by Contributed | Mar 2, 2022 | Technology
This article is contributed. See the original author and article here.
Watchlists are a critical component to enhance security operations and provide data correlation. Up till now, watchlist files have been limited to 3.8 MB per upload. We are excited to announce that Watchlists now support up to 500 MB file size per upload!
There are many scenarios where you will need to reference and look up a larger dataset in your detection rules or investigation. Here are some sample use cases you can use the large watchlists for.
- Map database of IPv4 address networks with their respective geographical location from known sources such as MaxMind or IP2Location.
- Leverage the CVE vulnerability database to help enrich incidents and alerts that may be related to a known exploit.
- Enrich alerts and incidents with custom datasets that are larger than 3.8MB in size.
How to create a large watchlist
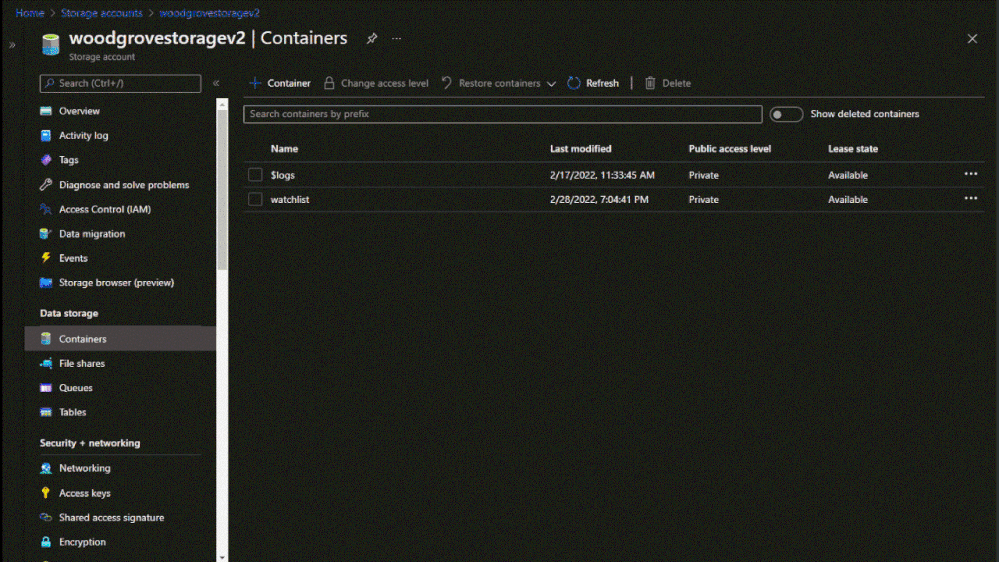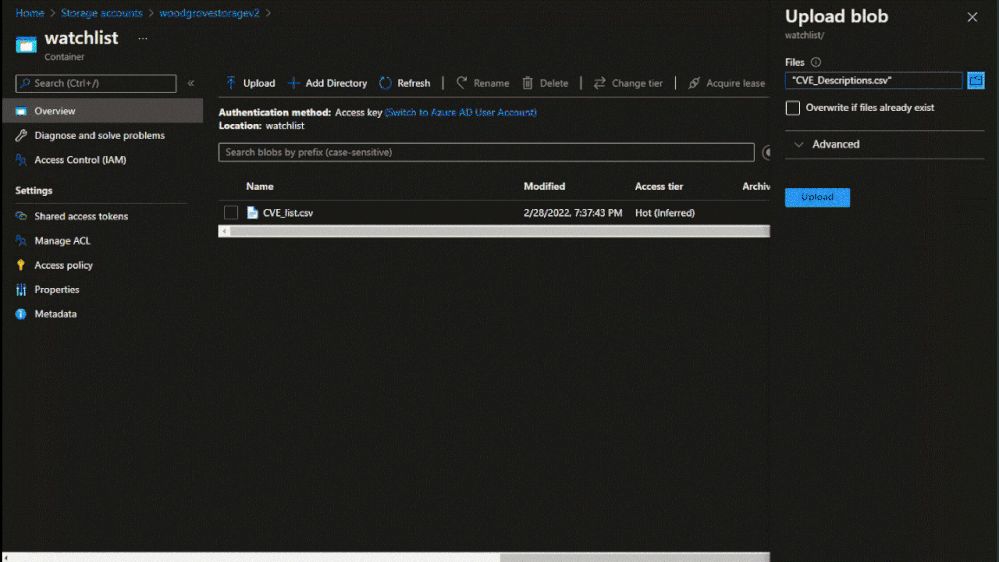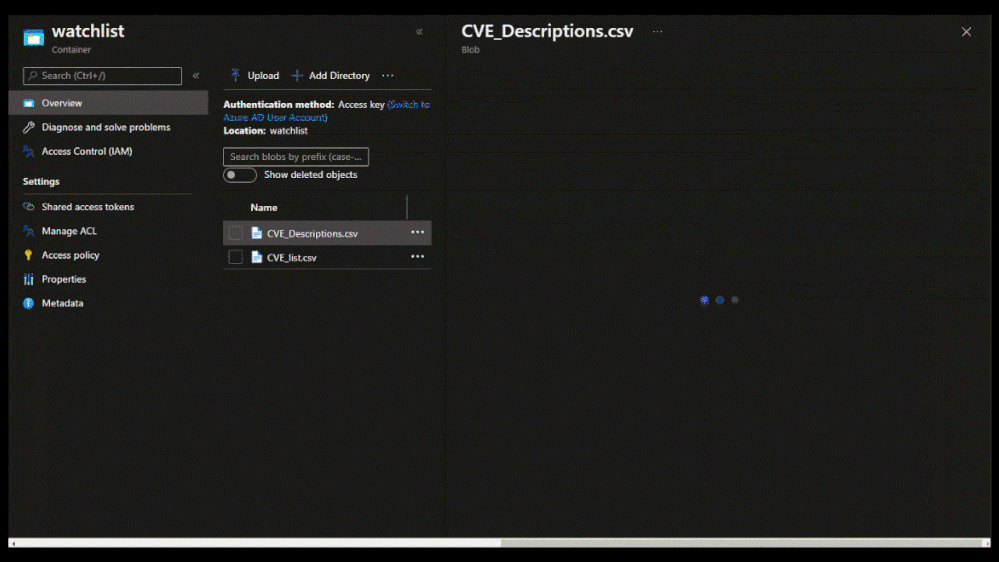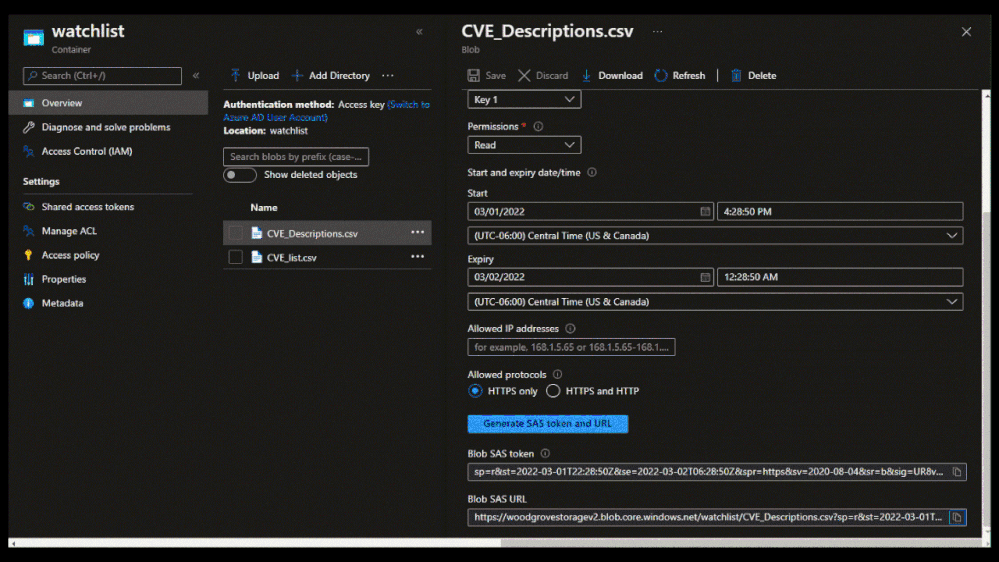
To create a large watchlist, you will need to upload a watchlist file in an Azure Storage account. Then create a shared access signature (SAS) URL for Microsoft Sentinel to securely retrieve the watchlist data. Finally upload the watchlist to your workspace in Microsoft Sentinel.
