NCSC Releases 2021 Annual Review
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
CISA has added four new vulnerabilities to its Known Exploited Vulnerabilities Catalog, which require remediation from federal civilian executive branch (FCEB) agencies by December 1, 2021. CISA has evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for malicious cyber actors of all types and pose significant risk to the federal enterprise.
| CVE Number | CVE Title | Remediation Due Date |
| CVE-2021-22204 | Exiftool Remote Code Execution vulnerability | 12/01/2021 |
| CVE-2021-40449 | Microsoft Win32k Elevation of Privilege | 12/01/2021 |
| CVE-2021-42292 | Microsoft Excel Security Feature Bypass | 12/01/2021 |
| CVE-2021-42321 | Microsoft Exchange Server Remote Code Execution | 12/01/2021 |
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the meet the specified criteria.
This article is contributed. See the original author and article here.
Azure Purview lets you govern Azure SQL Databases at scale, and with ease. The following details how to register and scan your Azure SQL Database, along with how to extract lineage to view and analyze how data is being transformed. It also describes how to discover assets easily by grouping Azure SQL Database schemas and tables into Purview collections.
Register and scan
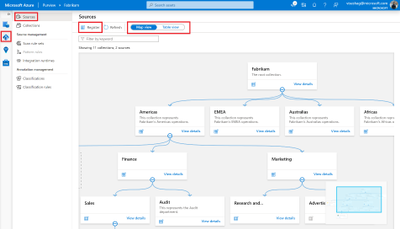
Navigate to your Purview account and click on the Data Map section to the left. You can view your data estate map and choose to view your sources in table format as well.

Purview now supports 20-plus source types, ranging from Azure SQL Database, to AWS S3, to Oracle Database. Sources can be registered in two ways: by either clicking on the register button on the top left or by navigating to the collection that you’d like to register the source to and clicking on the Register quick action icon. Then click on the Azure SQL Database source tile and fill in the required details.
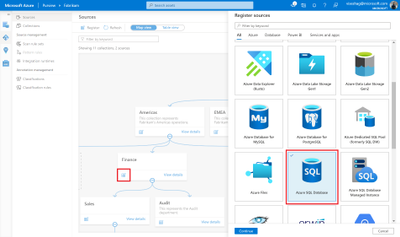
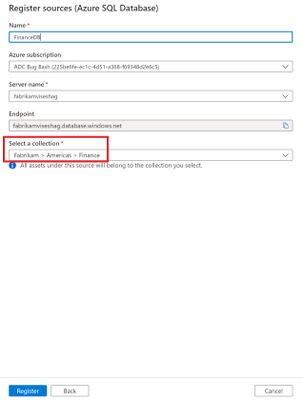
As part of the required details, register your source to a collection of interest. In our example, we register the source to the Finance collection.
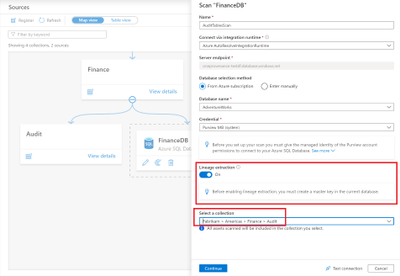
Once your source is registered, the next step is to set up a scan. While setting up your scan, fill in details for the integration runtime, database name, and credential. You can also set up your scan with a collection; in our example, it’s the Audit collection under Finance. So you can now scope your scan to only the Audit tables to ensure all assets are scanned into the catalog with the right collection associated for discovery and access control.
See results of the scan by clicking on View details for your source.
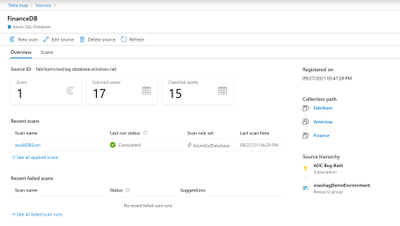
Lineage extraction (preview)
While setting up your scan, you can now extract lineage from stored procedures and other artifacts in your Azure SQL Database source.
Learn more on how to get onboarded to the Preview program here.
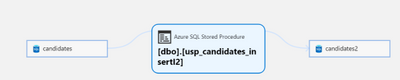
Discover—search and browse for your Azure SQL Database tables
Once a scan completes, you can discover assets either via search or browse. To search, enter keywords in the search bar on the top of the Purview studio and narrow down results by the facet filters Purview provides.
To browse, click on the browse assets tile on the catalog home page, navigate to the By collection tab and navigate to the collection that you scanned assets into. In our example, it would be Audit. If you have access to this collection, click on it to browse for your assets.
