by Contributed | Jun 21, 2021 | Technology
This article is contributed. See the original author and article here.
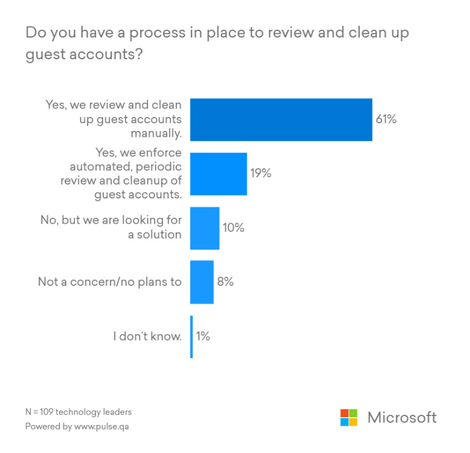
Companies collaborate with hundreds of clients, partners, and vendors every day. Today’s organizations use many applications and devices, and managing digital identities for these guests increases the risk of security breaches. More than 40% of IT leaders said that they want an identity governance solution that improves their security posture, according to an internal Microsoft survey.

These decision-makers’ top concern is the increased risk of security breaches due to distributed access to company resources. This problem is exacerbated as more companies adopt hybrid work and require secure collaboration with external users. IT admins have no way to track usage or answer the following questions:
- What content are users interacting with?
- How long have the resources been shared?
- Are accounts still active?
- Are user privileges at risk of expiring?
Organizations can manage guest access with automated reviews
More than 70% of survey respondents said they either don’t have a process for managing guest accounts or they manually manage guest accounts. Manual processes often involve reliance on custom scripts or middleware, increasing the chance of human error that leads to elevated security risk. Also, an IT admin can never know all of the external users who require access to company resources. Business managers are the ones who are best suited for identity and access management activities for their guests and external partners.
An Azure Active Directory Identity Governance solution empowers Microsoft customers to securely collaborate with guests across organizational boundaries. Customers can set up automated, periodic access reviews using an intuitive interface that provides smart recommendations, ensuring that guests gain the right access to the right resources for the right amount of time.
Once guests no longer require access to sensitive data, companies can automatically revoke their access to those resources. If a business owner or a manager isn’t in Azure AD, guests can review their own membership in a group.
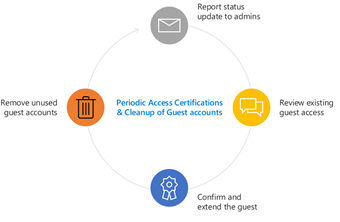
Figure 1: Access review features enable customers to securely manage guest access at scale.
Automated provisioning and deprovisioning of guest access to sensitive data enables customers to move away from custom scripts and reduces errors associated with manual processes Automated provisioning and de-provisioning of guest access into SaaS applications ensures that the only way guests can access these apps is through permissions set up by the organization and not decisions made on a case-by-case basis by an IT admin.
In large organizations, business managers are best suited to manage guest access for collaboration. Azure AD governance features put control firmly in the hands of business managers who are best suited to provide appropriate levels of access to sensitive data to external users. By delegating to non-administrators, customers can ensure that the right people are managing access to their department’s sensitive data. Delegation of responsibility reduces the IT helpdesk burden and frees up the IT staff for more strategic initiatives.
The response from Azure AD governance customers has been positive:
“Azure Active Directory guest access reviews give us that ability to be agile in our collaboration with external parties, with the right level of control, so our security, legal, and data privacy people are comfortable.” ~ Avanade
Microsoft customers in regulated industries and those that work with the government have to regularly demonstrate to auditors the effectiveness of their controls over access rights. Azure AD access reviews for guests enable these customers to easily prove to auditors that their organization has the appropriate controls in place. Azure AD provides a centralized view of all access reviews with a simple interface involving very few configuration steps, enabling IT admins to see which resources a user can or cannot access across a multi-cloud, multi-device, and fragmented application landscape.
Watch our video review of guest user access across all Microsoft 365 groups and Microsoft Teams for a step-by-step overview of Azure AD Access Reviews. To learn more about Microsoft Identity Governance solutions, visit our website.
Learn more about Microsoft identity:

by Contributed | Jun 21, 2021 | Technology
This article is contributed. See the original author and article here.
Azure Maps Location and a Smart Streetlight
For those of us that live in city centers, we regularly benefit from our connected urban environment through initiatives that are making our cities “smarter”. From the Azure IoT & Maps perspective, we look at this same benefit from the other direction. What does it mean for one location in a city to be made smarter and what are the benefits we get without maybe realizing it? To illustrate this, let us look at the typical upgrade path from a traditional streetlamp to a Smart streetlamp.

|
What are the things a streetlight can do that are autonomous?
The simplest examples of this would be using a more efficient bulb and adding an ambient light sensor so that energy is not spent lighting a bulb, even an efficient LED bulb, if it is not needed. Other environmental sensors such as temperature and humidity could allow the lamp to decide not to operate if it is too hot or too moist. However smart it may seem to be, this autonomous light would still require someone to report any failures and for it to be checked on a regular basis.
|
|
What are the benefits we can realize quickly if that streetlight, with these simple sensors, is now connected?
If the bulb fails or light chooses not to function correctly, for a reason such as it is too hot or too humid, an alert can be sent to have the light serviced. If the smart streetlight loses connectivity, it can still operate autonomously but an alert can be generated at the reporting center that this smart device has stopped communicating and should be checked. A connected device can decide how often it wants to report but it can also be asked for status as needed. This bi-directional communication completely removes the need to check a device unless there is a reported reason to do so saving time, resources, and money!
|

|
What are extra benefits we can realize if that streetlight has sensors added that go beyond the function of the streetlight itself?
Some cities have chosen to add microphones and listen for abnormal sounds such as a gunshot. Based on the decibels of the sound at various smart streetlamp locations, police and ambulance resources can be sent close to where the sound originated. In higher traffic regions, a camera may also be added for extra security and information gathering.
|
In all cases, it is important to know where the lamp is located and that is where Azure Maps pulls it all together.
If you would like to dig deeper into Smart Devices, Azure IoT and Azure Maps, I have the following recommended links:
Thank you for your interest in Azure Maps. If you have any questions feel free to post them in our Q&A section, we are here to help!
by Contributed | Jun 21, 2021 | Technology
This article is contributed. See the original author and article here.
Jeremy and Paul talk with Brian T. Jackett about the Graph Connectors API.
https://www.podbean.com/player-v2/?i=ms7mb-106d50d-pb&from=pb6admin&share=0&download=0&rtl=0&fonts=Courier%20New&skin=1&btn-skin=6
Listen to the show here: Microsoft Graph Connectors with Brian T. Jackett (m365devpodcast.com)
Links from the show:
Microsoft News
Community Links
by Contributed | Jun 21, 2021 | Technology
This article is contributed. See the original author and article here.
By Per Larsen – Sr. Program Manager | Microsoft Endpoint Manager – Intune
How to manage compliance policies on HoloLens devices is one of the most common questions we get from customers as they start to manage their HoloLens fleet with Microsoft Endpoint Manager.
Compliance policies are used to mark the device compliant or non-compliant, which can be used in conjunction with Azure Active Directory (Azure AD) Conditional Access to allow or block access to corporate data.
Microsoft Intune as a capability of Endpoint Manager, uses Configuration Service Providers (CSPs) to control and verify many of the settings in the compliance policy, so those CSP’s need to be supported on the HoloLens. You can find out more about supported CSPs in the Policies in Policy CSP supported by HoloLens 2 document.
Note:
Configuration Manager Compliance is not supported with Hololens devices. The ConfigMgr agent is a Win32 app, and Win32 apps cannot run on a HoloLens device.
HoloLens 2 runs the Windows Holographic Operating System, which is not the same as Windows 10 Desktop, and therefore some capabilities (like win32 apps) do not exist in this platform.
|
The same compliance policy is used for Windows 10 desktop and HoloLens in Microsoft Intune, however some settings supported for Windows 10 are not available for HoloLens. This is similar to how BitLocker and HoloLens work.
HoloLens 2 has BitLocker Device Encryption enabled automatically on the operating system and fixed data volumes and cannot be turned off – even by IT administrators – so that the device is always protected.
