This article is contributed. See the original author and article here.
Hi all, Alan here again with a new article, I’m a Customer Engineer from Italy on Identity and Security.
I want to show you how to block TOR browser using Cloud App Security, simple and fast!
During the last few months, I had several customers requesting how to block sign-in from anonymous Ip Addresses. One example would be someone using TOR Browser. I started playing around with CAS and finally found a quick solution. Continue reading to find out more.
We will use Azure AD “Conditional Access policy” with Session Control together with “Cloud App Security Conditional Access App Control”.
We will start creating a “special” Azure AD Condition Access policy that will enable the APP in CAS, let’s see how.
PS: the APP will appear in Cloud App Security Conditional Access App Control directly after the user start authenticating/using it.
You will need access to you tenant’s Azure AD (portal.azure.com) and Cloud App Security (mycompany. portal.cloudappsecurity.com).
Thirst thing to do is create an Azure AD Conditional Access policy:
1. Navigate to your Azure Active Directory
2. Under Manage click on Security
3. Click on Conditional Access
4. Select New Policy
5. Give it a Name
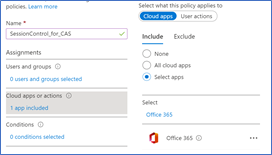
6. Select to which users it will apply
7. Select the cloud application, for this demo I will select Office 365
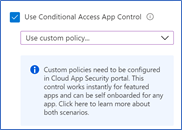
8. Go to Session and select Use Conditional Access App Control
9. Select Use Custom Policy
10. Click Select
11. Enable the policy and click Create
Once this is done the first time users log in Office 365 suite the application will be integrated in Cloud App Security
Open Cloud App Security portal : https://mycompany. portal.cloudappsecurity.com
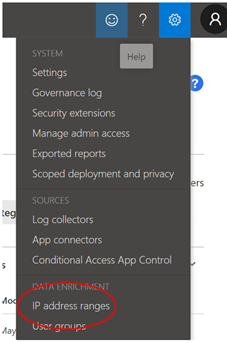
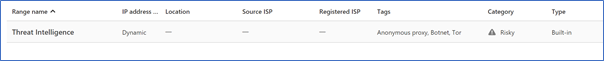
On the top right side you have the configuration wheel, click and select “IP Address ranges” as shown below
One interesting thing is that if you filter for one of the following Tags “Tor, Anonymous Proxy or Botnet” you will see it matches the following rule
CAS has the “intelligence” to know which are these suspicious IP Addresses or networks
Here some other details Create anomaly detection policies in Cloud App Security | Microsoft Docs
- Activity from anonymous IP addresses
- Activity from suspicious IP addresses, Botnet C&C
- Activity from a TOR IP address
Back to our Connected Apps:
1. Go to Connected Apps
2. In the central pane you will have three tabs, select “Conditional Access App Control apps”.
You will get a list of applications for which you can start creating CAS policies
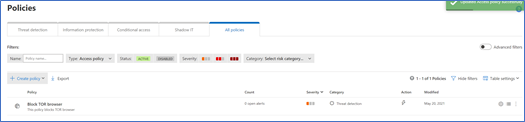
3. Now browse to Control menu and select “Policies”
4. Select “ + Create policy”
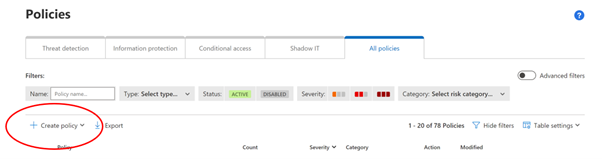
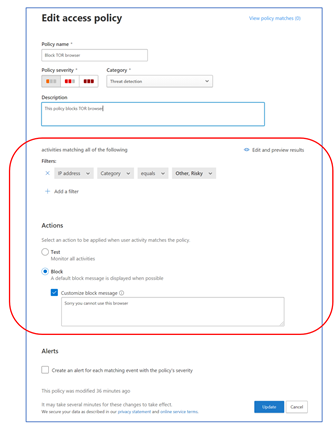
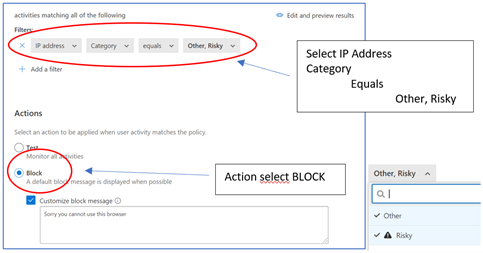
The important part here is FILTERS and ACTIONS
5. Click on “Create” (you will see it listed)
Access Office portal from the TOR Browser (use a valid user account from your Azure AD)
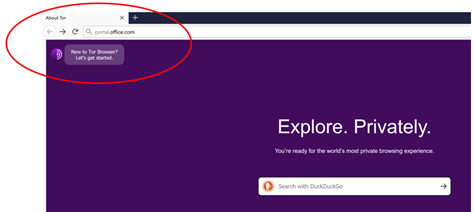
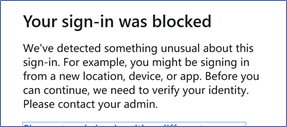 GREAT!!
GREAT!!
Hope this article gives some hints on how to use Cloud App Security which I think is a great tool, simple and powerful and can really help enhance your security posture.
Regards
Alan @CE
Customer Engineer – Microsoft Italy
Useful Resources:
Zero Trust Maturity Assessment Tool | Microsoft Security
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.





Recent Comments