Improve seller productivity with a sales cadence
This article is contributed. See the original author and article here.
In sales, planning is everything. Without a plan, a sales rep might give up too easily on a prospect or appear too aggressive. A potential customer might forget about a proposal or become annoyed by too-frequent contacts. Creating a step-by-step plan for how to follow up with prospects in each stage of the sales process is the basis for a sales cadence. Microsoft Dynamics 365 Sales tools help you create, manage, and scale customized sales cadences across your organization.
The top salespeople have a well-crafted plan to get their desired results, whether they are demonstrating a product or following up with leads. A successful plan, or sales cadence, involves knowing where your prospects are in the buyer’s journey and understanding how to reach them the right way, with the right message, at the right time to move them to the next step.
If you fail to plan, you are planning to fail.
A modern proverb
In this post, you’ll learn:
- What a sales cadence is
- What to consider when designing a sales cadence
- What an effective sales cadence looks like
- How Dynamics 365 Sales can help you build a sales cadence
What is a sales cadence?
A sales cadence is a detailed plan to connect with prospects and close deals. A sales cadence includes a prescribed sequence of activities, like reaching out on LinkedIn, sending emails, making calls, sharing case studies, arranging meetings, and sending text messages, which happen at specified intervals.
An effective sales cadence improves the efficiency of sales reps. A sales cadence guides sellers on which prospects to connect with, what communication channel to use, and what information to share at each touchpoint. This structured approach reduces guesswork and aims to grow the sales pipeline and conversion rate.
Managers create a sales cadence to guide sales reps in handling different types of prospects and sales scenarios. For example, one cadence could be used for inbound inquiry leads, and another cadence could be used for upcoming renewals.
As organizations mature, they can evolve their cadences to adapt to specific geographies, industries, companies, languages, and other parameters.
A strong sales cadence library also helps you scale your sales organization. Automated sales cadences ease the onboarding process for sellers as you grow, building in best practices and sequencing their activities.
How to design a sales cadence
When you design your sales cadences, consider these five elements:
- Prospects: It all starts with knowing your potential customers. What challenges or obstacles do they have? Why are they looking for a solution? What platforms do they use? What constraints do they contend with? What are their skills? Who is the decision maker?
- Communication channel:Reach out to prospects using the right channel, such as email, a phone call, messaging apps, or LinkedIn.
- Wait time: Consider a strategic delay between subsequent steps. You don’t want to be too soon or too late in your follow-ups.
- Attempts: Understand the optimal number of touchpoints to establish contact and build a relationship.
- Messaging:Use the right messaging, content, tone, and personalization to engage with prospects.
It’s important to note that creating an effective plan is not a one-time process. It takes time and iteration to fine-tune your sales cadences.
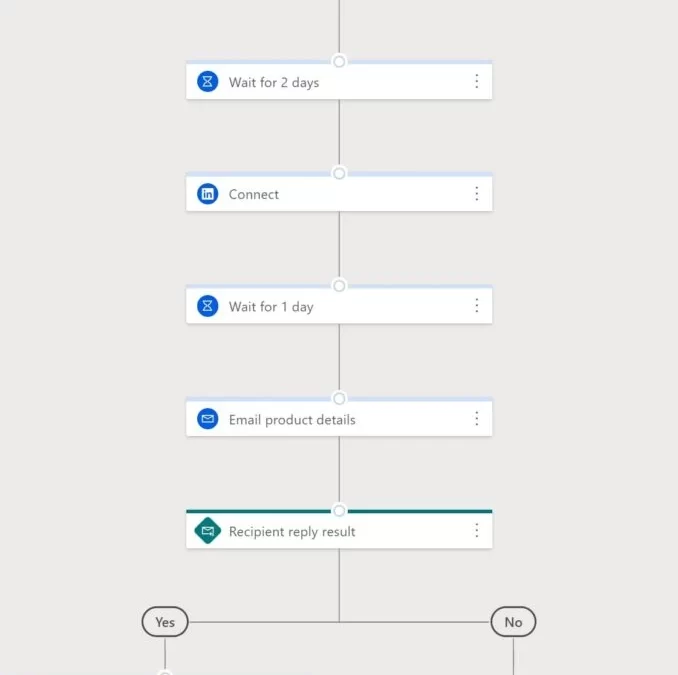
Example: A sales cadence for inbound inquiries
Here’s an example of a sales cadence for responding to inbound inquiries.
- Target: Leads that have reached out through your website or other channels.
- Purpose: Focus on and respond to high-priority inquiries to improve your conversion rate.
- Description: By responding immediately and through multiple channels, you are more likely to achieve a higher conversion rate. Since responding within the first hour increases your chance to close the deal by seven times, start with an automated email response, then follow up with a phone call. Connect on a social platform like LinkedIn. Finally, send an email that provides relevant information about your product or services.
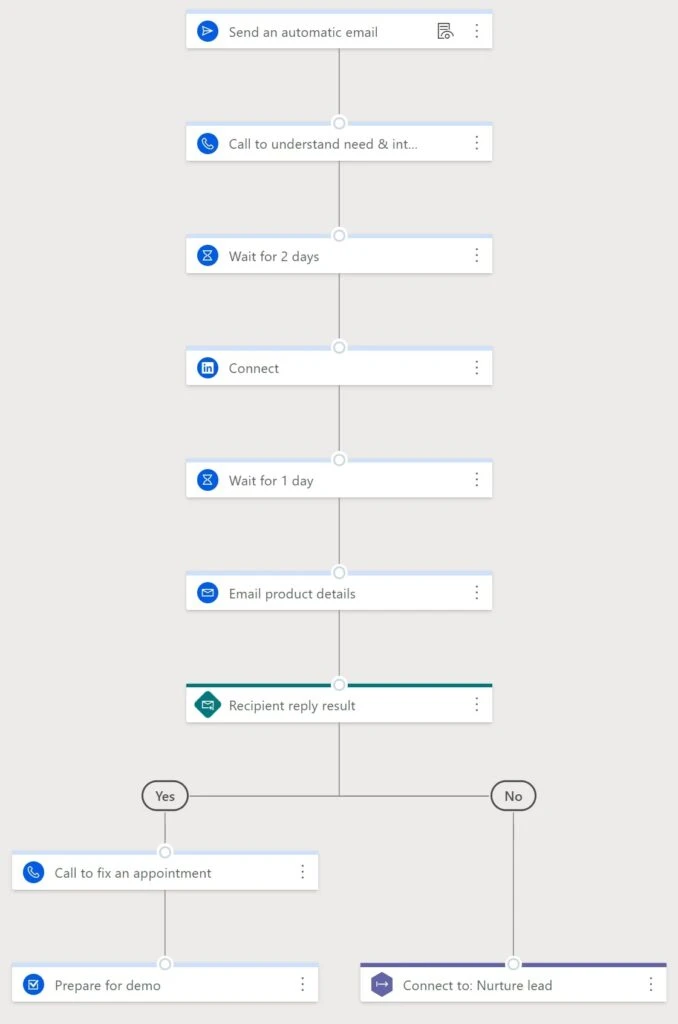
Create a sales cadence with sequence designer
The sales accelerator capability in Dynamics 365 Sales helps sellers spend less time searching for the best next customer to reach out to. Design and build your sales cadences in the sequence designer. Sales accelerator gathers information from multiple sources to build a strong and prioritized pipeline, offers context, and surfaces recommendations throughout each step in the sequence, speeding the sales process.
To create a sequence, you go to the Sales Insights settings area and open the Sequences page. For more details, check out the documentation: Create and activate a sequence.
You can use the sequence designer to configure sequences of activities for specific prospects, leads, opportunities, contacts, and so on, applying different strategies depending on priority. For example, leads of lower priority might have more automated email steps, whereas leads from your targeted accounts might have more personalized touchpoints.
As in the example sales cadence shown earlier, sequences can include multiple activities, with wait times between activities as needed. You can branch activities based on the response, such as if an email is opened or a reply is received. Using sales accelerator’s tight integration with LinkedIn, you can even send LinkedIn InMail or create a connect request as part of your sales cadence.
Next steps
A good sales cadence is a necessary to improve seller productivity, increase conversion rates, and close more deals. As we adjust to virtual ways of working, digitizing sales becomes a priority for most organizations. To get started, use sales accelerator in Dynamics 365 Sales to set up a sales cadence for the most common scenarios faced by the sales team.
To start building your own sequences in Dynamics 365 Sales, visit the documentation: Manage sequences. If you use a custom app, also refer to this section of the FAQ page for sales accelerator: How to add work list site map to your custom app.
Access to sales accelerator has now been made easier: new and existing customers using Dynamics 365 Sales (excluding Dynamics 365 Sales Professional) will now see sales accelerator and sequences available for quick setup. Read the documentation to learn more about setting up digital selling capabilities.
The post Improve seller productivity with a sales cadence appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


 It’s the second day of Identity Theft Awareness Week and today we’re talking about steps that can help reduce your risk of identity theft.
It’s the second day of Identity Theft Awareness Week and today we’re talking about steps that can help reduce your risk of identity theft.



 Today we’re kicking off Identity Theft Awareness Week 2022. Identity thieves have been busier than ever during the pandemic, with scammers and identity thieves after people’s information to apply for credit, unemployment benefits, file taxes, buy things, or get medical services. But there are some things you can do to protect yourself, and this week, you’ll learn how.
Today we’re kicking off Identity Theft Awareness Week 2022. Identity thieves have been busier than ever during the pandemic, with scammers and identity thieves after people’s information to apply for credit, unemployment benefits, file taxes, buy things, or get medical services. But there are some things you can do to protect yourself, and this week, you’ll learn how.
Recent Comments