This article is contributed. See the original author and article here.
Transport Layer Security (TLS) and its deprecated predecessor Secure Sockets Layer (SSL), are cryptographic protocols designed to provide communications security over a computer network. SSL/TLS have some available versions to use, but the newer versions were created because of the security issues found on the previous ones.
It’s important to use the latest TLS version to make sure to have a secure way to exchanging keys, encrypt data and authenticate message integrity during all the communications..
This means the client and server should support the same SSL/TLS version.
Azure Cache for Redis can currently support TLS 1.0, 1.1 and 1.2, but there are some changes planned on TLS version and cypher Suites supported by Azure Cache for Redis:
- Azure Cache for Redis will stop supporting TLS versions 1.0 and 1.1.
After this change, your application will be required to use TLS 1.2 or later to communicate with your cache. - Additionally, as a part of this change, Azure Cache for Redis will remove support for older, insecure cypher suites. The supported cypher suites will be restricted to the following when the cache is configured with a minimum TLS version of 1.2.
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256
These changes were announced more than one year ago, and should have already occurred but were postponed due to COVID 19. Please be updated on theses changes in this link:
Remove TLS 1.0 and 1.1 from use with Azure Cache for Redis
Actions:
As the client and server should support the same SSL/TLS version, the client application will be required to use TLS 1.2 or later to communicate with your cache.
1. Changing client application to use TLS 1.2
In StackExchange.Redis and in most of other client libraries you may need to change your connection string and add ssl=true and sslprotocols=tls12 parameters, but this may be a little bit different on each one of client libraries. Also some other changes may be needed.
You can follow this documentation Configure your application to use TLS 1.2 to verify what changed are needed and if some other client environment changes are needed to use the latest TLS version in your client application.
.NET Framework: StackExchange.Redis, ServiceStack.Redis
.NET Core: all .NET Core clients
Java: Jedis, Lettuce, and Redisson
Node.js: Node Redis, IORedis
PHP: Predis, PhpRedis
Python: Redis-py
GO: Redigo
2. Changing Redis Minimum TLS version on Azure side
To disable old TLS versions on your Azure Redis instance, you may need to change the minimum TLS Version to 1.2.
This may take some minutes to be applied and you may use the Powershell script bellow to make sure the changes have been applied.
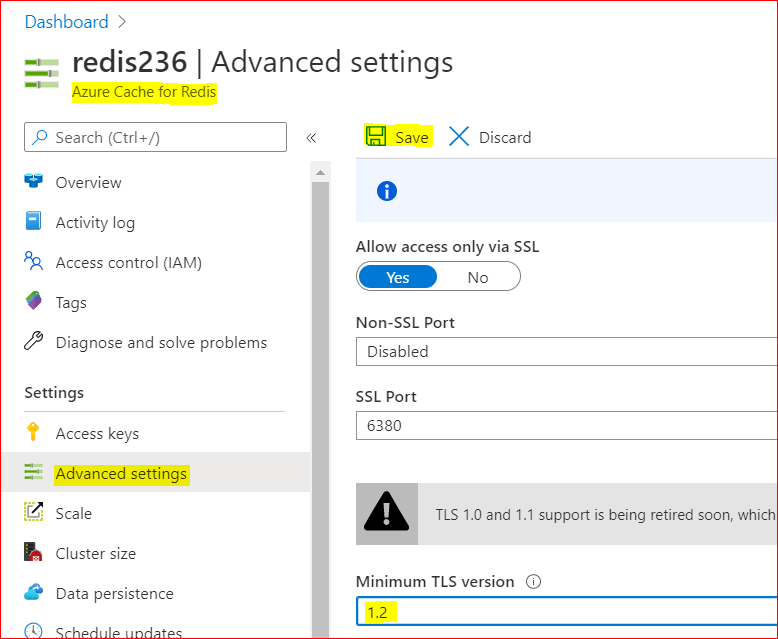
– Using Azure Portal :
– On Azure Portal, on your Azure Redis blade, choose Advanced Settings
– Change the minimum TLS Version to 1.2
– Save the changes
– Using PowerShell
You can do the same using PoweShell. You need the Az.RedisCache module already installed before run the command:
Set-AzRedisCache -Name <YourRedisName> -MinimumTlsVersion "1.2"
– Using CLI
Using CLI, the –minimum-tls-version are available only at Redis creation time and changing minimum-tls-version on an existing Azure Redis instance is not supported.
3. Check TLS versions supported by Redis endpoint
You can use this PowerShell script to verify what TLS versions are supported by your Azure Cache for Redis endpoint.
If your Redis instance have VNET integration implemented, you may need to run these PowerShell script from some VM inside your VNET, to have access to Azure Redis Instance:
param(
[Parameter(Mandatory=$true)]
[string]$redisCacheName,
[Parameter(Mandatory=$false)]
[string]$dnsSuffix = ".redis.cache.windows.net",
[Parameter(Mandatory=$false)]
[int]$connectionPort = 6380,
[Parameter(Mandatory=$false)]
[int]$timeoutMS = 2000
)
$redisEndpoint = "$redisCacheName$dnsSuffix"
$protocols = @(
[System.Security.Authentication.SslProtocols]::Tls,
[System.Security.Authentication.SslProtocols]::Tls11,
[System.Security.Authentication.SslProtocols]::Tls12
)
$protocols | % {
$ver = $_
$tcpClientSocket = New-Object Net.Sockets.TcpClient($redisEndpoint, $connectionPort )
if(!$tcpClientSocket)
{
Write-Error "$ver- Error Opening Connection: $port on $computername Unreachable"
exit 1;
}
else
{
$tcpstream = $tcpClientSocket.GetStream()
$sslStream = New-Object System.Net.Security.SslStream($tcpstream,$false)
$sslStream.ReadTimeout = $timeoutMS
$sslStream.WriteTimeout = $timeoutMS
try
{
$sslStream.AuthenticateAsClient($redisEndpoint, $null, $ver, $false)
Write-Host "$ver Enabled"
}
catch [System.IO.IOException]
{
Write-Host "$ver Disabled"
}
catch
{
Write-Error "Unexpected exception $_"
}
}
}
Conclusion:
Despite Azure Cache for Redis still currently support TLS 1.0, 1.1 and 1.2, it’s important to move only to TLS 1.2. Apart of the insecure TLS 1.0 and 1.1 versions, these versions will be deprecated soon from Azure Cache for Redis service.
For that reason is mandatory that all client applications can be adapted in advance to support TLS 1.2 on their Azure Cache for Redis connections, to avoid any downtime in the service.
Related documentation:
Remove TLS 1.0 and 1.1 from use with Azure Cache for Redis
PowerShell Az.RedisCache module
I hope this can be useful !!!
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments