
by Contributed | Sep 29, 2022 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
From how we’re helping every employee thrive with Microsoft Viva, to new Microsoft Teams Rooms offerings for hybrid meetings, to new security and management capabilities in Windows 11—read on to learn what’s new in Microsoft 365 this month.
The post From helping people thrive with Viva to creating hybrid Teams Rooms experiences—here’s what’s new in Microsoft 365 appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Sep 29, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Sep 28, 2022 | Technology
This article is contributed. See the original author and article here.
Connecting the Education Community
The Education community thrives on the never-ending quest for information, and the ability to share that information with others. It strengthens us, enlightens us, and can be harnessed and used for positive change in each of our lives. In today’s world, we have so many options on HOW we educate ourselves, and HOW we share that information with others. And in this digital age, the access to information and knowledge is abundant, but oftentimes can be overwhelming.
The technologies that help us enable our education are also changing, and they have become increasingly important in keeping us connected with those we teach and those who teach us. In fact, the importance that technology has in creating new ways to make information more accessible, more inclusive, and more comprehensive is at the core of what drives this tech community. As technology evolves, it’s our collective goal to ensure it changes for the better.
The End of an Era
This past month saw the industry exit of one of true pioneers in the education industry, Edmodo. For almost 15 years, Edmodo has helped strengthen the education community by creating tools that have enabled teachers to share content, distribute assignments, and manage communication with students, colleagues, and parents worldwide. And while we’d like to say a tremendous “Thank You” to the Edmodo team, we also wanted to reach out to the community to help fill the void that the loss of some of these tools may have on your classrooms.
How Teams Can Help
While technologies in this industry change, the connected classroom is still an essential part of our educational environment, and the tools and support teachers and students can utilize are important to our overall success. The entire team at Microsoft Education is dedicated to the continued support of the education community and offers a host of solutions that can help get the most out of in-person and hybrid learning environments.
For example, Microsoft Teams for Education is part of a product suite designed to empower every learner and bring everyone and everything together in one powerful communication application. It’s built with tools and features to support the evolving needs of students and teachers in both small classrooms and larger educational institutions. Microsoft Teams for Education has both free and paid subscription plans that can fit the needs of any school and provides the necessary tools and support to help you get started right away.
By combining a classroom’s communication and productivity tools in one place, Microsoft Teams enables you to:
- Collaborate seamlessly by making it easy for educators to set up virtual classrooms, keep assignments and grades organized, and collaborate on any number of files in real time.
- Connect virtually to make remote and hybrid learning fun and engaging. Chat, video, file sharing, and other features help students and educators connect and communicate more naturally.
- Communicate securely with the ability to reach out to students, staff, parents, and guardians in a safe and secure environment, including supervised chats for students.
In addition to providing collaboration, connection and communication tools, Teams can also greatly enhance the learning experience by:
- Encouraging independent learning by providing access to personalized tools that allow students to practice and learn on their own, with the help from our AI-assisted digital learning coaches and built-in progress trackers.
- Developing social skills by supporting students’ emotional and social well-being and providing a safe space to navigate feelings with age-appropriate activities that promote Social-Emotional Learning (SEL).
- Enhancing hybrid education by bridging the gap between in-person and remote educational environments with easy-to-use tools that make blended learning more convenient and efficient for everyone.
We understand that the school year has already begun, and that the amazing tools Edmodo brought to your classroom are going to be missed. We hope Teams can help fill some of these gaps and provide you the solutions you need in the fastest and most efficient manner. From all of us at Microsoft, to the entire education community, best of luck with the new school year, and let’s make this the best one ever, together.
Mike Tholfsen
Group Product Manager
Microsoft Education
by Scott Muniz | Sep 28, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Sep 27, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released three (3) Industrial Control Systems (ICS) advisories on September 27th, 2022. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations:
• ICSA-22-270-01 Hitachi Energy AFS
• ICSA-22-270-02 Hitachi Energy APM Edge
• ICSA-22-270-03 Rockwell Automation ThinManager ThinServer
by Contributed | Sep 27, 2022 | Technology
This article is contributed. See the original author and article here.
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Common business processes integrated into Microsoft Teams can range from Information Technology (IT) Service Management (ITSM), Content Approval Workflows, to Human Resources requests. Just know that your commonly used business processes and non-Microsoft software services are now surfacing inside of Microsoft Teams!
The common scenario we’ve heard from our customers is: “There are some daily-used non-Microsoft applications that we would like to incorporate into Microsoft Teams. Is it accredited to use in our O365 government cloud? Where should I check?”
With current trends, we wanted to provide a reference on where to look when you are planning for integration within Teams.
Option 1: 3P Applications in Teams for Government
Step 1: Check the Teams App Store
One of the first places most customers check is the Teams App Store for available apps suitable for their business needs. Searching the app store using keywords such as, ‘GCC’ or ‘government,’ you can find applications specifically built for the government industry. Applications in the Teams App Store have gone through the rigorous Microsoft Teams store validation process for compliance and testing.
*Please note: GCC High and DoD tenants do not have a public Teams App Store but are able to side load apps into their Tenant specific app store.
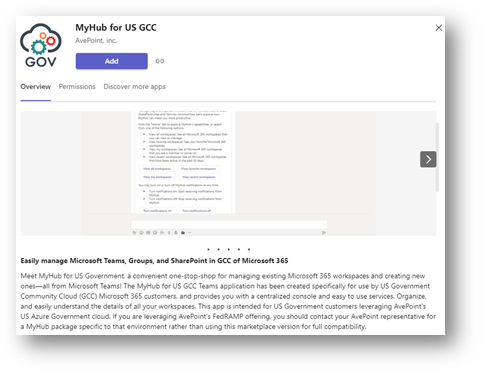
Each app has a store tile which provides an app description, included capabilities and features, plus the permissions the app requires for use.

Image above depicts MyHub for GCC and the description of the MyHub product.
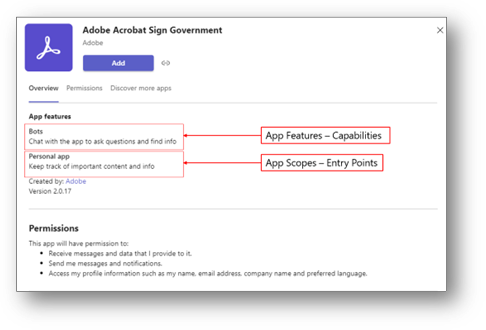
Image above depicts Adobe Sign for Government and the Adobe Sign app features.
Step 2: Check Security & Compliance for the Teams App
While the information from the Teams App Store might be enough for some organizations, there may be further investigation required on how the application handles data and up to security/compliance.
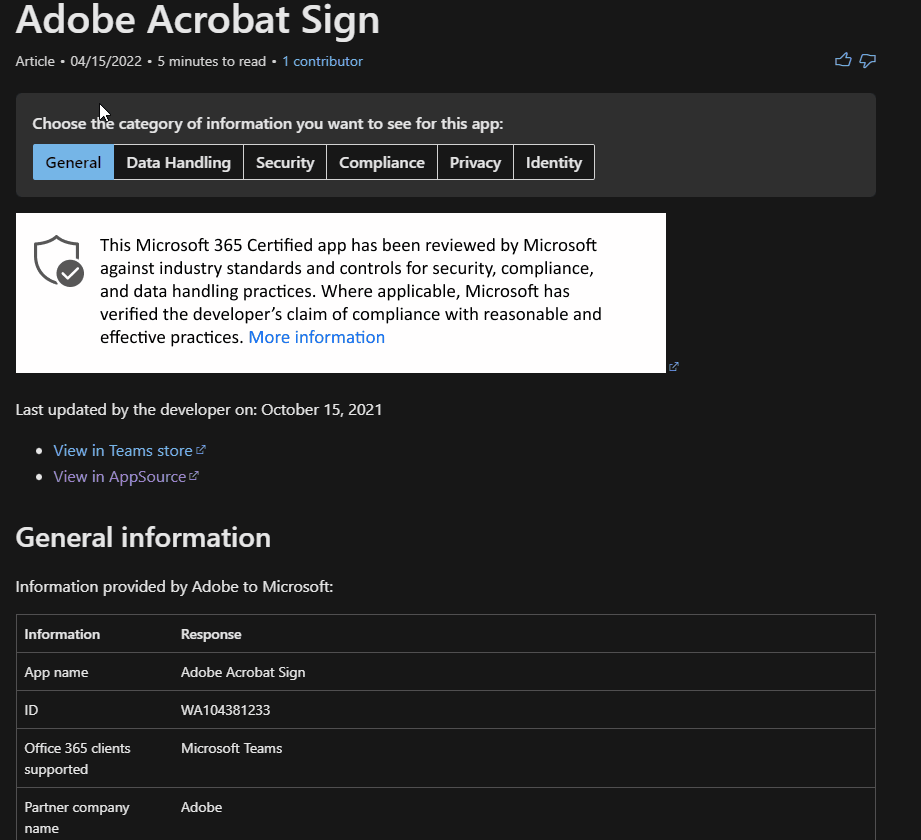
The Microsoft Teams Apps Security and Compliance Docs page provides customers key information to assess and manage risk for the Microsoft Teams 3P app under consideration. By clicking on each topic in the screenshot below, it will display the related information. Below is an example showcasing the information for Adobe Acrobat Sign.
Compliance
While all sections are important, one of the most common tabs frequently visited by government agencies is the Compliance tab where one can check if a 3P app is FedRAMP-compliant. Link to an example of a FedRAMP-compliant Teams app.
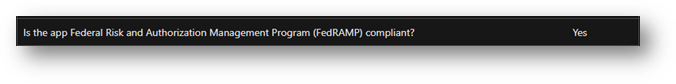
Image referencing FedRAMP compliance above.
Identity
Another common tab is the Identity tab which provides information around Graph permissions.
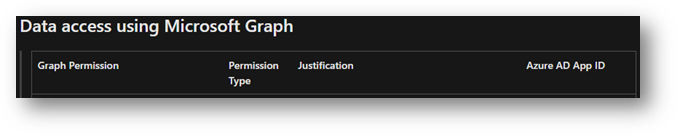
Image showing the privileges under Identity tab above.
Step 3: Validating Product Compliance on the FedRAMP website
The Federal Risk and Authorization Management Program (FedRAMP), is a standardized approach to security assessment for cloud service offerings with the intent to deploy to Federal agencies. FedRAMP makes it possible for agencies and cloud service providers to reuse authorizations.
*Please Note: Microsoft does not own or manage the FedRAMP site or program. FedRAMP is United States federal government-wide program (owned by GSA) that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services*
Using the FedRAMP Marketplace, you can look up approved products/providers for your own and other agencies.

Image depicting sorting/filtering options in FedRAMP marketplace above.
Using the FedRAMP site:
The left column in the Marketplace provides a search function to query based on your needs. For the Products tab, search based on the product name or company. For the Agencies tab, search by organization name.
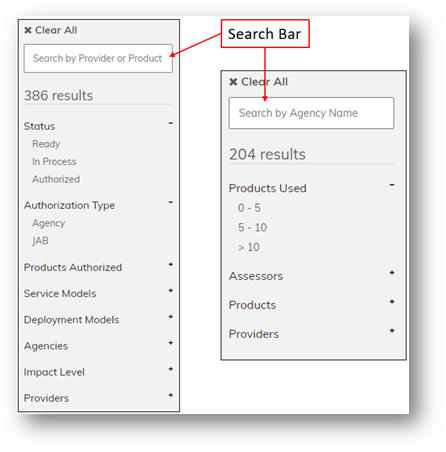
Image depicting filter and search bar above.
When filtering by product, key areas to consider are marked on the image below, which include, Impact Level, Current Status, etc.
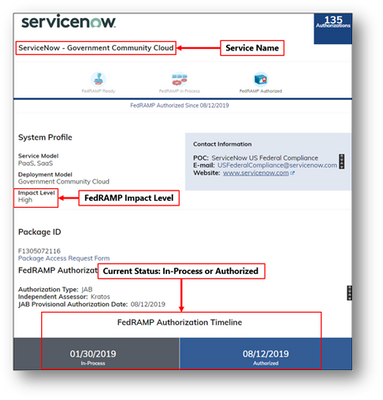
Image depicting FedRAMP key focal areas above using ServiceNow as an example.
Furthermore, other agencies using specific products will be listed under the FedRAMP site, as well. This provides a Agency-to-Agency reference when looking for deployment guidance and lessons learned. The Agencies using this product will be located at the bottom of the Product offering page. Example of FedRAMP product page.

Image depicting other Agencies using a specific product above.
To filter by Product, use the Product Marketplace link. To filter by Agency, use the Agencies Marketplace link.
Option 2: Line of Business (LOB)/Homegrown Teams Apps
Microsoft Teams allows developers within your organization to build, test, and deploy custom apps for organization’s internal users. Such apps are called custom apps or Line of Business (LOB) apps. Your organization may commission the creation of custom apps for org-specific requirements. For more information, click here.
Customers in GCC High and DoD do not have access to the Teams public app store and will therefore need to get app packages directly from software vendors. For example, ServiceNow is able to provide a Teams app package that points to their FedRAMP accredited environments. In this type of scenario, customers wonder how they can validate this app package for security risks/requirements. Most of the app packages that customers are receiving from vendors point to FedRAMP accredited services and endpoints, just like the above ServiceNow example. If your agency has an existing Authority To Operate (ATO) with the vendor, sideloading that app into Teams may fall under the same ATO umbrella and may not need a separate review. Note, apps in Teams are simply connecting to an existing service endpoint that may already have been approved for use on your network.
If your organization would like to build your own custom app, learn more by visiting our new Teams App Camp!
Summary
We covered looking at 3rd party applications from the Teams App Store, reviewing Microsoft Teams Apps Security and Compliance to assess and manage risk, and finally, reviewing the FedRAMP site for accreditation for Agency-to-Agency references.
For customers that use non-Microsoft services today and would like to see those integrations brought into Teams, please contact your Product Vendor to request the application and express the desired supported cloud, as well as, your Microsoft account team for awareness and options.
If your agency wants to build their own app Teams application and/or engage with Teams Engineering, please contact your Microsoft account team for coordination.
by Scott Muniz | Sep 26, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released three (3) Industrial Control Systems (ICS) advisories on September 27th, 2022. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations:
• ICSA-22-270-01 Hitachi Energy AFS
• ICSA-22-270-02 Hitachi Energy APM Edge
• ICSA-22-270-03 Rockwell Automation ThinManager ThinServer
by Contributed | Sep 26, 2022 | Technology
This article is contributed. See the original author and article here.
We’re not shy about using our own products and services internally here at Microsoft, and as such, we’re already taking advantage of recently moving our internal video platform—Microsoft Stream—under the Microsoft 365 umbrella.
The transformation of our corporate video platform has made it easier for our employees to create, upload, edit, and publish enterprise videos, says Marc Mroz, a product manager for Microsoft’s Office Media group, who explained that the new, modern Microsoft Stream experience is benefitting from now being located within SharePoint specifically.
“Many people were already familiar with what they can do in SharePoint,” says Mroz, who has been showing teams at Microsoft what they can now do with internal video. “We just helped connect the dots and showed them how to make a video destination, how to organize by folder, keyword, or metadata.”
The Microsoft Digital Employee Experience team has been working with Mroz and the product group team on deploying the modern Microsoft Stream experience across the company, with the team that publishes the company’s internal employee portal among those taking the lead on trying it first.
Using video to connect with employees in more meaningful ways has become more important as companies like Microsoft adjust to a new hybrid workstyle where employees aren’t working in the office as much as they used to, says Farnaz Hafezi, a program manager with Microsoft Digital Employee Experience.
“The last few years have really shown the importance of video for hybrid work,” Hafezi says. “It helps us collaborate, communicate, and educate. We’ve seen a significant increase in video within our tenant.”
Folding Microsoft Stream directly into Microsoft 365 and SharePoint using OneDrive for storage has made it more useable and accessible within Microsoft, Mroz says, adding that it also ensures that the product stays more current.
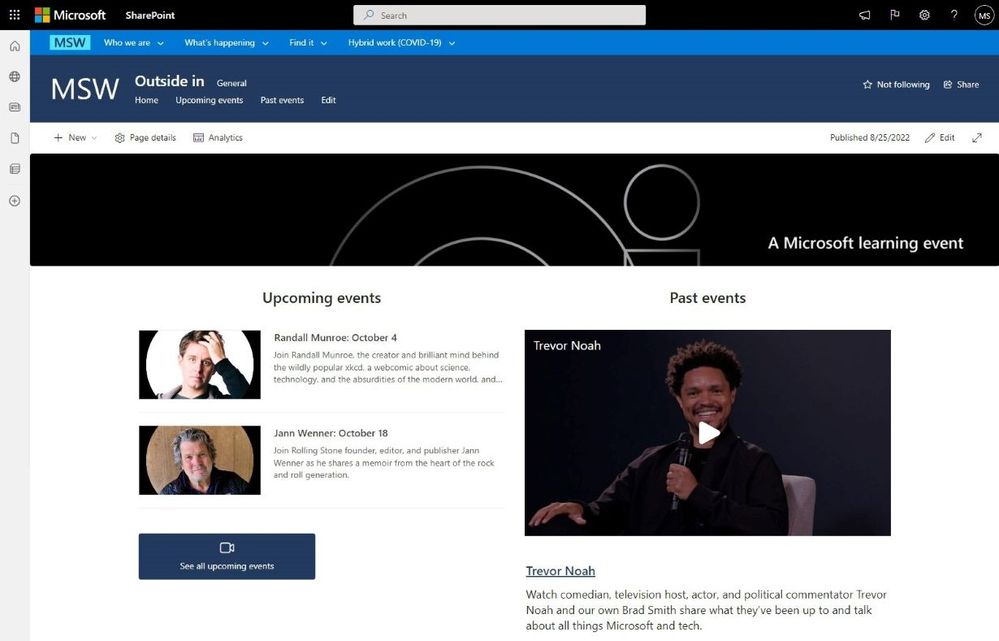
 An image providing a screen capture of Microsoft’s internal site, MSW, with an embedded video from Microsoft Stream.
An image providing a screen capture of Microsoft’s internal site, MSW, with an embedded video from Microsoft Stream.
Microsoft’s Customer Zero
The Microsoft Digital Employee Experience team plays a significant internal role here at Microsoft as Customer Zero. What does this mean? It’s about trying out the company’s new technology offerings first—in this case, that means deploying the new Microsoft Stream internally to early adopters before it is broadly deployed to customers, listening to feedback from our early users, and then feeding those insights back to the product group. This virtuous circle gives the product group important feedback that makes the product stronger before it gets to customers.
One of the early adopters was the team that runs MSW, the company’s internal employee portal.
“There are things we can do in modern Stream that were difficult to do in classic,” says David Potts, a site administrator for MSW. “Our team is a mix of employees and vendors at any given time, but the whole team needs to be able to do authoring and manage videos. Anything you can do in SharePoint, including guest permissions, is now available to us.”
The feedback from Potts and other early users of the product has made the modern Microsoft Stream experience stronger, Mroz says.
“It’ll look better and be more purpose fit than classic could ever do,” he says. “Now we have an out-of-the-box video platform built into SharePoint, and when we show it to customers, they get it.”
To learn more and to find out how you can deploy the modern Microsoft Stream experience at your company, read the full story here: Corporate video at Microsoft gets a big upgrade thanks to the modern Microsoft Stream experience. You can also check out this helpful guide for using Microsoft Stream at your company.
If you’re thinking about upgrading to the new Microsoft Stream experience, here a few things for you to consider:
- When moving from classic to the modern Microsoft Stream experience, take stock of your current inventory, especially if you have a large archive of Microsoft Teams recordings. Not every video is going to be worth the effort of bringing along.
- Thanks to the way SharePoint sites populate content, you can elegantly use parent and child sites to share content to targeted audiences without having to duplicate efforts
- Keep your SharePoint organized; this was true before Microsoft Stream came to Windows 365 and it’s still true after
- Video is a great way to onboard new employees or offer just-in-time training. Microsoft Stream’s compatibility with Microsoft Search makes it easy for connections to be made
Visit Microsoft Inside Track to learn more about how Microsoft uses its own technology and services as well as the company’s Customer Zero journey.
Continue the conversation by joining us in the Microsoft 365 community! Want to share best practices or join community events? Become a member by “Joining” the Microsoft 365 community. For tips & tricks or to stay up to date on the latest news and announcements directly from the product teams, make sure to “Follow” or subscribe to the Microsoft 365 Blog space!
by Scott Muniz | Sep 26, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Sep 23, 2022 | Technology
This article is contributed. See the original author and article here.
Improvements to the console
When performing a search on any node in the console, the hint text in the search bar will now indicate the scope of the search.
- By default, all subfolders are searched when you perform a search in any node that contains subfolders. You can narrow down the search by selecting the “Current Node” option from the search toolbar.
- If you want to expand the search to include all nodes, then select the “All Objects” button in the ribbon.
For more information, see Console changes and tips.
Improvements to the dark theme
Pop-ups in the Health attestation dashboard will now adhere to the dark theme.
Enable this pre-release feature to experience the dark theme. For more information, see Dark theme for the console.
Other updates
The software center logo dimension details are now added as a hint in the software center customization wizard.
- The image file can’t be larger than 2 MB size. The maximum dimension of the image should be 400 Pixels wide and 100 pixels tall.
For more information, see Software Center settings.
For more details and to view the full list of new features in this update, check out our Features in Configuration Manager technical preview version 2209 documentation.
Update 2209 for Technical Preview Branch is available in the Microsoft Endpoint Configuration Manager Technical Preview console. For new installations, the 2206 baseline version of Microsoft Endpoint Configuration Manager Technical Preview Branch is available on the link: MECM2206TP-Baseline or from Eval center
Technical Preview Branch releases give you an opportunity to try out new Configuration Manager features in a test environment before they are made generally available.
We would love to hear your thoughts about the latest Technical Preview! Send us feedback directly from the console.
Thanks,
The Configuration Manager team
Configuration Manager Resources:
Documentation for Configuration Manager Technical Previews
Try the Configuration Manager Technical Preview Branch
Documentation for Configuration Manager
Configuration Manager Forums
Configuration Manager Support



Recent Comments