by Scott Muniz | Sep 3, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Microsoft Ignite 2020 is launching as a free, 48-hour digital event this year (shifting from a week-long, in-person event as it had been in the past). With Ignite going all-digital, it now will now be split into two global events, the first is September 22-24 and the second in early 2021.
With registration now open, I encourage you to register to connect with the Azure SQL/ SQL Server experts as well as other technology professionals from around the world. Sessions will be delivered in 3 time zones (Americas, Asia, Europe) so you’ll have an opportunity to learn from your favorite speakers no matter where you are in the world!
More details about the events, including session times/dates are being updated online as it gets closer to show time, but below I’ve listed the sessions you can expect from the Azure Data team:
Rap with Rohan
Join Rohan Kumar, Corporate Vice President of Azure Data Engineering, for his “ask me anything” session covering all things Data & AI. Interview with Anna Hoffman.
Speakers: Rohan Kumar, Anna Hoffman
Deep dive in Azure SQL: What to use when and updates from the Product Group
Come learn about the latest capabilities in the Azure SQL family (VM, SQL Managed Instance, SQL Database) in the past year, along with the latest “game changers” that Azure SQL brings to the table for organizations, including hyperscale, serverless, intelligence, and more.
Speaker: Ajay Jagannathan
Enjoy 3 Digital Breakouts
Attend “Ask the Experts” after you virtually attending digital breakouts. You can connect with product teams, feature teams, community experts, and advocacy teams directly and get your questions answered live!
Migrate, Modernize .NET applications on Azure
Learn how to modernize .NET Framework Apps, by migrating to App Service or porting to .NET core on Azure. We’ll cover the latest product updates, new options for networking, and increased performance.
Speaker: Venkata Raj Pochiraju
Building a Hybrid data platform with Azure Arc enabled data services
Azure Arc extends Azure’s management services and other Azure data services like Azure SQL Managed Instance and PostgreSQL Hyperscale to run anywhere – on your on-premises datacenter, on the edge, or even on other public clouds. This session will update you on the latest hybrid innovations on data with Azure Arc enabled data services.
Speaker: Travis Wright
Running real-time data analytics on the edge with Azure SQL Edge
Azure SQL Edge has taken the same SQL database engine you already know, and optimized it for the Edge and IoT Workloads. With a small resource footprint and built-in capabilities, like data streaming, time series, and Machine Learning discover how Microsoft is creating the ability to “develop once, deploy anywhere” with its database offering at the Edge. This session explores popular customer implementations with Azure SQL Edge, along with new product features for the Intelligent Edge.
Speaker: Vasiya Krishnan
Looking forward to seeing you there! Tweet us at @AzureSQL for sessions you are most excited about.
by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
General News
Microsoft Security | Fall 2020 Public Webinars edition
Microsoft Security: What cybersecurity skills do I need to become a CISO?
Microsoft Security: How to cultivate a diverse cybersecurity team
Securing MEM at Microsoft
Rethinking IoT/OT Security to Mitigate Cyberthreats
How do I implement a Zero Trust security model for my Microsoft remote workforce?
New data from Microsoft shows how the pandemic is accelerating the digital transformation of cyber-security
Zero Trust: From security option to business imperative overnight
How to organize your security team: The evolution of cybersecurity roles and responsibilities
Afternoon Cyber Tea: Revisiting social engineering: The human threat to cybersecurity
How Microsoft Mission Critical team helped secure AAD
Microsoft joins Open Source Security Foundation
Azure Security & Compliance News
Become an Azure Security Center Ninja
Automation to Block Brute-force Attacked IP detected by Azure Security Center
Threat Protection for SQL IaaS VMs running on-premises using Azure Security Center
Threat Protection for SQL IaaS VMs hosted on Azure Arc using Azure Security Center
Built-in vulnerability assessment for VMs in Azure Security Center
Azure Security Center Secure Score Reduction Alert
Best practices for layering on cloud security through Azure Marketplace
Detect attacks using Application Gateway and Web Application Firewall
Remediate Vulnerable Secure Channel Connections with the Insecure Protocols Workbook
What’s New: Query line numbering, Azure Sentinel in the schema pane
MSTIC Notebooklets – Fast Tracking CyberSec Jupyter Notebooks
Monitoring Azure Kubernetes Service (AKS) with Azure Sentinel
Guided Hunting Notebook: Base64-Encoded Linux Commands
Ingesting log files from AWS S3 using AWS Lambda
Azure Sentinel Insecure Protocols Workbook Reimagined
What’s new: SOC operational metrics now available in Azure Sentinel
Whats new: Azure Sentinel and Microsoft Defender ATP improved alert integration
Microsoft 365 Security (All Up News)
Microsoft Office 365—Do you have a false sense of cloud security?
Security baseline for Microsoft Edge version 85
Security baseline (FINAL): Windows 10 and Windows Server, version 2004
Application Guard for M365 Apps public preview
Security best practices for Windows Server Update Services (WSUS)
Managing BitLocker with Microsoft Endpoint Manager
M365 Identity & Data Protection (Azure AD, Intune, AIP, MCAS)
Conditional Access policies now apply to all client applications by default
Microsoft Authenticator app lock now enabled by default
Risky Business in Azure AD…
Automated user provisioning from SAP SuccessFactors is now GA
ALERT! New Blog Series: Automation in Cloud App Security
New study by Forrester shows customers who deploy Azure AD can benefit from a 123% ROI
Assigning groups to Azure AD roles is now in public preview!
Using Azure PIM for the AIP Super User feature management
Let’s Talk About Azure Active Directory and the Microsoft Identity Platform
Gartner announces the 2020 Magic Quadrant for Unified Endpoint Management
M365 Threat Protection (Office ATP, Windows Defender ATP, Azure ATP/ATA)
Microsoft Defender ATP Ninja Training: August 2020 update
Webinar: How to maximize Microsoft Defender ATP configuration using attack simulations
On-demand webcast series: “Tracking the adversary”
Pull in more intelligence and act fast while you hunt
Microsoft Defender ATP Daily Operation – Part 1
Microsoft Threat Protection now uses more descriptive incident names
Introducing an improved timeline investigation with event flagging
Introducing EDR in block mode: Stopping attacks in their tracks
Microsoft Defender ATP: Web Content Filtering
A new look for threat analytics
Microsoft Defender ATP for Mac is moving to system extensions
Stopping Active Directory attacks and other post-exploitation behavior with AMSI and machine learning
How can Microsoft Threat Protection help reduce the risk from phishing?
Microsoft Defender ATP: Remediate Apps Using MEM
Linux ATP Configuration and Operation Command List
Microsoft Advanced Threat Protection for Linux
M365 Compliance & Governance
FAQ for Teams compliance
New features and improvements to Sensitivity labels for Containers Webinar
Classification Depth Private Preview
Regards,
Jeremy Windmiller | Enterprise Security Architect, CISSP, CEH, ITIL | Microsoft – Healthcare
by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
It took us a little longer than we wanted but we are finally ready to announce new versions of LGPO and Policy Analyzer as well as two new tools, GPO2PolicyRules and SetObjectSecurity.
The goal is to keep this post as short as possible so let’s just jump into the details.
LGPO v3.0
Two new options were added in LGPO.exe. The first, /ef which enables Group Policy extensions referenced in the backup.xml. The second, /p which allows for importing settings directly from a .PolicyRules file which negates the need to have the actual GPOs on hand. Additionally, LGPO.exe /b and /g now capture locally-configured client-side extensions (CSEs) (which we had an issue with previously). Lastly, /b also correctly captures all user rights assignments, overcoming a bug in the underlying “secedit.exe /export” that fails to capture user rights assignments that are granted to no one.
Policy Analyzer v4.0
The “Compare to Effective State” button has replaced the “Compare local registry” and “Local Policy” checkboxes that used to be in the Policy Analyzer main window. Press it to compare the selected baseline(s) to the current system state. If the selected baseline(s) contain any user configuration settings, they are compared against the current user’s settings. “Compare to Effective State” requires administrative rights if the selected baseline(s) include any security template settings or Advanced Auditing settings. The effective state corresponding to the selected baseline(s) settings are saved to a new policy rule set.
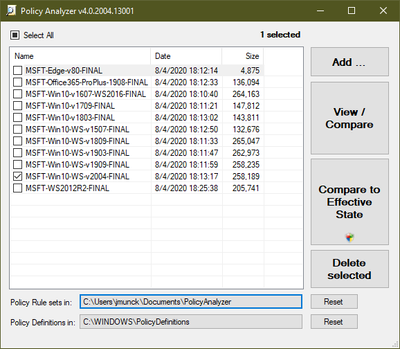
Policy Analyzer now captures information about Group Policy Client-Side Extensions (CSEs) when you import GPO backups. From a Policy Viewer window, choose View Client Side Extensions (CSEs) to view the Machine and User CSEs for each baseline in the Viewer. (Note that LGPO.exe’s improved support for CSEs includes the ability to apply CSE configurations from Policy Analyzer’s .PolicyRules files.)
Policy Analyzer now maps settings and sub-settings to display names more completely and more accurately, including mapping the GUIDs for Attack Surface Reduction (ASR) rules to their display names, and improved localization.
GPO2PolicyRules
You can now automate the conversion of GPO backups to Policy Analyzer .PolicyRules files and skip the GUI. GPO2PolicyRules is a new command-line tool that is included with the Policy Analyzer download. It takes two command-line parameters: the root directory of the GPO backup that you want to create a .PolicyRules file from, and the path to the new .PolicyRules file that you want to create. For example:
GPO2PolicyRules.exe C:BaselinePkgGPOs C:UsersAnalystDocumentsPolicyAnalyzerbaseline.PolicyRules
SetObjectSecurity v3.0
SetObjectSecurity.exe enables you to set the security descriptor for just about any type of Windows securable object (files, directories, registry keys, event logs, services, SMB shares, etc). For file system and registry objects, you can choose whether to apply inheritance rules. You can also choose to output the security descriptor in a .reg-file-compatible representation of the security descriptor for a REG_BINARY registry value.
Use cases include:
- Restoring default security descriptor on the file system root directory (which sometimes gets misconfigured by some system setup tools)
- Restricting access to sensitive event logs that grant access too broadly (examples include AppLocker and PowerShell script block logs that grant read or read-write to NT AUTHORITYINTERACTIVE)
- Locking down (or opening access to) file shares, directories, registry keys
SetObjectSecurity.exe is a 32-bit standalone executable that needs no installer, has no dependencies on redistributable DLLs, and works on all supported x86 and x64 versions of Windows. (x64 systems must support WOW64)
Terms of Use
We have now included standard use terms for the tooling that is delivered as part of the Security Compliance Toolkit.
We continually try to process all your feedback and make improvements along the way so please give the new and updated tooling a try and as always let us know any feedback in the comments below.

by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We sit in a lot of meetings and collaborate with a lot of people who are organizing and planning the Digital Experience of Microsoft Ignite – taking place ONLINE at https://myignite.microsoft.com on September 22nd through to the morning of the 24th (Pacific Time). It’s a free event open to all folks who are interested in what Microsoft is up to, targeting technical professionals, decision makers, students and startups.

We thought we’d pull together all the useful information we can dig up from the 187 slide PowerPoint presentation and share the interesting nuggets with YOU. (we’re not kidding, it grows at least a half dozen slides or more twice a week). Welcome to the first edition of the Unofficial End User Guide to Microsoft Ignite.
Keep on checking back periodically as we add more information and more videos as soon as we can share the information.
Got a question about Microsoft Ignite? Feel free to comment below the posts and we’ll be happy to answer them or heck – we might even create a video answer for ya!
Episode #1 – Go Register… why register?
In this entry of the Unofficial End User Guide of Microsoft Ignite, Patch and Switch talk about all things Registration.
Why should you register?
- It’s Free
- It’s Free
- Did we mention it’s free?
You need to register at https://myignite.microsoft.com in order to gain full access to all the content, all the digital breakouts and all the additional programming available during Microsoft Ignite.
by Scott Muniz | Sep 3, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
In part two of this three-part series, Vasiya Krishnan shares an example of how customers are using Azure SQL Edge as well as use cases. For an introduction to Azure SQL Edge, watch part one.
Watch on Data Exposed
Additional Resources:
Microsoft Industry Solutions
Learn more about Azure SQL Edge
Learn more about the features and building an end to end solution
Azure SQL Edge customer stories
Azure SQL Edge whitepaper
View/share our latest episodes on Channel 9 and YouTube!
by Scott Muniz | Sep 3, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Art by Dana Moot II
The past summer has been a magical one for the game-loving members of the Azure Advocacy team, as we presented to you our three-part game series entitled the Azure Maya Mystery. If you haven’t been following along, you can read about its genesis and continuation right here on dev.to.
True to our mission as Advocates on the Academic Team, lead developers Jen and Chris wanted to sneak in a little educational content, and we hope you have enjoyed learning more about Maya glyphs this summer. Congratulations, by the time you complete Level 3, you will know the meaning of 13 ancient Maya glyphs!
The following content contains spoilers about gameplay!
Back in July, we introduced you, the intrepid explorer, to a text-based online experience where you were introduced to a mysterious pyramid you have found, deep in the jungle. As you circle its base, reading half-hidden glyphs, you discover the keys to climb its steep flight of steps to its entrance.
Using your knowledge gleaned from matching clues found in Microsoft Learn and the newly discovered glyphs, you discover a code needed to open the pyramid’s door. You use your learnings about Azure Static Web Apps to launch a chat window to discover part of the pyramid’s name, and then gain entry into the pyramid.
But suddenly, the floor collapses under your feet and you start to slide!
In August, you discovered Level 2, where you speak to a grumpy turtle, launch a web app using Node.js to gather necessary equipment, dive into a cenote, or underground spring, and salvage broken glyphs.
Fitting them back together, you are granted access to the main chamber by the turtle, who seems to be more than a simple reptilian ally.
Now, in the very last level of the Azure Maya Mystery game, you will be able to ascend to the pinnacle of the pyramid by helping complete the restoration of the pyramid and reach the summit. Along the way, you will learn the name of the pyramid and the identity of the goddess to whom it is dedicated.
Using a web app powered by a machine learning model for image recognition, you will gain insight into the full meaning of the three parts of the pyramid’s name. Discover its meaning, and unlock the entry to the summit, where you will be rewarded by the goddess presiding over the pyramid.
We hope you have enjoyed learning about our three technical foci over this summer: Azure Static Web Apps, Node.js, and Machine Learning. In addition, we hope you enjoyed the scavenger hunt we sent you on as you shuttled between Microsoft Learn and the Mystery! Finally, we hope you learned a little about Maya pyramids and glyphs and enjoyed the adventure.
Visit the third level of the Maya Mystery today, ascend to the summit, and earn your reward!





Recent Comments