by Contributed | Aug 19, 2022 | Technology
This article is contributed. See the original author and article here.
We are excited to announce that the iOS and Android apps for Microsoft To Do (a tool for managing and sharing tasks and lists) is rolling out to GCC (Government Community Cloud) users. The rollout begins in late August, with plans to be completed by mid-September. This launch will add the mobile apps to the web and Outlook functionality that GCC accounts already have today.
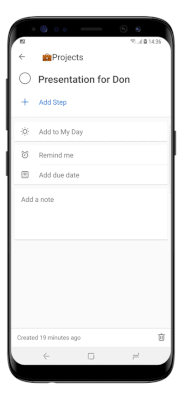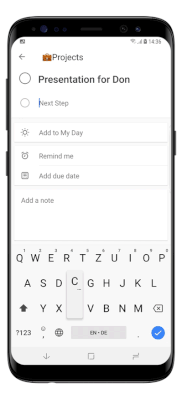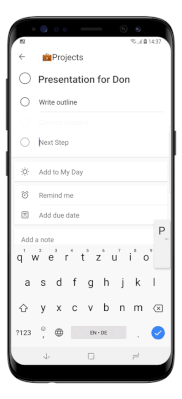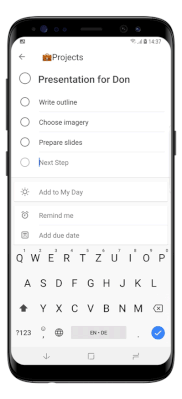
Using To Do on iOS and Android means that users can bring the power and flexibility of task list management wherever they go, with an intuitive UI closely resembling the experience users know from the web app:

Surface Duo users will also appreciate the 2-screen experience of the Android app that allows them to view their list of tasks on 1 screen, while viewing the details of a particular task on the other:
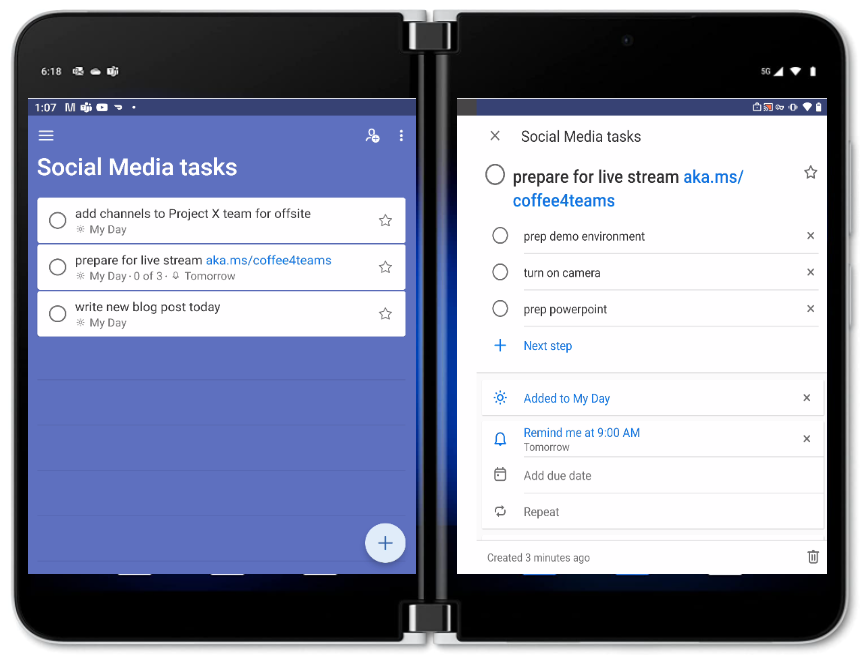
No admin action is needed to enable To Do mobile app access for GCC tenants. Features that remain unavailable in GCC at this time (consistent with the limitations of To Do Web) include shared list notifications, and the ability to share task lists outside your organization.
For more information, check out the support page.
For more info from me on collaboration & teamwork, follow me at TeamworkCowbell (blog | Twitter | YouTube) or at ricardo303, SharePointCowbell, and LinkedIn.
by Scott Muniz | Aug 19, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Aug 19, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Scott Muniz | Aug 18, 2022 | Security, Technology
This article is contributed. See the original author and article here.

Official websites use .gov
A .gov website belongs to an official government organization in the United States.

Secure .gov websites use HTTPS
A
lock ( )
) or
https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
by Scott Muniz | Aug 18, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has added seven new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise. Note: to view the newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column, which will sort by descending dates.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the specified criteria.


Recent Comments