Settings available for HoloLens:
|
Can you use the profile?
|
Device Health
|
|
Require BitLocker
|
Not applicable
|
Require Secure Boot to be enabled on the device
|
Not applicable
|
Require code integrity
|
Not applicable
|
Device Properties
|
|
Operating System Version
|
Yes
|
Minimum OS version
|
Yes
|
Maximum OS version
|
Yes
|
Minimum OS version for mobile devices
|
Not applicable
|
Maximum OS version for mobile devices
|
Not applicable
|
Valid operating system builds
|
Yes
|
Configuration Manager Compliance
|
|
Require device compliance from Configuration Manager
|
Not applicable
|
System Security
|
|
Password
|
|
Require a password to unlock mobile devices
|
Yes
|
Simple passwords
|
Yes
|
Password type
|
Yes
|
Minimum password length
|
Yes
|
Maximum minutes of inactivity before password is required
|
Not applicable
|
Password expiration (days)
|
Yes
|
Number of previous passwords to prevent reuse
|
Yes
|
Require password when device returns from idle state (Mobile and Holographic)
|
Yes
|
Require encryption of data storage on device.
|
Not applicable
|
Device Security
|
|
Firewall
|
*
|
Trusted Platform Module (TPM)
|
Yes
|
Antivirus
|
Not applicable
|
Antispyware
|
Not applicable
|
Defender
|
|
Microsoft Defender Antimalware
|
*
|
Microsoft Defender Antimalware minimum version
|
*
|
Microsoft Defender Antimalware security intelligence up-to-date
|
*
|
Real-time protection
|
*
|
Microsoft Defender for Endpoint
|
|
Microsoft Defender for Endpoint rules
|
|
Require the device to be at or under the machine risk score
|
*
|
Can you use the profile?
Yes = The settings will work on HoloLens
Not applicable = Will show as Not applicable in the compliance status
* = Settings are not included in the supported list of CSP for Windows Holographic for Business
How to deploy a compliance policy to HoloLens
Scenarios drive whether you deploy your compliance policy to users in user groups or devices in device groups. When a compliance policy is deployed to a user, all the user’s devices are checked for compliance.
Example Scenario 1
Let’s take a HoloLens device that is enrolled into Intune by the Windows Autopilot self-deploying mode process and automatically put in KIOSK mode. When onboarded with Autopilot the device is enrolled . In this case, we recommend deploying your compliance policy to a device group. This can be done with an Azure AD static or dynamic group. You can populate a dynamic group with HoloLens devices by using a device attribute where “Model” is “HoloLens 2” or by a Group Tag set on the Autopilot object.
Example Scenario 2
You have a group of users that use both Windows 10 Desktop devices and HoloLens 2 devices. In this case, the same Intune compliance policy will be applicable to both devices. It therefore makes sense to deploy your compliance policy to a user group. Any setting that is not applicable on the HoloLens 2 can mark the device non-complaint.
Create the compliance policy
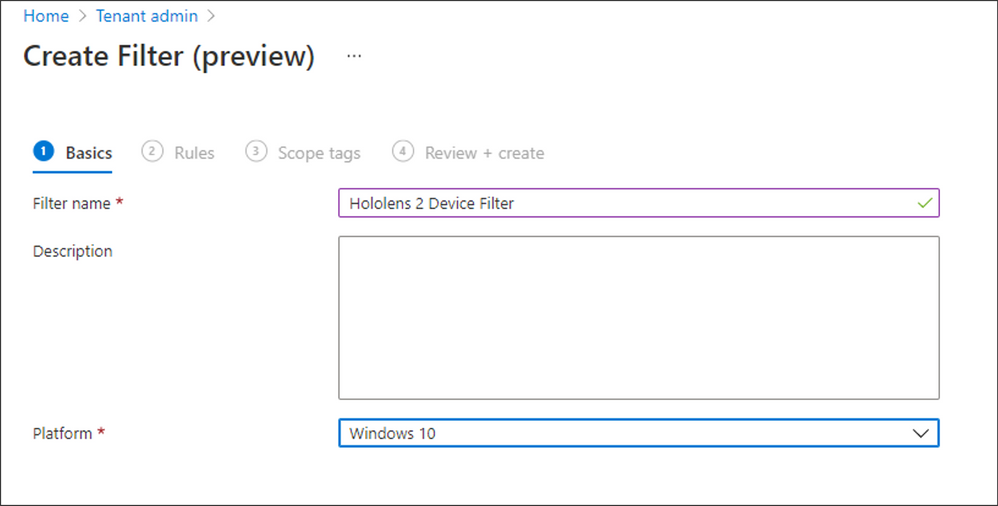
First, create a Filter to include or exclude HoloLens 2 devices when using user-based targeting:
- Navigate to Tenant admin > Filters (preview) > Create, choose a Filter name.
- From the Platform dropdown field, select “Windows 10” and click Next.

- Complete the Rules section as follows, then click Next.
- Property = Model
- Operator = Equals
- Value = HoloLens 2
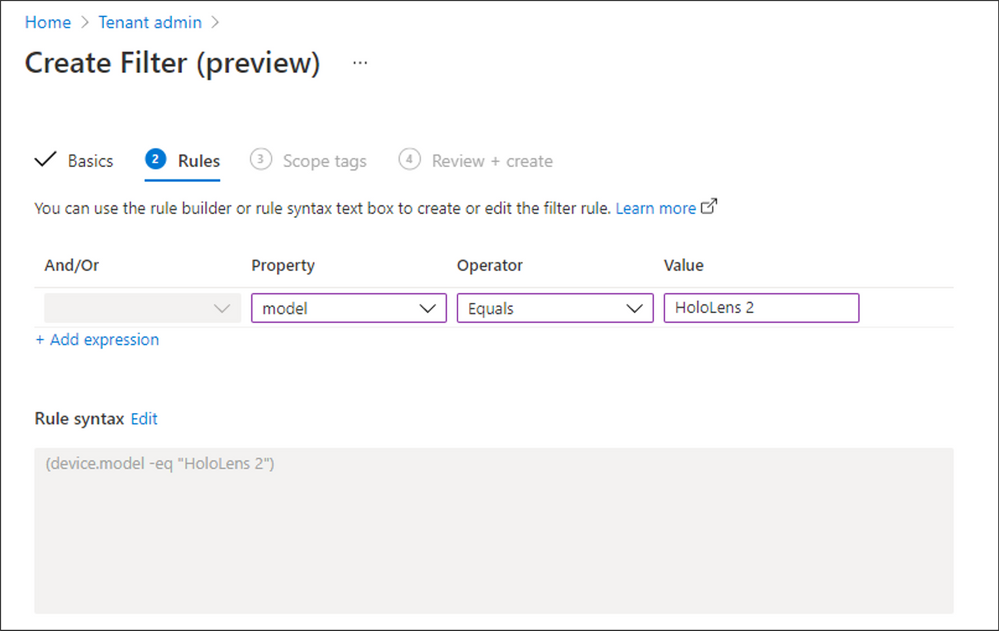
- Lastly, assign Scope tags if required, review your configuration, and then click Create.
Next, create the associated compliance policy:
- Navigate to Devices > Windows > Compliance policies and select Create Policy.
- Start by creating a simple compliance policy for your HoloLens devices, such as the following example:
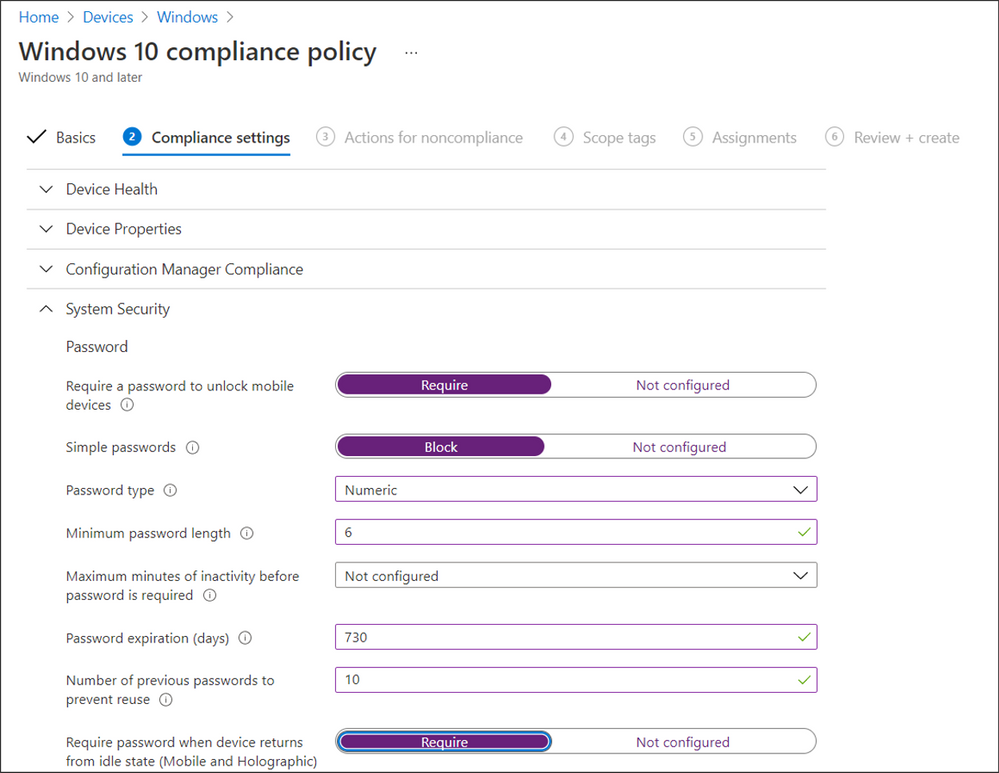
Note that there is no primary user when a HoloLens 2 device is onboarded with Autopilot for HoloLens, as shown in the following image:
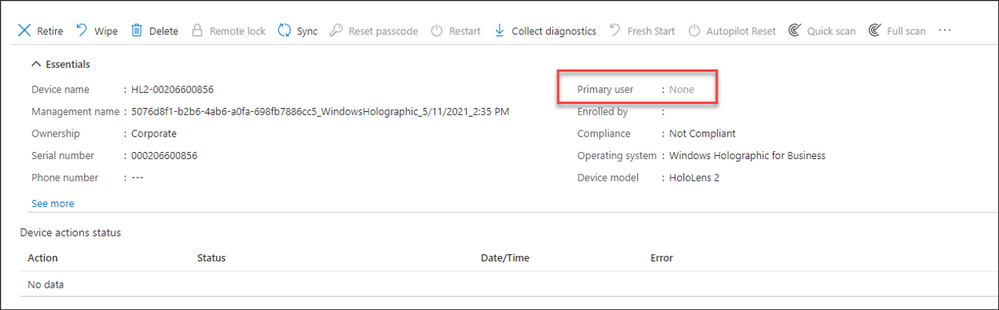
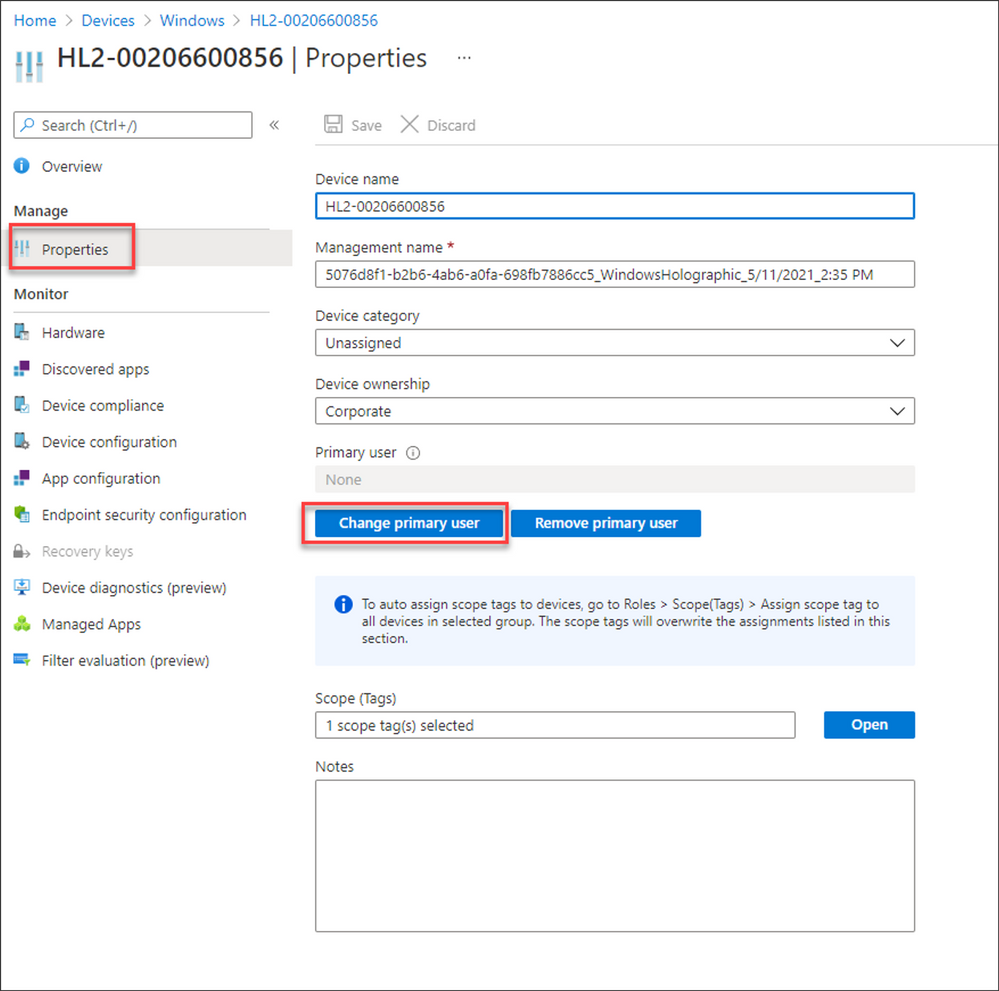
If a primary user is not identified, no one will receive an email if the compliance state of the device changes from compliant to non-compliant. You can change this by setting a primary user on the device so that Intune can send an email notification:
- Navigate Devices > Windows and find the device you want to assign a primary user to.
- Select Properties, click on Change Primary user, and then select the relevant user that will receive the non-compliant notification emails.
Conclusion
As new device types like HoloLens enter your endpoint estate, it’s critical that these devices are compliant with your corporate security policies to protect organizational data. Use these policies with Conditional Access to allow or block access to company resources for HoloLens 2 devices.
More info and feedback
For further resources on this subject, please see the links below.
Manage and use different device management features on Windows Holographic and HoloLens devices with Intune
Enroll HoloLens in MDM
Windows Autopilot for HoloLens 2
Let us know if you have any additional questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
by Contributed | Jun 21, 2021 | Technology
This article is contributed. See the original author and article here.
While the pandemic has slowed down many aspects of life, research shows that the last 18 months has accelerated digitization and the tech employment market. By 2025, Microsoft estimates that 149 million new jobs will be added in technology industries. Leading those gains will be 98 million new software development jobs and 23 million cloud and data roles.1
To help those around the world prepare for this growth, Microsoft’s skills initiative offers free training content and discounted certifications, and has helped over 30 million people in 249 countries and territories gain access to essential digital skills. As part of our ongoing #ProudToBeCertified blog series, we’d like to introduce you to Ricardo Lessa and how he went beyond personal advancement during the COVID crisis.
Ricardo: Helping others starts with helping yourself
Ricardo Lessa has a history of resilience and self-motivation. When he came out of the datacenter, Ricardo launched his career as an entrepreneur. For about a decade, he ran his own company until the pandemic struck in 2020. When the pandemic started, “My sources of income were literally cut off,” says Ricardo. He was forced to close his business. Searching for new opportunities, a Microsoft MVP and colleague introduced him to the power of certification through Microsoft Learn.
Making the most of available resources, Ricardo was able to earn Microsoft Certifications that helped him land a job as a pre-sales engineer. And that’s just the beginning. Certification is more than a credential; it’s a personal confidence builder, as Ricardo explains, “the term ‘proud to be’ is the sense of accomplishment for getting the job done, for having completed a stage, for having progressed, for truly scoring a win. And, on a personal level, it greatly improves our focus, our discipline and, consequently, our results.”
Ricardo was inspired by how his colleague’s advice had made a real impact on his career. So, they joined forces and found a way to help others in similar circumstances. “This situation and its demands inspired us to do something new – something unique,” he says. And together, they began a new technical support community: CloudExpert, an online network of support, training, and resources for professionals designed to get members trained to progress on their career paths. The goal of this network is to help peers rekindle their dreams and get back in the job market sooner than later.
By creating this new support system for others, Ricardo discovered more about himself than he ever imagined. “I was able to believe again in the possibility of starting over,” Ricardo says, “updating myself and returning to the IT market. I dreamed that I could influence others so that they can overcome hardship and believe in a new beginning. And it happened!”

Share your #ProudToBeCertified stories and opportunities
Like Ricardo’s initiative, the Microsoft Certification community can help you and your peers move forward, no matter how the world changes around you. Keep an eye out for more stories in this #ProudToBeCertified blog series and the latest videos – where people like you are dedicating themselves to continuing education to get an edge in our competitive and changing market.
Have a Microsoft Certifications story to share? We’d love to hear how you got started on your path, where it took you, the obstacles you overcame, or the confidence you gained from earning your first or fifteenth certification. Submit your own on Twitter, LinkedIn, or your preferred platform with #ProudToBeCertified.
Related posts:
1Microsoft Data Science, utilizing LinkedIn Data. Methodology and assumptions can be found in the white paper “Methodology: Digitization Capacity of the World Economy.”
2Official Microsoft Blog, “Building a more inclusive skills-based economy: The next steps for our global skills initiative,” Brad Smith, March 30, 2021














Recent Comments