This article is contributed. See the original author and article here.
In previous blog posts, we described how you can deploy SOC Prime TDM Azure Sentinel rules directly to your workspace or even multiple workspaces. This new promo from SOC prime enables you to do that for SOC Prime free content and select premium Azure Sentinel rules and playbooks available for free exclusively to Azure Sentinel users.
About SOC Prime and the Threat Detection Marketplace (TDM)
Improve what you have, not Replace. SOC Prime helps to centrally source and support SIEM content to
maximize the value of existing security investments. SOC Prime Threat Detection Marketplace (TDM) is
the first in the world SIEM agnostic Threat Detection Marketplace. TDM contains SOC ready dashboards, rule packages, and automation playbooks. The content is updated daily to cover emerging threats and allows automated deployment to your SIEM. The thousands of content items are mapped directly to MITRE ATT&CK methodology, allowing you to extend your MITRE ATT&CK coverage.
More information at https://www.socprime.com
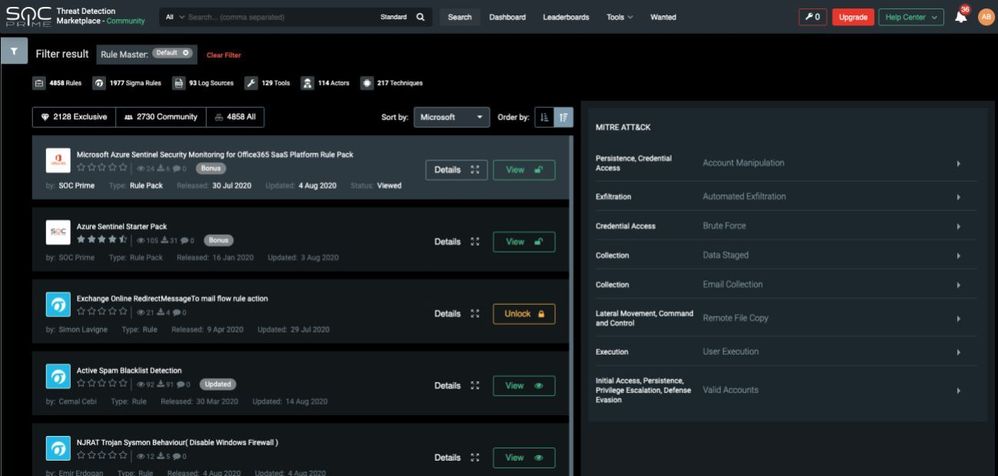
Promotion overview
SOC Prime offers a promotion which enables extended community access to SOC Prime Threat
Detection Marketplace (TDM), which includes, in addition to regular community benefits:
- A bonus Office365 security rule pack
- A bonus Azure Sentinel starter rule pack
- A selection of Azure Sentinel Playbooks
- Capability to deploy those and other free rules directly from TDM to an Azure Sentinel instance.
The bonus content, generally available only for paid SOC Prime TDM subscribers, can be used by Azure Sentinel clients and prospects for free as part of the promotion and can be kept free of charge after the PoC.
When using the promo code, your TDM Rule Master, used to customize your TDM environment, is predefined to highlight Azure Sentinel and Microsoft Defender ATP content.
Naturally, you can also use TDM free content in addition to the content available as part of the promotion, open to any TDM community member, in areas such as:
- Proactive exploit detection, providing immediate response to newly published exploits.
- Detection rules to ensure MITRE ATT&CK coverage.
- Cloud security monitoring and Microsoft Active Directory Monitoring, complementing your CASB
- and EDR solution, respectively.
- Playbooks to automate your response.
Getting the promotion
To get the promotion, when registering to the SOC prime TDM, use the following link to access the TDM Sign Up page: https://tdm.socprime.com/login/?promo=TDM-Microsoft-Promo-2020. The sign-up page will already be populated with the needed promo code:
Alternatively, go to SOC Prime TDM Sign Up page and use the promo code ‘TDM-Microsoft-Promo-2020’ by clicking on the ‘Have a Promo Code’ link:
If your organization already has a TDM account, contact SOC prime to check if you are eligible to the
promotion.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments