NCSC Releases 2021 Annual Review
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
CISA has added four new vulnerabilities to its Known Exploited Vulnerabilities Catalog, which require remediation from federal civilian executive branch (FCEB) agencies by December 1, 2021. CISA has evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for malicious cyber actors of all types and pose significant risk to the federal enterprise.
| CVE Number | CVE Title | Remediation Due Date |
| CVE-2021-22204 | Exiftool Remote Code Execution vulnerability | 12/01/2021 |
| CVE-2021-40449 | Microsoft Win32k Elevation of Privilege | 12/01/2021 |
| CVE-2021-42292 | Microsoft Excel Security Feature Bypass | 12/01/2021 |
| CVE-2021-42321 | Microsoft Exchange Server Remote Code Execution | 12/01/2021 |
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the meet the specified criteria.
This article is contributed. See the original author and article here.
Azure Purview lets you govern Azure SQL Databases at scale, and with ease. The following details how to register and scan your Azure SQL Database, along with how to extract lineage to view and analyze how data is being transformed. It also describes how to discover assets easily by grouping Azure SQL Database schemas and tables into Purview collections.
Register and scan
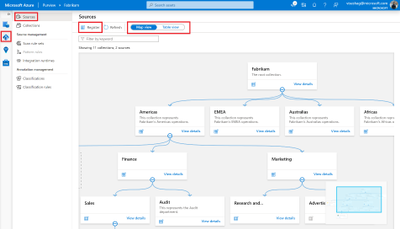
Navigate to your Purview account and click on the Data Map section to the left. You can view your data estate map and choose to view your sources in table format as well.

Purview now supports 20-plus source types, ranging from Azure SQL Database, to AWS S3, to Oracle Database. Sources can be registered in two ways: by either clicking on the register button on the top left or by navigating to the collection that you’d like to register the source to and clicking on the Register quick action icon. Then click on the Azure SQL Database source tile and fill in the required details.
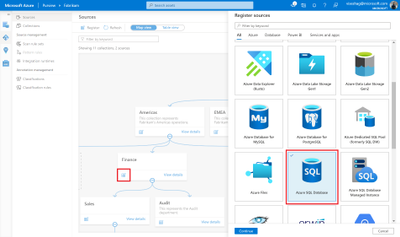
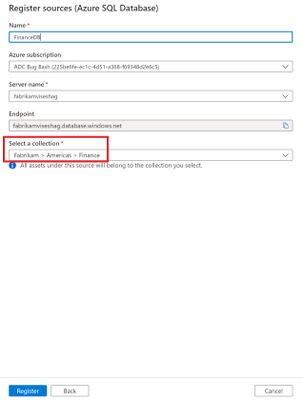
As part of the required details, register your source to a collection of interest. In our example, we register the source to the Finance collection.
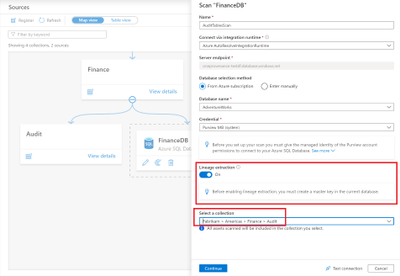
Once your source is registered, the next step is to set up a scan. While setting up your scan, fill in details for the integration runtime, database name, and credential. You can also set up your scan with a collection; in our example, it’s the Audit collection under Finance. So you can now scope your scan to only the Audit tables to ensure all assets are scanned into the catalog with the right collection associated for discovery and access control.
See results of the scan by clicking on View details for your source.
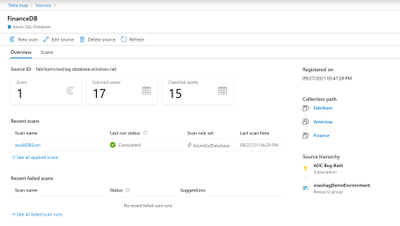
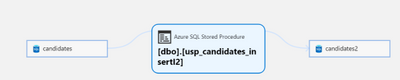
Lineage extraction (preview)
While setting up your scan, you can now extract lineage from stored procedures and other artifacts in your Azure SQL Database source.
Learn more on how to get onboarded to the Preview program here.
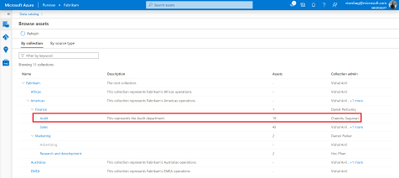
Discover—search and browse for your Azure SQL Database tables
Once a scan completes, you can discover assets either via search or browse. To search, enter keywords in the search bar on the top of the Purview studio and narrow down results by the facet filters Purview provides.
To browse, click on the browse assets tile on the catalog home page, navigate to the By collection tab and navigate to the collection that you scanned assets into. In our example, it would be Audit. If you have access to this collection, click on it to browse for your assets.
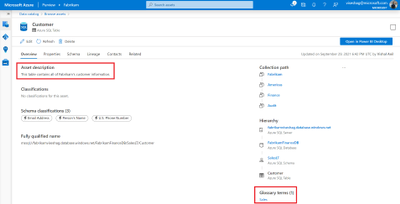
Add business metadata to your Azure SQL database assets
You can also navigate to one of your Azure SQL tables and view details. To aid in discoverability and compliance, add descriptions and business glossary terms by clicking on the Edit button.
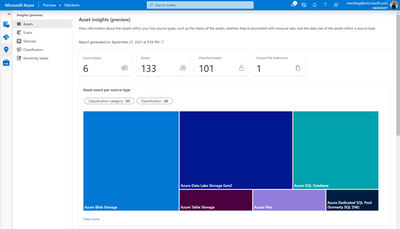
Insights (preview)
Finally, view all your Azure SQL Database-related insights around assets, scans, glossary, classification, and labels by navigating to the Insights section of Purview.
Get started today!
This article is contributed. See the original author and article here.
Actions to Take Today to Protect Against Iranian State-Sponsored Malicious Cyber Activity
• Immediately patch software affected by the following vulnerabilities: CVE-2021-34473, 2018-13379, 2020-12812, and 2019-5591.
• Implement multi-factor authentication.
• Use strong, unique passwords.
Note: this advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, version 10. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques.
This joint cybersecurity advisory is the result of an analytic effort among the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC) to highlight ongoing malicious cyber activity by an advanced persistent threat (APT) group that FBI, CISA, ACSC, and NCSC assess is associated with the government of Iran. FBI and CISA have observed this Iranian government-sponsored APT group exploit Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021 to gain initial access to systems in advance of follow-on operations, which include deploying ransomware. ACSC is also aware this APT group has used the same Microsoft Exchange vulnerability in Australia.
The Iranian government-sponsored APT actors are actively targeting a broad range of victims across multiple U.S. critical infrastructure sectors, including the Transportation Sector and the Healthcare and Public Health Sector, as well as Australian organizations. FBI, CISA, ACSC, and NCSC assess the actors are focused on exploiting known vulnerabilities rather than targeting specific sectors. These Iranian government-sponsored APT actors can leverage this access for follow-on operations, such as data exfiltration or encryption, ransomware, and extortion.
This advisory provides observed tactics and techniques, as well as indicators of compromise (IOCs) that FBI, CISA, ACSC, and NCSC assess are likely associated with this Iranian government-sponsored APT activity.
The FBI, CISA, ACSC, and NCSC urge critical infrastructure organizations to apply the recommendations listed in the Mitigations section of this advisory to mitigate risk of compromise from Iranian government-sponsored cyber actors.
For more information on Iranian government-sponsored malicious cyber activity, see us-cert.cisa.gov/Iran.
Click herefor a PDF version of this report.
Since at least March 2021, the FBI and CISA have observed Iranian government-sponsored APT actors leverage Microsoft Exchange and Fortinet vulnerabilities to target a broad range of victims across multiple critical infrastructure sectors in furtherance of malicious activities. Observed activity includes the following.
elie to further enable malicious activity. Note: for previous FBI reporting on this activity, refer to FBI FLASH: APT Actors Exploiting Fortinet Vulnerabilities to Gain Initial Access for Malicious Activity.91.214.124[.]143 and 162.55.137[.]20—which FBI and CISA judge are associated with Iranian government cyber activity—to further enable malicious activity against the hospital’s network. The APT actors accessed known user accounts at the hospital from IP address 154.16.192[.]70, which FBI and CISA judge is associated with government of Iran offensive cyber activity.CVE-2021-34473—to gain initial access to systems in advance of follow-on operations.ACSC considers that this APT group has also used the same Microsoft Exchange vulnerability (CVE-2021-34473) in Australia.
FBI, CISA, ACSC, and NCSC assess the following tactics and techniques are associated with this activity.
The APT actors have used the following malicious and legitimate tools [T1588.001, T1588.002] for a variety of tactics across the enterprise spectrum.
The Iranian government-sponsored APT actors gained initial access by exploiting vulnerabilities affecting Microsoft Exchange servers (CVE-2021-34473) and Fortinet devices (CVE-2018-13379, CVE-2020-12812, and CVE-2019-5591) [T1190].
The Iranian government-sponsored APT actors may have made modifications to the Task Scheduler [T1053.005]. These modifications may display as unrecognized scheduled tasks or actions. Specifically, the below established tasks may be associated with this activity:
SynchronizeTimeZoneGoogleChangeManagementMicrosoftOutLookUpdaterMicrosoftOutLookUpdateScheduleThe Iranian government-sponsored APT actors may have established new user accounts on domain controllers, servers, workstations, and active directories [T1136.001, T1136.002]. Some of these accounts appear to have been created to look similar to other existing accounts on the network, so specific account names may vary per organization. In addition to unrecognized user accounts or accounts established to masquerade as existing accounts, the following account usernames may be associated with this activity:
SupportHelpelieWADGUtilityAccountThe FBI and CISA observed outbound File Transfer Protocol (FTP) transfers over port 443.
The APT actors forced BitLocker activation on host networks to encrypt data [T1486]. The corresponding threatening notes were either sent to the victim or left on the victim network as a .txt file. The ransom notes included ransom demands and the following contact information.
The FBI, CISA, ACSC, and NCSC recommend that organizations using Microsoft Exchange servers and Fortinet investigate potential suspicious activity in their networks.
Note: for additional approaches on uncovering malicious cyber activity, see joint advisory Technical Approaches to Uncovering and Remediating Malicious Activity, authored by CISA and the cybersecurity authorities of Australia, Canada, New Zealand, and the United Kingdom.
The FBI, CISA, ACSC, and NCSC urge network defenders to apply the following mitigations to reduce the risk of compromise by this threat.
IP addresses and executables files are listed below.
IP Addresses
91.214.124[.]143 162.55.137[.]20 154.16.192[.]70Executable files observed in this activity are identified in table 1.
Table 1: Executable Files
| Filename: | MicrosoftOutLookUpdater[.]exe | |
|---|---|---|
| MD5: | 1444884faed804667d8c2bfa0d63ab13 | |
| SHA-1: | 95E045446EFB8C9983EBFD85E39B4BE5D92C7A2A | |
| SHA-256: | c51fe5073bd493c7e8d83365aace3f9911437a0f2ae80042ba01ea46b55d2624 | |
| SHA-512: | 6451077B99C5F8ECC5C0CA88FE272156296BEB91218B39AE28A086DBA5E7E39813F044F9AF0FEDBB260941B1CD52FA237C098CBF4B2A822F08E3E98E934D0ECF | |
| Filename: | MicrosoftOutlookUpdater.bat | |
| MD5: | 6735be6deea16d03cb628b553d71fe91 | |
| SHA-1 | 95E045446EFB8C9983EBFD85E39B4BE5D92C7A2A | |
| SHA-256 | C51FE5073BD493C7E8D83365AACE3F9911437A0F2AE80042BA01EA46B55D2624 | |
| SHA-512 | 6451077B99C5F8ECC5C0CA88FE272156296BEB91218B39AE28A086DBA5E7E39813F044F9AF0FEDBB260941B1CD52FA237C098CBF4B2A822F08E3E98E934D0ECF | |
| Filename: | MicrosoftOutlookUpdater.xml | |
| MD5: | AA40C49E309959FA04B7E5AC111BB770 | |
| SHA-1 | F1D90E10E6E3654654E0A677763C9767C913F8F0 | |
| SHA-256 | 5C818FE43F05F4773AD20E0862280B0D5C66611BB12459A08442F55F148400A6 | |
| SHA-512 | E55A86159F2E869DCDB64FDC730DA893718E20D65A04071770BD32CAE75FF8C34704BDF9F72EF055A3B362759EDE3682B3883C4D9BCF87013076638664E8078E | |
| Filename: | GoogleChangeManagement.xml | |
| MD5: | AF2D86042602CBBDCC7F1E8EFA6423F9 | |
| SHA-1 | CDCD97F946B78831A9B88B0A5CD785288DC603C1 | |
| SHA-256 | 4C691CCD811B868D1934B4B8E9ED6D5DB85EF35504F85D860E8FD84C547EBF1D | |
| SHA-512 | 6473DAC67B75194DEEAEF37103BBA17936F6C16FFCD2A7345A5A46756996FAD748A97F36F8FD4BE4E1F264ECE313773CC5596099D68E71344D8135F50E5D8971 | |
| Filename: | Connector3.exe | |
| MD5: | e64064f76e59dea46a0768993697ef2f | |
| Filename: | Audio.exe or frpc.exe | |
| MD5: | b90f05b5e705e0b0cb47f51b985f84db | |
| SHA-1 | 5bd0690247dc1e446916800af169270f100d089b | |
| SHA-256: | 28332bdbfaeb8333dad5ada3c10819a1a015db9106d5e8a74beaaf03797511aa | |
| Vhash: | 017067555d5d15541az28!z | |
| Authentihash: | ed463da90504f3adb43ab82044cddab8922ba029511da9ad5a52b8c20bda65ee | |
| Imphash: | 93a138801d9601e4c36e6274c8b9d111 | |
| SSDEEP: | 98304:MeOuFco2Aate8mjOaFEKC8KZ1F4ANWyJXf/X+g4:MeHFV2AatevjOaDC8KZ1xNWy93U | |
| Note: |
Identical to “frpc.exe” available at: https://github[.]com/fatedier/frp/releases/download/v0.34.3/frp_0.34.3_windows_amd64.zip |
|
| Filename: | Frps.exe | |
| MD5: | 26f330dadcdd717ef575aa5bfcdbe76a | |
| SHA-1 | c4160aa55d092cf916a98f3b3ee8b940f2755053 | |
| SHA-256: | d7982ffe09f947e5b4237c9477af73a034114af03968e3c4ce462a029f072a5a | |
| Vhash: | 017057555d6d141az25!z | |
| Authentihash: | 40ed1568fef4c5f9d03c370b2b9b06a3d0bd32caca1850f509223b3cee2225ea | |
| Imphash: | 91802a615b3a5c4bcc05bc5f66a5b219 | |
| SSDEEP: | 196608:/qTLyGAlLrOt8enYfrhkhBnfY0NIPvoOQiE:GLHiLrSfY5voO | |
| Note: |
Identical to “frps.exe” available at: https://github[.]com/fatedier/frp/releases/download/v0.33.0/frp_0.33.0_windows_amd64.zip |
Table 2 identifies MITRE ATT&CK Tactics and techniques observed in this activity.
Table 2: Observed Tactics and Techniques
To report suspicious or criminal activity related to information found in this Joint Cybersecurity Advisory, contact your local FBI field office at https://www.fbi.gov/contact-us/field-offices, or the FBI’s 24/7 Cyber Watch (CyWatch) at (855) 292-3937 or by e-mail at CyWatch@fbi.gov. When available, please include the following information regarding the incident: date, time, and location of the incident; type of activity; number of people affected; type of equipment used for the activity; the name of the submitting company or organization; and a designated point of contact. To request incident response resources or technical assistance related to these threats, contact CISA at CISAServiceDesk@cisa.dhs.gov. Australian organizations can visit cyber.gov.au or call 1300 292 371 (1300 CYBER 1) to report cybersecurity incidents and access alerts and advisories.
Initial Version: November 17, 2021
This product is provided subject to this Notification and this Privacy & Use policy.
This article is contributed. See the original author and article here.
CISA, the Federal Bureau of Investigation (FBI), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC) have released a joint Cybersecurity Advisory highlighting ongoing malicious cyber activity by an advanced persistent threat (APT) group that FBI, CISA, ACSC, and NCSC assess is associated with the government of Iran. FBI and CISA have observed this Iranian government-sponsored APT exploit Fortinet and Microsoft Exchange ProxyShell vulnerabilities to gain initial access to systems in advance of follow-on operations, which include deploying ransomware.
Joint Cybersecurity Advisory AA21-321A provides observed tactics and techniques, as well as indicators of compromise that FBI, CISA, ACSC, and NCSC assess are likely associated with this Iranian government-sponsored APT activity. FBI, CISA, ACSC, and NCSC urge critical infrastructure organizations to apply the recommendations listed in the advisory to mitigate risk of compromise from Iranian government-sponsored cyber actors.
CISA also recommends reviewing its Iran Cyber Threat Overview and other Iran-related Advisories.
Recent Comments