by Scott Muniz | Feb 10, 2023 | Security, Technology
This article is contributed. See the original author and article here.
CISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Note: To view the newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column, which will sort by descending dates.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the specified criteria.
by Contributed | Feb 10, 2023 | Technology
This article is contributed. See the original author and article here.
What is Arc for Azure VMware Solution? Simply put, it exposes your Azure VMware Solution resources (VMs, networks, datastores, etc.) to the Azure portal.
 Using Arc for Azure VMware Solution, those resources can be managed via the Azure portal, even though they are within your vSphere cluster running in an Azure datacenter. Even better, there is no cost to deploy Arc for Azure VMware Solution. More blogs to come on Arc for Azure VMware Solution, but if you want to get some more details check out this video from Jeremiah Megie.
Using Arc for Azure VMware Solution, those resources can be managed via the Azure portal, even though they are within your vSphere cluster running in an Azure datacenter. Even better, there is no cost to deploy Arc for Azure VMware Solution. More blogs to come on Arc for Azure VMware Solution, but if you want to get some more details check out this video from Jeremiah Megie.
First things first. Let’s get Arc for Azure VMware Solution installed into your private cloud.
You will need to collect the following information to input into the PowerShell script, which, if you use it, will make the deployment a bit more straightforward.
- Subscription ID and Resource Group where the Azure VMware Solution private cloud is deployed.
- Name of the Azure VMware Solution private cloud.
- /28 network segment for the ARC appliance.
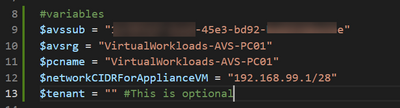
The/28 network segment will be an NSX-T segment in the private cloud. Under the covers, the deployment script creates NSX-T segment for use by the ARC appliances. The value must be entered into the script as the gateway to the segment, followed by /28. For example, if 192.168.99.1/28 is entered, there will be a /28 NSX-T segment created with the gateway 192.168.99.1.
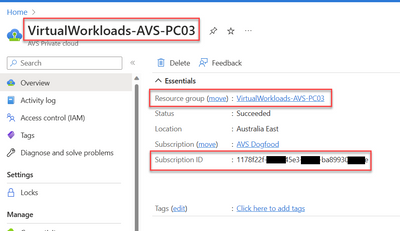
The other information you can get from the Overview blade of your private cloud.
Requirements
- Your private cloud must have Internet access.
- Also, because of the appliance size, ideally you would want to run this script as close to the private cloud, or from a machine inside the AVS Private Cloud.
The script can be found here;
https://virtualworkloads.com/2023/02/deploy-arc-for-azure-vmware-solution-simply-using-powershell/#script
by Scott Muniz | Feb 10, 2023 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Feb 10, 2023 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Feb 9, 2023 | Security, Technology
This article is contributed. See the original author and article here.
CISA, the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), the Department of Health and Human Services (HHS), and Republic of Korea’s Defense Security Agency and National Intelligence Service have released a joint Cybersecurity Advisory (CSA), Ransomware Attacks on Critical Infrastructure Fund DPRK Espionage Activities, to provide information on ransomware activity used by North Korean state-sponsored cyber to target various critical infrastructure sectors, especially Healthcare and Public Health (HPH) Sector organizations.
The authoring agencies urge network defenders to examine their current cybersecurity posture and apply the recommended mitigations in this joint CSA, which include:
- Train users to recognize and report phishing attempts.
- Enable and enforce phishing-resistant multifactor authentication.
- Install and regularly update antivirus and antimalware software on all hosts.
See Ransomware Attacks on Critical Infrastructure Fund DPRK Espionage Activities for ransomware actor’s tactics, techniques, and procedures, indicators of compromise, and recommended mitigations. Additionally, review StopRansomware.gov for more guidance on ransomware protection, detection, and response.
For more information on state-sponsored North Korean malicious cyber activity, see CISA’s North Korea Cyber Threat Overview and Advisories webpage.


Recent Comments