
by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Today Sarah answers a questions that is on every on-prem IT person.
When you have systems in all kinds of different location and platform how do you keep track of them all without going nuts? how do you tame the multi-RDP windows beast that ends up being your desktop. Sarah answers that questions in today’s One Ops Question.
Windows admin center is a key component of this simplification exercise. As you may know, Windows Admin Center is a locally deployed, browser-based app for managing Windows servers, clusters, hyper-converged infrastructure, as well as Windows 10 PCs. And it’s free.
Here are a few things you can use Windows Admin Center for:
 Simplify server management
Simplify server management
Manage your servers and clusters with modernized versions of familiar tools such as Server Manager. Install in under five minutes and manage servers in your environment immediately, no additional configuration required. For details, see What is Windows Admin Center?.
 Work with hybrid solutions
Work with hybrid solutions
Integration with Azure helps you optionally connect your on-premises servers with relevant cloud services. For details, see Azure hybrid services
 Streamline hyperconverged management
Streamline hyperconverged management
Streamline management of Azure Stack HCI or Windows Server clusters. Use simplified workloads to create and manage VMs, Storage Spaces Direct volumes, Software-Defined Networking and more. For details, see Manage Hyper-Converged Infrastructure with Windows Admin Center
in other words WAC is one of the tools that would simplify managing your environment on-prem, in the cloud and hybrid.
check it out!
by Scott Muniz | Jul 1, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
G ‘day, I am Vic Perdana, Sr. PFE based in Melbourne, Australia.
As COVID-19 forces people to work from home, the number of bad actors is ramping up as demonstrated by the increase of cyber-attacks globally, it is becoming *very* important to educate ourselves with ways we can protect our IT assets from being compromised.
IT Security is no longer a responsibility of the Security team but is everyone’s responsibility. Moreover, as an IT engineer we have unprecedented responsibility to ensure that our system is secure especially as we expand our footprint to the cloud. I often get asked, how secure is cloud? And as you know the answer is “it depends” on how much investment you’re willing to make to ensure it is secure. In Azure, we provide tons of security features, but not all customers are aware of these and this is the very reason this offering was created.
The Offering Overview
Within Microsoft Services, we provide a variety of support offerings which educate customers on several Azure Security-related features, and here the focus is our WorkshopPLUS Azure Security Best Practices.
The workshop introduces pivotal security controls to kickstart and improve your security journey in Azure. WorkshopPLUS designation signifies that hands-on labs will be part of the delivery experience. This enables you to implement various security concepts learned from Premier Field Engineer (PFE) knowledge sharing sessions and equips you with practical experience in a lab environment.
What’s Included
The content of this offering is a mix of governance, administration and security best practices at a L200-300 level which focuses on the breadth of Azure security topics.
Azure Security Foundation
This module sets up the context of cloud security and not only applicable to Azure. Many customers may have a misconception cloud is not secure or the opposite, by moving to the cloud we are automatically secured. We will revisit the basic security concepts that are applicable to both on-premises and cloud environments plus a review of the shared responsibility concept of cloud security.
You will be introduced with Microsoft Cybersecurity reference architecture which highlights the vast Azure hybrid-security capabilities.
Azure Governance
Bruce Schneier famously mentions “security is a process, not a product” and here’s why you will examine this further by emphasizing that onboarding the whole organization in the security journey (the process) is a mandatory pre-requisite for a successful impact of configuring security services (the product). You will be introduced to relevant security components related to Azure Governance such as Subscription Management, Role-Based Access Control (RBAC), Azure Policy, Blueprints.
Azure Identity Protection
Identity is the modern security perimeter; hence, it is vital to understand the security controls and features available in Azure to secure our identity both on-premises and in the cloud. That’s why we start the module by revisiting our Securing Privileged Access (SPA) roadmap as it is still applicable when you go to the cloud.
Next, you are introduced to Azure advanced protections such as Conditional Access, Identity Protection, and various Azure Active Directory identity governance services which includes Access Reviews, Privileged Identity Management, and Entitlement Management.
Azure Network Security
As we extend our IT footprint to the cloud, our assets will no longer be within the perimeter of our data center.
In this module you will be introduced to modern network security controls and features in Azure that will allow you to extend and connect your on-premises networks securely, such as Express Route, DDoS protection, Azure Firewall, Network Security Groups, WAF, and much more.
Azure Data Protection
As Security professionals, protecting data is ultimately our objective; hence we will spend quality time in educating our customers on fundamental Azure services that will help with our mission to protect data. Azure Key Vault is one of the core services which will be discussed including how we can leverage this effectively in a Business as Usual (BAU) setting. We will also walkthrough features to secure services our customers use to store their data e.g., Azure Storage, Azure SQL, and Azure Information Protection.
PaaS Security
This module demonstrates the use of Key Vault in a Web App coupled with Managed Identity. Deployment acceleration method with DevOps is widely used, we will cover the importance of embedding security in a DevOps process using Secure DevOps Kit.
Security Operations
This is the module where we put things together and provide practical information related to our flagship Security services in Azure: Azure Security Center and Azure Sentinel. We will also cover relevant technologies supporting these Security features such as Log Analytics, Activity Logs, and Azure Monitor.
Delivery model
This is a 3-day delivery (onsite or remote) led by an accredited Premier Field Engineer (PFE). While we focus on the breadth of Azure security topics, we will be discussing implementation areas that provide highest impact to your organization.
- Pre-engagement scoping call to highlight the overall engagement, including pre-requisites for a successful delivery.
- Knowledge Transfer and labs sessions
- Azure Security Foundation
- Azure Governance
- Identity Protection
- Azure Network Security
- Virtual Machine Security
- Data Protection
- Securing PaaS
- Security Operations
- Wrap up with a top 10 Azure security best practices
*For a closed workshop, there is an option to focus on some parts of the topics, but this needs to be agreed in advance as part of a scoping call.
Conclusion
Cybersecurity is a hot topic and there is no single product or a quick fix (band-aid) that can be applied to address security challenges. This recent post from our National Security Officer highlights the importance of keeping our security hygiene in check.
Taking up this offering is a great start to kickstart and boost your security journey as you extend your IT footprint to the cloud.
What are you waiting for, ask your TAMs to reserve a spot! :)
Disclaimer
As of this writing, the above modules are in scope, however, they are subject to change as Azure Security offerings and the offering evolve responding to customers feedback.
Credit
Special thanks to the offering team: Elliot Huffman, Joao Paulo Ramos.
by Scott Muniz | Jul 1, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
We are making available the private preview of Azure Arc enabled SQL Server. The preview includes the following features:
- Use the Azure Portal to register and track the inventory of your SQL Server instances across on-premises, edge sites, and multi-cloud in a single view.
- Use Azure Security Center to produce a comprehensive report of vulnerabilities in SQL Servers and get advanced, real time security alerts for threats to SQL Servers and the OS.
- Investigate threats in SQL Servers using Azure Sentinel.
You can register any Windows or Linux based SQL Server to track your inventory. Azure Security Center’s advanced data security works on Windows-based SQL Server version 2012 or higher, running on virtual machines and physical servers and hosted on any infrastructure outside of Azure.
Here’s a video of the Arc enabled SQL Server experience with Azure Security Center.
If you are interested in participating in this preview, please fill out the sign-up form and select the option Server Management (SQL Server).
by Scott Muniz | Jul 1, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Intro
There are many excellent resources available that explain the motivation for going to the cloud and/ or Application modernisation. Assumption is that Azure is the Cloud provider and there is a NEW application that needs to be hosted. The application can be written in any of the popular languages. For existing workloads have a look at this for guidance; please be aware that the flow is a start but not as binary as it would suggest.
Hosting the application on a VM is also an option but is not being considered as taking maximum advantage of the available cloud benefits. VM hosting is not within the scope.
Summary
With (full) PAAS offerings like Azure Webapps and Azure Functions you make optimal use of the Cloud Benefits. Although you have a Pay as You go model there is a price tag for all the functionality you get out of the box. Although the PAAS offerings try to have a non opinionated technology stack the implementation is done according to the best practices of Microsoft and will never be as open and flexible like the open source solutions.
Hosting on a (semi-paas) container solution like AKS, can be considerably cheaper initially. However customer responsibility and operational costs are higher than solutions based on Webapps and Functions. Container solutions give a higher flexibility but do not come with standard solutions like Application authentication out of the box. In general more skills are required from the Developers and Operators maintaining the Containerised solution(s) on the other hand you have a very flexible platform that is based on the latest open source standards.
There is no right or wrong here, only what is suitable to you. When making a decision try to make it an educated one, the decision matrix below could be a start for your journey.
Hosting options
To have a better understanding of the products a short description of the product and its features is given. Intention is to give a quick overview, more information can be found in the links provided.
Azure Web apps
WebApps gives you a platform to host your applications based on an underlying runtime stack, for eg: Tomcat on linux for nodejs and python based workloads.
This platform is linked to an App Service Plan which gives you a set of features and capabilities.
There are 3 major SKU types for WebApps:
- Dev/ Test; ideal for hosting small solution, has the least capabilities but is also the cheapest
- Prod; Has all the features you probably need, hosted on a shared platform
- Isolated; Has all the features you need. Also referred as Application Service Environment or ASE, this is the enterprise ready solution where you have dedicated hardware on a dedicated network and tenant.
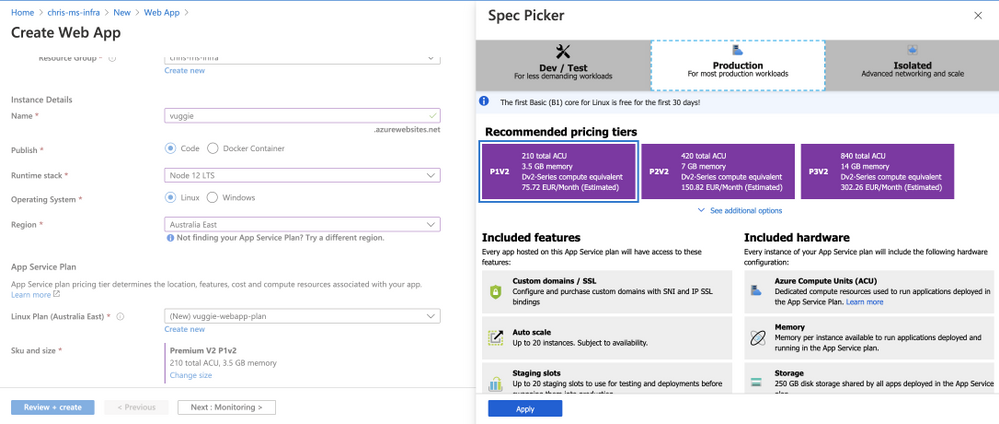
Within one of the SKU types you can select a tier which has impact on the specifications and specs:
With Azure Webapps you do not have to worry about setting up and maintaining an infrastructure for your applications.
Short summary of operational concerns:
- Scalability; depending on SKU and tier, your APP can scale as desired
- (High) Availability; depending on SKU and tier, WebApps will make sure that your service is available
- Security; built in features like integration with AAD and using Azure Services via Service endpoints (Prod SKU and up). Your Webapp is also by default protected against known vulnerabilities like Denial of Service Attacks.
- Monitoring and Alerting; Alerts can be easily configured and integration with Azure Monitoring and App insights provides valuable insights.
Other important features are the KUDU toolkit for version management and integration with CI/CD tooling and Deployment slots for deploying new releases in a blue/green scenarios.
Azure Webapps provides the functionality of hosting containers as well, but (my opinion) that makes no sense as Azure Webapps is not designed to be a container orchestrator or scheduler.
The AWS alternative to Azure Webapps is Elastic Beanstalk. For more information, please have a look at the documentation.
Azure Functions
Considered by many as the holy grail of modern application hosting. Azure Functions is also referred as Serverless technology, the idea is to abstract the Server (infra) away and put the main focus on the function(s) of your app.
Azure functions shines in scenarios where you need event driven architectures. It is (in general) not used for hosting long running (stateful) applications.
Azure functions is often used in conjunction with an (process) orchestrator like Azure Logic Apps. Below are some well known scenario’s for Azure Functions:
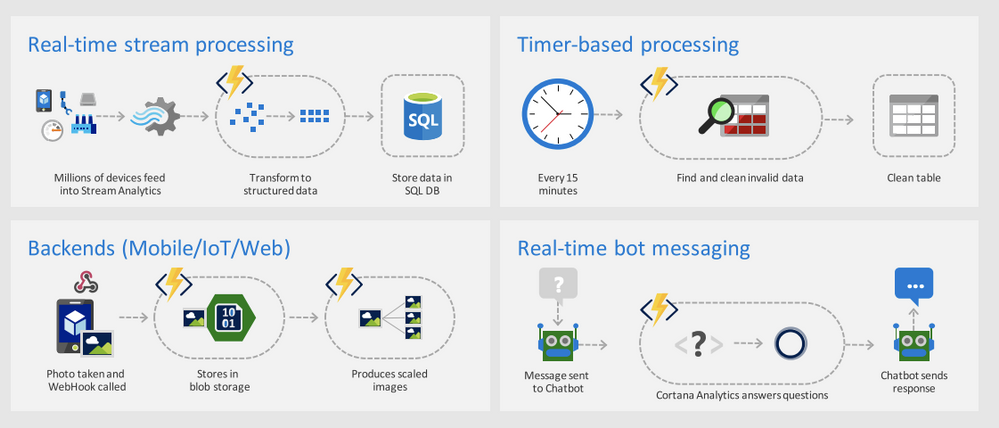
Two concepts are essential in the usage of Azure Functions: Trigger and Bindings.
A Trigger is an event that is responsible for the start of a the execution of a Function; example of triggers are:
- EventHub Trigger
- Blob Storage Trigger
- Http Webhook
- Timer Trigger
Bindings are links to the data used within the function.
There are Input Bindings and Output Bindings, an example of an InputBinding could be a message on a queue and the output could be a transformed message that will be persisted in a database using an output binding.
Short summary of operational concerns:
- Scalability; depending on SKU and tier, your Azure Function can scale as desired
- (High) Availability; depending on SKU and tier, Azure Functions will make sure that your service is available
- Security; built in features like integration with AAD, integrations with other Azure products are very easy as well, for eg APIm
- Monitoring and Alerting; Alerts can be easily configured and integration with Azure Monitoring and App insights provides valuable insights.
Cost efficiency is a major factor for using Azure Functions.
While with other platforms you are paying for the usage of the underlying hosting platform, with Azure functions you do not. Azure Functions provides the concept of Micro Billing, with micro billing you only pay for the actual usage of the function.
The AWS alternative to Azure Functions is Lambda. For more information, please have a look at the documentation.
Azure Kubernetes Service
Container technology has made a tremendous growth in usage and adaption the last 5 years. With Kubernetes on the forefront of hosting container workloads it has an enormous following and the fanbase is growing. Azure provides hosting of container workloads through several services but Azure Kubernetes Service (AKS) is by far the fastest growing service at the moment.
An alternative with most of the functionalities is Azure Redhat Openshift (ARO), this is considered an opinionated version of managed Kubernetes. It is implemented according to the best practices of Redhat. ARO uses Red Hat Enterprise Linux CoreOS in stead of Ubuntu (debian based), which is used by AKS . ARO is a collaboration between Microsoft and Redhat.
AKS is a semi PAAS offering; Simply put Kubernetes consists of 2 components:
- Management component; responsible for managing your workloads
- Worker nodes; the worker bees that are responsible for hosting your application
The managed component is a PAAS offering which is free of use; depending if you choose to have a SLA. The worker nodes are the compute power and is considered the IAAS solution for this offering.
However this is not fully true as the maintenance of the Operating System is executed by Microsoft, the customer is responsible for the reboot actions that might be needed.
Upgrading the Kubernetes version itself is very easy but must initiated by the customer, there are tools available that can assist in this (for eg KURED).
Microsoft has put all effort in to make maintenance of this shared responsibility platform as easy as possible.
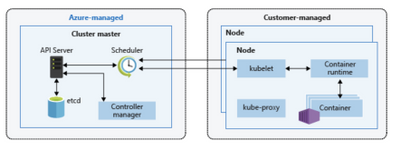
Once this platform is UP and running it provides an enormous flexible platform that can host almost all open source based solutions like: Apache Flink and ElasticSearch. AKS even supports hosting Windows containers.
Short summary of operational concerns:
- Scalability; AKS uses a POD autoscaler for Pod distribution across existing nodes and a Cluster Autoscaler that utilises the underlying VM scale-sets.
- (High) Availability; Kubernetes is designed for HA scenarios, in most regions Availability zones bring an extra layer of availability insurance
- Security; Application security does not come out of the box, however API security for managing AKS is an option that is easily configured to work with AAD integration and Kubernetes RBAC
- Monitoring and Alerting; AKS comes with the option to automatically integrate with Azure Monitor, by enabling this option an extra deployment on your kubernetes cluster is running which is responsible for logging the AKS/ app events.
Kubernetes and thus AKS is also suitable to host event driven solutions. With KEDA you can host Azure Functions on your AKS cluster, it does provide all the functionality using triggers and bindings but does not have the micro billing feature like Azure Functions does.
The AWS alternative to Azure Kubernetes Service is Elastic Kubernetes Service. For more information, please have a look at the documentation.
Decision Matrix
| Features |
Costs |
Features |
 = Fully Managed = Fully Managed |
$ = Affordable
|
+ = Limited
|
 = Partially Managed = Partially Managed |
$$ = Mid Priced
|
++ = OK
|
 = Self Managed = Self Managed |
$$$ = Premium |
+++ = Excellent |
Links:
by Scott Muniz | Jul 1, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
While building an Azure Functions application, setting an IoC container for dependency injection has many benefits by comparing to just using the static classes and methods. Azure Functions leverages the built-in IoC container featured by ASP.NET Core that is easy to use, without having to rely on any third-party libraries. Throughout this post, I’m going to discuss five different ways to pick up a dependency injected from multiple instances sharing with the same interface.
Implementing Interface and Classes
Let’s assume that we’re writing one IFeedReader interface and three different classes, BlogFeedReader, PodcastFeedReader and YouTubeFeedReader implementing the interface. There’s nothing fancy.
public interface IFeedReader
{
string Name { get; }
string GetSingleFeedTitle();
}
public class BlogFeedReader : IFeedReader
{
public BlogFeedReader()
{
this.Name = "Blog";
}
public string Name { get; }
public string GetSingleFeedTitle()
{
return "This is blog item 1";
}
}
public class PodcastFeedReader : IFeedReader
{
public PodcastFeedReader()
{
this.Name = "Podcast";
}
public string Name { get; }
public string GetSingleFeedTitle()
{
return "This is audio item 1";
}
}
public class YouTubeFeedReader : IFeedReader
{
public YouTubeFeedReader()
{
this.Name = "YouTube";
}
public string Name { get; }
public string GetSingleFeedTitle()
{
return "This is video item 1";
}
}
IoC Container Registration #1 – Collection
Let’s register all the classes declared above into the Configure() method in Startup.cs.
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.AddTransient<IFeedReader, BlogFeedReader>();
builder.Services.AddTransient<IFeedReader, PodcastFeedReader>();
builder.Services.AddTransient<IFeedReader, YouTubeFeedReader>();
}
By doing so, all three classes have been registered as IFeedReader instances. However, from the consumer perspective, it doesn’t know which instance is appropriate to use. In this case, using a collection as IEnumerable<IFeedReader> is useful. In other words, inject a dependency of IEnumerable<IFeedReader> to the FeedReaderHttpTrigger class and filter one instance from the collection.
public class FeedReaderHttpTrigger
{
private readonly IFeedReader _reader;
public FeedReaderHttpTrigger(IEnumerable<IFeedReader> readers)
{
this._reader = readers.SingleOrDefault(p => p.Name == "Blog");
}
[FunctionName(nameof(FeedReaderHttpTrigger.GetFeedItemAsync))]
public async Task<IActionResult> GetFeedItemAsync(
[HttpTrigger(AuthorizationLevel.Function, "post", Route = "feeds/item")] HttpRequest req,
ILogger log)
{
var title = this._reader.GetSingleFeedTitle();
return new OkObjectResult(title);
}
}
It’s one way to use the collection as a dependency. The other way to use the collection is to use a loop. It’s useful when we implement either a Visitor Pattern or Iterator Pattern.
public class FeedReaderHttpTrigger
{
private readonly IEnumerable<IFeedReader> _readers;
public FeedReaderHttpTrigger(IEnumerable<IFeedReader> readers)
{
this._readers = readers;
}
[FunctionName(nameof(FeedReaderHttpTrigger.GetFeedItemAsync))]
public async Task<IActionResult> GetFeedItemAsync(
[HttpTrigger(AuthorizationLevel.Function, "post", Route = "feeds/item")] HttpRequest req,
ILogger log)
{
var title = default(string);
foreach (reader in this._readers)
{
if (reader.Name != "Blog")
{
continue;
}
title = reader.GetSingleFeedTitle();
}
return new OkObjectResult(title);
}
}
IoC Container Registration #2 – Resolver
It’s similar to the first approach. This time, let’s use a resolver instance to get the dependency we want. First of all, declare both IFeedReaderResolver and FeedReaderResolver. Keep an eye on the instance of IServiceProvider as a dependency. It’s used for the built-in IoC container of ASP.NET Core, which can access to all registered dependencies.
In addition to that, this time, we don’t need the Name property any longer as we use conventions to get the required instance.
public interface IFeedReaderResolver
{
IFeedReader Resolve(string name);
}
public class FeedReaderResolver : IFeedReaderResolver
{
private readonly IServiceProvider _provider;
public FeedReaderResolver(IServiceProvider provider)
{
this._provider = provider;
}
public IFeedReader Resolve(string name)
{
var type = Assembly.GetAssembly(typeof(FeedReaderResolver))
.GetType($"{name}FeedReader");
var instance = this._provider.GetService(type);
return instance as IFeedReader;
}
}
After that, update Configure() on Startup.cs again. Unlike the previous approach, we registered xxxFeedReader instances, not IFeedReader. It’s fine, though. The resolver sorts this out for FeedReaderHttpTrigger.
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.AddTransient<BlogFeedReader>();
builder.Services.AddTransient<PodcastFeedReader>();
builder.Services.AddTransient<YouTubeFeedReader>();
builder.Services.AddTransient<IFeedReaderResolver, FeedReaderResolver>();
}
Update the FeedReaderHttpTrigger class like below.
public class FeedReaderHttpTrigger
{
private readonly IFeedReader _reader;
public FeedReaderHttpTrigger(IFeedReaderResolver resolver)
{
this._reader = resolver.Resolve("Blog");
}
[FunctionName(nameof(FeedReaderHttpTrigger.GetFeedItemAsync))]
public async Task<IActionResult> GetFeedItemAsync(
[HttpTrigger(AuthorizationLevel.Function, "post", Route = "feeds/item")] HttpRequest req,
ILogger log)
{
var title = this._reader.GetSingleFeedTitle();
return new OkObjectResult(title);
}
}
IoC Container Registration #3 – Resolver + Factory Method Pattern
Let’s slightly modify the resolver that uses the factory method pattern. After this modification, it removes the dependency on the IServiceProvider instance. Instead, it creates the required instance by using the Activator.CreateInstance() method.
public class FeedReaderResolver : IFeedReaderResolver
{
public IFeedReader Resolve(string name)
{
var type = Assembly.GetAssembly(typeof(FeedReaderResolver))
.GetType($"{name}FeedReader");
var instance = Activator.CreateInstance(type);
return instance as IFeedReader;
}
}
If we implement the resolver class in this way, we don’t need to register all xxxFeedReader classes to the IoC container, but IFeedReaderResolver would be sufficient. By the way, make sure that all xxxFeedReader instances cannot be used as a singleton if we take this approach.
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.AddTransient<IFeedReaderResolver, FeedReaderResolver>();
}
IoC Container Registration #4 – Explicit Delegates
We can replace the resolver with an explicit delegates. Let’s have a look at the code below. Within Startup.cs, declare a delegate just outside the Startup class.
public delegate IFeedReader FeedReaderDelegate(string name);
Then, update Configure() like below. As we only declared the delegate, its actual implementation goes here. The implementation logic is not that different from the previous approach.
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.AddTransient<BlogFeedReader>();
builder.Services.AddTransient<PodcastFeedReader>();
builder.Services.AddTransient<YouTubeFeedReader>();
builder.Services.AddTransient<FeedReaderDelegate>(provider => name =>
{
var type = Assembly.GetAssembly(typeof(FeedReaderResolver))
.GetType($"FeedReaders.{name}FeedReader");
var instance = provider.GetService(type);
return instance as IFeedReader;
});
}
Update the FeedReaderHttpTrigger class. As FeedReaderDelegate returns the IFeedReader instance, another method call should be performed through the method chaining.
public class FeedReaderHttpTrigger
{
private readonly FeedReaderDelegate _delegate;
public FeedReaderHttpTrigger(FeedReaderDelegate @delegate)
{
this._delegate = @delegate;
}
[FunctionName(nameof(FeedReaderHttpTrigger.GetFeedItemAsync))]
public async Task<IActionResult> GetFeedItemAsync(
[HttpTrigger(AuthorizationLevel.Function, "post", Route = "feeds/item")] HttpRequest req,
ILogger log)
{
var title = this._delegate("Blog").GetSingleFeedTitle();
return new OkObjectResult(title);
}
}
IoC Container Registration #5 – Implicit Delegates with Lambda Function
Instead of using the explicit delegate, the Lambda function can also be used as the implicit delegate. Let’s modify the Configure() method like below. As there is no declaration of the delegate, define the Lambda function.
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.AddTransient<BlogFeedReader>();
builder.Services.AddTransient<PodcastFeedReader>();
builder.Services.AddTransient<YouTubeFeedReader>();
builder.Services.AddTransient<Func<string, IFeedReader>>(provider => name =>
{
var type = Assembly.GetAssembly(typeof(FeedReaderResolver))
.GetType($"FeedReaders.{name}FeedReader");
var instance = provider.GetService(type);
return instance as IFeedReader;
});
}
As the injected object is the Lambda function, FeedReaderHttpTrigger should accept the Lambda function as a dependency. While it’s closely similar to the previous example, it uses the Lambda function this time for dependency injection.
public class FeedReaderHttpTrigger
{
private readonly Func<string, IFeedReader> _func;
public FeedReaderHttpTrigger(Func<string, IFeedReader> func)
{
this._func = func;
}
[FunctionName(nameof(FeedReaderHttpTrigger.GetFeedItemAsync))]
public async Task<IActionResult> GetFeedItemAsync(
[HttpTrigger(AuthorizationLevel.Function, "post", Route = "feeds/item")] HttpRequest req,
ILogger log)
{
var title = this._func("Blog").GetSingleFeedTitle();
return new OkObjectResult(title);
}
}
—
So far, we have discussed five different ways to resolve injected dependencies using the same interface, while building an Azure Functions application. Those five approaches are very similar to each other. Then, which one to choose? Well, there’s no one approach better than the other four, but I guess it would depend purely on the developer’s preference.

Work with hybrid solutions
Streamline hyperconverged management






Recent Comments