This article is contributed. See the original author and article here.
Introduction
This is John Barbare and I am a Sr Customer Engineer at Microsoft focusing on all things in the Cybersecurity space. With my large customer base in the Microsoft Federal space and having to comply with internal security baselines and moving to a cloud-centric platform to manage devices, it is important to know if the baselines/settings will carry over. In this article, I will explain and show how to import an on-premises baseline Group Policy Objects (GPO) into Microsoft Endpoint Manager (MEM) and see the settings that directly carry over and how to create a policy for the ones that are not MDM compliant. With that said, let’s import several baselines and see the correlation from on-premises to MEM mapping and see how we can make the move to the cloud that much easier.
What is Microsoft Security Baselines and/or STIGs?
Security baselines are a group of Microsoft-recommended configuration settings which explain their security impact. These settings are based on feedback from Microsoft security engineering teams, product groups, partners, and customers. Certain Federal agencies and other Department of Defense (DoD) entities have created their own internal and also publicly available baselines or better known as Security Technical Implementation Guides (STIGs). At the end of this article, I will reference several publicly available Federal baselines/STIGs to download and implement in your organization if you are not already using a stringent baseline as of today. If you are a State/Federal/DoD agency and use MEM, feel free to follow along with your tenant as this demo was performed in IL5 before writing this article below in my private Microsoft tenant.
Importing STIGs in Microsoft Endpoint Manager
This article assumes you have enrolled or are going to enroll devices in MEM and we want to check to make sure your tenant status is green on the home page before continuing. Navigate to Microsoft Endpoint Manager and log in with your credentials. Once logged in you will arrive at the home page.
Select “Devices” and then “Group Policy analytics” to land on the policy page to perform the import of the STIGs we are going to analyze. This feature will allow you or your enterprise to analyze your on-premises GPOs and determine the level of MEM support.
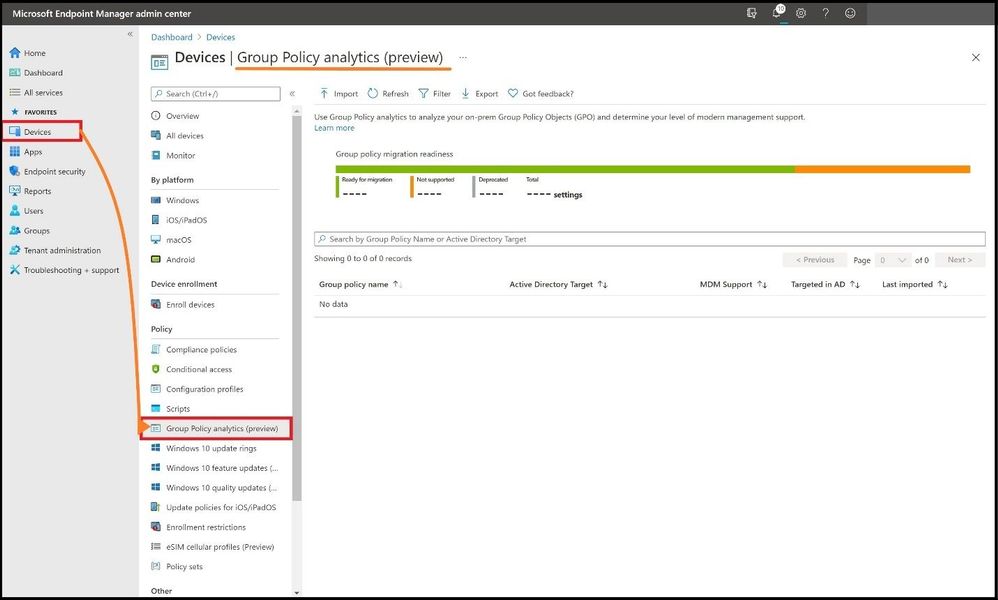 Group Policy Analytics
Group Policy Analytics
I have already downloaded the most current STIGs (Apr 2021) as seen below from the public page of the Department of Defense (DoD) Cyber Exchange hosted by the Defense Information Systems Agency (DISA).
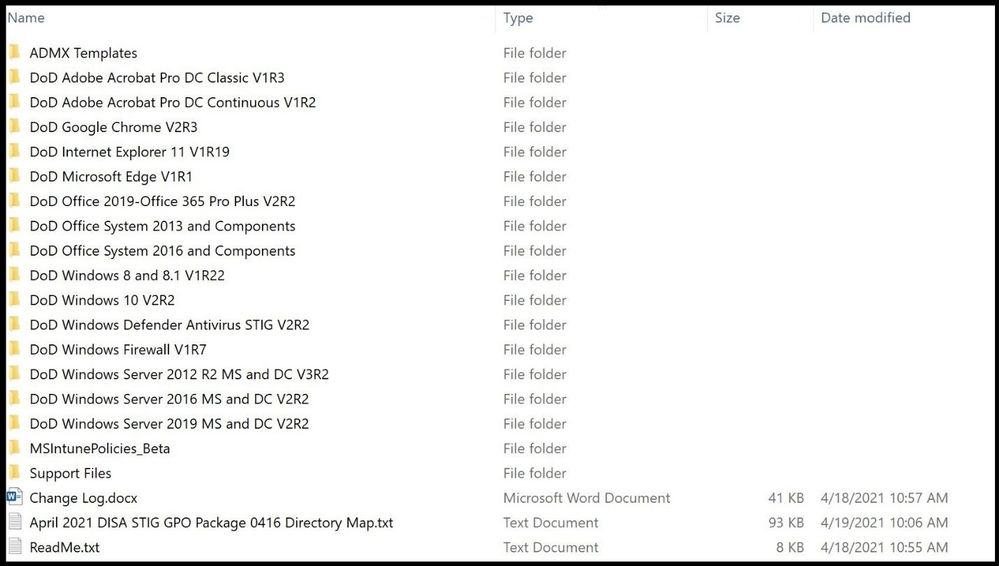 DISA STIGs
DISA STIGs
Next, I will go into the DoD Windows 10 V2R2 folder and locate and confirm the gpreport.xml file is present as we will be using this file for the import. Two GPOs exist in this folder and we will be importing both (User and Computer). I will also go into the DoD Microsoft Edge V1R1 folder and locate and confirm the gpreport.xml file is present as I will also use this file for the import in addition to the other STIGs.
If your enterprise has its own internal STIGs, you would just open GPMC.msc, right-click on the STIGed GPO, and then do a “save report” and name “gpreport” and then selecting “XML” as the output and not HTML. DISA is nice enough to provide the STIGed gpreport.xml file for what we want to accomplish in each folder, so it makes it that much easier.
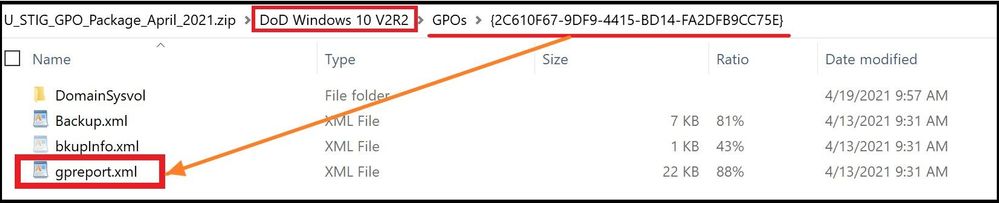 Selecting the gpreport.xml
Selecting the gpreport.xml
Next, we will import the three STIGs in the next several steps.
(Step 1) I will go back to the Group Policy Analytics page in MEM and (step 2) select the import icon at the top. (Step 3) This will bring out the flyout card and I will select the folder icon to import each gpreport.xml. (Step 4) I will locate and select each gpreport.xml in the three folders and (Step 5) select open each time.
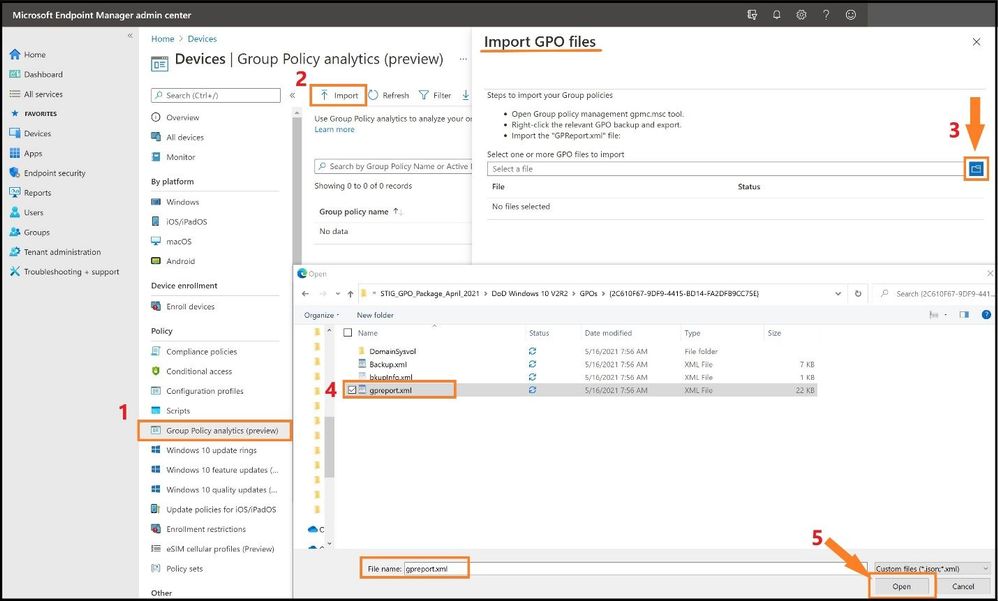 Importing the STIGs
Importing the STIGs
Note: Check the sizes of any GPO XML files that you import (STIGs or any baseline XML file). A single GPO cannot be larger than 750 kB. If the GPO is larger than 750 kB, the import process will fail. Any XML files without the appropriate Unicode ending will also fail the process. See below for failure errors.
