This article is contributed. See the original author and article here.
This blog is authored by Brian Delaney and Jon Shectman — with hearty thanks to our collaborator and pal Clive Watson.
In this article, we’ll share significant, functional enhancements we’ve made to the Insecure Protocols Workbook (IP Workbook) and we’ll detail how you can leverage these improvements to mitigate with speed, accuracy, and efficiency. If you’re new to the IP Workbook, we suggest starting with the implementation guide, which covers basic configuration steps, and sets you up for success in usage. Once you’ve completed the steps there, pop back over here to learn how to best use the recent enhancements and features.
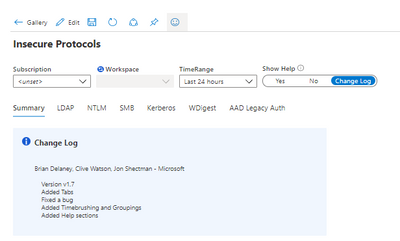
One of the first things you’ll notice in the new release is the new Show Help section in the top menu. By sliding the toggle, you can display Help for each protocol section. You can also display the Change Log.
By comparing your workbook version to the version in the Azure Sentinel Workbook Templates section, it’s easy to ensure you’re using the newest version. (At the time of this writing, Version 1.7 is the latest.)
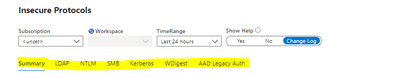
We have also reimagined the navigation experience by adding Tabs. Tabs mean you no longer need scroll down to the protocol data you want to research; gone are the days of a single linear page.
Clicking a tab hides all of the other protocol pages, making available only the protocol data that you wish to research at that given moment.
This way, there is no confusion about which protocol data you are viewing, and you can clearly display a mitigation success (e.g. a data void) when you have removed a particular protocol from your estate. Tabs should make for a visually simpler, more actionable data comprehension experience.
Next, let’s examine Timebrushing and Groupings. Groupings is a back-end feature that will be largely transparent to you. Groupings maximizes efficiency in the way that each set of queries runs, making them load faster and with more efficiency. You should see better performance, with fewer lags for data paging as your workbook sections populate.
Timebrushing is one of the most significant functional changes we have introduced with this update to the IP workbook. As its name implies, Timebrushing allows you to “paint” a particular slice of time in a graphical interface and to export that parameter to filter your subsequent queries.
The value here is that Timebrushing allows for very specific, precise data analysis. Put differently, it allows us to filter our data to zero in on a specific activity that might have happened during a specific time. By way of example, let’s examine how we might use Timebrushing and several other filters to research Insecure LDAP.
The Insecure LDAP tab features one of two starting points to parse our data: Account or IP addresses. In this example, we’ll start by filtering by Account. Let’s filter on the most active account, svc1:
This outputs the query parameter (e.g. display only accounts containing the value svc1) in the subsequent filters. Then let’s say I want to understand how svc1 was used during a time of heavy activity in the logs.
From the time graph, I can see that there’s a particularly heavy, sustained usage of svc1 to make insecure LDAP calls from about 3:50am through about 6:50am. Let’s Timebrush that slice and examine the data further:
And here a story emerges. Because of time binning (necessary to group the data into understandable chunks), we get a nice breakdown of the Insecure LDAP activity that can be sorted by BindingType, count or TimeGenerated (as I have done here). In other words, we see that during this time slice, svc1 made significant numbers of Insecure LDAP calls each and every (time binned) hour. I can then drop down on the page and take what I’ve just learned (e.g. that svc1 is being used in an insecure manner) and I can research it by Source IP address.
Here I can fill in the blanks in the story from the account. svc1 made Insecure LDAP calls during multiple slices of time from a computer with IP address 192.168.2.74. Instead of having to sift through thousands of log files or (worse yet) try mitigating Insecure LDAP without a solid understanding of its presence in the environment, we now have a place to focus our mitigation activities. And, of course, once we have mitigated all of our Insecure LDAP in the environment, we will configure our domain controllers to no longer accept it at all — thereby effectively mitigating significant business risk to the organization.
The final enhancement that you’ll see in examining the IP Workbook is the Help section I mentioned earlier.
Each Help section is tab-specific, as you can see while moving between tabs with the Help toggle switch turned on.
The Help sections mainly follow the same format and contain sections that provide insight into each insecure protocol:
- Protocol Risk: risk of having the protocol active
- Auditing Settings: how to populate the data in the IP Workbook
- Mitigation Planning: concrete, actionable steps to take in order to remove the protocol from your estate
- Data Filters: available data filters on the particular tab
By way of example, let’s examine the Help file for Azure Active Directory Legacy Authentication (AAD Legacy Auth Tab). From the start, Protocol Risk gives us some compelling reasons to remove these insecure, outdated protocols.
The AAD tab is the only tab that does not include Auditing Settings, since we simply use AAD Sign-in logs here (e.g. this is a cloud-native SaaS data source). Instead, this tab lists the Legacy Authentication Protocols that you should consider as in-scope for this project.
The Mitigation Planning and Data Filters sections will look familiar from other tabs and once you start using the IP Workbook’s Help section frequently. Of course, once you’re familiar with each protocol, you can and should toggle off the Help section in order to maximize your screen real estate and to focus on understanding your data.
In this article, we covered enhancements to the IP Workbook, discussed how to leverage them to aid your data understanding, and drilled a bit deeper into the Timebrushing and Help features. Let us know how the IP Workbook is working for you and especially if you have ideas for enhancements. And until then, as always, happy auditing.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments