by Contributed | Oct 4, 2022 | Technology
This article is contributed. See the original author and article here.
App Service Hybrid connection offers a quick and uncomplicated way to reach your on-premises services in scenarios where there aren’t other networking solutions like VPN or ExpressRoute available. Normally, you don’t even need to open any firewall ports in your on-premises environments because it only requires outbound HTTP connection over port 443 towards Azure to work. Behind the scenes, it is a TCP relay proxy over websockets. It only works to reach services that run on TCP protocols and not UDP.
Therefore, it might be a good fit if you are planning to migrate your application(s) to Azure App Service but this app has dependencies to on-premises databases or APIs and your networking team is not yet ready to set up a VPN/ExpressRoute connection between these environments. The migration work can be unblocked using Hybrid connections towards these external dependencies with no code changes within your app.
However, what to expect in terms of performance? Apart from the pure networking latency of having an App Service connecting back to on-premises service… will the Hybrid connection itself introduce extra latency on top of network? What about the different scenarios:
- Reaching on-premises HTTP APIs;
- Reaching on-premises databases;
- Downloading on-premises large files over HTTP
In this article we will run benchmarks on all given scenarios above and compare them with and without Hybrid connection. It is not the goal here how to configure such a connection, because that tutorial is very well described here.
The test setup
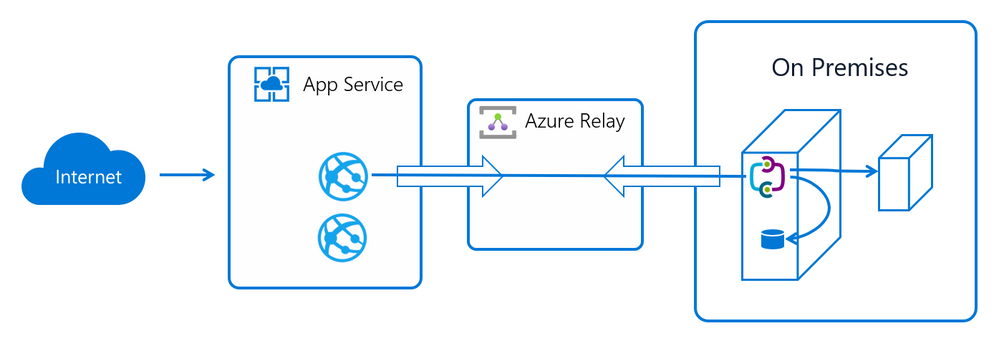
An App Service Hybrid connection relies on a service called Azure Relay to work (and Azure Relay is based on Azure Service Bus platform). This is how the architecture looks like:

Now, let me explain how the setup in this test is done when comparing to the diagram above:
- App Service: a small PremiumV2 .NET Core 6 app running in Brazil South;
- Azure Relay: if you don’t have an already created Azure Relay created, the App Service Hybrid connection will ask you to do so. Here, I created one in Brazil South region;
- On Premises: to simulate an on-premises environment, here I have a physical computer with a fast and modern hardware (Ryzen 5 5600H, 16GB ram, 512gb SSD) connected to a 600mbps stable fiber connection. This system has an average 12ms (milliseconds) latency to Azure and vice-versa. It also has one SQL Express 2019 database, a .NET 6 API to simulate on-premises services for these tests and the HCM (Hybrid Connection Manager) that is required for this setup.
Now, we want to compare the Hybrid connection overhead over the raw network connection. So, for each test that will follow in this article, we will configure the App Service to hit the services via Hybrid connection endpoints and then run the same test but going directly to the public IP of the “on-premises” server, skipping the relay completely.
Here’s the configuration in the Portal:
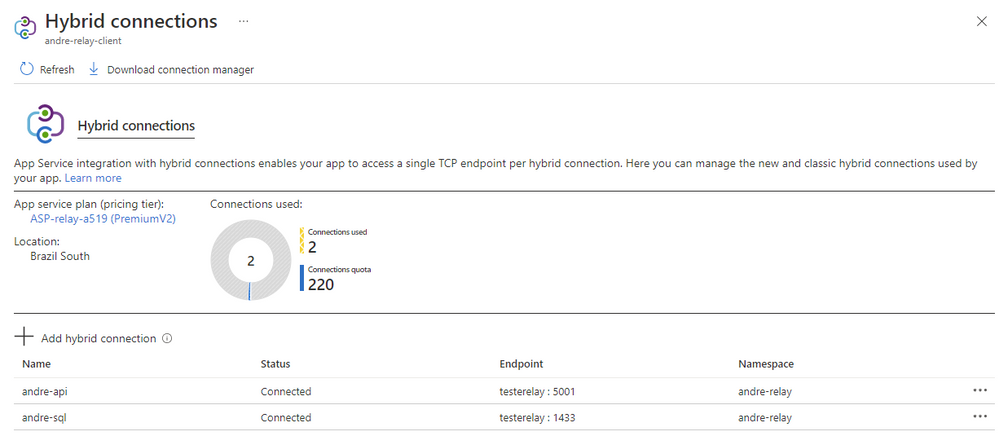
Scenario 1: HTTP requests
Let’s assume you got on-premises HTTP services to reach from an App Service via Hybrid connection. In the configuration picture above, that endpoint name is “andre-api” which points to a on-premises DNS name of “testerelay” on port 5001. That is the .NET API running in the on-premises computer. This API has a REST endpoint that returns random strings of around ~8kb in size.
From the App Service side, it runs another .NET API that calls the previous endpoint in three different ways:
- Single request: App Service calls the on-premises API once
- Sequentially: App Service calls the on-premises API 50 times in a row. When the previous request finishes, the next goes ahead and so on… until we reach 50 requests;
- Parallel: App Service calls the on-premises API 50 times at the same time. This is accomplished by making use of .NET tasks
The intention here is to verify how well the relay handles a typical real-world scenario where you get many parallel requests at a given time. All requests here are using HTTP2 protocol.
Check out the results table:
|
Average response time per HTTP request
|
Difference
|
Direct
|
Hybrid connection
|
Single request
|
13ms
|
24ms
|
+84%
|
Sequential (50)
|
13ms
|
34ms
|
+161%
|
Parallel (50)
|
50ms
|
60ms
|
+20%
|
Important note
Having the App Service .NET API calls the relay forcing the HttpClient to use HTTP2 by default made a huge difference for the positive side in the tests results. HTTP 1.1 was much worse especially in the parallel requests test;
Conclusion for HTTP tests
If we look at the difference numbers in % it seems to be a huge overhead added by the Hybrid Connection, but looking at absolute numbers, it is not. In the more realistic test of this setup – the Parallel HTTP simulation – we get only 10ms added compared to a direct connection, which is negligible for most applications. Another point to keep in mind here is that we are comparing the Hybrid connection to a direct connection back to on-premises. In reality we would have a VPN or other appliance which might add some extra delay there too.
Scenario 2: database connections
Another very common use case is the need to fetch data from a on-premises database that could not be migrated to Azure at the same time as the application. Here we will make the App Service .NET API call the on-premises SQL Server using the relay connection and then directly. The query returns from the database around ~8kb of data per call. Like the HTTP tests, there will be three different scenarios:
- Single request: AppService queries the database once
- Sequentially: App Service queries the database 50 times in a row. When the previous query finishes, the next goes ahead and so on… until we reach 50 queries;
- Parallel: App Service queries the on-premises database 50 times at the same time. This is accomplished by making use of .NET tasks
|
Average response time per SQL query
|
Difference
|
Direct
|
Hybrid connection
|
Single query
|
13ms
|
13ms
|
0%
|
Sequential (50)
|
13ms
|
27ms
|
+107%
|
Parallel (50)
|
13ms
|
30ms
|
+130%
|
Conclusion for database tests
Compared to the HTTP tests, the database queries have less overhead because of the TCP nature of the connections. While the direct connection had no extra overhead even when querying 50 in parallel, the Hybrid counterpart added some but not significantly – again, looking from absolute numbers perspective and not purely in percentage.
Scenario 3: large file downloads
Now let’s benchmark something less usual: what about using the Hybrid connection to stream a 1GB file (a Linux ISO file) from on-premises REST API via HTTP? Here I’m expecting more overhead because the underlying websockets protocol that Azure Relay is using is not really meant for these cases. But anyway, here are the results:
REST API HTTP download speed
|
Difference
|
Direct
|
Hybrid connection
|
27 MB/s
|
20 MB/s
|
35%
|
Conclusion for file download test
I was expecting a much worse result, but the Hybrid connection surprised for the better here. I wouldn’t recommend this connection for streaming large files but this test shows that this is possible if it is really needed.
Overall conclusion
These benchmarks did not cover all the possibilities for a Hybrid connection but certainly give us an idea what to expect. Generally speaking, it is a solid alternative and I would recommend for scenarios where a VPN or ExpressRoute connection is not possible. The biggest advantage for sure is ease of use – setting up your own environment to run similar tests will take just a couple of hours top.
If you wish that I run additional benchmarks and scenarios, please let me know in the comments!
by Contributed | Oct 3, 2022 | Technology
This article is contributed. See the original author and article here.
Attempting to impersonate someone is an activity as old as humanity, and has been used to great comedic effect by comedians and jesters throughout the ages.
Sadly, the crime of identity theft (in which a criminal uses someone’s identity details for fraudulent purposes) is very much not a joke. Not only because it can destroy someone’s finances and credit, but can even lead to false arrests and other life-altering consequences for the person whose identity is being abused.
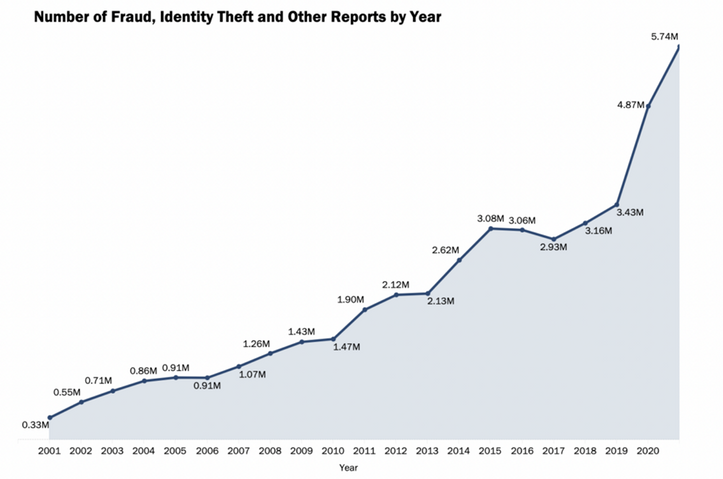
Even less funny than that, is that the number of these crimes is currently at an all-time high. According to identitytheft.org1 the number of identity theft incidents are up 70% compared to 2020, with the yearly number of reported identity theft incidents clocking in at 5.7 million in 2021 for the US alone.
 Figure 1 – Source: FTC annual data book 2021 (ftc.gov/data)
Figure 1 – Source: FTC annual data book 2021 (ftc.gov/data)
Figure 1 – Source: FTC annual data book 2021 (ftc.gov/data)
And along with the number of incidents, the median cost of these identity theft incidents is also on the rise, reaching an estimated $500 USD per incident based on the 2021 data2. This is in direct correlation with the ever-increasing number of devices and services people use in their daily lives, and the strong shift to conducting life online (from work, shopping, and entertainment), which have all served to increase exposure to this type of crime.
All of this means that, on average, someone’s identity is stolen every 22 seconds in the US, and 33% of Americans will become a victim of identity theft at some point in their lives. In fact, 1 in 4 have been victimized by identity theft before they turn 183. In all, this is most certainly not a laughing matter, especially when you consider that this type of crime costs the US economy 5.8 billion USD per year4.
Hopefully, after hearing the above numbers, you’re wondering what can be done to stop this. Or, at the very least, what you can do to prevent yourself and your family from becoming identity theft victims.
The answer to that question is both simple and very hard; It starts with implementing all the common security advice you’ve probably heard thousands of times before: Use strong passwords, do not reuse credentials, enable multi-factor authentication, do not post personal data on social media, monitor your credit cards, bank accounts, and credit history for anything out of the ordinary, etc.
But the problem with this is that securing your identity is not just solely your responsibility. What makes it hard is that every company, government body, institution, etc. that holds your information is also participating in this game of staying ahead of the identity thieves. And, when we remember that data loss incidents by those entities have been on a steady rise for years with no signs of stopping, it’s an almost statistical certainty that someone, somewhere, will expose your data at some point.
As a result, all too often people that follow the commonly espoused advice about account and identity security to the letter still become a victim of identity theft, through no fault of their own.
Introducing identity theft monitoring
Which brings us to the core topic of this article; Microsoft is excited to announce that identity theft monitoring is available today to Microsoft 365 subscribers (for both Personal and Family subscription plans) in the United States.
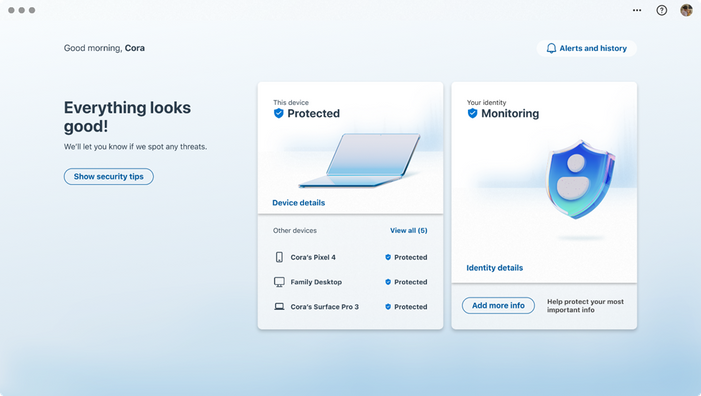 Figure 2 – Microsoft Defender with identity theft monitoring enabled
Figure 2 – Microsoft Defender with identity theft monitoring enabled
This solution addresses one of the biggest challenges in preventing identity theft: visibility. We’ve partnered with Experian® to leverage their powerful identity monitoring technology to detect, track, and alert you whenever we find any identifying information on the internet, the dark web, and less common sources like file sharing, chat rooms, and many other places.
By showing exactly what details are compromised and/or publicly available, Microsoft empowers you to take control of your personal identity security and make informed decisions. Once you know what’s out there, you can take action by resetting passwords for compromised services, enabling multi-factor authentication for services that support it, placing a credit freeze to avoid malicious actors affecting your credit, contacting your bank or card provider to report potential fraud on your account, etc.
Identity theft monitoring can currently track and report up to 64 different types of identity details per breach, from usernames and passwords to credit card numbers and even Social Security Numbers. And it does so intelligently; whenever a match is found on any monitored information, it will also alert you to any of your other personal information that was found in that same breach.
For example, when identity theft monitoring is tracking your email address, it will report all associated data it finds in a breach where your email was found. So, if you had a credit card on file with the breached company or service, it will not just report that it found your email, but also the credit card that was registered on your account there. Even if you never added your credit card number to your monitored identity details!
And, if the cause of the breach is known, identity theft monitoring will even tell you what happened to cause your data to be lost.
But knowing your identity has been compromised is only half the battle. While most people we surveyed were perfectly familiar with how to reset a password, many indicated that they wouldn’t know where to start if more sensitive information like their Social Security Number or driver’s license got exposed. Furthermore, many shared their struggles with looking up instructions online due to conflicting information and insufficient clarification of nuances like the difference between placing a credit freeze and a credit lock.
Identity theft monitoring helps answer these questions with contextual recommendations for each individual breach, as well as in-depth guides on how to perform more complex tasks. And, because we want to empower you to make informed decisions about your identity security, it will also inform you of the risks associated with each identity type. This way you can take the action that works best for your situation and risk tolerance.
That’s all well and good, but what if you need further help? Or if someone is actively trying to take over your identity, right now? For those cases Defender includes access to a 24/7 support team of restoration specialists that can guide you through the appropriate next steps for any situation regarding your identity and can even take action for you if time is of the essence.
This means, regardless of the situation, you are never left wondering what the appropriate next steps to resolving your identity breach are or having to fend for yourself in trying to get everything sorted.
This extends to the damages caused by identity theft too. Identity theft monitoring subscribers are insured for the costs associated with restoring their identity (document fees, legal fees, etc.) up to $1M USD and stolen funds caused by the identity theft up to $100k USD5.
So even if the worst should happen, Defender users who have identity theft monitoring enabled can rest (a little bit) easier, knowing that they have access to insurance that will help them in recovering their identities and the associated fallout.
And, as mentioned in the beginning, identity theft monitoring extends to family members in your Microsoft 365 family. These features and benefits can be set up and managed by the family organizer for all members of the family6. Once set up, family organizers will then receive alerts for all managed family members7 through the Defender app on any device they’re signed in on, as well as via email. This helps the organizer stay on top of not just their own identity security, but their families’ as well.
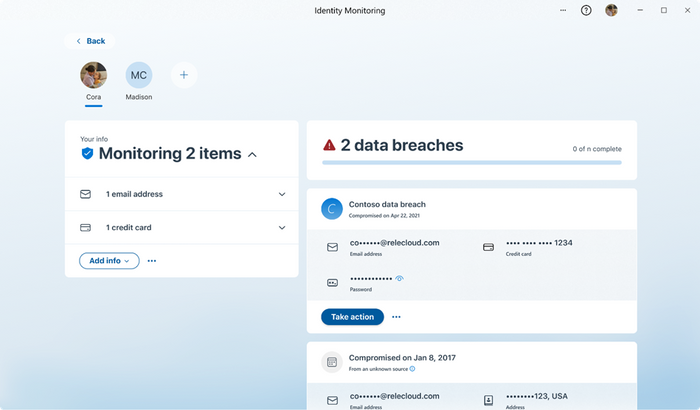 Figure 3 – Managing breaches for multiple family members
Figure 3 – Managing breaches for multiple family members
And of course, all of that can be easily managed from the central dashboard provided by the Defender app.
Getting started
To get started with identity theft monitoring today, visit https://mydefender.microsoft.com, sign-in with the personal Microsoft account (@gmail, @outlook, etc.) linked to your Microsoft 365 subscription, find the identity theft monitoring card on the dashboard, and select “Get started.” You can also download the app from the Microsoft, Google, and Apple app stores or download the MacOS app here (if you haven’t already)!
For more details and answers to frequently asked questions, visit: Getting started with identity theft monitoring in Microsoft Defender
References
1,2,4. 2022 Identity Theft Facts and Statistics – https://identitytheft.org/statistics/
3. Experian® Identity theft statistics https://www.experian.com/blogs/ask-experian/identity-theft-statistics/
5. The identity theft insurance is underwritten and administered by American Bankers Insurance Company of Florida, an Assurant company. Please refer to the actual policies for terms, conditions, and exclusions of coverage. Coverage may not be available in all jurisdictions. Review the Summary of Benefits.
6. All family members need an active Microsoft 365 subscription, and any user over the age of 13 need to explicitly consent to being monitored and managed by the family organizer.
7. Requires alert sharing to be enabled. Users over the age of 13 need to explicitly consent to sharing their alerts with a family organizer.

by Contributed | Oct 2, 2022 | Technology
This article is contributed. See the original author and article here.
A warm welcome!

In #30DaysOfDataScience we will go from understanding the Python language to working with real life data and finally creating Machine Learning models both on Azure and in Python. The main role is understanding our data and using the knowledge to make decisions such as fraud detection, customer segmentation and product pricing.
Register for the Program set to kick off on the 17th October to 17th November 2022.
The program journey.
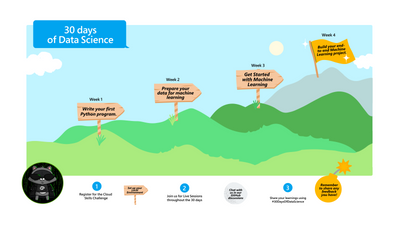
The program is set to start on the 17th of October, before then you need to register as part of the program then start learning on Microsoft Learn using the Cloud Skills Challenge modules.
We will hold discussions on GitHub and over the 30-day period we will host live sessions to help you navigate your journey. Register and join us for this epic adventure.
What to expect after 30 days.
- Successfully build 3 end to end Data Science projects i.e. fraud detection model, customer segmentation and product pricing model.
- Badge of completion to be posted on LinkedIn
Next Steps
Register for the Program set to kick off on the 17th October to 17th November 2022.
See you at the finish line!
by Contributed | Oct 1, 2022 | Technology
This article is contributed. See the original author and article here.
Starting on October 1, 2022, Microsoft is starting to disable an outdated way of logging into Exchange Online known as “basic authentication.” This outdated method is vulnerable to various forms of password attacks. The newer authentication standard is based on a standard called OAuth and the Microsoft implementation of this standard is called “modern authentication.”
Some customers might run into problems once the outdated log in method is disabled for their organization, such as not being able to sign into email.
When basic authentication is disabled for your organization, and various email clients are still using it, there are two things to know:
- How to temporarily re-enable basic authentication for your organization (which solves the immediate problem of not being able to sign in)
- How to stop using basic authentication permanently (because temporary re-enablement ends on December 31, 2022). Unless you address this, your users will not be able to sign into Exchange Online starting January 2023 when we permanently disable basic authentication.
Let’s cover both of these.
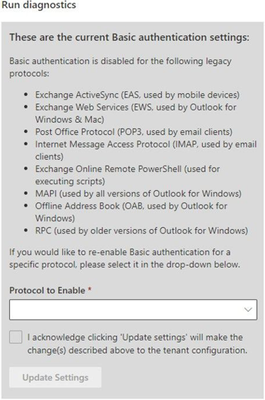
Temporarily re-enable basic authentication for your organization
You can re-enable basic auth in your tenant by using our self-service diagnostic. You launch this self-help diagnostic by clicking this button which will take you to the diagnostic in the Microsoft 365 admin center (if you are a Global admin):

Or, you can open the Microsoft 365 admin center and click the green Help & support button in the lower right-hand corner of the screen:

When you click the Help & support button, you enter our self-help system. Here you can enter the phrase Diag: Enable Basic Auth in EXO and then run the tests. The test results will look like the following (results will vary depending on what we have disabled for your organization):

You can enable basic auth for each protocol you need (one by one). Within an hour (often much sooner) of asking us to re-enable basic auth for a protocol, it will start to work again.
Be aware that by re-enabling basic auth for a protocol, your users and data are more vulnerable to security risks.
Stop using basic authentication permanently
Here are some client-specific tips for you, with links to learn more:
- Outlook for Windows: The first thing to do is to make sure Outlook is up to date and that the organization-wide switch to enable modern authentication is set to True. Without that setting, Outlook for Windows won’t use modern auth. So, make sure it’s turned on. We are turning on the organization setting for customers as we disable basic auth for MAPI/RPC protocols, so this should be enabled already, but it’s worth checking. If things are still not working, check that Outlook has the right registry keys in place.
Note: If you are using Outlook for Windows with POP or IMAP protocol, that will stop working permanently when basic authentication is disabled end of this year. Outlook for Windows does not support modern authentication using POP or IMAP and if you need to keep using those legacy protocols, you will have to use a different email client (for example, Thunderbird).
- Outlook for Mac: if your Outlook for Mac clients insist to keep using basic auth, please see our recent blog post on this subject.
- Exchange ActiveSync: this refers to a protocol used by various native email and calendar apps, such as the Mail app on iOS. All mainstream apps on up-to-date mobile clients support modern auth, but many user devices might still be using basic auth. Removing and re-adding the account from the device should automatically switch it to modern auth.
However, if you use some sort of mobile device management (MDM/MAM) solution, you should use it to deploy new profiles. Here’s how you can use Intune to set the auth mechanism for iPhone and iPad, for example. If you’re using Basic Mobility and Security take a look at this document for some more information on how to fix those devices.
There might also be some less common types of clients that stop working when basic auth is disabled; here is how to work with those:
- POP/IMAP applications: some of our customers use these protocols for application access. Please see this blog post for how to address both interactive and non-interactive apps.
- Exchange Web Service (EWS) applications: EWS supports app-only access and you can use Application Access Policies to control what an app can access. If you have apps using EWS with basic auth, you must either modify the code, or get the app developer to do so. Many partner apps have support for modern auth, they just need to modify their configuration or update to the latest versions.
- PowerShell scripts: If you have scripts, follow this guide to use modern auth within scripts.
Clients that we do not expect to have problems with starting October 1, 2022:
- Outlook for iOS and Android – this client does not use basic authentication when connecting directly to Exchange Online mailboxes.
- Outlook on the web – authenticating with Outlook on the web through your web browser always uses modern authentication if the mailbox is in Exchange Online.
Where can I find more information?
There are several resources that we wanted to provide here as additional reading:
The Exchange Team
by Contributed | Sep 30, 2022 | Technology
This article is contributed. See the original author and article here.
Not too long ago, it was the first day of school, then it was the first NFL game and we just passed the first day of fall. As seasons change, I am reminded of the things that I should do but often don’t. Either I forget or avoid. So it is for Business Continuity/Disaster Recovery (BCDR) efforts. About 10 years ago, I wrote a blog post with some points about DR (Disaster Recovery – Microsoft Tech Community) then, about seven years ago, I posted a DR ‘reminder’ (Disaster Recovery – A Reminder – Microsoft Tech Community). Those were both ‘pre-cloud’ – which seems so long ago. In any event, a post from me around BCDR for cloud components is well past due.
NOTE: Service availability is one aspect of BCDR, as is data availability. For the most part, those two elements are solid when it comes to SaaS – those are two of the value props of the SaaS model. However, in this post, I’m focusing on recovering from accidental or malicious deletions of configurations in some of your key Microsoft cloud services.
“What would you do if…?”
You get a call that ‘something is going on’ – people aren’t getting blocked when they should be. People aren’t getting prompted when they should be. Where you’d normally see your org’s logo on the sign in pages, you see the Microsoft logo. You recall that moments ago, you didn’t get prompted when you went to check email via OWA this morning. Your stomach turns.
You pop open the Azure portal and immediately notice you don’t get MFA’d. Your stomach turns again but more deeply. Your face gets hot. Your brain races as you ask yourself “Did I do something?” You open the AAD Conditional Access portal spot … there are only a few ‘default’ policies listed. There are normally a dozen or more policies with your custom naming standard. You rub your eyes to see if you’re just not seeing it but the emptiness remains. You refresh the portal page. You verify the tenant name … still blank. You quickly jump over to the MEM portal … many of the Intune policies and settings are gone, too. You check out the Defender for Cloud Apps (aka MCAS) policy page; your custom CASB policies are gone. It’s like you’re signing in to a brand new M365 trial.
Before you tackle the ‘who/what/when/where’ questions from management to explain what happened, you need to get back to a functional run-state. That won’t be too tough, thankfully, as you have nightly exports from the various M365 services. Or you have a weekly calendar reminder to run manual exports, every Friday when you first get into the office, right? Or you have Word docs with screen captures of the portal pages that you update the first Tuesday of every month, right? Or an XLS with the settings? Or you have a chicken-scratch Notepad file from when you first setup the policies?
Or, perhaps you don’t; perhaps you have nothing more than a vague visual memory of what you’d see when you’d look in the portals; a general idea of the various policies and what they did – but only sparse memories of a few of the myriad settings across the services. Oh, and the portal UIs have changed considerably since you setup those policies years ago (if it even was you who set them up). It’s gonna be a loooong day(s).
Ok, back to reality … whew.
An ounce of prevention (or planning) is worth a pound of cure. Just do something. It doesn’t need to be perfect. The only thing worse than a mass-deletion event is one without any sort of recoverability planning and desired settings references/materials. Staring at a blank portal page, trying to recall from memory what had been setup previously is no bueno. Plus, management will be asking ‘why weren’t we better prepared to recover from this?’ Have a solid answer vs a ‘deer in the headlights’ stare.
Sadly, as of today, there isn’t a ‘backup now’ or ‘recover now’ button in the portals but there is some good news; since these are SaaS capabilities, there are no servers to restore or infrastructure to recover/establish. It’s basically entering configuration information in web forms.
Here are a few ideas on possible BCDR for your M365 services (you may find/have others – if so, great! Share what’s worked/not worked for you in the comments)
- Screen-scrapes from the portal pages into organized docs that are stored in an available manner (electronically, local USB and hard-copy – three ring binders are great for this type of info, stored in your DR tubs)
- In the past, this was a more viable option but these days, in my view, there are just too many configuration screens/options for a given configuration and it takes a long time and a lot of clicks to drill-down to all of the various pages/sub-pages of a configuration/policy.
- That said, if this is your jam, rock on. Put on some headphones, fire up Winamp and blast REO Speedwagon while you try to wear out the CTRL/C/V buttons on your keyboard.
- M365 DSC is a well-developed PowerShell toolset to do all sorts of things with many cloud service configurations (export/import, monitor for drift, etc.)
- AAD Exporter looks very promising, but I’ve not spent any time with it, and it only captures AAD
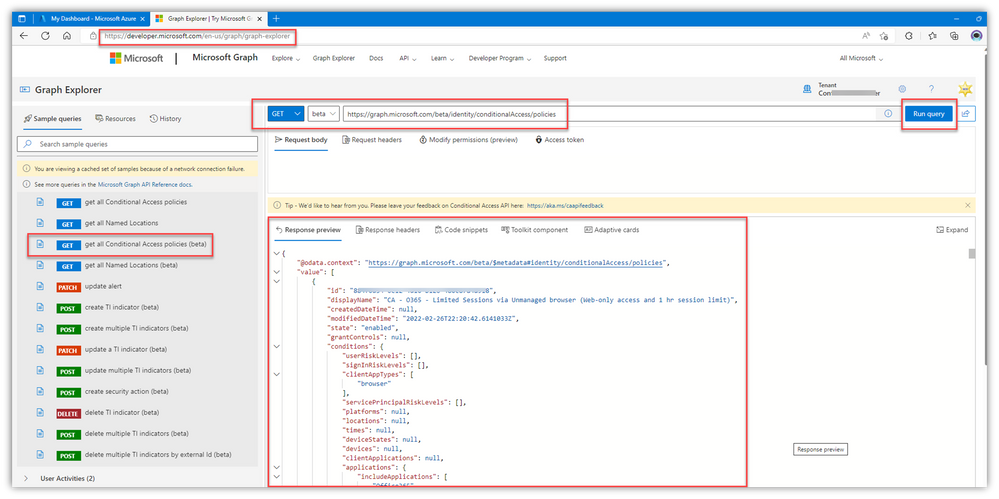
- Ad hoc Graph Explorer queries

Explore the various options “discoverable” in the dynamic auto-fill query box – I guarantee you’ll be giddy at some of the things you’ll find:
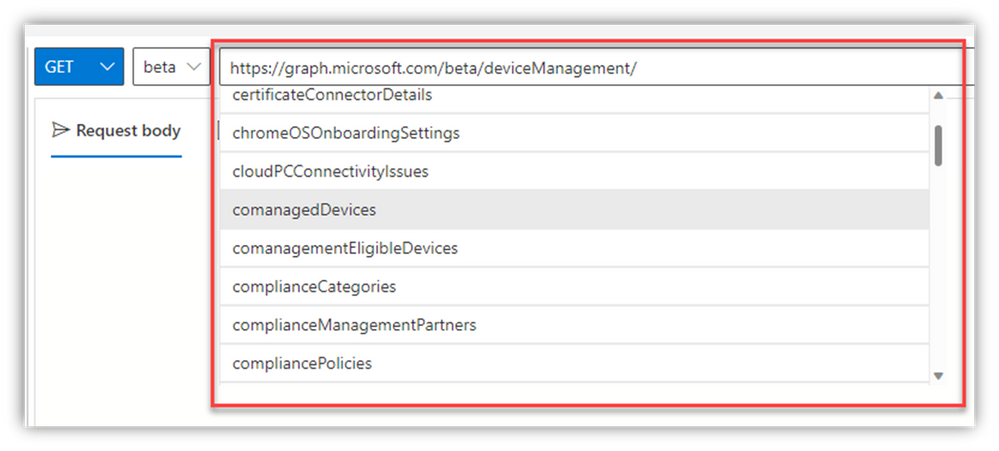
- Here are a few query URLs you can copy and paste in the query box, then copy/paste the GET results into Notepad or something – It’s literally THAT easy to grab many of your critical cloud configs
NOTE: You might not have the proper permissions to access certain elements from Graph, even if you’re using a GA account:
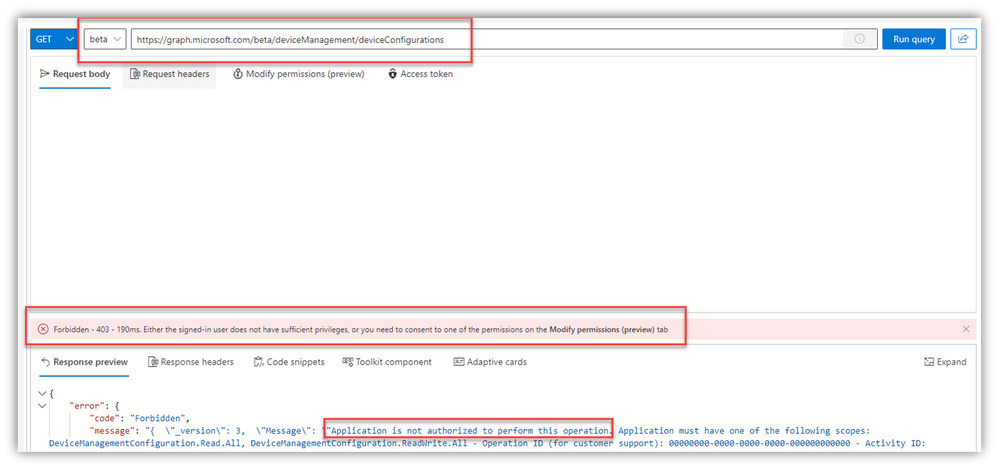
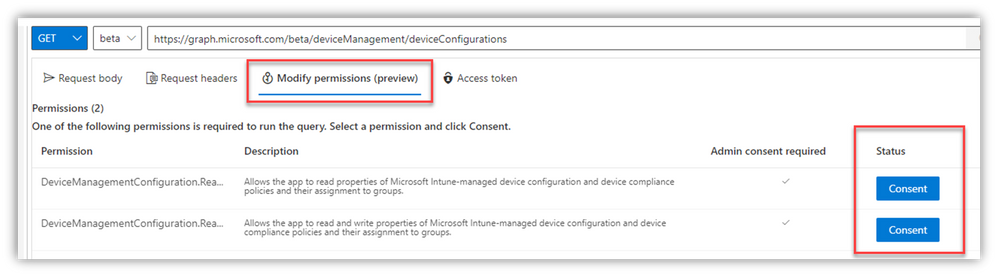
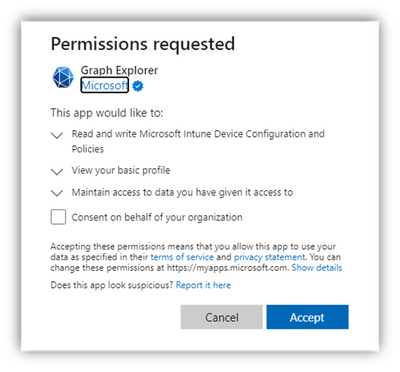
It’s an easy fix, right from within Graph Explorer, but be sure you understand what ‘Consent’ means – and also realize that your global AAD settings might restrict or block these consent actions:
NOTE: MDCA (Defender for Cloud Apps aka MCAS) doesn’t seem to have similar graph exposure. You can export the ‘whole’ portal config, policies and IP list into a single JSON file via Settings but I don’t know what that includes/leaves out, and there isn’t a way to re-import it for recovery.
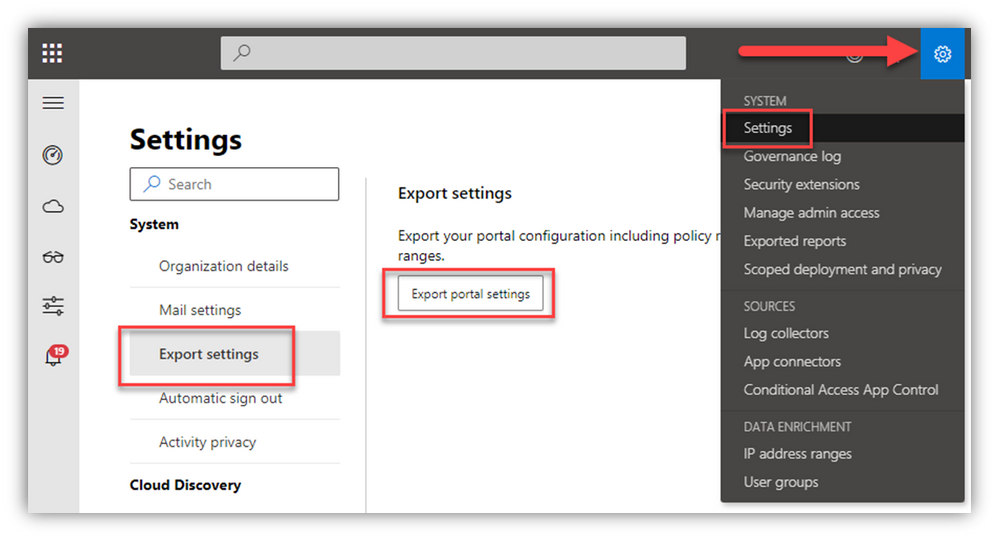
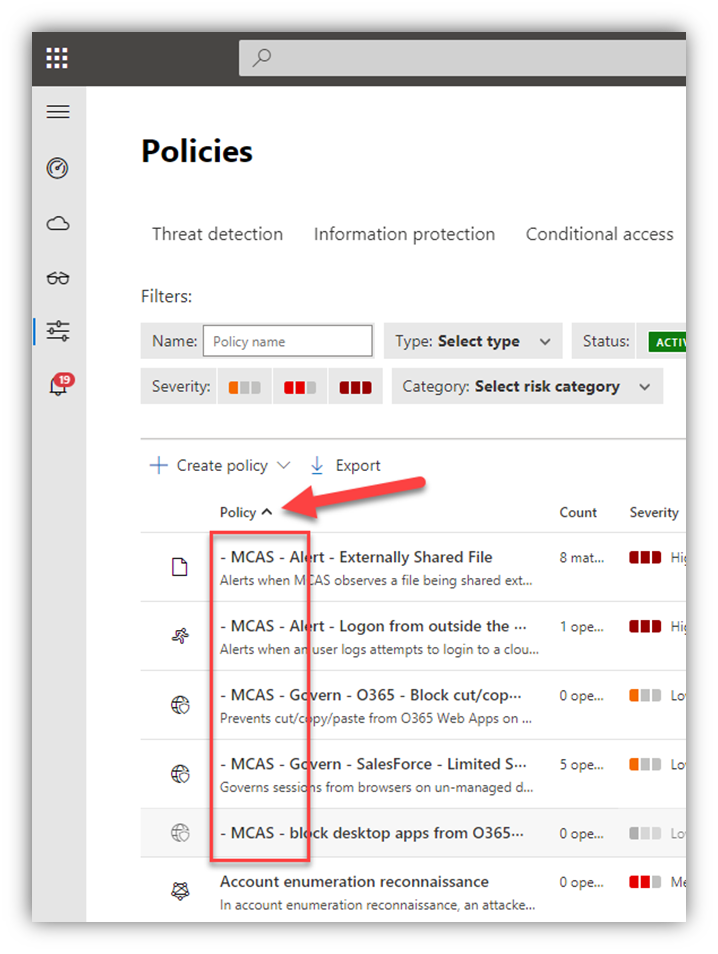
Regardless, you can easily get screen captures of your custom policies from the portal.
- In my case, I use a naming convention for my custom MCAS policies which makes it super easy to sort them in the portal, then get screen shots of each policy
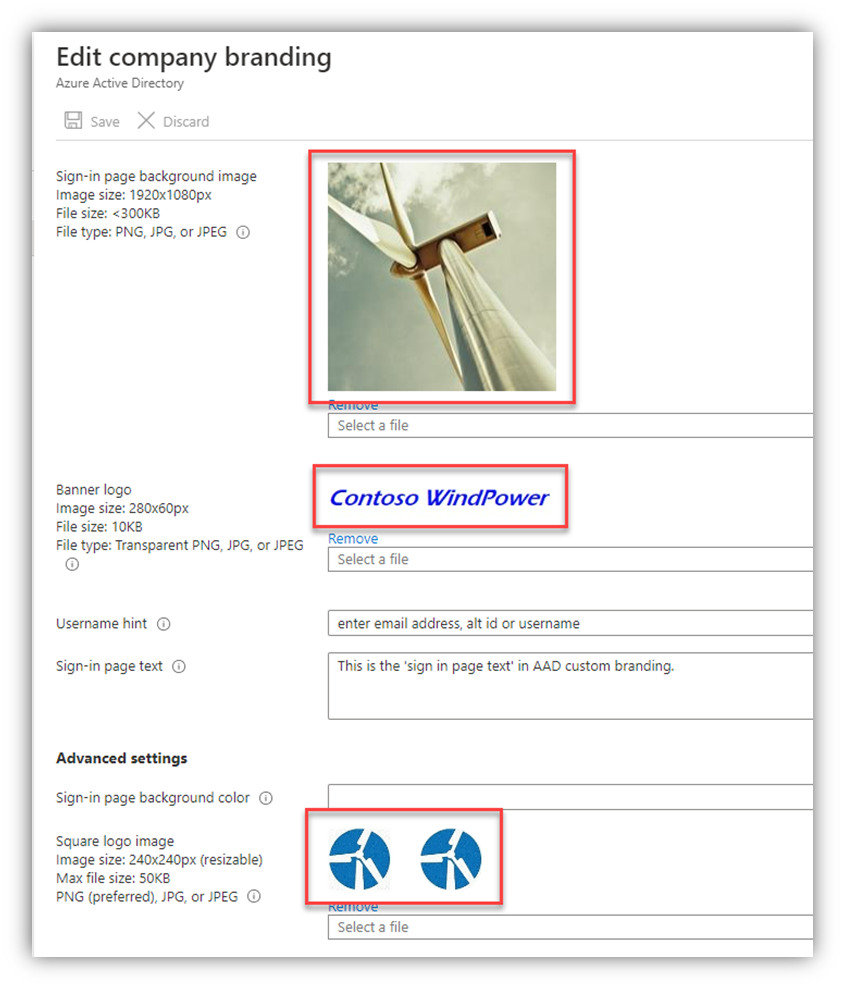
Visuals are Important
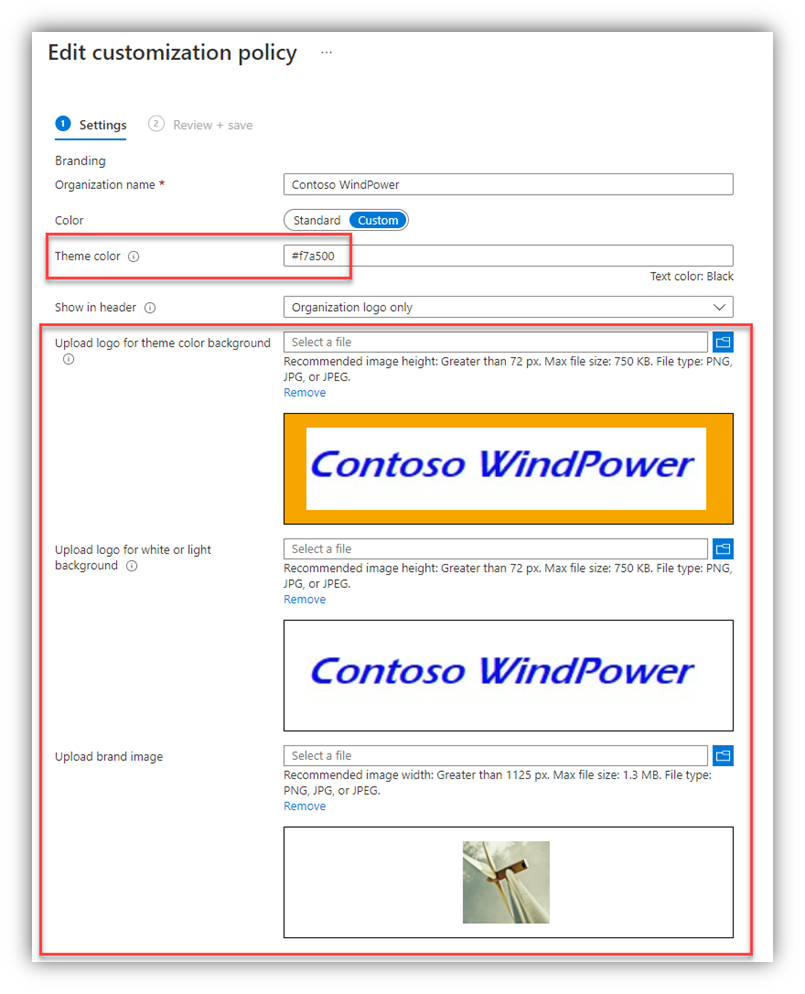
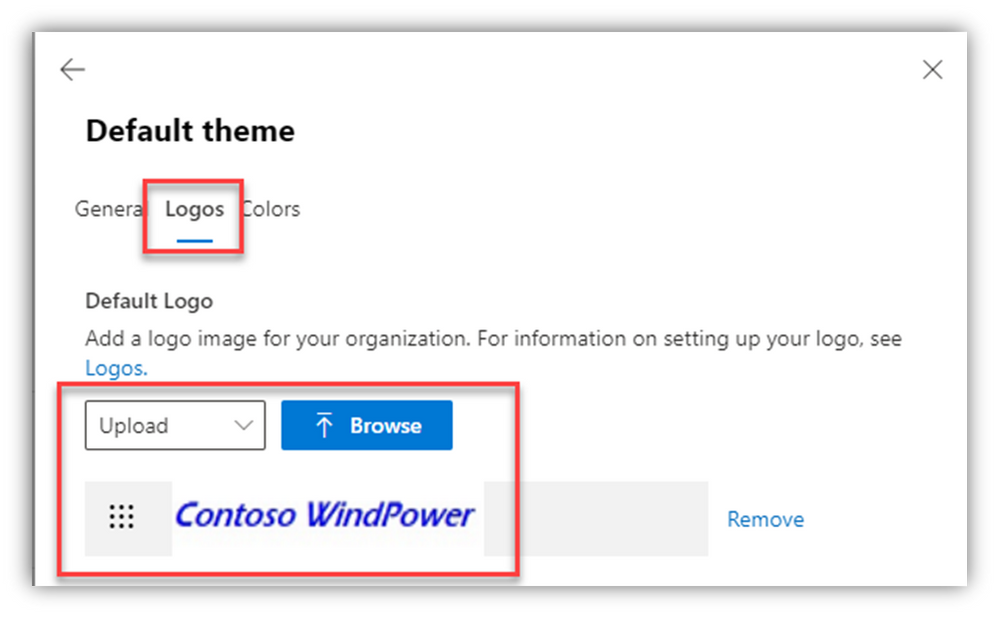
A few notes about the visual branding elements of the various services/portals, and the Company Portal for Intune:
- At this point, I don’t know of a way to export the images/pictures/graphics that are uploaded to the services. In the exports of the settings (if you can find them), there are references to CDN URL links but they’re ambiguous and don’t point directly to a ‘file.’
- Those files have very specific size limits/pixel counts and other parameters, not to mention there were probably hoops to jump through to get ‘organizational approval’ to use those specific images, etc. Track down those specific files that were uploaded and store them in the event that an accidental (or planned) change gets made to those and you want to revert/roll-back/recover.
- Those visual elements are part of your org’s ‘front door’ to most M365 services – most of your users will see those often.
- If those visuals change, even expectedly, it can cause “confusion” for a lot of people (read: many helpdesk calls). Be prepared.
- If you use custom colors in the Intune customizations and/or the Office ‘theme,’ they are likely hex values that you should make a note of.
- Further, some of the AAD branding elements apply to Autopilot, too – Windows Autopilot Azure AD Branding – Microsoft Tech Community
Think outside the box
With BCDR topics, you have to think well outside of typical ‘day to day’ operations. Make sure you have a plan, the plan is documented and vetted/tested and updated every month/quarter/year.
Here are a few more “table-top exercises” and thoughts related to BCDR:
- If Teams/chat and Exchange/email are down, along with AD/AAD (i.e. the GAL), how will you communicate with one another? No Teams chats. No email. No phone numbers.
- You can call someone’s cellphone but how will you find phone numbers?
- How will you execute a ‘war room’ meeting/conference call if Teams is down?
- Make a plan, make a list of names and phone numbers, store it somewhere and have a hard-copy. Update it (quarterly?).
- Ensure the decision tree used to declare a BCDR ‘incident’ includes cloud services/issues
- Print out the settings/config/recovery docs and put them into a 3-ring binder in your DR tub, along with a USB stick containing those files
- Don’t fall prey to the idea that ‘high availability’ is all you need. Accidents happen – and they replicate.
- Try to expect the unexpected. Think through the ‘what ifs’ and worst-case scenarios.
- I recall being part of a DR event where the highly available SAN went down … care to guess where the well-developed DR plans/docs/tools/etc. were stored?
Cautionary reminders
- Credential exposure: All of this BCDR documentation I mentioned above should be for your service settings, profiles and configurations – it should not include your (nor anyone’s) credentials. Safety first. Zero trust.
- Of course, special accounts/credentials needed for BCDR might need to be stored – but securely and separately from configuration recovery docs.
- Risk of unintended changes:
- Using Graph is very helpful but stick with GET. If you wander down the paths of POST, DELETE, SET … anything other than GET … you could very well enter a world of pain.
- Many of the cloud configuration screens/UIs don’t have the typical Win32 app ‘Are you sure?’ verification prompts. Admins sometimes accidentally make a change just by ‘casual administration,’ while they poke around in portal pages.
Sharing IT horror stories is a pretty fun past-time of ‘the job’ but in the heat of an incident or outage, there is VERY little fun. Do yourself a favor (and your org), take some time in the next week and review/setup exports of your key configurations. You’ll sleep a bit better once you do.
Hilde




Recent Comments