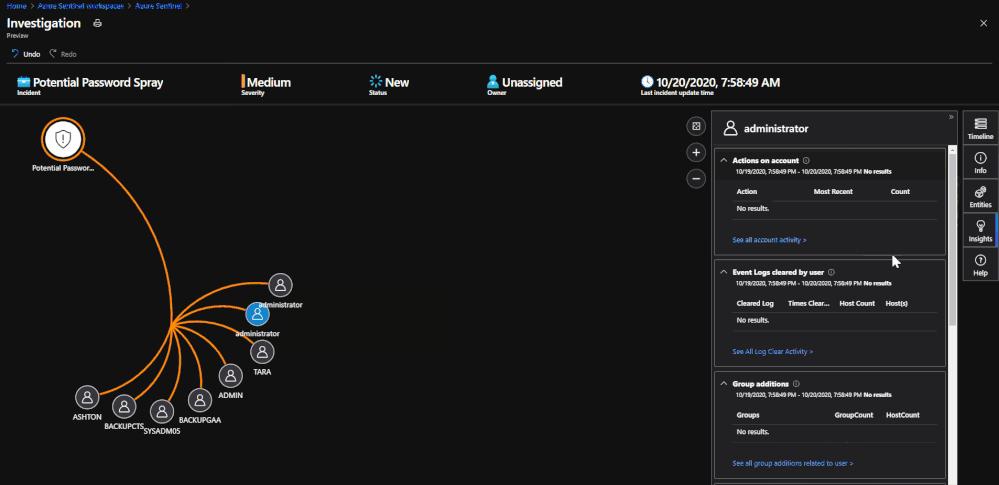
*Note: If the Insights are blank, there are not any pieces of information to show for that Entity. This can be confirmed by checking Entity Analytics if needed.
When to Use:
Entity Insights can be used with any incident that contains the Host or User entity. This feature is meant to provide valuable information within the Investigation Graph that is already being used. An example of when value is provided by Entity Insights is the gif provided above. The incident is for a password spray attempt. The Entity Insights tab provides the total number of failed sign-ins on one of the administrator accounts over a time period surrounding the alert. This also would have shown if any attempts during the spray were successful.
Get started today!
We encourage you to utilize this new feature to enhance your experience when performing investigations on newly raised incidents.
Try it out and let us know what you think!
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments