by Contributed | May 14, 2021 | Technology
This article is contributed. See the original author and article here.
Hello! I’m Sue Bohn, Partner Director of Program Management for Identity and Access Management. In this Voice of the Partner blog post, we’ve invited Prakash Narayanamoorthy, Principal Microsoft Security Architect for Wipro, and Terence Oliver Jayabalan, Practice Partner and Global Solutions Lead for IAM at Wipro, to share how their company envisioned, engineered, and brought to market a one-of-a-kind solution for automatically migrating third-party apps to Azure Active Directory—shrinking the migration process from months to hours.
Seamlessly and automatically migrate SSO applications to Azure AD
By Terence Oliver Jayabalan, Practice Partner, Global Solutions Lead for Identity and Access Management
Wipro Limited is a leading global information technology, consulting, and business process services company. We harness the power of cognitive computing, hyper-automation, robotics, cloud, analytics, and emerging technologies to help our clients succeed in the digital world. With over 180,000 employees serving clients across six continents, we’ve been recognized for our comprehensive portfolio of services, commitment to sustainability, and good corporate citizenship. With a staff of more than 8,000 security professionals, Wipro has been helping customers in the Identity and Access Management (IAM) domain for more than two decades through our consulting, advisory, and implementation solutions.
Moving a mountain—app migrations and IAM
Our customers come to us from across industry verticals, but a common pain point for most of them involves user provisioning and access management for single sign-on (SSO) software-as-a-service (SaaS) apps. With Zero Trust now the gold standard for enterprise security, identity has become the new perimeter. Many of our customers are looking to modernize their identity and access management (IAM) landscape by bringing advanced platforms like Azure Active Directory (Azure AD) into their environment; so they can connect and secure all their apps with a single identity solution. With Azure AD, Conditional Access, multifactor authentication, single-sign on (SSO), and automatic user provisioning make IAM easier and more secure across the enterprise. Azure AD also saves money by reducing admin overhead for on-premises user provisioning and authentication—Forrester estimates the value of IT efficiency gains at USD 3.0 million over three years.
However, moving to a new IAM solution often requires the time-consuming task of manually migrating hundreds of SaaS applications from their existing IAM solution. This typically involves the admin getting the connection parameters from the existing tool and manually bringing it into Azure AD, usually by typing information or with some form of export-import function. Then, the admin has to validate those settings and do the application site configurations before the end-to-end integration/migration is finally completed. For a typical business, this process can require several hours just for one app.
Wipro sought to change that. We set out to build a solution that could automate migrating applications from one IAM platform to another while addressing the biggest IAM app-migration challenges:
- Large number of applications needing to be migrated.
- Need for a specialized skillset to carry out the migration.
- Extensive manual effort needed to migrate applications to a new platform.
- No centralized view of the vast IAM landscape.
- Lack of centralized monitoring, reporting, and management for IAM.
- No centralized repository for documents, best practices, templates, or delivery kits.
- Lack of IAM tasks and process automations.
- No simplified view of IAM operations (user details, who has access to what).
Wipro’s solution—Identity Management Center (IMC)
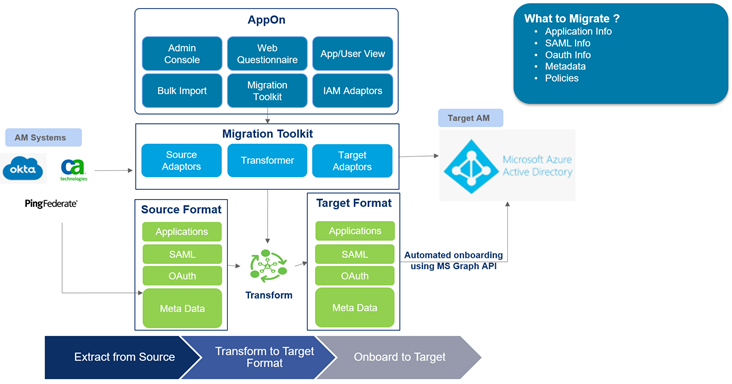
To solve this pain point for our customers, Wipro worked closely with the Microsoft Identity engineering team to enable a seamless solution for onboarding SSO apps to Azure AD. Our new accelerator solution, Identity Management Center (IMC), automates and accelerates the app migration/onboarding process from end to end. IMC supports migrating OIDC and SAML applications, as well as multiple IAM systems both as a source and a target—including a new functionality to speed up migration of SSO apps from Okta to Azure AD.
We make use of customer Okta instance APIs to pull information about the application into IMC, i.e., SAML and related metadata, any URLs, and policy information. As all that is pulled in, we transform it into a format which Microsoft Azure AD understands. Once it’s present in that format within IMC, we make use of the Microsoft Graph API to push that information into Azure AD.

Figure 1: IMC for Azure AD: Reference architecture
Once the application configuration is loaded into the IMC platform, migrating from one environment to another (Dev to QA, QA to Prod, etc.) requires just the click of a button. It begins with the discovery process in the Okta platform, followed by bringing the required configuration into IMC. The intuitive IMC interface helps users gather the applications’ onboarding details effortlessly via web-form questionnaires. Once the app configurations are onboarded, IMC automatically provisions the apps to Azure AD. Our IMC solution also integrates with IT service management (ITSM) tools like SNOW, helping to incorporate change-management processes for automated onboarding to Azure AD as well.

Figure 2: IMC accelerated process for SaaS app migration
Wipro’s IMC solution is a web-tiered architecture that can be quickly setup on customers’ on-premises or cloud infrastructure. And because IMC is not a multi-tenant solution, data residency and control remains completely within the customer’s hands. IMC provides a single pane of glass for monitoring IAM solutions across your enterprise—a single, holistic service-management platform which provides compliance visibility and includes accelerators and automation tool-kits.
IMC contains eight modules covering enterprise IAM:
- Data VX: Data validation and transformation
- AppOn: Application onboarding
- Unified dashboards: Singular view of IAM ecosystem
- Delivery toolkits: Industry best practices and tool kits
- IAM monitoring: Live monitoring via APIs and agents
- TestAX: Test automation and execution
- UAmatic: Unified access management
- Bot management: Bot execution monitoring
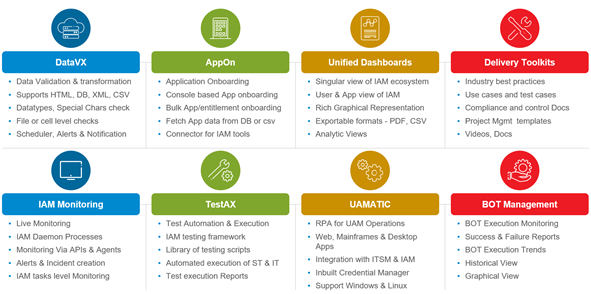
Figure 3: IMC modules
For questions like, how many orphan accounts do you have? Or how many concurrent logins are happening in your access-management system? Those are the types of things you can configure in the dashboard. For example, if you have 100 applications integrated to your Azure AD; validating those normally is going to be a huge manual effort. Instead, TestAX will run scripts for you at the click of a button—all the use cases can run in a series and provide you with a PDF report.
Results—fast, easy app migration
If a typical manual migration of 500 applications takes around 10 months, our IMC solution can reduce app migration efforts by 60 to 70 percent—dropping migration timelines from months to hours. Working closely with the Azure AD engineering team on the Microsoft Graph APIs and IMC integration, we’ve been able to automate the entire SSO app migration to deliver one-click onboarding from Okta to Azure AD, including:
- Live auto discovery of Okta apps
- No Okta or Azure AD admins required for SSO application onboarding activities
- Automatic transformation of Okta configuration into Azure AD
- One-click migration of configurations
- Automated ticketing with integrated ITSM
- Easily assign applications to users in Azure AD
- Provides Azure AD certificate
Teamwork brings IMC to market
We have a deep connection with the Microsoft Identity engineering team, and they’re really excited about our IMC solution because it’s the only tool of its kind that provides a seamless migration from Okta to Azure AD. We’ve presented IMC to multiple customers, and they’re excited too. This is the only tool that solves their specific pain points around application migration and IAM. Our team at Wipro believes that IMC has the potential for migrating thousands of applications, including deeper integrations with other ecosystems. The results have been so promising, we’re now building migration capabilities for more IAM solutions, such as Ping Identity and Oracle Access Management. We’re expecting IMC’s Okta-to-Azure AD migration feature to enter general availability in Q2, 2021
For additional information about Wipro and their IMC SaaS app-migration solution, please contact cybersecurity.services@wipro.com
Learn more about Microsoft identity:

by Contributed | May 14, 2021 | Technology
This article is contributed. See the original author and article here.
Azure Percept is a platform of hardware and services that simplifies use of Azure AI technologies on the edge. The development kit comes with an intelligent camera, Azure Percept Vision, and it can also be extended with Azure Percept Audio, a linear microphone array. Azure Percept works out of the box with Azure services such as Cognitive Services, Machine Learning, Live Video Analytics, and others to deliver vision and audio insights in real time. Scenarios like object detection, spatial analytics, anomaly detection, keyword spotting, and others can easily be solved with use of pre-built Azure AI models for edge.
I build “Perceptmobile”, an Azure Percept-powered obstacle avoidance LEGO Boost car, as a weekend project and in this post I will walk you through all steps how it was built.

In the standard LEGO Boost package you can find instructions on how to build 4 different models and one of them is M.T.R. 4 model, which I modified a bit to fit the needs of this project. Model was used as a base on top of which I placed Azure Percept with Azure Percept Vision camera. LEGO Boost package also comes with 3 cones that I took pictures of and trained the Custom Vision model. Custom vision models can easily be deployed to the Azure Percept via Azure Percept Studio, and you can easily test it with camera stream.
With NodeJS I made a small backend that is based on quickstart “Send telemetry from a device to an IoT hub and read it with a back-end application” and with use of Express I served results on the localhost. For the frontend application I used “Lego Boost Browser Application” which is a great React application for controlling LEGO Boost from the browser via Web Bluetooth API. With it you can easily connect to your LEGO Boost, and the application gives you a nice interface where you are not only able to control motors and other sensors, but you are also able to write different commands and programming logic.
In following video you can see full walkthrough how to build this project:
Quickstart: Send telemetry from a device to an IoT hub and read it with a back-end application (Node.js) can be found here.
Azure CLI commands used:
az iot hub show --query properties.eventHubEndpoints.events.endpoint --name {YourIoTHubName}
az iot hub show --query properties.eventHubEndpoints.events.path --name {YourIoTHubName}
az iot hub policy show --name service --query primaryKey --hub-name {YourIoTHubName}
Pictures used for model training and relevant code is available in GitHub repository.

by Contributed | May 14, 2021 | Technology
This article is contributed. See the original author and article here.

Augmented Reality 3D Photo Sphere in Xamarin, .NET and ARKit – Explained
Lee Englestone is an innovative Dev Manager who likes to operate in the area where technology, product, people and business strategy converge. Lee, from the UK, is constantly working on side projects, building things and looking for ways to educate the .NET community in great technologies. He is the creator of Visual Studio Tips, Hackathon Tips and Xamarin Arkit. For more, see Lee’s blog and Twitter @LeeEnglestone.

Send an Adaptive Card to Teams from Microsoft Lists using Power Automate
Norm Young is an Office Apps & Services MVP working as the Director of Collaborative Analytics at UnlimitedViz, the makers of tyGraph. He is focused on SharePoint and the Power Platform and shares his passion through his blog and speaking at conferences. Norm is also an active community contributor and helps to organize the Citizen Developers User Group. Follow him on Twitter @stormin_30 and visit his blog.

Firebase push notifications for dotnet. Advanced guide
Damien Doumer is a software developer and Microsoft MVP in development technologies, who from Cameroon and currently based in France. He plays most often with ASP.Net Core and Xamarin, and builds mobile apps and back-ends. He often blogs, and he likes sharing content on his blog at https://doumer.me. Though he’s had to deal with other programming languages and several frameworks, he prefers developing in C# with the .Net framework. Damien’s credo is “Learn, Build, Share and Innovate”. Follow him on Twitter @Damien_Doumer.

Teams Real Simple with Pictures: Custom Policy Packages
Chris Hoard is a Microsoft Certified Trainer Regional Lead (MCT RL), Educator (MCEd) and Teams MVP. With over 10 years of cloud computing experience, he is currently building an education practice for Vuzion (Tier 2 UK CSP). His focus areas are Microsoft Teams, Microsoft 365 and entry-level Azure. Follow Chris on Twitter at @Microsoft365Pro and check out his blog here.

Milestones – a new Dataverse for Teams ready-to-use template application
Vesku Nopanen is a Principal Consultant in Office 365 and Modern Work and passionate about Microsoft Teams. He helps and coaches customers to find benefits and value when adopting new tools, methods, ways or working and practices into daily work-life equation. He focuses especially on Microsoft Teams and how it can change organizations’ work. He lives in Turku, Finland. Follow him on Twitter: @Vesanopanen
by Scott Muniz | May 14, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Since December 2020, the Cybersecurity and Infrastructure Security Agency (CISA) has been responding to a significant cyber incident. An advanced persistent threat (APT) actor added malicious code to multiple versions of SolarWinds Orion and, in some instances, leveraged it for initial access to enterprise networks of multiple U.S. government agencies, critical infrastructure entities, and private sector organizations. Once inside the network, the threat actor bypassed multi-factor authentication (MFA) and moved laterally to Microsoft Cloud systems by compromising federated identity solutions. Note: on April 15, 2021, the U.S. Government attributed this activity to the Russian Foreign Intelligence Service (SVR). See the statement from the White House for additional details.
For more information and resources on this activity, refer to us-cert.cisa.gov/remediating-apt-
compromised-networks.
For more information on CISA’s response to this activity, refer to cisa.gov/supply-chain-compromise.
CISA has provided this guidance to federal agencies with networks that used affected versions of SolarWinds Orion and have evidence of follow-on threat actor activity—CISA Alert AA20-352A: Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organizations labels these as Category 3 agencies. This guidance is intended to support Category 3 agencies in crafting their eviction plans in accordance with ED 21-01: Supplemental Direction Version 4. Note: agencies should refer to CISA Alert AA20-352A for guidance on determining if they are Category 3. CISA is aware of other initial access vectors; agencies should not assume they are not compromised by this APT actor solely because they have never used affected versions of SolarWinds Orion.
Those agencies should investigate to confirm they have not observed related threat actor tactics, techniques, and procedures (TTPs). CISA recommends any agency that detects related activity review this guidance as well as CISA Alert AA20-352A, and contact CISA for further assistance.
Although this guidance is tailored to federal agencies, CISA encourages critical infrastructure entities; state, local, territorial, and tribal government organizations; and private sector organizations to review and apply it, as appropriate.
The steps provided in this guidance are resource-intensive and highly complex and will require the enterprise network to be disconnected from the internet for 3–5 days. In order to have fully informed senior-level support, CISA recommends that agency senior leadership conduct planning sessions throughout this process to understand the resources needed and any potential disruption in business operations. CISA encourages agency leadership to review CISA Insights: SolarWinds and AD/M365 Compromise Risk Decisions for Leaders for more information.
By taking steps to evict this adversary from compromised on-premises and cloud environments, agencies will position themselves for long-term actions to build more secure, resilient networks.
For a PDF copy of this report, click here.
Important: Category 3 organizations should use out-of-band communications for all mitigation and remediation communications and documentation, i.e., do not use any compromised systems to internally or externally communicate remediation plans or actions.
Remediation plans for dealing with malicious compromises are necessarily unique to every organization, and success requires careful consideration. There are three phases for evicting the actor:
- Phase 1: Pre-Eviction. Actions to detect and identify APT activity and prepare the network for eviction. Note: for the purposes of this guidance, a network is defined as any computer network with hosts that share either a logical trust or any account credentials with affected versions of SolarWinds Orion.
- Phase 2: Eviction. Actions to remove the APT actor from on-premises and cloud environments. This phase includes rebuilding devices and systems.
- Phase 3: Post-Eviction. Actions to ensure eviction was successful and the network has good cyber posture.
Conducting each step in this guidance is necessary to fully evict the adversary from Category 3 networks. Failure to perform comprehensive and thorough remediation activity will expose enterprise networks and cloud environments to substantial risk for long-term undetected APT activity, and compromised organizations will risk further loss of sensitive data and erosion of public trust in their networks.
Although this guidance provides a level of detail that describes actions to be completed, it does not describe how these actions should be completed. To successfully evict the threat actor, these actions need to be conducted in the order specified. Additionally, this guidance clearly notes caveats and provides references to help agencies develop their plan.
Pre-Eviction Phase
- Define the true scope by identifying trust boundaries (including between Active Directory [AD] forests and domains) and determining the enterprise assets to which this guidance applies (i.e., determine what assets are within the trust boundary).
- For example, the organization needs to determine the identity provider (IdP) sources (such as Okta, Microsoft Active Directory Federation Services [ADFS], Duo) that it uses to issue single-sign on (SSO) credentials and it needs to identify assets that rely on the SSO credentials to allow access (i.e., what controlled data sources are accessible via that credential).
- Investigate suspicious account activity associated with your SolarWinds servers, especially service accounts used by SolarWinds Orion. Additionally, enumerate and investigate any credentials stored or used on the SolarWinds server, including network administration and device credentials. This can be conducted, for example, using a transitive mapping of all potentially compromised credentials to the systems that those credentials accessed. If—as a Category 3 agency—you cannot confirm that all your credential activity is benign, you should proceed as if the highest administrative level of credentials on your affected SolarWinds server has been compromised. In many cases, the adversary may have had this access for months. Refer to the following resources for more information.
- FireEye: Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor
- CISA Alert AA20-352A: Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organization
- Investigate potential Security Assertion Markup Language (SAML) abuse in your environment. Refer to the following resources.
- CISA Alert AA21-008A: Detecting Post-Compromise Threat Activity in Microsoft Cloud Environments
- National Security Agency: Detecting Abuse of Authentication Mechanisms
- FireEye: Remediation and Hardening Strategies for Microsoft 365 to Defend Against UNC2452
- Microsoft: Understanding “Solorigate”‘s Identity IOCs – for Identity Vendors and their customers
- Scope the intrusion.
- Look for the artifacts from known TTPs associated with this activity. Refer to SolarWinds and Active Directory/M365 Compromise: Detecting Advanced Persistent Threat Activity from Known Tactics, Techniques, and Procedures for TTPs and corresponding detection artifacts. Prioritize these by biggest value for the investment (e.g., prioritize these by techniques or technologies that cover multiple tactics or that provide visibility into shared data sources). After identifying the TTPs for which your organization has security controls to detect/stop/mitigate, you can make risk-based decisions on how to address visibility and protection strategies for the remaining MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK)-based paths.
- Audit all network device configurations stored or managed on the SolarWinds monitoring server for signs of unauthorized or malicious configuration changes. Organizations should audit the current network device running configuration and any local configurations that could be loaded at boot time.
- Assess the current endpoint telemetry collection level and configure endpoint forensics and detection solutions for aggressive collection; prioritize this by value of asset and account.
- Harden the enterprise attack surface.
- Review and validate perimeter firewall rulesets. Remove all allow rules for which the organization does not have a clearly defined, understood, and documented need. “Deny all” statements that identify necessary connections and allow them as exceptions are the standard for perimeter devices.
- Reduce the number of systems that are able to access the internet directly. Note: this action may require analysis by network engineers with fundamental knowledge of (1) how network data communicates through agency trust boundaries and (2) the IP routing in the enterprise.
- For example, domain controllers should never be used for—or capable of— browsing the internet. (Microsoft’s analysis of domain controllers identified that privileged users often use Internet Explorer to browse the intranet or internet.
- For more information on designing networks where critical or security-related appliances and servers do not have access to the internet, refer to the United Kingdom’s National Cyber Security Centre (NCSC): Security Architecture Anti-Patterns.
- Reduce the number of egress ports at the enterprise perimeter. This requires a review of all perimeter firewall rulesets (rulesets may differ among firewalls).
- Implement host-based firewalls to make the work of moving laterally more challenging for the adversary, disrupting the ability to move from compromised workstations to domain resources. Consider blocking or closely monitoring workstation-to-workstation communications as much as possible, using Privileged Access Workstations (PAWs) and servers for administrative functions. Firewalls and endpoint detection and response functions may have similar capability, but both need to feature (1) filtering of allowed connections and (2) visibility/detection for connections.
- Close and/or monitor high-risk ports (e.g., Remote Desktop Protocol [RDP], Server Message Block [SMB], File Transfer Protocol [FTP], Trivial File Transfer Protocol [TFTP], Secure Shell [SSH], and WebDAV).
- Carefully employ application execution control (allowlisting), especially for systems providing remote access to the enterprise.
- Enforce enterprise Domain Name System (DNS) resolution for all systems. Do not allow internal systems to directly access internet DNS servers.
- Ensure that all endpoints that will need to be updated are powered on for as long as possible during the eviction phase. Note: this action is necessary for all vital changes to AD to be pushed to all systems in the environment prior to reconnection and also to verify that all systems are rebooted. This action is especially tricky given that many user endpoints are not connected 24/7 due to remote work. Organizations may want to look at “jailing” systems that connect in this way into minimal virtual local area networks (VLANs) until they can be verified to have received and implemented updates and any other mitigations (endpoint detection and response [EDR] agents, patches, antivirus definitions, specific scans, etc.) decided on by the organization.
- Agencies using Microsoft Defender for Endpoint or Microsoft 365 Defender should refer to Microsoft: Use attack surface reduction rules to prevent malware infection for more information on hardening the enterprise attack surface.
- Identify federation model for on-premises resources to cloud trust relationship and identify adversary activity in Microsoft 365 (M365)/Azure environment.
- Identify the Source Anchor for Azure AD Connect in the current Azure Tenant, if used. (This is required in order to sever the connection and restore later).
- Run Sparrow or similar tools to identify permission and credential changes to applications and service principals. Identify overly permissive applications, unusual credentials in applications, or modifications to federation trust settings. Refer to CISA Alert AA21-008A: Detecting Post-Compromise Threat Activity in Microsoft Cloud Environments for more information.
- Review M365 tenant configuration and perform a cloud security assessment for administrative accounts and applications. Specifically, review all accounts with privileged access and each application to determine if the rights and credentials are as intended and still necessary. This assessment should include shared trusts or identity relationships with third-party cloud service providers (CSPs) in which the identity is a resident on the CSP’s tenant but is also capable of performing actions in the organization’s M365 environment.
Eviction Phase
Note: to effectively the APT actor, the following steps should be completed fully and in the order listed. These steps may affect operations of critical business functions. CISA recommends agencies conduct a thorough risk assessment prior to starting eviction so that potential impacts on critical business functions are documented and understood. Given that these steps are complex, CISA also encourages agencies to use third-party help to support eviction efforts if needed.
- Sever the enterprise network from the internet.
Note: this step requires the agency to understand its internal and external connections. When making the decision to sever internet access, knowledge of connections must be combined with care to avoid disrupting critical functions.
-
Reset the Kerberos Ticket Granting Ticket account (krbtgt).
Note: krbtgt must be reset twice; the second time after the first has finished. The resets may take a long time to propagate fully on large AD environments. For more information, refer to Microsoft guidance: AD Forest Recovery – Resetting the krbtgt password.
-
Eradicate known malware/backdoors/implants discovered during pre-eviction steps.
Note: this can be done while waiting for the krbtgt resets to complete.
-
Apply network device mitigations identified in CISA Alert AA20-352A: Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organization.
For network devices managed by the SolarWinds monitoring server, the running firmware/software should be checked against known good hash values from the network vendor. CISA recommends that, if possible, organizations re-upload known good firmware/software to managed network devices and perform a reboot.
Note: be sure to wait until krbtgt reset completes to avoid interrupting the reset.
-
Unenroll any suspicious MFA Tokens. Audit all MFA tokens configured in your environment, especially those used for remote access. Unenroll any tokens that cannot be accounted for or are suspicious.
-
Rebuild and reimage systems.
Note: agencies should do an impact assessment for endpoints to determine if they need to be reimaged. An agency should identify (1) credentials observed on compromised machines as at risk and (2) any subsequent system accessed from the corresponding accounts as compromised. Consider:
- Was the endpoint altered by a known malicious actor action? If yes, reimage the system.
- Was data on the endpoint accessed but the endpoint shows no sign of being altered? If yes, you may not need to reimage the system.
-
Regain control of the AD and ADFS, by instituting Local Administrator Password Solution (LAPS), PAWs, and modified administrative accounts.
- Re-establish control of the ecosystem items that were most easily manipulated by the attacker. Start with the “lowest hanging fruit,” i.e., items that are low risk to operations, low administrative overhead, that do not require new skill sets to control. These actions block the most frequently used attack methods on a network. Refer to the Microsoft and Center for Internet Security joint presentation Critical Hygiene for Preventing Major Breaches for more information on prioritizing controls with the largest return on investment.
- Audit the privilege levels of accounts that were utilized on affected SolarWinds Orion servers. Consider only granting the minimal rights and accounts needed to function, following Just Enough Administration (JEA) principles. (Refer to Microsoft: Just Enough Administration for more information.)
- Ensure there are unique and distinct administrative accounts for each set of administrative tasks. Enforce the principle of least privilege. Remove all accounts that are unnecessary; remove privileges not expressly required by an account’s function or role. Institute a group policy that disables remote interactive logins, and use Domain Protected Users Group.Ensure there are unique and distinct administrative accounts for each set of administrative tasks. Enforce the principle of least privilege. Remove all accounts that are unnecessary; remove privileges not expressly required by an account’s function or role. Institute a group policy that disables remote interactive logins, and use Domain Protected Users Group.
- Enforce MFA for all administrative accounts and functions.
- Create and establish PAWs for administrative accounts and mandate use for administrative functions (AD Administrators first, at minimum).
- Enable unique local administrative accounts (e.g., LAPS) and a management function for those accounts. Note: for LAPS, if the endpoints are cloned, each individual endpoint’s local administrative account password needs to be changed afterward to enforce uniqueness.
- Rotate all the Secrets.
- Rotate secrets associated with remote access MFA token generation.
- Reset passwords for:
- All AD accounts with elevated privileges (such as administrators)
- All AD service accounts
- Directory Services Restore Mode (DSRM) account on domain controllers
- All AD accounts
- Accounts with suspicious activity or whose credentials existed on compromised systems, such as affected SolarWinds servers
- Any account where Smartcard/Personal Identity Verification (PIV) is not enforced (which are on an exception or similar exemption)
Note: the New Technology LAN Manager (NTLM) hashes of smartcard/PIV-enabled accounts can be used in pass-the-hash attacks and should be refreshed regularly. For more information, including guidance and scripts on rolling over these hashes, refer to the National Security Agency (NSA) Information Assurance Advisory: Long-Lived Hashes for AD Smartcard Required Accounts, NSA Cyber’s GitHub page on Pass the-Hash Guidance, and Microsoft: Passwordless Strategy.
- All AD user accounts
- All Windows local administrative accounts (including those that are renamed, especially those not managed by LAPS in environment)
- Non-AD application privileged accounts (e.g., elevated accounts on systems that are not joined to AD; some high value assets (HVAs) may fall into this category)
- Network device administrative accounts
- Non-AD HVA user accounts
- Change all credentials being used to manage network devices, including keys and strings used to secure network device functions (Simple Network Management Protocol [SNMP] strings/user credentials, IPsec/IKE preshared keys, routing secrets, TACACS/RADIUS secrets, RSA keys/certificates, etc.). Monitor for failed logins resulting from these resets.
- Sever Azure environment from on-premises, and conduct M365/Azure remediation.
- Evaluate IdP sources. Harden SSO features. (See FireEye’s white paper, Remediation and Hardening Strategies for Microsoft 365 to Defend Against UNC2452). Turn on advanced logging and establish a privileged access management (PAM) baseline (expected privileged account state) for cloud environments.
- Harden the Azure AD Connect Service. (See Trimarc Security’s post, Securing Microsoft Azure AD Connect).
- Review and adjust federation trust relationships. Note: Microsoft recommends severing federation trusts between on-premises networks and the cloud; organizations should migrate to an external IdP or use Azure AD to manage users and, if the latter, users should be “mastered” from Azure AD. Revoke unauthorized or unnecessary federation trusts if maintaining a federated identity solution. (CISA recommends avoiding federated enterprise environments whenever possible.) For more information review the following resources.
- Fully isolate your M365 admin accounts. Activities in this step include, but are not limited to (1) creating cloud-only administrators, controlled appropriately with role based access control (RBAC) and MFA, and (2) monitoring, in an automated fashion, any changes to the established baseline or unusual use. See the following resources for more information (Note: CISA will be releasing guidance on cloud remediation and hardening following dissemination of this guidance).
- After remediating privileged identities (step d), revoke all existing M365 tokens.
- Double check to ensure no on-premises accounts have administrative privileges in M365.
- Review and sanitize (i.e., remove unwelcome actions) compromised mailboxes using industry standard tooling and service portal manual review.
- Review, and adjust accordingly, Tenant settings and configurations. Use publicly available or open-source tools such as CrowdStrike Reporting Tool for Azure (CRT) and Hawk to review Tenant settings. Refer to CISA Alert AA21-008A: Detecting Post-Compromise Threat Activity in Microsoft Cloud Environments.
- Use tools—such as Sparrow or Azure AD Investigator—to review existing Azure applications. Remediate applications that have been compromised. Refer to CISA Alert AA21-008A: Detecting Post-Compromise Threat Activity in Microsoft Cloud Environments.
- Perform IdP review and eviction.
- Clear DNS cache on all servers, workstations, and non-Windows systems.
- Reduce the “Domain member: Maximum machine account password age” in Group Policy to 2–3 days during eviction; it can be set back to the default 30 days after eviction is complete. This will hasten the resetting of the Computer object passwords. For more information, refer to Microsoft: Machine Account Password Process.
- Reboot all servers and workstations, especially those joined to the AD.
- Verify eviction steps have been properly completed.
- Have all the tasks above been completed on all applicable systems and accounts? Note: CISA highly recommends implementing a process to verify you have completed each task.
- Have the endpoints that were not completely mitigated been removed from network communication, pending their completion?
- Have you applied all critical and high patches to the endpoints that lack them, especially any that needed re-imaging?
- Have you added enhanced visibility and monitoring capabilities for cloud environments—such as telemetry for cloud environments—into existing agency security information and event management (SIEM) technology?
- Have you implemented monitoring capability for highly privileged cloud identities and Service Principals?
Post Eviction
- Report to your senior leadership completed pre-eviction and eviction actions as well as those remaining to be completed; provide leadership an assessment of the risk remaining, including assumed residual risk.
- Reconnect to the internet. Note: the decision to reconnect to the internet depends on senior leadership’s confidence in the actions taken. It is possible—depending on the environment—that new information discovered during pre-eviction and eviction steps could add additional eviction tasks.
- Create an actionable and accountable plan for integrating the next 60 days of Active Directory privilege credential baselining guidance (i.e., completing the next step). Note: this next step has high overhead and will likely disrupt business operations; agencies must have a plan for testing breaks associated with the changes to administrative control schemes and will need to alter their policies and procedures to accommodate these disruptions.
- Establish and control baseline mechanisms for administrators. Note: this step should be completed over the next 60 days. While completing this task, agencies should move on to the next step.
- Implement PAWs for remaining administrative accounts.
- Perform additional hardening of administrative accounts.
- Implement Credential Guard. (Refer to Microsoft: Manage Windows Defender Credential Guard for more information). Introducing Credential Guard as an endpoint tool can be challenging for organizations due to hardware restrictions, but the impact on privileged identity credential management is significant. Chief information security officers (CISOs) should prioritize identity-focused solutions for immediate action.
- Restrict RDP usage to an exclusive list of necessary administrators and from only dedicated administrative workstations (such as PAWs) and identified necessary alternative locations. RDP access should be judiciously and carefully scoped and monitored.
- Establish time bound and temporal escalated Domain Privileges (require second factor for elevation and that access expires).
- Implement JEA for domain controller access and maintenance.
- Harden/reduce attack surface of domain controllers. Remove connection to the internet whenever possible, and remove all unnecessary protocols, services, and accounts (in accordance with the principle of least functionality). Consider implementing Windows Server Core for all domain controllers.
- Integrate detection mechanisms that focus on endpoints and changes to privileged identity sources. Solutions include pervasive use of endpoint security (such as the Microsoft Defender Suite of services, including Endpoint and Identity) as well as high value identity monitoring solutions. The view of user behavior should be unified across all platforms and behavioral analytics should be enabled. Note: behavioral analytics (with an understanding of what traditional administrative activity consists of, and what tools are used for it) combined with frequency analysis of activity is often the only avenue for network defenders to detect anomalous activity.
- Report to CISA. Post-eviction, all Category 3 agencies should report to CISA actions taken, any actions left incomplete, and their assessments of the residual risk. Following dissemination of this guidance, CISA will release a checklist to the Homeland Security Information Network (HSIN) for agencies to use to complete the steps in this guidance. Agencies should fill out and submit the checklist to CISA.
- Maintain vigilance. In the hours, days, and weeks after the network’s internet connection is restored, the agency’s detection capability will be important in verifying that all threat actor activity within the enterprise has stopped. Extended vigilance is necessary because this threat actor has demonstrated extreme patience with follow-on activity.
- Agencies should ensure their security operations center (SOC) has capabilities for enhanced visibility and monitoring of enterprise network and cloud environments. Refer to SolarWinds and Active Directory/M365 Compromise: Detecting APT Activity from Known Tactics, Techniques, and Procedures for known TTPs that agencies should look out for as part of network and environment monitoring.
- Configure endpoint forensics and detection solutions for aggressive collection; prioritize this by value of asset and account.
Frequently Asked Questions
Does my organization have to complete all the steps in this eviction guidance?
In accordance with ED 21-01: Supplemental Direction Version 4, agencies with networks that used affected versions of SolarWinds Orion and have evidence of follow-on threat actor activity, such as binary beaconing to avsvmcloud[.]com and secondary command and control (C2) activity to a separate domain or IP address, must execute and complete the pre-eviction phase of this guidance. Agencies that find additional adversarial activities must execute and complete the eviction and post eviction phases of this guidance. Conducting all of the steps in this guidance is necessary to fully evict the adversary from applicable networks. Failure to perform comprehensive and thorough remediation activity will expose enterprise networks and cloud environments to substantial risk for long-term undetected APT activity.
Is there a time limit to completing the eviction activities?
In accordance with ED 21-01: Supplemental Direction Version 4, agencies subject to the requirements must complete the applicable phases in this eviction guidance by July 16, 2021, or within 90 days of discovery of follow-on threat activity after issuance of ED 21-01 Supplemental Direction Version 4.
Given that severing the enterprise network from the internet will have significant operational impact, does the organization need to take all its endpoints offline?
If the affected organization can authoritatively and comprehensively identify compromised internet-connected endpoints, identities, and systems and is able to take those offline without affecting uncompromised or non-internet connected systems, then the agency does not need to disconnect non-compromised endpoints or non-internet-connected systems. This will still disrupt C2 activities while allowing the agency to keep as much of the system up as possible. Note: access to environments with pervasively compromised credentials will frequently appear to be standard user activity, as it will use “native” services and identities.
Will CISA provide agencies new TTPs in the event of a reinfection?
Refer to SolarWinds and Active Directory/M365 Compromise: Detecting Advanced Persistent Threat Activity from Known Tactics, Techniques, and Procedures for reinfection TTPs and corresponding detection artifacts.
Will CISA provide architectural recommendations for future rebuilds?
This current guidance is tailored to provide short-term remediation steps for agencies to evict this adversary from compromised on-premises and cloud environments and protect networks against additional compromise. CISA will be releasing long-term enterprise architecture and security operations guidance that incorporates updated credential/access management, monitoring, and detection guidance for a more secure, resilient federal enterprise.
May 13, 2021: Initial Version
by Contributed | May 14, 2021 | Technology
This article is contributed. See the original author and article here.
I recently encountered a scenario recently where I was looking to do a quick technical check on some advice I was giving to another member of the community regarding PowerShell – especially capturing the output of PnP PowerShell commands and store in a text file. When I responded to the tweet, I was away from my computer, but I did have my iPad (with keyboard) with me and wanted to see if I could use PnP PowerShell with Azure Shell – you may have guessed the result by – YES you can.
I was not using best security practice at the time to log in (username/password), which would not work if I had MFA on the account (which I should have ☹). I will include better practice configuration to include certificates and an Azure AD App in this article.
What you will need
So, let’s get started; you will need a few things to get going,
- Azure Subscription – this is necessary for a storage account that preserves your files between sessions and is mandatory for Azure cloud shell to work.
- Azure Resource Group – the grouping of resources in Azure
- Azure KeyVault – to store a certificate for a secure connection to M365 services.
- PnP PowerShell – the newest PnP power shell module, this article uses v1.5.0
- Permissions to consent an app as this uses an Azure AD app for the authentication.
- Windows Machine – for creating the app and certificate.
- If setting up services locally by PowerShell, then install the Az module.
Setting Up
There are a few tasks we are going to do to set up working with Azure Shell, Azure AD App and Certificates.
Activate Azure Shell
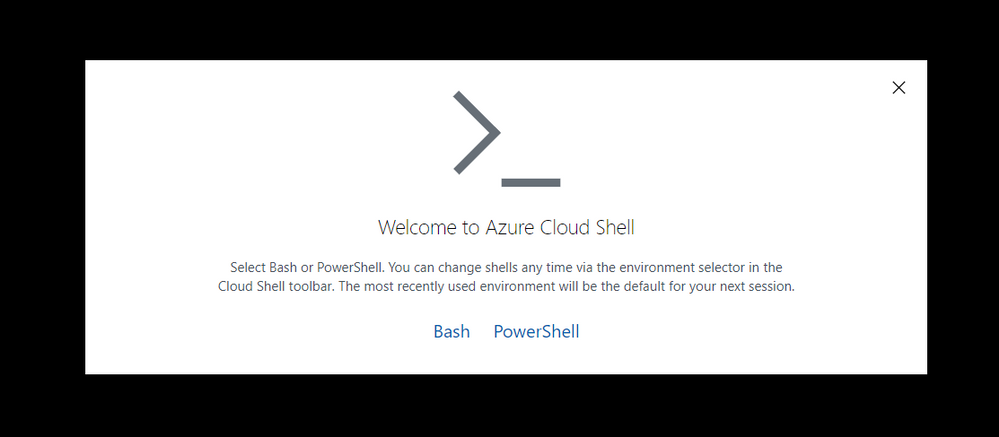
First, let’s go ahead and activate the Azure Shell; we will use this to set up the required resources as well:
Navigate to https://shell.azure.com or click on the icon in the Azure Portal.
Then run through the first setup of the Azure Shell:
 Welcome screen Azure Shell
Welcome screen Azure Shell
Select PowerShell. Then run through the first setup of the Azure Shell:
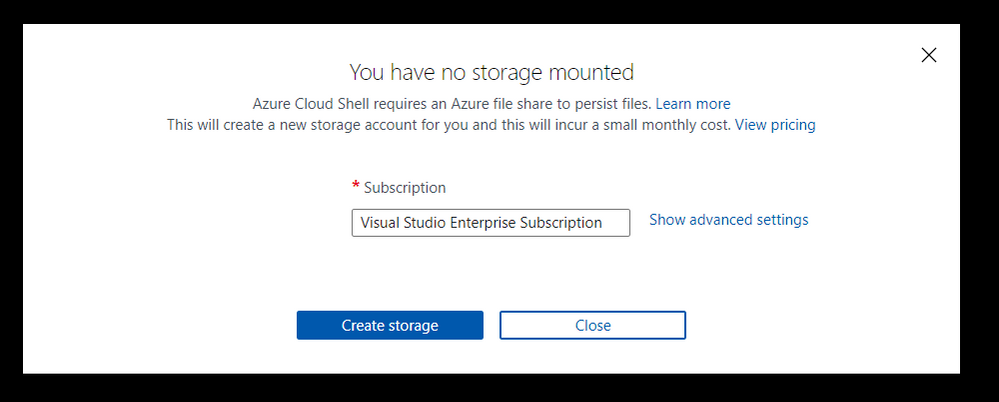 Simple setup screen for storage
Simple setup screen for storage
If you choose “Create storage” at this point, then this will set up the storage account and resource group for you, using Azure’s naming standards and region. If you want to specify:
- Subscription
- Region
- Resource Group
- Storage account
- File share name
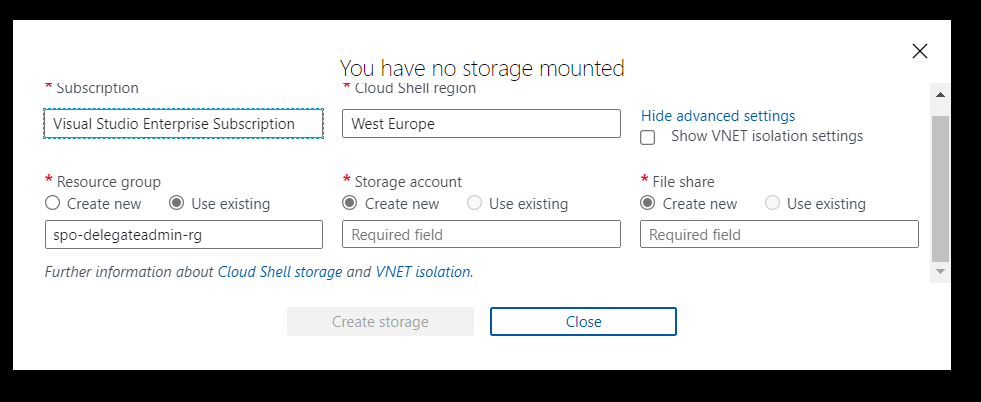 Azure Shell Advanced Setup
Azure Shell Advanced Setup
Then select Advanced settings. I like to name resources myself in a standard manner. For this article, I am going to use the advanced options and specify:
- Region: “North Europe”
- Resource Group Name: “azure-cloud-shell”
- Storage Account: “pkbtenantcloudshell”
- File Share: “pkbtenantcloudshellfiles”
Note: the naming of some of these resources is very strict, e.g., 3 -24 characters, no spaces, lowercase.
Click “Create Storage”
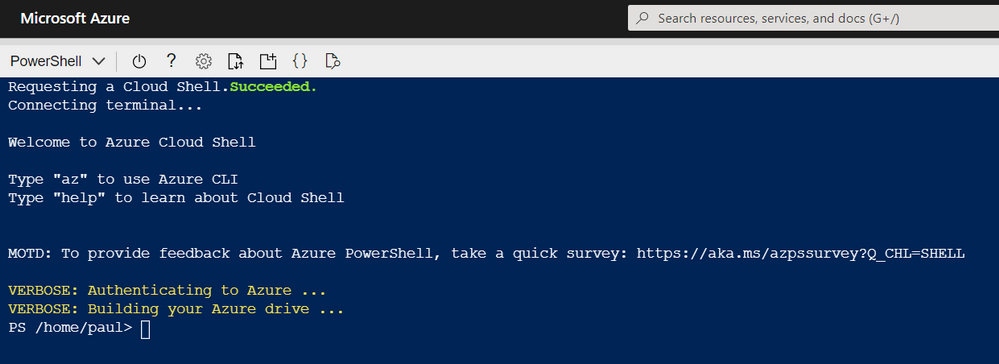 Azure Shell – Setup Complete
Azure Shell – Setup Complete
Now the Azure Shell is ready to use.
Installing PnP-PowerShell
Next, we need to install the PnP PowerShell module in Azure Cloud shell, enter:
Install-Module -Name PnP.PowerShell
The great thing about Azure Cloud Shell is the installation is persistent between sessions, so you will only have to do this once. However, you will need to upgrade the module periodically.
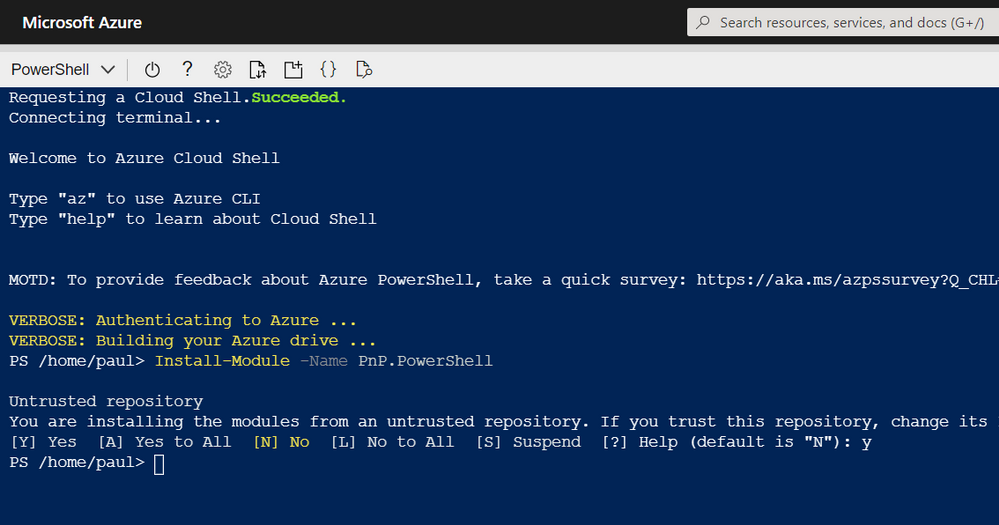 Azure Shell – Install PnP PowerShell
Azure Shell – Install PnP PowerShell
For information on installing PnP-PowerShell, check out the documentation site for more details: https://pnp.github.io/powershell/
Create a KeyVault
Next, we want somewhere secure to store a certificate – Azure KeyVault.
A KeyVault is a secure method of storing keys, secrets and certificates. We intend to keep the certificate used for this setup in the vault. Another benefit of using this method, in larger organisations, where other teams manage apps or the security aspect of the tenant, they can set up this vault and retain control over the certificate and app creation.
You can, if you prefer, navigate to the Azure Portal and use the marketplace to create a new KeyVault resource; check out this quick start guide.
OR set this up in Azure Cloud Shell run the following commands:
Firstly, to check that the service is available in your preferred region, run the following:
New-AzKeyVault -VaultName 'pkbtenant-keyvault' -ResourceGroupName 'azure-cloud-shell' -Location 'North Europe'
Then, provision a new KeyVault (if you have one already, then skip this step) and give yourself access to Secrets and Certificates.
Set-AzKeyVaultAccessPolicy -VaultName 'pkbtenant-keyvault' -UserPrincipalName 'paul.bullock@tenant.co.uk' -PermissionsToCertificates All -PermissionsToSecrets All
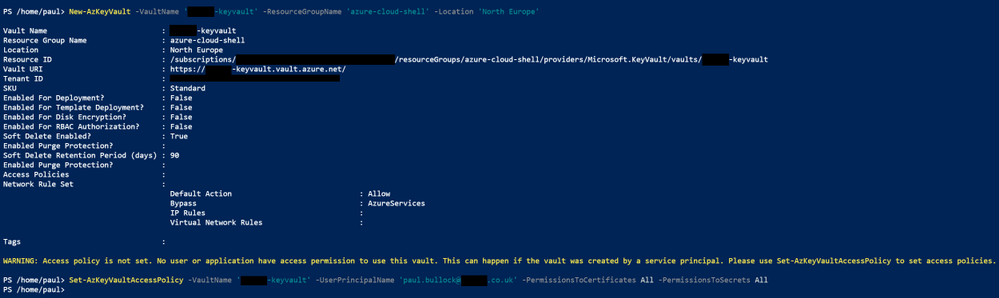 Azure Shell – Create KeyVault
Azure Shell – Create KeyVault
Please refer to the documentation if you want to be more specific around the KeyVault – Azure Portal | PowerShell.
We will be importing a certificate in a later section.
Create Azure AD App with Register-PnPAzureApp
There are a few options when setting up the authentication to connect with PnP PowerShell:
- Azure AD App – using your app (recommended), which will use the APPLICATION permissions, meaning the connection will use the permissions the app does.
- PnP Management Shell – the multi-tenant app PnP provides – this uses DELEGATE permissions meaning the connection will need to log in as the user and will only have access to services THE user has access to.
If you need clarification on the difference between the types of permissions, I highly recommend checking out an awesome community call demo from Philippe Signoret, Program Manager of the Microsoft Identity team: https://youtu.be/_BfI4L7j1Po
So why are use an Azure AD app? Using the Azure Shell restricts some authentication options when connecting to services with PnP PowerShell, such as interactive login, because it cannot display a pop-up window.
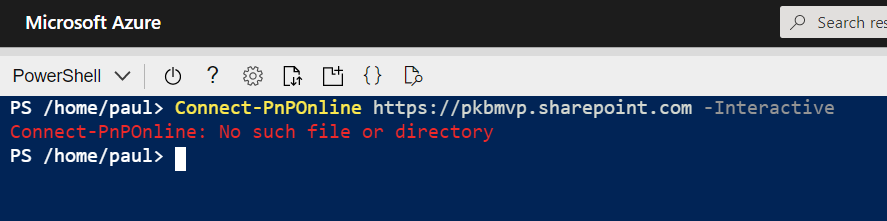 Azure Shell – doesn’t support interactive login
Azure Shell – doesn’t support interactive login
The “-PnPManagementShell” parameter is an option; this uses the device login method BUT will require you to navigate to another site/page to authenticate, including going back to grab the code – then enter your login credentials further steps if MFA is enabled. IMHO feels a bit cumbersome to do this each time I want to do a task in the Shell, especially on an iPad/phone.
Create an Azure AD App
To set up the app quickly with PnP PowerShell, you need to use a Windows machine to run the cmdlet “Register-PnPAzureApp” which generates the certificate, creates the Azure AD app, sets API permissions, will pop up to consent to the app permissions.
Note: you may have to install the PnP PowerShell locally if you do not already have it.
To set up the app, run the following command using the PnP PowerShell cmdlet:
$result = Register-PnPAzureADApp -ApplicationName "PnP PowerShell Azure Shell Access" -Tenant yourtenant.co.uk -OutPath . -DeviceLogin -ValidYears 2 -CertificatePassword (ConvertTo-SecureString -String "yourpassword" -AsPlainText -Force)
$result #output the result – Specifically grab the AzureAppId/ClientId – you will need this later
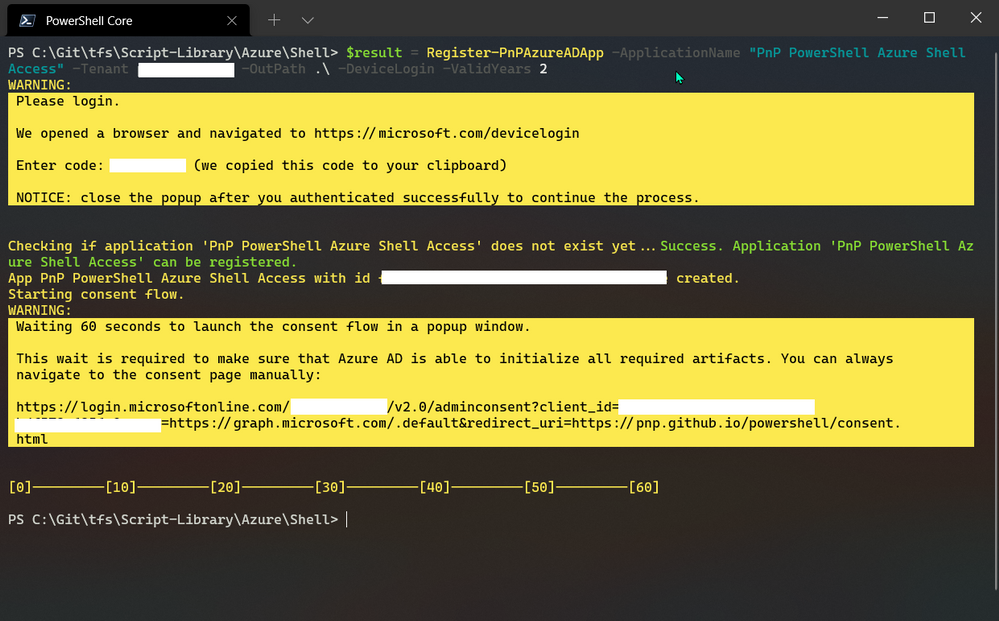 PowerShell – Registering Azure App
PowerShell – Registering Azure App
During this operation, two windows will pop-up to authenticate with the device login method and consent to the app permissions.
If you want to check the app in Azure AD, navigate to: https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps and find the app called “PnP PowerShell Azure Shell Access”
Note: This app uses the minimum API permissions (APPLICATION) as the default; if you want to perform operations with groups or flow as an example, you will need to add these permissions to the app.
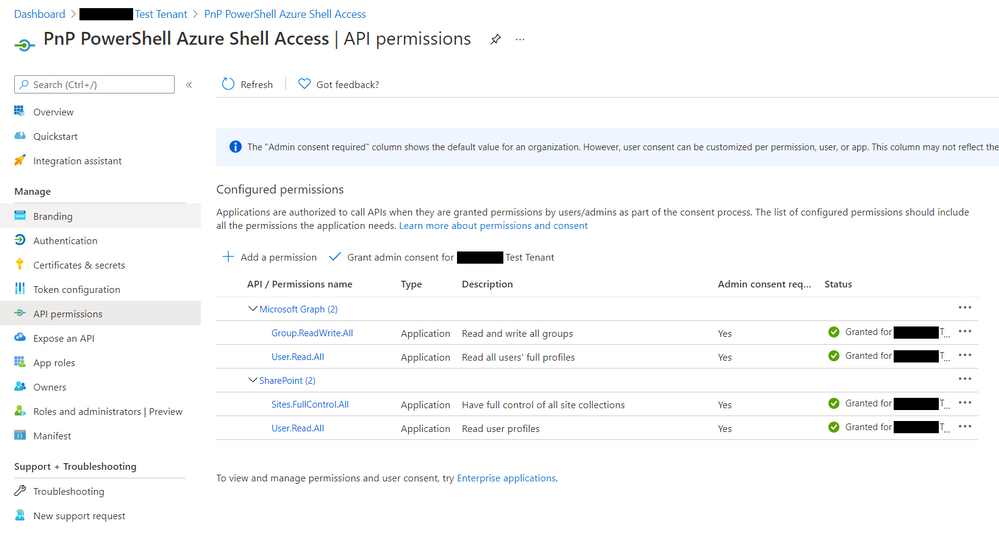 Azure App – API permissions
Azure App – API permissions
For more details on generating the app, check out the authentication section of the documentation.
Adding Certificate to KeyVault
Now that we have the app setup, we need to upload the certificate to the KeyVault.
Navigate to the KeyVault in the portal
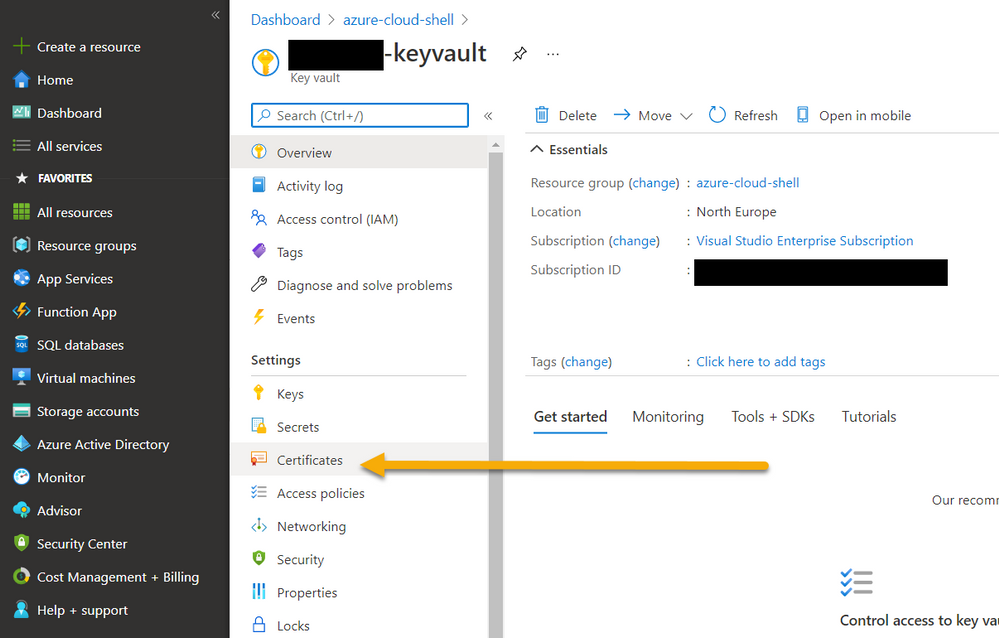 Azure KeyVault – Navigating to Certificates
Azure KeyVault – Navigating to Certificates
- Select “Import”
- Enter a name “azureshell-pnpps-connection”
- Select the generated certificate “PnP PowerShell Azure Shell Access.pfx”
- Enter the certificate password
Click Create
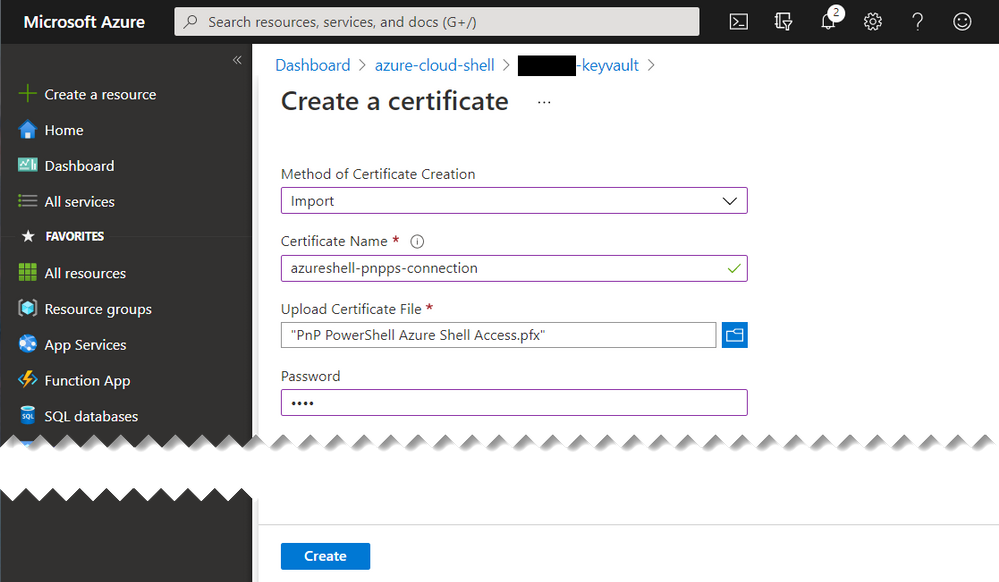 Azure Key Vault – Upload Certificate
Azure Key Vault – Upload Certificate
This is ready to use in a later section.
Reducing the time to get going on new sessions
When I start the Azure Shell, I want to minimize the number of lines, to connect to the services securely and get going quickly.
Parameter Splatting
Parameter splatting is a method to pass a collection of parameters for a PowerShell command into a variable and apply this to the cmdlet you intend to run. Example:
Get-NiceMessage -Param1 "good" -Param2 "morning" -Param3 "community"
# Splatting alternative
$MyParams = @{
Param1 = "good",
Param2 = "morning",
Param3 = "community"
}
Get-NiceMessage @MyParams
This will save time if you repeatedly apply the same parameters on the cmdlets, reducing the time to write the command and your scripts cleaner to read. To read more about this PowerShell feature, check out the documentation.
PowerShell Profiles
Interestingly, I did not know about this feature until the MOTD message appeared on the Azure Shell. I wanted to understand this further so dug deeper and I have managed to find a way to create a startup script that will make it easier to connect to Office 365.
With profiles, we can setup a script to run when the Azure Shell is started, so this is an awesome opportunity to add all of the connection information when the Shell starts including retrieval, of the certificates from the KeyVault.
To create a profile that is used across sessions but for your user account use:
# Create Profile
mkdir (Split-Path $profile.CurrentUserAllHosts)
New-Item -ItemType File -Path $PROFILE.CurrentUserAllHosts -Force
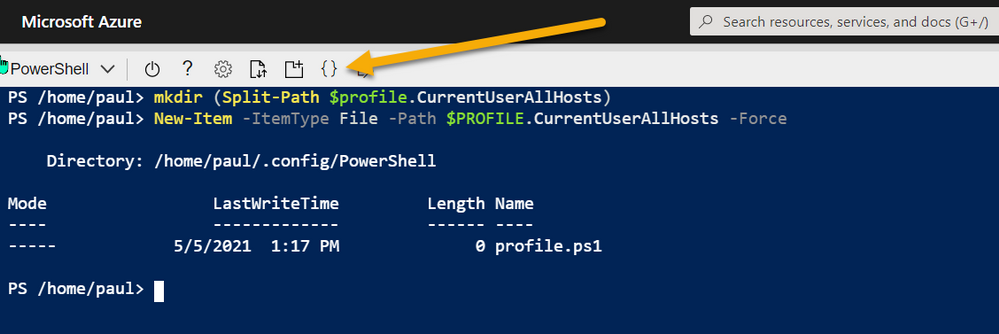 Azure Shell – Setup Profiles
Azure Shell – Setup Profiles
Once created, you can open an editor in the path above to the new profile script location.
Then using the following example, using a combination of parameter splatting and profiles, you can setup everything you need to connect to the service:
# Connect to KeyVault Data
try{
$vaultName = "pkbtenant-keyvault" # Replace with your KeyVault name
$appName = "PnP PowerShell Azure Shell Access"
$appId = (Get-AzADApplication -DisplayName $appName).ApplicationId
$tenantId = (Get-AzContext).Tenant.Id
$certName = "azureshell-pnpps-connection"
$baseSite = "https://tenant.sharepoint.com" # Replace with your tenant
$base64Cert = Get-AzKeyVaultSecret -VaultName $vaultName -Name $certName -AsPlainText
# Use of parameter splatting
$ConnectInfo = @{
ClientId = $appId
CertificateBase64Encoded = $base64Cert
Tenant = $tenantId
}
Write-Host "Ready to connect to M365/SharePoint" -ForegroundColor Green
}catch{
Write-Host "Failed to get the KeyVault data" -ForegroundColor Yellow
}
Editor – Ctrl-S (Save) then Ctrl-Q (Quit)
Restart Shell
After setting up the profile, reboot your Shell and you should see a prompt to indicate the prerequisites are ready to use for a connection (green text).
To learn more about profiles check out the documentation for profiles.
Connecting to the service
Once you have all these elements setup, you can connect with PnP PowerShell with one short line:
Connect-PnPOnline @ConnectInfo https://tenant.sharepoint.com
# -OR-
Connect-PnPOnline @ConnectInfo $baseSite
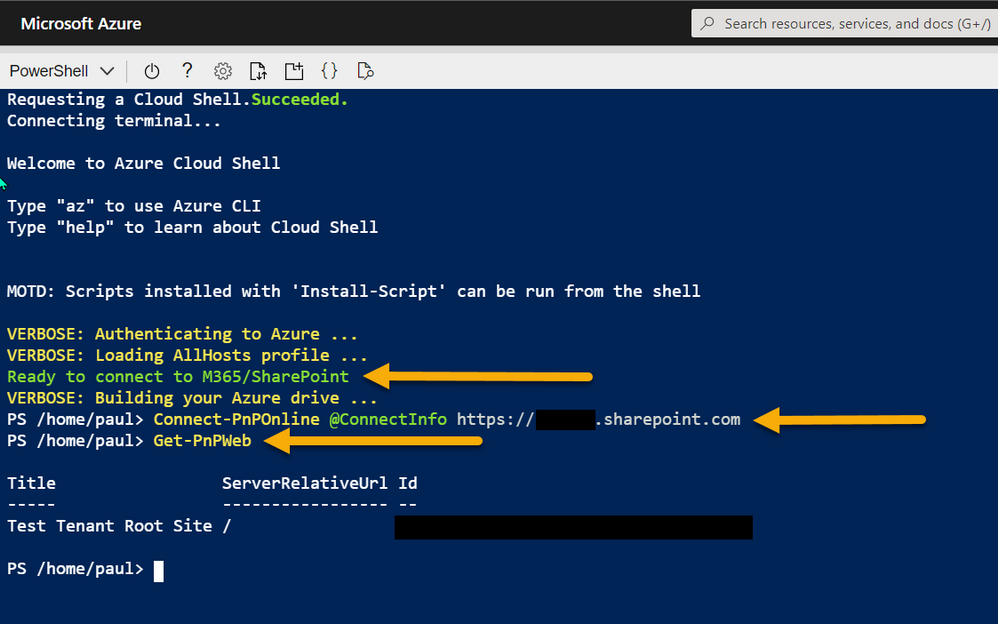 Azure Shell – connecting with PnP PowerShell
Azure Shell – connecting with PnP PowerShell
The settings are persistent across sessions/devices (like an Azure app on iPad), so once setup, you can open Azure Shell and reconnect to the service and make the changes in the Shell quickly.
Btw, at the beginning I mentioned about capturing the output to the text file, this is particularly useful if you are grabbing a lot of info in your session or need to show the changes you made, here is how to do it:
Start-Transcript "log.txt"
Get-PnPWeb
Stop-Transcript
This will save the file to the current location in the Azure Shell. Use Export-File to download it, or the UI button.
Enjoy!




























Recent Comments