by Contributed | Oct 21, 2021 | Technology
This article is contributed. See the original author and article here.
Did you know that Jupyter Notebooks can be automated? Join this episode with Julie Koesmarno to see an example of how you can use automate diagnostic notebooks automatically executed as an issue is assigned to you. We will be using Azure serverless architecture to illustrate this example. You will learn how you can leverage Azure Logic Apps and API that is available for executing Jupiter Notebook from command lines.
Troubleshooting SQL Server made easy via Notebooks – seeking your feedback: https://aka.ms/SQLDocsTSGBlog
by Scott Muniz | Oct 21, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Cisco has released security updates to address a vulnerability in IOS XE SD-WAN Software. An authenticated local attacker could exploit this vulnerability to take control of an affected system. For updates addressing lower severity vulnerabilities, see the Cisco Security Advisories page.
CISA encourages users and administrators to review Cisco Advisory cisco-sa-sd-wan-rhpbE34A and apply the necessary updates.
![Customizing Lists best practices [guest blog and video]](https://www.drware.com/wp-content/uploads/2021/10/fb_image-8.jpeg)
by Contributed | Oct 20, 2021 | Technology
This article is contributed. See the original author and article here.
Hello, my name is Norm Young, and I am Microsoft MVP from St. Catharines, Ontario, Canada. I am a 20 plus year data professional who has recently made the shift to the collaboration space using Microsoft Lists, Microsoft Teams and SharePoint. Microsoft asked if I would share both the way I approach leveraging technology and highlight a few recent custom solutions I put together. I’m thrilled to be here, so – here, we go.
Background
Many of the solutions I have built using Microsoft Lists reflect the current state of a business process. When I worked in higher education, we used Lists to track student exchange program information (school name, start/end dates, current student counts etc.). In my current role we use Microsoft Lists to track our new customer onboarding program (client name, contact information, products to onboarding, major milestones etc.). Business processes tend to have multiple stages with start and end dates, persons responsible, and other forms of supporting metadata that make the execution of the business process possible. Additional value is brought to the Lists experience through the integration with other apps and services like the Power Platform with list data serving as the foundation for applications developed using Power Apps, workflows using Power Automate and reporting using Power BI.
Approach
When I develop solutions using Microsoft Lists, I take a configure-first approach where the existing out-of-the-box functionality is evaluated to see if the minimum viable product can be achieved without customization. If this is not possible then extending functionality is undertaken.
In the not so recent past, if I needed to hide or rearrange columns in the list new/edit form I had use Power Apps and by doing so I created technical debt that someone would have to own and maintain. Don’t get me wrong, I think Power Apps is a great development platform but not all solutions require customization. In the current state of the new/edit form hiding columns or rearranging columns is as simple as deselecting a checkbox or dragging columns into the desired order with no Power Apps customization required.
In contrast, if the solution requires customization and the value of that customization outweighs the cost the technical debt then customization is the right choice. While working in higher-ed, I developed a Microsoft Lists based solution that was used to track multi-factor authentication token assignments to users. The token identifier was a very long string of numbers with an associated barcode. If we implemented a no-customization solution the user would be forced to manually enter the identifier. This implementation would be prone to data entry error and would be unnecessarily mundane. Integrating Power Apps meant we could use the barcode scanner control to eliminate data entry errors and improve the user experience. In this case the cost of technical debt is outweighed by better data quality and improved user experience.
Because of their availability and low barrier to use, Microsoft Lists are leveraged in many ways. Below are the use cases shown in the above video – with additional context and a few tips and tricks along the way for why and how I customized lists to create business solutions.
Use case | Application submission solution using Forms, Microsoft Lists and Power Automate
Lists can be used to store response data from Microsoft Forms using Power Automate allowing for additional information tracking or analysis using Power BI. Integrating these tools helps to create a self-service platform for enhancing and modernizing business processes. Check out this blog article to learn more: Get responses from Forms to Microsoft Lists using Power Automate.
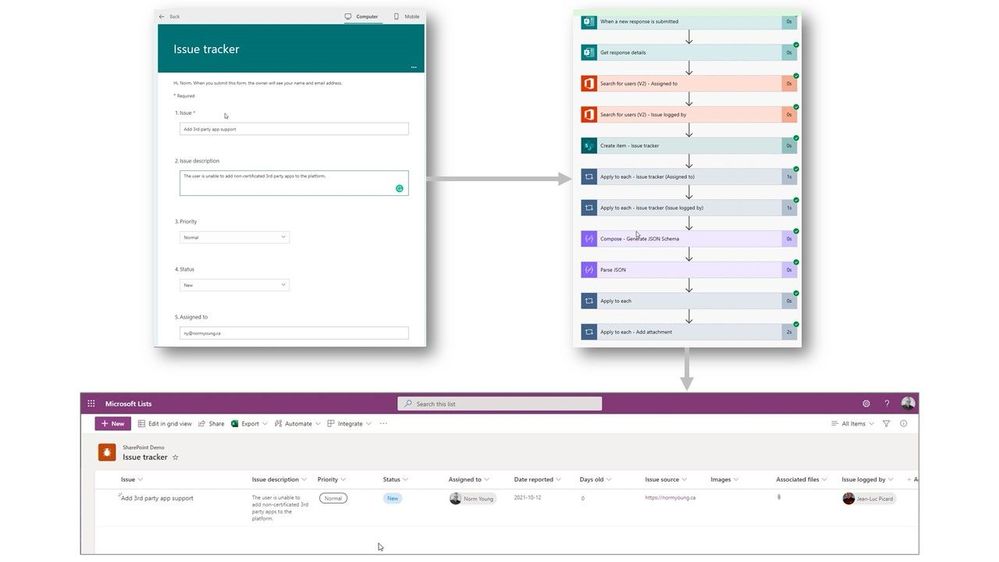
Connect Microsoft Forms to Power Automate flows to capture and populate Microsoft Lists list items.
Tip | When integrating apps and services into Microsoft Lists, it is important to remember that not all list column types will translate to the destination data types and some concessions in functionality may be required. Complex data types like the person column include additional information like email address, mobile phone number, department name, job title, first name, last name and many more that may need to be split into separate columns to store the additional person information (email, first and last name) or handled in some programmatic way like an expression in a Power Automate.
Use case | Organization specific project management tracker using Microsoft Lists.
If you have created a list-based solution, why not share it with others in your organization using
Custom List Templates? Custom List Templates are a great way to extend the value of one solution to others with similar needs by giving users a well-thought-out starting point that brings value to them in a very quick manner. Read more at: A first look at Templates in Microsoft Lists.
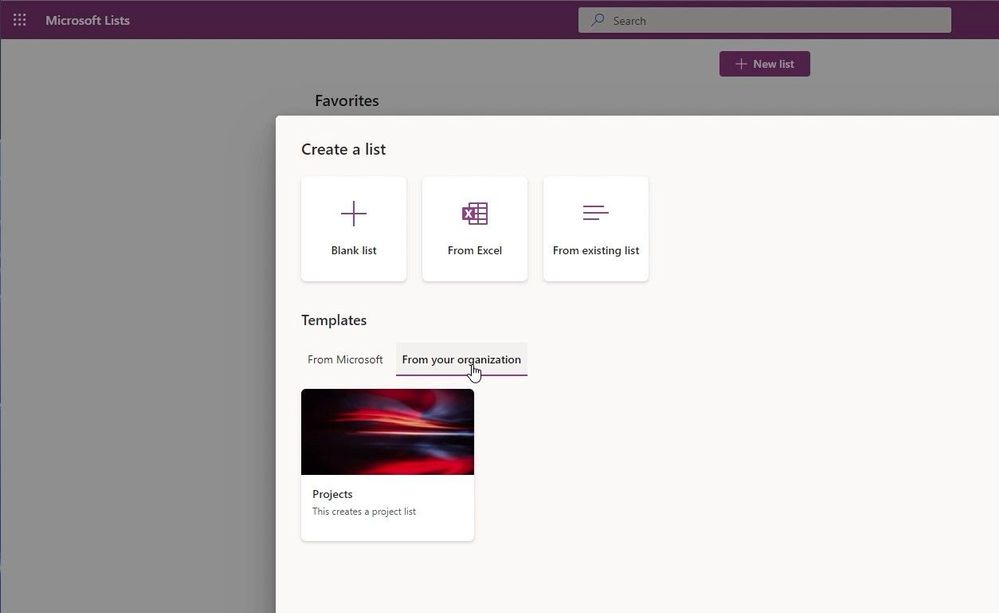
Microsoft Lists now supports custom lists design by your organization.
Use case | Issue tracking management using Microsoft Lists, Microsoft Teams and Power Automate.
Microsoft Lists solutions that leverage a target date or end date will find value added through reminders prior to the date. Value comes in the form of users not having to manually look for items that are coming due, it is pushed to them. Get started with List reminders in teams with this blog post: Send reminders to Teams from Microsoft Lists using Power Automate.
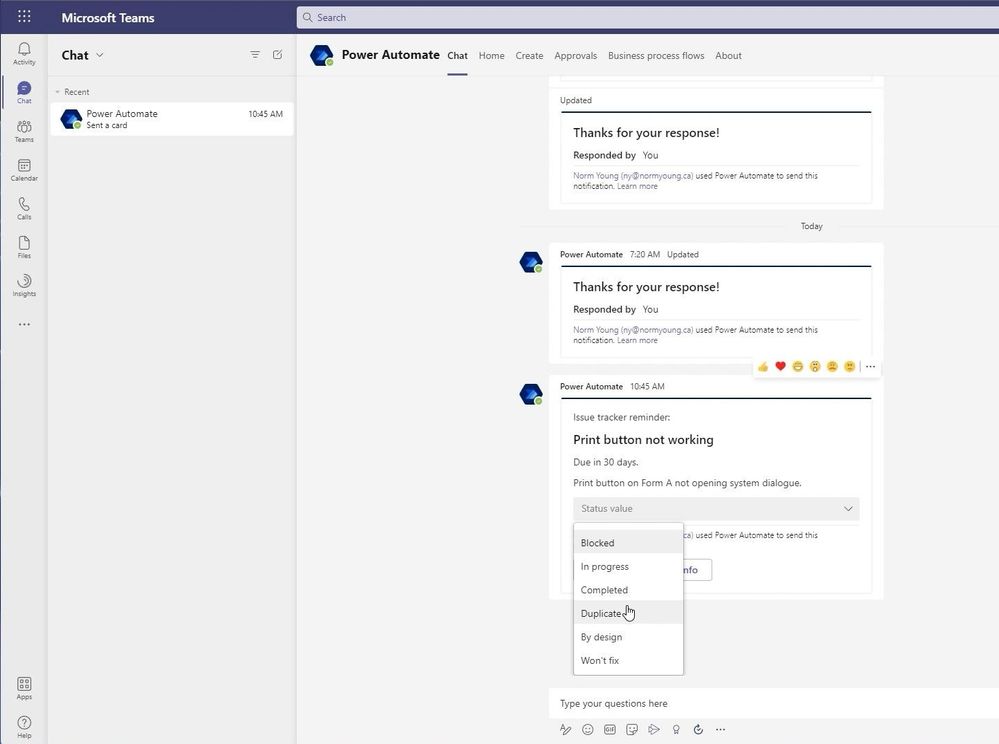
Use adaptive cards populated with Microsoft Lists list item data to push actionable requests into Microsoft Teams chats.
Tip | Another point of consideration are how column names are referenced internally with Microsoft Lists. Depending on how the column was created will influence the internal column name. As an example, if we create two similarly name columns, we will get two different internal names as shown in the table below:
Method
|
External name
|
Internal name
|
From default experience
|
Column 1
|
Column1
|
From List settings
|
Column 2
|
Column_x0020_2
|
Trick | A simple way to view the internal column name is to Edit Column (click on the column name) while in List Settings and check the Field value at the end of the URL.
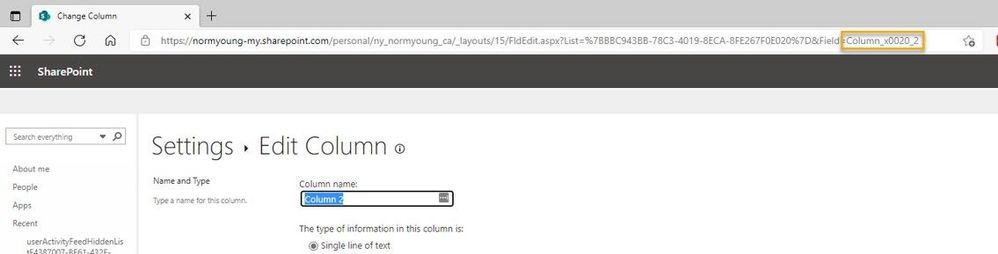
Trick | Go to List setting > Edit Column to view an internal column’s name.
Caution
Lists are great for centralizing and collaborating on data with teams but there are situations where lists are not the right fit. Solutions requiring complex data relationships and/or high-volume transactions should look to other offerings like Dataverse or Azure SQL Database as a more suitable platform.
Another caution when using lists as a data source is exceeding the List View Threshold – when apps and services attempt to fetch more than 5,000 items from a list. This doesn’t mean a list can only store 5,000 items – in fact a list can have up to 30 million items – but it does mean that any single call to a list must be 5,000 or fewer items. Be sure to check out the Living Large with Large Lists and Large Libraries article for more information on the List View Threshold issue, and how to design within it.
Final thoughts
Microsoft Lists are a great platform for collaborating on data using a single, low-barrier platform where solutions, can start modestly and grow as requirements, experience, and features increase. When deciding to customize lists be sure to take a configure-first approach and when it makes sense then customize using app and services like the Power Platform. To learn more be sure to check out the Microsoft Lists Resource Center for the latest blogs, videos, demos, and access to learning resources.
If you want to see more examples of how to extend functionality in Microsoft Lists be sure to check out my blog at https://normyoung.ca/. If you want to keep the conversation going lets connect on LinkedIn or following me on Twitter.
I hope you found some value in this post and thanks for reading!
Cheers, Norm
by Scott Muniz | Oct 20, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Google has released Chrome version 95.0.4638.54 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.
CISA encourages users and administrators to review the Chrome Release Note and apply the necessary update as soon as possible.

by Scott Muniz | Oct 20, 2021 | Security
This article was originally posted by the FTC. See the original article here.
Has Amazon contacted you to confirm a recent purchase you didn’t make or to tell you that your account has been hacked? According to the FTC’s new Data Spotlight, since July 2020, about one in three people who have reported a business impersonator scam say the scammer pretended to be Amazon.
These scams can look a few different ways. In one version, scammers offer to “refund” you for an unauthorized purchase but “accidentally transfer” more than promised. They then ask you to send back the difference. What really happens? The scammer moves your own money from one of your bank accounts to the other (like your Savings to Checkings, or vice versa) to make it look like you were refunded. Any money you send back to “Amazon” is your money (not an overpayment) — and as soon as you send it out of your account, it becomes theirs. In another version of the scam, you’re told that hackers have gotten access to your account — and the only way to supposedly protect it is to buy gift cards and share the gift card number and PIN on the back. Once that information is theirs, the money is, too.
Here are some ways to avoid an Amazon impersonator scam:
- Never call back an unknown number. Use the information on Amazon’s website and not a number listed in an unexpected email or text.
- Don’t pay for anything with a gift card. Gift cards are for gifts. If anyone asks you to pay with a gift card – or buy gift cards for anything other than a gift, it’s a scam.
- Don’t give remote access to someone who contacts you unexpectedly. This gives scammers easy access to your personal and financial information—like access to your bank accounts.
Have you spotted this scam? Report it at ReportFraud.ftc.gov.
If you think someone has gotten access to your accounts or personal information, visit IdentityTheft.gov. There, you’ll find steps to take to see if your identity has been misused, and how to report and recover from identity theft.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Oct 19, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Oracle has released its Critical Patch Update for October 2021 to address 419 vulnerabilities across multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the Oracle October 2021 Critical Patch Update and apply the necessary updates.

by Contributed | Oct 19, 2021 | Dynamics 365, Microsoft 365, Technology
This article is contributed. See the original author and article here.
2021 has been an interesting year as we embrace the new hybrid world while bringing back the best practices from our old life and work style. With all these changes, the need for products and services to adapt to our new norm has become more important than ever. Sales organizations need solutions that are fluid, dynamic, and cloud-based. During our recent LinkedIn Live session (The Evolution of the Modern CRM), we had the honor to hear from industry sales leader, Santina Franci, Microsoft’s VP of Business Applications, and Amanda Homes, CEO of The Ultimate Sales Machine, as they provided us with gems to help up-level digital sellers.
1. Dream 100 strategy
Amanda mentioned the Dream 100 strategy referencing from her father’s book, The Ultimate Sales Machine, and how this strategy focuses heavily on a small group of clients who purchase your product the most. Implementing sales efforts to narrow down your best clients and focusing your resources on a select group will help yield higher sales. This strategy is much more effective than cold calling 2,000 clients with the slight hope of future leads. It is “the fastest and least expensive way to double sales.” To implement this strategy, you need data from your customer, which can be very complex with the amount of data we receive on a day-to-day basis.
For many sales teams, implementing the technology and human skills to keep up with the evolving demands of digitally savvy customers may seem like a stretch, even by 2025. Microsoft Dynamics 365 Sales accelerator helps sellers work faster and smarter with a prioritized work list of the next best lead or opportunity, allowing them to engage through their customers’ preferred channel with integrated email, phone dialer, and a Microsoft Teams channel. Sellers are equipped with timely, AI-driven insights and recommendations based on customer events and needs, so sales teams know when to offer customer guidance.
Sellers now have the information and insights to have more meaningful conversations. It is ultimately still your decision on how to proceed with your sale strategy, but these tools can give you a better view of your decision.
2. Educating not selling
As a seller, you are constantly reaching out via email to potential clients, but out of your pool, how many are ready to buy? Amanda mentioned that about 3 percent of clients are in the buying now category, 7 percent are open to your product, and 90 percent are not interested in you, your product, or service. As sellers, we send out emails to that 90 percent of potential customers, explaining our product, while the consumers have no interest in the product or service in the first place. It can be advantageous to educate the consumer on why this product can be of interest instead of explaining the features of the product itself. Being able to educate your customer about the current landscape of their business and the challenges they might face will put you in a better position to market your product to them.
In the era of digital selling, even now more than before, email is one of the most used avenues of contacting new customers. To run an educational marketing strategy, your CRM must be able to integrate with your communication platform, so that all aspects can work together. Not having to rely heavily on manual labor to ingest, respond, and avoid mistakes when communicating with your customers will in return free up time for sellers to further their personal and intimate relations with their customers. Microsoft Dynamics 365 allows you to integrate your communication platform and add applications that can ingest, send, and alert sellers of high-value customers. Collaborative apps from Dynamics 365, Microsoft Teams, and Microsoft 365bring together the right people, both inside and outside the companywith new ways to see who is available to chat, call, and collaborateall right from within Dynamics 365 or Teams. Sellers can also bring in resources from across the organization and across the globe in real-time to ensure they have the most up-to-date context.
3. Relationship selling reduces rejection
“On average three out of four salespeople are ineffective at their job.0.08 percent of universities offer sales as a major or minor” as mentioned by Amanda. Without a proper educational background, it is understandable why leads are being missed, follow-up is lacking, and referrals have missteps; it usually all boils down to the human reaction to rejection. After hours, days, and weeks of customer interaction, the last thing you want to hear is, “I am not interested.” With social platforms being such a powerful player in this arena, we must look towards social selling and bring back the element of human empathy. Having the strength to let go of the fear of rejection and instead use tools to help enable social engagement.
With the pandemic, social selling has been an important pillar for sellers around the world and with LinkedIn Sales Navigator and Dynamics 365, the ability to socially interact with customers has been made easier. Being able to comment on a post with something engaging or clever brings back the empathy sellers have been struggling with. Actual human interaction, and showing you care, will go a long way when creating relationships with new customers. With conversation intelligence in Dynamics 365 Sales, sales leadersand the sellers themselvesreceive real-time insights about the customer’s priorities, sentiments, and emotions during the actual conversation. Also, customer mentions of competitors are flagged for instant follow-up. This helps the seller take action during the call, and it allows the sales leader to help through guided selling. Having the proper tools helps get rid of the fear of rejection.
Watch the recap of our LinkedIn live session: The Evolution of the Modern CRM
As the market evolves, we as sellers must level up as well. In this day and age, having the correct strategy is only half the battle. It is imperative to have the tools and the platform that can help integrate all avenues into one. Santina and Amanda deep dive into this subject. Be sure to check out the recap of the LinkedIn session to gain further insights and learn more about Dynamics 365 Sales.
The post 3 secrets to optimize your sales strategy appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Contributed | Oct 19, 2021 | Technology
This article is contributed. See the original author and article here.
 Recently Microsoft HLS put on a webinar “Enhance Your Employee Experience with MS Viva.” This all up, high level webinar, led by Microsoft’s Michael Gannotti, covered all four of the current Microsoft Viva modules. Covered were Viva Connections, Viva Insights, Viva Topics, and Viva Learning. To provide deeper insight into each of the Viva modules, and to help customers test and investigate these modules, Microsoft HLS is putting on a 4-part webinar series “Microsoft HLS Viva Webinar Series.” You can read about each of the deep dive webinars below as well as download the individual calendar invites for each. Each session will be delivered by Michael Gannotti, Principal Technical Specialist, Microsoft HLS.
Recently Microsoft HLS put on a webinar “Enhance Your Employee Experience with MS Viva.” This all up, high level webinar, led by Microsoft’s Michael Gannotti, covered all four of the current Microsoft Viva modules. Covered were Viva Connections, Viva Insights, Viva Topics, and Viva Learning. To provide deeper insight into each of the Viva modules, and to help customers test and investigate these modules, Microsoft HLS is putting on a 4-part webinar series “Microsoft HLS Viva Webinar Series.” You can read about each of the deep dive webinars below as well as download the individual calendar invites for each. Each session will be delivered by Michael Gannotti, Principal Technical Specialist, Microsoft HLS.
- Webinar Calendar Invites:
Microsoft Viva Connections – The Personalized Next Gen Intranet for Engaging Employees
October 27: Microsoft HLS Viva Webinar Series – 1
Microsoft Viva Connections delivers a role based “curated, company-branded experience that brings together relevant news, conversations, and resources in the apps and devices you use every day.” – Viva Connections. Microsoft Viva Connection is designed not only to inform employees but to also engage them in a meaningful fashion that help reduce feelings of disconnectedness that can arise in a hybrid workplace.
Agenda:
- Overview of Microsoft Viva Connections
- Instructions around its setup (Step by step walkthrough of standing up Viva Connections. Yes, it’s that straightforward and we will show you how.) including configuring the Connections Dashboard and Feed.
- Opportunities for extension of the Microsoft Viva Connections experience to add additional value and employee engagement.
- Open Q&A – Bring your questions, comments, concerns. Wondering what to do if you are still on premise or in SharePoint classic, maybe even another Intranet technology altogether? This will be a great opportunity to ask.
- Resources to get started on your journey to better employee engagement.
- Wrap up/Next steps
Microsoft Viva Insights – Improving Employee Productivity and Well Being
November 10: Microsoft HLS Viva Webinar Series – 2
Microsoft Viva Insights provides powerful, actionable, insights to “improve productivity and wellbeing with data-driven, privacy-protected insights and recommendations.” – Viva Insights
Microsoft Viva Insights enables employees to get personal insights in the flow of work as well as assists employees in managing their day, priorities, breaks, and more. Microsoft Viva Insights also helps managers address team stressors, productivity, and avoid employee burnout. Finally, Microsoft Viva Insights generates valuable insights and reports for business leaders that address challenges within the workplace. In all of these scenarios Microsoft Viva Insights is designed to keep employee data safe, private, while helping to enable organizations to maintain compliance with industry and regional requirements.
Agenda:
- Deep dive into Microsoft Viva Insights capabilities
- Learn how Microsoft Viva Insights can provide deep actionable insights while delivering privacy and ensuring organizational compliance.
- Address areas for expansion, customization, potentially leveraging data from additional non-Microsoft resources.
- Open Q&A
- Resources for Microsoft Viva Insights
- Wrap up/Next Steps
Microsoft Viva Topics – Automatically Organize Content/Expertise Across Your Organization Improving Ease of Information Discovery/Use
November 23: Microsoft HLS Viva Webinar Series – 3
Microsoft Viva Topics “automatically organizes content and expertise across your organization, making it easy for people to find information and put knowledge to work.” – Viva Topics
With Microsoft Viva Topics you can turn content into knowledge using AI to reason over your organization’s data and automatically identify, process, and organize content. You can organize knowledge, improving topics by combining AI and human expertise. Finally, make knowledge easy to discover by automatically displaying topic cards across Microsoft 365 apps to enable knowledge discovery in the context of your work.
Agenda:
During the Microsoft Viva Insights webinar attendees will:
- Deep dive into Microsoft Viva Topics capabilities
- Learn how Microsoft Viva Topics can improve information and expertise discovery within the context of work.
- Address areas for expansion, customization, of Microsoft Viva Topics pages.
- Open Q&A
- Resources for Microsoft Viva Topics
- Wrap up/Next Steps
Microsoft Viva Learning – Bringing Together the Continuum of Learning from AdHoc Projects to LMS hosted Compliance Training
December 23: Microsoft HLS Viva Webinar Series – 4
“Empower employees to discover, share, recommend, and learn from content libraries across your organization with this center for learning in Microsoft 365” – Viva Learning
With Microsoft Viva Learning employees can easily discover, recommend, and share all learning within and organization including Sharepoint content, 3rd party learning/training packages, Microsoft public resources, formalized Learning Management Systems (LMS), and more.
Agenda:
During the Microsoft Viva Insights webinar attendees will:
- Deep dive into Microsoft Viva Learning capabilities
- Learn how Microsoft Viva Learning can improve organizational readiness and skilling.
- Address areas for expansion, customization, of Microsoft Viva Learning content.
- Open Q&A
- Resources for Microsoft Viva Learning
- Wrap up/Next Steps
Thanks for visiting – Michael Gannotti LinkedIn | Twitter
 Michael Gannotti
Michael Gannotti

by Contributed | Oct 19, 2021 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
When the working world split between those who could work from home and those who could not, the frontline transformed beyond anyone’s expectations. Frontline workers—the associates at the forefront of your customer interactions, the clinicians delivering patient care, and those running your operations on the ground—have long been underserved by technology and are only now…
The post 3 ways to support frontline workers in a hybrid world appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Oct 18, 2021 | Security, Technology
This article is contributed. See the original author and article here.
CISA, the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) have released joint Cybersecurity Advisory (CSA): BlackMatter Ransomware.
Since July 2021, malicious cyber actors have used BlackMatter ransomware to target multiple U.S. critical infrastructure entities, including a U.S. Food and Agriculture Sector organization. Using an analyzed sample of BlackMatter ransomware and information from trusted third parties, this CSA provides cyber actor tactics, techniques, and procedures and outlines mitigations to improve ransomware protection, detection, and response.
To reduce the risk of BlackMatter ransomware, CISA, FBI, and NSA encourage organizations to implement the recommended mitigations in the joint CSA and visit StopRansomware.gov for more information on protecting against and responding to ransomware attacks.

![Customizing Lists best practices [guest blog and video]](https://www.drware.com/wp-content/uploads/2021/10/fb_image-8.jpeg)








Recent Comments