This article is contributed. See the original author and article here.
One of the huge advantages of using Microsoft Defender for Identity to help protect your on-premises identities from advanced attacks, is that new detections, features and improvements are being added all the time. After some recent updates, we thought that we’d take some time to properly introduce one of these new detections and give it the attention it deserves!
The alert in today’s update covers a notorious attack method that was requested by many of our customers and security partners. It addresses an attack technique that we’ve seen become more and more popular – AS-REP Roasting.
What is AS-REP Roasting?
In short, AS-REP Roasting is an attack against Kerberos that targets users that do not require Kerberos pre-authentication.
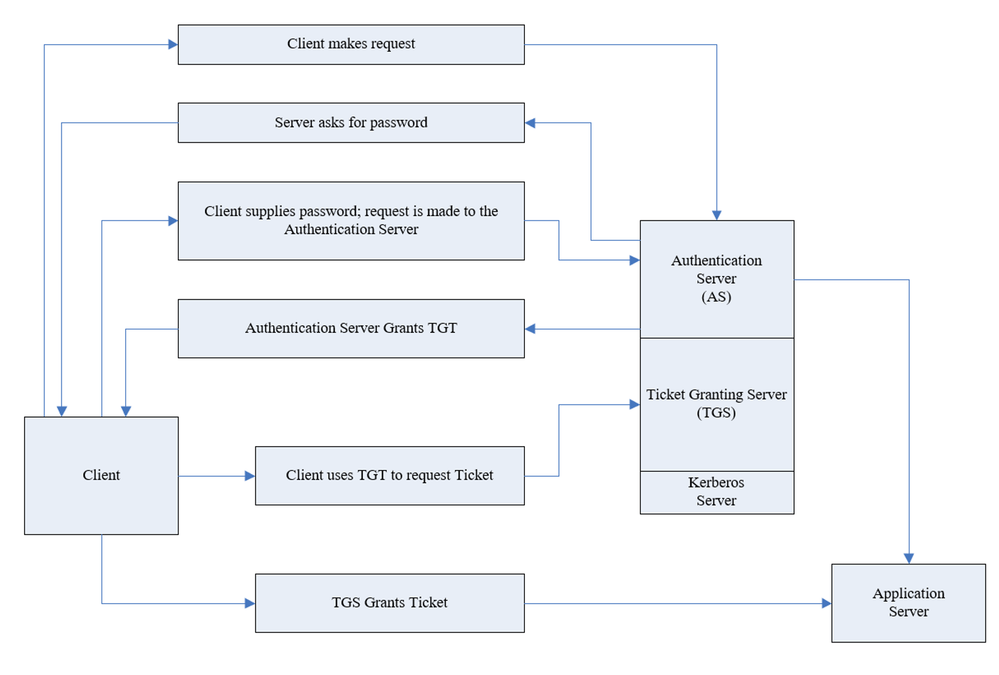
To understand what AS-REP Roasting is, we need to start with simple explanation about what Kerberos is and how it works.
Kerberos is authentication protocol that works based on tickets and this is its basic flow:
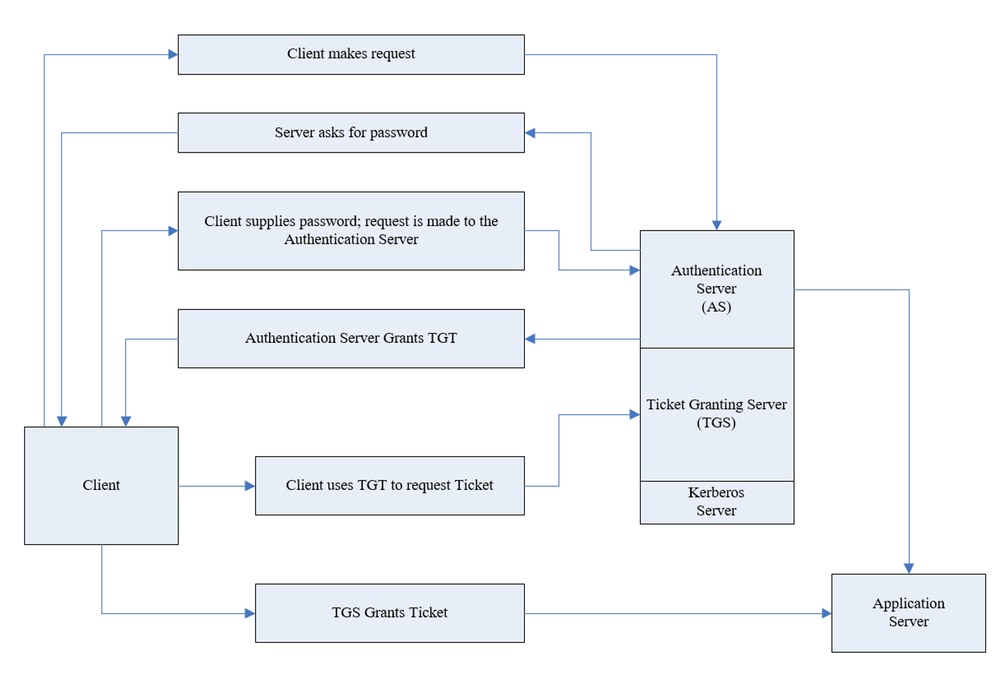
As part of the authentication request sent (AS-REQ), the user will provide their password that encrypts the timestamp. The domain controller will attempt to decrypt it and validate that the right password was used. If the request is granted, the user will be issued with a ticket-granting ticket (TGT) that will be used for future authentication. However, there is an attribute in Active Directory that facilitates disabling pre-authentication for users in the organization. Although this attribute is required by default in Active directory, this can be changed freely.
The typical attack vector in this scenario is to enumerate users that have the attribute turned off and then ask for TGT for these users. The TGT allows a potential attack to crack the password offline.
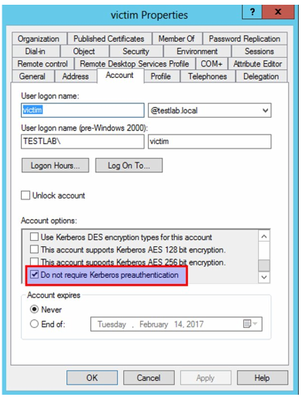
Covering all of the bases…
Microsoft Defender for Identity can help protect against these kinds of threats in different ways. Let’s dive in to each of these approaches:
Prevention
Defender for Identity allows you to pre-emptively protect against this kind of method using our Security Assessments. If you are not familiar with our security assessments, check out our docs pages for a summary of how you can help prevent threats before they happen.
In short, Defender for Identity offers proactive identity security posture assessments to detect misconfigurations or legacy settings that may not have been reviewed in a long time. Suggested improvement actions are then given to bolster your identity posture across your on-premises Active Directory. One of these assessments is “Unsecure account attributes”. This assessment continuously monitors your environment to identify accounts with attribute values that expose a security risk – including Kerberos pre-authentication. Click here to learn more about this assessment
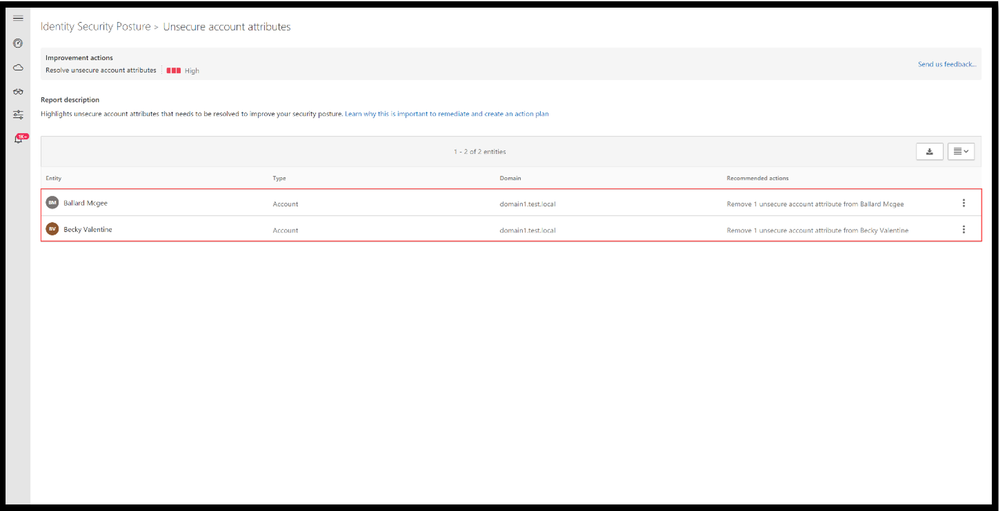
Detections
Aside from the preventative nature of the assessments that have been covered above, we offer two detections to help identify this type of attack – 1) the reconnaissance phase and 2) the actual ticket granting ask for future brute force usage.
The reconnaissance portion often involves the attacker preforming enumeration techniques to find users that have the pre-authentication attribute turned off. If the reconnaissance was performed with LDAP it will result in triggering Active Directory attributes reconnaissance (LDAP) alert. This alert triggers when certain attributes are enumerated.
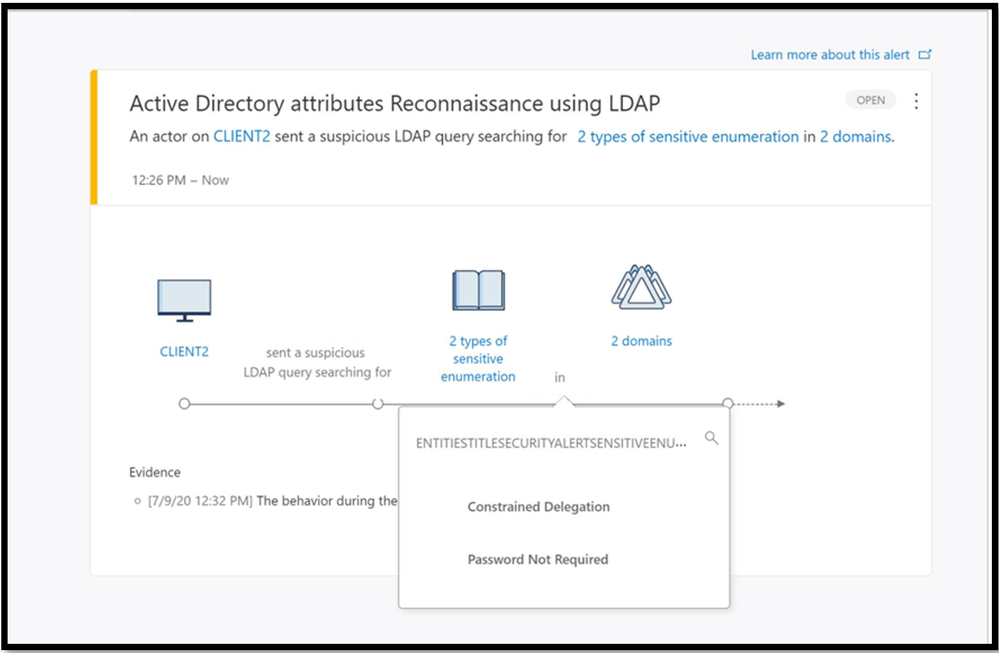
The new detection we are announcing today, Suspected AS-REP Roasting attack helps identify AS-REQ messages without encrypted timestamps and AS-REP messages with TGT data.
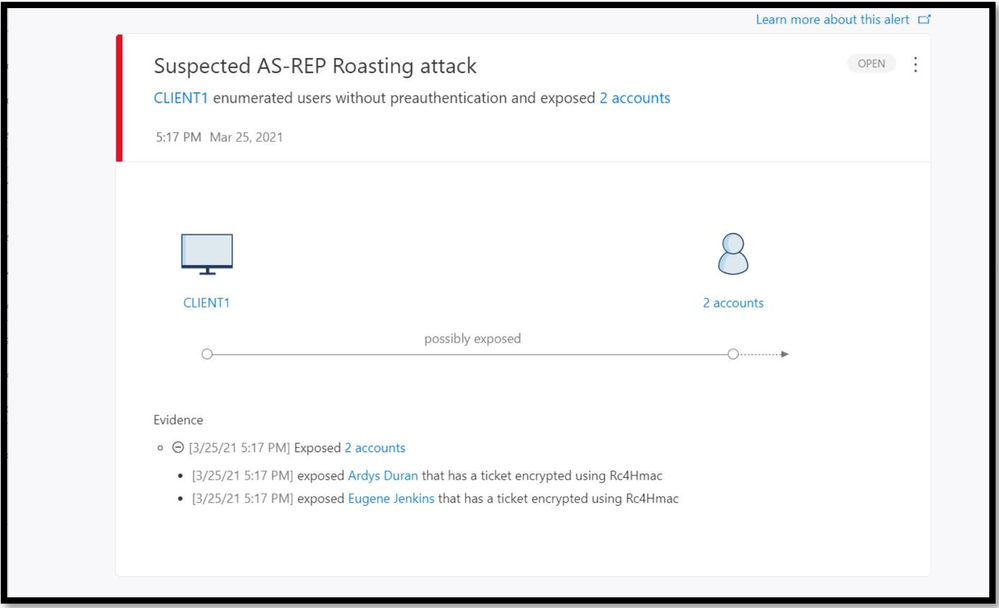
This comprehensive protection against AS-REP roasting style attacks will be available in Defender for Identity starting from version 2.141. Try it out for yourselves, and as always, we’d love to hear your feedback on this new feature.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments