by Scott Muniz | Aug 24, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released CISA Insights: Preparing Critical Infrastructure for Post-Quantum Cryptography, which outlines the actions that critical infrastructure stakeholders should take now to prepare for their future migration to the post-quantum cryptographic standard that the National Institute of Standards and Technology (NIST) will publish in 2024.
CISA strongly urges critical infrastructure stakeholders follow the recommendations in the Insights now to ensure a smooth migration to the post-quantum cryptography standard.
by Scott Muniz | Aug 23, 2022 | Security, Technology
This article is contributed. See the original author and article here.
VMware has released a security update to address a vulnerability in Tools. A remote attacker could likely exploit the vulnerability to take control of an affected system.
CISA encourages users and administrators to review VMware Security Advisory VMSA-2022-0024 and apply the necessary update.

by Contributed | Aug 23, 2022 | Technology
This article is contributed. See the original author and article here.

Before we start, please note that if you want to see a table of contents for all the sections of this blog and their various Purview topics, you can locate them in the following link:
Microsoft Purview- Paint By Numbers Series (Part 0) – Overview – Microsoft Tech Community
Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Information Protection section of this blog series is aimed at Security and Compliance officers who need to properly label data, encrypt it where needed.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through using Compliance Manager to run an assessment.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Purview, including:
- Data Classification
- Information Protection
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Data Lifecycle Management (retention and disposal)
- Records Management (retention and disposal)
- eDiscovery
- Insider Risk Management (IRM)
- Priva
- Advanced Audit
- Microsoft Cloud App Security (MCAS)
- Information Barriers
- Communications Compliance
- Licensing
It is presumed that you have a pre-existing understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
For details on licensing (i.e. which components and functions of Purview are in E3 vs E5) you will need to contact your Microsoft Security Specialist, Account Manager, or certified partner.
Overview of Document
This document will give a brief explanation of Compliance Manager and walk you through the basic tabs and aspects of the tool
- Add Assessment
- Step through the assessment sections
- Overview
- Progress (tab)
- Controls (tab)
- Improvement Actions (tab)
- Microsoft Actions (tab)
Use Case
An administrator wants to run their first Compliance Manager assessment.
Definitions
- Actions– the things that need to be done to mark a Control as completed and
- Assessments – these help you implement data protection controls specified by compliance, security, privacy, and data protection standards, regulations, and laws. Assessments include actions that have been taken by Microsoft to protect your data, and they’re completed when you take action to implement the controls included in the assessment.
- Assessment Templates – these templates track compliance with over 300 industry and government regulations around the world.
- Compliance Score – Compliance Manager awards you points for completing improvement actions taken to comply with a regulation, standard, or policy, and combines those points into an overall compliance score. Each action has a different impact on your score depending on the potential risks involved. Your compliance score can help prioritize which action to focus on to improve your overall compliance posture. You receive an initial score based on the Microsoft 365 data protection baseline. This baseline is a set of controls that includes key regulations and standards for data protection and general data governance.
- Controls – the various requirements in your tenant that must be met to meet a part of an assessment.
- Control Family – a group of Controls.
- Microsoft Actions – These are actions that Microsoft has performed inside of your tenant to help it meet a specific assessment.
- Progress – each assessment has a progress chart to help you visualize the progress you are making to meet the requirements of the assessment
- Your Improvement Actions – These are actions that you and your organization must perform to meet a specific assessment/certification/regulation.
Done – Notes
Types of Assessments in Compliance Manager:
This is taken from the official Microsoft documentation (see the link in the Appendix and Links section):
“Compliance Manger can be used to assess different types of products. All templates, except the Microsoft Data Protection Baseline default template, come in two versions:
- A version that applies to a pre-defined product, such as Microsoft 365, and
- A universal version that can be tailored to suit other products.
Assessments from universal templates are more generalized but offer expanded versatility, since they can help you easily track your organization’s compliance across multiple products.
Note that US Government Community (GCC) Moderate, GCC High, and Department of Defense (DoD) customers cannot currently use universal templates.”
Note – for this blog entry, we will not be running any further discussions or comparisons on Microsoft and/or Universal assessments.
Pre-requisites
It is recommended you read the official Microsoft documentation on Compliance Manager and the Paint By Numbers – Compliance Manager – Overview (Part 9a) blog.
Add an Assessment
Now that you have a basic understanding of Compliance Manager (See Part 9a – Compliance Manager – Overview blog entry), we will add an assessment.
- Go to Compliance Manager – Assessments
- Click Add assessment.

- Click Select template.
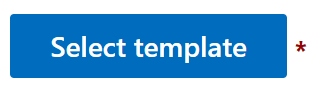
- At the time of writing this blog, there are 700+ templates. Search the list and see which assessment is most applicable for your need, regulation, certification, etc. I have chosen the EU GDPR for Microsoft assessment for this blog entry. Once you have the assessment you want, click Save.

- You will then see your assessment populated with information on the assessment. Click Next.
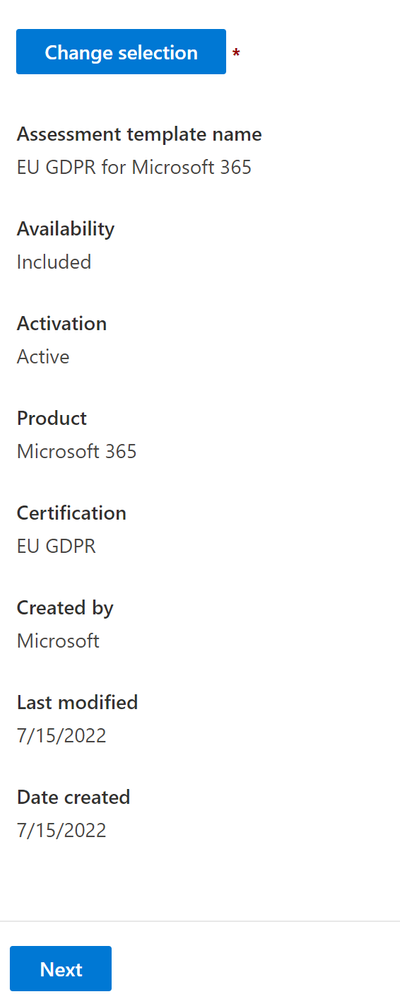
- On the next step of the wizard, the Product will be preselected (because I chose an assessment specific to Microsoft). We will just give it a name and then add an assessment Group.
- For the Assessment group, I selected Default Group. As for what an Assessment Group is, here is the official definition from the Microsoft Documentation:
“When you create an assessment, you’ll need to assign it to a group. Groups are containers that allow you to organize assessments in a way that is logical to you, such as by year or regulation, or based on your organization’s divisions or geographies.”
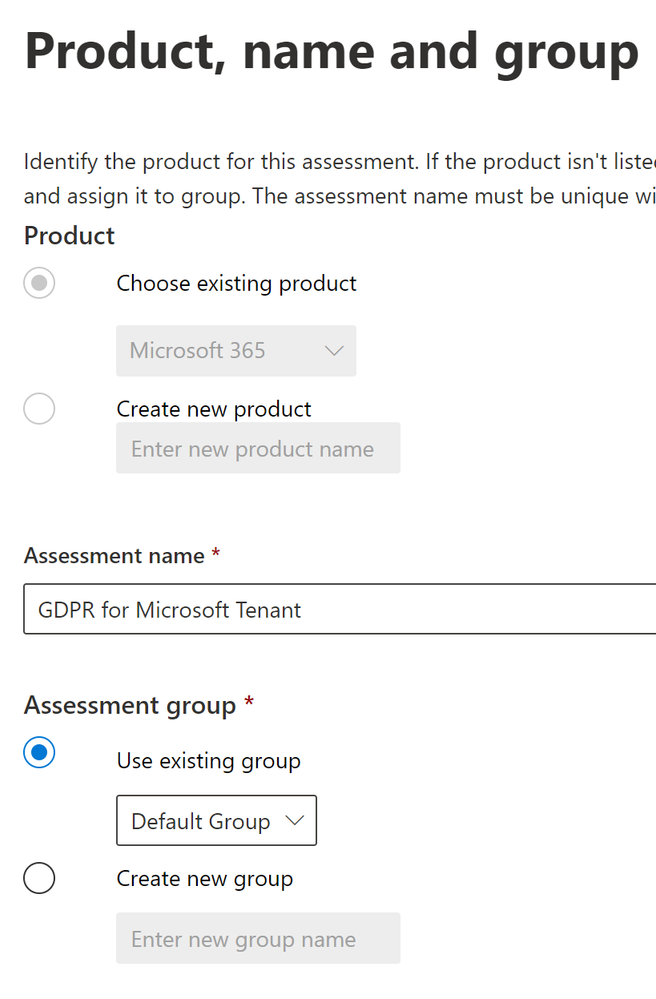
- When you are satisfied, click Next.
- Review your assessment information and make changes as needed. Then click Create Assessment and then Done.
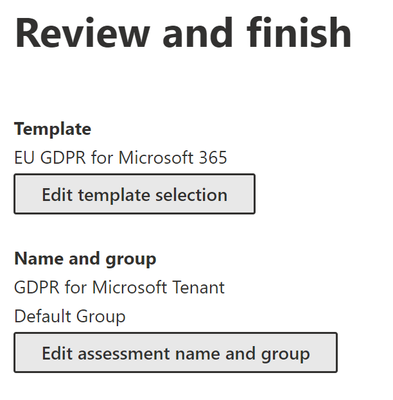
- You will be automatically taken to your new assessment. Proceed to the next Overview and Tabs section below.
Assessment – Overview (tab)
We will start with the Overview section of the assessment on the left-hand side.
- The Overview tab does exactly what you will expect.

- The Details section will show you the highest of high-level states about your assessment.
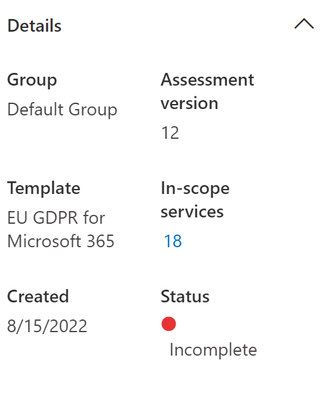
- The About section will give a high-level comment about your particular regulation or certification. The link provided will take you to the official website for that regulation or certification.

- On the right you will see your 4 tabs for the assessment. We will take each of these one at a time, from left to right, beginning with the Progress tab.

- Let us move to the Progress tab on the right. Proceed to the next section.
Assessment – Controls (tab)
This tab covers the controls and Control Families that are needed to meet your regulation/certification. Controls are the various requirements in your tenant that must be met to meet a part of an assessment. A Control Family is a grouping of Controls. This will be visible in the top section.
Top section:
In this example, there are 4 Controls Families. You can see by the color if something is done (colored) or not done (grey).
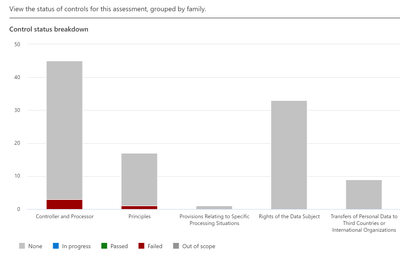
Bottom section:
In the bottom section, you will be able see the Control Family and under each, a Control.
- If you click on a family and then on a control, you will be taken to a specific Control. I will select Controller and Processor – Agreements.
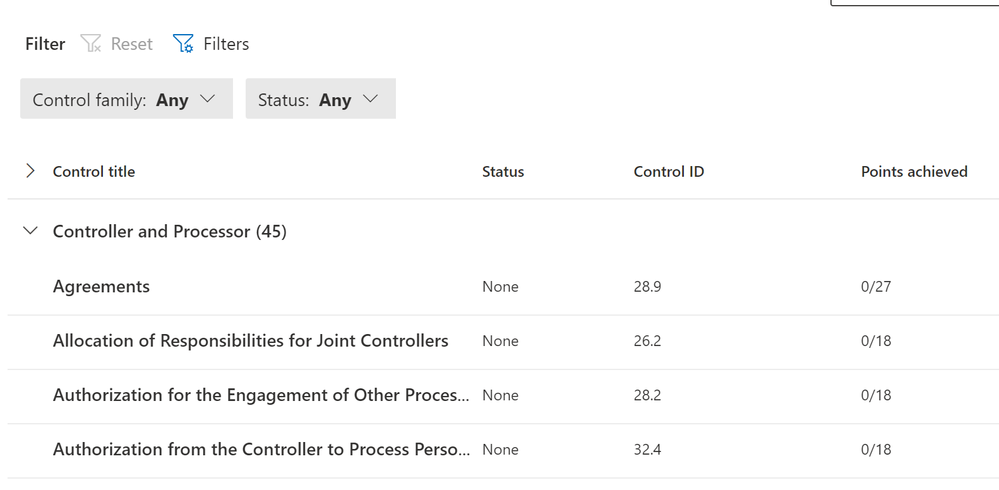
- This will take your Improvements actions (and Microsoft actions). Here you can select a specific improvement action to run to help meet your regulation/certification.
- Note – Because there are multiple paths to arrive at a specific Control and the Improvements, you can make, we will cover how to take an action on a Control in the Control flows section below. You can skip to that section now if you wish to see how to run an improvement action. Otherwise, we will take a half step back and look at the Improvement Actions (tab)
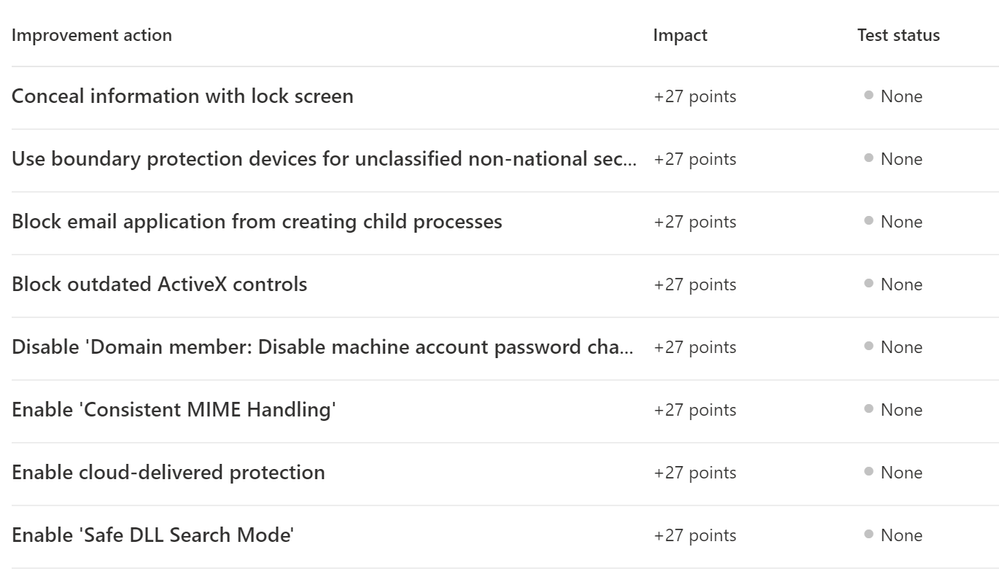
- Here you will see the top 10 actions you can do to improve your assessment score. We will cover this in the Your Improvement action section below. If you want more detail on these improvement actions, skip to that section.
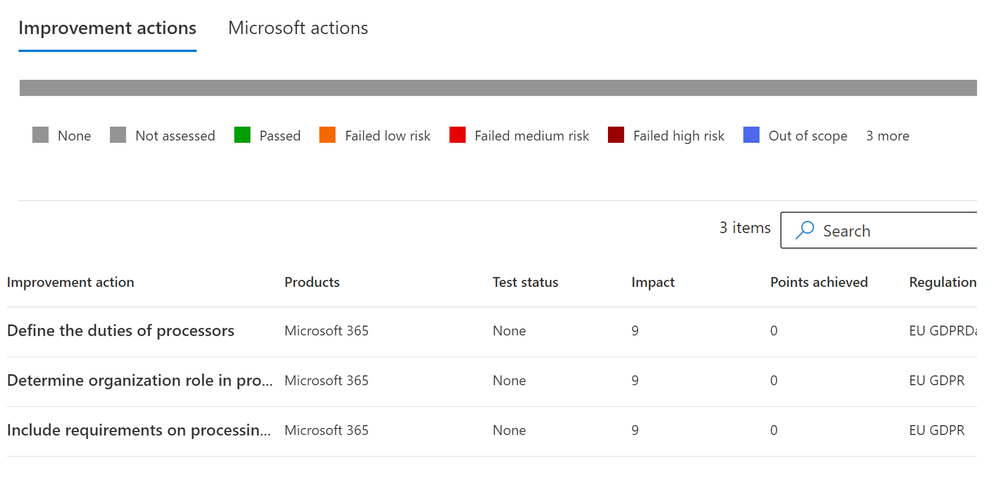
Assessment – Improvement Actions (tab)
This tab will show you ALL the improvements you can make to help meet your regulation/certification needs. Here is a sample screenshot.
If you click on any of these actions, it will take you to the Improvement Action.
- Note – Because there are multiple paths to arrive at a specific Control and the Improvements, you can make, we will cover how to take an action on a Control in the Control flows section below. You can skip to that section now if you wish to see how to run an improvement action. Otherwise, we will take a half step back and look at the Microsoft Actions (tab)
Assessment – Microsoft Actions (tab)
Listed here are all the items Microsoft will make sure are secured in your tenant.
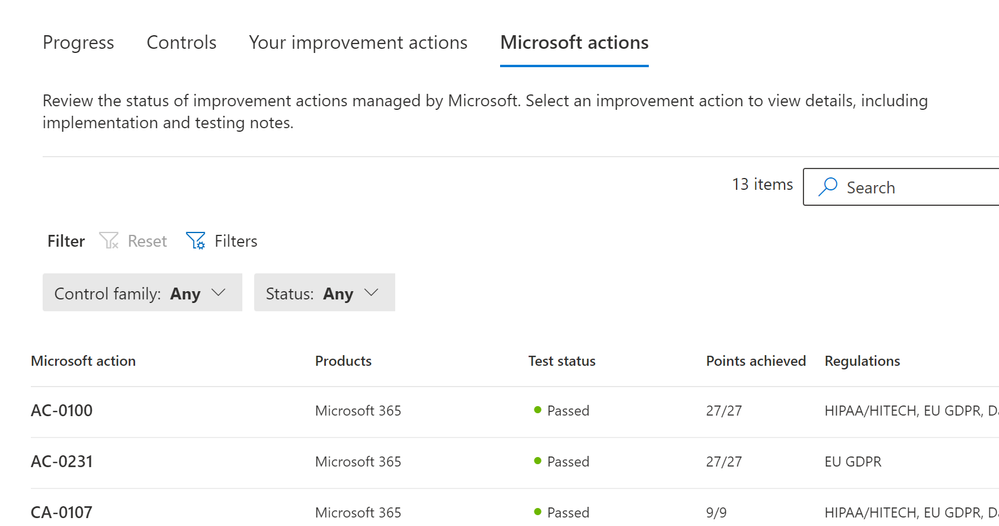
- Click on the first of these Microsoft actions. I’ve clicked on the action AC—0100.
- When you click on an action, it will take you to a pane similar to the one found in the Improvement Actions. So, I will not explain these steps here.
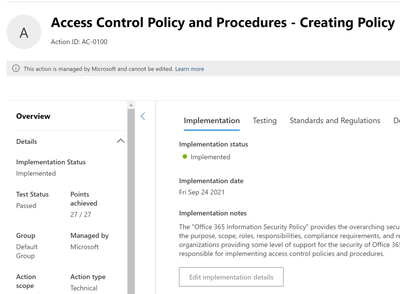
- There is nothing for you to do in this tab.
- You have now reached the end of this part of the blog. To know how to run improvements, please proceed to next part of this blog series Microsoft Purview – Paint By Numbers Series (Part 9c) – Compliance Manager – Improvement Actions.
Here is the link Microsoft Purview- Paint By Numbers Series (Part 9c) – Compliance Manager – Improvement Actions – Microsoft Tech Community
Appendix and Links
Microsoft Purview Compliance Manager – Microsoft Purview (compliance) | Microsoft Docs
Build and manage assessments in Microsoft Purview Compliance Manager – Microsoft Purview (compliance) | Microsoft Docs
Learn about assessment templates in Microsoft Purview Compliance Manager – Microsoft Purview (compliance) | Microsoft Docs
Build and manage assessments in Microsoft Purview Compliance Manager – Microsoft Purview (compliance) | Microsoft Docs
Working with improvement actions in Microsoft Purview Compliance Manager – Microsoft Purview (compliance) | Microsoft Docs
Microsoft Purview- Paint By Numbers Series (Part 9c) – Compliance Manager – Improvement Actions – Microsoft Tech Community
Note: This solution is a sample and may be used with Microsoft Compliance tools for dissemination of reference information only. This solution is not intended or made available for use as a replacement for professional and individualized technical advice from Microsoft or a Microsoft certified partner when it comes to the implementation of a compliance and/or advanced eDiscovery solution and no license or right is granted by Microsoft to use this solution for such purposes. This solution is not designed or intended to be a substitute for professional technical advice from Microsoft or a Microsoft certified partner when it comes to the design or implementation of a compliance and/or advanced eDiscovery solution and should not be used as such. Customer bears the sole risk and responsibility for any use. Microsoft does not warrant that the solution or any materials provided in connection therewith will be sufficient for any business purposes or meet the business requirements of any person or organization.
by Scott Muniz | Aug 23, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Mozilla has released security updates to address vulnerabilities in Firefox, Firefox ESR, and Thunderbird. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the Mozilla security advisories for Firefox 104, Firefox ESR 91.13, Firefox ESR 102.2 and Thunderbird 91.13, Thunderbird 102.2 and apply the necessary updates.
by Contributed | Aug 22, 2022 | Technology
This article is contributed. See the original author and article here.
We are excited to announce that you can now block suspicious entities when submitting emails, URLs, or attachments for Microsoft to review. In the Microsoft 365 Defender portal (https://security.microsoft.com), security operations team can now block the sender or domain, URL or attachment while submitting suspicious emails, URLs or attachments from the admin submission flyout panel. You’ll no longer need to switch to the Tenant allow/block list page to block a suspicious entity.

Let’s look at how it works!
Blocking email addresses or domains through email admin submission flyout
From the Emails tab under the submissions portal in Actions & submissions in the Microsoft 365 Defender portal, select Submit to Microsoft for analysis to report phishing, malware or spam email. You can choose to block the sender or domain and provide block expiry date and optional notes. Make sure that you have the required permissions before submitting to Microsoft.
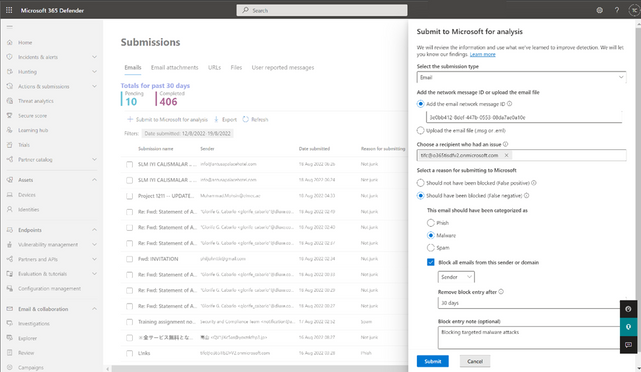
To learn more about blocking email addresses or domains in Tenant allow/block list, See Allow or block emails using the Tenant Allow/Block List.
Blocking URL through URL admin submission flyout
From the URLs tab under the submissions portal in Actions & submissions in the Microsoft 365 Defender portal, select Submit to Microsoft for analysis to report phishing or malware URL. You can choose to block the URL and provide block expiry date and optional notes. Make sure that you have the required permissions before submitting to Microsoft.
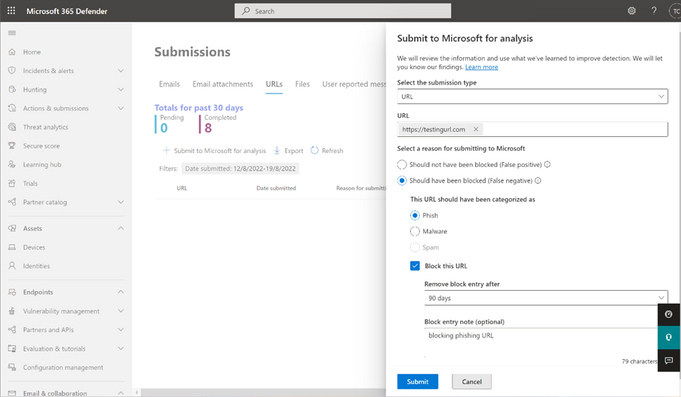
To learn more about blocking urls in Tenant allow/block list, see Allow or block URLs using the Tenant Allow/Block List.
Blocking email attachment through email attachment admin submission flyout
From the Email attachments tab, under the submissions portal in Actions & submissions in the Microsoft 365 Defender portal, select Submit to Microsoft for analysis to report phishing or malware email attachment. You can choose to block the email attachment and provide block expiry date and optional notes. Make sure that you have the required permissions before submitting to Microsoft.
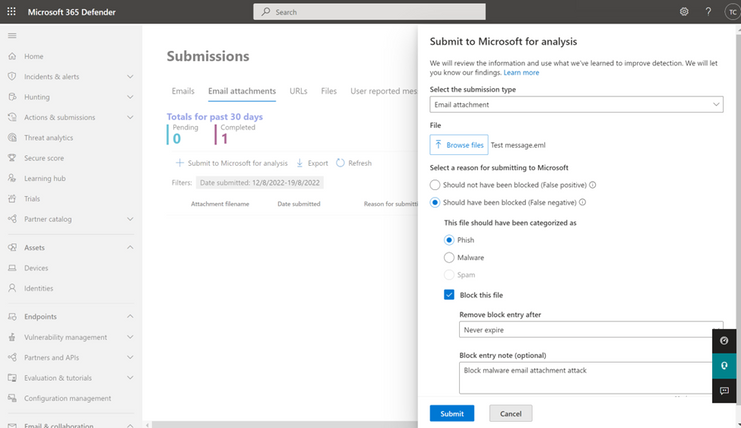
To learn more about blocking email attachment in Tenant allow/block list, see Allow or block files using the Tenant Allow/Block List.
Viewing blocked entities from the admin submission flyout
All of the blocked entities created from the admin submission panel for URL, email attachment and emails will show up in Tenant allow/block list under the URL, file and Domains & addresses tab, respectively.
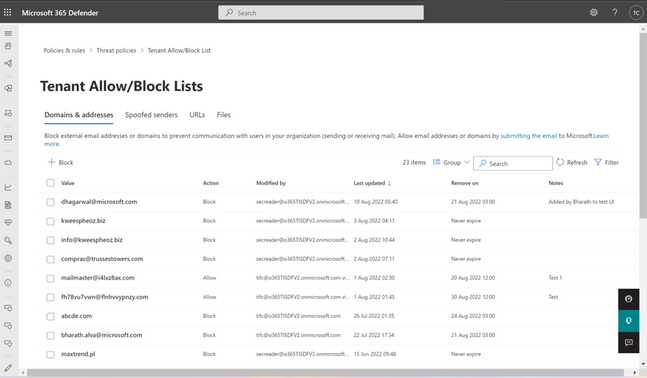
To learn more about Tenant allow/block list, see View entries in the Tenant Allow/Block List.
All other aspects of the submission experience, such as submitting a sample for analysis and viewing the results, remain as it is.
Let us know what you think!
The experience will start rolling out by the end of August. You can expect to see these changes over the next few weeks. The new submissions experience will be available to customers with Exchange Online Protection, Defender for Office 365 Plan 1, Defender for Office 365 Plan 2, including those with Office 365 E5, Microsoft 365 E5, or Microsoft 365 E5 Security licenses.
We’re excited for you to try out these new capabilities. Let us know what you think using the Defender for Office 365 forum.



Recent Comments