Check out our step-by-step instructions to create a large watchlist.
 Upload the watchlist file in an Azure Storage account and generate a secure SAS URL
Upload the watchlist file in an Azure Storage account and generate a secure SAS URL
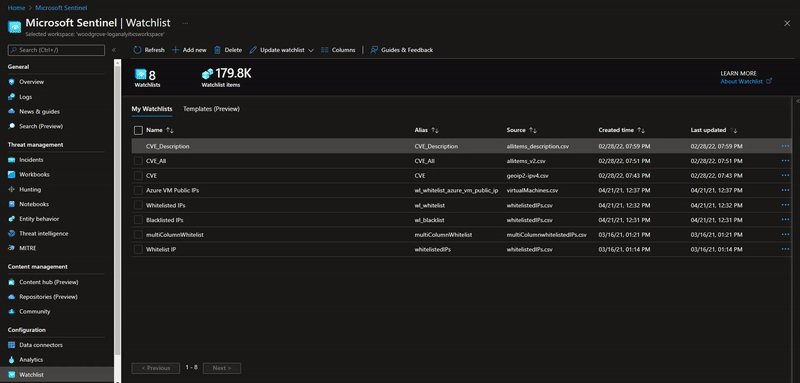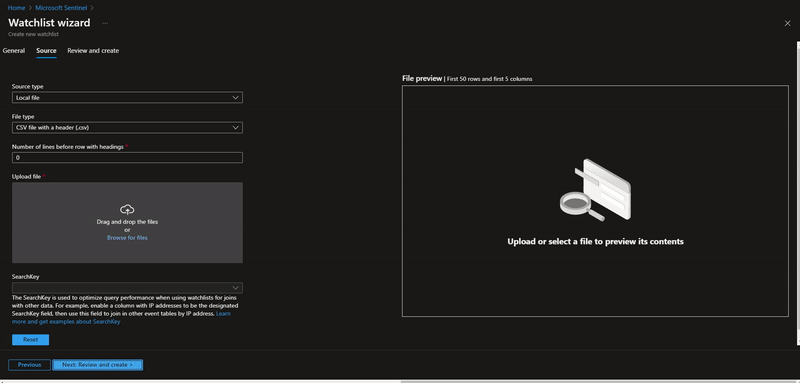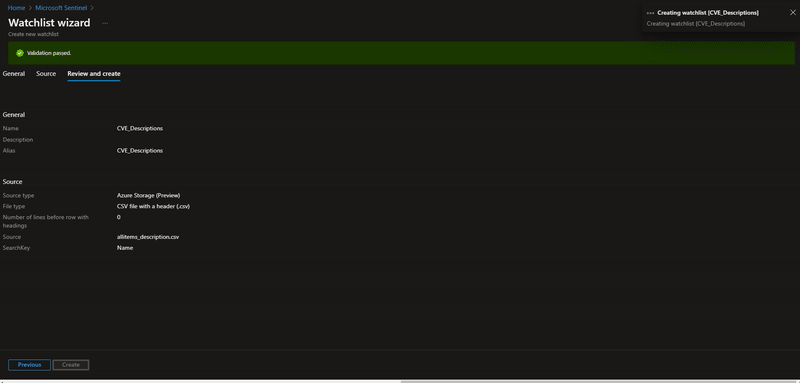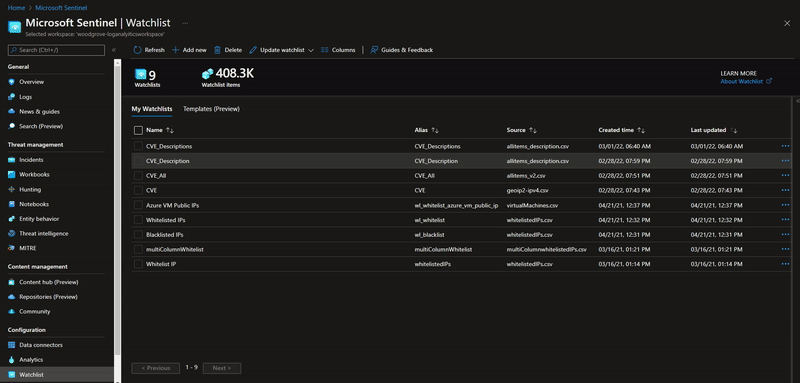 Upload a large watchlist in Microsoft Sentinel portal
Upload a large watchlist in Microsoft Sentinel portal
Considerations:
- Creating a watchlist from a local file is still limited to 3.8 MB per upload. The increased limit applies only to watchlist files stored in Azure Storage.
- Microsoft Sentinel will require an Azure Storage Blob SAS URL to access and download the file for processing and ingestion into the watchlist table. The SAS URL must have at least 6 hours away from its expiry time.
- An entry in the CSV file must not exceed 10,240 characters per line.
Further reading resources:
Try out this new watchlist capability and let us know your feedback!

by Contributed | Mar 1, 2022 | Business, Microsoft 365, Microsoft Teams, Technology, Windows 365
This article is contributed. See the original author and article here.
Over the past two years, businesses of all industries and sizes have had to adapt to new ways of working, a challenging operating environment, and ever-changing customer expectations. With all this change, it’s hard to overstate the impact of having secure and reliable productivity and collaboration tools.
The post Unleash the power of your small business with Microsoft 365 appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Feb 28, 2022 | Technology
This article is contributed. See the original author and article here.
We are happy to announce self-service trials for Microsoft Visio. As of today, you can sign up for free 30-day trials of Visio Plan 1 or Visio Plan 2 on existing Microsoft 365 tenants managed by your organization using your business login. Then, test out the full functionality of the Visio web and desktop apps before directly purchasing subscriptions.
With self-service trials, you can sign up for trial licenses for up to five users and then, with a limited admin role, assign the trial licenses to your colleagues in the Microsoft 365 admin center. If you run in to any issues signing up for your trial licenses, please contact your IT department.
These new self-service trial capabilities are available worldwide except for India. They are not available for Education or Government customers.
Please note: You will be asked to provide credit card details at signup. At the end of your 30-day trial, you will be charged the applicable subscription fee to continue using Visio. Cancel at any time to stop future charges.
Determine which Visio trial is right for you
With the Visio Plan 1 trial, you and your team members will have full access to the Visio web app—including dozens of diagram templates and hundreds of shapes—and 2 GB of OneDrive for Business cloud storage. The Visio Plan 2 trial includes all the features in the Visio Plan 1 trial, plus additional templates, shapes, and advanced features in the Visio desktop app. During both trials, you’ll be able to create, edit, share, and collaborate on diagrams and flowcharts using Visio or Microsoft Teams (requires a Microsoft 365 subscription to use Teams).
How to sign up
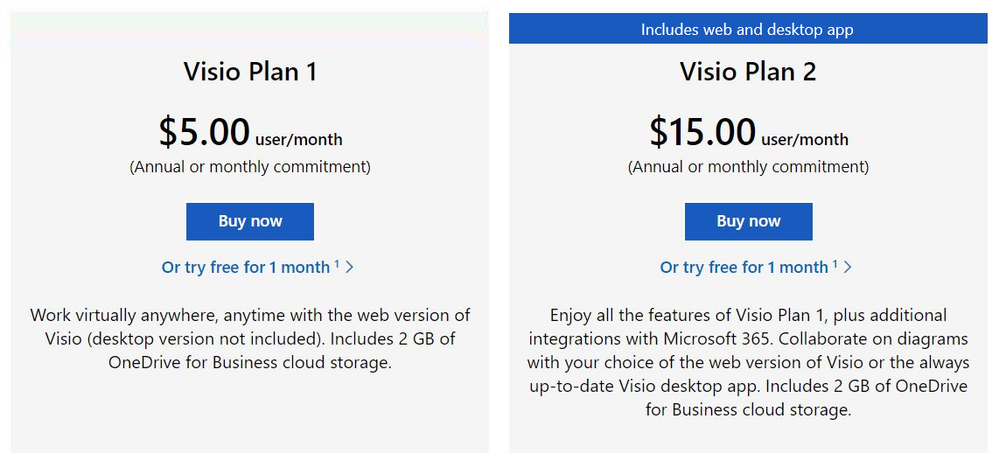
The 30-day trials of Visio Plan 1 and Visio Plan 2 are available for self-service signup by individuals and departments from the Visio plans and pricing comparison page. Select the corresponding trial link below the Buy Now button and complete the necessary steps.
 Screenshot of Visio Plan 1 and Visio Plan 2: Click on “Or try free for 1 month” to complete the steps to start your trial
Screenshot of Visio Plan 1 and Visio Plan 2: Click on “Or try free for 1 month” to complete the steps to start your trial
Manage trial licenses as a Global or Billing admin
The self-service trial capabilities do not compromise IT oversight or control. If you are an admin, you can use the same self-service purchase controls to disable self-service trials while making use of subscription management capabilities to oversee and manage trial licenses on the licensing page in the Microsoft 365 admin center.
If you’ve disabled the self-service purchase functionality for Visio in the past, self-service trials signup for individuals or departments will automatically allow users to request licenses directly from you. Learn more about managing self-service licenses acquired by individuals or departments in your organization.
Give us feedback about your trial experience! Please tell us what you think in the comments below or send feedback via the Visio Feedback portal.
Continue the conversation by joining us in the Microsoft 365 Tech Community! Whether you have product questions or just want to stay informed with the latest updates on new releases, tools, and blogs, Microsoft 365 Tech Community is your go-to resource to stay connected!
by Contributed | Feb 27, 2022 | Technology
This article is contributed. See the original author and article here.
Introduction
Azure Form Recognizer is an amazing Azure AI Service to extract and analyze form fields documents. One benefit of using Form Recognizer is the ability to create your own custom model based on documents specific to your business needs.
To create custom models, Azure provides Form Recognizer Studio, a web application that makes creation and training of custom model simple without the needs of an AI expert.
One common challenge most customers have when dealing with more than a handful of models is to apply the same DevOps processes, they are familiar with when promoting code changes from one environment to another to their AI models.
This article demonstrates the use of Form Recognizer’s REST APIs to implement a CI/CD pipeline for model management.
The complete implementation is available on Github.
Why DevOps matters
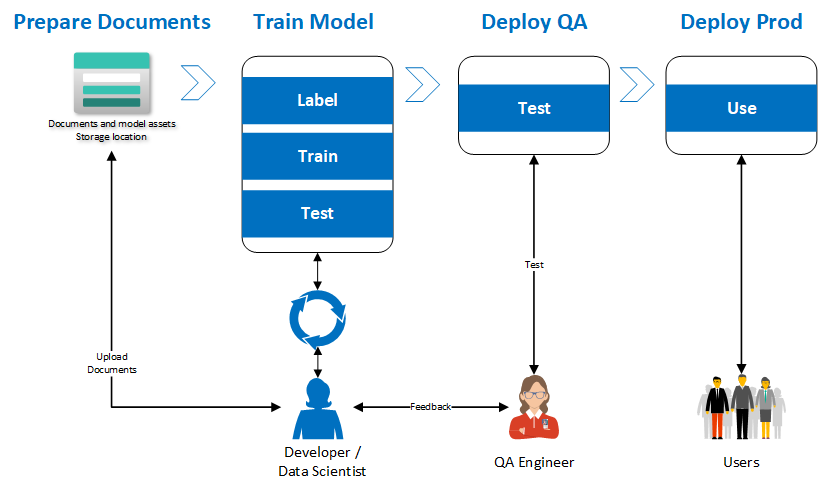
When creating a custom model based on documents that map your business needs, your programmers and data scientists will go through multiple iterations of training, resulting in multiple different models in the development environment. Once they have a model that works well for the specific scenario, this model will then need to be promoted to other environments.
While it is possible to copy the training dataset and train a model in all of the other environments, that process is cumbersome and can result in missed labels resulting in lower accuracy models. A more effective approach is to treat the model like a source code artifact and use a DevOps pipeline to orchestrate the movement of the model across the different environments ensuring traceability and compliance. The diagram below explains the proposed implementation flow to achieve this result.

Our implementation
For our use case, let’s assume we have three environments: each is in a respective resource group. This approach would work even if the resource groups are in three different subscriptions.
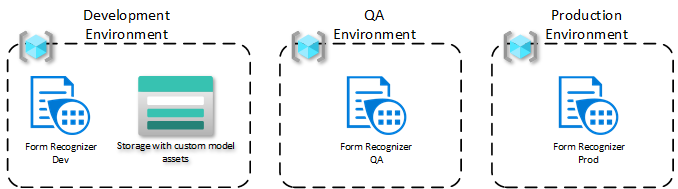
The model is trained in the development environment, where , data scientists and/or developers will use the Form Recognizer Studio to label the documents in a storage account. The following steps describe that process in greater detail.
Start by moving the training dataset to a specific container in Azure Blob Storage.
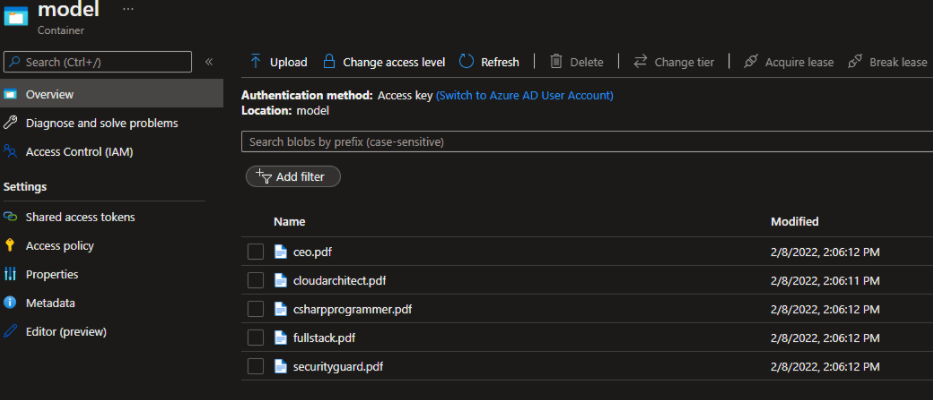
In the Form Recognizer Studio, start by creating a custom project and connecting the Studio to work with the dataset, you just created.
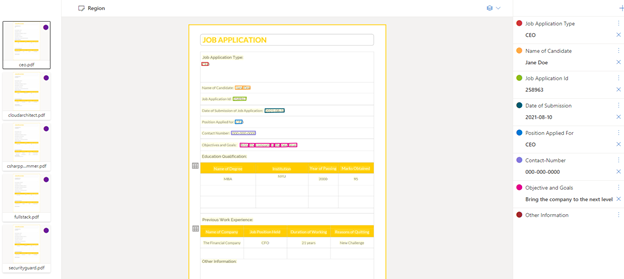
When you train your model, be sure to save the model ID you provided or find the model from the list of models within the project. This model ID will be needed when it’s time to migrate the model to other environments.
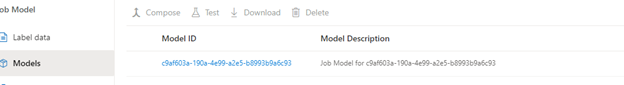
Form Recognizer provides a model copy operation that starts with generating a model copy authorization for the target resource, in this case the QA environment. This copy automation is provided to the Form Recognizer development resource to then execute the copy action.
To orchestrate this set of actions, a simple GitHub action was created. The API can be integrated into your CI/CD pipeline using REST or any of the language specific SDKs. In this case, we created an Azure Function that uses the .NET SDK for Form Recognizer. This Azure Function provides multiple endpoints that are leveraged in the GitHub Action.

The following diagram describes the GitHub Actions Orchestration.
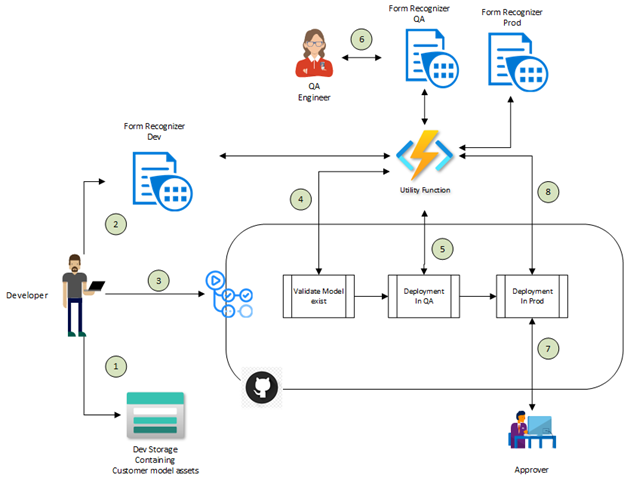
- The developer moves all the documents needed to train the custom model into Azure Storage account.
- The developer uses the Form Recognizer Studio to train the custom model in the development environment. Once the model is trained and the developer is satisfied with the model quality, the model ID is saved for use with the GitHub action.
- The developer initiates the GitHub action by providing the model ID from the previous step as an input parameter.
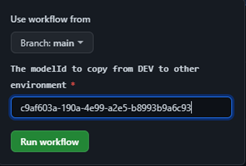
- The first step is to validate that the model ID exists in the DEV environment.
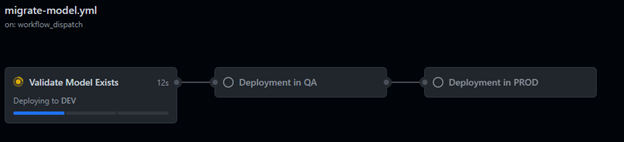
- If the model exists in the DEV environment, it will be copied to the QA environment
- Now, a QA engineer can validate the model produces the expected results.
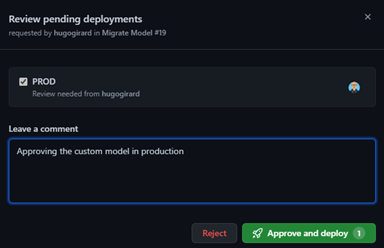
- Once the QA tests are successful, an approver needs to approve the next job to promote the model to the production environment.
- The model is now copied to the production environment and is available for use.

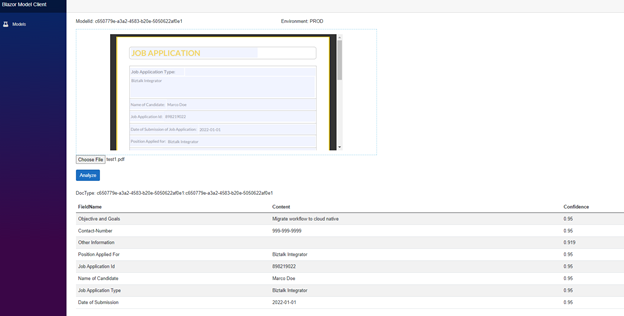
Once the model is in production, you can use it within your applications. The following example demonstrates how the model is being used to analyze documents.
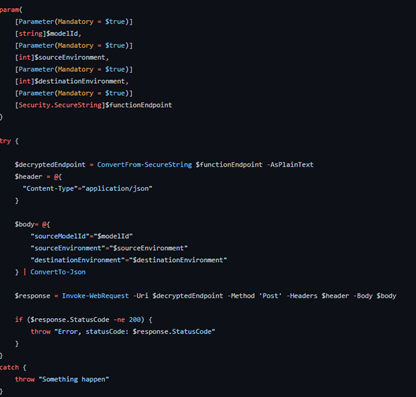
Here are the GitHub Action used in this sample, it consists of 3 jobs that invoke the Azure Function using a PowerShell script. As stated earlier, the Azure Function implementation is optional, this could be accomplished via HTTP requests directly to the Form Recognizer resources from your pipelines.

Here is the simple PowerShell script.
Conclusion
In this blog post, we explain the importance of implementing a DevOps practice around your custom models in Azure Form Recognizer. We provide an implementation and illustrate how easy it is to implement with the REST API.

by Contributed | Feb 25, 2022 | Technology
This article is contributed. See the original author and article here.

How does using Microsoft Teams everyday make you feel? Does it improve your work? Impede it? Whether you are using Teams simply for 1:1 chat or for all your various collaboration throughout the day, we want to hear from you, the good, bad, and ugly.
Join us for an open-ended one hour session, where Federal Customer Success Managers, Abby and Kyren, will create a space to gain a better understanding of where the pain points are in our technology, as well as uncover opportunities to connect Federal organizations to the right resources. There will be no recording. Consider this your first relationship management session for Teams! You can register at : aka.ms/ModernWork4Gov
Upload the watchlist file in an Azure Storage account and generate a secure SAS URL
Upload a large watchlist in Microsoft Sentinel portal



Recent Comments