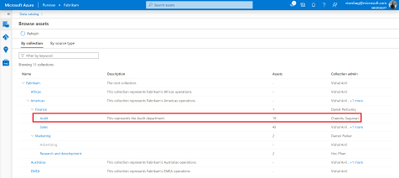
Add business metadata to your Azure SQL database assets
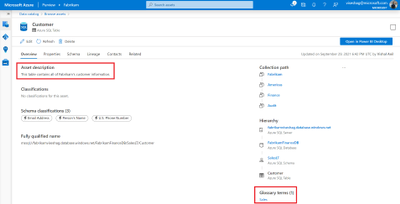
You can also navigate to one of your Azure SQL tables and view details. To aid in discoverability and compliance, add descriptions and business glossary terms by clicking on the Edit button.
Insights (preview)
Finally, view all your Azure SQL Database-related insights around assets, scans, glossary, classification, and labels by navigating to the Insights section of Purview.
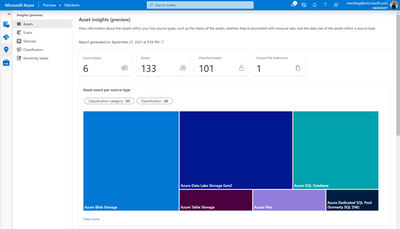
Get started today!

This article is contributed. See the original author and article here.
The concept of the global control tower first appeared on the radar of supply chain leaders around 15 years ago. As more and more companies pursued end-to-end visibility for increasingly globalized supply chains, the idea quickly gained momentum. IndustryWeek noted global control towers as one of the hottest supply chain buzzwords of 2008.1 Still, for an idea that has been buzzing for over a decade, many companies have been challenged to move from concept to reality.
Microsoft Dynamics 365 Supply Chain Management is helping companies overcome these challenges by equipping them with the tools necessary to create digital supply chains that are highly collaborative, coordinated, agile, and demand-driven. With these new supply chain solutions in place, businesses can achieve real-time, end-to-end visibility across the supply chain, breathing new life into concepts like supply chain control towers in the process.
This embed requires accepting cookies from the embed’s site to view the embed. Activate the link to accept cookies and view the embedded content.
It has quickly become essential for businesses to invest in technology that can help them sense and predict supply chain constraints and disruptions and spikes and troughs in demand. From using advanced forecasting techniques to real-time collaboration between trading partners and commercial teams, business processes are increasingly geared to generate and proactively shape customer demand. Companies must also integrate the agility to continuously optimize supply and production plans in real-time, as forecast and predictions shift into actual customer order receipts. Supply chains control towers help in these efforts by building both agility and resiliency into the supply chain by delivering end-to-end operational visibility, all the way from planning to delivery and back.
Resiliency in this context is about driving business continuity. This can take the form of digitizing production in factories, automating operations on the shop floor, and providing unparallel transparency, in real-time, to leadership. By utilizing Dynamics 365 Supply Chain Insightspreview to create a digital representation of the physical supply chain, whether called a control tower, digital twin, or supply chain nerve center, businesses can reach new levels of agility and gain the ability to sense and proactively mitigate disruptions before they occur. And to respond faster when the inevitable happens, such as an unpredictable or unforeseen event.
McKinsey & Company estimates that a $10 billion business with a high-performing supply chain can reduce cost by as much as $50 million annually through digital initiatives such as supply chain nerve centers.2 This is because control towers enable supply chain organizations to blur the lines between planning and execution, allowing businesses to uncover and exploit improvement opportunities faster than ever before.
Starting with the end in mind, regardless of the mixture of people, processes, data, organization, and technology used to erect a control tower, it must deliver end-to-end visibility across all supply chain nodes to be successful. This visibility should penetrate beyond tier 1 and tier 2 partners.
While visibility is the starting point, visibility by itself is not sufficient. Supply chain solutions must also deliver improvements to agility so companies can more effectively respond to changing customer demands. In practice, this means going beyond the ability to immediately grasp what is happening (system-wide visibility) and on to making predictions of what is likely to happen next. This way, business leaders can adapt and overcome challenges as they are identified in real-time.
The value that a construct such as a supply chain control tower can deliver is proportional to the organizations’ ability to unify data from disparate sources. Enterprise resource planning (ERP) systems, legacy business applications, supplier systems of records, siloed hard drives, PLCs, and even IoT data streams all must be incorporated and unified.
Businesses also need supply chain solutions that incorporate rules-based orchestration to model and automate responses to fulfillment constraints. By leveraging automation in this manner, organizations can proactively address issues with actionable, data-driven insights, allowing them to adapt faster to disruptions and constraints.
At Microsoft, we see supply chain control towers as a shared service process that can be brought together from a mix of supply chain solutions. For example, a control tower can be assembled using Dynamics 365 Supply Chain Management, Dynamics 365 Intelligent Order Management, Dynamics 365 Supply Chain Insightspreview together with Microsoft Power Platform, and our rapidly growing ecosystem of digital supply chain applications.
A supply chain control tower enabled by Dynamics 365 in this fashion positions organizations to respond faster and more intelligently to disruptions and opportunities. With seamless integration to many market-leading API-enabled applications using our configurable pre-built partner connectors, businesses can convert the action signals from what-if analysis into directives sent to the applications that guide day-to-day operational execution.
When organizations use Dynamics 365 to create a supply chain control tower, they can realize the benefits of a single platform. One version of truth brings together internal and external stakeholders to visualize constraints and disruptions at any point in the value stream. Then, affected agents and authorities can work together to analyze the upstream or downstream impacts, collaborate in near real-time to formulate and enact optimal responsesall from one location and one pane of glass.
In this way, a supply chain control tower created with Dynamics 365 enables organizations to adapt quickly to demand shifts by deliberately blurring the lines between planning and execution and effectively creating a continuous digital feedback loop across entities and distinct business processes.
Let’s now look at how a customer, Breville Group, is creating a resilient supply chain of the future with Dynamics 365.
This embed requires accepting cookies from the embed’s site to view the embed. Activate the link to accept cookies and view the embedded content.
Dynamics 365 Supply Chain Management provides manufacturers, distributors, and retailers with the real-time visibility and intelligence they need to move from reactive to proactive. It unifies data and uses predictive insightsacross order fulfillment, planning, procurement, production, inventory, warehousing, and transportationto maximize operational efficiency, product quality, and profitability. And, with innovative technologies, such as AI and machine learning integrated into the solution, it helps organizations accelerate performance even further.
Learn more about how Microsoft Dynamics 365 Supply Chain Management, Dynamics 365 Intelligent Order Management, and Dynamics 365 Supply Chain Insights preview enable companies to strengthen and expand the Four Pillars of the Digital Supply Chain. To learn more, check out our recent webinar Create Agile and Digital Supply Chains with Dynamics 365, and join a panel of Microsoft Experts in the live Ask the Expert session scheduled for December 7, 2021, at 10AM Pacific Time.
1- IndustryWeek, A Guide to the Hottest Supply Chain Buzzwords of 2008, January 2008
The post Enhance visibility with Dynamics 365 digital supply chain solutions appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
CISA, the Federal Bureau of Investigation (FBI), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC) have released a joint Cybersecurity Advisory highlighting ongoing malicious cyber activity by an advanced persistent threat (APT) group that FBI, CISA, ACSC, and NCSC assess is associated with the government of Iran. FBI and CISA have observed this Iranian government-sponsored APT exploit Fortinet and Microsoft Exchange ProxyShell vulnerabilities to gain initial access to systems in advance of follow-on operations, which include deploying ransomware.
Joint Cybersecurity Advisory AA21-321A provides observed tactics and techniques, as well as indicators of compromise that FBI, CISA, ACSC, and NCSC assess are likely associated with this Iranian government-sponsored APT activity. FBI, CISA, ACSC, and NCSC urge critical infrastructure organizations to apply the recommendations listed in the advisory to mitigate risk of compromise from Iranian government-sponsored cyber actors.
CISA also recommends reviewing its Iran Cyber Threat Overview and other Iran-related Advisories.
This article is contributed. See the original author and article here.
Actions to Take Today to Protect Against Iranian State-Sponsored Malicious Cyber Activity
• Immediately patch software affected by the following vulnerabilities: CVE-2021-34473, 2018-13379, 2020-12812, and 2019-5591.
• Implement multi-factor authentication.
• Use strong, unique passwords.
Note: this advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, version 10. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques.
This joint cybersecurity advisory is the result of an analytic effort among the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC) to highlight ongoing malicious cyber activity by an advanced persistent threat (APT) group that FBI, CISA, ACSC, and NCSC assess is associated with the government of Iran. FBI and CISA have observed this Iranian government-sponsored APT group exploit Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021 to gain initial access to systems in advance of follow-on operations, which include deploying ransomware. ACSC is also aware this APT group has used the same Microsoft Exchange vulnerability in Australia.
The Iranian government-sponsored APT actors are actively targeting a broad range of victims across multiple U.S. critical infrastructure sectors, including the Transportation Sector and the Healthcare and Public Health Sector, as well as Australian organizations. FBI, CISA, ACSC, and NCSC assess the actors are focused on exploiting known vulnerabilities rather than targeting specific sectors. These Iranian government-sponsored APT actors can leverage this access for follow-on operations, such as data exfiltration or encryption, ransomware, and extortion.
This advisory provides observed tactics and techniques, as well as indicators of compromise (IOCs) that FBI, CISA, ACSC, and NCSC assess are likely associated with this Iranian government-sponsored APT activity.
The FBI, CISA, ACSC, and NCSC urge critical infrastructure organizations to apply the recommendations listed in the Mitigations section of this advisory to mitigate risk of compromise from Iranian government-sponsored cyber actors.
For more information on Iranian government-sponsored malicious cyber activity, see us-cert.cisa.gov/Iran.
Click herefor a PDF version of this report.
Since at least March 2021, the FBI and CISA have observed Iranian government-sponsored APT actors leverage Microsoft Exchange and Fortinet vulnerabilities to target a broad range of victims across multiple critical infrastructure sectors in furtherance of malicious activities. Observed activity includes the following.
elie to further enable malicious activity. Note: for previous FBI reporting on this activity, refer to FBI FLASH: APT Actors Exploiting Fortinet Vulnerabilities to Gain Initial Access for Malicious Activity.91.214.124[.]143 and 162.55.137[.]20—which FBI and CISA judge are associated with Iranian government cyber activity—to further enable malicious activity against the hospital’s network. The APT actors accessed known user accounts at the hospital from IP address 154.16.192[.]70, which FBI and CISA judge is associated with government of Iran offensive cyber activity.CVE-2021-34473—to gain initial access to systems in advance of follow-on operations.ACSC considers that this APT group has also used the same Microsoft Exchange vulnerability (CVE-2021-34473) in Australia.
FBI, CISA, ACSC, and NCSC assess the following tactics and techniques are associated with this activity.
The APT actors have used the following malicious and legitimate tools [T1588.001, T1588.002] for a variety of tactics across the enterprise spectrum.
The Iranian government-sponsored APT actors gained initial access by exploiting vulnerabilities affecting Microsoft Exchange servers (CVE-2021-34473) and Fortinet devices (CVE-2018-13379, CVE-2020-12812, and CVE-2019-5591) [T1190].
The Iranian government-sponsored APT actors may have made modifications to the Task Scheduler [T1053.005]. These modifications may display as unrecognized scheduled tasks or actions. Specifically, the below established tasks may be associated with this activity:
SynchronizeTimeZoneGoogleChangeManagementMicrosoftOutLookUpdaterMicrosoftOutLookUpdateScheduleThe Iranian government-sponsored APT actors may have established new user accounts on domain controllers, servers, workstations, and active directories [T1136.001, T1136.002]. Some of these accounts appear to have been created to look similar to other existing accounts on the network, so specific account names may vary per organization. In addition to unrecognized user accounts or accounts established to masquerade as existing accounts, the following account usernames may be associated with this activity:
SupportHelpelieWADGUtilityAccountThe FBI and CISA observed outbound File Transfer Protocol (FTP) transfers over port 443.
The APT actors forced BitLocker activation on host networks to encrypt data [T1486]. The corresponding threatening notes were either sent to the victim or left on the victim network as a .txt file. The ransom notes included ransom demands and the following contact information.
The FBI, CISA, ACSC, and NCSC recommend that organizations using Microsoft Exchange servers and Fortinet investigate potential suspicious activity in their networks.
Note: for additional approaches on uncovering malicious cyber activity, see joint advisory Technical Approaches to Uncovering and Remediating Malicious Activity, authored by CISA and the cybersecurity authorities of Australia, Canada, New Zealand, and the United Kingdom.
The FBI, CISA, ACSC, and NCSC urge network defenders to apply the following mitigations to reduce the risk of compromise by this threat.
IP addresses and executables files are listed below.
IP Addresses
91.214.124[.]143 162.55.137[.]20 154.16.192[.]70Executable files observed in this activity are identified in table 1.
Table 1: Executable Files
| Filename: | MicrosoftOutLookUpdater[.]exe | |
|---|---|---|
| MD5: | 1444884faed804667d8c2bfa0d63ab13 | |
| SHA-1: | 95E045446EFB8C9983EBFD85E39B4BE5D92C7A2A | |
| SHA-256: | c51fe5073bd493c7e8d83365aace3f9911437a0f2ae80042ba01ea46b55d2624 | |
| SHA-512: | 6451077B99C5F8ECC5C0CA88FE272156296BEB91218B39AE28A086DBA5E7E39813F044F9AF0FEDBB260941B1CD52FA237C098CBF4B2A822F08E3E98E934D0ECF | |
| Filename: | MicrosoftOutlookUpdater.bat | |
| MD5: | 6735be6deea16d03cb628b553d71fe91 | |
| SHA-1 | 95E045446EFB8C9983EBFD85E39B4BE5D92C7A2A | |
| SHA-256 | C51FE5073BD493C7E8D83365AACE3F9911437A0F2AE80042BA01EA46B55D2624 | |
| SHA-512 | 6451077B99C5F8ECC5C0CA88FE272156296BEB91218B39AE28A086DBA5E7E39813F044F9AF0FEDBB260941B1CD52FA237C098CBF4B2A822F08E3E98E934D0ECF | |
| Filename: | MicrosoftOutlookUpdater.xml | |
| MD5: | AA40C49E309959FA04B7E5AC111BB770 | |
| SHA-1 | F1D90E10E6E3654654E0A677763C9767C913F8F0 | |
| SHA-256 | 5C818FE43F05F4773AD20E0862280B0D5C66611BB12459A08442F55F148400A6 | |
| SHA-512 | E55A86159F2E869DCDB64FDC730DA893718E20D65A04071770BD32CAE75FF8C34704BDF9F72EF055A3B362759EDE3682B3883C4D9BCF87013076638664E8078E | |
| Filename: | GoogleChangeManagement.xml | |
| MD5: | AF2D86042602CBBDCC7F1E8EFA6423F9 | |
| SHA-1 | CDCD97F946B78831A9B88B0A5CD785288DC603C1 | |
| SHA-256 | 4C691CCD811B868D1934B4B8E9ED6D5DB85EF35504F85D860E8FD84C547EBF1D | |
| SHA-512 | 6473DAC67B75194DEEAEF37103BBA17936F6C16FFCD2A7345A5A46756996FAD748A97F36F8FD4BE4E1F264ECE313773CC5596099D68E71344D8135F50E5D8971 | |
| Filename: | Connector3.exe | |
| MD5: | e64064f76e59dea46a0768993697ef2f | |
| Filename: | Audio.exe or frpc.exe | |
| MD5: | b90f05b5e705e0b0cb47f51b985f84db | |
| SHA-1 | 5bd0690247dc1e446916800af169270f100d089b | |
| SHA-256: | 28332bdbfaeb8333dad5ada3c10819a1a015db9106d5e8a74beaaf03797511aa | |
| Vhash: | 017067555d5d15541az28!z | |
| Authentihash: | ed463da90504f3adb43ab82044cddab8922ba029511da9ad5a52b8c20bda65ee | |
| Imphash: | 93a138801d9601e4c36e6274c8b9d111 | |
| SSDEEP: | 98304:MeOuFco2Aate8mjOaFEKC8KZ1F4ANWyJXf/X+g4:MeHFV2AatevjOaDC8KZ1xNWy93U | |
| Note: |
Identical to “frpc.exe” available at: https://github[.]com/fatedier/frp/releases/download/v0.34.3/frp_0.34.3_windows_amd64.zip |
|
| Filename: | Frps.exe | |
| MD5: | 26f330dadcdd717ef575aa5bfcdbe76a | |
| SHA-1 | c4160aa55d092cf916a98f3b3ee8b940f2755053 | |
| SHA-256: | d7982ffe09f947e5b4237c9477af73a034114af03968e3c4ce462a029f072a5a | |
| Vhash: | 017057555d6d141az25!z | |
| Authentihash: | 40ed1568fef4c5f9d03c370b2b9b06a3d0bd32caca1850f509223b3cee2225ea | |
| Imphash: | 91802a615b3a5c4bcc05bc5f66a5b219 | |
| SSDEEP: | 196608:/qTLyGAlLrOt8enYfrhkhBnfY0NIPvoOQiE:GLHiLrSfY5voO | |
| Note: |
Identical to “frps.exe” available at: https://github[.]com/fatedier/frp/releases/download/v0.33.0/frp_0.33.0_windows_amd64.zip |
Table 2 identifies MITRE ATT&CK Tactics and techniques observed in this activity.
Table 2: Observed Tactics and Techniques
To report suspicious or criminal activity related to information found in this Joint Cybersecurity Advisory, contact your local FBI field office at https://www.fbi.gov/contact-us/field-offices, or the FBI’s 24/7 Cyber Watch (CyWatch) at (855) 292-3937 or by e-mail at CyWatch@fbi.gov. When available, please include the following information regarding the incident: date, time, and location of the incident; type of activity; number of people affected; type of equipment used for the activity; the name of the submitting company or organization; and a designated point of contact. To request incident response resources or technical assistance related to these threats, contact CISA at CISAServiceDesk@cisa.dhs.gov. Australian organizations can visit cyber.gov.au or call 1300 292 371 (1300 CYBER 1) to report cybersecurity incidents and access alerts and advisories.
Initial Version: November 17, 2021
This product is provided subject to this Notification and this Privacy & Use policy.
This article is contributed. See the original author and article here.
Mark a device non-compliant after 7 days of inactivity in the Microsoft Defender for Endpoint mobile app.
To be protected, customers must be confident that their end users’ devices are compliant with security policies. Today, end users are often able to bypass protections that are set by their organization. For example, users uninstall, disable settings/permissions, and force stop or clear storage of their Defender for Endpoint mobile app. Removing or disabling the Defender for Endpoint app can leave a mobile device more vulnerable to an attack.
We are excited to announce the public preview of tamper protection for mobile devices. This new feature helps ensure the retention of the Defender for Endpoint mobile app on users’ devices and helps protect devices persistently. This feature detects devices that are out of protection for over 7 days, due to tampering with the Defender for Endpoint mobile app. These devices are marked non-compliant in Microsoft Intune (part of Microsoft Endpoint Manager).
Organizations can also set up Conditional Access policies to enforce the activation and use of the Defender for Endpoint mobile app. With these Conditional Access policies in place, users can access corporate resources only if their devices are in a compliant state. Blocked users can regain access only after the Defender for Endpoint mobile app is set up with all required permissions and the app is actively sending signals to Defender for Endpoint.
For this initial release we have scoped the detection of devices out of protection for 7 days. In upcoming releases, we plan to make this duration configurable by your security admin or your tenant admin.
How to get and configure this feature
Try tamper protection for mobile devices out and let us know how it goes! We’re excited to share these new updates with you and continue to build on security capabilities across platforms.
We look forward to hearing your feedback!

This article is contributed. See the original author and article here.
Thank you to everyone from across the globe who attended Microsoft Ignite last week. This year’s virtual event was packed with learning sessions, announcements, engaging conversations, and Q&Asfar too much content to absorb in just three days. To help you catch up on the news and content from Microsoft Ignite, we’ve rounded up the highlights for you.
To get started, we recommend watching three featured sessions. Start with Satya Nadella’s opening keynotean overview of trends and innovations across the Microsoft cloud that will transform your business. Then, watch the session, “Microsoft Ignite into Focus: Business Applications,” for a closer look at new and upcoming capabilities for Microsoft Dynamics 365 and Microsoft Power Platform. Also, learn about innovation across the Microsoft cloud that will allow every organization to build a hyperconnected business, providing the agility and flexibility for organizations and employees to thrive now and into the future.
Next, explore innovation across Dynamics 365 discussed in breakout and on-demand sessions during the event, starting with the highlights below.
We’re making it easier to connect with people, information, and conversations from Dynamics 365 workspaces, reducing the need to switch between apps to access who and what you need in the moment. At Microsoft Ignite, we announced Context IQ, a set of capabilities for Dynamics 365 and Microsoft 365 that make information, people, and conversations more accessible in the moment, reducing the need to switch between apps. Context IQ helps ensure business users can access documents and records, colleagues across the organization, and conversationsall in the flow of work, whether from within Dynamics 365 or Microsoft 365 applications.
Read a deep dive on the Dynamics 365 blog and watch the Microsoft Ignite sessionto see Context IQ in action.
Organizations must be able to unlock the power of customer data to create experiences that build strong relationships. The Microsoft Customer Experience Platform, introduced at Microsoft Ignite, is a complete solution that puts organizations in control of their customer data to personalize, automate and orchestrate journeys during the entire customer lifecycle of awareness, to purchase, to service. With a deep understanding of customers and rich, out-of-the-box insights, organizations can now determine and predict intent to deliver the right content on the right channel and in the right moment.
Read a deep dive on the Dynamics 365 blog and watch the Microsoft Ignite session to see these capabilities in action.
At Microsoft Ignite, we announced the general availability of our first-party voice channel for Dynamics 365 Customer Service, built on the planet-scale communications platform that powers Microsoft Teams. The addition of the voice channel helps your organization provide consistent and personalized service to customers across all channels with one data-driven, AI-infused, end-to-end solutionno integration required.
The new first-party voice solutions join a host of other capabilities demonstrated at Microsoft Ignite, including conversational IVR, call transcription, sentiment analysis, proactive recommendations, and other built-in AI capabilities that empower your agents to resolve customer issues quickly.
Read a deep dive on the Dynamics 365 blog and watch the Microsoft Ignite session to see these capabilities in action.
The current supply chain crisis spotlights the need for new levels of visibility across your entire supply chain. At Microsoft Ignite, we announced Dynamics 365 Supply Chain Insights, providing organizations with the visibility they need along with the intelligence to predict and proactively manage supply chain challenges.
We also announced updates to Dynamics 365 Supply Chain Management to optimize production processes. New capabilities enable your organization to innovate with intelligent manufacturing operations by easily adapting to new business models, improving planning agility, enhancing the visibility of your shop floor, and ensuring round-the-clock uptime and business continuity.
In addition, Microsoft introduced the preview of the Microsoft Cloud for Manufacturing, which connects experiences across the end-to-end product and service lifecycle and lights up the entire Microsoft cloud with capabilities specifically tailored to manufacturing.
Explore updates to Dynamics 365 Supply Chain Management, learn how to mitigate disruptions with Dynamics 365 Supply Chain Insights, and read about theMicrosoft Cloud for Manufacturing preview. Also, watch Microsoft Ignite sessions that take a deep dive into Dynamics 365 Supply Chain Insights, Dynamics 365 Supply Chain Management, and Microsoft Cloud for Manufacturing.
Announced at Microsoft Ignite, the preview of Dynamics 365 Connected Spaces, previously Dynamics 365 Connected Store, signals our expansion from retail scenarios to all spaces, from retail to manufacturing. With Dynamics 365 Connected Spaces, your organization can harness observational data (the data we generate as we move throughout the world), use AI-powered models to unlock insights about your environment, and respond in real-time to trends and patterns.
Learn more on the Dynamics 365 blog and watch the Microsoft Ignite session to see these capabilities in action.
Be sure to catch up on all the news and sessions from Microsoft Ignite, now available on-demandincluding downloadable videos of sessions, transcripts, and related resources. If you need a roadmap, check out our guide to Microsoft Ignite.
The post Microsoft Ignite recap: Dynamics 365 news and announcements you may have missed appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
Google has released Chrome version 96.0.4664.45 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.
CISA encourages users and administrators to review the Chrome Release Note and apply the necessary updates as soon as possible.
This article is contributed. See the original author and article here.
Customer engagement professionals still need to build relationships, trust, and loyalty to be successful, but how we achieve these outcomes has fundamentally changed. Those changes offer the opportunity to be more effective than ever at driving these results.
To meet customer expectations, marketers are looking to create end-to-end customer experiences that are customer-led, highly personalized, and that reach their customers wherever they are, across all physical and digital channels. Data and AI make all these things possible and bring us into an exciting new frontierfrom the reactive to the predictive era.
Microsoft Dynamics 365 Marketing brings together the worlds of customer experience and marketing automation, empowering businesses to orchestrate individualized journeys across all touchpoints to strengthen relationships and earn loyalty.
With the 2021 release wave 2, we focused on improving processes and capabilities for creating moments-based customer journeys that span all customer touchpoints, and on taking personalization to the next level, all with less effort. Here are a few highlights of these exciting new innovations that will be releasing over the next few months and what they can mean for marketers and business users alike.
To truly embrace customer-led journeys you must be ready to engage and respond when the customer wants to engage, in the moments that matter to them. Here are new ways Dynamics 365 Marketing will help you do just that.
Send SMS messages using Twilio and TeleSign integration. Engaging customers in moments that matter means that connecting with mobile users is a must. Dynamics 365 Marketing enables you to utilize the SMS channel to send fast, transactional communications and marketing messages. In this release, we have extended these capabilities by enabling integration with Twilio and TeleSign for the ultimate level of flexibility.
Reach more customers with a 10X increase in the scale of interactions in real-time marketing journeys. To reach your customers in moments that matter to them, you must be able to scale. Prospects and customers are starting to take the lead on how frequently they want to interact with companies they do business with. Companies must be able to respond to customers whenever they want to engage. We now support up to 100 million outbound interactions (email, SMS, or push notifications) per month to a maximum of 20 million contacts using real-time marketing journeys. With the added interaction capacity, you can communicate as much as you need to help move prospects and customers along their buying journey.
Engaging your customers in an individually personalized way is easier than ever thanks to the innovative new capabilities added to Dynamics 365 Marketing.
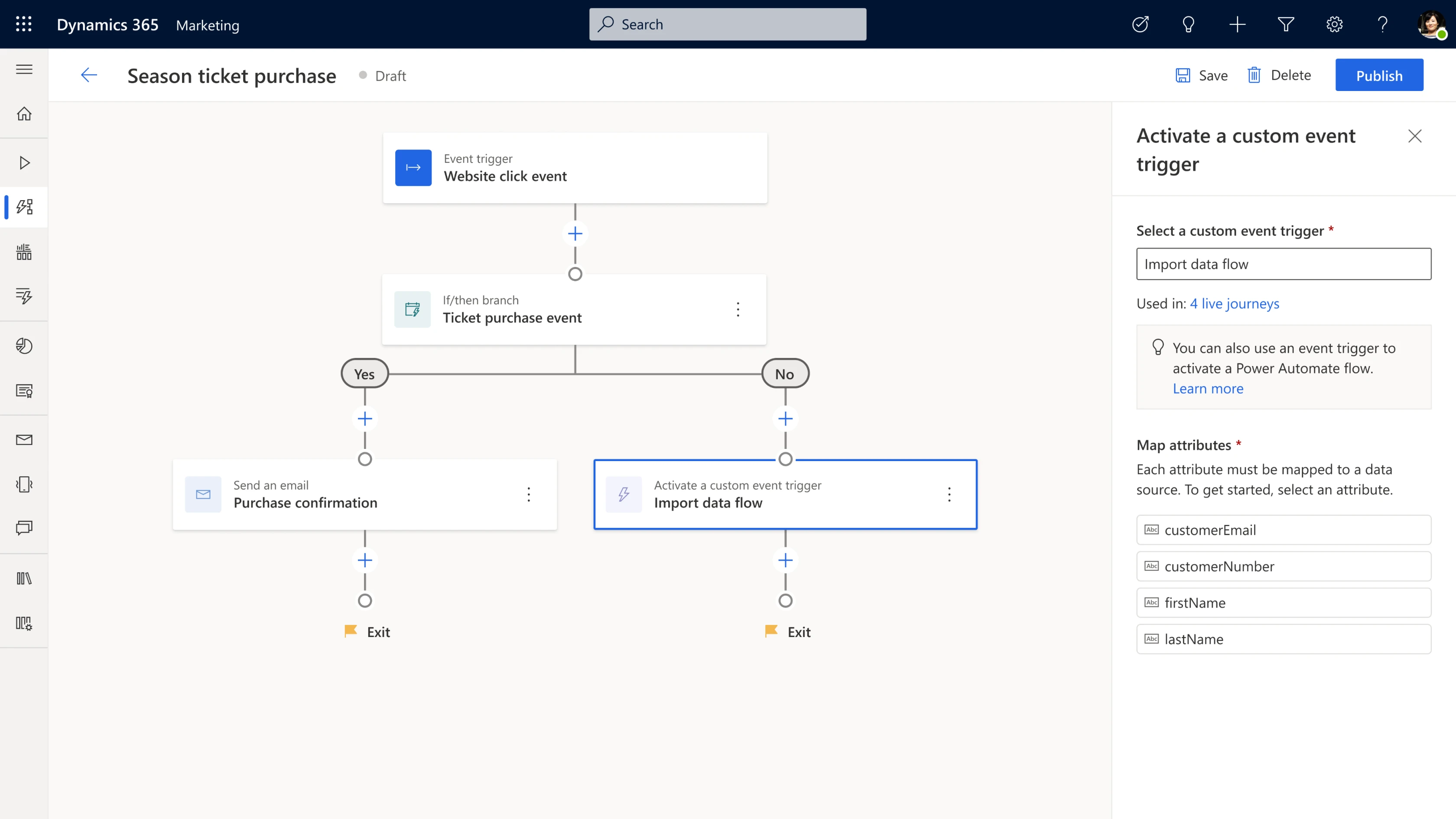
Deliver rich customer experiences by raising custom events from journey steps. Because every business is unique, you may need to define custom processes to enhance your journeys. By using Microsoft Power Automate Flows, you will have limitless customization and precise control of your customer experience.
You can call a Power Automate Flow from the journey canvas to connect with proprietary and external business systems. This end-to-end integration allows you to leverage the entire Power Automate ecosystem of connectors and controls to deliver the unique experience your customers demand. And what’s even better, is that anyone, from citizen marketing developers to pro marketing operations teams, IT professionals, or partners, can create very advanced custom scenarios in only a few clicks.
Personalize emails to include lists of related data. To save time and to further personalize your emails, you can now include lists of related data that are specific to the individual receiving the email. For example, you can add a list of sessions in a conference registration email or a list of items purchased in an order confirmation email. The ‘helper tool’ in real-time marketing generates the code for conditional statements and lists for you, making it easier to ensure your syntax is correct.
Gain more control over journey branching conditions through increased attribute support. Creating personalized journeys for customers based on their demographics and behaviors can help increase engagement. With this release, you can now create journey branches based on any attribute associated with the customer or event trigger that started the journey. In addition, for attributes based on date and time, you can create branches based on relative or partial dates.
A deep understanding of your customer coupled with knowledge of what has worked before can bring amazing customer experiences to life.
Use AI-powered ideas to automatically generate content for emails. Looking for the right email copy to catch a customer’s eye? Use Content Ideas to help you get writing inspiration and move faster from concept to execution. No more needing to start from a blank screen. This new capability uses powerful AI technology to generate custom text ideas in your Dynamics 365 Marketing email editor.
We’re taking an intentional approach to integrating our responsible AI principles by building this experience with transparency and control, while boosting value for you. The automated ideas are based on your key points and recent emails sent by your organization. Now you can take advantage of this breakthrough technology to deliver the most impactful content to your audience.
Optimize the performance of emails in the new outbound marketing email editor with A/B testing. A good way to create an email that resonates with your audience is to test different versions with subsets of your recipients, and then analyze interaction records to determine which one is better received. The new editor in Dynamics 365 Marketing now can A/B test your emails, allowing you to optimize the performance of your emails.
Use natural language to create targeted segments. You can also use natural language sentences to build segments faster in Dynamics 365 Marketing. We introduced a preview of this capability in our previous release and have been working to refine, enhance, and continue the AI model training, so it’s better than ever before. Just use simple words to specify the attributes and logic for the segment you want to target, the AI-powered model does the rest for you. For example, using natural language, you can create a segment of “Contacts who were born between 1970 and 2000 and make more than $50K”, the correct query fields will be filled in for you and the segment will be generated automatically.
The innovations in this 2021 release wave 2 for Dynamics 365 Marketing support our Dynamics 365 vision to build data first, AI-enabled applications. Starting from data, we bring new insights and automation to your business processes and customer experiences. We power those processes and experiences with AI and next best actions while upholding Microsoft’s commitment to building AI responsibly, using our six principles as a lens for innovation. I’m excited to take you on this exciting journey with usas always, there will be more to come.
To learn more about how your organization can elevate your customer experiences, visit the Dynamics 365 Marketing webpage and sign up for a free Dynamics 365 Marketing trial to explore real-time customer journey orchestration and the other rich capabilities offered in Dynamics 365 Marketing.
The post Dynamics 365 Marketing is leading the way with personalized engagement appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
Recent Comments