by Contributed | Feb 11, 2021 | Technology
This article is contributed. See the original author and article here.
The Cybersecurity Maturity Model Certification (CMMC) is a set of certification standards produced by the United States Department of Defense and intended to serve as a verification mechanism to ensure that companies bidding on defense contracts have appropriate levels of cybersecurity practices and processes in place. The CMMC is a unified standard for implementing cybersecurity across the defense industrial base (DIB). The CMMC is the DoD’s response to significant compromises of sensitive defense information located on contractors’ information systems.
Of particular interest is the following requirement:
CMMC – Level 3 – IA.3.083 (NIST 800-171r2 3.5.3) – Use multifactor authentication for local and network access to privileged accounts and for network access to non-privileged accounts.
- Local Access – Access to an organizational information system by a user (or process acting on behalf of a user) communicating through a direct connection without the use of a network.
- Network Access – Access to an information system by a user (or a process acting on behalf of a user) communicating through a network (e.g., local area network, wide area network, Internet).
- Privileged User – A user that is authorized (and therefore, trusted) to perform security-relevant functions that ordinary users are not authorized to perform.
Breaking down the above requirement means the following:
- All users are required MFA for network/remote access.
- Only privileged users are required MFA for local access (if regular user accounts have administrative rights only on their computers, they are not considered a “privileged account” and as such do not require MFA authentication for local access).
Why Windows Hello for Business is a viable MFA authenticator
Windows Hello for Business provides authentication methods intended to replace passwords, which can be difficult to remember and easily compromised. The Windows Hello provisioning process creates a cryptographic key pair bound to the Trusted Platform Module (TPM) and combines it with additional information to authenticate users. The additional information the user supplies is the activation factor for Windows Hello for Business and can be a PIN value (“something you know”) or, if the system has the necessary hardware, biometric information, such as fingerprint or facial recognition (“something you are”). The TPM constitutes the “something you have” factor for the purpose of MFA. Learn more about How Windows Hello for Business uses the TPM.
The idea of TPM as a valid “something you have” factor is not new, and addressed by NIST 800-63B Section 5.1.9.1 back in December 2017 (as captured in the errata) where a TPM is recognized as a hardware cryptographic authenticator. Multi-factor cryptographic device authenticators use tamper-resistant hardware to encapsulate one or more secret keys unique to the authenticator and accessible only through the input of an additional factor, either a memorized secret or a biometric. The authenticator operates by using a private key that was unlocked by the additional factor to sign a challenge nonce presented through a direct computer interface (e.g., a USB port). Alternatively, the authenticator could be a suitably secure processor integrated with the user endpoint itself (e.g., a hardware TPM).
Configuring Windows Hello in a way that adheres to NIST guidance
Now that we unveiled the mystery behind CMMC – Level 3 – IA.3.083 requirement and explained why Windows Hello for Business is a viable MFA authenticator, let us make sure it is configured in a way that adheres to NIST guidance and provides the required strength:
- To adhere to NIST 800-63B Section 5.1.2.2 requirements of activation factor (PIN) at least 8 characters long, configure minimum PIN length Group Policy setting for PIN Complexity to be at least 8 characters (no complexity rules are required, PIN can be digits only).
- Make sure Windows Hello for Business cryptographic key are protected using a tamper-resistant hardware by enabling use a hardware security device Group Policy setting for Windows Hello for Business.
- For securing privileged access, restrict privileged users to only access from secure workstations and require MFA for sign-in:
For those who still do not accept TPM as “something you have” factor for local accesses (sign-in to the endpoint) or for those seeking additional risk mitigation, an alternative option is using FIDO2 keys or smart cards.
Additional resources
Achieving National Institute of Standards and Technology Authenticator Assurance Levels with the Microsoft Identity Platform
About the author
@Ehud_Itshaki is a Principal Program Manager in the Azure Active Directory Customer Success Team. Currently he is focused on regulatory issues for highly regulated industries and Government. Areas of focus include but are not limited to NIST, FedRAMP, DoD SRG, CMMC, CJIS, IRS 1075, EPCS, etc.
by Contributed | Feb 11, 2021 | Technology
This article is contributed. See the original author and article here.
Overview
Businesses today are applying Optical Character Recognition (OCR) and document AI technologies to rapidly convert their large troves of documents and images into actionable insights. These insights power robotic process automation (RPA), knowledge mining, and industry-specific solutions. However, there are several challenges to successfully implementing these scenarios at scale.
The challenge
Your customers are global, and their content is global so your systems should also speak and read international languages. Nothing is more frustrating than not reaching your global customers due to lack of support for their native languages.
Secondly, your documents are large, with potentially hundreds and even thousands of pages. To complicate things, they have print and handwritten style text mixed into the same documents. To make matters worse, they have multiple languages in the same document, possibly even in the same line.
Thirdly, you are a business that’s trusted by your customers to protect their data and information. If your customers are in industries such as healthcare, insurance, banking, and finance, you have stringent data privacy and security needs. You need the flexibility to deploy your solutions on the world’s most trusted cloud or on-premise within your environment.
Finally, you should not have to choose between world-class AI quality, world languages support, and deployment on cloud or on-premise.
Computer Vision OCR (Read API)
Microsoft’s Computer Vision OCR (Read) technology is available as a Cognitive Services Cloud API and as Docker containers. Customers use it in diverse scenarios on the cloud and within their networks to help automate image and document processing.
What’s New
We are announcing Computer Vision’s Read API v3.2 public preview as a cloud service and Docker container. It includes the following updates:
- OCR for 73 languages including Simplified and Traditional Chinese, Japanese, Korean, and several Latin languages.
- Natural reading order for the text line output.
- Handwriting style classification for text lines.
- Text extraction for selected pages for a multi-page document.
- Available as a Distroless container for on-premise deployment.
First wave of language expansion
With the latest Read preview version, we are announcing OCR support for 73 languages, including Chinese Simplified, Chinese Traditional, Japanese, Korean, and several Latin languages, a 10x increase from the Read 3.1 GA version.
Thanks to Read’s universal model, to extract the text in these languages, use the Read API call without the optional language parameter. We recommend not using the language parameter if you are unsure of the language of the input document or image at run time.
The latest Read preview supports the following languages:
English
French
Italian
German
Spanish
Portuguese
Dutch
Chinese Simplified
Chinese Traditional
Japanese
Korean
Czech
Hungarian
Polish
Swedish
Turkish
Danish
Norwegian
|
Cebuano
Fijian
Swahili (Latin)
Uzbek (Latin)
Zulu
Afrikaans
Albanian
Indonesian
Malay (Latin script)
Filipino
Catalan
Galician
Basque
Haitian Creole
Irish
Javanese
Scottish Gaelic
Scots
Romansh
|
Luxembourgish
Occitan
Breton
Asturian
Neapolitan
Western Frisian
Corsican
Friulian
Manx
Kara-Kalpak
Gilbertese
Bislama
Kachin (Latin script)
Khasi
Hani
Greenlandic
Tetum
Zhuang
|
Volapük
Interlingua
Kabuverdianu
Cornish
Hmong Daw (Latin)
Inuktitut (Latin)
K’iche’
Yucatec Maya
Estonian
Finnish
Slovenian
Kashubian
Kurdish (Latin)
Tatar (Latin)
Crimean Tatar (Latin)
Chamorro
Upper Sorbian
Walser
|
For example, once you have created a Computer Vision resource, the following curl code will call the Read 3.2 preview with the sample image.
Make the following changes in the command where needed:
- Replace the value of
<subscriptionKey> with your subscription key.
- Replace the first part of the request URL (
westcentralus) with the text in your own endpoint URL.
curl -v -X POST "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyze" -H "Content-Type: application/json" -H "Ocp-Apim-Subscription-Key: <subscription key>" --data-ascii "{"url":"https://upload.wikimedia.org/wikipedia/commons/thumb/a/af/Atomist_quote_from_Democritus.png/338px-Atomist_quote_from_Democritus.png"}"
The response will include an Operation-Location header, whose value is a unique URL. You use this URL to query the results of the Read operation. The URL expires in 48 hours.
curl -v -X GET "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyzeResults/{operationId}" -H "Ocp-Apim-Subscription-Key: {subscription key}" --data-ascii "{body}"
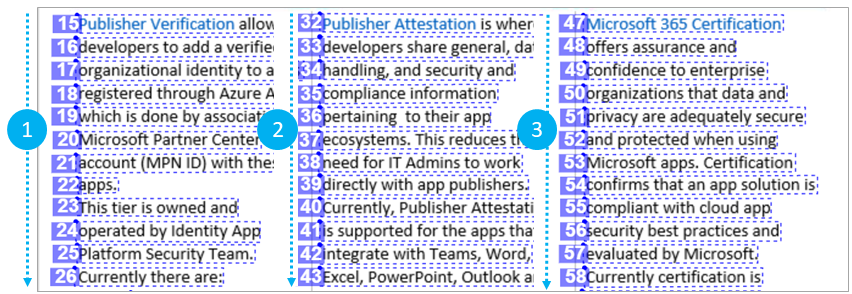
Natural reading order output
OCR services typically output text in a certain order in their output. With the new Read preview, choose to get the text lines in the natural reading order instead of the default left to right and top to bottom ordering. Use the new readingOrder query parameter with the “natural” value for a more human-friendly reading order output as shown in the following example.
The following visualization of the JSON formatted service response shows the text line order for the same document. Note the first column’s text lines output in order before listing the second column and finally the third column.
 OCR Read order example
OCR Read order example
For example, the following curl code sample calls the Read 3.2 preview to analyze the sample newsletter image and output a natural reading order for the extracted text lines.
curl -v -X POST "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyze?readingOrder=natural -H "Content-Type: application/json" -H "Ocp-Apim-Subscription-Key: <subscription key>" --data-ascii "{"url":"https://docs.microsoft.com/en-us/microsoft-365-app-certification/media/dec01.png"}"
The response will include an Operation-Location header, whose value is a unique URL. You use this URL to query the results of the Read operation.
curl -v -X GET "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyzeResults/{operationId}" -H "Ocp-Apim-Subscription-Key: {subscription key}" --data-ascii "{body}"
Handwriting style classification
When you apply OCR on business forms and applications, it’s useful to know which parts of the form has handwritten text in them so that they can be handled differently. For example, comments and the signature areas of agreements typically contain handwritten text. With the latest Read preview, the service will classify English and Latin languages-only text lines as handwritten style or not along with a confidence score.
For example, in the following image, you see the appearance object in the JSON response with the style classified as handwriting along with a confidence score.
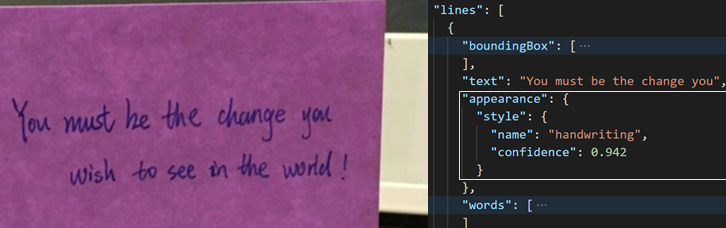 OCR handwriting style classification for text lines
OCR handwriting style classification for text lines
The following code analyzes the sample handwritten image with the Read 3.2 preview.
curl -v -X POST "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyze -H "Content-Type: application/json" -H "Ocp-Apim-Subscription-Key: <subscription key>" --data-ascii "{"url":"https://intelligentkioskstore.blob.core.windows.net/visionapi/suggestedphotos/2.png"}"
The response will include an Operation-Location header, whose value is a unique URL. You use this URL to query the results of the Read operation.
curl -v -X GET "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyzeResults/{operationId}" -H "Ocp-Apim-Subscription-Key: {subscription key}" --data-ascii "{body}"
Extract text from select pages of a document
Many standard business forms have fillable sections followed by long informational sections that are identical between documents, and versions of those documents. At other times, you will be interested in applying OCR to specific pages of interest for business-specific reasons.