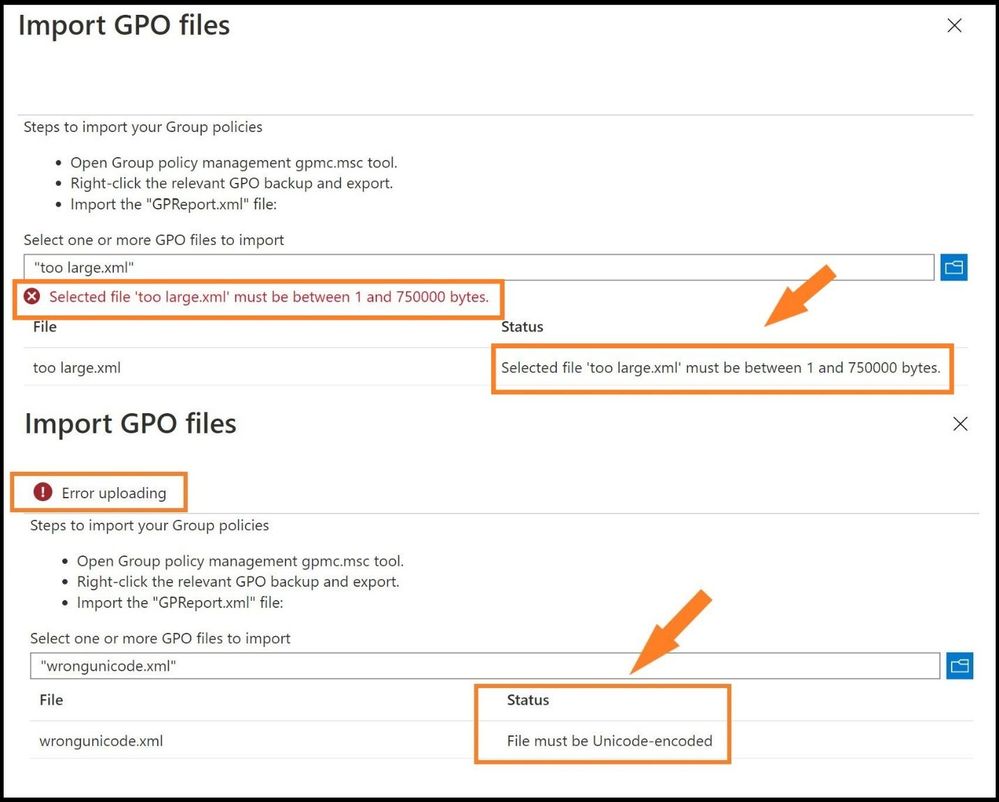 Errors
Errors
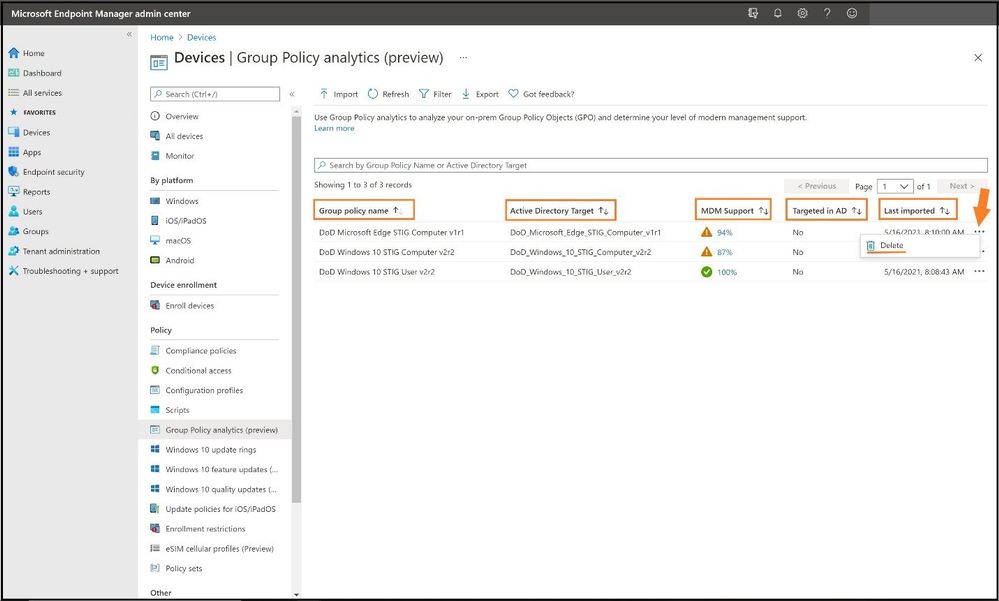
When all three STIGs from the respective GPO folders I targeted are successfully imported, it will list the following information:
- Group Policy name: This name is automatically generated using the information inside the GPO.
- Active Directory Target: The target is automatically generated using the organizational unit (OU) target information in inside the GPO.
- MDM Support: Displays the percentage of group policy settings in the GPO that has the same setting in MEM.
- Targeted in AD: Yes, means the GPO is linked to an OU in on-premises group policy. No means the GPO is not linked to an on-premises OU.
- Last imported: Shows the date/time stamp of the last import.
- Delete: Three dots on the end to delete the imported GPO (RBAC dependent).
 After Importing the STOGs
After Importing the STOGs
As one can see, all three STIGs were successfully imported in MEM Group Policy analytics showing the percentage of MDM support. Next, we will have to see what STIG settings do not have MDM support and then add them in.
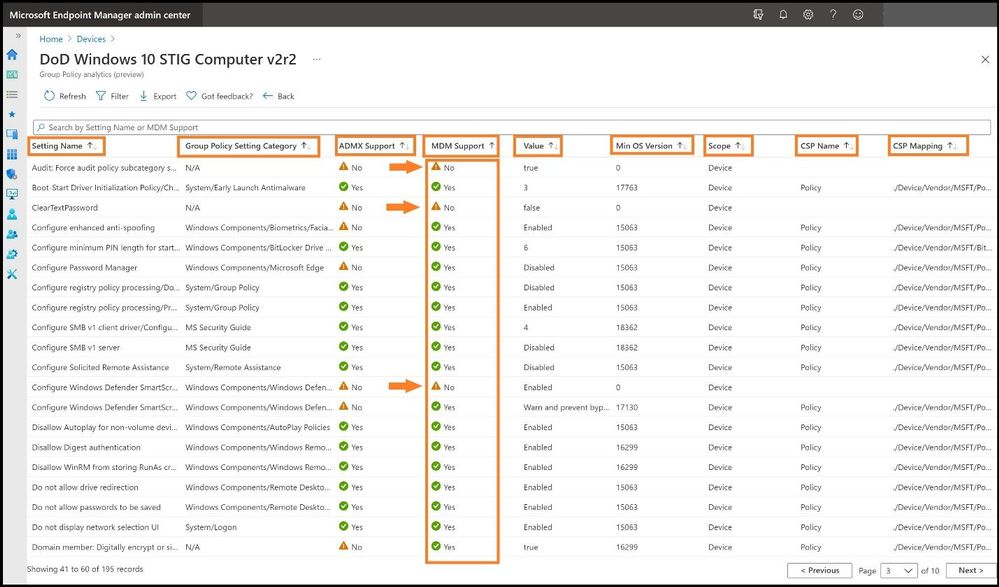
We will select the second STIG, DoD Windows 10 STIG Computer v2r2, by clicking on the blue 87% under MDM Support. This will show which STIGs are mapped and which are not and more detail about each GPO. The details will display the following:
- Setting Name: The name is automatically generated using the information in the GPO setting.
- Group Policy Setting Category: This shows the setting category for ADMX settings, such as Internet Explorer and Microsoft Edge. Not all settings have a setting category.
- ADMX Support: Yes, means there is an ADMX template for this setting. No means there is not an ADMX template for the specific setting.
- MDM Support: Yes, means there is a matching setting available in Endpoint Manager. You can configure this setting in a device configuration profile. Settings in device configuration profiles are mapped to Windows CSPs. No means there is not a matching setting available to MDM providers, including Intune.
- Value: This shows the value imported from the GPO. It shows different values, true, false, enabled, disabled, etc.
- Scope: This shows if the imported GPO targets users or targets devices.
- Min OS Version: This shows the minimum Windows OS version build numbers that the GPO setting applies. It may show 18362 (1903), 17130 (1803), and other Windows 10 versions. For example, if a policy setting shows 18362, then the setting supports build 18362 and newer builds.
- CSP Name: A Configuration Service Provider (CSP) exposes device configuration settings in Windows 10. This column shows the CSP that includes the setting. For example, you may see Policy, BitLocker, PassportforWork, etc.
- CSP Mapping: This shows the OMA-URI path for the on-premises policy. You can relate this to the MDM version of GPOs.
 STIGs and MDM Support
STIGs and MDM Support
Under the MDM support column, we can see several that are not mapped in MEM/no MDM support. To add these into MEM, we need to create a custom configuration profile.
Creating a Custom Configuration Profile for Non-Mapped STIGed GPOs
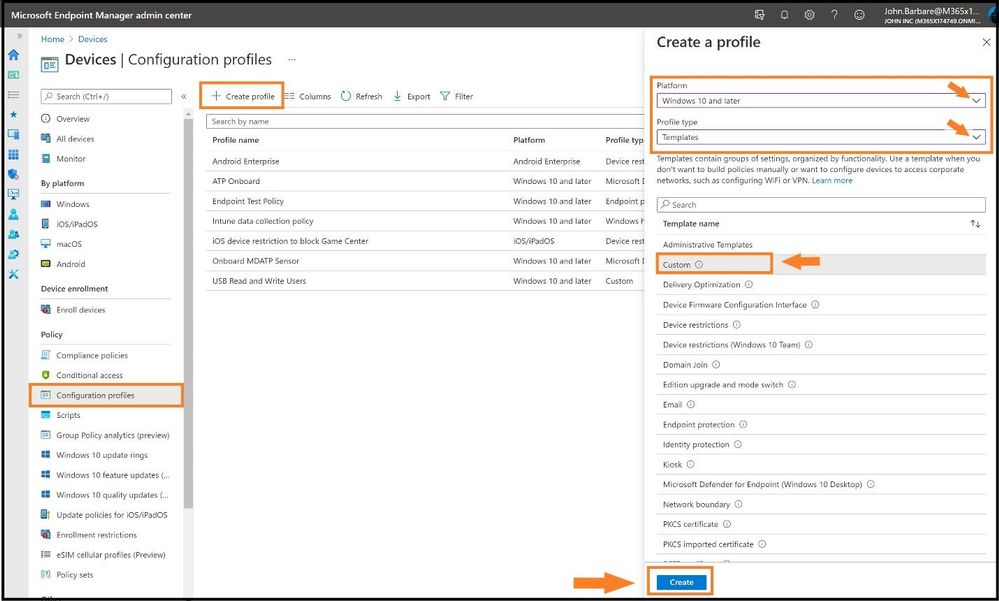
After you have created the direct mapping of all the STIGed GPOs in a Configuration policy, you will need to create a custom policy for the ones that did not match or either do not have MDM support.
Select Configuration profiles, Create a profile, and for Platform select Windows 10 and later. For profile type, we will select Templates and choose Custom from the list and select create.
 Creating a Custom Profile
Creating a Custom Profile
This will bring us to the custom policy page to create the policy so we can map the STIG to MEM/MDM. Go ahead create a name for the policy and select next. For Configuration settings, select Add, and then we will need to fill in the appropriate information for the policy. The name and description should be the policy you are creating. Next, we need to find the correct OMA-URI path and data type as this must match perfectly or it will not map.
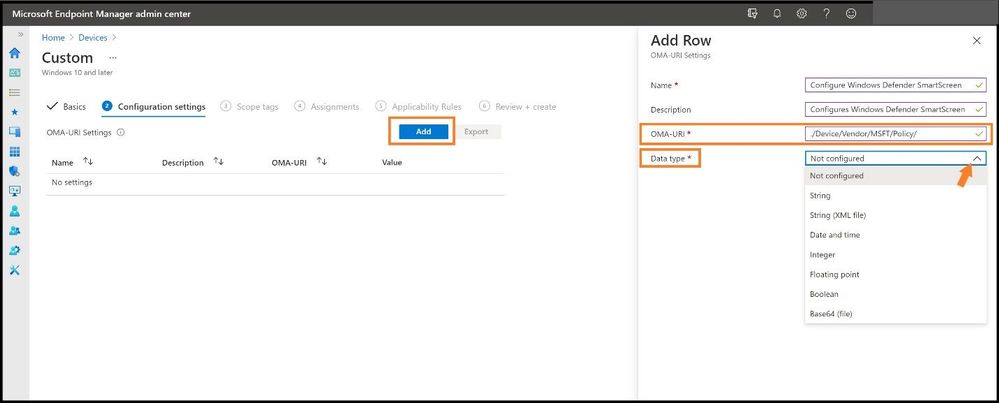 Selecting the Data Type
Selecting the Data Type
To find the OMA-URI path to map, you will need to use the Policy configuration service provider page from Microsoft Docs to find the setting for the path. Since this a Windows 10 policy, it will start with ./Device/Vendor/MSFT/Policy/Config/ but we will need the path after the Config/. After we go to the link, we search for the setting for “Windows Defender SmartScreen” and we can find the rest of the path as seen below. The full value for the OMA-URI path will be:
./Device/Vendor/MSFT/Policy/Config/SmartScreen/EnableSmartScreenInShell
Down at the bottom, we have values of 0 and 1 and this tells me this will be an integer value for the Data Type drop-down menu and we use 1 as the value.
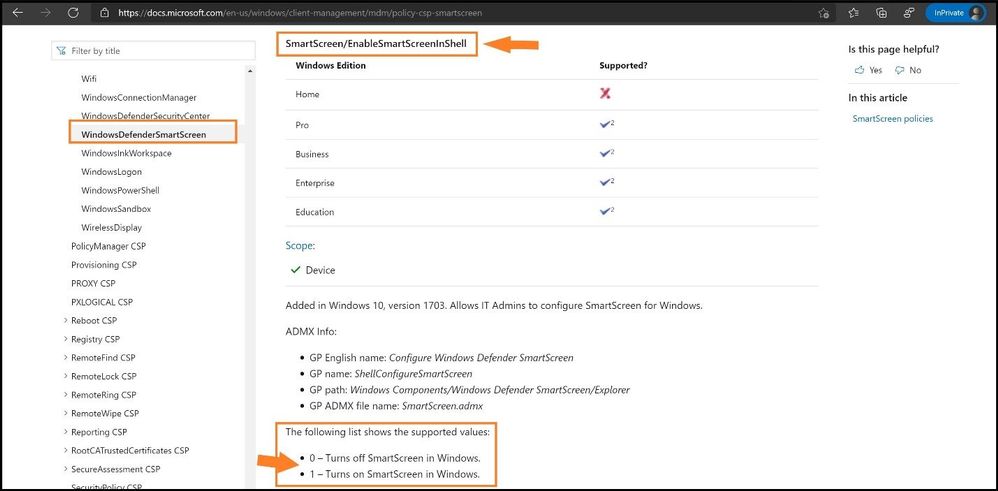 Finding the path on Microsoft Docs
Finding the path on Microsoft Docs
With these pieces of information, we can apply these values found from the docs page into the correct settings as seen below.
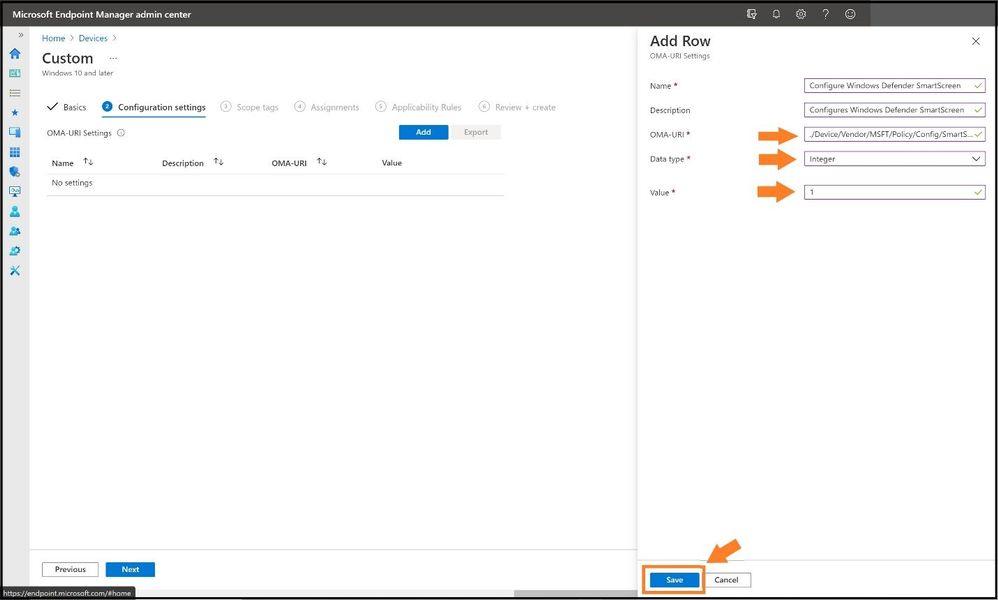 Confirming the Rows
Confirming the Rows
Go ahead and select save and then continue to add more for the ones that are not MDM compliant by selecting add again. When finished, it will display a list after you have added the ones needed and also to confirm. Go ahead and select next.
Select the groups you want the policy to apply to and select next.
 Selecting the Assignments for the Policy
Selecting the Assignments for the Policy
Select any custom Applicability Rules to apply the policy and select next. Review and then create the policy to apply.
 Selecting any Applicability Rules
Selecting any Applicability Rules
What About Conflicting Settings in MEM from STIGed GPOs? Who Wins?
If anyone has applied multiple STIGs on top of other GPOs or other baselines (I have a customer that uses three STIGs), the big question I always get is “who wins?” Is it the first baseline policy I created or the strongest GPO setting that will win once everything is synced? Let’s go ahead a make sure that does not happen and create a policy that is called “ControlPolicyConflict policies” or “ControlPolicyConflict/MDMWinsOverGP.” This feature was added in Windows 10, version 1803 and allows the IT admin to control which policy will be used whenever both the MDM policy and its equivalent GPO are set on the device. MDMWinsOverGP only applies to policies in Policy CSP. MDM policies win over Group Policies where applicable; not all Group Policies are available via MDM or CSP. It does not apply to other MDM settings with equivalent Group Policy settings that are defined in other CSPs. This policy is used to ensure that MDM policy wins over Group Policy when the policy is configured on the MDM channel. The default value is 0. The MDM policies in Policy CSP will behave as described if this policy value is set 1. This policy does not support the Delete command and does not support setting the value to 0 again after it was previously set to 1. In Windows 10 version 1809 it will support using the Delete command to set the value to 0 again if it was previously set to 1.
You would perform the same steps as above to create a custom configuration profile as seen below. Select Configuration profiles, Create a profile, and for Platform select Windows 10 and later. For profile type, we will select Templates and choose Custom from the list and select create.
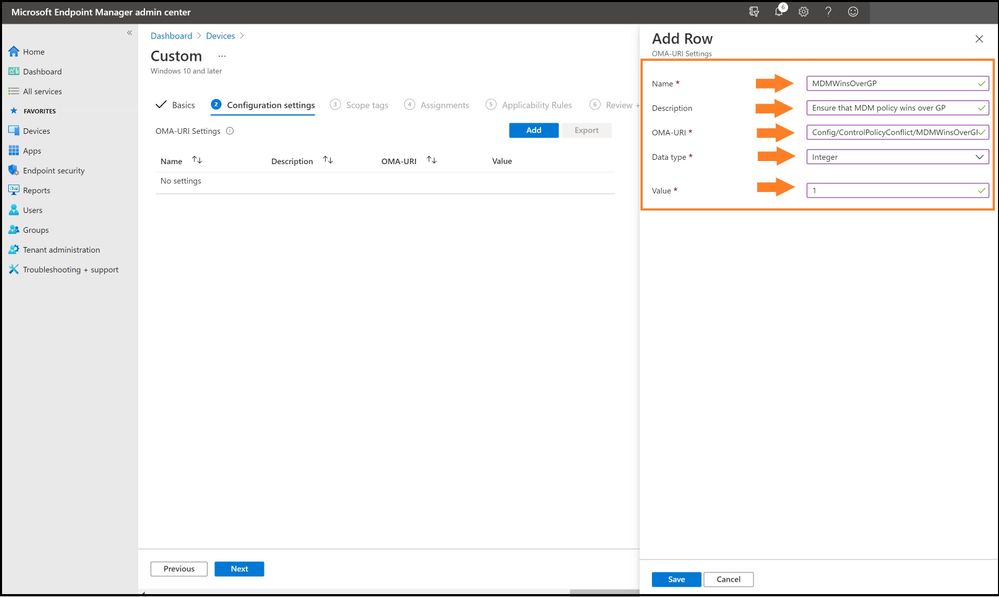
For the configuration settings, use the below values:
Name: MDMWinsOverGP
Description: Ensure that MDM policy wins over GP
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP
Data Type: Integer
Value: 1
 MDMWinsOverGP
MDMWinsOverGP
And for a close-up view:
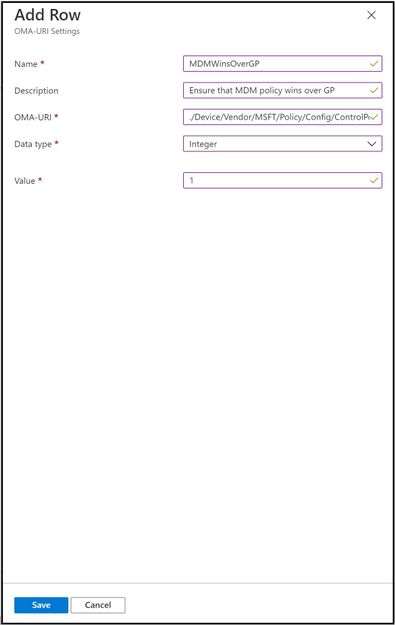
STIGed GPO Migration Report for MEM
With importing all the STIGs and seeing what we can migrate from on-premises, every IT Manager needs a report that will determine the status of the policies for your journey to the cloud. Select reports and then Group policy analytics.
