This article is contributed. See the original author and article here.
Microsoft’s Azure Sentinel now provides a Timeline view within the Incident where alerts now display remediation steps. The list of alerts that have remediations provided by Microsoft will continue to grow. As you can see in the graphic below, one or more remediation steps are contained in each alert. These remediation steps tell you what to do with the alert or Incident in question.
However, what if you want to have your own steps, or what if you have alerts without any remediation steps?
Now available to address this is the Get-SOCActions Playbook found in GitHub (Azure-Sentinel/Playbooks/Get-SOCActions at master · Azure/Azure-Sentinel (github.com)). This playbook uses a .csv file uploaded your Azure Sentinel instance, as a Watchlist containing the steps your organization wants an analyst to take to remediate the Incident they are triaging. More on this in a minute.
Below is an example of a provided Remediation from one of the Alerts:
Example Remediation Steps Provided by Microsoft
- Enforce the use of strong passwords and do not re-use them across multiple resources and services
- In case this is an Azure Virtual Machine, set up an NSG allow list of only expected IP addresses or ranges. (see https://azure.microsoft.com/en-us/documentation/articles/virtual-networks-nsg/)
- In case this is an Azure Virtual Machine, lock down access to it using network JIT (see https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time)
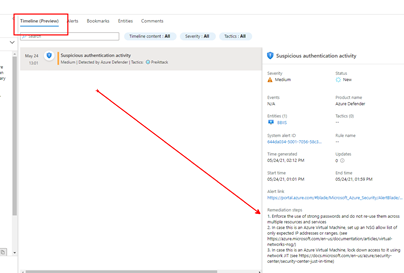
Remediation steps were added to the Timeline View recently in Azure Sentinel, as shown above
We highly encourage you to look at the SOC Process Framework blog, Playbook and the amazing Workbook; you may have already noticed the SocRA Watchlist which was called out in that article, it is a .csv file that Rin published, and is the template you need to build your own steps (or just use the enhanced ones provided by Rin).
It’s this .csv file that creates the Watchlist that forms the basis of enhancing your SOC process for remediation, its used in the Workbook and Playbook. The .csv file has been used as it’s an easy to edit format (in Excel or Notepad etc…), you just need to amend the rows or even add your own rows and columns for new Alerts or steps you would like. There are columns called A1, A2 etc… these are essentially Answer1 (Step1), Answer 2(Step2) etc…
Example of a new Alert that has been added.
You can also in the last column add a DATE (of when the line in the watchlist was updated). Note that any URL link will appear its own column in the [Incident Overview] workbook – we parse the string so it can be part of a longer line of text in any of the columns headed A1 thru A19 (you can add more answers if required, just inset more columns named A20, A21 etc…after column A19). Just remember to save your work as a .CSV.
How to install the Watchlist file
You must download the Watchlist file (then edit as required) it’s called SOCAnalystActionsByAlert.csv (https://github.com/Azure/Azure-Sentinel/blob/master/docs/SOCAnalystActionsByAlert.csv)
Then when you name the Watchlist, our suggestion is “SOC Recommended Actions”, make sure you set the ‘Alias’ to: SocRA
Important: SocRA is case sensitive, you need an uppercase S, R and A.
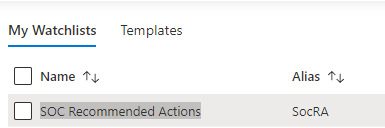
You should now have entries in Log Analytics for the SocRA alias.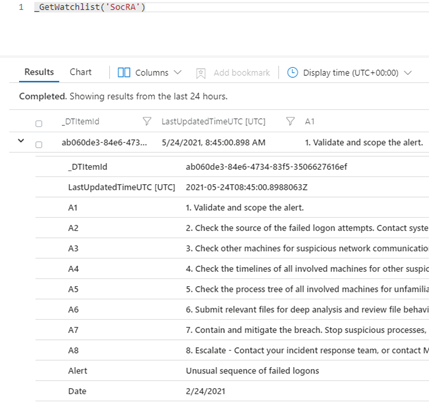
The SocRA watchlist .csv file serves both the Incident Overview Workbook and supports the Get-SOCActions Playbook, should you want to push Recommended Actions to the Comments section of the Incident your Analyst is working on. You will want to keep this in mind when you edit the SocRA watchlist. The Get-SOCActions Playbook leverages the formatting of the SocRA watchlist, i.e. A1 – A19, Alert, Date when querying the watchlist for Actions. If the alert is not found, or has not been onboarded, the Playbook then defaults to a set of questions pulled from the SOC Process Framework Workbook to help the analyst triage the alert & Incident.
Important – Should you decide to add more steps to the watchlist .csv file beyond A1-A19 you will need to edit the Playbooks conditions to include the additional step(s) you added both in the JSON response, the KQL query, and the variable HTML formatting prior to committing the steps to the Incidents Comments section.
Incident Overview Workbook
To make Investigation easier, we have integrated the above Watchlist with the default “Investigation Overview” Workbook you see, just simply click on the normal link from within the Incident blade:
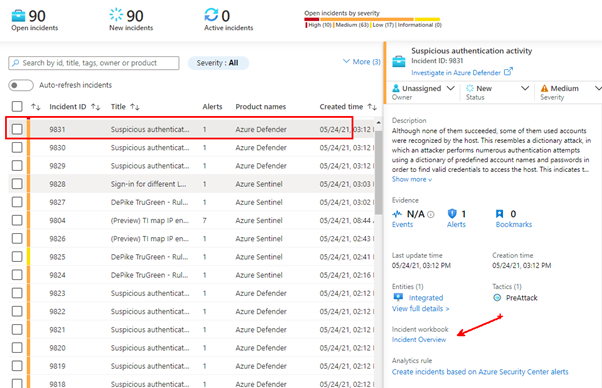
This will still open Workbook as usual. Whist I was making changes, I have also colour coded the alert status and severity fields (Red, Amber and Green), just to make them stand out a little, and Blue for new alerts.
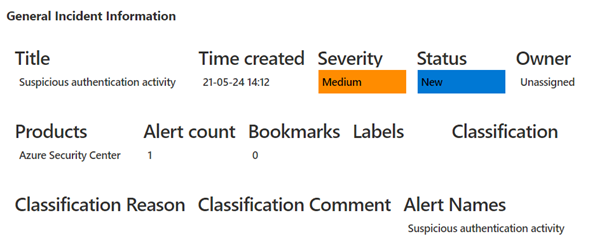
If an alert has NO remediations, nothing will be visible in the workbook. However, if the alert has a remediation and there is no Watchlist called: SocRA then you will be able to expand the menu that will appear:
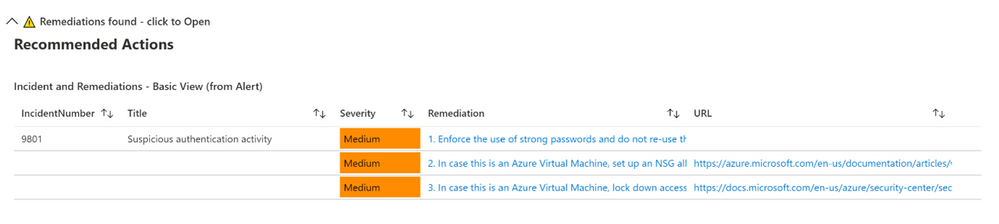
This will show the default or basic remediations that the alert has, in this example there are 3 remediation steps shown.
If you have the SocRA watchlist installed, then you will see that data shown instead (as the Watchlist is the authoritative source, rather than the steps in the alert). In this example there is a 4th step (A4) shown, which is specific to the Watchlist and the specific alert called “Suspicious authentication activity”.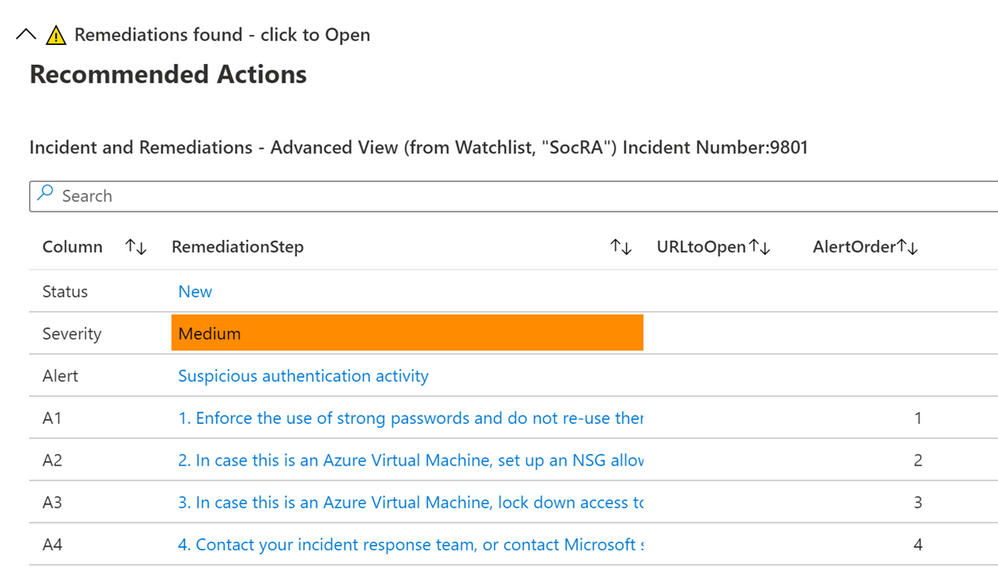
Conclusion
In conclusion, these Workbooks, the Playbook, and Watchlist all work together in concert to provide you with a customized solution to creating remediation steps that are tailored to a specific line of business. As you on-board custom analytics/detections that are pertinent to your business, you will have actions you will want an analyst to take and this solution provides a mechanism for delivering the right actions per analytic/use-case.
Thanks for reading!
We hope you found the details of this article interesting. Thanks Clive Watson and Rin Ure for writing this Article and creating the content for this solution.
And a special thanks to Sarah Young and Liat Lisha for helping us to deploy this solution.
Links
Content | Link |
SOC process Framework Wiki SOC Process Framework · Azure/Azure-Sentinel Wiki (github.com)
Main SOC Process Framework Blog, author Rin Ure | |
SOC Process Framework Workbook, author Rin Ure | https://github.com/Azure/Azure-Sentinel/blob/master/Workbooks/SOCProcessFramework.json |
Incident Overview Workbook, amended by Clive Watson for remediation and watchlist integration | https://github.com/Azure/Azure-Sentinel/blob/master/Workbooks/IncidentOverview.json |
Watchlist, author Rin Ure | https://github.com/Azure/Azure-Sentinel/blob/master/docs/SOCAnalystActionsByAlert.csv |
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.



Recent Comments