The following curl code sample calls the Read 3.2 preview to analyze the financial report PDF document with the pages input parameter set to the page range, “3-5”.
curl -v -X POST "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyze?pages=3-5 -H "Content-Type: application/json" -H "Ocp-Apim-Subscription-Key: <subscription key>" --data-ascii "{"url":"https://www.annualreports.com/HostedData/AnnualReports/PDF/NASDAQ_MSFT_2019.pdf"}"
The response will include an Operation-Location header, whose value is a unique URL. You use this URL to query the results of the Read operation.
curl -v -X GET "https://westcentralus.api.cognitive.microsoft.com/vision/v3.2-preview.2/read/analyzeResults/{operationId}" -H "Ocp-Apim-Subscription-Key: {subscription key}" --data-ascii "{body}"
The following JSON extract shows the resulting OCR output that extracted the text from pages 3, 4, and 5. You should see a similar output for your sample documents.
"readResults": [
{
"page": 3,
"angle": 0,
"width": 8.5,
"height": 11,
"unit": "inch",
"lines": []
},
{
"page": 4,
"angle": 0,
"width": 8.5,
"height": 11,
"unit": "inch",
"lines": []
},
{
"page": 5,
"angle": 0,
"width": 8.5,
"height": 11,
"unit": "inch",
"lines": []
}
]
On-premise option with Distroless container

The Read 3.2 preview OCR container provides:
- All features from the Read cloud API preview
- Distroless container release
- Performance and memory enhancements
Install and run the Read containers to get started and find the recommended configuration settings.
Get Started
by Scott Muniz | Feb 11, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Summary
On February 5, 2021, unidentified cyber actors obtained unauthorized access to the supervisory control and data acquisition (SCADA) system at a U.S. drinking water treatment plant. The unidentified actors used the SCADA system’s software to increase the amount of sodium hydroxide, also known as lye, a caustic chemical, as part of the water treatment process. Water treatment plant personnel immediately noticed the change in dosing amounts and corrected the issue before the SCADA system’s software detected the manipulation and alarmed due to the unauthorized change. As a result, the water treatment process remained unaffected and continued to operate as normal. The cyber actors likely accessed the system by exploiting cybersecurity weaknesses, including poor password security, and an outdated operating system. Early information indicates it is possible that a desktop sharing software, such as TeamViewer, may have been used to gain unauthorized access to the system. Onsite response to the incident included Pinellas County Sheriff Office (PCSO), U.S. Secret Service (USSS), and the Federal Bureau of Investigation (FBI).
The FBI, the Cybersecurity and Infrastructure Security Agency (CISA), the Environmental Protection Agency (EPA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) have observed cyber criminals targeting and exploiting desktop sharing software and computer networks running operating systems with end of life status to gain unauthorized access to systems. Desktop sharing software, which has multiple legitimate uses—such as enabling telework, remote technical support, and file transfers—can also be exploited through malicious actors’ use of social engineering tactics and other illicit measures. Windows 7 will become more susceptible to exploitation due to lack of security updates and the discovery of new vulnerabilities. Microsoft and other industry professionals strongly recommend upgrading computer systems to an actively supported operating system. Continuing to use any operating system within an enterprise beyond the end of life status may provide cyber criminals access into computer systems.
Click here for a PDF version of this report.
Technical Details
Desktop Sharing Software
The FBI, CISA, EPA, and MS-ISAC have observed corrupt insiders and outside cyber actors using desktop sharing software to victimize targets in a range of organizations, including those in the critical infrastructure sectors. In addition to adjusting system operations, cyber actors also use the following techniques:
- Use access granted by desktop sharing software to perform fraudulent wire transfers.
- Inject malicious code that allows the cyber actors to
- Hide desktop sharing software windows,
- Protect malicious files from being detected, and
- Control desktop sharing software startup parameters to obfuscate their activity.
- Move laterally across a network to increase the scope of activity.
TeamViewer, a desktop sharing software, is a legitimate popular tool that has been exploited by cyber actors engaged in targeted social engineering attacks, as well as large scale, indiscriminate phishing campaigns. Desktop sharing software can also be used by employees with vindictive and/or larcenous motivations against employers.
Beyond its legitimate uses, TeamViewer allows cyber actors to exercise remote control over computer systems and drop files onto victim computers, making it functionally similar to Remote Access Trojans (RATs). TeamViewer’s legitimate use, however, makes anomalous activity less suspicious to end users and system administrators compared to RATs.
Windows 7 End of Life
On January 14, 2020, Microsoft ended support for the Windows 7 operating system, which includes security updates and technical support unless certain customers purchased an Extended Security Update (ESU) plan. The ESU plan is paid per-device and available for Windows 7 Professional and Enterprise versions, with an increasing price the longer a customer continues use. Microsoft will only offer the ESU plan until January 2023. Continued use of Windows 7 increases the risk of cyber actor exploitation of a computer system.
Cyber actors continue to find entry points into legacy Windows operating systems and leverage Remote Desktop Protocol (RDP) exploits. Microsoft released an emergency patch for its older operating systems, including Windows 7, after an information security researcher discovered an RDP vulnerability in May 2019. Since the end of July 2019, malicious RDP activity has increased with the development of a working commercial exploit for the vulnerability. Cyber actors often use misconfigured or improperly secured RDP access controls to conduct cyberattacks. The xDedic Marketplace, taken down by law enforcement in 2019, flourished by compromising RDP vulnerabilities around the world.
Mitigations
General Recommendations
The following cyber hygiene measures may help protect against the aforementioned scheme:
- Update to the latest version of the operating system (e.g., Windows 10).
- Use multiple-factor authentication.
- Use strong passwords to protect Remote Desktop Protocol (RDP) credentials.
- Ensure anti-virus, spam filters, and firewalls are up to date, properly configured, and secure.
- Audit network configurations and isolate computer systems that cannot be updated.
- Audit your network for systems using RDP, closing unused RDP ports, applying multiple-factor authentication wherever possible, and logging RDP login attempts.
- Audit logs for all remote connection protocols.
- Train users to identify and report attempts at social engineering.
- Identify and suspend access of users exhibiting unusual activity.
Water and Wastewater Systems Security Recommendations
The following physical security measures serve as additional protective measures:
- Install independent cyber-physical safety systems. These are systems that physically prevent dangerous conditions from occurring if the control system is compromised by a threat actor.
- Examples of cyber-physical safety system controls include:
- Size of the chemical pump
- Size of the chemical reservoir
- Gearing on valves
- Pressure switches, etc.
The benefit of these types of controls in the water sector is that smaller systems, with limited cybersecurity capability, can assess their system from a worst-case scenario. The operators can take physical steps to limit the damage. If, for example, cyber actors gain control of a sodium hydroxide pump, they will be unable to raise the pH to dangerous levels.
TeamViewer Software Recommendations
For a more secured implementation of TeamViewer software:
- Do not use unattended access features, such as “Start TeamViewer with Windows” and “Grant easy access.”
- Configure TeamViewer service to “manual start,” so that the application and associated background services are stopped when not in use.
- Set random passwords to generate 10-character alphanumeric passwords.
- If using personal passwords, utilize complex rotating passwords of varying lengths. Note: TeamViewer allows users to change connection passwords for each new session. If an end user chooses this option, never save connection passwords as an option as they can be leveraged for persistence.
- When configuring access control for a host, utilize custom settings to tier the access a remote party may attempt to acquire.
- Require remote party to receive confirmation from the host to gain any access other than “view only.” Doing so will ensure that, if an unauthorized party is able to connect via TeamViewer, they will only see a locked screen and will not have keyboard control.
- Utilize the ‘Block and Allow’ list which enables a user to control which other organizational users of TeamViewer may request access to the system. This list can also be used to block users suspected of unauthorized access.
Contact Information
To report suspicious or criminal activity related to information found in this Joint Cybersecurity Advisory, contact your local FBI field office at www.fbi.gov/contact-us/field, or the FBI’s 24/7 Cyber Watch (CyWatch) at (855) 292-3937 or by e-mail at CyWatch@fbi.gov or your local WMD Coordinator. When available, please include the following information regarding the incident: date, time, and location of the incident; type of activity; number of people affected; type of equipment used for the activity; the name of the submitting company or organization; and a designated point of contact.
To request incident response resources or technical assistance related to these threats, contact CISA at Central@cisa.dhs.gov.
Revisions
February 11, 2021: Initial Version
This product is provided subject to this Notification and this Privacy & Use policy.


Recent Comments