by Contributed | Aug 15, 2022 | Technology
This article is contributed. See the original author and article here.
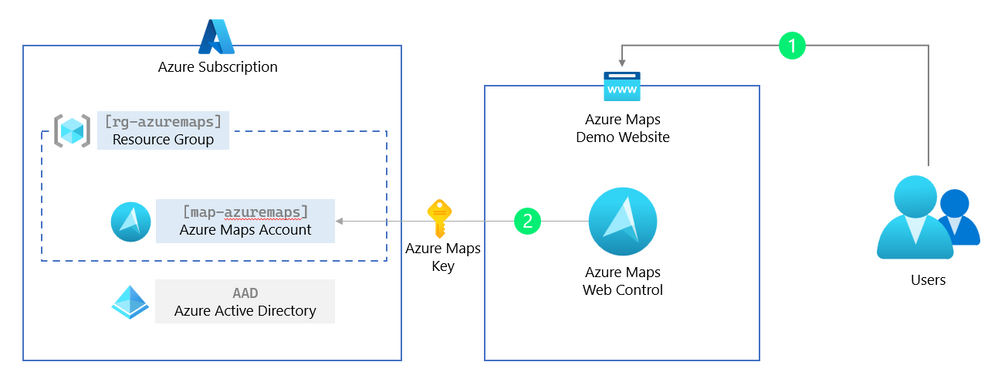
One of the requirements when building a business application is that only authenticated users can access it. So how do you use Azure Maps in combination with authentication and authorization? When you are reading our Azure Maps docs, you find that we support many different authentication scenarios, which makes it hard for some developers to implement. This blogpost will focus on the most requested scenario for Azure Maps: Have a .NET web application with an embedded Azure Maps web control where only authenticated users can see the website and use the map. Follow me step by step.
In this article, we make use of .NET 6.0 and the C# programming language, download, and install the latest version of .NET from https://dot.net/.
To make it easier to edit source code, we also recommend installing Visual Studio Code, which is a lightweight but powerful source code editor from Microsoft https://code.visualstudio.com/.
Before you can use Azure Maps, you need to sign up for a free Azure subscription, what you can do here https://azure.microsoft.com/free.
And as last, install the Azure Command-Line Interface (CLI) tools. Read here How to install the Azure CLI.
First, we start with a basic .NET web application and Azure Maps. No authentication yet, that will come in the next paragraph. This first step will use an Azure Maps Key (a ‘shared Key authentication’ or subscription key) that should not be used in production. An Azure Maps Key has complete control over your Azure Maps resource. In the next paragraph, we will remove this key and replace this with managed identities for Azure resources.
We start by creating a folder and adding a new web application to it, and we then open the newly created web application in Visual Studio Code. Start PowerShell (or any other terminal) and enter the following commands:
mkdir AzureMapsDemo
cd .AzureMapsDemo
dotnet new mvc
code .
Next, we need to add the Azure Maps web control to the Home view, open the file Views/Home/index.cshtml, and replace all the content with:
@{
ViewData["Title"] = "Home Page";
}
<div class="text-center">
<h1 class="display-4">Azure Maps</h1>
<p>Learn about <a href="https://docs.microsoft.com/azure/azure-maps/">building Azure Maps apps with ASP.NET Core</a>.</p>
</div>
<div id="myMap" style="width:100%;min-width:290px;height:600px;"></div>
@section Scripts
{
<link rel="stylesheet" href="https://atlas.microsoft.com/sdk/javascript/mapcontrol/2/atlas.min.css" />
https://atlas.microsoft.com/sdk/javascript/mapcontrol/2/atlas.min.js
<script>
var map;
// Initialize a map instance.
map = new atlas.Map('myMap', {
center: [-122.33, 47.6],
zoom: 12,
style: 'satellite_road_labels',
view: 'Auto',
// Add authentication details for connecting to Azure Maps.
authOptions: {
authType: 'subscriptionKey',
subscriptionKey: '[YOUR_AZURE_MAPS_KEY]'
}
});
// Wait until the map resources are ready.
map.events.add('ready', function() {
// Add your post map load code here.
});
</script>
}
As you can see, we need a subscription key for Azure Maps before starting the web application and using the map. In the next step, we are creating an Azure resource group and adding a new Azure Maps Account. Then we extract the Azure Maps Primary Key from this Azure Maps Account, which we use in our Home view.
1.1 Login into your Azure subscription and save the Azure subscription Id, we need this for later.
1.2 (Optional) Select the subscription where you would like to create the Azure Maps Account.
az account set --subscription "<your subscription>"
1.3 Create a resource group, and change the name and the location for your needs.
az group create -l westeurope -n rg-azuremaps
1.4 Create the Azure Maps Account, and accept the terms and conditions. Save the uniqueId for later.
az maps account create -n map-azuremaps -g rg-azuremaps -s "G2" --kind "Gen2"
1.5 Now we can extract the Azure Maps Primary Key and add it to the Home view in our web application.
az maps account keys list -n map-azuremaps -g rg-azuremaps
1.6 Replace the [YOUR_AZURE_MAPS_KEY] in the file Views/Home/index.cshtml with the Azure Maps Primary Key we just listed in step 1.5.
1.7 Now we can run and test our AzureMapsDemo web application.
dotnet run

In this paragraph, we are removing the ‘shared Key authentication’ (the Azure Maps subscription key) and replacing this with a more secure and production ready managed identities for Azure Maps.
Managed identities for Azure resources provide Azure services with an automatically managed application-based security principal that can authenticate with Azure AD. With Azure role-based access control (Azure RBAC), the managed identity security principal can be authorized to access Azure Maps services.
This means that the web application can request a short-lived token to get access to Azure Maps from Azure Active Directory (AAD). Because this is managed, we do not need to know any passwords or create users. However, to get this token back to the client (the Azure Maps Web Controls runs in the users’ browser), we need to create a simple token proxy API in our web application to forward this token.
We start by creating an Azure Web App where our web application will be hosted and running. This Azure Web App then needs to have rights to get a token for Azure Maps, which we will forward using the token proxy API we create in the below steps.
2.1 Create an app service plan and web app, and change the unique name and the location for your needs.
az appservice plan create -g rg-azuremaps -n plan-azuremaps -l westeurope
az webapp create -g rg-azuremaps -p plan-azuremaps -n web-azuremaps -r "dotnet:6"
2.2 Next, we create a system-assigned identity for this web app. When finished, we are presented with the principalId, we need this in the next step. To make it simple, you can see the system-assigned identity as an account Azure manages.
az webapp identity assign -n web-azuremaps -g rg-azuremaps
2.3 Now that we have the principalId (use this in the below command) for this system-assigned identity, we can assign the role (what can this system-assigned identity do and access). In this step, we assign the role of Azure Maps Data Reader to this system-assigned identity, which means that this system-assigned identity can only read and not modify or delete data from your Azure Maps account. You already see this is way more secure than the plain Azure Maps key, which has all the rights to do everything. We also need the [YOUR_AZURE_SUBSCRIPTION_ID] from the first step.
az role assignment create --assignee "[PRINCIPAL_ID]" --role "Azure Maps Data Reader" --scope "/subscriptions/[YOUR_AZURE_SUBSCRIPTION_ID]/resourceGroups/rg-azuremaps/providers/Microsoft.Maps/accounts/map-azuremaps"
Hint to get your Azure subscription Id use the following command: az account subscription list
2.4 To get the access token from Azure Active Directory (AAD) back to the client (the web browser), we will create a simple proxy API forwarding this access token. We start by creating an API controller in our web application and adding the GetAzureMapsToken() method.
2.5 First, we must add the Azure Identity NuGet package to our web application.
dotnet add package Azure.Identity
2.6 Next, we create a new ApiController.cs file under the folder Controllers. This new ApiController.cs file will have a method GetAzureMapsToken() that is acting like a proxy for our access token. Read here more about Controllers in a MVC web application.
using Azure.Core;
using Azure.Identity;
using Microsoft.AspNetCore.Mvc;
namespace AzureMapsDemo.Controllers;
public class ApiController : Controller
{
private static readonly DefaultAzureCredential tokenProvider = new();
public async Task<IActionResult> GetAzureMapsToken()
{
var accessToken = await tokenProvider.GetTokenAsync(
new TokenRequestContext(new[] { "https://atlas.microsoft.com/.default" })
);
return new OkObjectResult(accessToken.Token);
}
}
2.7 Now that we have our token API proxy, we only need to change the authentication options for the Azure Maps Web Control. Replace in the file Views/Home/index.cshtml the authOptions with the following:
// Add authentication details for connecting to Azure Maps.
authOptions: {
// Use Azure Active Directory authentication.
authType: 'anonymous',
// Your Azure Maps client id for accessing your Azure Maps account.
clientId: '[YOUR_AZUREMAPS_CLIENT_ID]',
getToken: function(resolve, reject, map) {
// URL to your authentication service that retrieves
// an Azure Active Directory Token.
var tokenServiceUrl = "/api/GetAzureMapsToken";
fetch(tokenServiceUrl).then(r => r.text()).then(token => resolve(token));
}
}
2.8 We also need to update the clientId we saved when we created the Azure Maps account. (Optional) To get the Azure Maps Client Id again, use the value of uniqueId from:
az maps account show -n map-azuremaps -g rg-azuremaps
2.9 Now we can build and deploy our web application that uses managed identities for Azure Maps. We first build and create a release package.
dotnet publish --configuration Release
Compress-Archive -Path binReleasenet6.0publish* -DestinationPath release1.zip
2.10 Then we publish our release package to the Azure Web App.
az webapp deployment source config-zip -g rg-azuremaps -n web-azuremaps --src release1.zip
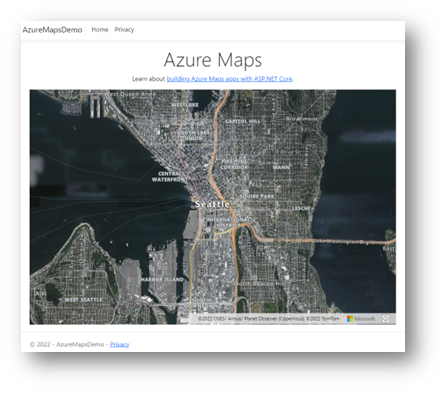
2.11 Open a web browser and navigate to the https://web-azuremaps.azurewebsites.net/ where the web-azuremaps subdomain is your unique name when creating the Azure Web App. The application looks like this:
2.12. (Optional) We can also navigate to the token proxy API https://web-azuremaps.azurewebsites.net/api/GetAzureMapsToken, copy the token, and past this in the https://jwt.ms/ tool to decode and inspect the token.
3. Protecting the web application and the Azure Maps token proxy API
The web application we built in the last paragraph uses managed identities, and the Azure Maps Web Control uses the access token. Unfortunately, the web application and token proxy API are still accessible to everybody. Therefore, in this paragraph, we are adding the Azure Active Directory (AAD) Authentication to the web application and the token proxy API, so that only authenticated users can view the web application and use the Azure Maps Web Control in a secure way.
3.1 We start by registering an application in the Azure Active Directory, and we need this application registration later to give access to the web application and token proxy API.
az ad app create --display-name "Azure Maps Demo App" --web-redirect-uris https://web-azuremaps.azurewebsites.net/signin-oidc --enable-access-token-issuance true --enable-id-token-issuance true --sign-in-audience AzureADMyOrg
3.2 We need to add four Identity and Authentication NuGet packages to our web application.
dotnet add package Microsoft.Identity.Web
dotnet add package Microsoft.Identity.Web.UI
dotnet add package Microsoft.AspNetCore.Authentication.JwtBearer
dotnet add package Microsoft.AspNetCore.Authentication.OpenIdConnect
3.3 Next, we need to add the [Authorize] attribute to every controller in our web application. Below is our token API proxy controller as an example. Do not forget to do this also for the Home controller!
using Azure.Core;
using Azure.Identity;
using Microsoft.AspNetCore.Mvc;
using Microsoft.AspNetCore.Authorization;
namespace AzureMapsDemo.Controllers;
[Authorize]
public class ApiController : Controller
{
3.4 In the program startup file Program.cs we need to add the Authentication and Authentication logic. Replace all the default code in the Program.cs file with the following:
using Microsoft.AspNetCore.Authentication;
using Microsoft.AspNetCore.Authentication.OpenIdConnect;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Mvc.Authorization;
using Microsoft.Identity.Web;
using Microsoft.Identity.Web.UI;
var builder = WebApplication.CreateBuilder(args);
// Add services to the container.
builder.Services.AddAuthentication(OpenIdConnectDefaults.AuthenticationScheme)
.AddMicrosoftIdentityWebApp(builder.Configuration.GetSection("AzureAd"));
builder.Services.AddAuthorization(options =>
{
options.FallbackPolicy = options.DefaultPolicy;
});
builder.Services.AddControllersWithViews(options =>
{
var policy = new AuthorizationPolicyBuilder()
.RequireAuthenticatedUser()
.Build();
options.Filters.Add(new AuthorizeFilter(policy));
});
builder.Services.AddRazorPages()
.AddMicrosoftIdentityUI();
var app = builder.Build();
// Configure the HTTP request pipeline.
if (!app.Environment.IsDevelopment())
{
app.UseExceptionHandler("/Home/Error");
// The default HSTS value is 30 days. You may want to change this for production scenarios, see https://aka.ms/aspnetcore-hsts.
app.UseHsts();
}
app.UseHttpsRedirection();
app.UseStaticFiles();
app.UseRouting();
app.UseAuthentication();
app.UseAuthorization();
app.MapControllerRoute(
name: "default",
pattern: "{controller=Home}/{action=Index}/{id?}");
app.MapRazorPages();
app.MapControllers();
app.Run();
3.5 The last step before redeploying our secure web application is to add the details from our registered application in the Azure Active Directory into the configuration file. Open the appsettings.json file and replace this with:
{
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"Domain": "[PUBLISHER_DOMAIN]",
"TenantId": "[AAD_TENANT_ID]",
"ClientId": "[APP_ID]",
"CallbackPath": "/signin-oidc"
},
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft.AspNetCore": "Warning"
}
},
"AllowedHosts": "*"
}
3.6 Replace the [PUBLISHER_DOMAIN] and [APP_ID] with the values we saved in step 1 when we registered the application. Your Azure Active Directory Tenant ID [AAD_TENANT_ID], you can get with the following command:
3.7 Now we can build and deploy our web application that uses Azure Active Directory to login. We first build and create a release package.
dotnet publish --configuration Release
Compress-Archive -Path binReleasenet6.0publish* -DestinationPath release2.zip
3.8 Then we publish our release package to the Azure Web App.
az webapp deployment source config-zip -g rg-azuremaps -n web-azuremaps --src release2.zip
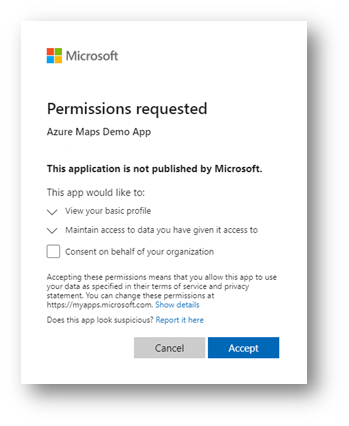
3.9 Open a web browser and navigate to the https://web-azuremaps.azurewebsites.net/ where the web-azuremaps subdomain is your unique name when creating the Azure Web App. You are now prompted to log in with your work or school account (AAD) and give permissions.
3.10 A recommended last step is to disable the use of the Azure Maps Key authentication.
az maps account update -n map-azuremaps -g rg-azuremaps --disable-local-auth true -s "G2"
When we have done all the steps in this step-by-step article, you have a protected web application in combination with Azure Maps that uses of Azure Active Directory, Azure role-based access control (Azure RBAC), and Azure Maps tokens. I recommend that you read our Authentication best practices and Azure Maps documentation. As an example, the Azure Maps Samples website uses most of the steps described in this article. Happy coding.
by Contributed | Aug 12, 2022 | Technology
This article is contributed. See the original author and article here.
Hey ADF fans! Here is a quick note on an important update that we will be making to ADF …
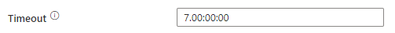
In Azure Data Factory and Azure Synapse Analytics, the default timeout for new pipeline activities is 7 days for most activities:

In a few weeks, we are going to change that default for new activities in your pipelines to 12 hours before the activity will timeout. This change is in direct response to your feedback. We gathered feedback across channels directly from the ADF product, customer interviews, and on social media.
It became very clear that the default timeout of 7 days was too long and far outside of the most common activity execution times we observed and heard from you. Keep in mind that you should adjust the timeout on long-running processes (i.e. large copy activity and data flow jobs) to a higher value if needed.
When this change is deployed to ADF and Synapse pipelines, we will include banners and notifications in your browser UI to indicate this is the new default value for timeouts so that you are aware it has been implemented.
As always, a big Thank You for using ADF and for sharing your ideas and feedback on ADF. It helps us tremendously in the product team at Microsoft Azure to make ADF and Synapse the best products for data engineers!
by Contributed | Aug 12, 2022 | Technology
This article is contributed. See the original author and article here.
We have released an update to Microsoft.Data.SqlClient 3.1, version 3.1.1. The update addresses several issues that are important to our customers.
Updates in Microsoft.Data.SqlClient 3.1.1 include:
Fixed
- Fixed null SqlBinary as rowversion. #1700
- Fixed Kerberos authentication failure when using .NET 6. #1696
- Fixed NullReferenceException during Azure Active Directory authentication. #1695
- Removed union overlay design and use reflection in
SqlTypeWorkarounds. #1699
To get the new package, add a NuGet reference to Microsoft.Data.SqlClient in your application.
For the list of changes in Microsoft.Data.SqlClient 3.1.1, you can also see the Release Notes.
If you encounter any issues or have any feedback, head over to the SqlClient GitHub repository and submit an issue.
David Engel
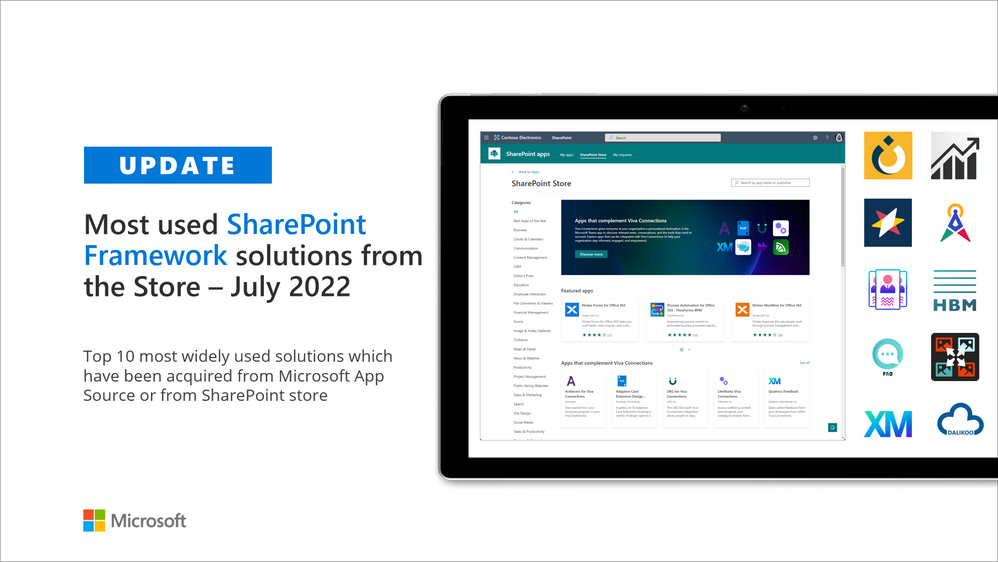
by Contributed | Aug 11, 2022 | Technology
This article is contributed. See the original author and article here.

We are excited to see the continuous growth on the submissions of the SharePoint Framework solutions to the app source and on the usage of the SharePoint store. Given the significant number of new solutions, we want to acknowledge the top 10 most widely used solutions on monthly bases and to provide quick update on the following roadmap items.
Here are the latest roadmap items around SharePoint Framework and store:
- SharePoint Framework 1.16 in autumn 2022 with updates for Microsoft Teams, Microsoft Viva and SharePoint
- Native support of Microsoft Teams JavaScript SDK v2 for SPFx solutions
- Viva Connections product type in AppSource for easier acquire of the Viva apps to your environment – no ETA
- Support for SharePoint Framework solutions in the Microsoft Teams store – no ETA
- Support SharePoint Framework extensibility for list and library new, edit and view panels
- and more…
We are looking forward to more great solutions that enable innovation, and help our customers get more done with Microsoft Viva, Microsoft Teams and SharePoint.
These are the most widely used solutions and their providers last month:
Ichicraft Widgets: Your Digital Workplace
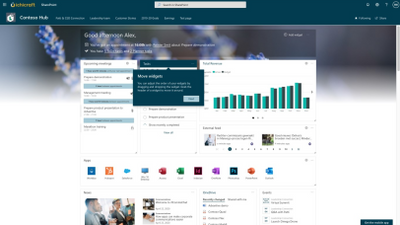
Ichicraft Widgets allows users to personalize their digital workplace in SharePoint or Microsoft Teams. It offers the user a canvas that can be filled with configurable widgets (blocks) that clearly display up-to-date and personalized information. This increases the productivity and involvement of employees in the organization.
Solution details:
Bitalus-StockQuotes
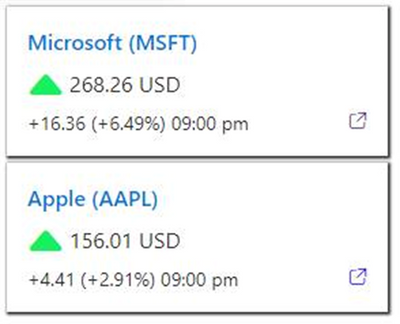
Show Stock information on your SharePoint Homepage with a couple of clicks. The Stock Quotes Web Part displays the configured stock information with display options. The integrated Field Template offers great flexibility to define your own look and feel. For static monitors, the integrated “Autorefresh” function offers the ability to configure an update interval in minutes. This way, the stock information will stay up to date without any page refresh.
Solution details:
Navigator 365 – Sharepointalist, Inc.
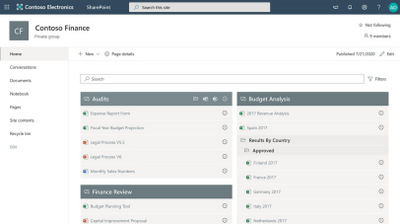
SharePoint & Teams content aggregation with search, grouping and filtering. Navigator 365 for Teams & SharePoint displays aggregated content with rich search, grouping, filtering, and layout capabilities. This versatile app works as a SharePoint web part, Microsoft Teams tab and Microsoft Teams personal app.
Solution details:
Cerkl Broadcast for SharePoint
Ensure your internal communications are seen with SharePoint push alerts and newsfeed. Cerkl Broadcast for SharePoint provides unique notifications to employees through your existing SharePoint. Cerkl Broadcast for SharePoint simplifies your labyrinth of essential content into an easily navigable widget. Cross-channel performance metrics and customizable dashboards are included.
Solution details:
Employee Directory Plus – Support | HR365
SharePoint Employee Directory Plus is free, fully featured 30 days trial for one office 365 tenant upto 999 users. Employee Directory Plus displays information of employees in the organization in visually manner and allows you to find any user in fraction of seconds with various filters to select, departments, skills, Job title, manager, location, etc. It helps in retrieving important information on the fly. Now it comes multiple options to exclude users, enhanced performance and new fields i.e. date of joining, date of birth, etc.
Solution details:
HM Munich GmbH – Table of Contents
Dieses WebPart hilft Ihnen qualitativ hochwertige Dokumentationen zu erstellen. Die Modern Pages sind ideal für Ihre Dokumentation von Inhalten (als eine Art Wikipedia) im Office 365. Ohne ein Inhaltsverzeichnis ist der Überblick schnell verloren.
Solution details:
Modern FAQ
The Modern FAQ app provides users a better way to search for the answers to the questions they have in mind. It also helps the organizations to prepare the frequently asked questions, and answers categorized and presented to the users in a readable and most understandable format.
With a clean, user-friendly interface, users or employees can find the relevant information at the right time. The grouping of questions and answers will help the users to find the answers more effectively.
Solution details:
Image Map – APPS 365 LTD
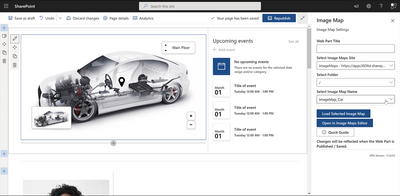
Supercharge your processes and navigation by using any image to deliver interactive visual content. Create hotspot navigation with image maps. Create eye catching and interactive images with clickable regions to supercharge navigation with the Image Maps Web Part. Offer a more intuitive interface and add life to your site.
Description
Solution details:
Qualtrics Feedback
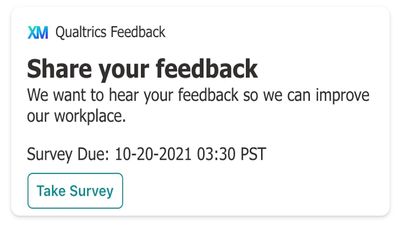
Add a way for your employees to easily give you feedback from within Viva Connections. Easily add a card to your Viva Connections surface to allow your employees to give you feedback in their flow of work. This card will link to your survey and let your employees know when feedback is due.
This Add-in requires a Qualtrics Employee Experience License.
What is Qualtrics Employee Experience?
The Qualtrics Employee Experience suite allows you to:
- Fix problems before they become part of your culture through predictive analytics.
- Go beyond measurement. Drive immediate change through automated actions.
- Transform experiences across the entire employee lifecycle.
Solution details:
My Links – Dalikoo
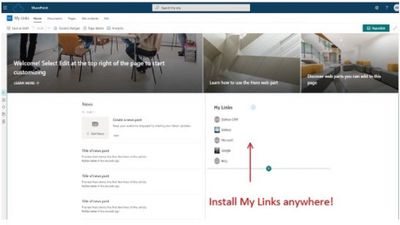
My Links is a SharePoint app where you can add and manage your web links through an intuitive interface. The links can point to locations across your Microsoft 365 environment as well as any web site on the Internet.
After installing My Links in a SharePoint page and adding your links, you can also install the My Links web part in another location and your original links will be available to you at the new location. My Links can be installed in multiple SharePoint locations, always providing you quick access to your original links list. Furthermore, you can update your links using the same intuitive interface from any location where the app is installed.
Solution details:
Resources
Please see following resources around getting started on building extensibility for Microsoft Teams, Microsoft Viva and SharePoint using SharePoint Framework.
Happy coding! ?

by Contributed | Aug 11, 2022 | Dynamics 365, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Effective October 1, 2022, you will no longer be able to use Basic authentication to connect to Microsoft Exchange Online. If your organization uses server-side synchronization or the deprecated Dynamics 365 Email Router, you should find out now whether you need to prepare for the change.
How will removing Exchange Online Basic authentication affect Dynamics 365 and Power Apps?
After October 1, 2022, any connection to Exchange Online that uses server-side sync or the Dynamics 365 Email Router with Basic authentication (username and password) will quit working. Dynamics 365 mailboxes that use these connections will no longer be able to:
- Send email from Dynamics 365 through Exchange Online
- Retrieve email from Exchange Online
- Synchronize appointments, contacts, or tasks between Dynamics 365 and Exchange Online
This change doesn’t affect connections that use Modern authentication (OAuth 2.0 token-based authorization).
How can I find out if I need to prepare?
If your company is using server-side sync or the Email Router to connect to Exchange Online using a username and password, you need to act. There are a couple of ways to find out whether your organization is affected and what you need to do if it is.
Review your Message Center Posts (recommended)
The fastest and most reliable way to know if you need to prepare and what to do is to look in the Microsoft 365 Message Center. (You must have admin rights to sign in to the Message Center.) The Exchange Online team has been sending monthly Message Center posts to all affected customers with the following title format: “Basic Authentication – Monthly Usage Report – <Month> 2022.”
If your organization is using server-side sync with Basic authentication, you may also have received Message Center posts from the Dynamics 365 or Power Apps services. Look for posts with the following title: “Impact due to Exchange Online disabling Basic Authentication.”
The posts provide detailed information about the change and actions you need to take before October 1.
Check your Dynamics 365 email settings
If you don’t find any posts in the Message Center, read our guide on how to check whether your organization is affected and if it is, what you need to do before October 1.
Learn more
You can find more information, including FAQs, in the documentation:
Use of Basic authentication with Exchange Online | Microsoft Docs
The post Exchange Online Basic authentication is going away: What you need to know appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Aug 11, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise. Note: to view the newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column, which will sort by descending dates.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the specified criteria.
by Scott Muniz | Aug 11, 2022 | Security, Technology
This article is contributed. See the original author and article here.
|
5841ef35aaff08bb03d25e5afe3856a2
|
ffd228b0d7afe7cab4e9734f7093e7ba01c5a06e
|
1e3c5a0aa079f8dfcc49cdca82891ab78d016a919d9810120b79c5deb332f388
|
|
d6c4b253ab1d169cf312fec12cc9a28f
|
0f47c279fea1423c7a0e7bc967d9ff3fae7a0de8
|
347f14497df4df73bc414f4e852c5490b12db991a4b3811712bac7476a3f1bc9
|
|
fba7180ad49d6a7f3c60c890e2784704
|
f561f9e3c949fe87f12dbfa166ffb2eb85712419
|
7d8c4c742689c097ac861fcbf7734709fd7dcab1f7ef2ceffb4b0b7dec109f55
|
|
bc6c991941d9afbd522fa0a2a248a97a
|
a243ce234fc8294e2e2e526418b4eaadc2d6c84f
|
37c320983ae4c1fd0897736a53e5b0481edb1d1d91b366f047aa024b0fc0a86e
|
|
f3490951ae51922cb360a3d76a670159
|
e2cb60be111716e32db7ca2365ad6e73c30f0e21
|
894b03ed203cfa712a28ec472efec0ca9a55d6058115970fe7d1697a3ddb0072
|
|
e4f1f05c2e6c3fc2f3336a8c8799ffb4
|
dbd9fcf2b05e703d34181c46f4c22392b9fcc1da
|
307877881957a297e41d75c84e9a965f1cd07ac9d026314dcaff55c4da23d03e
|
|
aa2048271f0aef3383480ce4a7c93b52
|
512b16ea74027fa4d0055831de5e51278812c8de
|
bafd3434f3ba5bb9685e239762281d4c7504de7e0cfd9d6394e4a85b4882ff5d
|
|
f66b738e1bfe1f8aab510abed850c424
|
571f50fee0acad1da39fe06c75116461800cc719
|
faa79c796c27b11c4f007023e50509662eac4bca99a71b26a9122c260abfb3c6
|
|
bb30f050546f5d6e61fafc59eaf097c3
|
ee44179f64918f72a8d2e88a5074d89efab3d81b
|
e48cf17caffc40815efb907e522475722f059990afc19ac516592231a783e878
|
|
78621f1e196497d440afb57f4609fcf9
|
eed7c3bb3fc5181b88abeed2204997f350324022
|
4a4be110d587421ad50d2b1a38b108fa05f314631066a2e96a1c85cc05814080
|
|
f4e0ee0200de397691748a2cdcd7e34a
|
bd3f6b878284a63c72e8354e877e3f48d6fca53c
|
9ef90ec912543cc24e18e73299296f14cb2c931a5d633d4c097efa372ae59846
|
|
cf5a358a22326f09fd55983bb812b7d8
|
1addcffae4fd4211ea24202783c2ffad6771aa34
|
dd89d939c941a53d6188232288a3bd73ba9baf0b4ca6bf6ccca697d9ee42533f
|
|
7afe492a38ca6f27e24028aab68406b5
|
5870a3adbce9737319f3c9461586d5f2afbc7adb
|
79d6e498e7789aaccd8caa610e8c15836267c6a668c322111708cf80bc38286c
|
|
1da1c0115caca5ebf064380eb7490041
|
5edb8b651c7013ebaba2eb81c87df76a1e0724d6
|
b22b3625bcce7b010c0ee621434878c5f8d7691c2a101ae248dd221a70668ac0
|
|
8c3c663ffcf363d087f4e114a79945ca
|
905726d178962dd1d7fe87504d051aca440740b8
|
961fbc7641f04f9fed8391c387f01d64435dda6af1164be58c4cb808b08cc910
|
|
17c5cae3bce5832dd42986fe612517d9
|
6f70e73c53d7622d8c4808ae7849133df1343484
|
d618c1ccd24d29e911cd3e899a4df2625155297e80f4c5c1354bc2e79f70768c
|
|
bfe7f54f1f0640936dd7a3384608b1f6
|
9436ccee41c01ca3cb4db55c10884615aba76d19
|
8170612574f914eec9e66902767b834432a75b1d6ae510f77546af2a291a48a2
|
|
f28af04ef0370addfebfdd31f1ec25ed
|
cfcfa995c15d9f33de21d0dd88d3b95d0f91d6bc
|
5326f52bd9a7a52759fe2fde3407dc28e8c2caa33abf1c09c47b192a1c004c12
|
|
f3bcad5358f89df1eb0294ef53f54437
|
eb036759beb28f86ee981bdca4fad24152b82d8c
|
6bafc7e2c7edc2167db187f50106e57b49d4a0e1b9269f1d8a40f824f2ccb42b
|
|
b1f6370582fbaf5c51e826fecef53cd7
|
4b2d0127699f708a8116bff8f25c9d6140033197
|
f7af51f1b2b98b482885b702508bd65d310108a506e6d8cef3986e69f972c67d
|
|
de785ed922d4e737dc0fa0bb30a4de8b
|
4d280105e724db851f03de8fc76409ef4057ff2c
|
bc214c74bdf6f6781f0de994750ba3c50c0e10d9db3483183bd47f5cef154509
|
|
7a296f7c1ac4aeee18d4c23476735be7
|
c13542310f7a4e50a78247fc7334096ca09c5d7f
|
ed1548744db512a5502474116828f75737aec8bb11133d5e4ad44be16aa3666b
|
|
37f18b38e1af6533d93bbb3f2ddb86dc
|
d3929331d9bc278dea5607aec1574012a08de861
|
cf9b6dda84cbf2dbfc6edd7a740f50bddc128842565c590d8126e5d93c024ff2
|
|
291de974e5cbe5e3d47e3d17487e027f
|
def93f18aaf146fe8f3c4f9a257364f181197608
|
21807d9fcaa91a0945e80d92778760e7856268883d36139a1ad29ab91f9d983d
|
|
99d59c862a082b207a868e409ce2d97c
|
908a9026d61717b5fa29959478a9bd939da9206f
|
0d22d3d637930e7c26a0f16513ec438243a8a01ea9c9d856acbcda61fcb7b499
|
|
d27125d534e398f1873b7f4835a79f09
|
1862f063c30cd02cfea6070d3dba41ac5eee2a35
|
6fbfc8319ed7996761b613c18c8cb6b92a1eaed1555dae6c6b8e2594ac5fa2b9
|
|
4534f2afe5f7df1d998f37ad4e35afeb
|
e2cc94e471509f9fa58620b8bb56d77f2cfe74b0
|
e8596675fef4ad8378e4220c22f4358fdb4a20531b59d7df5382c421867520a9
|
|
7ab0676262c681b8ec15bdada17d7476
|
2f1803d444891abb604864d476a8feac0d614f77
|
353e59e96cbf6ea6c16d06da5579d3815aaaeeefacabd7b35ba31f7b17207c5b
|
|
d7d3d23a5e796be844af443bda5cd67e
|
a9771c591f6ccc2f3419d571c64ab93228785771
|
85f9bf4d07bc2ac1891e367f077dd513d6ca07705bffd1b648d32a7b2dc396f5
|
|
0a1cd4efda7543cec406a6822418daf6
|
af4f8d889d6a2049e7a379ea197f8cd361feb074
|
614cb70659ef5bb2f641f09785adc4ab5873e0564a5303252d3c141a899253b2
|
|
23eda650479fc4908d0ddff713508025
|
b1e6527c10f68586f7f1a279ed439d46c3f12a06
|
fb3e0f1e6f53ffe680d66d2143f06eb6363897d374dc5dc63eb2f28188b8ad83
|
|
6607d8c1a28d7538e2a6565cf40d1260
|
f618879c011cde344066072949f025827feea663
|
594df9c402abfdc3c838d871c3395ac047f256b2ac2fd6ff66b371252978348d
|
|
caa7a669da39ffd8a3a4f3419018b363
|
44538b7f8f065e3cef0049089a8522a76a7fccc6
|
2dffe3ba5c70af51ddf0ff5a322eba0746f3bf3ae0751beb3dc0059ed3faaf3d
|
|
48b844494a746ca96c7b96d6bd90f45f
|
7bf83b98f798f3a8f4ce85b6d29554a435e516e3
|
45fba1ef399f41227ae4d14228253237b5eb464f56cab92c91a6a964dc790622
|
|
9c13ab7b79aec8dc02869999773cd4b2
|
4b4d865132329e0dd1d129e85fc4fa9ad0c1d206
|
774ef04333c3fb2a6a4407654e28c2900c62bd202ad6e5909336eb9bc180d279
|
|
450e5bf4b42691924d09267ac1a570cb
|
665a563157f4aa0033a15c88f55ac4fa28397b49
|
677035259ba8342f1a624fd09168c42017bdca9ebc0b39bf6c37852899331460
|
|
51104215a618a5f56ad9c884d6832f79
|
801580a46f9759ceeeebbce419d879e2ed6943fe
|
26ec12b63c0e4e60d839aea592c4b5dcff853589b53626e1dbf8c656f4ee6c64
|
|
73627cbe2ba139e2ec26889a4e8d6284
|
1116dc35993fce8118e1e5421000a70b6777433f
|
37efe10b04090995e2f3d9f932c3653b27a65fc76811fa583934a725d41a6b08
|
|
935f54b6609c5339001579e96dc34244
|
a809327d39fab61bfcfac0c97b1d4b3bfb9a2cfe
|
a5847867730e7849117c31cdae8bb0a25004635d49f366fbfaebce034d865d7d
|
|
ba681db97f283c2e784d9bb4969b1f5a
|
5d28acf52f399793e82ec7e79da47d372d9175d7
|
e61edbddf9aed8a52e9be1165a0440f1b6e9943ae634148df0d0517a0cf2db13
|
|
c1ab7b68262b5ab31c45327e7138fd25
|
b8c74327831e460d2b2a8eb7e68ee68938779d8d
|
746f0c02c832b079aec221c04d2a4eb790287f6d10d39b95595a7df4086f457f
|
|
f818938b987236cdd41195796b4c1fb5
|
bfed40f050175935277c802cbbbce132f44c06ec
|
b191a004b6d8a706aba82a2d1052bcb7bed0c286a0a6e4e0c4723f073af52e7c
|
|
0a1cd4efda7543cec406a6822418daf6
|
af4f8d889d6a2049e7a379ea197f8cd361feb074
|
614cb70659ef5bb2f641f09785adc4ab5873e0564a5303252d3c141a899253b2
|
|
d7d3d23a5e796be844af443bda5cd67e
|
a9771c591f6ccc2f3419d571c64ab93228785771
|
85f9bf4d07bc2ac1891e367f077dd513d6ca07705bffd1b648d32a7b2dc396f5
|
|
7ab0676262c681b8ec15bdada17d7476
|
2f1803d444891abb604864d476a8feac0d614f77
|
353e59e96cbf6ea6c16d06da5579d3815aaaeeefacabd7b35ba31f7b17207c5b
|
|
4534f2afe5f7df1d998f37ad4e35afeb
|
e2cc94e471509f9fa58620b8bb56d77f2cfe74b0
|
e8596675fef4ad8378e4220c22f4358fdb4a20531b59d7df5382c421867520a9
|
|
d27125d534e398f1873b7f4835a79f09
|
1862f063c30cd02cfea6070d3dba41ac5eee2a35
|
6fbfc8319ed7996761b613c18c8cb6b92a1eaed1555dae6c6b8e2594ac5fa2b9
|
|
99d59c862a082b207a868e409ce2d97c
|
908a9026d61717b5fa29959478a9bd939da9206f
|
0d22d3d637930e7c26a0f16513ec438243a8a01ea9c9d856acbcda61fcb7b499
|




Recent Comments