
by Contributed | Oct 14, 2022 | Technology
This article is contributed. See the original author and article here.
This is a session recap from BRK33 – Create rich connections and customer experiences with Microsoft Teams Phone and contact center capabilities at Microsoft Ignite 2022.
Speakers:
Mahendra Sekaran, Vice President of Microsoft Teams Engineering
Pete Daderko, Director of Product Marketing, Microsoft Teams
Effective communication and collaboration are important in the new way of hybrid work, Microsoft Teams is an important part of that hybrid work and ensures that users in organizations can communicate whenever they want from wherever they want. Telephony in Microsoft Teams helps users in this modern way of working and Microsoft Teams Phone users have now passed 12 million PSTN Teams Phones users.
Mahendra mentions in the session that Microsoft Teams has been named Frost & Sullivan Company of the Year in the UCaaS industry. Microsoft Teams is also listed as a leader in the Gartner 2021 Unified Communication as a Service magic quadrant. This shows that Microsoft Teams with Teams Phone capabilities is a mature and market leading platform.
Teams Phone Mobile
Today’s workforce is more mobile than ever before. Employees need a full featured mobile experience that works across networks and devices. To help organizations with this, Microsoft is now releasing Teams Phone Mobile in General Available. Previously, this service was announced as Operator Connect Mobile. To start with, it will be available from Rogers in Canada and Telia in Sweden. More partners will release Teams Phone Mobile soon.

Users enabled with Teams Phone Mobile will get their mobile phone number assigned to their Teams user account, there is no need for an additional fixed number in Teams anymore. All incoming calls to their mobile phone number will ring on their signed-in Teams Devices and on their mobile phone, Teams mobile app or native dialer.
When you do an outbound call (or inbound) from your mobile native dialer to a colleague or external user in Teams, you will be able to uplift the call from your native dialer to your Teams mobile app and start sharing documents and video in Teams. When you uplift a PSTN call from your native dialer to Teams you will be able to use features in Teams—like recording, transcription, and easily transfer calls to users in your company directory. With Teams Phone Mobile, users will have the same voicemail for both Teams and mobile calls since you now only have one number.
Incoming calls will only ring on one native dialer, never both, as users might have experienced in earlier simultaneous ring scenarios. Users will be able to select if incoming calls should ring on Teams mobile app or on native dialer. This can also be controlled with a mobile policy from Teams Admin Center.
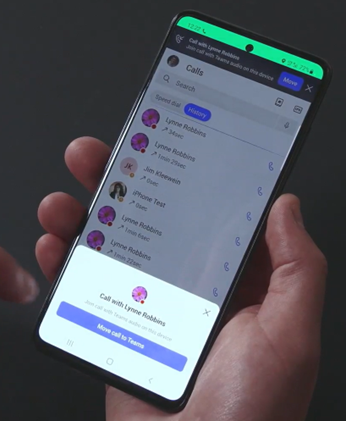 When starting your Teams app, you get the option to move an ongoing call from native dialer to Teams.
When starting your Teams app, you get the option to move an ongoing call from native dialer to Teams.
You can do an uplift of native PSTN calls in your mobile to any Teams device where you are signed in. If you receive a call from a Teams user when you are out walking, you can uplift your call to Teams on your computer when you arrive to your home or office to start using all features you have in Teams like sharing video, apps, and desktop.
With Teams Phone Mobile you will get all calls from native dialer and Teams, listed in the Teams history, so you can keep track of all outbound and inbound calls from one place – your Teams client.
Administration
Since Teams Phone Mobile is built on the same platform as Operator Connect, the administration is the same. All TPM numbers will be shown Teams Admin Center and administrators can assign them directly to users as they would do with an Operator Connect number or a Calling Plan number.
With Teams Phone Mobile, Operator Connect, and Microsoft Calling Plans, administrators will have the same way of assigning phone numbers and managing users from all carriers around the world. No different administration for different locations, all users can be managed the same way.
With Teams Phone Mobile, administrators will also get a new policy type called Mobility policy. With this, administrators can select if calls should arrive on Microsoft Teams mobile app or in the mobile phone native dialer. There is also an option for users to configure this themselves coming soon.
Mobile Control Point Azure for Operators
Mobile Control Points in Azure enables a deeper integration between Microsoft Teams and the operator network, so users can have a unique integrated experience in their mobile phone and Teams applications.
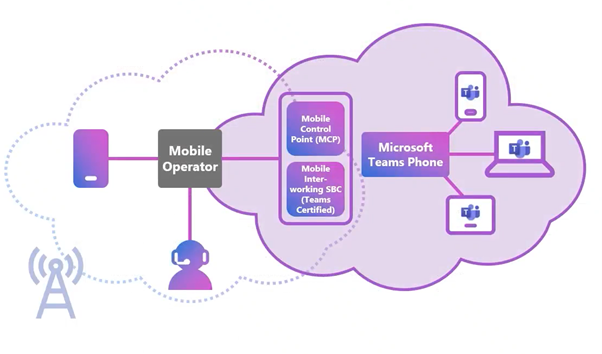
This integration enables Microsoft and operators to deliver a joint technical support model, quality of service for all calls, and a fully managed service. And this is only the start of this integration; we will see more upcoming features further on.
See below for interviews with some of the operators of what they have to say about this technology and what the integrations with Microsoft Teams means for their customers.
https://aka.ms/VerizonTeamsPhoneMobile
https://aka.ms/BTTeamsPhoneMobile
New Teams Phones Features
Since last Ignite, Microsoft released over 40 new features for Teams phone. Features like pay-as-you-go calling plans, 1:1 VoIP calls with end-to-end encryption, SIP Gateway and custom on-hold music. The list of new features is long, and it is getting longer with more features coming to Teams Phone.
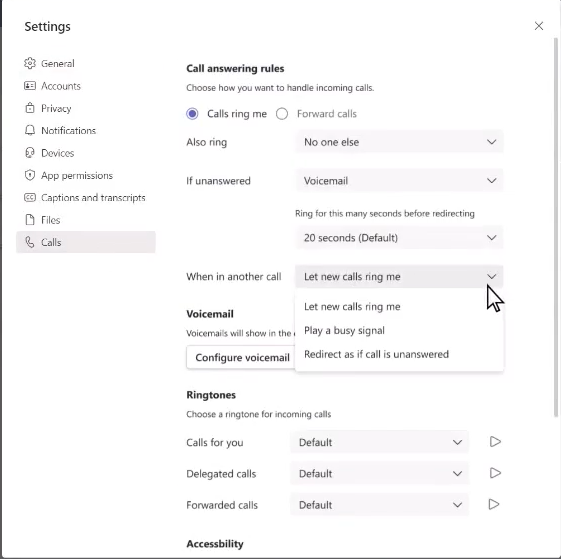
Busy on Busy
Teams users will be able to configure how calls should be handled when they are busy in another call.
“Let new calls ring med” – the default setting today.
“Play a busy signal” – the setting many users are familiar with from a traditional land line number.
“Redirect as if a call is unanswered” – as default the calls will be redirected to Voicemail, but this can also be changed to a coworker, call queue, or external phone number.
All settings can be handled by the end user themselves, so they get the settings that suites them and their way of working the best. New busy-on-busy will arrive early 2023 and settings will include users busy in a native dialer call on their Teams Phone Mobile enabled phone.
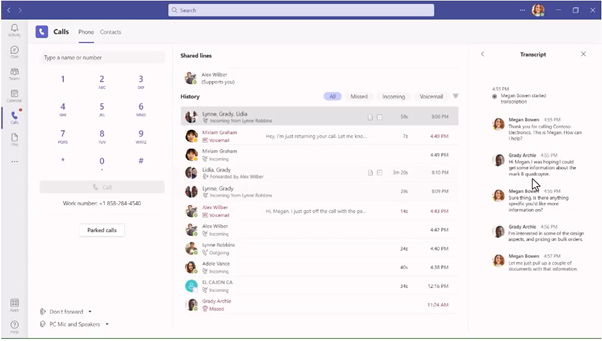
Rich Call History
With Rich call history, General Available now, you can glean more information about the call. In the call history, you see how calls arrived, how they were routed and forwarded, and how they were controlled once received. Teams Phones now include the ability to make recordings and transcriptions—for both PSTN and VoIP calls, and both recordings and transcriptions are available from the call history.
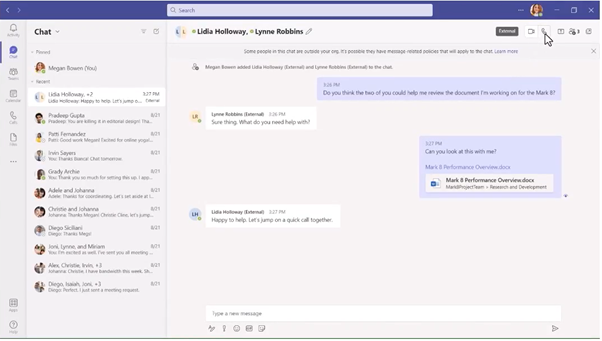
Federated Group Calling
From Teams groups chat, it has been possible to start audio and video calls with internal users. Now, Microsoft is announcing that it will be possible to do calls from federated group chats, too. A federated group chat is when you have a group chat with external participants. You will be able to call everyone in the group and add video and application sharing to the call.
Teams Phone Coverage and Reliability
Teams Phone is available via Direct Routing in over 180 countries, via Operator Connect in 62 countries and with Microsoft Teams Calling Plans in 33 countries. Later this year, Calling Plans will also be available in Mexico.
A recent report published by GigaOm rated Teams Phone highest in both call quality and reliability among tested competitors. The test included network service up-time, voice quality, and top features during benchmark. For more information:
https://aka.ms/TeamsPhoneReliability
Survivable Branch Appliance (SBA)
Survivable Branch Appliance (SBA) is a device that organizations can deploy to remote locations to enable Teams phone services even when internet connectivity is lost. In 2023, they will release new capabilities to SBA for Teams to allow better service for users in remote locations. First, you will be able to use chat and call history in addition to make outbound PSTN calls from Teams dial pad, even when you are in offline mode. Users will also be able to make VoIP calls to users in other locations. When in offline mode, calls will be routed via PSTN to the phone number associated with the user receiving the call.
Reference Case: SAP
Volker Rieger from SAP told us about their journey from 220+ traditional PBX-systems that they moved in 2013 to Lync telephony. During that journey, they upgraded to Skype for Business and now have moved to Teams Phone. With Teams Phone, they have a better tool for hybrid workers, Yet, even with a migration without any service interruptions for end users, there have been some challenges. While these challenges are not related to the new service, they still affect the end user experience such as bad home networks, uncertified headsets ,and that scaling of network had to change after introducing a cloud service.
Volker also mentioned there has been resistance from some users when they took their desk phones away, but they now realized how much better tool they got in Teams that integrates calling, chat, meetings, and collaboration in the same place.
SAP was able to cut over 15,000 users into Teams Phone in a single day. For organizations with doubts in moving to Teams Phone from their traditional PXB, Volker gave advice based on their experience of making it a priority to communicate and invite users to be a part of the journey.
Teams Phone with Contact Center
Microsoft receives many requests to move more of the investment customers into their platforms and to serve their customers in a better way using the tools they already have invested. Customers want quick answers, personalized offerings and services, and seamless interactions. That first contact with your customer sets the tone for the rest of the relationship. With Teams Phone, you can enable everyone in your organization to help service customers in the best way, and for many organizations this starts with Call Queues and Auto Attendants in Teams. Both have increased usage of over 200% in the last year.
To help customers track this usage, Microsoft will add reporting into Teams Admin Center, so you can follow the usage of Auto Attendants and Calls Queues as you can do with Call details records today.
Last year, Voice enabled channels (Collaborative calling) was introduced enabling users to receive calls for Call Queues in a Teams channel. With voice enabled channels, agents get calls to Call Queues into a Teams channels giving them a better overview of calls coming to Teams Call Queues.
Users of Teams Phone and Virtual Agents will be able to chat with a bot that can provide a phone number associated to a Call Queue.
This is only the beginning and Microsoft is developing enhanced customer experience with Dynamics 365, Nuance AI, Power Platform, Teams, and Azure. These integrations reduce average call handling time by 73% and enables 85% first call resolution. Agents can deliver a personalized experience on customers preferred channel with access to key information and keeping information in safe storage.

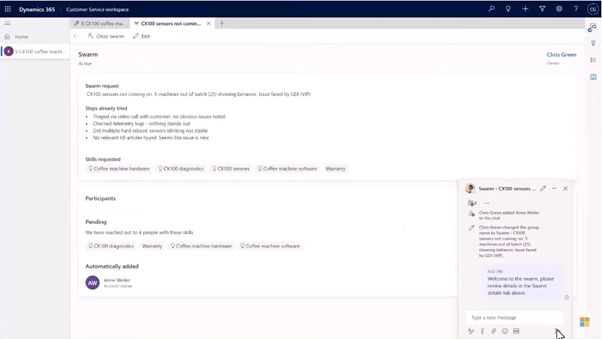
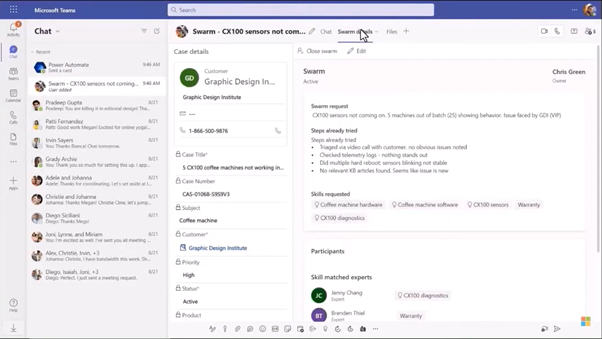
Agents needing assistance with a customer support case can enter keywords for skills needed to solve the customer issue. Agent in Dynamics creates a swarm to find experts that receive the swarm in Teams and can then accept it to help the customer agent. The Dynamics agent and the expert in Teams can both see the same information (in their respective application) on the customer case without changing application.
Now, this chat capability between Dynamics and Teams will be expanded with the capability to call between Dynamics and Teams with audio and video to solve customers issues in real time.
Third party Contact Center solutions
For customers that are using third party Customer Center solutions for Teams from Microsoft partners, Microsoft will continue to support these. Currently, there are 13 certified partners that provide Contact Center and Attendant solutions for Microsoft Teams.
With the recently announced Azure Communication Services SDK, there are more possibilities for partners to build solutions integrated with Teams. Developers can use the SDK to develop custom solutions that integrate audio, video, and telephony for Teams users. New enhanced Teams call flow management can be developed to place calls between external and internal users.
CRM Integration
General Available is a new CRM integration that allows administrators to configure Teams calling policies to open URLs leading to CRMs and other web applications when user receives an incoming call. When a user receives the incoming call, either directly or via Call Queue, a web browser will open with the predefined URL and the phone number of the caller. With the phone number added in the URL, the CRM or web application can look up the caller’s phone number to find the correct customer card and caller information in the Teams user’s web browser. Users can turn on or turn off the features from their Teams application.
Desk Phones and Devices
There are currently over 150 IP phones and peripherals certified for Teams, enabling organizations and users to get the best suited experience for them. For customers reliant on desk phones, recent updates to Teams phone app have made responsiveness of the client near instantaneous. Additionally, the UI has been updated showing frequently used features as Hold, Trans, and Mute in the main display of a call.

Common Area Phone license
Common Area Phone license that is used for shared devices have been updated with more experiences with the CAP license. Support for Hot Desking in Teams Displays and support for Panels have now been added in addition to recent updates as Call Queue capabilities, Group Pickup, Cloud Voicemail ,and Call Parking pickup and receive.
To reflect these updates, the license name will be renamed to Microsoft Teams Shared Device from December 2022.
Cisco Devices
Microsoft is partnering with Cisco to certify Cisco peripherals to Teams delivering a rich calling experience, this will start with the Cisco Desk Camera 4K and headset 320 with the headset 720 following early next year. But this is just the beginning to bring Cisco devices into the Teams environment.
SIP Gateway
Last December, Microsoft introduced the SIP Gateway that allows organizations to connect legacy devices to Teams and give them basic calling capabilities. Since then, additional calling capabilities have been added and support for DECT devices from Spectralink and Poly. Later this month, Ascom DECT devices will be supported by the SIP Gateway as well. SIP Gateway allows organizations to continue using legacy devices they invested in and enables a seamless move to a Teams Phone.
Early 2023 analog devices will be supported in SIP Gateway via certified ATA boxes from Cisco, AudioCodes, and Poly. With this capability, scenarios with gate phones and elevator emergency phones—that earlier required an on-premises PBX, can now be solved with SIP Gateways.
Teams Phone Admin Guide
It should not be hard to configure and setup Teams Phone. With the new Microsoft 365 Phone System setup guide, administrators will be able to configure Teams Phone with an easy step-by-step guide. You don’t need to be a voice expert to setup a Teams Phone; you only have to follow this setup guide and answer a few questions.
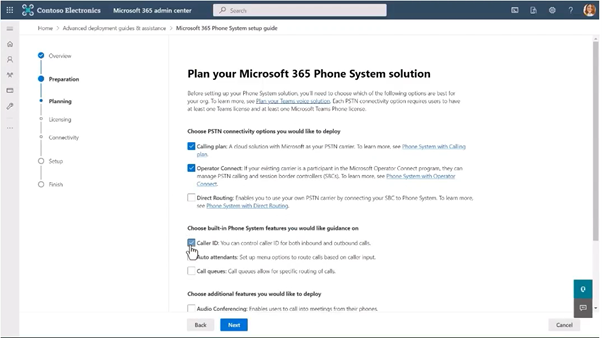
And with the Fast Track program, there is no additional setup cost for your organization using the Fast Track engineers or the Fast Track ready partners.
To find more resources use the following URLs.
FastTrack Assistance/End-to-End Expert Advice:
https://aka.ms/FastTrackForTeams
Resources to Support Adoption (links to zip files by user role):
https://aka.ms/TeamsPhoneAdoptionGuide
Get Started with Teams Phone YouTube playlist:
https://aka.ms/TeamsPhoneYouTube
Start a Trial:
https://aka.ms/TeamsPhoneTrial
Teams Phone Setup Guide (for users with access to M365 admin center):
https://aka.ms/TeamsPhoneSetUpGuide
_______________________
Linus Cansby, Microsoft MVP
@lcansby LinkedIn https://www.lync.se
by Contributed | Oct 13, 2022 | Technology
This article is contributed. See the original author and article here.
Azure autoscale automatically increase or decrease the number of VM instances for an Azure virtual machine scale set (VMSS) that run your application. This automated and elastic behavior reduces the management overhead to monitor and optimize the performance of your application. You create rules that define the acceptable performance for a positive customer experience. When those defined thresholds are met, autoscale rules take action to adjust the capacity of your scale set. You can also schedule events to automatically increase or decrease the capacity of your scale set at fixed times.
Now you can use machine learning to help manage and scale out your Virtual Machine Scale Sets with Predictive autoscale. The capacity needs of your Virtual Machine Scale Sets are forecasted based on the historical CPU patterns. When enabled, the predicted overall CPU load is observed and scale-out occurs in advance and in time to meet the demand.
Predictive autoscale complements loads that have cyclical workload patterns and are especially advantageous when Virtual Machines have long provisioning times. Having the scale out occur before the workload demand covers peak load while lowering the costs.
Predictive autoscale is available for Virtual Machine Scale Sets and support scale out only for Percentage CPU metrics only. Users will have to continue to create standard autoscale settings when creating scale ins for Virtual Machine Scale Sets.
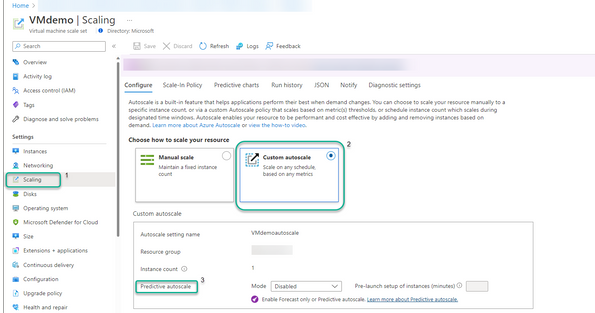
Predictive autoscale can be configured via Azure Portal, CLI and PowerShell.
To get started with predictive autoscale from Azure Portal navigate to their Virtual Machine Scale Set scaling blade and then to Predictive autoscale section

Using the Predictive Autoscale dropdown selection, you can:
- Enable forecast only mode
- Enable predictive autoscale
- Disable predictive autoscale. This is the default setting when you first land on the page for predictive autoscale.
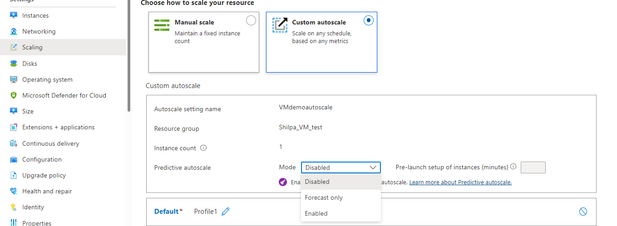
Once you’ve made your predictive autoscale selection (i.e. enable forecast only or predictive autoscale) and optionally configure how far in advance you want to scale out click on Save and then the process starts.
A new tab is now available in the scaling tab: Predictive Charts which provides you an in depth overview of the forecasted CPU as well as any autoscaling that occurs if predictive autoscale is enabled.
Please note that Predictive autoscale requires a minimum of 7 days of history to provide predictions. The most accurate results come from 15 days of historical data.
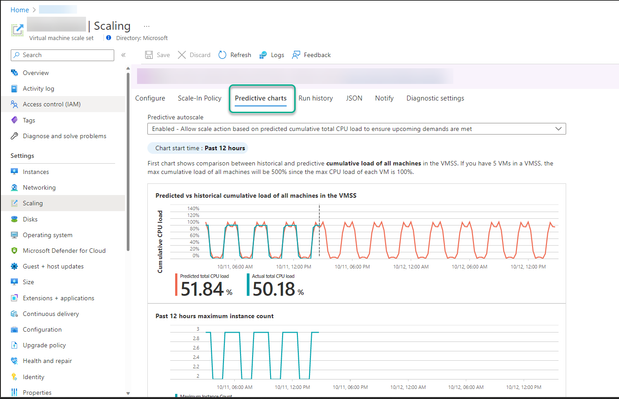
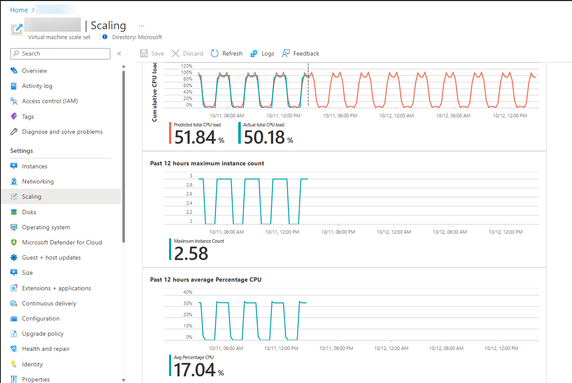
- The top chart shows an overlaid comparison of actual versus predicted total CPU percentage. The time span of the graph shown is from the last 24 hours to the next 24 hours.
- The middle chart shows the number of instances running at specific times over the last 24 hours.
- The bottom chart shows the current Average CPU utilization over the last 24 hours
In addition to this you have an option to enable/ disable forecast only or predictive autoscale as well as the ability to view the charts with time grain ranging from 12 hours to 7 days.
You can head over to Run History to review when scale outs occur due to predictive autoscale.
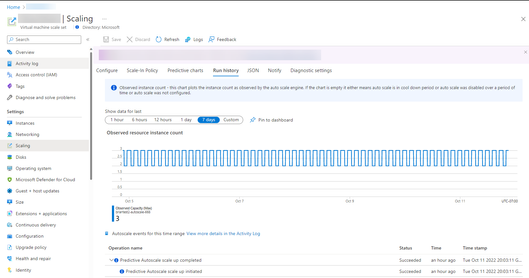
The forecast model observes the different capacity needs during the day and manages the overall load on an as needed basis. You will need to create a standard autoscale while creating predictive autoscale as it provides a fall back in case of say, missing forecast data. Predictive autoscale can work with other autoscale conditions, autoscale will always observe the request for highest number of resources to address any workload requirements.
Predictive autoscale is generally available in all public regions as of today, Oct 12, 2022. For more information you can refer to the documentation or email: predautoscalesupport@microsoft.com


Recent Comments