RDCMan v2.8, AccessChk v6.14, Process Monitor v3.83, Strings v2.54, Sysmon v13.22 and TCPView v4.13
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
Organizations use a wide array of tools to connect apps and processes together, including frameworks that automate other apps. To support these kinds of scenarios, we are pleased to announce the availability of the Microsoft 365 E3: Unattended License! This is a new license option for Office apps, which allows usage of Office client apps with service accounts or other non-user accounts, which is common for when executing automation processes. These processes may be unattended during their operation; whereas, leveraging traditional user accounts when running automation processes while unattended is not recommended. IT admins deploying new or existing solutions that leverage this new license can choose to use update Office apps via the Semi-Annual Enterprise Channel or Monthly Enterprise Channel updates. For pricing and availability information, contact a Microsoft sales representative or your reseller.
It is important to note that this license for unattended use does not change the behavior or functionality of Office apps. They are generally designed to operate as end-user apps and will have known limitations in unattended use cases. For example, the Office user experience may occasionally feature new updates to its user interface that can change the behavior of broader automation processes. As we work to improve overall accessibility of the products, the ordering and behavior of accessibility capabilities may change in ways that impact broader usage in automation workflows. These various updates and changes are part of improving the product for a broad audience, but may at times, inhibit fully predictable unattended automation of Office apps.
Additionally, Office apps are not specifically designed for unattended usage at scale. For more details, check out this helpful support article about unattended automation of Office. If you are considering building new unattended processes, consider these factors and guidelines for Office products outlined in the article.
Where possible, we recommend that automation processes leverage product Application Programming Interfaces (API), such as Microsoft Graph to drive products wherever possible. Microsoft Graph features hundreds of APIs for accessing relevant organizational data, including files, mail, calendars, and much more. For example, extensive APIs with Microsoft Excel allow for the use of workbook models and calculations with custom cell inputs in broader apps.
The new Microsoft 365 E3: Unattended License provides new flexibility for a growing number of scenarios involving automation processes. As you consider new scenarios for unattended automation, this license can provide a new option for working with productivity data and tools, and we hope you explore the broader capabilities that Office within this scenario can provide.
These are the requirements for using Microsoft 365 Apps for enterprise with unattended RPA:
For steps on how to enable RPA, check out this helpful Microsoft Docs article.
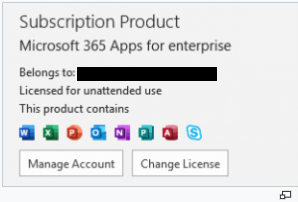
Once you’ve activated the license, you can verify this directly from any Microsoft 365 Apps for enterprise app by going to File > Account. Here’s a screenshot of an example:

Or, you can you find it under, “%LocalAppData%MicrosoftOfficeLicenses5Unattended.”
To deploy the Microsoft 365 E3: Unattended License to devices, you simply purchase the required number of Microsoft 365 licenses and assign a license to a user in the Microsoft 365 admin center. To enable this functionality on a device, use the group policy
for currently installed devices or the applicable command in the command prompt window.
If user is signed in, but there is no RPA entitlement (license) associated with an account, the user will see the following message in the Office app:
To learn more about unattended RPA with Microsoft 365 Apps for enterprise, click here.
Continue the conversation by joining us in the Microsoft 365 Tech Community! Whether you have product questions or just want to stay informed with the latest updates on new releases, tools, and blogs, Microsoft 365 Tech Community is your go-to resource to stay connected!
This article is contributed. See the original author and article here.
By: Marc Swinnen, Dir. Product Marketing, Semiconductors, Ansys and Andy Chan, Director, Azure Global Solutions, Semiconductor/EDA/CAE
What is Ansys RedHawk-SC?
Modern semiconductor integrated circuits (IC), or chips, can contain over 50 billion transistors and would be impossible to design without the help of software tools grouped under the Electronic Design Automation (EDA) category that support, automate, and verify every step of the chip design process.
RedHawk-SC is an EDA tool developed by Ansys that is the market leader for power integrity and reliability sign-off. This is a vital verification step in the design process for all semiconductor designs. Sign-off algorithms are extremely resource-intensive requiring hundreds of CPU cores running over many hours, making it an ideal application for cloud computing.
Designed for the Cloud
RedHawk-SC was architected on a cloud-friendly analysis platform called Ansys SeaScape™. RedHawk-SC’s SeaScape database is fully distributed and thrives on distributed disk access across a network. RedHawk-SC distributes the computational workload across many “workers”, that have low memory requirements – less than 32GB per worker. Each CPU can host one or more workers. This elastic compute architecture allows for instant start as soon as just a few workers become available.
The distribution of the computational workload is extremely memory efficient, allowing the optimal utilization of over 2,500 CPUs. There is also no need for a heavy head node because the distribution is orchestrated by an ultra-light scheduler using less than 2GB for even the largest chips. The same is true for loading, viewing, or debugging results.
RedHawk-SC Workloads on Azure
EDA applications like RedHawk-SC have specific requirements for optimal cloud deployment. We can summarize these considerations with the following points:
Ansys and Microsoft have worked together to evaluate the performance of realistic RedHawk-SC workloads on the Intel-based Azure cloud instances and how to optimally configure the hardware setup.

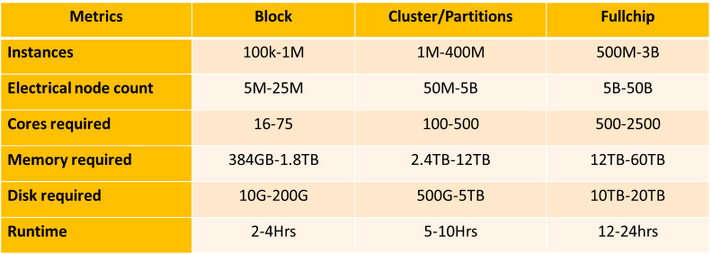
Table-1: RedHawk-SC resource requirements for representative small “Block” workloads, medium “Cluster/Partition” workloads, and large “Full Chip” workloads
Table-1 list the resources required to run RedHawk-SC on a variety of workload sizes. They range from verifying just a small section, or ‘block’, of a chip to full chip analysis.
Cloud Compute Models for EDA
Microsoft worked closely with Ansys to develop finely tuned solutions for RedHawk-SC running on Azure’s high-performance computing (HPC) infrastructure. These targeted reference architectures help ease the transition to Azure and allow design teams to run faster at a much lower cost.
IC design companies may choose to contract with cloud providers like Azure under an “all-in” model where the entire design project is conducted in the cloud or may look for a “hybrid” use model where cloud resources complement their existing in-house capacity (Figure-1).
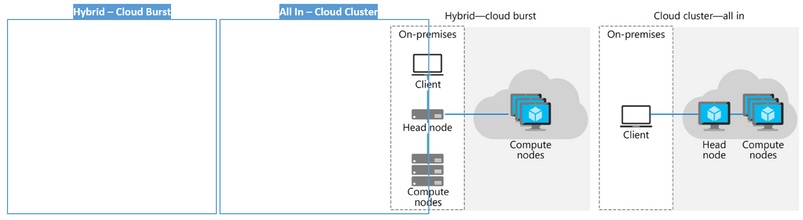
Figure-1. Hybrid versus all-in model with both the head and compute nodes in the cloud.
Ansys and Microsoft Azure have verified that RedHawk-SC successfully accommodates both “all-in” and “hybrid” use models and licensing.
Azure infrastructure optimized for EDA
To achieve the fastest possible runtimes, companies typically start by investing in processors that support the highest clock speed available. Additionally, the cloud poses other efficiency considerations such as datacenter efficiency and workflow architecture. Benchmarks show that storage in the cloud is a high-impact architectural component, as are scale technologies.
Azure’s new Intel processor-based FXv1 Virtual Machine instances were designed specifically for compute intensive workloads with high memory footprints and looked to be an ideal fit for the demand of RedHawk-SC. Not only does FXv1 offer high clock speeds up to 4.1GHz, but it also has low-latency cache and up to 2TB of NVMe local disk that has the high IOPS throughput desired by RedHawk-SC. RedHawk-SC also takes advantage of Intel’s Math Kernel Library when running on Intel processors.
Through extensive testing with these realistic workloads, Microsoft and Ansys have recommended an optimized hardware configuration for running RedHawk-SC on Azure in Figure-2 (below) The Azure Silicon team selected the following infrastructure to power this test:
Azure’s Accelerated Networking provides high bandwidth 50GbE ethernet connectivity between the workers with Smart NICs to offload networking tasks from the CPUs, thus increasing computational throughput. CycleCloud cloud-scaling was used to support RedHawk-SC in orchestrating dynamic VM deployment.
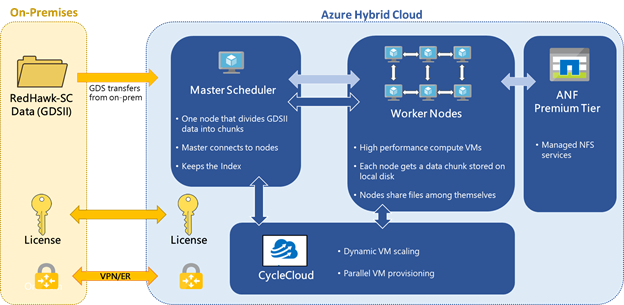
Figure-2: Reference architecture for running Ansys RedHawk-SC on an Azure hybrid cloud
Testing of FXv1 running RedHawk-SC with a large, full chip workload (Graph-1) shows near-linear runtime scaling as the number of CPUs is increased. The favorable scaling reflects the efficient distribution technology underlying RedHawk-SC’s SeaScape architecture as well as the optimized high memory per core offered by FXv1
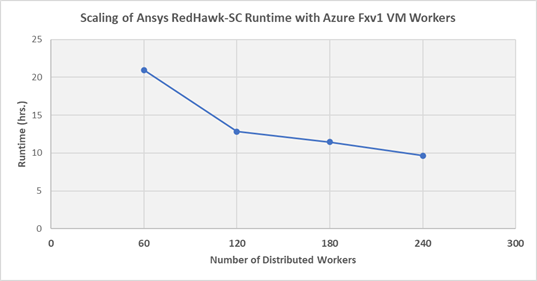
Graph-1: Runtime required to run various RedHawk-SC workloads on Microsoft Azure’s FXv1 VM as a function of the number of workers
In a surprising finding from Graph-1, the total cost of running a RedHawk-SC job on Azure actually decreases as you increase the number of workers (up to the optimum threshold). This contradicts the commonly held assumption that the total cost will increase as you enlist more CPUs. The reason for this is the very high CPU utilization RedHawk-SC can achieve. The optimal number of workers is equal to the number of power partitions automatically calculated by RedHawk-SC.
This result is not intuitively obvious and indicates that customers should not try to reduce the CPU count to save money. In fact, they should actually increase their CPU count to the optimal value to achieve lower cost and a faster runtime.
Conclusion
Extensive testing of RedHawk-SC on Azure has allowed Microsoft to optimize the FXv1 VM configuration powered by Intel processors for cloud-based EDA work. This configuration has demonstrated excellent scalability to over 240 CPUs running on a range of realistic and very large EDA workloads. The testing further identified the optimal number of CPUs to minimize the total cost for running RedHawk-SC on Azure. The result is that customers can easily set up their power integrity signoff analysis jobs on Azure with optimal configurations for both throughput and cost.
For further information contact your local sales representative or visit www.ansys.com
This article is contributed. See the original author and article here.
In case you missed it….. we had a vibrant conversation with Microsoft Yammer MVPs, Amy Dolzine and Melanie Hohertz, and other customers on ways to build engagement in your Yammer networks. This was an interactive discussion with over 45 folks from across the globe.
Here’s the recording.
We’ve pulled together some highlights and best practices that’s shared below.
We’ve shared previously how important leaders are to the community and the Yammer network. We started by discussing the merits of the upcoming Post on Behalf of (POBO) feature, authenticity, and how to use it to get your leaders involved.
Related resources for Leadership Engagement
Use other social media platforms to harvest new ideas! There’s something about how and why things are viral, how can you adapt it to your community and culture. It’s easier to contribute to the familiar, so take cues from the social networks around you and see what resonates with you.
Related Resource:
You can set up All Company to be a strategic tool for your organization! Make a stand. Either restrict it or don’t but come up with some governance.
Related resources:
Related resource:
Related Resources:
Thanks for joining us!
Stay tuned for more customer conversations in the upcoming months.
This article is contributed. See the original author and article here.
While the increase in work-from-anywhere capabilities have been crucial to enabling productivity, they can be met with concerns from Security Operations (SecOps) teams around data protection and governance. Employees need to have frictionless collaboration, both inside and outside the company, as well as being empowered to access internal resources from endpoints outside organization boundaries. With organizational data and files roaming across devices, apps, and services, IT admins and SecOps teams must ensure it remains protected and meets the organization’s security and compliance requirements. An effective security and compliance strategy protects people, data, and endpoints across the organization without restricting end user productivity.
Data protection and governance is critical for organizations – it helps keep sensitive business information from being improperly shared while also ensuring external compliance obligations are met. To formulate a robust data protection and governance strategy, business stakeholders need to adequately assess both internal and external data requirements. For many organizations, this means involving IT, SecOps, legal, human resources, apps and tooling, and various other teams to ensure all stakeholders have shared any data handling requirements they operate under. This effort can be complex and challenging to understand how to create strong internal security standards, while meeting external compliance obligations without impacting end user productivity. In this blog, we’ll discuss some helpful tips on how to take advantage of data protection and governance across Microsoft 365 to meet your business needs.
Encryption is a key component to protecting files and organizational information, but it’s important to understand the details of how encryption works. Encryption by itself doesn’t prevent content interception. Organizations need to have a larger data protection strategy to ensure only authorized parties can use the encrypted data. Encryption can, and more importantly should, co-exist in multiple layers operating at the same time – such as encrypting both the email message and the channel it flows through. Different layers of encryption can help achieve different business goals, such as safeguarding sensitive content or helping meet regulatory obligations. A robust business strategy uses multiple layers of encryption together enabling the business to meet both internal and external data protection requirements.
Microsoft uses industry standard technologies such as Transport Layer Security (TLS) and Secure Real-Time Transport Protocol (SRTP) to encrypt all data in transit between users’ devices and Microsoft datacenters, and between Microsoft datacenters. Data in transit includes, mail messages in the process of being delivered, files shared and in transit between users, and conversations in online meetings. Microsoft also helps keep data safe by encrypting it while at rest in Microsoft datacenters, starting with volume-level encryption enabled through BitLocker while service encryption ensures that content at rest is encrypted at the application layer. In order to help organizations meet security and compliance obligations, data encrypted at rest in Microsoft datacenters is done in a way that enables organizations to decrypt the content if needed. On top of our standard encryption in transit and at rest, Microsoft also provides additional encryption solutions and layers that customers can manage and control to ensure security and compliance requirements are met.
One of the top questions we hear from organizations is – what type of encryption does my organization need? The answer depends on many factors, such as the type of business information being handled, sensitivity of the data, industry or regional requirements, and even internal standards. While the answer may seem complex, Microsoft provides a portfolio of encryption and compliance solutions that help businesses meet their data protection and governance needs while being in full control. Let’s dive into how Microsoft supports customers with additional security and compliance needs.
Customer Key is built on service encryption, providing a layer of encryption at the application level for data-at-rest and allows the organization to provide and control the encryption keys used to encrypt customer data in Microsoft’s datacenters. Customer Key assists customers in meeting regulatory or compliance obligations for controlling root keys. After providing the keys, the organization can create a data encryption policy (DEP) and assign it to encrypt the following data for all tenant users:
For customers currently using Customer Key for Exchange Online and SharePoint, data encryption policies add broader control and now includes support for Microsoft Teams! You can create multiple DEPs per tenant, but only one DEP can be assigned at a time. When a DEP is assigned, encryption begins automatically, but will take some time to complete depending on size of the tenant.
For more details on using Customer Key for tenant-level encryption, please see the following articles:
Customer Lockbox is a solution that provides an extra layer of control to customers by offering the ability to give explicit access authorization for service operations. This additional control can help customers meet certain compliance obligations, such as Health Insurance Portability and Accountability Act (HIPAA) and Federal Risk and Authorization Management Program (FedRAMP), and supports requests to access data in Exchange Online, SharePoint, and OneDrive. A foundational principle of Microsoft 365 is that the service operates without Microsoft access to customer content. However, a Microsoft engineer may need access to customer content when the customer makes a support request. While issues are usually fixed through extensive telemetry and debugging tools, some cases may require a Microsoft engineer to access customer content to determine the root cause and fix the issue. Customer Lockbox requires the engineer to request access from the customer as a final step in the approval workflow, giving organizations the option to approve or deny these requests and providing direct-access control to the customer. Customer Lockbox is included with Microsoft 365 E5 subscriptions and can be added to other plans.
Organizations need to be able to manage risk in communications to protect company assets and identify concerning content that may violate internal code of conduct standards. Communication Compliance is an insider risk solution in Microsoft 365 that helps minimize communication risks by helping detect, capture, and act on inappropriate messages within the organization. Communication Compliance helps organizations remain compliant with regulatory requirements and detect internal violations without disrupting the business.
Communication Compliance policies can assist with detecting policy matches in several important compliance areas, such as corporate policies, risk management, and regulatory compliance. IT admins can take advantage of pre-defined policies or build custom policies to detect violations in both internal and external communications covering email, Microsoft Teams, Yammer, or even third-party communications. Since there may be a separation of duties between IT admins and the team that manages organizational compliance, Communication Compliance supports the separation between configuration of policies and the investigation of messages through rules based access controls.
Microsoft recently announced some exciting new Communication Compliance capabilities, including a deeper integration with Microsoft Teams. In accordance with helping customers meet privacy and compliance obligations, strong safeguards and controls are built into the solution by default on all the new features highlighted in the article above. This includes items like, pseudonymization, rules-based access control, admin explicit opt-in of users, and audit trails.
 Selection of optical character recognition to extract printed or handwritten text from images
Selection of optical character recognition to extract printed or handwritten text from images
Available in the Microsoft 365 Compliance Center for all Microsoft enterprise customers, Compliance Manager helps simplify compliance and reduce risks. Compliance Manager translates complex regulatory requirements to specific controls, and through compliance score, provides a quantifiable measure of compliance. It offers intuitive compliance management, a vast library of scalable assessments, and built-in automation. Customers can see step-by-step implementation guidance, recommended solutions to implement controls, and the controls with most impact – empowering them to act quickly to improve their organization compliance. Customers can select from 300+ out-of-box assessments for common industry, regional, and global standards and regulations, or create custom assessments to meet specific organizational needs. Compliance Manager is available for all Microsoft 365 customers – get started today!
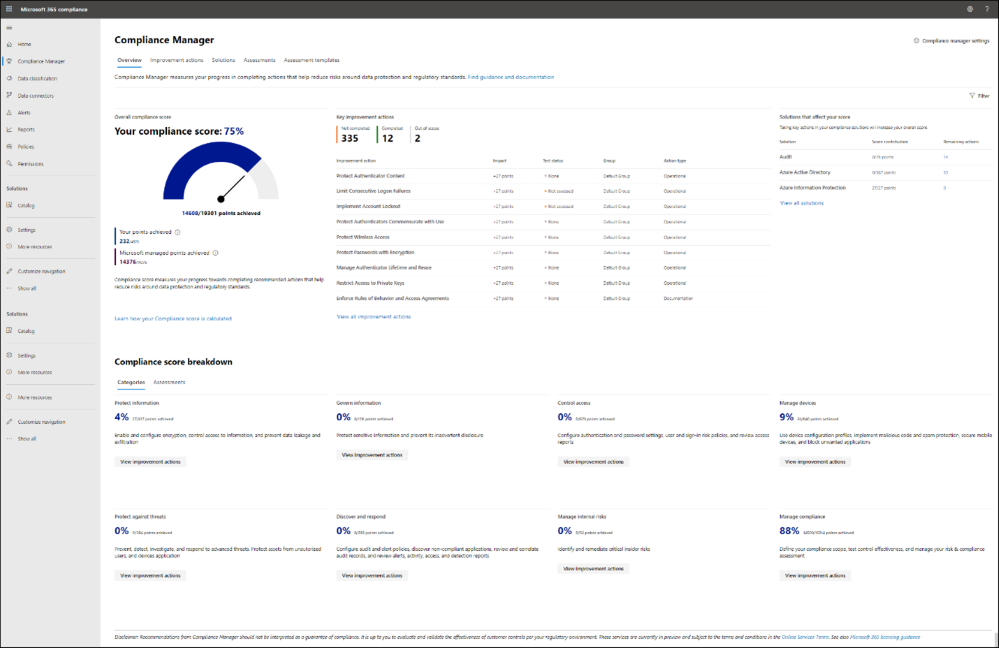 Compliance Manager dashboard
Compliance Manager dashboard
As previously mentioned, encryption is a component of a larger data protection strategy that should include using multiple encryption layers working in parallel. Part of an effective data protection and governance strategy includes safeguarding sensitive business information by classifying and protecting content itself. Office 365 Message Encryption (OME) and sensitivity labels are a core part of Microsoft Information Protection, enabling organizations to protect organizational data without interrupting end user productivity.
Sensitivity labels help protect content in Microsoft 365 apps across platforms and devices, third-party apps and services, and even common collaboration containers, like Teams and SharePoint. When a sensitivity label is assigned to content, it acts as a stamp enforcing the conditions of the label wherever the content goes. While a document or email can only have a single sensitivity label applied, they can have both a sensitivity label and a retention label applied to support compliance obligations. Sensitivity labels can be configured to apply watermarks to content, encrypt the content restricting access to specific groups, and protect content in site and group containers. As organizations continue to push the boundaries of external collaboration, another great capability sensitivity labels provide is the ability to restrict access for external members in Teams and SharePoint containers. For instance, the finance department may have a team for internal employees only that has a sensitivity label applied restricting guest access to the team.
Sensitivity labels and message encryption are important tools to help protect sensitive business data and are designed to not disrupt the way end users work. Documents encrypted with sensitivity labels fully support co-authoring across devices and platforms, making it easy to collaborate in encrypted documents in real time. For even greater proactive data protection and governance, organizations with a Microsoft 365 E5 subscription can take advantage of automatic labeling with sensitivity labels to automatically assign a label to content that matches specified conditions.
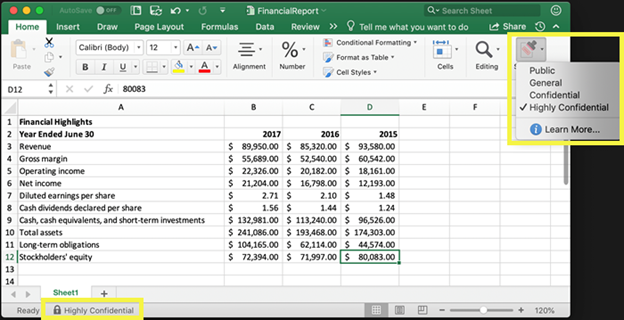 Example of a Highly Confidential sensitivity label applied to an Excel file
Example of a Highly Confidential sensitivity label applied to an Excel file
Microsoft’s encryption in transit and at rest is the service-layer protection needed for most organizations who don’t face key arrangement requirements. Organizations should develop and put in place a content encryption strategy leveraging Microsoft Information Protection to safeguard content. Some additional data protection and governance capabilities customers should consider in their strategy are:
Continue the conversation by joining us in the Microsoft 365 Tech Community! Whether you have product questions or just want to stay informed with the latest updates on new releases, tools, and blogs, Microsoft 365 Tech Community is your go-to resource to stay connected!
This article is contributed. See the original author and article here.
Want a second chance to perfect that family portrait? Need to adjust the colors on your sunset photo? Now you can with OneDrive’s new photo editing features. Starting today you can crop, rotate and adjust the light and color in your photos on OneDrive.1, 2 Plus, we’re launching new ways to organize and view your photos on OneDrive for Android. Our new editing, organization, and viewing features put you in control, so you can take your pictures to the next level and add your own touch of style.
Today is just the start of a number of new enhancements that OneDrive is bringing to photos over the next year, all of which are built on trust and powered by innovation like the rest of your OneDrive experiences. Relentless innovation has made OneDrive a world-class app for file storage, sharing and collaboration. We’re now extending that same commitment to a refreshed photos experience that will enhance the joy you get from your photos. Like always, you can expect that we’ll remain committed to your privacy – we don’t scan your photos, files, or personal content to target ads to you, and we don’t share your data without permission.
Here’s a deeper look at our new editing, viewing, and organization features to help you maximize your photo enjoyment.
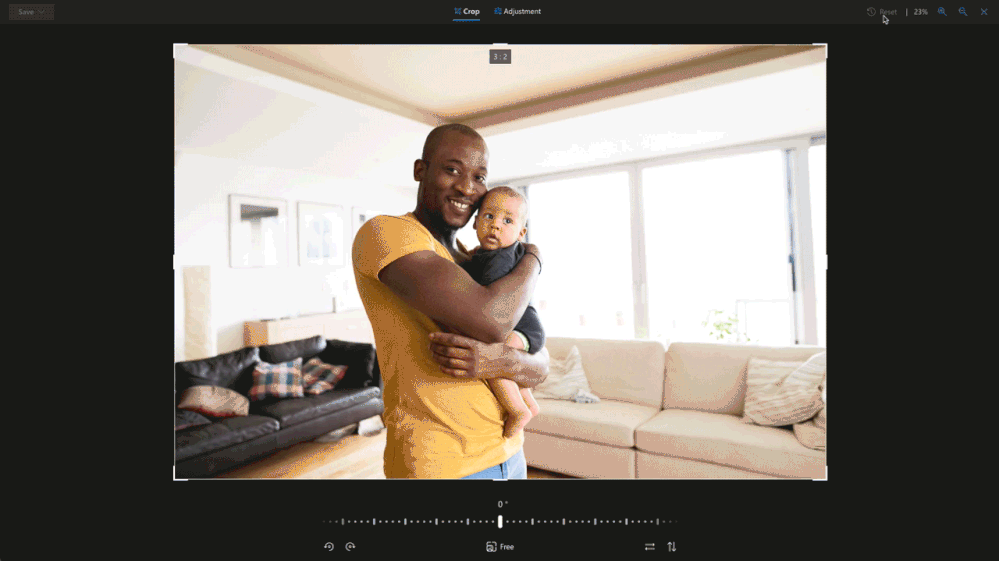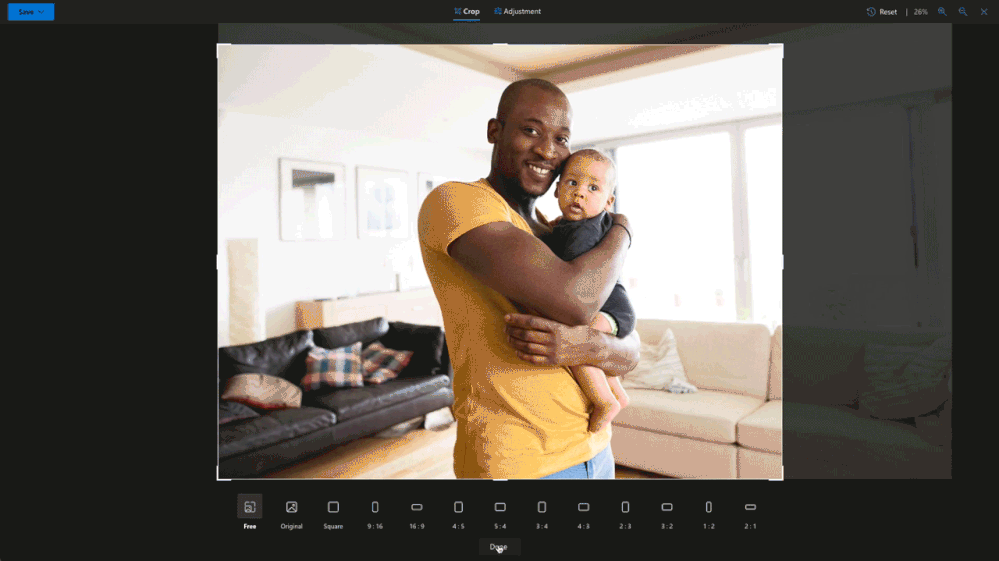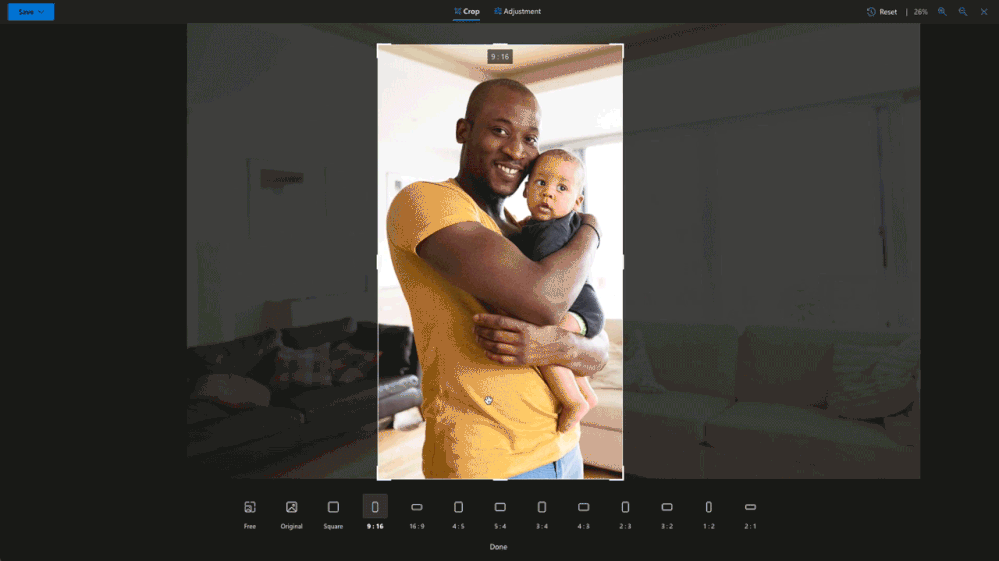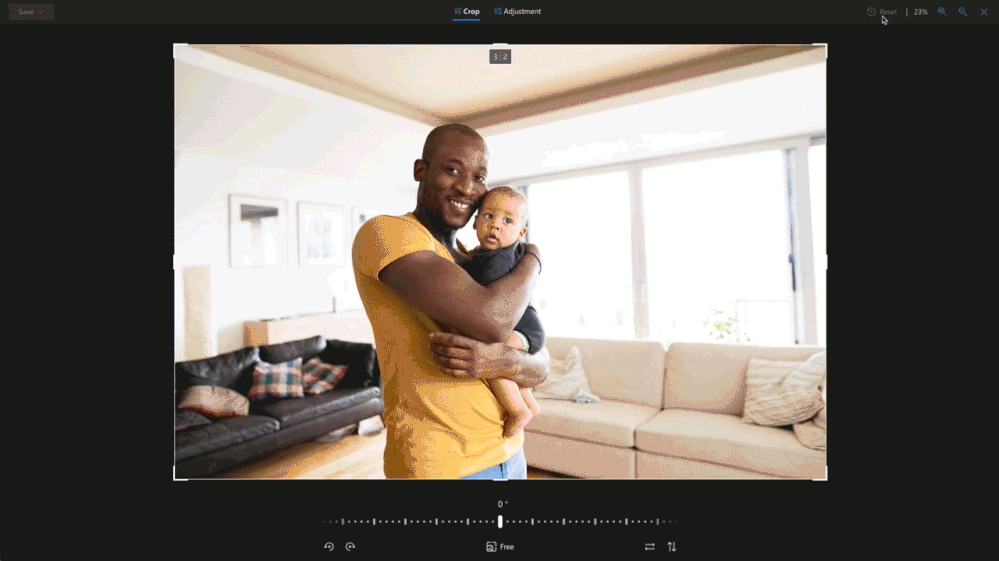
Crop away
Sometimes you just need to trim out unwanted parts of an image to bring more focus to your subject. Now you can easily crop to standard image sizes for your social media apps with our built-in presets, or you can go free-form and crop your image exactly the way you want3. These preset ratios are perfect for when you want to share a picture in your social stories, create a new profile image or even a banner.

Rotate and flip
Our rotation feature makes it simple to rotate left and right by 90 degrees or flip an image by 180 degrees. We’ve also added incremental degree rotation, so you can easily straighten out those slightly tilted pictures. Now you don’t need to tilt your head to view your pictures just the right way.
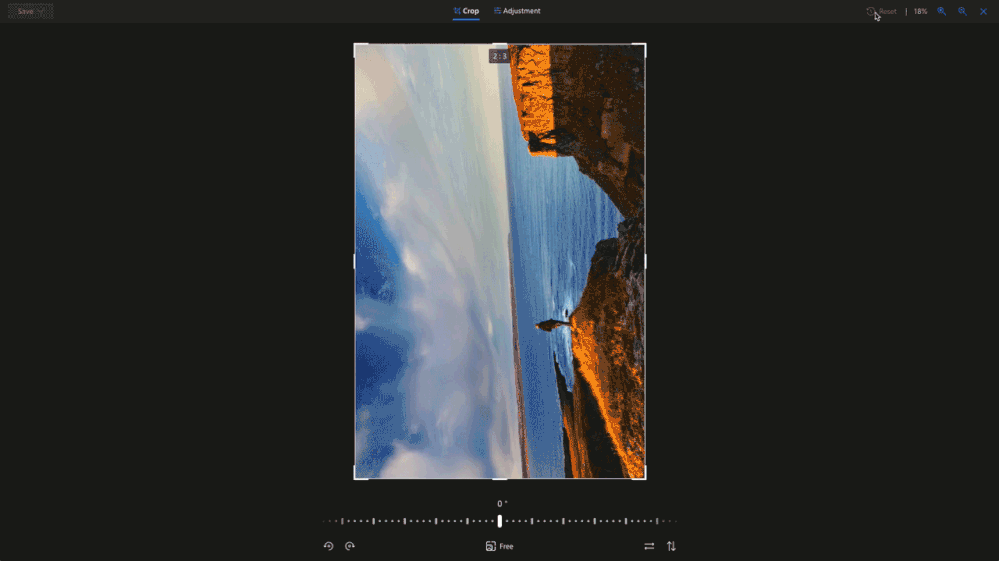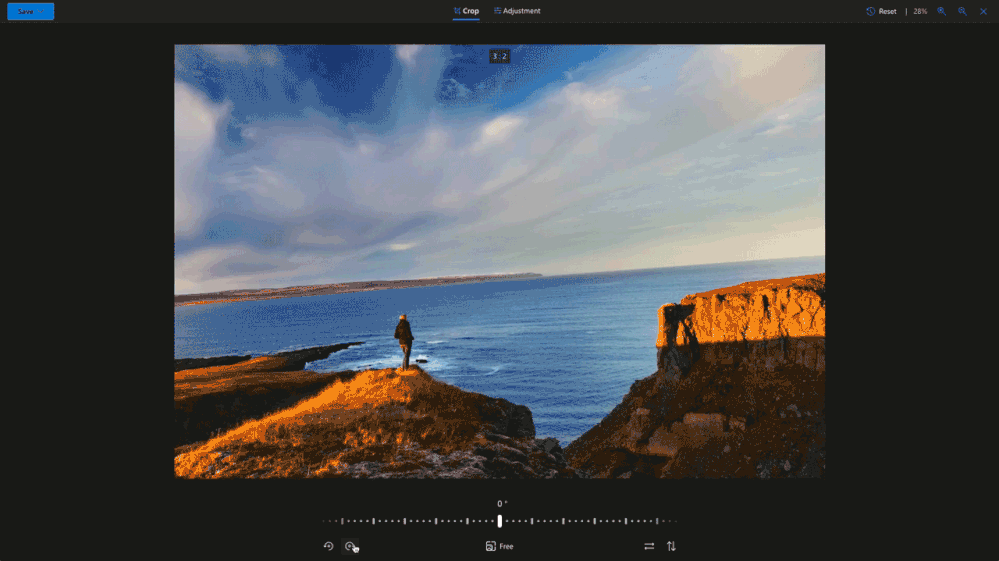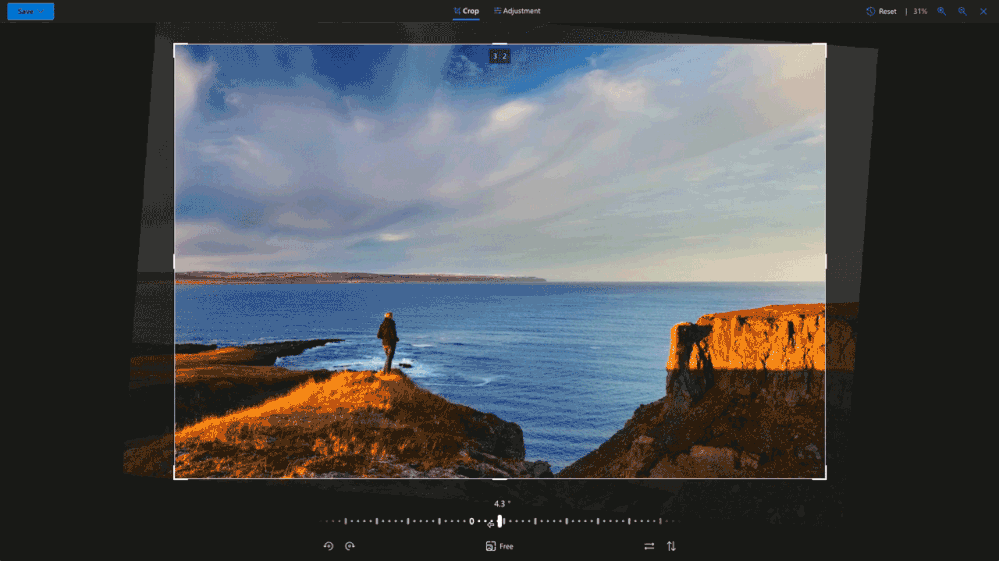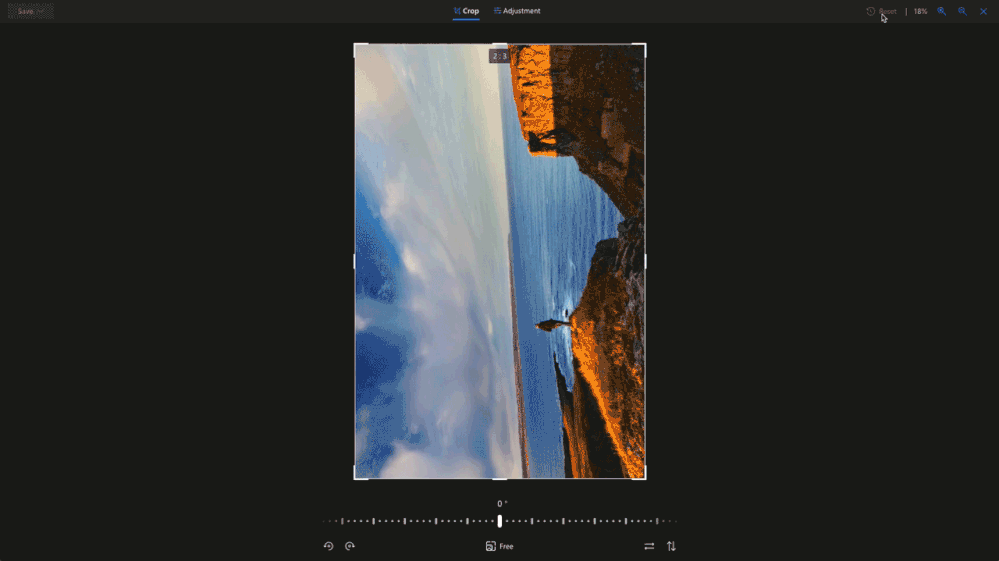
Light and Color Adjustments
Have you ever noticed how satisfying it is to adjust the light and color saturation of your images? There’s no better feeling than watching an image transform from muted colors and low contrast to richly colored and stunning. Now it’s easy to make those transformations with adjustments for brightness, exposure, contrast, highlights, shadows, and color saturation. Once you’re done with the enhancements, admire your artistry by tapping and holding on the image to compare the new version with its original.

When you make edits to photos on OneDrive you’ll have the option to save the changes as a new image or overwrite the original image. And if you accidentally overwrite your original, you can use version history to recover it.
These editing features are now rolling out to OneDrive for Web and OneDrive for Android1. We expect to bring them to OneDrive for iOS later this year. Currently, editing is rolling out for OneDrive personal accounts – we expect to bring these features to OneDrive for work and school accounts this summer.
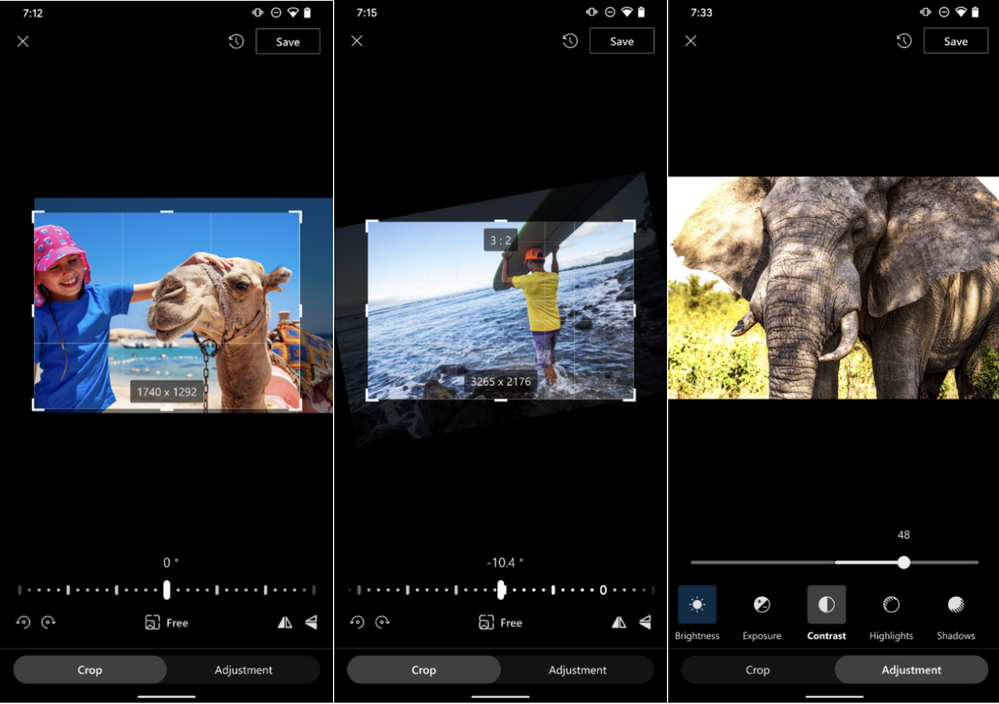 From left to right photo cropping, rotation and light adjustments as seen on OneDrive for Android.
From left to right photo cropping, rotation and light adjustments as seen on OneDrive for Android.
Ready to make your photos picture perfect? Try out these features today. Download OneDrive for Android or open OneDrive for Web.
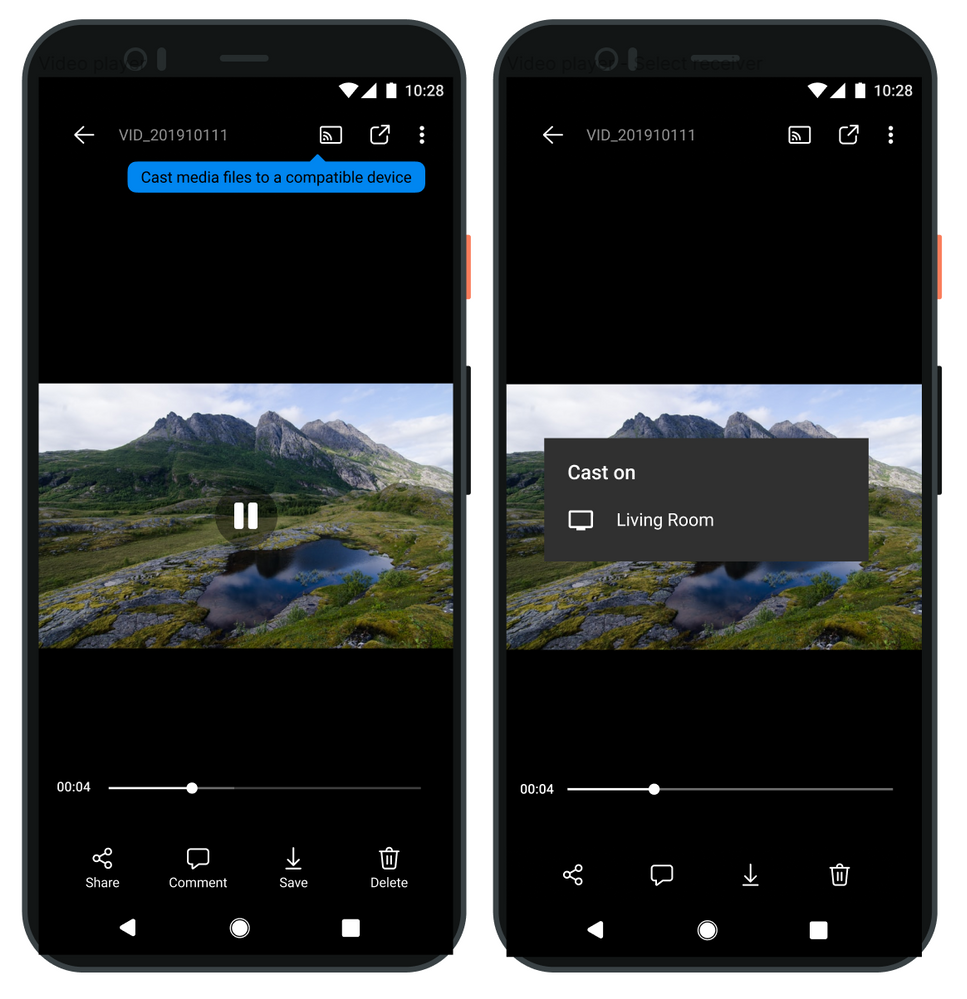
Cast it to the big screen with Chromecast
Now you can enjoy your OneDrive photos and videos in a larger format by displaying them on your TV with Chromecast. To display media files on Chromecast devices, just connect your phone to a Chromecast-enabled device, open the OneDrive for Android app, and tap on the upper right corner of the OneDrive home tab. As you move through photos and videos on your phone, you’ll see them on your Chromecast-enabled TV or device.
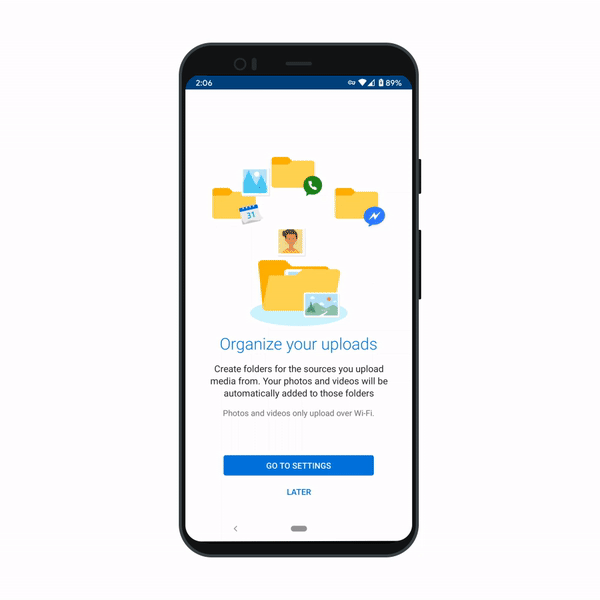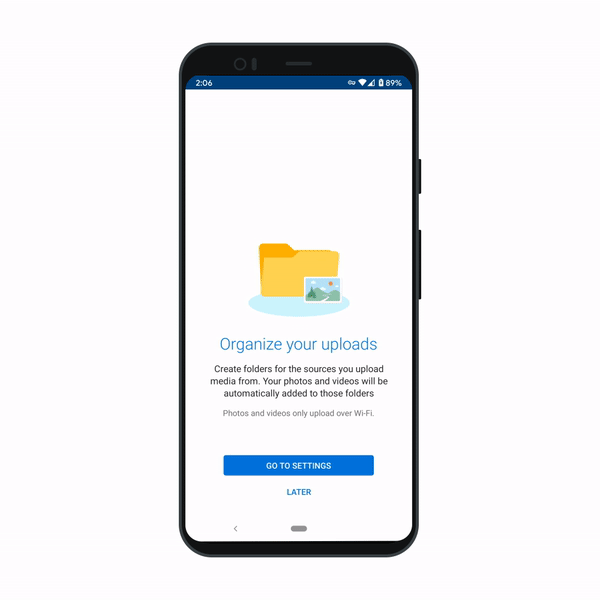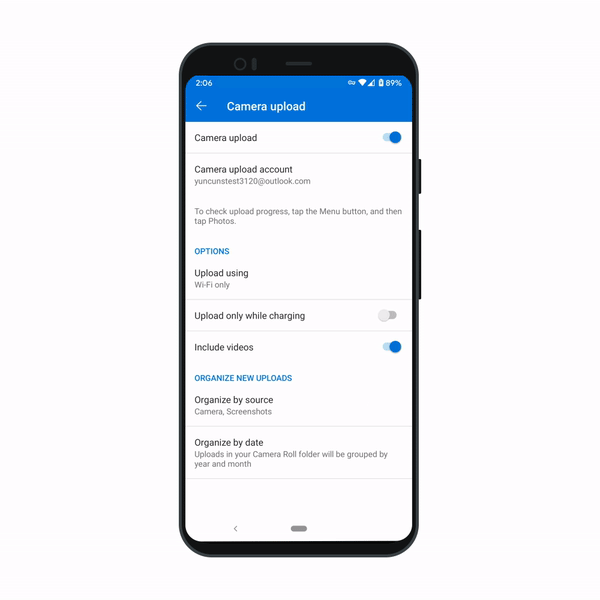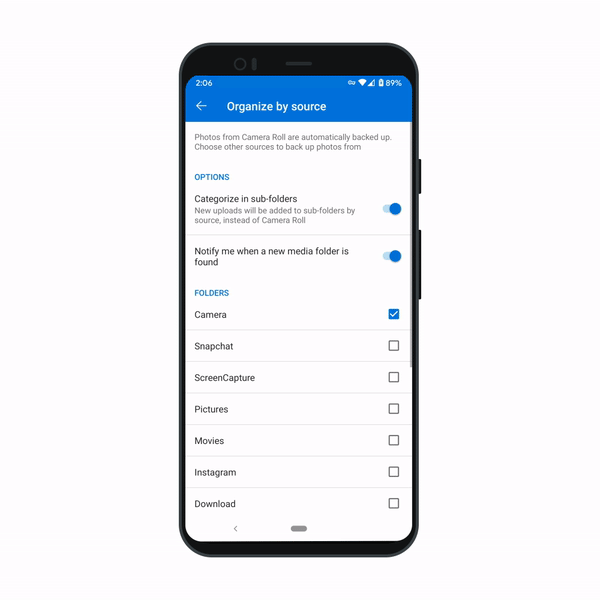
Organize your photos by date and source
We’re making it easy to organize your photos. Many of us save images to OneDrive not just from our phone’s camera, but also from sources like text messages, social media, WhatsApp, and screenshots. To help keep these better organized, we’re soon introducing a new setting that creates folders based on the upload source. Images from those sources are automatically added to their respective folders. And if you like to keep images organized by date, you can group your images by month and year. We expect this feature to ship within the next two months on OneDrive for Android.
Filter your photos
There are times when you only want to see images from your Pictures folder and times when you want to see all the photos in your OneDrive. Whatever the time, now you can filter for it. You can find this new option in the top right of your Photos tab on OneDrive for Android and the photos area of OneDrive for Web.
Let OneDrive protect and organize your photos, so you have time to be you. Download the OneDrive app and turn on camera roll backup today.
1 Photo editing is available on OneDrive for Web and OneDrive for Android (requires Android Version 6.0 or higher and OneDrive app version 6.30 or above).
2Photo editing in OneDrive is currently limited to JPEG and PNG formats.
3 OneDrive’s preset ratios include square, 9:16, 16:9, 4:5, 5:4, 3:4, 4:3, 2:3, 3:2,1:2 and 2:1.
This article is contributed. See the original author and article here.
We just added new APIs in preview in the Azure IoT SDK for C# that will make it easier and more intuitive for device developers to implement IoT Plug and Play, and we’d love to have your feedback.
When we released IoT Plug and Play back in September 2020, we provided the Plug and Play specific helpers functions in the form of samples to help demonstrate the Plug and Play convention e.g., how to format Plug and Play telemetry message, how to ack on properties updates, etc.
As IoT Plug and Play is becoming the “new normal” for connecting devices to Azure IoT, it is important that there is a solid set of APIs in the C# client SDK to help you efficiently implement IoT Plug and Play in your devices. IoT Plug and Play models expose components, telemetry, commands, and properties. These new APIs format and send messages for telemetry and property updates. They can also help the client receive and ack writable property update requests and incoming command invocations.
These additions to the C# SDK can become the foundation of your solution, taking the load off your plate when it comes to formatting data and making your devices future proof. We introduced these functions in preview for now, so you can test them in your scenarios and give us feedback on the design. Your feedback will help us to simplify, streamline and improve these APIs before we make them generally available.
The NuGet package can be found here: https://www.nuget.org/packages/Microsoft.Azure.Devices.Client/1.38.0-preview-001
We have created a couple of samples to help you get started with these new APIs, have a look at:
The API names are aligned with the concepts of the IoT Plug and Play convention, making development more intuitive. With IoT Plug and Play, we use the terminology telemetry, commands, properties and component in place of events, direct method and device twin, so we added these terms in the API name to make them more aligned with the concepts.
For example, we introduced a couple of new types to help with convention operations mapped directly to the IoT Plug and Play concept and terminology. For telemetry, we expose TelemetryMessage that simplifies message formatting for the telemetry, notably when you use component (here thermostat1) in the model:
double temperature = 70.0D;
using var telemetryMessage = new TelemetryMessage("thermostat1")
{
Telemetry = {["temperature"] = temperature },
};
await _deviceClient.SendTelemetryAsync(telemetryMessage, cancellationToken);
For properties, we introduced the type ClientProperties which exposes the method TryGetValue.
With this new type, accessing a device twin property becomes:
// Retrieve the client's properties.
ClientProperties properties = await _deviceClient.GetClientPropertiesAsync(cancellationToken);
// To fetch the value of client reported property "serialNumber" under component "thermostat1".
bool isSerialNumberReported = properties.TryGetValue("thermostat1", "serialNumber", out string serialNumberReported);
// To fetch the value of service requested "targetTemperature" value under component "thermostat1".
bool isTargetTemperatureUpdateRequested = properties.Writable.TryGetValue("thermostat1", "targetTemperature", out double targetTemperatureUpdateRequest);
Note that in that case, we have a component named thermostat1, first we get the serialNumber and second for a writable property, we use properties.Writable.
Same pattern for reporting properties, we have now the ClientPropertyCollection, that helps to update properties by batch, as we have here a collection and exposing the method AddComponentProperty:
// Update the property "serialNumber" under component "thermostat1".
var propertiesToBeUpdated = new ClientPropertyCollection();
propertiesToBeUpdated.AddComponentProperty("thermostat1", "serialNumber", "SR-1234");
ClientPropertiesUpdateResponse updateResponse = await _deviceClient
.UpdateClientPropertiesAsync(propertiesToBeUpdated, cancellationToken);
long updatedVersion = updateResponse.Version;
With this, it became much easier to respond to top-level property update requests even for a component model:
await _deviceClient.SubscribeToWritablePropertiesEventAsync(
async (writableProperties, userContext) =>
{
if (writableProperties.TryGetValue("thermostat1", "targetTemperature", out double targetTemperature))
{
IWritablePropertyResponse writableResponse = _deviceClient
.PayloadConvention
.PayloadSerializer
.CreateWritablePropertyResponse(targetTemperature, CommonClientResponseCodes.OK, writableProperties.Version, "The operation completed successfully.");
var propertiesToBeUpdated = new ClientPropertyCollection();
propertiesToBeUpdated.AddComponentProperty("thermostat1", "targetTemperature", writableResponse);
ClientPropertiesUpdateResponse updateResponse = await _deviceClient.UpdateClientPropertiesAsync(propertiesToBeUpdated, cancellationToken); }
As long as we stay in preview for these APIs, you ‘ll find the set of usual Iot Plug and Play samples, migrated to use these news APIs in the code repository, in the preview branch:
See project Thermostat for the non-component sample and TemperatureController for the component sample.
Again, now is a great time to let us know of any feedback and comments on these APIs. Contact us, open an issue, and help us provide the right IoT Plug and Play API you need.
Happy testing,
Eric for the Azure IoT Managed SDK team

This article is contributed. See the original author and article here.
Unified Service Desk for model-driven apps provides a configurable framework that allows you to build applications that give call center agents a unified view of customer data.
Unified Service Desk version 4.2, generally available since June, enables you to host web applications using Microsoft Edge WebView2 Process based on the Chromium open-source framework, as well as delivering improved performance and other enhancements.
The Microsoft Edge WebView2 control enables you to embed web technologies (HTML, CSS, and JavaScript) in your native apps. Microsoft Edge WebView2 Process is based on the open-source framework in Chromium that powers many modern browsers.
With support for Microsoft Edge WebView2, Unified Service Desk admins have these capabilities:
In addition, Microsoft Edge WebView2 Process delivers:
To learn more, check out the Unified Service Desk documentation or the Microsoft Edge WebView2 documentation. To use the capabilities, download and install or update Unified Service Desk 4.2.
The post Host web apps using Microsoft Edge WebView2 Process in Unified Service Desk 4.2 appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

This article is contributed. See the original author and article here.
Today, we are excited to launch a new show – Jumpstart Lightning! The show where customers, partners, and the technical community members can come and talk about their Azure Arc, Jumpstart, and Hybrid cloud experience and share awesome stories.

Jumpstart Lightning is designed to be short and sweet with highly technical episodes that go no longer than 10-15 minutes – we don’t want you to get bored and we know you’re busy ![]()
No show is good without episodes so hop over to the Jumpstart YouTube channel to watch our first four episodes!
So, how do you get to record an episode with us?! Super easy!
What are you waiting for?! Fill the submission form (or share it with your customer/partner) and if it’s snazzy enough, you will be hearing from us soon ![]()
See you at the show!
The Jumpstart team
This article is contributed. See the original author and article here.
From your desktop to the cloud, we’ve got you covered. The design intent and integration boosts productivity with scale management in mind.
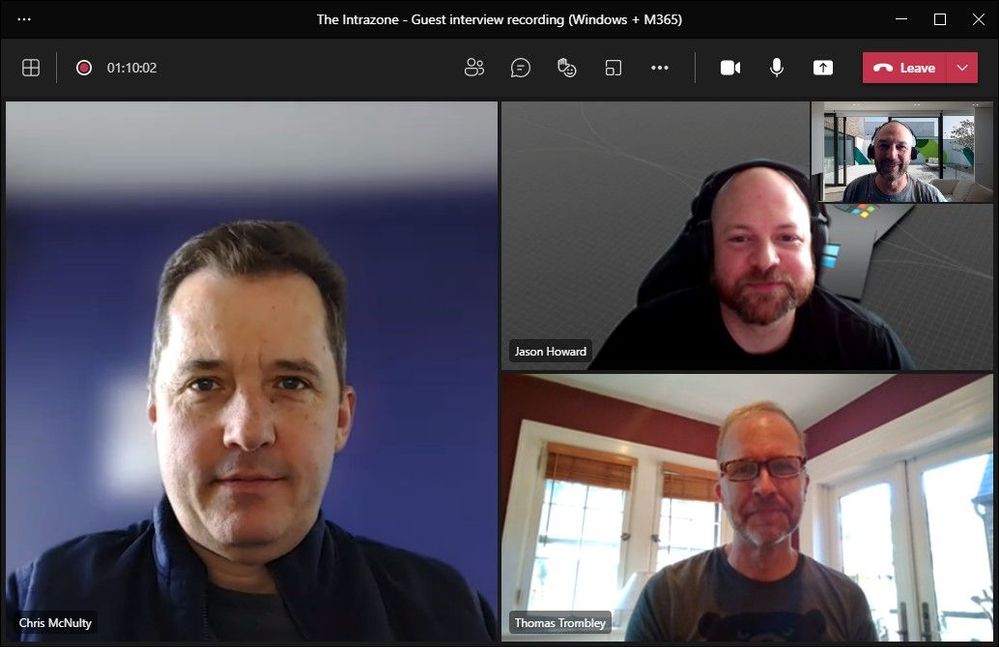
In this episode, Chris McNulty and I talk with Thomas Trombley (Senior program manager – Windows Servicing and Delivery) and Jason Howard (Senior program manager – Windows, Developers, and Experiences (WDX)) about how the Windows desktop and ecosystem supports modern work in the context of Microsoft 365. We dig into helping customers plan for hybrid work, best practices for systems and services for IT to tune and optimize, and how to get into and remain in a good run state for managing it all from “the chip to the cloud.”
Listen to podcast below:
Subscribe to The Intrazone podcast! And listen to episode 67 now + show links and more below.
![Chris-Jason-Thomas-Mark_via Teams.jpg Intrazone hosts + guests: Chris McNulty (Director – Microsoft Viva Topics and SharePoint Syntex) [co-host], Jason Howard (Senior program manager - Windows, Developers, and Experiences (WDX)), {smaller inlay photo upper-right} Mark Kashman (Senior product manager – Microsoft Lists and SharePoint) [co-host], and Thomas Trombley (Senior program manager - Windows Servicing and Delivery).](https://www.drware.com/wp-content/uploads/2021/06/fb_image-160.jpeg) Intrazone hosts + guests: Chris McNulty (Director – Microsoft Viva Topics and SharePoint Syntex) [co-host], Jason Howard (Senior program manager – Windows, Developers, and Experiences (WDX)), {smaller inlay photo upper-right} Mark Kashman (Senior product manager – Microsoft Lists and SharePoint) [co-host], and Thomas Trombley (Senior program manager – Windows Servicing and Delivery).
Intrazone hosts + guests: Chris McNulty (Director – Microsoft Viva Topics and SharePoint Syntex) [co-host], Jason Howard (Senior program manager – Windows, Developers, and Experiences (WDX)), {smaller inlay photo upper-right} Mark Kashman (Senior product manager – Microsoft Lists and SharePoint) [co-host], and Thomas Trombley (Senior program manager – Windows Servicing and Delivery).
Links to important on-demand recordings and articles mentioned in this episode:
Subscribe today!
Listen to the show! If you like what you hear, we’d love for you to Subscribe, Rate and Review it on iTunes or wherever you get your podcasts.
Be sure to visit our show page to hear all the episodes, access the show notes, and get bonus content. And stay connected to the SharePoint community blog where we’ll share more information per episode, guest insights, and take any questions from our listeners and SharePoint users (TheIntrazone@microsoft.com). We, too, welcome your ideas for future episodes topics and segments. Keep the discussion going in comments below; we’re hear to listen and grow.
Subscribe to The Intrazone podcast! And listen to episode 67 now.
Thanks for listening!
The SharePoint teams want you to unleash your magic, creativity, and productivity – and visualize it all. And we will do this, together, one diagram at a time.
The Intrazone links
+ Listen to other Microsoft podcasts at aka.ms/microsoft/podcasts.
![Chris-Mark_in-studio.jpg Left to right [The Intrazone co-hosts]: Chris McNulty, director (SharePoint/Viva – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).](https://www.drware.com/wp-content/uploads/2021/04/fb_image-89.jpeg) Left to right [The Intrazone co-hosts]: Chris McNulty, director (SharePoint/Viva – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).
Left to right [The Intrazone co-hosts]: Chris McNulty, director (SharePoint/Viva – Microsoft) and Mark Kashman, senior product manager (SharePoint – Microsoft).
 The Intrazone, a show about the Microsoft 365 intelligent intranet (aka.ms/TheIntrazone)
The Intrazone, a show about the Microsoft 365 intelligent intranet (aka.ms/TheIntrazone)
Recent Comments