This article is contributed. See the original author and article here.
I was working on this case last week and discussing with my colleagues Sergio Fonseca from SQLDB and Arjun Bardhan from AAD about this issue.
Let me just write a few lines here about the issue and solution.
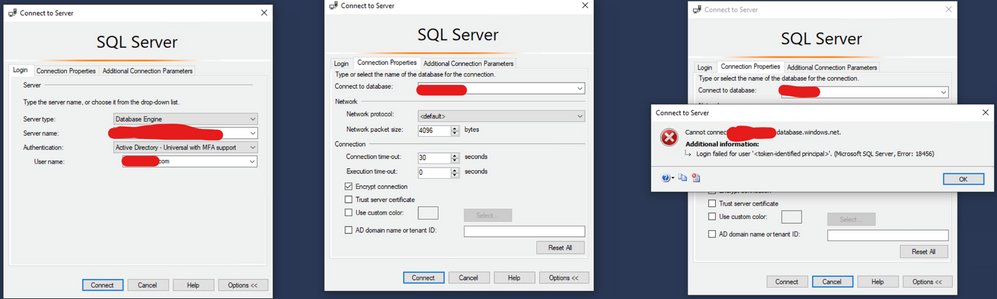
Issue: You have a SQL as a Service ( SQL DB or SQL DW) and you are trying to connect using MFA, you already tried to connect to the database on the SSMS as this blog mentioned: https://techcommunity.microsoft.com/t5/azure-database-support-blog/aad-auth-error-login-failed-for-user-lt-token-identified/ba-p/1417535. It did not work as Fig. 1 shows.
Fig. 1: Connection Failed
What else could you do?
Try to connect again using the same steps provided on the blog that I mentioned. But now check the option AD Domain Name or Tenant ID and type your AAD domain name that you can require from your AAD administrator.
Why? Because If you are connecting as a guest user using SSMS 17.x or older, you must use this option as provided on this documentation: https://docs.microsoft.com/en-us/azure/azure-sql/database/authentication-mfa-ssms-configure#connecting-by-using-universal-authentication-with-ssms
Example, Fig. 2:
Fig. 2 Tenant
Liliam
UK Engineer
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments