by Contributed | Jan 23, 2022 | Technology
This article is contributed. See the original author and article here.
Final Update: Sunday, 23 January 2022 13:18 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 01/23, 12:45 UTC. Our logs show the incident started on 01/23, 11:07 UTC and that during the 1 hour and 38 minutes that it took to resolve the issue some customers using Azure Monitor and Azure Sentinel may have experienced issues accessing data as well as missed or delayed Log Search alerts in China East 2 region.
- Root Cause: The failure was due to one of our dependent service.
- Incident Timeline: 1 Hours & 38 minutes – 01/23, 11:07 UTC through 01/23, 12:45 UTC
We understand that customers rely on Application Insights as a critical service and apologize for any impact this incident caused.
-Anmol
by Contributed | Jan 22, 2022 | Technology
This article is contributed. See the original author and article here.
The huge success of Docker in energizing the tech community around containers has been truly amazing to see. As containers are the foundation of Kubernetes, it goes hand in hand that Docker was a core part of the platform. As Kubernetes matured, and the needs of the community and our customers grew, the tight coupling of Docker to Kubernetes through dockershim (the interface between the Kubernetes platform and the Docker runtime) needed to evolve. On 2 December 2020, with the release of Kubernetes 1.20, Kubernetes announced it is deprecating Docker as a container runtime, through the use of dockershim, in a future release of Kubernetes.
With the upcoming Kubernetes 1.24 release, dockershim will be removed.
If you are using a supported Kubernetes version in Azure Kubernetes Service (AKS):
- For Linux node pools, there is no action required on your part. All supported Kubernetes versions on AKS use containerd as the default runtime for Kubernetes 1.19 and greater.
- For Windows Server 2019 node pools, in January 2021, we announced the general availability of containerd as the default container runtime for Kubernetes 1.23 and greater. If you are using a cluster with a Kubernetes version prior to 1.23, you can create a new node pool with containerd enabled before the switch over to it being the default in 1.23 then move your pods to the new pool.
We work very closely with the community through our participation in the Kubernetes Special Interest Groups (SIG) from Storage, to Windows and everything in between and I’d like to thank both the community and our engineering teams for the work to get to this milestone.

by Scott Muniz | Jan 21, 2022 | Security, Technology
This article is contributed. See the original author and article here.

Official websites use .gov
A .gov website belongs to an official government organization in the United States.

Secure .gov websites use HTTPS
A
lock ( )
) or
https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
by Contributed | Jan 21, 2022 | Technology
This article is contributed. See the original author and article here.
Hello friends,
Happy new year everyone! With the new year come new possibilities. Today I’m excited to announce two Azure AD External Identities updates including the public preview of multi-factor authentication (MFA) with time-based one-time passcode (time-based OTP) for B2C users and an important change to our support for data residency in Azure AD B2C directories.
Strengthen MFA for B2C users with time-based OTP
Rising fraud and security attacks make it critical to protect consumer accounts with more secure forms of MFA. By incorporating time-based OTP through an authenticator app in your B2C user flows, you can provide a higher level of security compared to existing email and phone factors, without incurring additional telephony charges. Learn more from my colleague, Alex Weinert, about why we believe app-based MFA is more secure than email and phone MFA alone.
Time-based OTP for your user accounts can be configured with any authentication application. We recommend setting up your time-based OTP with Microsoft Authenticator, which uses encrypted bi-directional communication for authentication status and supports additional context and control that make it easier for your users to help protect themselves.
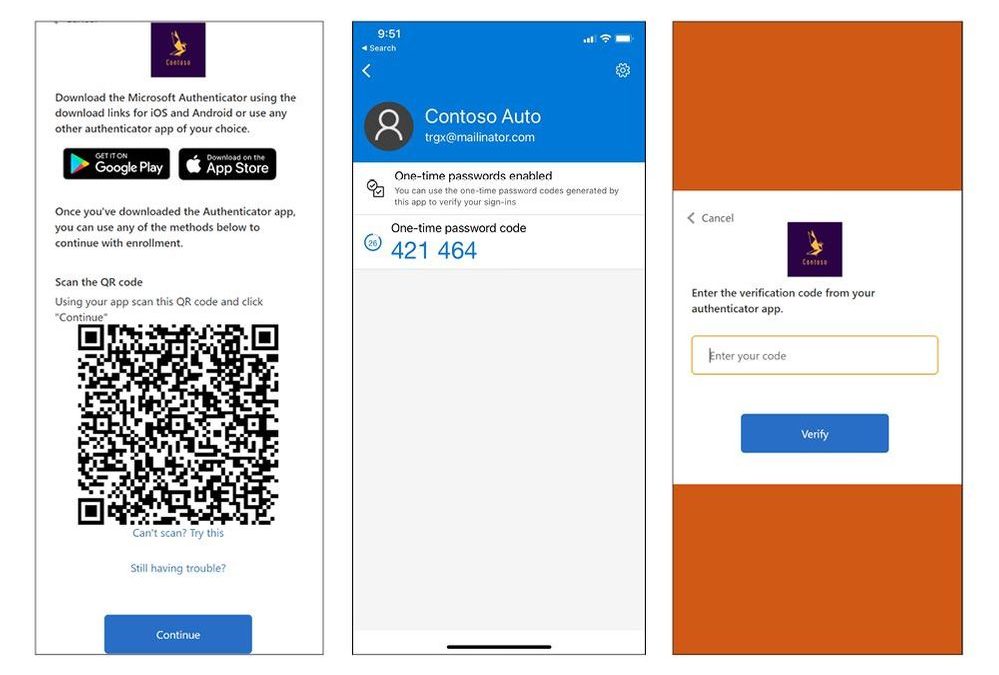
 In this B2C user flow, a Contoso customer is prompted to complete authentication using time-based OTP with the Microsoft Authenticator application.
In this B2C user flow, a Contoso customer is prompted to complete authentication using time-based OTP with the Microsoft Authenticator application.
Read the documentation to learn how to set up time-based OTP for Azure AD B2C.
Data residency pricing update
We understand how important it is for our customers to have control over their data and to comply with local data residency requirements. As a first step in supporting this business-critical need, earlier this year we announced the general availability of Azure AD B2C data residency in Australia. To support increased demand for this support, beginning mid-2022, current and new customers who have data residency configured for Australia or other specific countries/regions will incur an add-on charge of $0.02 per monthly active user (MAU).
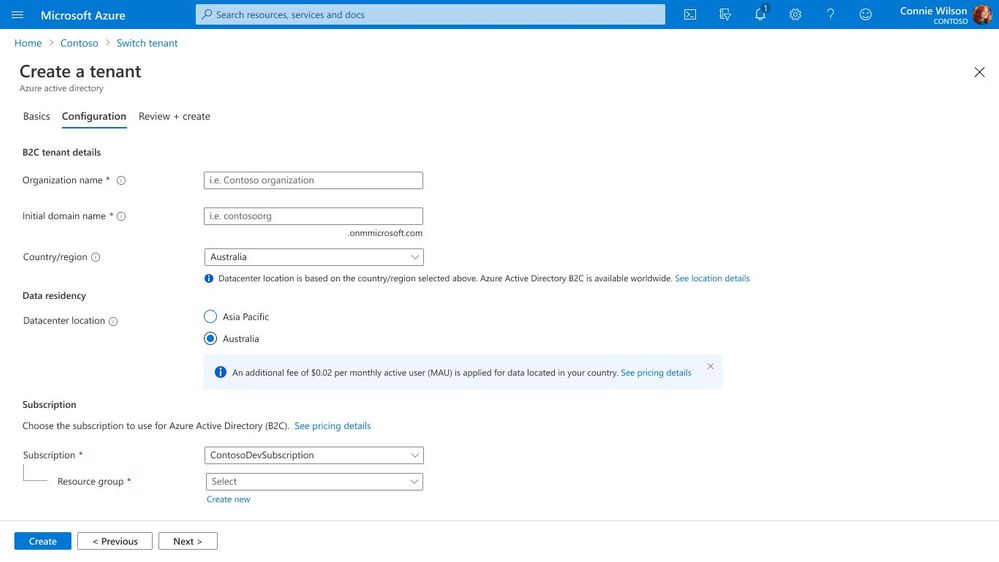
Based on your feedback, we are continuing to grow our data residency offerings so that you can target selection of the country/region needed to meet data storage requirements.
We love hearing from you, so please share your feedback on these updates through the Azure forum or by tagging @AzureAD on Twitter.
Robin Goldstein
Twitter: @RobinGo_MS
Learn more about Microsoft identity:
by Scott Muniz | Jan 21, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has added four new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for malicious cyber actors of all types and pose significant risk to the federal enterprise.
| CVE Number |
CVE Title |
Required Action Due Date |
| CVE-2006-1547 |
Apache Struts 1 ActionForm Denial of Service Vulnerability |
07/21/2022 |
| CVE-2012-0391 |
Apache Struts 2 Improper Input Validation Vulnerability |
07/21/2022 |
| CVE-2018-8453 |
Microsoft Windows Win32k Privilege Escalation Vulnerability |
07/21/2022 |
| CVE-2021-35247 |
SolarWinds Serv-U Improper Input Validation Vulnerability |
02/04/2022 |
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the meet the specified criteria.


Recent Comments