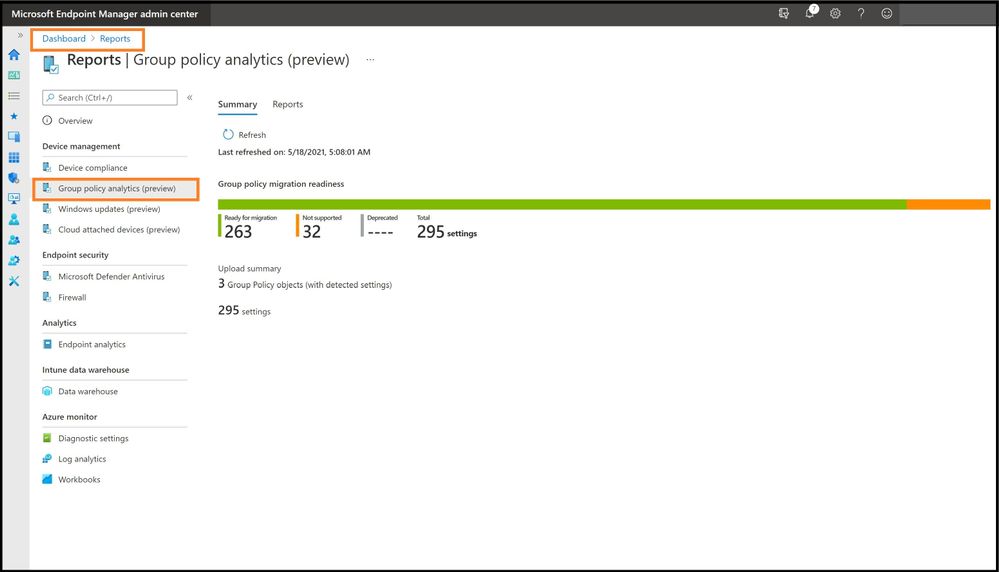 STIGed GPO Migration Report for MEM
STIGed GPO Migration Report for MEM
Select the reports tab next to the summary to see a more detailed report about the readiness of your Group Policy for modern management. Export out the results for planning purposes or to send to a certain IT Team.
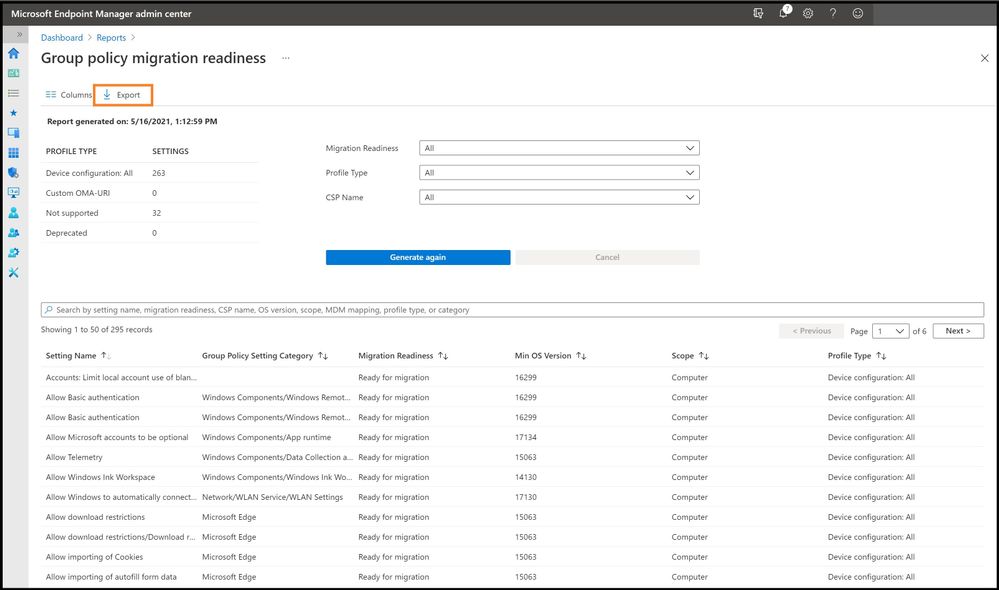 Export the Report
Export the Report
Conclusion
Thanks for taking the time to read this article and I hope you better understand the new Group Policy analytics in MEM as you use this function in your enterprise or in any Government IL5 tenant. Using the new Group Policy analytics will further show the value for any IT Manager the value of seeing what STIGs can be brought over, the mapping, and then create custom policies for the ones that are not MDM. Then finally, seeing how MEM battles the age-old question of which STIG/GPO wins for the finale! Hope to see you in the next blog and always protect your endpoints! STIG away!
Thanks for reading and have a great Cybersecurity day!
Follow my Microsoft Security Blogs: http://aka.ms/JohnBarbare and also on LinkedIn.
References
CIS Microsoft Windows Desktop Benchmarks – Center for Internet Security (CIS)
Defense Information Systems Agency Security Technical Implementation Guide
Group Policy Objects – DoD Cyber Exchange
Policy CSP – ControlPolicyConflict – Windows Client Management | Microsoft Docs
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments