by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Security commitments and improvements on Azure Database for MySQL are attracting a growing number of customers to the platform. Our customers rely on national and industry standard security controls to develop and improve their cybersecurity defenses, and they expect the same level of security due diligence when they build their open source workloads in the cloud. These security controls also ensure that they meet the security and compliance certification requirements applicable to their industry, country, or region. This blog will highlight some of Azure Database for MySQL most notable security compliance offerings and new security features on the platform that we will be blogging about in the coming weeks.
Azure Database for MySQL have achieved a comprehensive set of national, regional, and industry-specific compliance certifications in our public cloud to help customers comply with requirements governing the collection and use of their data . To date, Azure Database for MySQL have amassed over 50 compliance offerings, including the more notable ones such as HIPAA, HITRUST, PCI-DSS, ISO 27001, ISO/IEC 27018, FedRAMP High, etc. Azure Database for MySQL are continuing to pursue even more compliance certifications, which we’ll announce in future blogs and as part of Azure’s compliance offerings.
|
Certificate
|
Applicable to…
|
|
HIPAA and HITECH Act (U.S.), HITRUST
|
Healthcare Providers, Healthcare Clearinghouses, and Health Plans
|
|
PCI-DSS
|
Commercial payment applications
|
|
ISO 27001
|
Information Security Management Systems
|
|
ISO/IEC 27018
|
Public and private companies, government entities and not-for-profits that provides PII processing services via the cloud
|
|
NIST Cybersecurity Framework
|
Public and private companies, government entities and not-for-profits
|
|
FedRAMP High
|
U.S. Federal Agencies
|
|
SOC 1, 2 and 3
|
Cloud service providers; offers assurance to customers and stakeholders that effective internal controls that affect financial reports and operational control systems are in place
|
|
Cloud Security Allowance STAR
|
Cloud service providers; demonstrates ISO/IEC 27001 and Cloud Controls Matrix compliance
|
|
EU Model Clauses
|
All EU countries Norway, Iceland, and Liechtenstein; provides assurances for personal data leaving the European Economic Area
|
|
UK G-Cloud
|
UK Government
|
Azure’s continued commitments have also led to the development and implementation of several new security features on Azure Database for MySQL that we’ll be blogging about in the next couple of weeks. These new features include high-demand capabilities such as Data Security at Rest (bring your own key [BYOK] and double encryption), Data security in Motion (TLS and SSL), Network Security (firewall, service endpoint, private link), and Access Methods (native authentication and AAD).
Microsoft also offers the Azure IP Advantage for services running open source technologies. The Azure IP Advantage provides best-in-industry intellectual property protection, uncapped indemnification, the ability to deter and defend lawsuits with patent pick and broad protection with a springing license.
These new features and others in development highlight Azure’s commitment to be the most secure cloud in the world and collectively strengthen the security portfolio of our open source services.
If you have questions, please feel free to reach out to the AskAzureDBforPostgreSQL@service.microsoft.com alias.
Thanks!
Zubah Koweh
Senior Program Manager – Microsoft
by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Final Update: Thursday, 02 July 2020 22:49 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 7/2, 20:00 UTC. Our logs show the incident started on 7/2, 18:00 UTC and that during the 2 hours that it took to resolve the issue customers may have experienced data latency, data gaps and incorrect alert activation
- Root Cause: The failure was due to an incorrect DNS entry.
- Incident Timeline: 2 Hours – 7/2, 18:00 UTC through 7/2, 20:00 UTC
We understand that customers rely on Application Insights as a critical service and apologize for any impact this incident caused.
-Ian Cairns

by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
In today’s security operation centers (SOCs), analysts have a large set of security solutions that they leverage to protect their organization and monitor activity. However, when setting up a SIEM it is challenging to prioritize what data to ingest and what protections each solution provides. SOCs must consider size and cost of ingestion, detections, and necessary use cases for each data source they would like to connect to their SIEM. Because of these considerations, SOCs should focus on ingesting data that is critical and has a low level of overlap to reduce the probability of double ingestion.
To aid SOCs as they navigate this challenge in understanding the value that each data source provides, the figure below (“Integrated Toolset”) can be used as a reference to understand how Microsoft security solutions can be grouped into categories. To expand on this, at the end of this blog the “Data Connector Table” describes several of Azure Sentinel’s built-in Microsoft data sources and maps out the respective sources to their detections (called analytics in Sentinel), use cases, and category of protection. While there are many more capabilities that Sentinel offers, this blog will focus on Data Sources and their relevant detections. The list provides a summary so that a SOC can prioritize what data they need to ingest into Sentinel as their SIEM. This blog will focus on a subset of major Microsoft data sources that can be easily leveraged in Azure Sentinel and should not be viewed as an exhaustive list. For more information on available data connectors please refer to the Azure Sentinel: Syslog, CEF, Logstash and other 3rd party connectors grand list.

Figure: Integrated Toolset
From Data Ingestion to Detection
By connecting relevant security logs into Sentinel, organizations can consolidate all their relevant data into one place. Utilizing Sentinel’s built-in Machine Learning and other detections, SOCs can analyze their logs with ease and determine what truly malicious activity has taken or (more importantly) is currently taking place.
Wherever your logs are located; you can bring them into Sentinel and benefit from Sentinel’s centralized incident management view and built-in intelligence, as well as leverage Security Playbooks to implement orchestration and automation to react to emerging threats. In the figure below (“Data Collection”) one can see how Sentinel allows for the ingestion of data across Azure, other clouds, and OnPrem to fuel its ML and built-in rules.
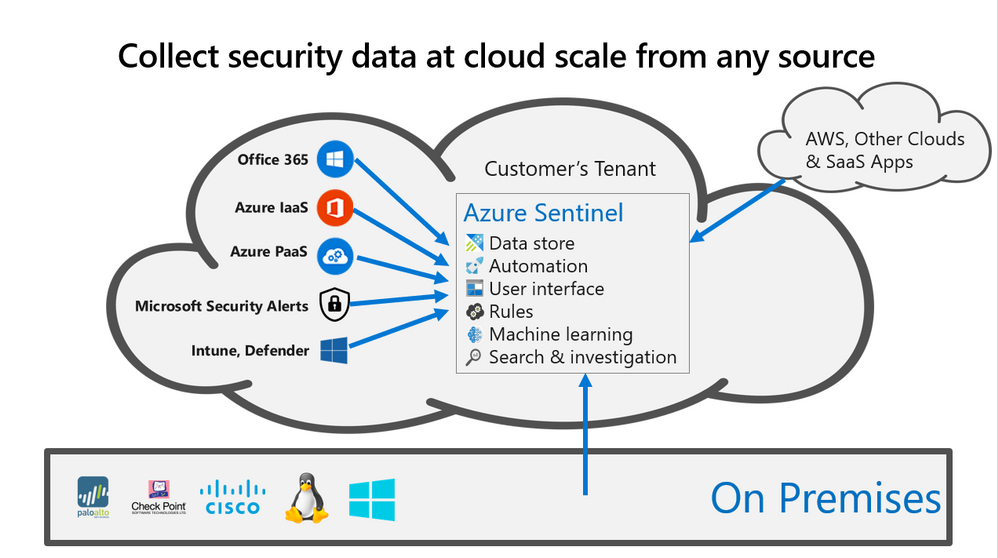
Figure: Data Collection
There are many built-in data connectors and methods to get data into Sentinel that are not covered in this blog, but the below table can be leveraged for understanding the built-in data connectors for Microsoft technologies. Listed in the table are links to related documents that provide a deeper dive into the respective Data Connector, a list of the relevant Sentinel built-in analytics to determine observed threats, and a category of security coverage that the data source provides.
This list serves as a partial guide to a handful of major Microsoft data sources that can be easily and quickly ingested into Sentinel to help SOCs adopt Sentinel and see value quickly. However, it is important to note that Sentinel provides additional data source coverage, machine learning, and fusion alerts that span across multiple data sources. While this blog focuses on built-in single-source Sentinel detections and receiving detections from their respective data sources, there are more use cases to consider on cross-source detection, investigating alerts, visualizing data with workbooks, and hunting.
Data Connector Table
Note: This is an expanding list
|
Data Connector
|
Description
|
Relevant Links
|
Category
|
Free/Paid
|
|
Azure Active Directory
|
The Azure Active Directory (Azure AD) enterprise identity service provides single sign-on and multi-factor authentication to help protect users from 99.9 percent of cybersecurity attacks.
|
|
Identity
Devices
|
Paid
|
|
Azure Active Directory Identity Protection
|
Detect threats to user’s identity such as compromised Azure Active Directory credentials or when someone other than the account owner is attempting to sign in using their identity
|
|
Identity
|
Paid
|
|
Azure Activity
|
Subscription level oversight and event tracking. This includes a record of ‘write’ changes that occur in Azure. This shows for each PUT, POST, and DELETE: who was involved, when the change happened, and what did the user change.
|
|
Identity
Infrastructure
|
Free
|
|
Azure Advanced Threat Protection (Alerts)
|
Domain Controller based anomaly detection on User/Entity Behavior Analytics, malicious insider action, lateral movements, domain dominance, and compromised identities for OnPrem and Cloud scenarios.
|
|
Identity
|
Free
|
|
Azure Firewall
|
Protection for Azure Virtual Network resources. Threat intelligence-based filtering to alert and deny traffic from/to known malicious IP addresses and domains.
|
|
Network
Infrastructure
|
Paid
|
|
Azure Information Protection (Alerts)
|
Oversight and protection in the cloud and OnPrem for advanced data related attacks and insider threats. Unusual data access attempts and custom alerts based on data.
|
|
Data
Apps
|
Free
|
|
Azure Security Center (Alerts)
|
In addition to its Security Posture Management features; Security Center’s threat protection enables you to detect and prevent threats at the IaaS & PaaS layers (Azure Resources), as well as non-Azure servers.
|
|
Infrastructure
Azure Resources
IaaS & PaaS (see detections for full list)
|
Free
|
|
Azure Security Center for IoT (alerts)
|
Built-in and custom detections on you IoT Hub and or IoT devices potentially malicious activity.
|
|
IoT
Identity
Devices
Endpoints
|
Free
|
|
Azure Web Application Firewall
|
Protection from common web vulnerabilities such as SQL injection and cross-site scripting. Monitor your web applications using custom rules, rule groups, and Sentinel detections based on the diagnostics of Application Gateways to suit your requirements and eliminate false positives.
|
|
Infrastructure
Identity
|
Paid
|
|
Domain Name Server
|
Oversight on malicious domain names, stale resource records, talkative DNS clients, and DNS registration failures.
|
|
Microsoft DNS
|
Paid
|
|
Microsoft Cloud App Security (Alerts and Shadow IT Report)
|
Raise alerts on user or file behavior anomalies in cloud apps leveraging API connectors. Detections are grouped into risk factors: risky IP address, login failures, admin activity, inactive accounts, location, impossible travel, device and user agent, and activity rate
|
|
Apps
Data
Identity
(see detections for full list)
|
Free
|
|
Microsoft Defender Advanced Threat Protection (Alerts)
|
Detection of attacker tools, techniques, and procedures, behavioral signals through the embedded endpoint behavioral sensors. Threat recognition leverages big-data, machine-learning, and Microsoft optics across Windows, other cloud products (Office 365), and online assets.
|
|
Endpoints
Infrastructure
Devices
|
Free
|
|
Office 365 (Office Activity: Exchange & SharePoint)
|
Custom and built-in detections on user, admin, system, and policy actions and events from ingestion of the OfficeActivity Log (Exchange Online and SharePoint raw audit logs).
|
|
Apps
Data
|
Free
|
|
Windows Security Events
|
Streaming of windows security and AppLocker events to protect your Windows servers and workstations (physical and virtual). This can include full user audit trails, security group changes, key domain controller Kerberos operations, and more.
|
|
Identity
Infrastructure
|
Paid
|
To prioritize the onboarding of critical data connectors please view ‘Part 3: Alert and Log Ingestion’ of the Microsoft security architecture recommendations
For data sources missing from the above table, please refer to the following links:
Next Steps
Setting up a Data Connector in Sentinel can be as easy as two-clicks, but it is important to make sure that after you have setup a Data Connector that you enable the applicable built-in analytics to start detecting threats to your environment. By enabling an analytic, Sentinel will monitor the connected logs for that specific threat and will create an alert. Sentinel will then review other contextual events and potentially create an incident for investigation. Using the table above, you can navigate the Sentinel GitHub community and other relevant documents to view Sentinel’s detections per each respective data table. Additionally, you can view and enable each data sources analytics by navigating to the respective Data Connector page as seen in the graphic below.
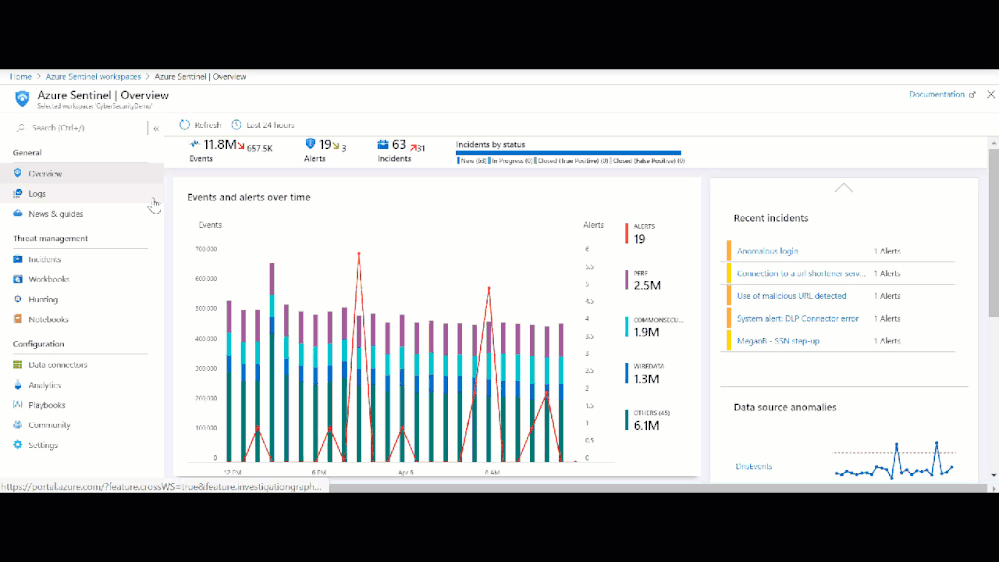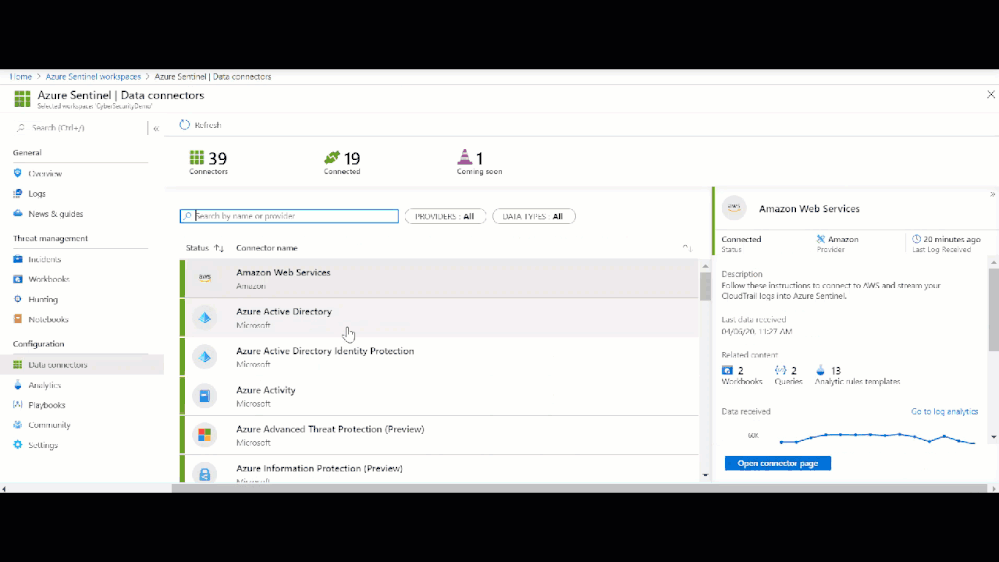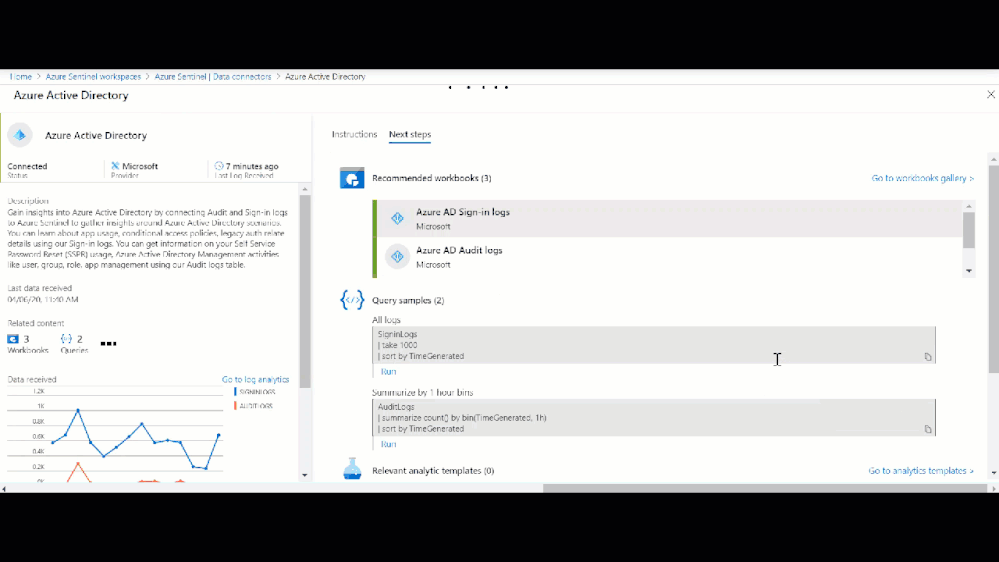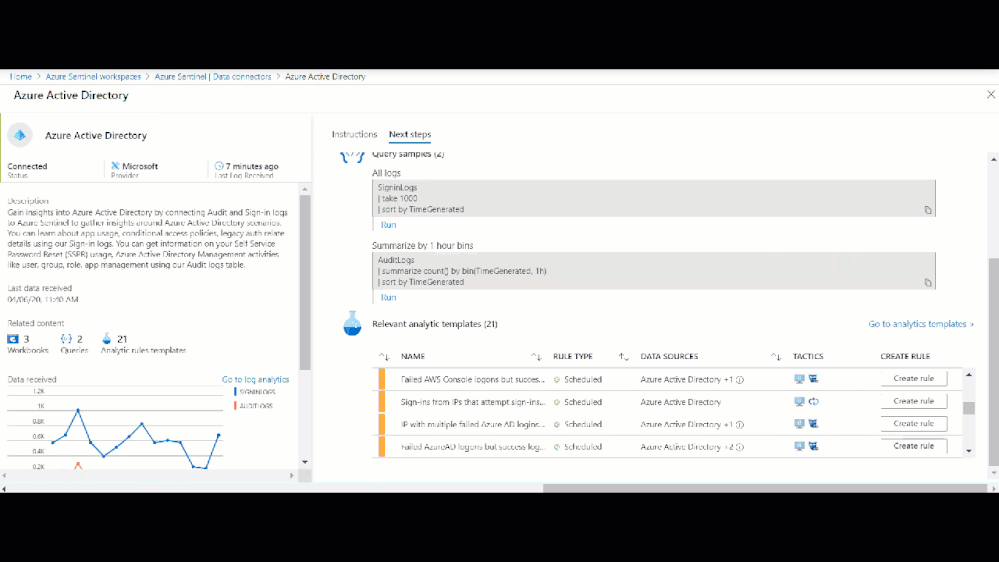 Sentinel built-in single source analytic rules
Sentinel built-in single source analytic rules
Figure: Built-in single-source analytic rules per data source in Azure Sentinel
To reduce alert fatigue and understand how one attack spanned across multiple data sources check out Sentinel’s fusion based analytics. For additional detections that span across multiple data sources, please view the artifacts located in the Sentinel GitHub Community.
Related Blogs:
Identifying Threat Hunting opportunities in your data
Azure Sentinel correlation rules: the join KQL operator

by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
In today’s security operation centers (SOCs), analysts have a large set of security solutions that they leverage to protect their organization and monitor activity. However, when setting up a SIEM it is challenging to prioritize what data to ingest and what protections each solution provides. SOCs must consider size and cost of ingestion, detections, and necessary use cases for each data source they would like to connect to their SIEM. Because of these considerations, SOCs should focus on ingesting data that is critical and has a low level of overlap to reduce the probability of double ingestion.
To aid SOCs as they navigate this challenge in understanding the value that each data source provides, the figure below (“Integrated Toolset”) can be used as a reference to understand how Microsoft security solutions can be grouped into categories. To expand on this, at the end of this blog the “Data Connector Table” describes several of Azure Sentinel’s built-in Microsoft data sources and maps out the respective sources to their detections (called analytics in Sentinel), use cases, and category of protection. While there are many more capabilities that Sentinel offers, this blog will focus on Data Sources and their relevant detections. The list provides a summary so that a SOC can prioritize what data they need to ingest into Sentinel as their SIEM. This blog will focus on a subset of major Microsoft data sources that can be easily leveraged in Azure Sentinel and should not be viewed as an exhaustive list. For more information on available data connectors please refer to the Azure Sentinel: Syslog, CEF, Logstash and other 3rd party connectors grand list.

Figure: Integrated Toolset
From Data Ingestion to Detection
By connecting relevant security logs into Sentinel, organizations can consolidate all their relevant data into one place. Utilizing Sentinel’s built-in Machine Learning and other detections, SOCs can analyze their logs with ease and determine what truly malicious activity has taken or (more importantly) is currently taking place.
Wherever your logs are located; you can bring them into Sentinel and benefit from Sentinel’s centralized incident management view and built-in intelligence, as well as leverage Security Playbooks to implement orchestration and automation to react to emerging threats. In the figure below (“Data Collection”) one can see how Sentinel allows for the ingestion of data across Azure, other clouds, and OnPrem to fuel its ML and built-in rules.

Figure: Data Collection
There are many built-in data connectors and methods to get data into Sentinel that are not covered in this blog, but the below table can be leveraged for understanding the built-in data connectors for Microsoft technologies. Listed in the table are links to related documents that provide a deeper dive into the respective Data Connector, a list of the relevant Sentinel built-in analytics to determine observed threats, and a category of security coverage that the data source provides.
This list serves as a partial guide to a handful of major Microsoft data sources that can be easily and quickly ingested into Sentinel to help SOCs adopt Sentinel and see value quickly. However, it is important to note that Sentinel provides additional data source coverage, machine learning, and fusion alerts that span across multiple data sources. While this blog focuses on built-in single-source Sentinel detections and receiving detections from their respective data sources, there are more use cases to consider on cross-source detection, investigating alerts, visualizing data with workbooks, and hunting.
Data Connector Table
Note: This is an expanding list
|
Data Connector
|
Description
|
Relevant Links
|
Category
|
Free/Paid
|
|
Azure Active Directory
|
The Azure Active Directory (Azure AD) enterprise identity service provides single sign-on and multi-factor authentication to help protect users from 99.9 percent of cybersecurity attacks.
|
|
Identity
Devices
|
Paid
|
|
Azure Active Directory Identity Protection
|
Detect threats to user’s identity such as compromised Azure Active Directory credentials or when someone other than the account owner is attempting to sign in using their identity
|
|
Identity
|
Paid
|
|
Azure Activity
|
Subscription level oversight and event tracking. This includes a record of ‘write’ changes that occur in Azure. This shows for each PUT, POST, and DELETE: who was involved, when the change happened, and what did the user change.
|
|
Identity
Infrastructure
|
Free
|
|
Azure Advanced Threat Protection (Alerts)
|
Domain Controller based anomaly detection on User/Entity Behavior Analytics, malicious insider action, lateral movements, domain dominance, and compromised identities for OnPrem and Cloud scenarios.
|
|
Identity
|
Free
|
|
Azure Firewall
|
Protection for Azure Virtual Network resources. Threat intelligence-based filtering to alert and deny traffic from/to known malicious IP addresses and domains.
|
|
Network
Infrastructure
|
Paid
|
|
Azure Information Protection (Alerts)
|
Oversight and protection in the cloud and OnPrem for advanced data related attacks and insider threats. Unusual data access attempts and custom alerts based on data.
|
|
Data
Apps
|
Free
|
|
Azure Security Center (Alerts)
|
In addition to its Security Posture Management features; Security Center’s threat protection enables you to detect and prevent threats at the IaaS & PaaS layers (Azure Resources), as well as non-Azure servers.
|
|
Infrastructure
Azure Resources
IaaS & PaaS (see detections for full list)
|
Free
|
|
Azure Security Center for IoT (alerts)
|
Built-in and custom detections on you IoT Hub and or IoT devices potentially malicious activity.
|
|
IoT
Identity
Devices
Endpoints
|
Free
|
|
Azure Web Application Firewall
|
Protection from common web vulnerabilities such as SQL injection and cross-site scripting. Monitor your web applications using custom rules, rule groups, and Sentinel detections based on the diagnostics of Application Gateways to suit your requirements and eliminate false positives.
|
|
Infrastructure
Identity
|
Paid
|
|
Domain Name Server
|
Oversight on malicious domain names, stale resource records, talkative DNS clients, and DNS registration failures.
|
|
Microsoft DNS
|
Paid
|
|
Microsoft Cloud App Security (Alerts and Shadow IT Report)
|
Raise alerts on user or file behavior anomalies in cloud apps leveraging API connectors. Detections are grouped into risk factors: risky IP address, login failures, admin activity, inactive accounts, location, impossible travel, device and user agent, and activity rate
|
|
Apps
Data
Identity
(see detections for full list)
|
Free
|
|
Microsoft Defender Advanced Threat Protection (Alerts)
|
Detection of attacker tools, techniques, and procedures, behavioral signals through the embedded endpoint behavioral sensors. Threat recognition leverages big-data, machine-learning, and Microsoft optics across Windows, other cloud products (Office 365), and online assets.
|
|
Endpoints
Infrastructure
Devices
|
Free
|
|
Office 365 (Office Activity: Exchange & SharePoint)
|
Custom and built-in detections on user, admin, system, and policy actions and events from ingestion of the OfficeActivity Log (Exchange Online and SharePoint raw audit logs).
|
|
Apps
Data
|
Free
|
|
Windows Security Events
|
Streaming of windows security and AppLocker events to protect your Windows servers and workstations (physical and virtual). This can include full user audit trails, security group changes, key domain controller Kerberos operations, and more.
|
|
Identity
Infrastructure
|
Paid
|
To prioritize the onboarding of critical data connectors please view ‘Part 3: Alert and Log Ingestion’ of the Microsoft security architecture recommendations
For data sources missing from the above table, please refer to the following links:
Next Steps
Setting up a Data Connector in Sentinel can be as easy as two-clicks, but it is important to make sure that after you have setup a Data Connector that you enable the applicable built-in analytics to start detecting threats to your environment. By enabling an analytic, Sentinel will monitor the connected logs for that specific threat and will create an alert. Sentinel will then review other contextual events and potentially create an incident for investigation. Using the table above, you can navigate the Sentinel GitHub community and other relevant documents to view Sentinel’s detections per each respective data table. Additionally, you can view and enable each data sources analytics by navigating to the respective Data Connector page as seen in the graphic below.

Figure: Built-in single-source analytic rules per data source in Azure Sentinel
To reduce alert fatigue and understand how one attack spanned across multiple data sources check out Sentinel’s fusion based analytics. For additional detections that span across multiple data sources, please view the artifacts located in the Sentinel GitHub Community.
Related Blogs:
Identifying Threat Hunting opportunities in your data
Azure Sentinel correlation rules: the join KQL operator
by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Azure Stack Hub is an extension of Azure that provides a way to run apps in an on-premises environment and deliver Azure services in your datacenter. In this episode of One Ops Question @thomasmaurer talks about the different use cases is can be applied to.
I often get asked by customers about what are the use cases for Azure Stack Hub. It really comes down to bringing Azure services to your own datacenter or your location.
For example you have compliance reason where you can’t use Azure in another country this is where address that Azure Stack Hub can come in and bring those Azure services to you. This allows you to
confidently make technology decisions based on your business requirements, rather than business decisions based on technology limitations.
Here are some of the use cases:
-
Edge and disconnected solutions. this will address latency and connectivity requirements by processing data locally in Azure Stack Hub and then aggregating it in Azure for further analytics, with common app logic across both. You can even deploy Azure Stack Hub disconnected from the internet without connectivity to Azure. Think of factory floors, cruise ships, and air-gaped networks as examples.
-
Cloud apps that meet varied regulations. Develop and deploy apps in Azure with full flexibility to deploy on-premises with Azure Stack Hub to meet regulatory or policy requirements. No code changes are needed. App examples include global audit, financial reporting, foreign exchange trading, online gaming, and expense reporting.
-
Cloud app model on-premises. Use Azure services, containers, serverless, and microservice architectures to update and extend existing apps or build new ones. Use consistent DevOps processes across Azure in the cloud and Azure Stack Hub on-premises to speed up app modernization for core mission-critical apps.
There are even Azure Stack Hub datacenter integration walkthrough that describes the end-to-end process for Azure Stack Hub datacenter integration, from purchasing to post-deployment support..
You can always refer to our documentation to learn more about Azure Stack Hub here: https://cda.ms/1nH and if you’re interested, try Azure for yourself: https://aka.ms/TryAzure13
Cheers!
by Scott Muniz | Jul 2, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
We are making available the private preview of Azure Arc enabled SQL Server. To read more, see the original article in the SQL Server Tech Community.
-Marko



Recent Comments