by Contributed | Jan 18, 2021 | Technology
This article is contributed. See the original author and article here.
Oracle 19c on Azure NetApp Files for SAP Workloads
PoC and Validation
Oracle Installation Guide
Introduction
This document will show how you can install Oracle 19c on Azure for SAP Applications using Azure NetApp Files (ANF) as storage platform for data and log areas. The support is mentioned in the two SAP notes:
2015553 – SAP on Microsoft Azure: Support prerequisites – SAP ONE Support Launchpad
2039619 – SAP Applications on Microsoft Azure using the Oracle Database: Supported Products and Versions – SAP ONE Support Launchpad
This document written for experienced technical people. Not all aspects are covered because we assume a profound technical knowledge on all the mentioned topics like Linux, Oracle DB and NFS.
The supported components are: Oracle Linux 8.2, Oracle 19c and NFS 4.1 on ANF
Thank you from the awesome support to:
Jan Klokkers Oracle
Christoph Kurucz Oracle
Geert van Teylingen Azure NetApp Files alliance
Jeffrey Steiner NetApp
Juergen Thomas Microsoft
Installation
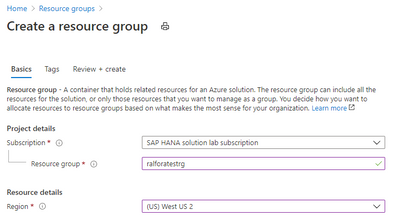
Create a resource Group.

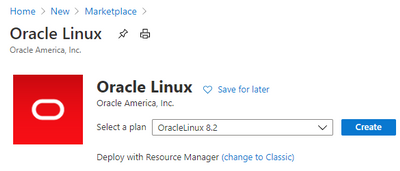
Create the VM
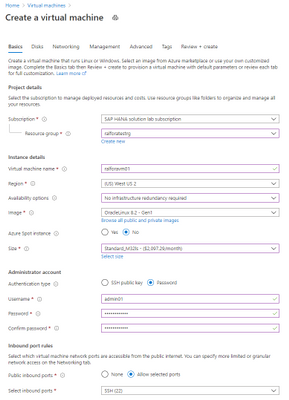
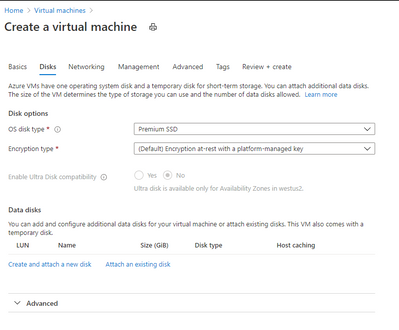
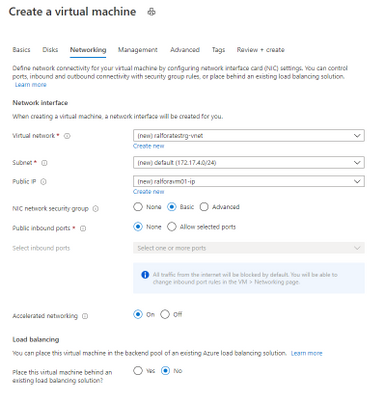
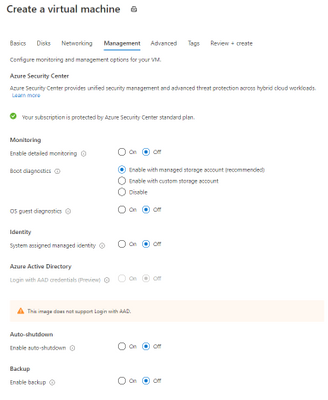
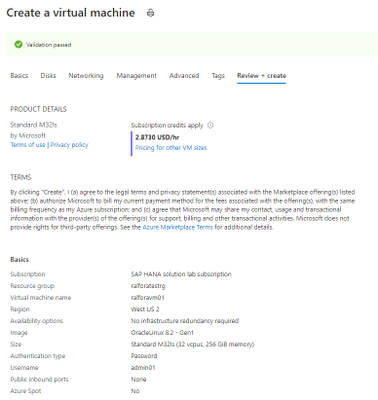
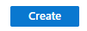
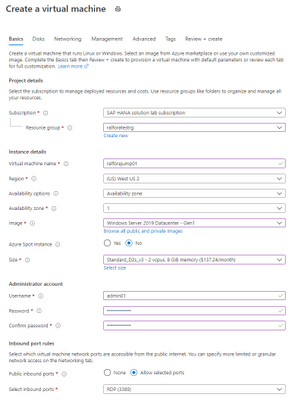
Creating the Jump Box
Oracle Linux
Check the Kernel version
uname -a
Linux ralforavm01 5.4.17-2011.6.2.el8uek.x86_64 #2 SMP Thu Sep 3 13:38:27 PDT 2020 x86_64 x86_64 x86_64 GNU/Linux
Check the OS Release
cat /etc/os-release
NAME="Oracle Linux Server"
VERSION="8.2"
ID="ol"
ID_LIKE="fedora"
VARIANT="Server"
VARIANT_ID="server"
VERSION_ID="8.2"
PLATFORM_ID="platform:el8"
PRETTY_NAME="Oracle Linux Server 8.2"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:oracle:linux:8:2:server"
HOME_URL="https://linux.oracle.com/"
BUG_REPORT_URL="https://bugzilla.oracle.com/"
List the number and type of CPU’S of the VM
lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
CPU(s): 32
On-line CPU(s) list: 0-31
Thread(s) per core: 2
Core(s) per socket: 16
Socket(s): 1
NUMA node(s): 1
Vendor ID: GenuineIntel
CPU family: 6
Model: 63
Model name: Intel(R) Xeon(R) CPU E7-8890 v3 @ 2.50GHz
Stepping: 4
CPU MHz: 2493.986
BogoMIPS: 4987.97
Virtualization: VT-x
Hypervisor vendor: Microsoft
Virtualization type: full
L1d cache: 32K
L1i cache: 32K
L2 cache: 256K
L3 cache: 46080K
NUMA node0 CPU(s): 0-31
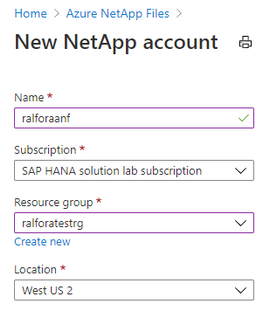
Create a storage Account
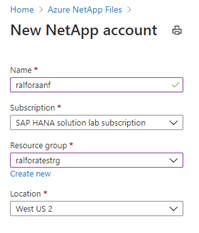
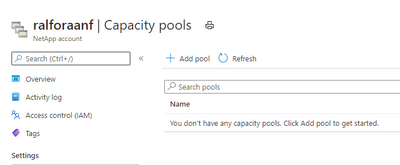
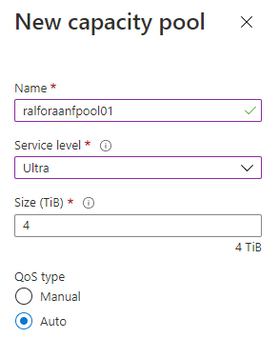
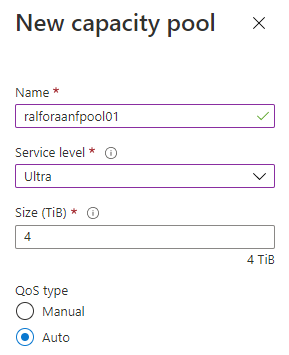
Create a capacity Pool
Add a capacity Pool
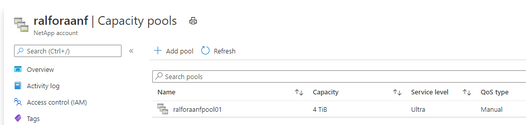
Depending on the database size and expected performance decide which ANF SKU does fit best for the target database. In our case it is Ultra.
Finished
Volume design
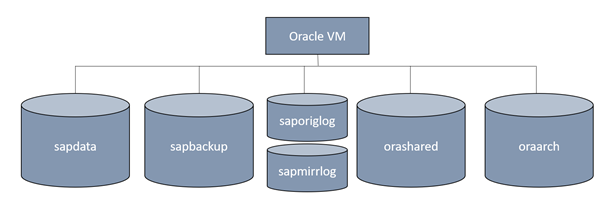
Create the delegated subnet for ANF
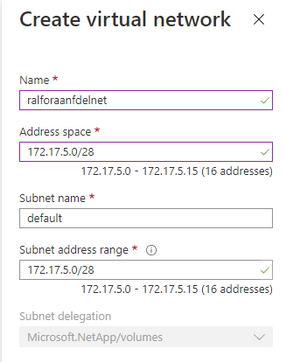
Create a Capacity Pool
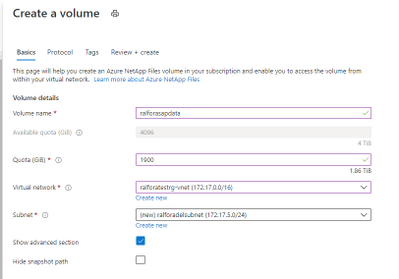
Select the protocol for the volumes
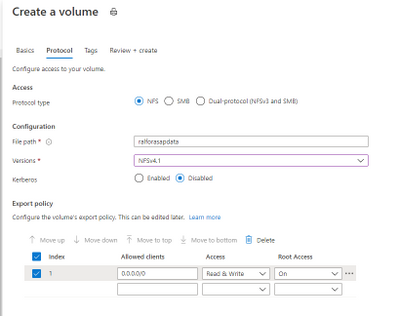
Add a Capacity Pool
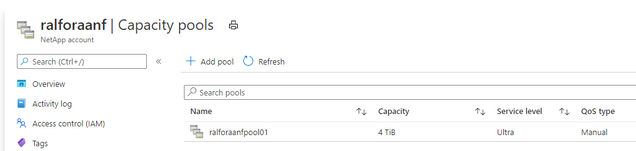
After deploying the above mentioned design it looks like this:
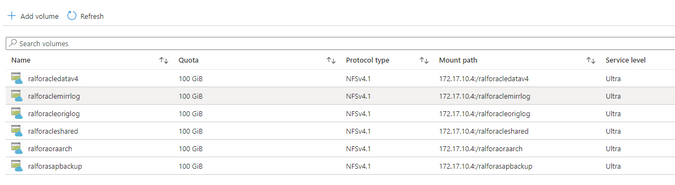
Configure the /etc/hosts
vi /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
172.17.4.9 ralforavm01.localdomain ralforavm01
172.17.10.4 anf01
Configure the hostname as FQDN
vi /etc/hostname
ralforavm01.localdomain
Create the mountpoints for Oracle and SAP
mkdir -p /oracle/C11/sapdata1 /oracle/C11/sapdata2 /oracle/C11/sapdata3 /oracle/C11/sapdata4 /oracle/C11/origlogA /oracle/C11/origlogB /oracle/C11/mirrlogA /oracle/C11/mirrlogB /oracle/C11/saparch /oracle/C11/sapbackup /oracle/C11/sapreorg /oracle/C11/orainstall /oracle/C11/saptrace /oracle/C11/oraarch /oracle/C11/19.0.0 /oracle/stage /oracle/client
mkdir -p /usr/sap/C11 /sapmnt/C11 /usr/sap/trans
mount the root volume and create the mountpoints.
mount anf01:/ralforasapdatav3 /mnt
mkdir /mnt/sapdata1 /mnt/sapdata2 /mnt/sapdata3 /mnt/sapdata4 ; umount /mnt
mount anf01:/ralforaclemirrlog /mnt
mkdir /mnt/mirrlogA /mnt/mirrlogB; umount /mnt
mount anf01:/ralforacleoriglog /mnt
mkdir /mnt/origlogA /mnt/origlogB; umount /mnt
mount anf01:/ralforacleshared /mnt
mkdir /mnt/oraarch /mnt/saparch /mnt/sapbackup /mnt/sapreorg /mnt/saptrace /mnt/Software /mnt/usr_sap /mnt/sapmnt /mnt/19.0.0 /mnt/trans /mnt/ora_client /mnt/orainstall /mnt/ora_stage ;umount /mnt
Manage the idmapd for ANF
vi /etc/idmapd.conf
# Example
[General]
Domain = defaultv4iddomain.com
modify the /etc/fstab
#
# Oracle
#
anf01:/ralforacledatav4/sapdata1 /oracle/C11/sapdata1 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata2 /oracle/C11/sapdata2 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata3 /oracle/C11/sapdata3 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata4 /oracle/C11/sapdata4 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforaclemirrlog/mirrlogA /oracle/C11/mirrlogA nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforaclemirrlog/mirrlogB /oracle/C11/mirrlogB nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
##
anf01:/ralforacleoriglog/origlogA /oracle/C11/origlogA nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleoriglog/origlogB /oracle/C11/origlogB nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
##
anf01:/ralforacleshared/19.0.0 /oracle/C11/19.0.0 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/oraarch /oracle/C11/oraarch nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/saparch /oracle/C11/saparch nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapbackup /oracle/C11/sapbackup nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapreorg /oracle/C11/sapreorg nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/saptrace /oracle/C11/saptrace nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/Software /oracle/C11/Software nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/ora_client /oracle/client nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/ora_stage /oracle/stage nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/usr_sap /usr/sap/C11 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/trans /usr/sap/trans nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapmnt /sapmnt nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/orainst /oracle/C11/orainstall nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
Stop the firewalld
systemctl disable firewalld
systemctl stop firewalld
Update the VM’s OS image (no registration required)
yum update
Last metadata expiration check: 1:24:42 ago on Tue 03 Nov 2020 10:04:53 AM UTC.
…
Install 5 Packages
Upgrade 25 Packages
Total download size: 159 M
Is this ok [y/N]:y
Install the required libraries.
dnf install -y oracle-database-preinstall-19c
dnf install -y binutils
dnf install -y compat-libstdc++-33
dnf install -y elfutils-libelf
dnf install -y elfutils-libelf-devel
dnf install -y fontconfig-devel
dnf install -y glibc
dnf install -y glibc-devel
dnf install -y ksh
dnf install -y libaio
dnf install -y libaio-devel
dnf install -y libXrender
dnf install -y libXrender-devel
dnf install -y libX11
dnf install -y libXau
dnf install -y libXi
dnf install -y libXtst
dnf install -y libgcc
dnf install -y librdmacm-devel
dnf install -y libstdc++
dnf install -y libstdc++-devel
dnf install -y libxcbdnf install -y unixODBC
# New for OL8
dnf install -y ipmiutil
dnf install -y libnsl2
dnf install -y libnsl2-devel
dnf install -y net-tools
dnf install -y nfs-utils
dnf install -y libnsl
dnf install -y make
dnf install -y python # ACFS
dnf install -y python-configshell # ACFS
dnf install -y python-rtslib # ACFS
dnf install -y python-six # ACFS
dnf install -y targetcli # ACFS
dnf install -y smartmontools
dnf install -y sysstat
modify the /etc/sysctl.conf
Change the nessesary kernel parameter in /etc/sysctl.conf
kernel.sem = 250 32000 100 128
kernel.shmmni = 4096
kernel.shmall = 1073741824
kernel.shmmax = 4398046511104
kernel.panic_on_oops = 1
net.ipv6.conf.all.disable_ipv6 = 1
net.core.rmem_max = 16777216
net.core.wmem_max = 16777216
net.core.optmem_max = 16777216
net.core.somaxconn = 4096
net.core.netdev_max_backlog = 300000
net.ipv4.ip_local_port_range = 9000 65500
net.ipv4.conf.all.rp_filter = 2
net.ipv4.conf.default.rp_filter = 2
net.ipv4.conf.default.rp_filter = 2
net.ipv4.tcp_rmem = 65536 16777216 16777216
net.ipv4.tcp_wmem = 65536 16777216 16777216
net.ipv4.tcp_max_syn_backlog = 16348
net.ipv4.tcp_slow_start_after_idle = 0
net.ipv4.tcp_dsack = 1
net.ipv4.tcp_sack = 1
net.ipv4.tcp_no_metrics_save = 1
net.ipv4.tcp_moderate_rcvbuf = 1
net.ipv4.tcp_window_scaling = 1
net.ipv4.tcp_syn_retries = 8
net.ipv4.tcp_tw_reuse = 1
net.ipv4.tcp_timestamps = 1
vm.swappiness = 10
vm.dirty_bytes = 629145600
vm.dirty_background_bytes = 314572800
vm.max_map_count = 2147483647
vm.memory_failure_early_kill = 1
fs.file-max = 820448174
fs.aio-max-nr = 18446744073709551615
Download the Oracle 19c DB and the Patch-Set 19.8.0.0 from the SAP Software download Center
Create the SAP and Oracle user
groupadd sapsys -g 79
groupadd dba -g 80
groupadd oper -g 85
groupadd oinstall -g 90
Create the required oracle user
useradd c11adm -u 1001 -d /usr/sap/C11 -g 79 -s /bin/csh -c "SAP Administrator C11"
useradd orac11 -u 1002 -d /oracle/C11 -g 80 -G oper,dba,oinstall -s /bin/bash -c "Oracle Administrator C11"
useradd oracle -u 1003 -d /oracle/C11 -g 90 -G oper,dba -s /bin/bash -c "Oracle Installation"
usermod -a -G oper orac11
disable selinux
[root@ralforavm01 ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: permissive
Mode from config file: permissive
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 31
Disable selinux
vi /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted change the user Permission to the sap and oracle directories.
Reboot the server
Check if selinux is disabled
sestatus
SELinux status: disabled
Change the nfs mountpoint permissions.
chown -R c11adm:sapsys /usr/sap/
chown -R orac11:dba /oracle
Unzip the compressed files into “your” Software directory and execute the install process under the directory SAP.
su – orac11
cd /Software/Oracle_19c_Inst/LINUX_X86_64/db_home/SAP
export DB_SID=C11
export ORACLE_STAGE=/oracle/stage
export ORACLE_BASE=/oracle/C11
Call the Oracle installer for 19c
./19cinstall.sh -silent -db C11 -oracle_stage /oracle/C11/Software/Oracle_19c_Inst/LINUX_X86_64/db_home/
As a root user, execute the following script(s):
- 1. /oracle/oraInventory/orainstRoot.sh
- 2. /oracle/C11/19.0.0/root.sh
[root@ralforavm01 SAP]# /oracle/oraInventory/orainstRoot.sh
[root@ralforavm01 SAP]# /oracle/C11/19.0.0/root.sh
Test connect to Oracle
su – orac11
sqlplus /nolog
SQL> CONNECT / SYS AS SYSDBA
SQL*Plus: Release 19.0.0.0.0 - Production on Wed Nov 4 11:51:28 2020
Version 19.3.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Connected to an idle instance.
SQL> exit
Patch Installation
Install the OPatch utility first.
https://updates.oracle.com/ARULink/PatchDetails/process_form?patch_num=6880880
or download it from SAP swdc à databases Oracle19c
chmod 777 OPATCH19P_2008-70004508.ZIP
su – orac11
/oracle/C11/19.0.0/OPatch/opatch version
OPatch Version: 12.2.0.1.17
OPatch succeeded.
cd /oracle/C11/19.0.0/
unzip /Software/OPATCH19P_2008-70004508.ZIP
/oracle/C11/19.0.0/OPatch/opatch version
========================================================
GENERIC OPATCH VERSION - FOR USE IN SAP ENVIRONMENT ONLY
========================================================
OPatch Version: 12.2.0.1.21
OPatch succeeded.
Validate the Oracle Inventory
/oracle/C11/19.0.0/OPatch/opatch lsinventory -detail -oh /oracle/C11/19.0.0
…..
...
OPatch succeeded.
Apply the OPatch 19.8.0.0 to the DB
Apply the patches
cd /Software/Oracle_Patch_19.8/31305339/31281355
/oracle/C11/19.0.0/OPatch/opatch apply
========================================================
GENERIC OPATCH VERSION - FOR USE IN SAP ENVIRONMENT ONLY
========================================================
Oracle Interim Patch Installer version 12.2.0.1.21
Copyright (c) 2020, Oracle Corporation. All rights reserved.
Oracle Home : /oracle/C11/19.0.0
Central Inventory : /oracle/oraInventory
from : /oracle/C11/19.0.0/oraInst.loc
OPatch version : 12.2.0.1.21 FOR USE IN SAP ENVIRONMENT ONLY
OUI version : 12.2.0.7.0
Log file location : /oracle/C11/19.0.0/cfgtoollogs/opatch/opatch2020-11-04_16-10-50PM_1.log
Verifying environment and performing prerequisite checks...
OPatch continues with these patches: 31281355
Do you want to proceed? [y|n] Y
...
..
cd ../31304218
/oracle/C11/19.0.0/OPatch/opatch apply
cd ../31305087
/oracle/C11/19.0.0/OPatch/opatch apply
cd ../31335188
/oracle/C11/19.0.0/OPatch/opatch apply
cd /oracle/C11/19/OPatch/
datapatch -verbose
Any databases that have invalid objects after the execution of datapatch should have utlrp.sql run to revalidate those objects.
For example:
cd $ORACLE_HOME/rdbms/admin
sqlplus /nolog
SQL> CONNECT / AS SYSDBA
SQL> @utlrp.sql
Apply the SAP Bundle Patch SAP19P_2008-70004508.ZIP (also downloaded from SWDC
dnf install bc.x86_64
cd /Software/SAP19P/SBP_19800200714_202008
ls -l /oracle/C11/19/MOpatch
ls: cannot access '/oracle/C11/19/MOpatch': No such file or directory
cp -r MOPatch /oracle/C11/19/
$ORACLE_HOME/MOPatch/mopatch.sh -hv
MOPatch - Install Multiple Oracle Patches in One Run - 2.5.1.
Copyright (c) 2007, 2020, Oracle and/or its affiliates. All rights reserved.
cd /Software/SAP19P
ls -l
-rw-r--r--. 1 root root 14532539 Nov 4 15:52 SAP19P_2008-70004508.ZIP
drwxr-xr-x. 24 oracle oinstall 4096 Aug 18 17:02 SBP_19800200714_202008
-rw-r--r--. 1 oracle oinstall 76390 Aug 21 15:21 SIGNATURE.SMF
export IHRDBMS=/oracle/C11/19.0.0
env |grep ORA
ORACLE_UNQNAME=C11
ORACLE_SID=C11
ORACLE_BASE=/oracle/C11
ORACLE_HOME=/oracle/C11/19.0.0
ORA_INVENTORY=/oracle/oraInventory
ORACLE_HOSTNAME=ralforavm01.localdomain
$IHRDBMS/MOPatch/mopatch.sh -v -s SAP19P_2008-70004508.ZIP
Create a Database
https://docs.oracle.com/cd/B28359_01/server.111/b28310/create003.htm#ADMIN11073
vi /oracle/C11/19.0.0/dbs/initC11.ora
db_name='C11'
memory_target=1G
processes = 150
db_block_size=8192
open_cursors=300
compatible ='11.2.0'
sqlplus /nolog
SQL*Plus: Release 19.0.0.0.0 - Production on Thu Nov 5 14:57:34 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2020, Oracle. All rights reserved.
SQL> connect / as sysdba
Connected to an idle instance.
SQL> CREATE SPFILE FROM PFILE;
File created.
SQL> startup nomount
ORACLE instance started.
Total System Global Area 713031464 bytes
Fixed Size 8900392 bytes
Variable Size 557842432 bytes
Database Buffers 134217728 bytes
Redo Buffers 12070912 bytes
SQL>
Create C11 Database (only for a Test! The DB will get created during the SAP installation)
vi create_db.sql
CREATE DATABASE C11
USER SYS IDENTIFIED BY manager
USER SYSTEM IDENTIFIED BY manager
LOGFILE GROUP 1 ('/oracle/C11/origlogA/redo01.log') SIZE 100M,
GROUP 2 ('/oracle/C11/origlogB/redo02.log') SIZE 100M,
GROUP 3 ('/oracle/C11/origlogA/redo03.log') SIZE 100M,
GROUP 4 ('/oracle/C11/origlogB/redo04.log') SIZE 100M
MAXLOGFILES 5
MAXLOGMEMBERS 5
MAXLOGHISTORY 1
MAXDATAFILES 100
CHARACTER SET US7ASCII
NATIONAL CHARACTER SET AL16UTF16
EXTENT MANAGEMENT LOCAL
DATAFILE '/oracle/C11/sapdata1/system01.dbf' SIZE 500M REUSE
SYSAUX DATAFILE '/oracle/C11/sapdata2/sysaux01.dbf' SIZE 325M REUSE
DEFAULT TABLESPACE users
DATAFILE '/oracle/C11/sapdata3/users01.dbf'
SIZE 500M REUSE AUTOEXTEND ON MAXSIZE UNLIMITED
DEFAULT TEMPORARY TABLESPACE tempts1
TEMPFILE '/oracle/C11/sapdata1/temp01.dbf'
SIZE 20M REUSE
UNDO TABLESPACE undotbs
DATAFILE '/oracle/C11/sapdata4/undotbs01.dbf'
SIZE 200M REUSE AUTOEXTEND ON MAXSIZE UNLIMITED;
Create the DB
SQL> @create_db.sql
Database created.
Run the required post processing scripts
SQL> @$ORACLE_HOME/rdbms/admin/catalog.sql;
SQL> @$ORACLE_HOME/rdbms/admin/catproc.sql;
SQL> @$ORACLE_HOME/sqlplus/admin/pupbld.sql;
Test if the DB is open
SQL> select status from v$instance;
STATUS
------------
OPEN
1 row selected.
DROP DATABASE:
SQL> shutdown abort
SQL> startup force mount restrict;
ORACLE instance started.
Total System Global Area 243268208 bytes
Fixed Size 8895088 bytes
Variable Size 180355072 bytes
Database Buffers 50331648 bytes
Redo Buffers 3686400 bytes
Database mounted.
SQL> drop database;
Database dropped.
Enable dNFS
To use Oracle dNFS MultiPath with Azure NetApp Files you will need an oranfstab file, Oracle will look in the following order and locations for the configuration file.
- /etc/oranfstab – Server wide
- $ORACLE_HOME/dbs/oranfstab – Oracle Home specific
You need to specify ONLY those volumes in the oranfstab which are used by Oracle. If you specify not used volumes this construct will end up in an non working dNFS scenario. Theoretically oracle should look into the /etc/mtab to automatically enable dNFS volumes.
Below is a copy of my $ORACLE_HOME/dbs/oranfstab
cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
172.17.4.9 ralforavm01.localdomain ralforavm01
172.17.5.4 anf01
dNFS oranfstab for NFSv4.1
[root@ralforavm01 dbs]# cat oranfstab
server: anf01
path: 172.17.10.4
nfs_version: NFSv4.1
security_default: sys
export: /ralforacledatav4/sapdata1 mount: /oracle/C11/sapdata1
export: /ralforacledatav4/sapdata2 mount: /oracle/C11/sapdata2
export: /ralforacledatav4/sapdata3 mount: /oracle/C11/sapdata3
export: /ralforacledatav4/sapdata4 mount: /oracle/C11/sapdata4
export: /ralforacleoriglog/origlogA mount: /oracle/C11/origlogA
export: /ralforacleoriglog/origlogB mount: /oracle/C11/origlogB
export: /ralforacleshared mount: /oracle/C11/19.0.0
export: /ralforaoraarch mount: /oracle/C11/oraarch
export: /ralforasapbackup mount: /oracle/C11/sapbackup
Enabling dNFS
Change dir to $ORACLE_HOME/rdbms/lib and use the make command e.g
cd $ORACLE_HOME/rdbms/lib
make -f ins_rdbms.mk dnfs_on
rm -f /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so;
cp /oracle/C11/19.0.0/lib/libnfsodm19.so /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so
restart oracle
Verify Oracle dNFS Usage
If dNFS is enabled correctly there should be no errors in the alert files. Here we see dNFS issues in the trace directory:
pwd
/oracle/C11/diag/rdbms/c11/C11/trace
The output here shows dNFS issues…. If everything is configured correctly there should be no output.
grep -i kgnfs *.trc
....
…
C11_lgwr_99210.trc: [53257270973] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257271002] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257271026] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_lgwr_99210.trc: [53257283545] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257283571] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257283595] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_lgwr_99210.trc: [53257296302] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257296328] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257296359] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_ora_99256.trc:[53257072683] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257072983] kgnfs_dump_hex_data: 0x7ffd811d920c len 120 lt 30
C11_ora_99256.trc: [53257073007] kgnfs_dump_hex_data: 0x7ffd811db638 len 528 lt 132
C11_ora_99256.trc: [53257102434] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257102459] kgnfs_dump_hex_data: 0x7ffd811d920c len 120 lt 30
C11_ora_99256.trc: [53257102485] kgnfs_dump_hex_data: 0x7ffd811db638 len 528 lt 132
C11_ora_99256.trc:[53257522107] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257522142] kgnfs_dump_hex_data: 0x7ffd811e39ec len 120 lt 30
C11_ora_99256.trc: [53257522167] kgnfs_dump_hex_data: 0x7ffd811e5e18 len 528 lt 132
In this example dNFS is not enabled correctly.
On NFSv4.1
col SVRNAME format a10
col DIRNAME format a40
col NFSVERSION format a10
col SECURITY format a10
SQL> select SVRNAME,DIRNAME,NFSVERSION,SECURITY from v$dnfs_servers;
SVRNAME DIRNAME NFSVERSION SECURITY
---------- ---------------------------------------- ---------- ----------
anf01 /ralforacleshared NFSv4.1 sys
anf01 /ralforacledatav4/sapdata1 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata2 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata4 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata3 NFSv4.1 sys
anf01 /ralforacleoriglog/origlogB NFSv4.1 sys
anf01 /ralforacleoriglog/origlogA NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
8 rows selected.
After switching the redo-logfile also the oraarch should appear
SQL> alter system switch logfile;
System altered.
SQL> select SVRNAME,DIRNAME,NFSVERSION,SECURITY from v$dnfs_servers;
SVRNAME DIRNAME NFSVERSION SECURITY
---------- ---------------------------------------- ---------- ----------
anf01 /ralforacleshared NFSv4.1 sys
anf01 /ralforacledatav4/sapdata1 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata2 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata4 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata3 NFSv4.1 sys
anf01 /ralforacleoriglog/origlogB NFSv4.1 sys
anf01 /ralforacleoriglog/origlogA NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
9 rows selected.
Disable dNFS
For test reasons it can be necessary to disable the dNFS cleint.
Change dir to $ORACLE_HOME/rdbms/lib and use the make command e.g
cd $ORACLE_HOME/rdbms/lib
make -f ins_rdbms.mk dnfs_off
rm -f /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so
restart oracle
Performance Test
Before we start the performance testing we configure the system accordingly.
Reference: I/O Configuration and Design (oracle.com)
DB_FILE_MULTIBLOCK_READ_COUNT parameter is used to specifies the maximum number of blocks read in one I/O operation during a sequential scan.
SQL> show parameter DB_FILE_MULTIBLOCK_READ_COUNT
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_file_multiblock_read_count integer 128
SQL> alter system set DB_FILE_MULTIBLOCK_READ_COUNT=256 scope=both;
Setting the dNFS_BATCH_SIZE parameter to 128 (restart of the DB is required to activate)
SQL> alter system set DNFS_BATCH_SIZE=128 scope=spfile;
SQL> shutdown
SQL> startup
SQL> show parameter DNFS_BATCH_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
dnfs_batch_size integer 128
For now we keep the default for:
SORT_AREA_SIZE
|
Determines I/O sizes and concurrency for sort operations.
|
HASH_AREA_SIZE
|
Determines the I/O size for hash operations.
|
SQL> show parameter SORT_AREA_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
sort_area_size integer 65536
SQL> show parameter HASH_AREA_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
hash_area_size integer 131072
Running I/O Calibration
The I/O calibration feature of Oracle Database is accessed using the DBMS_RESOURCE_MANAGER.CALIBRATE_IO procedure. This procedure issues an I/O intensive read-only workload, made up of one megabyte of random of I/Os, to the database files to determine the maximum IOPS (I/O requests per second) and MBPS (megabytes of I/O per second) that can be sustained by the storage subsystem.
Preparation:
SQL> show parameter TIMED_STATISTICS
NAME TYPE VALUE
----------------------------------- ----------- ------------------------------
timed_statistics boolean TRUE
SQL> show parameter STATISTICS_LEVEL
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
client_statistics_level string TYPICAL
statistics_level string TYPICAL
Data Volume = 4*2TB Ultra = 4*256MB/s
NFSv4.1 dNFS disabled:
SQL> SET SERVEROUTPUT ON
DECLARE
lat INTEGER;
iops INTEGER;
mbps INTEGER;
BEGIN
-- DBMS_RESOURCE_MANAGER.CALIBRATE_IO (<DISKS>, <MAX_LATENCY>, iops, mbps, lat);
DBMS_RESOURCE_MANAGER.CALIBRATE_IO (2, 10, iops, mbps, lat);
DBMS_OUTPUT.PUT_LINE ('max_iops = ' || iops);
DBMS_OUTPUT.PUT_LINE ('latency = ' || lat);
DBMS_OUTPUT.PUT_LINE ('max_mbps = ' || mbps);
end;
/
max_iops = 38049
latency = 1.208
max_mbps = 297
max_iops = 38049
latency = 1
max_mbps = 297
PL/SQL procedure successfully completed.
Data Volume = 4*2TB Ultra = 4*256MB/s
NFSv4.1 dNFS enabled:
SQL> SET SERVEROUTPUT ON
DECLARE
lat INTEGER;
iops INTEGER;
mbps INTEGER;
BEGIN
-- DBMS_RESOURCE_MANAGER.CALIBRATE_IO (<DISKS>, <MAX_LATENCY>, iops, mbps, lat);
DBMS_RESOURCE_MANAGER.CALIBRATE_IO (2, 10, iops, mbps, lat);
DBMS_OUTPUT.PUT_LINE ('max_iops = ' || iops);
DBMS_OUTPUT.PUT_LINE ('latency = ' || lat);
DBMS_OUTPUT.PUT_LINE ('max_mbps = ' || mbps);
end;
/
max_iops = 38083
latency = .497
max_mbps = 296
max_iops = 38083
latency = 0
max_mbps = 296
PL/SQL procedure successfully completed.
Set the tablespaces to async_io
SQL> col name format a50
SELECT name, asynch_io FROM v$datafile f,v$iostat_file i
WHERE f.file# = i.file_no
AND filetype_name = 'Data File'
NAME ASYNCH_IO
-------------------------------------------------- ---------
/oracle/C11/sapdata1/system01.dbf ASYNC_OFF
/oracle/C11/sapdata2/sysaux01.dbf ASYNC_OFF
/oracle/C11/sapdata4/undotbs01.dbf ASYNC_OFF
/oracle/C11/sapdata3/users01.dbf ASYNC_OFF
SQL> SHOW PARAMETER FILESYSTEMIO_OPTIONS
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
filesystemio_options string none
SQL> ALTER SYSTEM SET FILESYSTEMIO_OPTIONS=SETALL SCOPE=SPFILE;
SQL> shutdown
SQL> startup
SQL> SHOW PARAMETER FILESYSTEMIO_OPTIONS
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
filesystemio_options string SETALL
SQL> col name format a50
SELECT name, asynch_io FROM v$datafile f,v$iostat_file i
WHERE f.file# = i.file_no
AND filetype_name = 'Data File'
NAME ASYNCH_IO
-------------------------------------------------- ---------
/oracle/C11/sapdata1/system01.dbf ASYNC_ON
/oracle/C11/sapdata2/sysaux01.dbf ASYNC_ON
/oracle/C11/sapdata4/undotbs01.dbf ASYNC_ON
/oracle/C11/sapdata3/users01.dbf ASYNC_ON
Preparing the Orion Performance check tool
1 ANF Data-Volume 6TB with Ultra = 768MB/s troughput
Creating the orion files for the test
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata1/orion1 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7701 s, 821 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata2/orion2 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.744 s, 823 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata3/orion3 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7365 s, 823 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata4/orion4 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7354 s, 823 MB/s
Preparing the orion “lun” declaration file
vi orion_nfs.lun
/oracle/C11/sapdata1/orion1
/oracle/C11/sapdata2/orion2
/oracle/C11/sapdata3/orion3
/oracle/C11/sapdata4/orion4
Run the test (NFSv4.1)
~/19.0.0/bin/orion -run oltp -testname orion_nfs -hugenotneeded
ORION: ORacle IO Numbers -- Version RDBMS_19.3.0.0.0DBRU_LINUX.X64_190417
orion_nfs_20201125_1351
Calibration will take approximately 25 minutes.
[orac11@ralforavm01 ~]$ ~/19.0.0/bin/orion -run normal -testname orion_nfs -hugenotneeded
ORION: ORacle IO Numbers -- Version RDBMS_19.3.0.0.0DBRU_LINUX.X64_190417
orion_nfs_20201125_1425
Calibration will take approximately 190 minutes.
Using a large value for -cache_size may take longer.
Setting ftype=0
Maximum Large MBPS=771.28 @ Small=5 and Large=8
Maximum Small IOPS=34449 @ Small=19 and Large=0
Small Read Latency: avg=550.983 us, min=322.815 us, max=11369.239 us, std dev=134.209 us @ Small=19 and Large=0
Minimum Small Latency=419.288 usecs @ Small=1 and Large=0
Small Read Latency: avg=419.288 us, min=311.915 us, max=43826.080 us, std dev=153.365 us @ Small=1 and Large=0
Small Read / Write Latency Histogram @ Small=1 and Large=0
Latency: # of IOs (read) # of IOs (write)
0 - 256 us: 0 ( 0.00%) 0 ( 0.00%)
256 - 512 us: 138100 ( 96.71%) 0 ( 0.00%)
512 - 1024 us: 4268 ( 99.70%) 0 ( 0.00%)
1024 - 2048 us: 366 ( 99.95%) 0 ( 0.00%)
2048 - 4096 us: 52 ( 99.99%) 0 ( 0.00%)
4096 - 8192 us: 9 (100.00%) 0 ( 0.00%)
8192 - 16384 us: 3 (100.00%) 0 ( 0.00%)
16384 - 32768 us: 0 (100.00%) 0 ( 0.00%)
32768 - 65536 us: 1 (100.00%) 0 ( 0.00%)
65536 - 268435456 us: 0 (100.00%) 0 ( 0.00%)
Configuration of the Listener
Create the tnsnames.ora file
pwd
/oracle/C11/19/network/admin
vi tnsnames.ora
C11 =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = 172.17.4.9)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = C11)
)
)
Start the listener
[orac11@ralforavm01 admin]$ lsnrctl start
LSNRCTL for Linux: Version 19.0.0.0.0 - Production on 01-DEC-2020 14:07:00
Copyright (c) 1991, 2020, Oracle. All rights reserved.
Starting /oracle/C11/19.0.0/bin/tnslsnr: please wait...
TNSLSNR for Linux: Version 19.0.0.0.0 - Production
Log messages written to /oracle/C11/diag/tnslsnr/ralforavm01/listener/alert/log.xml
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=ralforavm01.localdomain)(PORT=1521)))
Connecting to (ADDRESS=(PROTOCOL=tcp)(HOST=)(PORT=1521))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for Linux: Version 19.0.0.0.0 - Production
Start Date 01-DEC-2020 14:07:01
Uptime 0 days 0 hr. 0 min. 0 sec
Trace Level off
Security ON: Local OS Authentication
SNMP OFF
Listener Log File /oracle/C11/diag/tnslsnr/ralforavm01/listener/alert/log.xml
Listening Endpoints Summary...
(DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=ralforavm01.localdomain)(PORT=1521)))
The listener supports no services
The command completed successfully
RMAN Configuration
Check the DB logmode:
SQL> select log_mode from v$database;
LOG_MODE
------------
NOARCHIVELOG
Configure database in ARCHIVELOG mode.
SQL> shutdown
Database closed.
Database dismounted.
ORACLE instance shut down.
SQL> startup mount;
ORACLE instance started.
Total System Global Area 1073737800 bytes
Fixed Size 8904776 bytes
Variable Size 864026624 bytes
Database Buffers 188743680 bytes
Redo Buffers 12062720 bytes
Database mounted.
SQL> alter database archivelog;
Database altered.
SQL> alter database open;
Database altered.
Ensure ARCHIVELOG destination.
SQL> select open_mode from v$database;
OPEN_MODE
--------------------
READ WRITE
SQL> archive log list
Database log mode Archive Mode
Automatic archival Enabled
Archive destination /oracle/C11/19.0.0/dbs/arch
Oldest online log sequence 30
Next log sequence to archive 33
Current log sequence 33
Change the oracle archive destination.
SQL> alter system set log_archive_dest_1='location=/oracle/C11/oraarch' scope=both;
SQL> archive log list
Database log mode Archive Mode
Automatic archival Enabled
Archive destination /oracle/C11/oraarch
Oldest online log sequence 30
Next log sequence to archive 33
Current log sequence 33
Ensure the flash/fast recovery area location.
SQL> show parameter db_recovery_file_dest
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_recovery_file_dest string
db_recovery_file_dest_size big integer 0
Connect to RMAN prompt with target database.
[orac11@ralforavm01 ~]$ rman target /
Recovery Manager: Release 19.0.0.0.0 - Production on Mon Nov 30 16:47:40 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
RMAN>
Configure RMAN with control file auto-backup feature that will be auto-backup control file in case of major changes done in database.
RMAN> configure controlfile autobackup on;
using target database control file instead of recovery catalog
new RMAN configuration parameters:
CONFIGURE CONTROLFILE AUTOBACKUP ON;
new RMAN configuration parameters are successfully stored
Enable the optimization
RMAN> configure backup optimization on;
new RMAN configuration parameters:
CONFIGURE BACKUP OPTIMIZATION ON;
new RMAN configuration parameters are successfully stored
Configure the retention policy
RMAN> CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters are successfully stored
Connect to the recovery catalog database (RMAN Repository) & Create a tablespace to store RMAN catalog database objects.
SQL> show parameter db_recovery_file_dest
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_recovery_file_dest string
db_recovery_file_dest_size big integer 0
SQL> select global_name from global_name;
GLOBAL_NAME
--------------------------------------------------------------------------------
C11
Create a tablespace to be used for RMAN and the temp tablespace
SQL> create tablespace catalogtbs datafile '/oracle/C11/sapdata1/catalogtbs1.dbf' size 100M autoextend on maxsize unlimited;
SQL> create tablespace temporary tablespace temp_01 tempfile '/oracle/C11/sapdata1/temp_01.dbf' size 5M autoextend ON;
Create a RMAN user, assign RMAN tablespace to RMAN user as a default & grant recovery catalog owner,connect & resource privileges to RMAN user.
SQL> create user recoveryman identified by recoveryman;
SQL> alter user recoveryman default tablespace catalogtbs temporary tablespace temp_01 ;
SQL> grant recovery_catalog_owner to recoveryman;
SQL> grant connect,resource to recoveryman;
alter user recoveryman DEFAULT TABLESPACE catalogtbs quota unlimited on catalogtbs;
Connect to RMAN on target and recovery catalog database.
rman target / catalog recoveryman/recoveryman@C11
Recovery Manager: Release 19.0.0.0.0 - Production on Tue Dec 1 14:13:27 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
connected to recovery catalog database
RMAN>
create catalog by issuing the following command in RMAN prompt and register the DB
RMAN> create catalog;
recovery catalog created
RMAN> register database;
database registered in recovery catalog
starting full resync of recovery catalog
full resync complete
Check whether registration was successful.
RMAN> report schema;
Report of database schema for database with db_unique_name C11
List of Permanent Datafiles
===========================
File Size(MB) Tablespace RB segs Datafile Name
---- -------- -------------------- ------- ------------------------
1 500 SYSTEM YES /oracle/C11/sapdata1/system01.dbf
2 325 SYSAUX NO /oracle/C11/sapdata2/sysaux01.dbf
3 305 UNDOTBS YES /oracle/C11/sapdata4/undotbs01.dbf
4 500 USERS NO /oracle/C11/sapdata3/users01.dbf
5 100 CATALOGTBS NO /oracle/C11/sapdata1/catalogtbs1.dbf
List of Temporary Files
=======================
File Size(MB) Tablespace Maxsize(MB) Tempfile Name
---- -------- -------------------- ----------- --------------------
1 20 TEMPTS1 20 /oracle/C11/sapdata1/temp01.dbf
2 5 TEMP_01 32767 /oracle/C11/sapdata1/temp_01.dbf
Or
RMAN> LIST INCARNATION OF DATABASE;
List of Database Incarnations
DB Key Inc Key DB Name DB ID STATUS Reset SCN Reset Time
------ ------- -------- ---------------- --- ---------- ----------
1 2 C11 365226479 CURRENT 1 23-NOV-20
Creating a system backup
[orac11@ralforavm01 ~]$ ls -l /oracle/C11/sapbackup/
total 0
Starting an RMAN session and configure the backup path.
rman target / catalog recoveryman/recoveryman@C11
Recovery Manager: Release 19.0.0.0.0 - Production on Tue Dec 1 14:42:22 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
connected to recovery catalog database
RMAN> CONFIGURE CHANNEL DEVICE TYPE DISK FORMAT '/oracle/C11/sapbackup/full_%u_%s_%p';
new RMAN configuration parameters:
CONFIGURE CHANNEL DEVICE TYPE DISK FORMAT '/oracle/C11/sapbackup/full_%u_%s_%p';
new RMAN configuration parameters are successfully stored
starting full resync of recovery catalog
full resync complete
Next, you should specify how long you want to retain the backup for. When RMAN takes a backup, it automatically deletes all the old backups that are older than the retention period. In the following example, I’m setting the retention period as 7 days, which will keep the DB backup for a week.
RMAN> CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
old RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters are successfully stored
starting full resync of recovery catalog
full resync complete
Typically we’ll use “BACKUP AS BACKUPSET” to backup a database. So, to take a full backup of the database without the archive logs, do the following.
RMAN> BACKUP AS BACKUPSET DATABASE
To take a full backup of the database with the archive logs, do the following:
RMAN> BACKUP AS BACKUPSET DATABASE PLUS ARCHIVELOG;
You can also take a backup of only a specific table space. The following example takes backup of only PRD01 tablespace.
RMAN> BACKUP AS BACKUPSET TABLESPACE PRD01;
Example output:
RMAN> BACKUP AS BACKUPSET DATABASE PLUS ARCHIVELOG;
Starting backup at 01-DEC-20
current log archived
allocated channel: ORA_DISK_1
channel ORA_DISK_1: SID=44 device type=DISK
channel ORA_DISK_1: starting archived log backup set
channel ORA_DISK_1: specifying archived log(s) in backup set
input archived log thread=1 sequence=33 RECID=1 STAMP=1057971633
input archived log thread=1 sequence=34 RECID=2 STAMP=1058020317
input archived log thread=1 sequence=35 RECID=3 STAMP=1058021321
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_02vh07ub_2_1 tag=TAG20201201T144843 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:03
Finished backup at 01-DEC-20
Starting backup at 01-DEC-20
using channel ORA_DISK_1
channel ORA_DISK_1: starting full datafile backup set
channel ORA_DISK_1: specifying datafile(s) in backup set
input datafile file number=00001 name=/oracle/C11/sapdata1/system01.dbf
input datafile file number=00004 name=/oracle/C11/sapdata3/users01.dbf
input datafile file number=00002 name=/oracle/C11/sapdata2/sysaux01.dbf
input datafile file number=00003 name=/oracle/C11/sapdata4/undotbs01.dbf
input datafile file number=00005 name=/oracle/C11/sapdata1/catalogtbs1.dbf
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_03vh07ug_3_1 tag=TAG20201201T144846 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:07
Finished backup at 01-DEC-20
Starting backup at 01-DEC-20
current log archived
using channel ORA_DISK_1
channel ORA_DISK_1: starting archived log backup set
channel ORA_DISK_1: specifying archived log(s) in backup set
input archived log thread=1 sequence=36 RECID=4 STAMP=1058021335
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_04vh07uo_4_1 tag=TAG20201201T144856 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:01
Finished backup at 01-DEC-20
Starting Control File and SPFILE Autobackup at 01-DEC-20
piece handle=/oracle/C11/19.0.0/dbs/c-365226479-20201201-00 comment=NONE
Finished Control File and SPFILE Autobackup at 01-DEC-20
RMAN>
Check the backup location:
[orac11@ralforavm01 admin]$ ls -l /oracle/C11/sapbackup/
total 782612
-rw-r----- 1 orac11 dba 169256448 Dec 1 14:48 full_02vh07ub_2_1
-rw-r----- 1 orac11 dba 628776960 Dec 1 14:48 full_03vh07ug_3_1
-rw-r----- 1 orac11 dba 204800 Dec 1 14:48 full_04vh07uo_4_1
References
Microsoft
Solution architectures using Azure NetApp Files – Oracle
Solution architectures using Azure NetApp Files – SAP on Azure
SAP deployment on Azure using an Oracle DB – Azure Architecture Center | Microsoft Docs
Oracle:
https://oracle-base.com/articles/19c/oracle-db-19c-installation-on-oracle-linux-8
https://docs.oracle.com/en/database/oracle/oracle-database/19/ladbi/supported-oracle-linux-8-distributions-for-x86-64.html#GUID-F4902762-325B-4C89-B85B-F52BA482190F
SAP
2015553 – SAP on Microsoft Azure: Support prerequisites – SAP ONE Support Launchpad
2039619 – SAP Applications on Microsoft Azure using the Oracle Database: Supported Products and Versions – SAP ONE Support Launchpad
NetApp
Oracle Databases on Microsoft Azure Using Azure NetApp Files | TR-4780 | NetApp
TR-3633: Oracle Databases on NetApp ONTAP | NetApp

by Contributed | Jan 18, 2021 | Technology
This article is contributed. See the original author and article here.
Oracle 19c on Azure NetApp Files for SAP Workloads
PoC and Validation
Oracle Installation Guide
Introduction
This document will show how you can install Oracle 19c on Azure for SAP Applications using Azure NetApp Files (ANF) as storage platform for data and log areas. The support is mentioned in the two SAP notes:
2015553 – SAP on Microsoft Azure: Support prerequisites – SAP ONE Support Launchpad
2039619 – SAP Applications on Microsoft Azure using the Oracle Database: Supported Products and Versions – SAP ONE Support Launchpad
This document written for experienced technical people. Not all aspects are covered because we assume a profound technical knowledge on all the mentioned topics like Linux, Oracle DB and NFS.
The supported components are: Oracle Linux 8.2, Oracle 19c and NFS 4.1 on ANF
Thank you from the awesome support to:
Jan Klokkers Oracle
Christoph Kurucz Oracle
Geert van Teylingen Azure NetApp Files alliance
Jeffrey Steiner NetApp
Juergen Thomas Microsoft
Installation
Create a resource Group.


Create the VM









Creating the Jump Box


Oracle Linux
Check the Kernel version
uname -a
Linux ralforavm01 5.4.17-2011.6.2.el8uek.x86_64 #2 SMP Thu Sep 3 13:38:27 PDT 2020 x86_64 x86_64 x86_64 GNU/Linux
Check the OS Release
cat /etc/os-release
NAME="Oracle Linux Server"
VERSION="8.2"
ID="ol"
ID_LIKE="fedora"
VARIANT="Server"
VARIANT_ID="server"
VERSION_ID="8.2"
PLATFORM_ID="platform:el8"
PRETTY_NAME="Oracle Linux Server 8.2"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:oracle:linux:8:2:server"
HOME_URL="https://linux.oracle.com/"
BUG_REPORT_URL="https://bugzilla.oracle.com/"
List the number and type of CPU’S of the VM
lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
CPU(s): 32
On-line CPU(s) list: 0-31
Thread(s) per core: 2
Core(s) per socket: 16
Socket(s): 1
NUMA node(s): 1
Vendor ID: GenuineIntel
CPU family: 6
Model: 63
Model name: Intel(R) Xeon(R) CPU E7-8890 v3 @ 2.50GHz
Stepping: 4
CPU MHz: 2493.986
BogoMIPS: 4987.97
Virtualization: VT-x
Hypervisor vendor: Microsoft
Virtualization type: full
L1d cache: 32K
L1i cache: 32K
L2 cache: 256K
L3 cache: 46080K
NUMA node0 CPU(s): 0-31
Create a storage Account

Create a capacity Pool

Add a capacity Pool

Depending on the database size and expected performance decide which ANF SKU does fit best for the target database. In our case it is Ultra.

Finished

Volume design

Create the delegated subnet for ANF

Create a Capacity Pool

Select the protocol for the volumes

Add a Capacity Pool
After deploying the above mentioned design it looks like this:

Configure the /etc/hosts
vi /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
172.17.4.9 ralforavm01.localdomain ralforavm01
172.17.10.4 anf01
Configure the hostname as FQDN
vi /etc/hostname
ralforavm01.localdomain
Create the mountpoints for Oracle and SAP
mkdir -p /oracle/C11/sapdata1 /oracle/C11/sapdata2 /oracle/C11/sapdata3 /oracle/C11/sapdata4 /oracle/C11/origlogA /oracle/C11/origlogB /oracle/C11/mirrlogA /oracle/C11/mirrlogB /oracle/C11/saparch /oracle/C11/sapbackup /oracle/C11/sapreorg /oracle/C11/orainstall /oracle/C11/saptrace /oracle/C11/oraarch /oracle/C11/19.0.0 /oracle/stage /oracle/client
mkdir -p /usr/sap/C11 /sapmnt/C11 /usr/sap/trans
mount the root volume and create the mountpoints.
mount anf01:/ralforasapdatav3 /mnt
mkdir /mnt/sapdata1 /mnt/sapdata2 /mnt/sapdata3 /mnt/sapdata4 ; umount /mnt
mount anf01:/ralforaclemirrlog /mnt
mkdir /mnt/mirrlogA /mnt/mirrlogB; umount /mnt
mount anf01:/ralforacleoriglog /mnt
mkdir /mnt/origlogA /mnt/origlogB; umount /mnt
mount anf01:/ralforacleshared /mnt
mkdir /mnt/oraarch /mnt/saparch /mnt/sapbackup /mnt/sapreorg /mnt/saptrace /mnt/Software /mnt/usr_sap /mnt/sapmnt /mnt/19.0.0 /mnt/trans /mnt/ora_client /mnt/orainstall /mnt/ora_stage ;umount /mnt
Manage the idmapd for ANF
vi /etc/idmapd.conf
# Example
[General]
Domain = defaultv4iddomain.com
modify the /etc/fstab
#
# Oracle
#
anf01:/ralforacledatav4/sapdata1 /oracle/C11/sapdata1 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata2 /oracle/C11/sapdata2 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata3 /oracle/C11/sapdata3 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacledatav4/sapdata4 /oracle/C11/sapdata4 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforaclemirrlog/mirrlogA /oracle/C11/mirrlogA nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforaclemirrlog/mirrlogB /oracle/C11/mirrlogB nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
##
anf01:/ralforacleoriglog/origlogA /oracle/C11/origlogA nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleoriglog/origlogB /oracle/C11/origlogB nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
##
anf01:/ralforacleshared/19.0.0 /oracle/C11/19.0.0 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/oraarch /oracle/C11/oraarch nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/saparch /oracle/C11/saparch nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapbackup /oracle/C11/sapbackup nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapreorg /oracle/C11/sapreorg nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/saptrace /oracle/C11/saptrace nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/Software /oracle/C11/Software nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/ora_client /oracle/client nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/ora_stage /oracle/stage nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/usr_sap /usr/sap/C11 nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/trans /usr/sap/trans nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/sapmnt /sapmnt nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
anf01:/ralforacleshared/orainst /oracle/C11/orainstall nfs rw,hard,timeo=600,vers=4.1,rsize=1048576,wsize=1048576,noatime,nointr,lock 0 0
Stop the firewalld
systemctl disable firewalld
systemctl stop firewalld
Update the VM’s OS image (no registration required)
yum update
Last metadata expiration check: 1:24:42 ago on Tue 03 Nov 2020 10:04:53 AM UTC.
…
Install 5 Packages
Upgrade 25 Packages
Total download size: 159 M
Is this ok [y/N]:y
Install the required libraries.
dnf install -y oracle-database-preinstall-19c
dnf install -y binutils
dnf install -y compat-libstdc++-33
dnf install -y elfutils-libelf
dnf install -y elfutils-libelf-devel
dnf install -y fontconfig-devel
dnf install -y glibc
dnf install -y glibc-devel
dnf install -y ksh
dnf install -y libaio
dnf install -y libaio-devel
dnf install -y libXrender
dnf install -y libXrender-devel
dnf install -y libX11
dnf install -y libXau
dnf install -y libXi
dnf install -y libXtst
dnf install -y libgcc
dnf install -y librdmacm-devel
dnf install -y libstdc++
dnf install -y libstdc++-devel
dnf install -y libxcbdnf install -y unixODBC
# New for OL8
dnf install -y ipmiutil
dnf install -y libnsl2
dnf install -y libnsl2-devel
dnf install -y net-tools
dnf install -y nfs-utils
dnf install -y libnsl
dnf install -y make
dnf install -y python # ACFS
dnf install -y python-configshell # ACFS
dnf install -y python-rtslib # ACFS
dnf install -y python-six # ACFS
dnf install -y targetcli # ACFS
dnf install -y smartmontools
dnf install -y sysstat
modify the /etc/sysctl.conf
Change the nessesary kernel parameter in /etc/sysctl.conf
kernel.sem = 250 32000 100 128
kernel.shmmni = 4096
kernel.shmall = 1073741824
kernel.shmmax = 4398046511104
kernel.panic_on_oops = 1
net.ipv6.conf.all.disable_ipv6 = 1
net.core.rmem_max = 16777216
net.core.wmem_max = 16777216
net.core.optmem_max = 16777216
net.core.somaxconn = 4096
net.core.netdev_max_backlog = 300000
net.ipv4.ip_local_port_range = 9000 65500
net.ipv4.conf.all.rp_filter = 2
net.ipv4.conf.default.rp_filter = 2
net.ipv4.conf.default.rp_filter = 2
net.ipv4.tcp_rmem = 65536 16777216 16777216
net.ipv4.tcp_wmem = 65536 16777216 16777216
net.ipv4.tcp_max_syn_backlog = 16348
net.ipv4.tcp_slow_start_after_idle = 0
net.ipv4.tcp_dsack = 1
net.ipv4.tcp_sack = 1
net.ipv4.tcp_no_metrics_save = 1
net.ipv4.tcp_moderate_rcvbuf = 1
net.ipv4.tcp_window_scaling = 1
net.ipv4.tcp_syn_retries = 8
net.ipv4.tcp_tw_reuse = 1
net.ipv4.tcp_timestamps = 1
vm.swappiness = 10
vm.dirty_bytes = 629145600
vm.dirty_background_bytes = 314572800
vm.max_map_count = 2147483647
vm.memory_failure_early_kill = 1
fs.file-max = 820448174
fs.aio-max-nr = 18446744073709551615
Download the Oracle 19c DB and the Patch-Set 19.8.0.0 from the SAP Software download Center
Create the SAP and Oracle user
groupadd sapsys -g 79
groupadd dba -g 80
groupadd oper -g 85
groupadd oinstall -g 90
Create the required oracle user
useradd c11adm -u 1001 -d /usr/sap/C11 -g 79 -s /bin/csh -c "SAP Administrator C11"
useradd orac11 -u 1002 -d /oracle/C11 -g 80 -G oper,dba,oinstall -s /bin/bash -c "Oracle Administrator C11"
useradd oracle -u 1003 -d /oracle/C11 -g 90 -G oper,dba -s /bin/bash -c "Oracle Installation"
usermod -a -G oper orac11
disable selinux
[root@ralforavm01 ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: permissive
Mode from config file: permissive
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 31
Disable selinux
vi /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted change the user Permission to the sap and oracle directories.
Reboot the server
Check if selinux is disabled
sestatus
SELinux status: disabled
Change the nfs mountpoint permissions.
chown -R c11adm:sapsys /usr/sap/
chown -R orac11:dba /oracle
Unzip the compressed files into “your” Software directory and execute the install process under the directory SAP.
su – orac11
cd /Software/Oracle_19c_Inst/LINUX_X86_64/db_home/SAP
export DB_SID=C11
export ORACLE_STAGE=/oracle/stage
export ORACLE_BASE=/oracle/C11
Call the Oracle installer for 19c
./19cinstall.sh -silent -db C11 -oracle_stage /oracle/C11/Software/Oracle_19c_Inst/LINUX_X86_64/db_home/
As a root user, execute the following script(s):
- 1. /oracle/oraInventory/orainstRoot.sh
- 2. /oracle/C11/19.0.0/root.sh
[root@ralforavm01 SAP]# /oracle/oraInventory/orainstRoot.sh
[root@ralforavm01 SAP]# /oracle/C11/19.0.0/root.sh
Test connect to Oracle
su – orac11
sqlplus /nolog
SQL> CONNECT / SYS AS SYSDBA
SQL*Plus: Release 19.0.0.0.0 - Production on Wed Nov 4 11:51:28 2020
Version 19.3.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Connected to an idle instance.
SQL> exit
Patch Installation
Install the OPatch utility first.
https://updates.oracle.com/ARULink/PatchDetails/process_form?patch_num=6880880
or download it from SAP swdc à databases Oracle19c
chmod 777 OPATCH19P_2008-70004508.ZIP
su – orac11
/oracle/C11/19.0.0/OPatch/opatch version
OPatch Version: 12.2.0.1.17
OPatch succeeded.
cd /oracle/C11/19.0.0/
unzip /Software/OPATCH19P_2008-70004508.ZIP
/oracle/C11/19.0.0/OPatch/opatch version
========================================================
GENERIC OPATCH VERSION - FOR USE IN SAP ENVIRONMENT ONLY
========================================================
OPatch Version: 12.2.0.1.21
OPatch succeeded.
Validate the Oracle Inventory
/oracle/C11/19.0.0/OPatch/opatch lsinventory -detail -oh /oracle/C11/19.0.0
…..
...
OPatch succeeded.
Apply the OPatch 19.8.0.0 to the DB
Apply the patches
cd /Software/Oracle_Patch_19.8/31305339/31281355
/oracle/C11/19.0.0/OPatch/opatch apply
========================================================
GENERIC OPATCH VERSION - FOR USE IN SAP ENVIRONMENT ONLY
========================================================
Oracle Interim Patch Installer version 12.2.0.1.21
Copyright (c) 2020, Oracle Corporation. All rights reserved.
Oracle Home : /oracle/C11/19.0.0
Central Inventory : /oracle/oraInventory
from : /oracle/C11/19.0.0/oraInst.loc
OPatch version : 12.2.0.1.21 FOR USE IN SAP ENVIRONMENT ONLY
OUI version : 12.2.0.7.0
Log file location : /oracle/C11/19.0.0/cfgtoollogs/opatch/opatch2020-11-04_16-10-50PM_1.log
Verifying environment and performing prerequisite checks...
OPatch continues with these patches: 31281355
Do you want to proceed? [y|n] Y
...
..
cd ../31304218
/oracle/C11/19.0.0/OPatch/opatch apply
cd ../31305087
/oracle/C11/19.0.0/OPatch/opatch apply
cd ../31335188
/oracle/C11/19.0.0/OPatch/opatch apply
cd /oracle/C11/19/OPatch/
datapatch -verbose
Any databases that have invalid objects after the execution of datapatch should have utlrp.sql run to revalidate those objects.
For example:
cd $ORACLE_HOME/rdbms/admin
sqlplus /nolog
SQL> CONNECT / AS SYSDBA
SQL> @utlrp.sql
Apply the SAP Bundle Patch SAP19P_2008-70004508.ZIP (also downloaded from SWDC
dnf install bc.x86_64
cd /Software/SAP19P/SBP_19800200714_202008
ls -l /oracle/C11/19/MOpatch
ls: cannot access '/oracle/C11/19/MOpatch': No such file or directory
cp -r MOPatch /oracle/C11/19/
$ORACLE_HOME/MOPatch/mopatch.sh -hv
MOPatch - Install Multiple Oracle Patches in One Run - 2.5.1.
Copyright (c) 2007, 2020, Oracle and/or its affiliates. All rights reserved.
cd /Software/SAP19P
ls -l
-rw-r--r--. 1 root root 14532539 Nov 4 15:52 SAP19P_2008-70004508.ZIP
drwxr-xr-x. 24 oracle oinstall 4096 Aug 18 17:02 SBP_19800200714_202008
-rw-r--r--. 1 oracle oinstall 76390 Aug 21 15:21 SIGNATURE.SMF
export IHRDBMS=/oracle/C11/19.0.0
env |grep ORA
ORACLE_UNQNAME=C11
ORACLE_SID=C11
ORACLE_BASE=/oracle/C11
ORACLE_HOME=/oracle/C11/19.0.0
ORA_INVENTORY=/oracle/oraInventory
ORACLE_HOSTNAME=ralforavm01.localdomain
$IHRDBMS/MOPatch/mopatch.sh -v -s SAP19P_2008-70004508.ZIP
Create a Database
https://docs.oracle.com/cd/B28359_01/server.111/b28310/create003.htm#ADMIN11073
vi /oracle/C11/19.0.0/dbs/initC11.ora
db_name='C11'
memory_target=1G
processes = 150
db_block_size=8192
open_cursors=300
compatible ='11.2.0'
sqlplus /nolog
SQL*Plus: Release 19.0.0.0.0 - Production on Thu Nov 5 14:57:34 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2020, Oracle. All rights reserved.
SQL> connect / as sysdba
Connected to an idle instance.
SQL> CREATE SPFILE FROM PFILE;
File created.
SQL> startup nomount
ORACLE instance started.
Total System Global Area 713031464 bytes
Fixed Size 8900392 bytes
Variable Size 557842432 bytes
Database Buffers 134217728 bytes
Redo Buffers 12070912 bytes
SQL>
Create C11 Database (only for a Test! The DB will get created during the SAP installation)
vi create_db.sql
CREATE DATABASE C11
USER SYS IDENTIFIED BY manager
USER SYSTEM IDENTIFIED BY manager
LOGFILE GROUP 1 ('/oracle/C11/origlogA/redo01.log') SIZE 100M,
GROUP 2 ('/oracle/C11/origlogB/redo02.log') SIZE 100M,
GROUP 3 ('/oracle/C11/origlogA/redo03.log') SIZE 100M,
GROUP 4 ('/oracle/C11/origlogB/redo04.log') SIZE 100M
MAXLOGFILES 5
MAXLOGMEMBERS 5
MAXLOGHISTORY 1
MAXDATAFILES 100
CHARACTER SET US7ASCII
NATIONAL CHARACTER SET AL16UTF16
EXTENT MANAGEMENT LOCAL
DATAFILE '/oracle/C11/sapdata1/system01.dbf' SIZE 500M REUSE
SYSAUX DATAFILE '/oracle/C11/sapdata2/sysaux01.dbf' SIZE 325M REUSE
DEFAULT TABLESPACE users
DATAFILE '/oracle/C11/sapdata3/users01.dbf'
SIZE 500M REUSE AUTOEXTEND ON MAXSIZE UNLIMITED
DEFAULT TEMPORARY TABLESPACE tempts1
TEMPFILE '/oracle/C11/sapdata1/temp01.dbf'
SIZE 20M REUSE
UNDO TABLESPACE undotbs
DATAFILE '/oracle/C11/sapdata4/undotbs01.dbf'
SIZE 200M REUSE AUTOEXTEND ON MAXSIZE UNLIMITED;
Create the DB
SQL> @create_db.sql
Database created.
Run the required post processing scripts
SQL> @$ORACLE_HOME/rdbms/admin/catalog.sql;
SQL> @$ORACLE_HOME/rdbms/admin/catproc.sql;
SQL> @$ORACLE_HOME/sqlplus/admin/pupbld.sql;
Test if the DB is open
SQL> select status from v$instance;
STATUS
------------
OPEN
1 row selected.
DROP DATABASE:
SQL> shutdown abort
SQL> startup force mount restrict;
ORACLE instance started.
Total System Global Area 243268208 bytes
Fixed Size 8895088 bytes
Variable Size 180355072 bytes
Database Buffers 50331648 bytes
Redo Buffers 3686400 bytes
Database mounted.
SQL> drop database;
Database dropped.
Enable dNFS
To use Oracle dNFS MultiPath with Azure NetApp Files you will need an oranfstab file, Oracle will look in the following order and locations for the configuration file.
- /etc/oranfstab – Server wide
- $ORACLE_HOME/dbs/oranfstab – Oracle Home specific
You need to specify ONLY those volumes in the oranfstab which are used by Oracle. If you specify not used volumes this construct will end up in an non working dNFS scenario. Theoretically oracle should look into the /etc/mtab to automatically enable dNFS volumes.
Below is a copy of my $ORACLE_HOME/dbs/oranfstab
cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
172.17.4.9 ralforavm01.localdomain ralforavm01
172.17.5.4 anf01
dNFS oranfstab for NFSv4.1
[root@ralforavm01 dbs]# cat oranfstab
server: anf01
path: 172.17.10.4
nfs_version: NFSv4.1
security_default: sys
export: /ralforacledatav4/sapdata1 mount: /oracle/C11/sapdata1
export: /ralforacledatav4/sapdata2 mount: /oracle/C11/sapdata2
export: /ralforacledatav4/sapdata3 mount: /oracle/C11/sapdata3
export: /ralforacledatav4/sapdata4 mount: /oracle/C11/sapdata4
export: /ralforacleoriglog/origlogA mount: /oracle/C11/origlogA
export: /ralforacleoriglog/origlogB mount: /oracle/C11/origlogB
export: /ralforacleshared mount: /oracle/C11/19.0.0
export: /ralforaoraarch mount: /oracle/C11/oraarch
export: /ralforasapbackup mount: /oracle/C11/sapbackup
Enabling dNFS
Change dir to $ORACLE_HOME/rdbms/lib and use the make command e.g
cd $ORACLE_HOME/rdbms/lib
make -f ins_rdbms.mk dnfs_on
rm -f /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so;
cp /oracle/C11/19.0.0/lib/libnfsodm19.so /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so
restart oracle
Verify Oracle dNFS Usage
If dNFS is enabled correctly there should be no errors in the alert files. Here we see dNFS issues in the trace directory:
pwd
/oracle/C11/diag/rdbms/c11/C11/trace
The output here shows dNFS issues…. If everything is configured correctly there should be no output.
grep -i kgnfs *.trc
....
…
C11_lgwr_99210.trc: [53257270973] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257271002] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257271026] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_lgwr_99210.trc: [53257283545] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257283571] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257283595] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_lgwr_99210.trc: [53257296302] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_lgwr_99210.trc:[53257296328] kgnfs_dump_hex_data: 0x7ffe492523bc len 120 lt 30
C11_lgwr_99210.trc: [53257296359] kgnfs_dump_hex_data: 0x7ffe492547e8 len 528 lt 132
C11_ora_99256.trc:[53257072683] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257072983] kgnfs_dump_hex_data: 0x7ffd811d920c len 120 lt 30
C11_ora_99256.trc: [53257073007] kgnfs_dump_hex_data: 0x7ffd811db638 len 528 lt 132
C11_ora_99256.trc: [53257102434] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257102459] kgnfs_dump_hex_data: 0x7ffd811d920c len 120 lt 30
C11_ora_99256.trc: [53257102485] kgnfs_dump_hex_data: 0x7ffd811db638 len 528 lt 132
C11_ora_99256.trc:[53257522107] kgnfs_mntrsp: KGNFS_NFSPROC3_MNT FAIL 13
C11_ora_99256.trc:[53257522142] kgnfs_dump_hex_data: 0x7ffd811e39ec len 120 lt 30
C11_ora_99256.trc: [53257522167] kgnfs_dump_hex_data: 0x7ffd811e5e18 len 528 lt 132
In this example dNFS is not enabled correctly.
On NFSv4.1
col SVRNAME format a10
col DIRNAME format a40
col NFSVERSION format a10
col SECURITY format a10
SQL> select SVRNAME,DIRNAME,NFSVERSION,SECURITY from v$dnfs_servers;
SVRNAME DIRNAME NFSVERSION SECURITY
---------- ---------------------------------------- ---------- ----------
anf01 /ralforacleshared NFSv4.1 sys
anf01 /ralforacledatav4/sapdata1 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata2 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata4 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata3 NFSv4.1 sys
anf01 /ralforacleoriglog/origlogB NFSv4.1 sys
anf01 /ralforacleoriglog/origlogA NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
8 rows selected.
After switching the redo-logfile also the oraarch should appear
SQL> alter system switch logfile;
System altered.
SQL> select SVRNAME,DIRNAME,NFSVERSION,SECURITY from v$dnfs_servers;
SVRNAME DIRNAME NFSVERSION SECURITY
---------- ---------------------------------------- ---------- ----------
anf01 /ralforacleshared NFSv4.1 sys
anf01 /ralforacledatav4/sapdata1 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata2 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata4 NFSv4.1 sys
anf01 /ralforacledatav4/sapdata3 NFSv4.1 sys
anf01 /ralforacleoriglog/origlogB NFSv4.1 sys
anf01 /ralforacleoriglog/origlogA NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
anf01 /ralforaoraarch NFSv4.1 sys
9 rows selected.
Disable dNFS
For test reasons it can be necessary to disable the dNFS cleint.
Change dir to $ORACLE_HOME/rdbms/lib and use the make command e.g
cd $ORACLE_HOME/rdbms/lib
make -f ins_rdbms.mk dnfs_off
rm -f /oracle/C11/19.0.0/rdbms/lib/odm/libnfsodm19.so
restart oracle
Performance Test
Before we start the performance testing we configure the system accordingly.
Reference: I/O Configuration and Design (oracle.com)
DB_FILE_MULTIBLOCK_READ_COUNT parameter is used to specifies the maximum number of blocks read in one I/O operation during a sequential scan.
SQL> show parameter DB_FILE_MULTIBLOCK_READ_COUNT
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_file_multiblock_read_count integer 128
SQL> alter system set DB_FILE_MULTIBLOCK_READ_COUNT=256 scope=both;
Setting the dNFS_BATCH_SIZE parameter to 128 (restart of the DB is required to activate)
SQL> alter system set DNFS_BATCH_SIZE=128 scope=spfile;
SQL> shutdown
SQL> startup
SQL> show parameter DNFS_BATCH_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
dnfs_batch_size integer 128
For now we keep the default for:
SORT_AREA_SIZE
|
Determines I/O sizes and concurrency for sort operations.
|
HASH_AREA_SIZE
|
Determines the I/O size for hash operations.
|
SQL> show parameter SORT_AREA_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
sort_area_size integer 65536
SQL> show parameter HASH_AREA_SIZE
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
hash_area_size integer 131072
Running I/O Calibration
The I/O calibration feature of Oracle Database is accessed using the DBMS_RESOURCE_MANAGER.CALIBRATE_IO procedure. This procedure issues an I/O intensive read-only workload, made up of one megabyte of random of I/Os, to the database files to determine the maximum IOPS (I/O requests per second) and MBPS (megabytes of I/O per second) that can be sustained by the storage subsystem.
Preparation:
SQL> show parameter TIMED_STATISTICS
NAME TYPE VALUE
----------------------------------- ----------- ------------------------------
timed_statistics boolean TRUE
SQL> show parameter STATISTICS_LEVEL
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
client_statistics_level string TYPICAL
statistics_level string TYPICAL
Data Volume = 4*2TB Ultra = 4*256MB/s
NFSv4.1 dNFS disabled:
SQL> SET SERVEROUTPUT ON
DECLARE
lat INTEGER;
iops INTEGER;
mbps INTEGER;
BEGIN
-- DBMS_RESOURCE_MANAGER.CALIBRATE_IO (<DISKS>, <MAX_LATENCY>, iops, mbps, lat);
DBMS_RESOURCE_MANAGER.CALIBRATE_IO (2, 10, iops, mbps, lat);
DBMS_OUTPUT.PUT_LINE ('max_iops = ' || iops);
DBMS_OUTPUT.PUT_LINE ('latency = ' || lat);
DBMS_OUTPUT.PUT_LINE ('max_mbps = ' || mbps);
end;
/
max_iops = 38049
latency = 1.208
max_mbps = 297
max_iops = 38049
latency = 1
max_mbps = 297
PL/SQL procedure successfully completed.
Data Volume = 4*2TB Ultra = 4*256MB/s
NFSv4.1 dNFS enabled:
SQL> SET SERVEROUTPUT ON
DECLARE
lat INTEGER;
iops INTEGER;
mbps INTEGER;
BEGIN
-- DBMS_RESOURCE_MANAGER.CALIBRATE_IO (<DISKS>, <MAX_LATENCY>, iops, mbps, lat);
DBMS_RESOURCE_MANAGER.CALIBRATE_IO (2, 10, iops, mbps, lat);
DBMS_OUTPUT.PUT_LINE ('max_iops = ' || iops);
DBMS_OUTPUT.PUT_LINE ('latency = ' || lat);
DBMS_OUTPUT.PUT_LINE ('max_mbps = ' || mbps);
end;
/
max_iops = 38083
latency = .497
max_mbps = 296
max_iops = 38083
latency = 0
max_mbps = 296
PL/SQL procedure successfully completed.
Set the tablespaces to async_io
SQL> col name format a50
SELECT name, asynch_io FROM v$datafile f,v$iostat_file i
WHERE f.file# = i.file_no
AND filetype_name = 'Data File'
NAME ASYNCH_IO
-------------------------------------------------- ---------
/oracle/C11/sapdata1/system01.dbf ASYNC_OFF
/oracle/C11/sapdata2/sysaux01.dbf ASYNC_OFF
/oracle/C11/sapdata4/undotbs01.dbf ASYNC_OFF
/oracle/C11/sapdata3/users01.dbf ASYNC_OFF
SQL> SHOW PARAMETER FILESYSTEMIO_OPTIONS
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
filesystemio_options string none
SQL> ALTER SYSTEM SET FILESYSTEMIO_OPTIONS=SETALL SCOPE=SPFILE;
SQL> shutdown
SQL> startup
SQL> SHOW PARAMETER FILESYSTEMIO_OPTIONS
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
filesystemio_options string SETALL
SQL> col name format a50
SELECT name, asynch_io FROM v$datafile f,v$iostat_file i
WHERE f.file# = i.file_no
AND filetype_name = 'Data File'
NAME ASYNCH_IO
-------------------------------------------------- ---------
/oracle/C11/sapdata1/system01.dbf ASYNC_ON
/oracle/C11/sapdata2/sysaux01.dbf ASYNC_ON
/oracle/C11/sapdata4/undotbs01.dbf ASYNC_ON
/oracle/C11/sapdata3/users01.dbf ASYNC_ON
Preparing the Orion Performance check tool
1 ANF Data-Volume 6TB with Ultra = 768MB/s troughput
Creating the orion files for the test
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata1/orion1 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7701 s, 821 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata2/orion2 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.744 s, 823 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata3/orion3 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7365 s, 823 MB/s
[orac11@ralforavm01 ~]$ dd if=/dev/zero of=/oracle/C11/sapdata4/orion4 bs=1024k count=10000
10000+0 records in
10000+0 records out
10485760000 bytes (10 GB, 9.8 GiB) copied, 12.7354 s, 823 MB/s
Preparing the orion “lun” declaration file
vi orion_nfs.lun
/oracle/C11/sapdata1/orion1
/oracle/C11/sapdata2/orion2
/oracle/C11/sapdata3/orion3
/oracle/C11/sapdata4/orion4
Run the test (NFSv4.1)
~/19.0.0/bin/orion -run oltp -testname orion_nfs -hugenotneeded
ORION: ORacle IO Numbers -- Version RDBMS_19.3.0.0.0DBRU_LINUX.X64_190417
orion_nfs_20201125_1351
Calibration will take approximately 25 minutes.
[orac11@ralforavm01 ~]$ ~/19.0.0/bin/orion -run normal -testname orion_nfs -hugenotneeded
ORION: ORacle IO Numbers -- Version RDBMS_19.3.0.0.0DBRU_LINUX.X64_190417
orion_nfs_20201125_1425
Calibration will take approximately 190 minutes.
Using a large value for -cache_size may take longer.
Setting ftype=0
Maximum Large MBPS=771.28 @ Small=5 and Large=8
Maximum Small IOPS=34449 @ Small=19 and Large=0
Small Read Latency: avg=550.983 us, min=322.815 us, max=11369.239 us, std dev=134.209 us @ Small=19 and Large=0
Minimum Small Latency=419.288 usecs @ Small=1 and Large=0
Small Read Latency: avg=419.288 us, min=311.915 us, max=43826.080 us, std dev=153.365 us @ Small=1 and Large=0
Small Read / Write Latency Histogram @ Small=1 and Large=0
Latency: # of IOs (read) # of IOs (write)
0 - 256 us: 0 ( 0.00%) 0 ( 0.00%)
256 - 512 us: 138100 ( 96.71%) 0 ( 0.00%)
512 - 1024 us: 4268 ( 99.70%) 0 ( 0.00%)
1024 - 2048 us: 366 ( 99.95%) 0 ( 0.00%)
2048 - 4096 us: 52 ( 99.99%) 0 ( 0.00%)
4096 - 8192 us: 9 (100.00%) 0 ( 0.00%)
8192 - 16384 us: 3 (100.00%) 0 ( 0.00%)
16384 - 32768 us: 0 (100.00%) 0 ( 0.00%)
32768 - 65536 us: 1 (100.00%) 0 ( 0.00%)
65536 - 268435456 us: 0 (100.00%) 0 ( 0.00%)
Configuration of the Listener
Create the tnsnames.ora file
pwd
/oracle/C11/19/network/admin
vi tnsnames.ora
C11 =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = 172.17.4.9)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = C11)
)
)
Start the listener
[orac11@ralforavm01 admin]$ lsnrctl start
LSNRCTL for Linux: Version 19.0.0.0.0 - Production on 01-DEC-2020 14:07:00
Copyright (c) 1991, 2020, Oracle. All rights reserved.
Starting /oracle/C11/19.0.0/bin/tnslsnr: please wait...
TNSLSNR for Linux: Version 19.0.0.0.0 - Production
Log messages written to /oracle/C11/diag/tnslsnr/ralforavm01/listener/alert/log.xml
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=ralforavm01.localdomain)(PORT=1521)))
Connecting to (ADDRESS=(PROTOCOL=tcp)(HOST=)(PORT=1521))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for Linux: Version 19.0.0.0.0 - Production
Start Date 01-DEC-2020 14:07:01
Uptime 0 days 0 hr. 0 min. 0 sec
Trace Level off
Security ON: Local OS Authentication
SNMP OFF
Listener Log File /oracle/C11/diag/tnslsnr/ralforavm01/listener/alert/log.xml
Listening Endpoints Summary...
(DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=ralforavm01.localdomain)(PORT=1521)))
The listener supports no services
The command completed successfully
RMAN Configuration
Check the DB logmode:
SQL> select log_mode from v$database;
LOG_MODE
------------
NOARCHIVELOG
Configure database in ARCHIVELOG mode.
SQL> shutdown
Database closed.
Database dismounted.
ORACLE instance shut down.
SQL> startup mount;
ORACLE instance started.
Total System Global Area 1073737800 bytes
Fixed Size 8904776 bytes
Variable Size 864026624 bytes
Database Buffers 188743680 bytes
Redo Buffers 12062720 bytes
Database mounted.
SQL> alter database archivelog;
Database altered.
SQL> alter database open;
Database altered.
Ensure ARCHIVELOG destination.
SQL> select open_mode from v$database;
OPEN_MODE
--------------------
READ WRITE
SQL> archive log list
Database log mode Archive Mode
Automatic archival Enabled
Archive destination /oracle/C11/19.0.0/dbs/arch
Oldest online log sequence 30
Next log sequence to archive 33
Current log sequence 33
Change the oracle archive destination.
SQL> alter system set log_archive_dest_1='location=/oracle/C11/oraarch' scope=both;
SQL> archive log list
Database log mode Archive Mode
Automatic archival Enabled
Archive destination /oracle/C11/oraarch
Oldest online log sequence 30
Next log sequence to archive 33
Current log sequence 33
Ensure the flash/fast recovery area location.
SQL> show parameter db_recovery_file_dest
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_recovery_file_dest string
db_recovery_file_dest_size big integer 0
Connect to RMAN prompt with target database.
[orac11@ralforavm01 ~]$ rman target /
Recovery Manager: Release 19.0.0.0.0 - Production on Mon Nov 30 16:47:40 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
RMAN>
Configure RMAN with control file auto-backup feature that will be auto-backup control file in case of major changes done in database.
RMAN> configure controlfile autobackup on;
using target database control file instead of recovery catalog
new RMAN configuration parameters:
CONFIGURE CONTROLFILE AUTOBACKUP ON;
new RMAN configuration parameters are successfully stored
Enable the optimization
RMAN> configure backup optimization on;
new RMAN configuration parameters:
CONFIGURE BACKUP OPTIMIZATION ON;
new RMAN configuration parameters are successfully stored
Configure the retention policy
RMAN> CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters are successfully stored
Connect to the recovery catalog database (RMAN Repository) & Create a tablespace to store RMAN catalog database objects.
SQL> show parameter db_recovery_file_dest
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
db_recovery_file_dest string
db_recovery_file_dest_size big integer 0
SQL> select global_name from global_name;
GLOBAL_NAME
--------------------------------------------------------------------------------
C11
Create a tablespace to be used for RMAN and the temp tablespace
SQL> create tablespace catalogtbs datafile '/oracle/C11/sapdata1/catalogtbs1.dbf' size 100M autoextend on maxsize unlimited;
SQL> create tablespace temporary tablespace temp_01 tempfile '/oracle/C11/sapdata1/temp_01.dbf' size 5M autoextend ON;
Create a RMAN user, assign RMAN tablespace to RMAN user as a default & grant recovery catalog owner,connect & resource privileges to RMAN user.
SQL> create user recoveryman identified by recoveryman;
SQL> alter user recoveryman default tablespace catalogtbs temporary tablespace temp_01 ;
SQL> grant recovery_catalog_owner to recoveryman;
SQL> grant connect,resource to recoveryman;
alter user recoveryman DEFAULT TABLESPACE catalogtbs quota unlimited on catalogtbs;
Connect to RMAN on target and recovery catalog database.
rman target / catalog recoveryman/recoveryman@C11
Recovery Manager: Release 19.0.0.0.0 - Production on Tue Dec 1 14:13:27 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
connected to recovery catalog database
RMAN>
create catalog by issuing the following command in RMAN prompt and register the DB
RMAN> create catalog;
recovery catalog created
RMAN> register database;
database registered in recovery catalog
starting full resync of recovery catalog
full resync complete
Check whether registration was successful.
RMAN> report schema;
Report of database schema for database with db_unique_name C11
List of Permanent Datafiles
===========================
File Size(MB) Tablespace RB segs Datafile Name
---- -------- -------------------- ------- ------------------------
1 500 SYSTEM YES /oracle/C11/sapdata1/system01.dbf
2 325 SYSAUX NO /oracle/C11/sapdata2/sysaux01.dbf
3 305 UNDOTBS YES /oracle/C11/sapdata4/undotbs01.dbf
4 500 USERS NO /oracle/C11/sapdata3/users01.dbf
5 100 CATALOGTBS NO /oracle/C11/sapdata1/catalogtbs1.dbf
List of Temporary Files
=======================
File Size(MB) Tablespace Maxsize(MB) Tempfile Name
---- -------- -------------------- ----------- --------------------
1 20 TEMPTS1 20 /oracle/C11/sapdata1/temp01.dbf
2 5 TEMP_01 32767 /oracle/C11/sapdata1/temp_01.dbf
Or
RMAN> LIST INCARNATION OF DATABASE;
List of Database Incarnations
DB Key Inc Key DB Name DB ID STATUS Reset SCN Reset Time
------ ------- -------- ---------------- --- ---------- ----------
1 2 C11 365226479 CURRENT 1 23-NOV-20
Creating a system backup
[orac11@ralforavm01 ~]$ ls -l /oracle/C11/sapbackup/
total 0
Starting an RMAN session and configure the backup path.
rman target / catalog recoveryman/recoveryman@C11
Recovery Manager: Release 19.0.0.0.0 - Production on Tue Dec 1 14:42:22 2020
Version 19.8.0.0.0
Copyright (c) 1982, 2019, Oracle and/or its affiliates. All rights reserved.
connected to target database: C11 (DBID=365226479)
connected to recovery catalog database
RMAN> CONFIGURE CHANNEL DEVICE TYPE DISK FORMAT '/oracle/C11/sapbackup/full_%u_%s_%p';
new RMAN configuration parameters:
CONFIGURE CHANNEL DEVICE TYPE DISK FORMAT '/oracle/C11/sapbackup/full_%u_%s_%p';
new RMAN configuration parameters are successfully stored
starting full resync of recovery catalog
full resync complete
Next, you should specify how long you want to retain the backup for. When RMAN takes a backup, it automatically deletes all the old backups that are older than the retention period. In the following example, I’m setting the retention period as 7 days, which will keep the DB backup for a week.
RMAN> CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
old RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters:
CONFIGURE RETENTION POLICY TO RECOVERY WINDOW OF 7 DAYS;
new RMAN configuration parameters are successfully stored
starting full resync of recovery catalog
full resync complete
Typically we’ll use “BACKUP AS BACKUPSET” to backup a database. So, to take a full backup of the database without the archive logs, do the following.
RMAN> BACKUP AS BACKUPSET DATABASE
To take a full backup of the database with the archive logs, do the following:
RMAN> BACKUP AS BACKUPSET DATABASE PLUS ARCHIVELOG;
You can also take a backup of only a specific table space. The following example takes backup of only PRD01 tablespace.
RMAN> BACKUP AS BACKUPSET TABLESPACE PRD01;
Example output:
RMAN> BACKUP AS BACKUPSET DATABASE PLUS ARCHIVELOG;
Starting backup at 01-DEC-20
current log archived
allocated channel: ORA_DISK_1
channel ORA_DISK_1: SID=44 device type=DISK
channel ORA_DISK_1: starting archived log backup set
channel ORA_DISK_1: specifying archived log(s) in backup set
input archived log thread=1 sequence=33 RECID=1 STAMP=1057971633
input archived log thread=1 sequence=34 RECID=2 STAMP=1058020317
input archived log thread=1 sequence=35 RECID=3 STAMP=1058021321
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_02vh07ub_2_1 tag=TAG20201201T144843 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:03
Finished backup at 01-DEC-20
Starting backup at 01-DEC-20
using channel ORA_DISK_1
channel ORA_DISK_1: starting full datafile backup set
channel ORA_DISK_1: specifying datafile(s) in backup set
input datafile file number=00001 name=/oracle/C11/sapdata1/system01.dbf
input datafile file number=00004 name=/oracle/C11/sapdata3/users01.dbf
input datafile file number=00002 name=/oracle/C11/sapdata2/sysaux01.dbf
input datafile file number=00003 name=/oracle/C11/sapdata4/undotbs01.dbf
input datafile file number=00005 name=/oracle/C11/sapdata1/catalogtbs1.dbf
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_03vh07ug_3_1 tag=TAG20201201T144846 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:07
Finished backup at 01-DEC-20
Starting backup at 01-DEC-20
current log archived
using channel ORA_DISK_1
channel ORA_DISK_1: starting archived log backup set
channel ORA_DISK_1: specifying archived log(s) in backup set
input archived log thread=1 sequence=36 RECID=4 STAMP=1058021335
channel ORA_DISK_1: starting piece 1 at 01-DEC-20
channel ORA_DISK_1: finished piece 1 at 01-DEC-20
piece handle=/oracle/C11/sapbackup/full_04vh07uo_4_1 tag=TAG20201201T144856 comment=NONE
channel ORA_DISK_1: backup set complete, elapsed time: 00:00:01
Finished backup at 01-DEC-20
Starting Control File and SPFILE Autobackup at 01-DEC-20
piece handle=/oracle/C11/19.0.0/dbs/c-365226479-20201201-00 comment=NONE
Finished Control File and SPFILE Autobackup at 01-DEC-20
RMAN>
Check the backup location:
[orac11@ralforavm01 admin]$ ls -l /oracle/C11/sapbackup/
total 782612
-rw-r----- 1 orac11 dba 169256448 Dec 1 14:48 full_02vh07ub_2_1
-rw-r----- 1 orac11 dba 628776960 Dec 1 14:48 full_03vh07ug_3_1
-rw-r----- 1 orac11 dba 204800 Dec 1 14:48 full_04vh07uo_4_1
References
Microsoft
Solution architectures using Azure NetApp Files – Oracle
Solution architectures using Azure NetApp Files – SAP on Azure
SAP deployment on Azure using an Oracle DB – Azure Architecture Center | Microsoft Docs
Oracle:
https://oracle-base.com/articles/19c/oracle-db-19c-installation-on-oracle-linux-8
https://docs.oracle.com/en/database/oracle/oracle-database/19/ladbi/supported-oracle-linux-8-distributions-for-x86-64.html#GUID-F4902762-325B-4C89-B85B-F52BA482190F
SAP
2015553 – SAP on Microsoft Azure: Support prerequisites – SAP ONE Support Launchpad
2039619 – SAP Applications on Microsoft Azure using the Oracle Database: Supported Products and Versions – SAP ONE Support Launchpad
NetApp
Oracle Databases on Microsoft Azure Using Azure NetApp Files | TR-4780 | NetApp
TR-3633: Oracle Databases on NetApp ONTAP | NetApp
by Scott Muniz | Jan 18, 2021 | Security, Technology
This article is contributed. See the original author and article here.
| 1c — 1c:enterprise |
The Web server in 1C:Enterprise 8 before 8.3.17.1851 sends base64 encoded credentials in the creds URL parameter. |
2021-01-13 |
not yet calculated |
CVE-2021-3131
MISC |
| 360f5 — 360f5 |
In the 3.1.3.64296 and lower version of 360F5, the third party can trigger the device to send a deauth frame by constructing and sending a specific illegal 802.11 Null Data Frame, which will cause other wireless terminals connected to disconnect from the wireless, so as to attack the router wireless by DoS. At present, the vulnerability has been effectively handled, and users can fix the vulnerability after updating the firmware version. |
2021-01-11 |
not yet calculated |
CVE-2019-3405
MISC |
| acmailer — acmailer |
Improper access control vulnerability in acmailer ver. 4.0.1 and earlier, and acmailer DB ver. 1.1.3 and earlier allows remote attackers to execute an arbitrary OS command, or gain an administrative privilege which may result in obtaining the sensitive information on the server via unspecified vectors. |
2021-01-14 |
not yet calculated |
CVE-2021-20617
MISC
MISC |
| acmailer — acmailer |
Privilege chaining vulnerability in acmailer ver. 4.0.2 and earlier, and acmailer DB ver. 1.1.4 and earlier allows remote attackers to bypass authentication and to gain an administrative privilege which may result in obtaining the sensitive information on the server via unspecified vectors. |
2021-01-14 |
not yet calculated |
CVE-2021-20618
MISC
MISC |
| adobe — animate |
Adobe Animate version 21.0 (and earlier) is affected by an uncontrolled search path element that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21008
CONFIRM |
adobe — bridge
|
Adobe Bridge version 11.0 (and earlier) is affected by an out-of-bounds write vulnerability when parsing TTF files that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21013
MISC |
adobe — bridge
|
Adobe Bridge version 11.0 (and earlier) is affected by an out-of-bounds write vulnerability when parsing TTF files that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21012
MISC |
| adobe — campaign_classic_gold_standard |
Adobe Campaign Classic Gold Standard 10 (and earlier), 20.3.1 (and earlier), 20.2.3 (and earlier), 20.1.3 (and earlier), 19.2.3 (and earlier) and 19.1.7 (and earlier) are affected by a server-side request forgery (SSRF) vulnerability. Successful exploitation could allow an attacker to use the Campaign instance to issue unauthorized requests to internal or external resources. |
2021-01-13 |
not yet calculated |
CVE-2021-21009
MISC |
adobe — captivate
|
Adobe Captivate 2019 version 11.5.1.499 (and earlier) is affected by an uncontrolled search path element vulnerability that could lead to privilege escalation. An attacker with permissions to write to the file system could leverage this vulnerability to escalate privileges. |
2021-01-13 |
not yet calculated |
CVE-2021-21011
CONFIRM |
adobe — illustrator
|
Adobe Illustrator version 25.0 (and earlier) is affected by an uncontrolled search path element that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21007
CONFIRM |
| adobe — incopy |
InCopy version 15.1.1 (and earlier) for Windows is affected by an uncontrolled search path vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21010
MISC |
| adobe — photoshop |
Adobe Photoshop version 22.1 (and earlier) is affected by a heap buffer overflow vulnerability when handling a specially crafted font file. Successful exploitation could lead to arbitrary code execution. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
2021-01-13 |
not yet calculated |
CVE-2021-21006
CONFIRM |
anydesk — anydesk
|
AnyDesk before 6.1.0 on Windows, when run in portable mode on a system where the attacker has write access to the application directory, allows this attacker to compromise a local user account via a read-only setting for a Trojan horse gcapi.dll file. |
2021-01-11 |
not yet calculated |
CVE-2020-35483
CONFIRM |
apache — tomcat
|
When serving resources from a network location using the NTFS file system, Apache Tomcat versions 10.0.0-M1 to 10.0.0-M9, 9.0.0.M1 to 9.0.39, 8.5.0 to 8.5.59 and 7.0.0 to 7.0.106 were susceptible to JSP source code disclosure in some configurations. The root cause was the unexpected behaviour of the JRE API File.getCanonicalPath() which in turn was caused by the inconsistent behaviour of the Windows API (FindFirstFileW) in some circumstances. |
2021-01-14 |
not yet calculated |
CVE-2021-24122
MLIST
MISC
MLIST
MLIST
MLIST
MLIST
MLIST
MLIST
MLIST |
apache — xmlbeans
|
The XML parsers used by XMLBeans up to version 2.6.0 did not set the properties needed to protect the user from malicious XML input. Vulnerabilities include possibilities for XML Entity Expansion attacks. Affects XMLBeans up to and including v2.6.0. |
2021-01-14 |
not yet calculated |
CVE-2021-23926
MISC
MISC |
| aruba_networks — airwave_glass |
Multiple authenticated remote command executions are possible in Airwave Glass before 1.3.3 via the glassadmin cli. These allow for a user with glassadmin privileges to execute arbitrary code as root on the underlying host operating system. |
2021-01-15 |
not yet calculated |
CVE-2020-24638
MISC |
| aruba_networks — airwave_glass |
There is a vulnerability caused by insufficient input validation that allows for arbitrary command execution in a containerized environment within Airwave Glass before 1.3.3. Successful exploitation can lead to complete compromise of the underlying host operating system. |
2021-01-15 |
not yet calculated |
CVE-2020-24640
MISC |
| aruba_networks — airwave_glass |
In Aruba AirWave Glass before 1.3.3, there is a Server-Side Request Forgery vulnerability through an unauthenticated endpoint that if successfully exploited can result in disclosure of sensitive information. This can be used to perform an authentication bypass and ultimately gain administrative access on the web administrative interface. |
2021-01-15 |
not yet calculated |
CVE-2020-24641
MISC |
aruba_networks — airwave_glass
|
There is a vulnerability caused by unsafe Java deserialization that allows for arbitrary command execution in a containerized environment within Airwave Glass before 1.3.3. Successful exploitation can lead to complete compromise of the underlying host operating system. |
2021-01-15 |
not yet calculated |
CVE-2020-24639
MISC |
bosch — praesideo_and_praesensa
|
A vulnerability in the web-based management interface of Bosch PRAESIDEO until and including version 4.41 and Bosch PRAESENSA until and including version 1.10 allows an unauthenticated remote attacker to trigger actions on an affected system on behalf of another user (Cross-Site Request Forgery). This requires the victim to be tricked into clicking a malicious link or submitting a malicious form. A successful exploit allows the attacker to perform arbitrary actions with the privileges of the victim, e.g. creating and modifying user accounts, changing system configuration settings and cause DoS conditions. Note: For Bosch PRAESIDEO 4.31 and newer and Bosch PRAESENSA in all versions, the confidentiality impact is considered low because user credentials are not shown in the web interface. |
2021-01-14 |
not yet calculated |
CVE-2020-6776
CONFIRM |
bosch — praesideo_and_praesensa
|
A vulnerability in the web-based management interface of Bosch PRAESIDEO until and including version 4.41 and Bosch PRAESENSA until and including version 1.10 allows an authenticated remote attacker with admin privileges to mount a stored Cross-Site-Scripting (XSS) attack against another user. When the victim logs into the management interface, the stored script code is executed in the context of his browser. A successful exploit would allow an attacker to interact with the management interface with the privileges of the victim. However, as the attacker already needs admin privileges, there is no additional impact on the management interface itself. |
2021-01-14 |
not yet calculated |
CVE-2020-6777
CONFIRM |
canonical — remote-login-service
|
In crypt.c of remote-login-service, the cryptographic algorithm used to cache usernames and passwords is insecure. An attacker could use this vulnerability to recover usernames and passwords from the file. This issue affects version 1.0.0-0ubuntu3 and prior versions. |
2021-01-13 |
not yet calculated |
CVE-2013-1053
UBUNTU |
canonical — ubuntu
|
Use-after-free vulnerability in the Linux kernel exploitable by a local attacker due to reuse of a DCCP socket with an attached dccps_hc_tx_ccid object as a listener after being released. Fixed in Ubuntu Linux kernel 5.4.0-51.56, 5.3.0-68.63, 4.15.0-121.123, 4.4.0-193.224, 3.13.0.182.191 and 3.2.0-149.196. |
2021-01-14 |
not yet calculated |
CVE-2020-16119
UBUNTU
UBUNTU
CONFIRM
UBUNTU
UBUNTU
UBUNTU
UBUNTU
UBUNTU |
|
cisco — anyconnect_secure_mobility_client
|
A vulnerability in the upgrade component of Cisco AnyConnect Secure Mobility Client could allow an authenticated, local attacker with low privileges to read arbitrary files on the underlying operating system (OS) of an affected device. The vulnerability is due to insufficient file permission restrictions. An attacker could exploit this vulnerability by sending a crafted command from the local CLI to the application. A successful exploit could allow the attacker to read arbitrary files on the underlying OS of the affected device. The attacker would need to have valid user credentials to exploit this vulnerability. |
2021-01-13 |
not yet calculated |
CVE-2021-1258
CISCO |
cisco — anyconnect_secure_mobility_client
|
A vulnerability in the Network Access Manager and Web Security Agent components of Cisco AnyConnect Secure Mobility Client for Windows could allow an authenticated, local attacker to perform a DLL injection attack. To exploit this vulnerability, the attacker would need to have valid credentials on the Windows system. The vulnerability is due to insufficient validation of resources that are loaded by the application at run time. An attacker could exploit this vulnerability by inserting a configuration file in a specific path in the system which, in turn, causes a malicious DLL file to be loaded when the application starts. A successful exploit could allow the attacker to execute arbitrary code on the affected machine with SYSTEM privileges. |
2021-01-13 |
not yet calculated |
CVE-2021-1237
CISCO |
cisco — asr_5000_series_routers
|
A vulnerability in the Secure FTP (SFTP) of Cisco StarOS for Cisco ASR 5000 Series Routers could allow an authenticated, remote attacker to read arbitrary files on an affected device. To exploit this vulnerability, the attacker would need to have valid credentials on the affected device. The vulnerability is due to insecure handling of symbolic links. An attacker could exploit this vulnerability by sending a crafted SFTP command to an affected device. A successful exploit could allow the attacker to read arbitrary files on the affected device. |
2021-01-13 |
not yet calculated |
CVE-2021-1145
CISCO |
cisco — connected_mobile_experiences
|
A vulnerability in Cisco Connected Mobile Experiences (CMX) API authorizations could allow an authenticated, remote attacker to enumerate what users exist on the system. The vulnerability is due to a lack of authorization checks for certain API GET requests. An attacker could exploit this vulnerability by sending specific API GET requests to an affected device. A successful exploit could allow the attacker to enumerate users of the CMX system. |
2021-01-13 |
not yet calculated |
CVE-2021-1143
CISCO |
cisco — connected_mobile_experiences
|
A vulnerability in Cisco Connected Mobile Experiences (CMX) could allow a remote, authenticated attacker without administrative privileges to alter the password of any user on an affected system. The vulnerability is due to incorrect handling of authorization checks for changing a password. An authenticated attacker without administrative privileges could exploit this vulnerability by sending a modified HTTP request to an affected device. A successful exploit could allow the attacker to alter the passwords of any user on the system, including an administrative user, and then impersonate that user. |
2021-01-13 |
not yet calculated |
CVE-2021-1144
CISCO |
cisco — dna_center
|
A vulnerability in the web-based management interface of Cisco DNA Center software could allow an authenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the interface of an affected device. The vulnerability exists because the web-based management interface does not properly validate user-supplied input. An attacker could exploit this vulnerability by persuading a user to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the interface or access sensitive, browser-based information. To exploit this vulnerability, an attacker would need to have administrative credentials on the affected device. |
2021-01-13 |
not yet calculated |
CVE-2021-1130
CISCO |
cisco — enterprise_nfv_infrastructure_software
|
A vulnerability in the web-based management interface of Cisco Enterprise NFV Infrastructure Software (NFVIS) could allow an authenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the web-based management interface. The vulnerability is due to improper input validation of log file content stored on the affected device. An attacker could exploit this vulnerability by modifying a log file with malicious code and getting a user to view the modified log file. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or to access sensitive, browser-based information. |
2021-01-13 |
not yet calculated |
CVE-2021-1127
CISCO |
|
cisco — finesse
|
Multiple vulnerabilities in the web-based management interface of Cisco Finesse could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack and obtain potentially confidential information by leveraging a flaw in the authentication mechanism. For more information about these vulnerabilities, see the Details section of this advisory. |
2021-01-13 |
not yet calculated |
CVE-2021-1246
CISCO |
| cisco — finesse |
Multiple vulnerabilities in the web-based management interface of Cisco Finesse could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack and obtain potentially confidential information by leveraging a flaw in the authentication mechanism. For more information about these vulnerabilities, see the Details section of this advisory. |
2021-01-13 |
not yet calculated |
CVE-2021-1245
CISCO |
| cisco — firepower_management_center |
Multiple vulnerabilities in the web-based management interface of Cisco Firepower Management Center (FMC) could allow an authenticated, remote attacker to conduct a stored cross-site scripting (XSS) attack against a user of the interface of an affected system. The vulnerabilities exist because the web-based management interface does not properly validate user-supplied input. An attacker could exploit these vulnerabilities by persuading a user of the interface to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. |
2021-01-13 |
not yet calculated |
CVE-2021-1239
CISCO |
| cisco — firepower_management_center |
A vulnerability in the storage of proxy server credentials of Cisco Firepower Management Center (FMC) could allow an authenticated, local attacker to view credentials for a configured proxy server. The vulnerability is due to clear-text storage and weak permissions of related configuration files. An attacker could exploit this vulnerability by accessing the CLI of the affected software and viewing the contents of the affected files. A successful exploit could allow the attacker to view the credentials that are used to access the proxy server. |
2021-01-13 |
not yet calculated |
CVE-2021-1126
CISCO |
| cisco — firepower_management_center |
Multiple vulnerabilities in the web-based management interface of Cisco Firepower Management Center (FMC) could allow an authenticated, remote attacker to conduct a stored cross-site scripting (XSS) attack against a user of the interface of an affected system. The vulnerabilities exist because the web-based management interface does not properly validate user-supplied input. An attacker could exploit these vulnerabilities by persuading a user of the interface to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. |
2021-01-13 |
not yet calculated |
CVE-2021-1238
CISCO |
| cisco — firepower_management_center |
A vulnerability in the dashboard widget of Cisco Firepower Management Center (FMC) Software could allow an authenticated, remote attacker to cause a denial of service (DoS) condition on an affected device. The vulnerability is due to improper restrictions on XML entities. An attacker could exploit this vulnerability by crafting an XML-based widget on an affected server. A successful exploit could cause increased memory and CPU utilization, which could result in a DoS condition. |
2021-01-13 |
not yet calculated |
CVE-2021-1267
CISCO |
| cisco — multiple_products |
Multiple Cisco products are affected by a vulnerability in the Snort detection engine that could allow an unauthenticated, remote attacker to bypass a configured file policy for HTTP. The vulnerability is due to incorrect handling of an HTTP range header. An attacker could exploit this vulnerability by sending crafted HTTP packets through an affected device. A successful exploit could allow the attacker to bypass configured file policy for HTTP packets and deliver a malicious payload. |
2021-01-13 |
not yet calculated |
CVE-2021-1223
CISCO |
| cisco — multiple_products |
Multiple Cisco products are affected by a vulnerability in the Snort application detection engine that could allow an unauthenticated, remote attacker to bypass the configured policies on an affected system. The vulnerability is due to a flaw in the detection algorithm. An attacker could exploit this vulnerability by sending crafted packets that would flow through an affected system. A successful exploit could allow the attacker to bypass the configured policies and deliver a malicious payload to the protected network. |
2021-01-13 |
not yet calculated |
CVE-2021-1236
CISCO |
| cisco — multiple_products |
Multiple Cisco products are affected by a vulnerability with TCP Fast Open (TFO) when used in conjunction with the Snort detection engine that could allow an unauthenticated, remote attacker to bypass a configured file policy for HTTP. The vulnerability is due to incorrect detection of the HTTP payload if it is contained at least partially within the TFO connection handshake. An attacker could exploit this vulnerability by sending crafted TFO packets with an HTTP payload through an affected device. A successful exploit could allow the attacker to bypass configured file policy for HTTP packets and deliver a malicious payload. |
2021-01-13 |
not yet calculated |
CVE-2021-1224
CISCO |
cisco — multiple_products
|
A vulnerability in the audit logging component of Cisco Unified Communications Manager, Cisco Unified Communications Manager Session Management Edition, Cisco Unified Communications Manager IM & Presence Service, Cisco Unity Connection, Cisco Emergency Responder, and Cisco Prime License Manager could allow an authenticated, remote attacker to view sensitive information in clear text on an affected system. The vulnerability is due to the storage of certain unencrypted credentials. An attacker could exploit this vulnerability by accessing the audit logs on an affected system and obtaining credentials that they may not normally have access to. A successful exploit could allow the attacker to use those credentials to discover and manage network devices. |
2021-01-13 |
not yet calculated |
CVE-2021-1226
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1201
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1205
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1181
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1173
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1175
CISCO |
| cisco — multiple_small_business_routers |
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1161
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1183
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1168
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1169
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1170
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1179
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1171
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1174
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1182
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1176
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1177
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1178
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1172
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1202
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1167
MISC
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1190
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1165
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to inject arbitrary commands that are executed with root privileges. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to a targeted device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on an affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1146
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1180
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1164
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1307
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1217
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1204
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1159
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1166
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1160
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1203
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1200
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1191
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1162
CISCO |
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1163
CISCO |
|
cisco — multiple_small_business_routers
|
Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code or cause an affected device to restart unexpectedly. The vulnerabilities are due to improper validation of user-supplied input in the web-based management interface. An attacker could exploit these vulnerabilities by sending crafted HTTP requests to an affected device. A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system or cause the device to reload, resulting in a denial of service (DoS) condition. To exploit these vulnerabilities, an attacker would need to have valid administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. |
2021-01-13 |
not yet calculated |
CVE-2021-1360
CISCO |
cisco — proximity_desktop_for_windows
|
A vulnerability in the loading process of specific DLLs in Cisco Proximity Desktop for Windows could allow an authenticated, local attacker to load a malicious library. To exploit this vulnerability, the attacker must have valid credentials on the Windows system. This vulnerability is due to incorrect handling of directory paths at run time. An attacker could exploit this vulnerability by placing a malicious DLL file in a specific location on the targeted system. This file will execute when the vulnerable application launches. A successful exploit could allow the attacker to execute arbitrary code on the targeted system with the privileges of another user’s account. |
2021-01-13 |
not yet calculated |
CVE-2021-1240
CISCO |
cisco — video_surveillance_8000_series_ip_cameras
|
A vulnerability in the Cisco Discovery Protocol implementation for Cisco Video Surveillance 8000 Series IP Cameras could allow an unauthenticated, adjacent attacker to cause an affected IP camera to reload. The vulnerability is due to missing checks when Cisco Discovery Protocol messages are processed. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol packet to an affected IP camera. A successful exploit could allow the attacker to cause the affected IP camera to reload unexpectedly, resulting in a denial of service (DoS) condition. Note: Cisco Discovery Protocol is a Layer 2 protocol. To exploit this vulnerability, an attacker must be in the same broadcast domain as the affected device (Layer 2 adjacent). |
2021-01-13 |
not yet calculated |
CVE-2021-1131
CISCO |
|
cisco — webex_meetings
|
A vulnerability in the reclaim host role feature of Cisco Webex Meetings and Cisco Webex Meetings Server could allow an authenticated, remote attacker to take over the host role during a meeting. This vulnerability is due to a lack of protection against brute forcing of the host key. An attacker could exploit this vulnerability by sending crafted requests to a vulnerable Cisco Webex Meetings or Webex Meetings Server site. A successful exploit would require the attacker to have access to join a Webex meeting, including applicable meeting join links and passwords. A successful exploit could allow the attacker to acquire or take over the host role for a meeting. |
2021-01-13 |
not yet calculated |
CVE-2021-1311
CISCO |
cisco — webex_meetings
|
A vulnerability in the web-based management interface of Cisco Webex Meetings could allow an unauthenticated, remote attacker to redirect a user to an untrusted web page, bypassing the warning mechanism that should prompt the user before the redirection. This vulnerability is due to improper input validation of the URL parameters in an HTTP request. An attacker could exploit this vulnerability by persuading a user to click a crafted link. A successful exploit could allow the attacker to redirect a user to a malicious website, bypassing the Webex URL check that should result in a warning before the redirection to the web page. Attackers may use this type of vulnerability, known as an open redirect attack, as part of a phishing attack to convince users to unknowingly visit malicious sites. |
2021-01-13 |
not yet calculated |
CVE-2021-1310
CISCO |
cisco — webex_teams
|
A vulnerability in Cisco Webex Teams could allow an unauthenticated, remote attacker to manipulate file names within the messaging interface. The vulnerability exists because the affected software mishandles character rendering. An attacker could exploit this vulnerability by sharing a file within the application interface. A successful exploit could allow the attacker to modify how the shared file name displays within the interface, which could allow the attacker to conduct phishing or spoofing attacks. |
2021-01-13 |
not yet calculated |
CVE-2021-1242
CISCO |
clusterlabs — hawk
|
An issue was discovered in ClusterLabs Hawk 2.x through 2.3.0-x. There is a Ruby shell code injection issue via the hawk_remember_me_id parameter in the login_from_cookie cookie. The user logout routine could be used by unauthenticated remote attackers to execute code as hauser. |
2021-01-12 |
not yet calculated |
CVE-2020-35458
MLIST
MISC
MISC
CONFIRM |
coturn — coturn
|
Coturn is free open source implementation of TURN and STUN Server. Coturn before version 4.5.2 by default does not allow peers to connect and relay packets to loopback addresses in the range of `127.x.x.x`. However, it was observed that when sending a `CONNECT` request with the `XOR-PEER-ADDRESS` value of `0.0.0.0`, a successful response was received and subsequently, `CONNECTIONBIND` also received a successful response. Coturn then is able to relay packets to the loopback interface. Additionally, when coturn is listening on IPv6, which is default, the loopback interface can also be reached by making use of either `[::1]` or `[::]` as the peer address. By using the address `0.0.0.0` as the peer address, a malicious user will be able to relay packets to the loopback interface, unless `–denied-peer-ip=0.0.0.0` (or similar) has been specified. Since the default configuration implies that loopback peers are not allowed, coturn administrators may choose to not set the `denied-peer-ip` setting. The issue patched in version 4.5.2. As a workaround the addresses in the address block `0.0.0.0/8`, `[::1]` and `[::]` should be denied by default unless `–allow-loopback-peers` has been specified. |
2021-01-13 |
not yet calculated |
CVE-2020-26262
MISC
MISC
CONFIRM |
dell — emc_avamar_server
|
DELL EMC Avamar Server, versions 19.1, 19.2, 19.3, contain a SQL Injection Vulnerability in Fitness Analyzer. A remote unauthenticated attacker could potentially exploit this vulnerability, leading to the execution of certain SQL commands on the application’s backend database, causing unauthorized read and write access to application data. Exploitation may lead to leakage or deletion of sensitive backup data; hence the severity is Critical. Dell EMC recommends customers to upgrade at the earliest opportunity. |
2021-01-14 |
not yet calculated |
CVE-2020-29493
CONFIRM |
dell — emc_avamar_server
|
Dell EMC Avamar Server, versions 19.1, 19.2, 19.3, contain a Path Traversal Vulnerability in PDM. A remote user could potentially exploit this vulnerability, to gain unauthorized write access to the arbitrary files stored on the server filesystem, causing deletion of arbitrary files. |
2021-01-14 |
not yet calculated |
CVE-2020-29494
CONFIRM |
dell — emc_avamar_server
|
DELL EMC Avamar Server, versions 19.1, 19.2, 19.3, contain an OS Command Injection Vulnerability in Fitness Analyzer. A remote unauthenticated attacker could potentially exploit this vulnerability, leading to the execution of arbitrary OS commands on the application’s underlying OS with high privileges. This vulnerability is considered critical as it can be leveraged to completely compromise the vulnerable application as well as the underlying operating system. Dell recommends customers to upgrade at the earliest opportunity. |
2021-01-14 |
not yet calculated |
CVE-2020-29495
CONFIRM |
| discourse — discourse |
In Discourse 2.7.0 through beta1, a rate-limit bypass leads to a bypass of the 2FA requirement for certain forms. |
2021-01-14 |
not yet calculated |
CVE-2021-3138
MISC
MISC
MISC |
| docker — desktop_community |
Docker Desktop Community before 2.5.0.0 on macOS mishandles certificate checking, leading to local privilege escalation. |
2021-01-15 |
not yet calculated |
CVE-2021-3162
MISC
MISC |
| eclipse — hawkbit |
In all version of Eclipse Hawkbit prior to 0.3.0M7, the HTTP 404 (Not Found) JSON response body returned by the REST API may contain unsafe characters within the path attribute. Sending a POST request to a non existing resource will return the full path from the given URL unescaped to the client. |
2021-01-14 |
not yet calculated |
CVE-2020-27219
CONFIRM
CONFIRM |
eclipse — hono_amqp_and_mqtt
|
The Eclipse Hono AMQP and MQTT protocol adapters do not check whether an authenticated gateway device is authorized to receive command & control messages when it has subscribed only to commands for a specific device. The missing check involves verifying that the command target device is configured giving permission for the gateway device to act on its behalf. This means an authenticated device of a certain tenant, notably also a non-gateway device acting like a gateway, may receive command & control messages targeted at a different device of the same tenant without corresponding permissions getting checked. |
2021-01-14 |
not yet calculated |
CVE-2020-27220
CONFIRM |
elasticsearch — elasticsearch
|
Elasticsearch versions 7.7.0 to 7.10.1 contain an information disclosure flaw in the async search API. Users who execute an async search will improperly store the HTTP headers. An Elasticsearch user with the ability to read the .tasks index could obtain sensitive request headers of other users in the cluster. This issue is fixed in Elasticsearch 7.10.2 |
2021-01-14 |
not yet calculated |
CVE-2021-22132
MISC |
erlang — otp
|
An issue was discovered in Erlang/OTP before 23.2.2. The ssl application 10.2 accepts and trusts an invalid X.509 certificate chain to a trusted root Certification Authority. |
2021-01-15 |
not yet calculated |
CVE-2020-35733
CONFIRM
MISC
MISC
MISC |
espressif — esp-idf
|
Espressif ESP-IDF 2.x, 3.0.x through 3.0.9, 3.1.x through 3.1.7, 3.2.x through 3.2.3, 3.3.x through 3.3.2, and 4.0.x through 4.0.1 has a Buffer Overflow in BluFi provisioning in btc_blufi_recv_handler function in blufi_prf.c. An attacker can send a crafted BluFi protocol Write Attribute command to characteristic 0xFF01. With manipulated packet fields, there is a buffer overflow. |
2021-01-12 |
not yet calculated |
CVE-2020-16146
MISC
MISC |
| facade — ignition |
Ignition before 2.5.2, as used in Laravel and other products, allows unauthenticated remote attackers to execute arbitrary code because of insecure usage of file_get_contents() and file_put_contents(). This is exploitable on sites using debug mode with Laravel before 8.4.2. |
2021-01-12 |
not yet calculated |
CVE-2021-3129
MISC
MISC |
flatcore — flatcore
|
An issue was discovered in flatCore before 2.0.0 build 139. A reflected XSS vulnerability was identified in the media_filter HTTP request body parameter for the acp interface. The affected parameter accepts malicious client-side script without proper input sanitization. For example, a malicious user can leverage this vulnerability to steal cookies from a victim user and perform a session-hijacking attack, which may then lead to unauthorized access to the site. |
2021-01-15 |
not yet calculated |
CVE-2021-23838
MISC
MISC
MISC |
flatcore — flatcore
|
An issue was discovered in flatCore before 2.0.0 build 139. A time-based blind SQL injection was identified in the selected_folder HTTP request body parameter for the acp interface. The affected parameter (which retrieves the file contents of the specified folder) was found to be accepting malicious user input without proper sanitization, thus leading to SQL injection. Database related information can be successfully retrieved. |
2021-01-15 |
not yet calculated |
CVE-2021-23837
MISC
MISC
MISC |
flatcore — flatcore
|
An issue was discovered in flatCore before 2.0.0 build 139. A stored XSS vulnerability was identified in the prefs_smtp_psw HTTP request body parameter for the acp interface. An admin user can inject malicious client-side script into the affected parameter without any form of input sanitization. The injected payload will be executed in the browser of a user whenever one visits the affected module page. |
2021-01-15 |
not yet calculated |
CVE-2021-23836
MISC
MISC
MISC |
flatcore — flatcore
|
An issue was discovered in flatCore before 2.0.0 build 139. A local file disclosure vulnerability was identified in the docs_file HTTP request body parameter for the acp interface. This can be exploited with admin access rights. The affected parameter (which retrieves the contents of the specified file) was found to be accepting malicious user input without proper sanitization, thus leading to retrieval of backend server sensitive files, e.g., /etc/passwd, SQLite database files, PHP source code, etc. |
2021-01-15 |
not yet calculated |
CVE-2021-23835
MISC
MISC
MISC |
flatpak — flatpak
|
Flatpak is a system for building, distributing, and running sandboxed desktop applications on Linux. A bug was discovered in the `flatpak-portal` service that can allow sandboxed applications to execute arbitrary code on the host system (a sandbox escape). This sandbox-escape bug is present in versions from 0.11.4 and before fixed versions 1.8.5 and 1.9.4. The Flatpak portal D-Bus service (`flatpak-portal`, also known by its D-Bus service name `org.freedesktop.portal.Flatpak`) allows apps in a Flatpak sandbox to launch their own subprocesses in a new sandbox instance, either with the same security settings as the caller or with more restrictive security settings. For example, this is used in Flatpak-packaged web browsers such as Chromium to launch subprocesses that will process untrusted web content, and give those subprocesses a more restrictive sandbox than the browser itself. In vulnerable versions, the Flatpak portal service passes caller-specified environment variables to non-sandboxed processes on the host system, and in particular to the `flatpak run` command that is used to launch the new sandbox instance. A malicious or compromised Flatpak app could set environment variables that are trusted by the `flatpak run` command, and use them to execute arbitrary code that is not in a sandbox. As a workaround, this vulnerability can be mitigated by preventing the `flatpak-portal` service from starting, but that mitigation will prevent many Flatpak apps from working correctly. This is fixed in versions 1.8.5 and 1.9.4. |
2021-01-14 |
not yet calculated |
CVE-2021-21261
MISC
MISC
MISC
MISC
MISC
CONFIRM
DEBIAN |
| fortinet — fortideceptor |
An OS command injection vulnerability in FortiDeceptor 3.1.0, 3.0.1, 3.0.0 may allow a remote authenticated attacker to execute arbitrary commands on the system by exploiting a command injection vulnerability on the Customization page. |
2021-01-14 |
not yet calculated |
CVE-2020-29017
MISC |
| fortinet — fortiweb |
A stack-based buffer overflow vulnerability in FortiWeb 6.3.0 through 6.3.5 and version before 6.2.4 may allow an unauthenticated, remote attacker to overwrite the content of the stack and potentially execute arbitrary code by sending a crafted request with a large certname. |
2021-01-14 |
not yet calculated |
CVE-2020-29016
MISC |
fortinet — fortiweb
|
A stack-based buffer overflow vulnerability in FortiWeb 6.3.0 through 6.3.7 and version before 6.2.4 may allow a remote, unauthenticated attacker to crash the httpd daemon thread by sending a request with a crafted cookie header. |
2021-01-14 |
not yet calculated |
CVE-2020-29019
MISC |
fortinet — fortiweb
|
A format string vulnerability in FortiWeb 6.3.0 through 6.3.5 may allow an authenticated, remote attacker to read the content of memory and retrieve sensitive data via the redir parameter. |
2021-01-14 |
not yet calculated |
CVE-2020-29018
MISC |
fortinet — fortiweb
|
A blind SQL injection in the user interface of FortiWeb 6.3.0 through 6.3.7 and version before 6.2.4 may allow an unauthenticated, remote attacker to execute arbitrary SQL queries or commands by sending a request with a crafted Authorization header containing a malicious SQL statement. |
2021-01-14 |
not yet calculated |
CVE-2020-29015
MISC |
| git-big-picture — git-big-picture |
git-big-picture before 1.0.0 mishandles ‘ characters in a branch name, leading to code execution. |
2021-01-13 |
not yet calculated |
CVE-2021-3028
MISC
MISC
MISC |
| git-lfs — git-lfs |
Git LFS is a command line extension for managing large files with Git. On Windows, if Git LFS operates on a malicious repository with a git.bat or git.exe file in the current directory, that program would be executed, permitting the attacker to execute arbitrary code. This does not affect Unix systems. This is the result of an incomplete fix for CVE-2020-27955. This issue occurs because on Windows, Go includes (and prefers) the current directory when the name of a command run does not contain a directory separator. Other than avoiding untrusted repositories or using a different operating system, there is no workaround. This is fixed in v2.13.2. |
2021-01-15 |
not yet calculated |
CVE-2021-21237
MISC
MISC
MISC
CONFIRM |
| gitlab — gitlab |
A regular expression denial of service issue has been discovered in NuGet API affecting all versions of GitLab starting from version 12.8. |
2021-01-15 |
not yet calculated |
CVE-2021-22168
CONFIRM
MISC |
| gitlab — gitlab |
An attacker could cause a Prometheus denial of service in GitLab 13.7+ by sending an HTTP request with a malformed method |
2021-01-15 |
not yet calculated |
CVE-2021-22166
CONFIRM
MISC |
gitlab — gitlab
|
An issue has been discovered in GitLab affecting all versions starting from 12.4. The regex used for package names is written in a way that makes execution time have quadratic growth based on the length of the malicious input string. |
2021-01-15 |
not yet calculated |
CVE-2020-26414
CONFIRM
MISC |
gitlab — gitlab
|
An issue has been discovered in GitLab affecting all versions starting from 12.1. Incorrect headers in specific project page allows attacker to have a temporary read access to the private repository |
2021-01-15 |
not yet calculated |
CVE-2021-22167
CONFIRM
MISC
MISC |
gitlab — gitlab_pages
|
Insufficient validation of authentication parameters in GitLab Pages for GitLab 11.5+ allows an attacker to steal a victim’s API token if they click on a maliciously crafted link |
2021-01-15 |
not yet calculated |
CVE-2021-22171
CONFIRM
MISC
MISC |
google — chrome
|
Use after free in Media in Google Chrome prior to 81.0.4044.92 allowed a remote attacker to execute arbitrary code via a crafted HTML page. |
2021-01-14 |
not yet calculated |
CVE-2020-6572
MISC
MISC |
google — chrome_for_android
|
Use after Free in Payments in Google Chrome on Android prior to 87.0.4280.66 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. |
2021-01-14 |
not yet calculated |
CVE-2020-16045
MISC
MISC |
google — chrome_for_ios
|
Script injection in iOSWeb in Google Chrome on iOS prior to 84.0.4147.105 allowed a remote attacker to execute arbitrary code via a crafted HTML page. |
2021-01-14 |
not yet calculated |
CVE-2020-16046
MISC
MISC |
| html/java_api — html/java_api |
There exists a race condition between the deletion of the temporary file and the creation of the temporary directory in `webkit` subproject of HTML/Java API version 1.7. A similar vulnerability has recently been disclosed in other Java projects and the fix in HTML/Java API version 1.7.1 follows theirs: To avoid local privilege escalation version 1.7.1 creates the temporary directory atomically without dealing with the temporary file: https://github.com/apache/netbeans-html4j/commit/fa70e507e5555e1adb4f6518479fc408a7abd0e6 |
2021-01-11 |
not yet calculated |
CVE-2020-17534
MISC |
huawei — cloudengine
|
There is an out-of-bounds read vulnerability in Huawei CloudEngine products. The software reads data past the end of the intended buffer when parsing certain PIM message, an adjacent attacker could send crafted PIM messages to the device, successful exploit could cause out of bounds read when the system does the certain operation. |
2021-01-13 |
not yet calculated |
CVE-2020-1865
MISC |
huawei — multiple_products
|
There is an out-of-bounds read vulnerability in several products. The software reads data past the end of the intended buffer when parsing certain crafted DHCP messages. Successful exploit could cause certain service abnormal. Affected product versions include:NIP6800 versions V500R001C30,V500R001C60SPC500,V500R005C00;S12700 versions V200R008C00;S2700 versions V200R008C00;S5700 versions V200R008C00;S6700 versions V200R008C00;S7700 versions V200R008C00;S9700 versions V200R008C00;Secospace USG6600 versions V500R001C30SPC200,V500R001C30SPC600,V500R001C60SPC500,V500R005C00;USG9500 versions V500R001C30SPC300,V500R001C30SPC600,V500R001C60SPC500,V500R005C00. |
2021-01-13 |
not yet calculated |
CVE-2020-1866
MISC |
| huawei — multiple_smartphones |
There is an Out-of-bounds Write vulnerability in some Huawei smartphone. Successful exploitation of this vulnerability may cause out-of-bounds access to the physical memory. |
2021-01-13 |
not yet calculated |
CVE-2020-9145
MISC |
| huawei — multiple_smartphones |
There is a vulnerability with buffer access with incorrect length value in some Huawei Smartphone.Unauthorized users may trigger code execution when a buffer overflow occurs. |
2021-01-13 |
not yet calculated |
CVE-2020-9140
MISC |
huawei — multiple_smartphones
|
There is a improper input validation vulnerability in some Huawei Smartphone.Successful exploit of this vulnerability can cause memory access errors and denial of service. |
2021-01-13 |
not yet calculated |
CVE-2020-9139
MISC |
huawei — multiple_smartphones
|
There is a heap base buffer overflow vulnerability in some Huawei smartphone.Successful exploitation of this vulnerability can cause heap overflow and memory overwriting when the system incorrectly processes the update file. |
2021-01-13 |
not yet calculated |
CVE-2020-9142
MISC |
huawei — multiple_smartphones
|
There is a heap-based buffer overflow vulnerability in some Huawei Smartphone, Successful exploit of this vulnerability can cause process exceptions during updating. |
2021-01-13 |
not yet calculated |
CVE-2020-9138
MISC |
huawei — multiple_smartphones
|
There is a missing authentication vulnerability in some Huawei smartphone.Successful exploitation of this vulnerability may lead to low-sensitive information exposure. |
2021-01-13 |
not yet calculated |
CVE-2020-9143
MISC |
huawei — multiple_smartphones
|
There is a heap overflow vulnerability in some Huawei smartphone, attackers can exploit this vulnerability to cause heap overflows due to improper restriction of operations within the bounds of a memory buffer. |
2021-01-13 |
not yet calculated |
CVE-2020-9144
CONFIRM |
huawei — multiple_smartphones
|
There is a improper privilege management vulnerability in some Huawei smartphone. Successful exploitation of this vulnerability can cause information disclosure and malfunctions due to insufficient verification of data authenticity. |
2021-01-13 |
not yet calculated |
CVE-2020-9141
MISC |
huawei — p30
|
There is a resource management errors vulnerability in Huawei P30. Local attackers construct broadcast message for some application, causing this application to send this broadcast message and impact the customer’s use experience. |
2021-01-13 |
not yet calculated |
CVE-2020-9203
MISC |
huawei — smc
|
There is a privilege escalation vulnerability in SMC2.0 product. Some files in a directory of a module are located improperly. It does not apply the directory limitation. Attackers can exploit this vulnerability by crafting malicious file to launch privilege escalation. This can compromise normal service of affected products. |
2021-01-13 |
not yet calculated |
CVE-2020-9209
MISC |
| jenkins — jenkins |
Jenkins 2.274 and earlier, LTS 2.263.1 and earlier allows users with Agent/Configure permission to choose agent names that cause Jenkins to override the global `config.xml` file. |
2021-01-13 |
not yet calculated |
CVE-2021-21605
CONFIRM |
| jenkins — jenkins |
Jenkins Bumblebee HP ALM Plugin 4.1.5 and earlier stores credentials unencrypted in its global configuration file on the Jenkins controller where they can be viewed by users with access to the Jenkins controller file system. |
2021-01-13 |
not yet calculated |
CVE-2021-21614
CONFIRM |
jenkins — jenkins
|
Jenkins TICS Plugin 2020.3.0.6 and earlier does not escape TICS service responses, resulting in a cross-site scripting (XSS) vulnerability exploitable by attackers able to control TICS service response content. |
2021-01-13 |
not yet calculated |
CVE-2021-21613
CONFIRM |
jenkins — jenkins
|
Jenkins TraceTronic ECU-TEST Plugin 2.23.1 and earlier stores credentials unencrypted in its global configuration file on the Jenkins controller where they can be viewed by users with access to the Jenkins controller file system. |
2021-01-13 |
not yet calculated |
CVE-2021-21612
CONFIRM |
| joomla! — joomla! |
An issue was discovered in Joomla! 3.9.0 through 3.9.23. The lack of escaping in mod_breadcrumbs aria-label attribute allows XSS attacks. |
2021-01-12 |
not yet calculated |
CVE-2021-23124
MISC |
joomla! — joomla!
|
An issue was discovered in Joomla! 3.0.0 through 3.9.23. The lack of ACL checks in the orderPosition endpoint of com_modules leak names of unpublished and/or inaccessible modules. |
2021-01-12 |
not yet calculated |
CVE-2021-23123
MISC |
| jquery-validation — jquery-validation |
The jQuery Validation Plugin provides drop-in validation for your existing forms. It is published as an npm package “jquery-validation”. jquery-validation before version 1.19.3 contains one or more regular expressions that are vulnerable to ReDoS (Regular Expression Denial of Service). This is fixed in 1.19.3. |
2021-01-13 |
not yet calculated |
CVE-2021-21252
MISC
MISC
CONFIRM
MISC |
juniper_networks — contrail_networking
|
An Information Exposure vulnerability in Juniper Networks Contrail Networking allows a locally authenticated attacker able to read files to retrieve administrator credentials stored in plaintext thereby elevating their privileges over the system. This issue affects: Juniper Networks Contrail Networking versions prior to 1911.31. |
2021-01-15 |
not yet calculated |
CVE-2021-0212
CONFIRM |
juniper_networks — ex_and_qfx5k_series_platforms
|
On Juniper Networks EX and QFX5K Series platforms configured with Redundant Trunk Group (RTG), Storm Control profile applied on the RTG interface might not take affect when it reaches the threshold condition. Storm Control enables the device to monitor traffic levels and to drop broadcast, multicast, and unknown unicast packets when a specified traffic level is exceeded, thus preventing packets from proliferating and degrading the LAN. Note: this issue does not affect EX2200, EX3300, EX4200, and EX9200 Series. This issue affects Juniper Networks Junos OS on EX Series and QFX5K Series: 15.1 versions prior to 15.1R7-S7; 16.1 versions prior to 16.1R7-S8; 17.2 versions prior to 17.2R3-S4; 17.3 versions prior to 17.3R3-S8; 17.4 versions prior to 17.4R2-S11, 17.4R3-S2; 18.1 versions prior to 18.1R3-S10; 18.2 versions prior to 18.2R3-S5; 18.3 versions prior to 18.3R2-S4, 18.3R3-S2; 18.4 versions prior to 18.4R2-S5, 18.4R3-S3; 19.1 versions prior to 19.1R2-S2, 19.1R3-S2; 19.2 versions prior to 19.2R1-S5, 19.2R2-S1, 19.2R3; 19.3 versions prior to 19.3R2-S4, 19.3R3; 19.4 versions prior to 19.4R1-S3, 19.4R2-S1, 19.4R3; 20.1 versions prior to 20.1R1-S2, 20.1R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0203
CONFIRM |
juniper_networks — ex_and_qfx_series_switches
|
A vulnerability in processing of certain DHCP packets from adjacent clients on EX Series and QFX Series switches running Juniper Networks Junos OS with DHCP local/relay server configured may lead to exhaustion of DMA memory causing a Denial of Service (DoS). Over time, exploitation of this vulnerability may cause traffic to stop being forwarded, or to crashing of the fxpc process. When Packet DMA heap utilization reaches 99%, the system will become unstable. Packet DMA heap utilization can be monitored through the following command: user@junos# request pfe execute target fpc0 timeout 30 command “show heap” ID Base Total(b) Free(b) Used(b) % Name — ———- ———– ———– ———– — ———– 0 213301a8 536870488 387228840 149641648 27 Kernel 1 91800000 8388608 3735120 4653488 55 DMA 2 92000000 75497472 74452192 1045280 1 PKT DMA DESC 3 d330000 335544320 257091400 78452920 23 Bcm_sdk 4 96800000 184549376 2408 184546968 99 Packet DMA <— 5 903fffe0 20971504 20971504 0 0 Blob An indication of the issue occurring may be observed through the following log messages: Dec 10 08:07:00.124 2020 hostname fpc0 brcm_pkt_buf_alloc:523 (buf alloc) failed allocating packet buffer Dec 10 08:07:00.126 2020 hostname fpc0 (buf alloc) failed allocating packet buffer Dec 10 08:07:00.128 2020 hostname fpc0 brcm_pkt_buf_alloc:523 (buf alloc) failed allocating packet buffer Dec 10 08:07:00.130 2020 hostnameC fpc0 (buf alloc) failed allocating packet buffer This issue affects Juniper Networks Junos OS on EX Series and QFX Series: 17.4R3 versions prior to 17.4R3-S3; 18.1R3 versions between 18.1R3-S6 and 18.1R3-S11; 18.2R3 versions prior to 18.2R3-S6; 18.3R3 versions prior to 18.3R3-S4; 18.4R2 versions prior to 18.4R2-S5; 18.4R3 versions prior to 18.4R3-S6; 19.1 versions between 19.1R2 and 19.1R3-S3; 19.2 versions prior to 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3; 19.4 versions prior to 19.4R2-S2, 19.4R3; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R1-S2, 20.2R2. Junos OS versions prior to 17.4R3 are unaffected by this vulnerability. |
2021-01-15 |
not yet calculated |
CVE-2021-0217
CONFIRM |
|
juniper_networks — junos_os
|
In an EVPN/VXLAN scenario, if an IRB interface with a virtual gateway address (VGA) is configured on a PE, a traffic loop may occur upon receipt of specific IP multicast traffic. The traffic loop will cause interface traffic to increase abnormally, ultimately leading to a Denial of Service (DoS) in packet processing. The following command could be used to monitor the interface traffic: user@junos> monitor interface traffic Interface Link Input packets (pps) Output packets (pps) et-0/0/1 Up 6492089274364 (70994959) 6492089235319 (70994956) et-0/0/25 Up 343458103 (1) 156844 (0) ae0 Up 9132519197257 (70994959) 9132519139454 (70994956) This issue affects Juniper Networks Junos OS on QFX Series: all versions prior to 17.3R3-S10; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R3-S6; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R2-S5, 18.4R3-S5; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R1-S5, 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3; 19.4 versions prior to 19.4R2-S2, 19.4R3; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R1-S2, 20.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0221
CONFIRM |
|
juniper_networks — junos_os
|
A command injection vulnerability in install package validation subsystem of Juniper Networks Junos OS that may allow a locally authenticated attacker with privileges to execute commands with root privilege. To validate a package in Junos before installation, an administrator executes the command ‘request system software add validate-on-host’ via the CLI. An attacker with access to this CLI command may be able to exploit this vulnerability. This issue affects Juniper Networks Junos OS: all versions prior to 17.3R3-S10; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R2-S8, 18.2R3-S6; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R1-S8, 18.4R2-S7, 18.4R3-S6; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3-S1; 19.4 versions prior to 19.4R2-S2, 19.4R3-S1; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R1-S2, 20.2R2; 20.3 versions prior to 20.3R1-S1, 20.3R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0219
CONFIRM |
juniper_networks — junos_os
|
When the “Intrusion Detection Service” (IDS) feature is configured on Juniper Networks MX series with a dynamic firewall filter using IPv6 source or destination prefix, it may incorrectly match the prefix as /32, causing the filter to block unexpected traffic. This issue affects only IPv6 prefixes when used as source and destination. This issue affects MX Series devices using MS-MPC, MS-MIC or MS-SPC3 service cards with IDS service configured. This issue affects: Juniper Networks Junos OS 17.3 versions prior to 17.3R3-S10 on MX Series; 17.4 versions prior to 17.4R3-S3 on MX Series; 18.1 versions prior to 18.1R3-S11 on MX Series; 18.2 versions prior to 18.2R3-S6 on MX Series; 18.3 versions prior to 18.3R3-S4 on MX Series; 18.4 versions prior to 18.4R3-S6 on MX Series; 19.1 versions prior to 19.1R2-S2, 19.1R3-S3 on MX Series; 19.2 versions prior to 19.2R3-S1 on MX Series; 19.3 versions prior to 19.3R2-S5, 19.3R3-S1 on MX Series; 19.4 versions prior to 19.4R3 on MX Series; 20.1 versions prior to 20.1R2 on MX Series; 20.2 versions prior to 20.2R2 on MX Series; |
2021-01-15 |
not yet calculated |
CVE-2021-0205
CONFIRM |
juniper_networks — junos_os
|
A NULL Pointer Dereference vulnerability in Juniper Networks Junos OS allows an attacker to send a specific packet causing the packet forwarding engine (PFE) to crash and restart, resulting in a Denial of Service (DoS). By continuously sending these specific packets, an attacker can repeatedly disable the PFE causing a sustained Denial of Service (DoS). This issue only affects Juniper Networks NFX Series, SRX Series platforms when SSL Proxy is configured. This issue affects Juniper Networks Junos OS on NFX Series and SRX Series: 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R3-S1; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3; 19.2 versions prior to 19.2R1-S2, 19.2R2; 19.3 versions prior to 19.3R2. This issue does not affect Juniper Networks Junos OS versions on NFX Series and SRX Series prior to 18.3R1. |
2021-01-15 |
not yet calculated |
CVE-2021-0206
CONFIRM |
juniper_networks — junos_os
|
An improper interpretation conflict of certain data between certain software components within the Juniper Networks Junos OS devices does not allow certain traffic to pass through the device upon receipt from an ingress interface filtering certain specific types of traffic which is then being redirected to an egress interface on a different VLAN. This causes a Denial of Service (DoS) to those clients sending these particular types of traffic. Such traffic being sent by a client may appear genuine, but is non-standard in nature and should be considered as potentially malicious, and can be targeted to the device, or destined through it for the issue to occur. This issues affects IPv4 and IPv6 traffic. An indicator of compromise may be found by checking log files. You may find that traffic on the input interface has 100% of traffic flowing into the device, yet the egress interface shows 0 pps leaving the device. For example: [show interfaces “interface” statistics detail] Output between two interfaces would reveal something similar to: Ingress, first interface: ——————– Interface Link Input packets (pps) Output packets (pps) et-0/0/0 Up 9999999999 (9999) 1 (0) ——————– Egress, second interface: ——————– Interface Link Input packets (pps) Output packets (pps) et-0/0/1 Up 0 (0) 9999999999 (0) ——————– Dropped packets will not show up in DDoS monitoring/protection counters as issue is not caused by anti-DDoS protection mechanisms. This issue affects: Juniper Networks Junos OS: 17.3 versions prior to 17.3R3-S7 on NFX250, QFX5K Series, EX4600; 17.4 versions prior to 17.4R2-S11, 17.4R3-S3 on NFX250, QFX5K Series, EX4600; 18.1 versions prior to 18.1R3-S9 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4600; 18.2 versions prior to 18.2R3-S3 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600; 18.3 versions prior to 18.3R3-S1 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series; 18.4 versions prior to 18.4R1-S5, 18.4R2-S3, 18.4R3 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series; 19.1 versions prior to 19.1R1-S5, 19.1R2-S1, 19.1R3 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series; 19.2 versions prior to 19.2R1-S5, 19.2R2 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series; 19.3 versions prior to 19.3R2-S3, 19.3R3 on NFX250, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series; 19.4 versions prior to 19.4R1-S2, 19.4R2 on NFX250, NFX350, QFX5K Series, EX2300 Series, EX3400 Series, EX4300 Multigigabit, EX4600 Series. This issue does not affect Junos OS releases prior to 17.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0207
CONFIRM |
juniper_networks — junos_os
|
An improper input validation vulnerability in the Routing Protocol Daemon (RPD) service of Juniper Networks Junos OS allows an attacker to send a malformed RSVP packet when bidirectional LSPs are in use, which when received by an egress router crashes the RPD causing a Denial of Service (DoS) condition. Continued receipt of the packet will sustain the Denial of Service. This issue affects: Juniper Networks Junos OS: All versions prior to 17.3R3-S10 except 15.1X49-D240 for SRX series; 17.4 versions prior to 17.4R3-S2; 18.1 versions prior to 18.1R3-S10; 18.2 versions prior to 18.2R2-S7, 18.2R3-S4; 18.3 versions prior to 18.3R3-S2; 18.4 versions prior to 18.4R1-S8, 18.4R2-S6, 18.4R3-S2; 19.1 versions prior to 19.1R1-S5, 19.1R3-S3; 19.2 versions prior to 19.2R3; 19.3 versions prior to 19.3R2-S5, 19.3R3; 19.4 versions prior to 19.4R2-S2, 19.4R3-S1; 20.1 versions prior to 20.1R1-S4, 20.1R2; 15.1X49 versions prior to 15.1X49-D240 on SRX Series. Juniper Networks Junos OS Evolved: 19.3 versions prior to 19.3R2-S5-EVO; 19.4 versions prior to 19.4R2-S2-EVO; 20.1 versions prior to 20.1R1-S4-EVO. |
2021-01-15 |
not yet calculated |
CVE-2021-0208
CONFIRM
MISC
MISC |
juniper_networks — junos_os
|
A command injection vulnerability in the license-check daemon of Juniper Networks Junos OS that may allow a locally authenticated attacker with low privileges to execute commands with root privilege. license-check is a daemon used to manage licenses in Junos OS. To update licenses, a user executes the command ‘request system license update’ via the CLI. An attacker with access to this CLI command may be able to exploit the vulnerability. This issue affects Juniper Networks Junos OS: 17.3 versions prior to 17.3R3-S9; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R3-S6; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R3-S6; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3; 19.4 versions prior to 19.4R2-S2, 19.4R3; 20.1 versions prior to 20.1R1-S4, 20.1R2; 20.2 versions prior to 20.2R1-S2, 20.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0218
CONFIRM |
juniper_networks — junos_os
|
An Information Exposure vulnerability in J-Web of Juniper Networks Junos OS allows an unauthenticated attacker to elevate their privileges over the target system through opportunistic use of an authenticated users session. This issue affects: Juniper Networks Junos OS 12.3 versions prior to 12.3R12-S17; 17.3 versions prior to 17.3R3-S10; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R3-S6; 18.3 versions prior to 18.3R2-S4, 18.3R3-S4; 18.4 versions prior to 18.4R2-S5, 18.4R3-S5; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R1-S5, 19.2R3, 19.2R3-S1; 19.3 versions prior to 19.3R2-S4, 19.3R3; 19.4 versions prior to 19.4R1-S3, 19.4R2-S2, 19.4R3; 20.1 versions prior to 20.1R1-S4, 20.1R2; 20.2 versions prior to 20.2R1-S1, 20.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0210
CONFIRM |
juniper_networks — junos_os
|
A sensitive information disclosure vulnerability in delta-export configuration utility (dexp) of Juniper Networks Junos OS may allow a locally authenticated shell user the ability to create and read database files generated by the dexp utility, including password hashes of local users. Since dexp is shipped with setuid permissions enabled and is owned by the root user, this vulnerability may allow a local privileged user the ability to run dexp with root privileges and access sensitive information in the dexp database. This issue affects Juniper Networks Junos OS: 15.1 versions prior to 15.1R7-S8; 15.1X49 versions prior to 15.1X49-D230; 17.3 versions prior to 17.3R3-S9; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R3-S6; 18.2X75 versions prior to 18.2X75-D34; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R2-S7, 18.4R3-S6; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R1-S5, 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3-S1; 19.4 versions prior to 19.4R1-S3, 19.4R2-S2, 19.4R3-S1; 20.1 versions prior to 20.1R1-S4, 20.1R2; 20.2 versions prior to 20.2R1-S2, 20.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0204
CONFIRM |
|
juniper_networks — junos_os_and_junos_os_evolved_routing_protocol_daemon
|
An improper check for unusual or exceptional conditions in Juniper Networks Junos OS and Junos OS Evolved Routing Protocol Daemon (RPD) service allows an attacker to send a valid BGP FlowSpec message thereby causing an unexpected change in the route advertisements within the BGP FlowSpec domain leading to disruptions in network traffic causing a Denial of Service (DoS) condition. Continued receipt of these update messages will cause a sustained Denial of Service condition. This issue affects Juniper Networks: Junos OS: All versions prior to 17.3R3-S10 with the exceptions of 15.1X49-D240 on SRX Series and 15.1R7-S8 on EX Series; 17.3 versions prior to 17.3R3-S10; 17.4 versions prior to 17.4R2-S12, 17.4R3-S4; 18.1 versions prior to 18.1R3-S12; 18.2 versions prior to 18.2R2-S8, 18.2R3-S6; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R1-S8, 18.4R2-S6, 18.4R3-S6; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S3; 19.2 versions prior to 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3-S1; 19.4 versions prior to 19.4R1-S3, 19.4R2-S3, 19.4R3; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R1-S3 20.2R2; 20.3 versions prior to 20.3R1-S1, 20.3R2. Junos OS Evolved: All versions prior to 20.3R1-S1-EVO, 20.3R2-EVO. |
2021-01-15 |
not yet calculated |
CVE-2021-0211
CONFIRM |
juniper_networks — junos_os_evolved
|
In Juniper Networks Junos OS Evolved an attacker sending certain valid BGP update packets may cause Junos OS Evolved to access an uninitialized pointer causing RPD to core leading to a Denial of Service (DoS). Continued receipt of these types of valid BGP update packets will cause an extended Denial of Service condition. RPD will require a restart to recover. An indicator of compromise is to see if the file rpd.re exists by issuing the command: show system core-dumps This issue affects: Juniper Networks Junos OS Evolved 19.4 versions prior to 19.4R2-S2-EVO; 20.1 versions prior to 20.1R1-S2-EVO, 20.1R2-S1-EVO. This issue does not affect Junos OS. |
2021-01-15 |
not yet calculated |
CVE-2021-0209
CONFIRM |
|
juniper_networks — junos_os
|
A local privilege escalation vulnerability in telnetd.real of Juniper Networks Junos OS may allow a locally authenticated shell user to escalate privileges and execute arbitrary commands as root. telnetd.real is shipped with setuid permissions enabled and is owned by the root user, allowing local users to run telnetd.real with root privileges. This issue affects Juniper Networks Junos OS: all versions prior to 15.1R7-S9; 17.3 versions prior to 17.3R3-S11; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R3-S6; 18.3 versions prior to 18.3R2-S4, 18.3R3-S4; 18.4 versions prior to 18.4R2-S7, 18.4R3-S6; 19.1 versions prior to 19.1R2-S2, 19.1R3-S4; 19.2 versions prior to 19.2R1-S6, 19.2R3-S1; 19.3 versions prior to 19.3R3-S1; 19.4 versions prior to 19.4R2-S2, 19.4R3; 20.1 versions prior to 20.1R1-S4, 20.1R2; 20.2 versions prior to 20.2R2. |
2021-01-15 |
not yet calculated |
CVE-2021-0223
CONFIRM |
|
juniper_networks — junos_os
|
A vulnerability in Juniper Networks Junos OS allows an attacker to cause a Denial of Service (DoS) to the device by sending certain crafted protocol packets from an adjacent device with invalid payloads to the device. These crafted packets, which should be discarded, are instead replicated and sent to the RE. Over time, a Denial of Service (DoS) occurs. Continued receipt of these crafted protocol packets will cause an extended Denial of Service (DoS) condition, which may cause wider traffic impact due to protocol flapping. An indication of compromise is to check “monitor interface traffic” on the ingress and egress port packet counts. For each ingress packet, two duplicate packets are seen on egress. This issue can be triggered by IPv4 and IPv6 packets. This issue affects all traffic through the device. This issue affects: Juniper Networks Junos OS: 14.1X53 versions prior to 14.1X53-D53 on EX4300, QFX3500, QFX5100, EX4600; 15.1 versions prior to 15.1R7-S6 on EX4300, QFX3500, QFX5100, EX4600; 16.1 versions prior to 16.1R7-S7 on EX4300, QFX5100, EX4600; 17.1 versions prior to 17.1R2-S11 on EX4300, QFX5100, EX4600; 17.1 versions prior to 117.1R3-S2 on EX4300; 17.2 versions prior to 17.2R1-S9 on EX4300; 17.2 versions prior to 17.2R3-S3 on EX4300, QFX5100, EX4600, QFX5110, QFX5200; 17.3 versions prior to 17.3R2-S5, 17.3R3-S7 on EX4300, QFX5100, EX4600, QFX5110, QFX5200; 17.4 versions prior to 17.4R2-S9, 17.4R3 on EX4300, QFX5100, EX4600, QFX5110, QFX5200; 18.1 versions prior to 18.1R3-S9 on EX4300, QFX5100, EX4600, QFX5110, QFX5200, QFX5210, EX2300, EX3400; 18.2 versions prior to 18.2R2-S7 on EX4300; 18.2 versions prior to 18.2R3-S3 on EX4300, QFX5100, EX4600, QFX5110, QFX5200, QFX5210, EX2300, EX3400; 18.3 versions prior to 18.3R2-S3, on EX4300; 18.3 versions prior to 18.3R1-S7, 18.3R3-S1 on EX4300, QFX5100, EX4600, QFX5110, QFX5200, QFX5210, QFX5120, EX4650, EX2300, EX3400; 18.4 versions prior to 18.4R1-S5, 18.4R2-S3, 18.4R3 on EX4300, QFX5100, EX4600, QFX5110, QFX5200, QFX5210, QFX5120, EX4650, EX2300, EX3400; 19.1 versions prior to 19.1R1-S4, 19.1R2-S1, 19.1R3 on EX4300, QFX5100, EX4600, QFX5110, QFX5200, QFX5210, QFX5120, EX4650, EX2300, EX3400; 19.2 versions prior to 19.2R1-S4, 19.2R2 on EX4300; 19.2 versions prior to 19.2R1-S3, 19.2R2 on QFX5100, EX4600, QFX5110, QFX5200, QFX5210, QFX5120, EX4650, EX2300, EX3400; 19.3 versions prior to 19.3R2-S1, 19.3R3 on EX4300; 19.3 versions prior to 19.3R1-S1, 19.3R2, 19.3R3 on QFX5100, EX4600, QFX5110, QFX5200, QFX5210, QFX5120, EX4650, EX2300, EX3400; |
2021-01-15 |
not yet calculated |
CVE-2021-0222
CONFIRM |
juniper_networks — multiple_products
|
On Juniper Networks Junos EX series, QFX Series and SRX branch series devices, a memory leak occurs every time the 802.1X authenticator port interface flaps which can lead to other processes, such as the pfex process, responsible for packet forwarding, to crash and restart. An administrator can use the following CLI command to monitor the status of memory consumption: user@device> show task memory detail Please refer to https://kb.juniper.net/KB31522 for details. This issue affects Juniper Networks Junos OS: 14.1X53 versions prior to 14.1X53-D54; 15.1X49 versions prior to 15.1X49-D240 ; 15.1X53 versions prior to 15.1X53-D593; 16.1 versions prior to 16.1R7-S8; 17.2 versions prior to 17.2R3-S4; 17.3 versions prior to 17.3R3-S8; 17.4 versions prior to 17.4R2-S11, 17.4R3-S2; 18.1 versions prior to 18.1R3-S10 ; 18.2 versions prior to 18.2R2-S7, 18.2R3-S3; 18.3 versions prior to 18.3R2-S4, 18.3R3-S2; 18.4 versions prior to 18.4R1-S7, 18.4R2-S4, 18.4R3-S2; 19.1 versions prior to 19.1R1-S5, 19.1R2-S2, 19.1R3; 19.2 versions prior to 19.2R1-S5, 19.2R2; 19.3 versions prior to 19.3R2-S3, 19.3R3; 19.4 versions prior to 19.4R1-S2, 19.4R2. This issue does not affect Juniper Networks Junos OS 12.3, 15.1. |
2021-01-15 |
not yet calculated |
CVE-2021-0215
CONFIRM |
juniper_networks — mx_and_ex9200_series_platforms
|
On Juniper Networks MX Series and EX9200 Series platforms with Trio-based MPC (Modular Port Concentrator) where Integrated Routing and Bridging (IRB) interface is configured and it is mapped to a VPLS instance or a Bridge-Domain, certain network events at Customer Edge (CE) device may cause memory leak in the MPC which can cause an out of memory and MPC restarts. When this issue occurs, there will be temporary traffic interruption until the MPC is restored. An administrator can use the following CLI command to monitor the status of memory usage level of the MPC: user@device> show system resource-monitor fpc FPC Resource Usage Summary Free Heap Mem Watermark : 20 % Free NH Mem Watermark : 20 % Free Filter Mem Watermark : 20 % * – Watermark reached Slot # % Heap Free RTT Average RTT 1 87 PFE # % ENCAP mem Free % NH mem Free % FW mem Free 0 NA 88 99 1 NA 89 99 When the issue is occurring, the value of “% NH mem Free” will go down until the MPC restarts. This issue affects MX Series and EX9200 Series with Trio-based PFEs (Packet Forwarding Engines). Please refer to https://kb.juniper.net/KB25385 for the list of Trio-based PFEs. This issue affects Juniper Networks Junos OS on MX Series, EX9200 Series: 17.3R3-S8; 17.4R3-S2; 18.2R3-S4, 18.2R3-S5; 18.3R3-S2, 18.3R3-S3; 18.4 versions starting from 18.4R3-S1 and later versions prior to 18.4R3-S6; 19.2 versions starting from 19.2R2 and later versions prior to 19.2R3-S1; 19.4 versions starting from 19.4R2 and later versions prior to 19.4R2-S3, 19.4R3; 20.2 versions starting from 20.2R1 and later versions prior to 20.2R1-S3, 20.2R2. This issue does not affect Juniper Networks Junos OS: 18.1, 19.1, 19.3, 20.1. |
2021-01-15 |
not yet calculated |
CVE-2021-0202
CONFIRM |
|
juniper_networks — space_network_management_platform
|
The Junos Space Network Management Platform has been found to store shared secrets in a recoverable format that can be exposed through the UI. An attacker who is able to execute arbitrary code in the victim browser (for example via XSS) or access cached contents may be able to obtain a copy of credentials managed by Junos Space. The impact of a successful attack includes, but is not limited to, obtaining access to other servers connected to the Junos Space Management Platform. This issue affects Juniper Networks Junos Space versions prior to 20.3R1. |
2021-01-15 |
not yet calculated |
CVE-2021-0220
CONFIRM |
jupyterhub — jupyterhub
|
JupyterHub 1.1.0 allows CSRF in the admin panel via a request that lacks an _xsrf field, as demonstrated by a /hub/api/user request (to add or remove a user account). |
2021-01-13 |
not yet calculated |
CVE-2020-36191
MISC
MISC |
linux — linux_kernel
|
In drivers/target/target_core_xcopy.c in the Linux kernel before 5.10.7, insufficient identifier checking in the LIO SCSI target code can be used by remote attackers to read or write files via directory traversal in an XCOPY request, aka CID-2896c93811e3. For example, an attack can occur over a network if the attacker has access to one iSCSI LUN. The attacker gains control over file access because I/O operations are proxied via an attacker-selected backstore. |
2021-01-13 |
not yet calculated |
CVE-2020-28374
MLIST
MLIST
MISC
MISC
CONFIRM
CONFIRM
CONFIRM
FEDORA
FEDORA |
| loxone — miniserver |
Loxone Miniserver devices with firmware before 11.1 (aka 11.1.9.3) are unable to use an authentication method that is based on the “signature of the update package.” Therefore, these devices (or attackers who are spoofing these devices) can continue to use an unauthenticated cloud service for an indeterminate time period (possibly forever). Once an individual device’s firmware is updated, and authentication occurs once, the cloud service recategorizes the device so that authentication is subsequently always required, and spoofing cannot occur. |
2021-01-13 |
not yet calculated |
CVE-2020-27488
MISC
MISC
MISC
MISC |
m2crypto — m2crypto
|
A flaw was found in all released versions of m2crypto, where they are vulnerable to Bleichenbacher timing attacks in the RSA decryption API via the timed processing of valid PKCS#1 v1.5 Ciphertext. The highest threat from this vulnerability is to confidentiality. |
2021-01-12 |
not yet calculated |
CVE-2020-25657
MISC |
malwarebytes — malwarebytes
|
An issue was discovered in Malwarebytes before 4.0 on macOS. A malicious application was able to perform a privileged action within the Malwarebytes launch daemon. The privileged service improperly validated XPC connections by relying on the PID instead of the audit token. An attacker can construct a situation where the same PID is used for running two different programs at different times, by leveraging a race condition during crafted use of posix_spawn. |
2021-01-15 |
not yet calculated |
CVE-2020-25533
MISC |
| microsoft — azure_kubernetes_service |
Azure Active Directory Pod Identity Spoofing Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1677
MISC |
| microsoft — edge_(edgehtml-based) |
Microsoft Edge (HTML-based) Memory Corruption Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1705
MISC |
| microsoft — multiple_products |
Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1651. |
2021-01-12 |
not yet calculated |
CVE-2021-1680
MISC |
| microsoft — multiple_products |
Microsoft Office Remote Code Execution Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1711
MISC |
| microsoft — multiple_sharepoint_products |
Microsoft SharePoint Server Remote Code Execution Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1707
MISC |
| microsoft — multiple_windows_products |
Windows Projected File System FS Filter Driver Information Disclosure Vulnerability This CVE ID is unique from CVE-2021-1663, CVE-2021-1672. |
2021-01-12 |
not yet calculated |
CVE-2021-1670
MISC |
| microsoft — multiple_windows_products |
Windows Installer Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1661
MISC |
| microsoft — multiple_windows_products |
Windows Event Tracing Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1662
MISC |
| microsoft — multiple_windows_products |
Windows Projected File System FS Filter Driver Information Disclosure Vulnerability This CVE ID is unique from CVE-2021-1670, CVE-2021-1672. |
2021-01-12 |
not yet calculated |
CVE-2021-1663
MISC |
| microsoft — multiple_windows_products |
Windows WalletService Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1681, CVE-2021-1687, CVE-2021-1690. |
2021-01-12 |
not yet calculated |
CVE-2021-1686
MISC |
| microsoft — multiple_windows_products |
GDI+ Remote Code Execution Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1665
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1666
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1667
MISC |
| microsoft — multiple_windows_products |
Microsoft DTV-DVD Video Decoder Remote Code Execution Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1668
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1664
MISC |
| microsoft — multiple_windows_products |
Windows Bluetooth Security Feature Bypass Vulnerability This CVE ID is unique from CVE-2021-1638, CVE-2021-1684. |
2021-01-12 |
not yet calculated |
CVE-2021-1683
MISC |
| microsoft — multiple_windows_products |
TPM Device Driver Information Disclosure Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1656
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1671
MISC |
| microsoft — multiple_windows_products |
Windows AppX Deployment Extensions Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1642. |
2021-01-12 |
not yet calculated |
CVE-2021-1685
MISC
MISC |
| microsoft — multiple_windows_products |
Windows WalletService Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1686, CVE-2021-1687, CVE-2021-1690. |
2021-01-12 |
not yet calculated |
CVE-2021-1681
MISC |
| microsoft — multiple_windows_products |
Windows Kernel Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1682
MISC |
| microsoft — multiple_windows_products |
NTLM Security Feature Bypass Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1678
MISC |
| microsoft — multiple_windows_products |
Windows NT Lan Manager Datagram Receiver Driver Information Disclosure Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1676
MISC |
| microsoft — multiple_windows_products |
Windows Remote Desktop Protocol Core Security Feature Bypass Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1674
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1673
MISC |
| microsoft — multiple_windows_products |
Windows Bluetooth Security Feature Bypass Vulnerability This CVE ID is unique from CVE-2021-1638, CVE-2021-1683. |
2021-01-12 |
not yet calculated |
CVE-2021-1684
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1658
MISC |
| microsoft — multiple_windows_products |
Windows CryptoAPI Denial of Service Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1679
MISC |
| microsoft — multiple_windows_products |
Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1680. |
2021-01-12 |
not yet calculated |
CVE-2021-1651
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700. |
2021-01-12 |
not yet calculated |
CVE-2021-1701
MISC |
| microsoft — multiple_windows_products |
Windows Remote Desktop Security Feature Bypass Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1669
MISC |
| microsoft — multiple_windows_products |
Windows Graphics Component Information Disclosure Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1696
MISC |
| microsoft — multiple_windows_products |
Windows Print Spooler Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1695
MISC
MISC |
| microsoft — multiple_windows_products |
Windows CSC Service Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1652, CVE-2021-1653, CVE-2021-1654, CVE-2021-1655, CVE-2021-1659, CVE-2021-1688. |
2021-01-12 |
not yet calculated |
CVE-2021-1693
MISC |
| microsoft — multiple_windows_products |
Windows Update Stack Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1694
MISC |
| microsoft — multiple_windows_products |
Windows WalletService Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1681, CVE-2021-1686, CVE-2021-1687. |
2021-01-12 |
not yet calculated |
CVE-2021-1690
MISC |
| microsoft — multiple_windows_products |
Hyper-V Denial of Service Vulnerability This CVE ID is unique from CVE-2021-1692. |
2021-01-12 |
not yet calculated |
CVE-2021-1691
MISC |
| microsoft — multiple_windows_products |
Hyper-V Denial of Service Vulnerability This CVE ID is unique from CVE-2021-1691. |
2021-01-12 |
not yet calculated |
CVE-2021-1692
MISC |
| microsoft — multiple_windows_products |
Windows Projected File System FS Filter Driver Information Disclosure Vulnerability This CVE ID is unique from CVE-2021-1663, CVE-2021-1670. |
2021-01-12 |
not yet calculated |
CVE-2021-1672
MISC |
| microsoft — multiple_windows_products |
Windows (modem.sys) Information Disclosure Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1699
MISC |
| microsoft — multiple_windows_products |
Windows InstallService Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1697
MISC
MISC |
| microsoft — multiple_windows_products |
Windows Remote Procedure Call Runtime Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1702
MISC |
| microsoft — multiple_windows_products |
Windows Event Logging Service Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1703
MISC |
| microsoft — multiple_windows_products |
Windows Hyper-V Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1704
MISC |
| microsoft — multiple_windows_products |
Windows LUAFV Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1706
MISC |
| microsoft — multiple_windows_products |
Windows GDI+ Information Disclosure Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1708
MISC |
| microsoft — multiple_windows_products |
Windows WalletService Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1681, CVE-2021-1686, CVE-2021-1690. |
2021-01-12 |
not yet calculated |
CVE-2021-1687
MISC |
| microsoft — multiple_windows_products |
Windows Win32k Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1709
MISC |
| microsoft — multiple_windows_products |
Microsoft Windows Media Foundation Remote Code Execution Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1710
MISC |
| microsoft — multiple_windows_products |
Windows CSC Service Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1652, CVE-2021-1653, CVE-2021-1654, CVE-2021-1655, CVE-2021-1659, CVE-2021-1693. |
2021-01-12 |
not yet calculated |
CVE-2021-1688
MISC |
| microsoft — multiple_windows_products |
Windows Multipoint Management Elevation of Privilege Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1689
MISC |
| microsoft — multiple_windows_products |
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1700
MISC |
microsoft — multiple_windows_products
|
Windows CSC Service Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1652, CVE-2021-1653, CVE-2021-1654, CVE-2021-1655, CVE-2021-1688, CVE-2021-1693. |
2021-01-12 |
not yet calculated |
CVE-2021-1659
MISC |
microsoft — multiple_windows_products
|
Remote Procedure Call Runtime Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-1658, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700, CVE-2021-1701. |
2021-01-12 |
not yet calculated |
CVE-2021-1660
MISC |
| microsoft — sharepoint_foundation_2010 |
Microsoft SharePoint Server Tampering Vulnerability |
2021-01-12 |
not yet calculated |
CVE-2021-1718
MISC |
|
microsoft — sharepoint_server_2019_and_sharepoint_enterprise_server_2016
|
Microsoft SharePoint Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-1712. |
2021-01-12 |
not yet calculated |
CVE-2021-1719
MISC |
| mubu — mubu |
Mubu 2.2.1 allows local users to gain privileges to execute commands, aka CNVD-2020-68878. |
2021-01-12 |
not yet calculated |
CVE-2021-3134
MISC
MISC |
| nagios — nagios_xi |
An issue was discovered in the Manage Plugins page in Nagios XI before 5.8.0. Because the line-ending conversion feature is mishandled during a plugin upload, a remote, authenticated admin user can execute operating-system commands. |
2021-01-13 |
not yet calculated |
CVE-2020-35578
MISC
MISC
CONFIRM |
nec — multiple_products
|
Multiple NEC products (Express5800/T110j, Express5800/T110j-S, Express5800/T110j (2nd-Gen), Express5800/T110j-S (2nd-Gen), iStorage NS100Ti, and Express5800/GT110j) where Baseboard Management Controller (BMC) firmware Rev1.09 and earlier is applied allows remote attackers to bypass authentication and then obtain/modify BMC setting information, obtain monitoring information, or reboot/shut down the vulnerable product via unspecified vectors. |
2021-01-13 |
not yet calculated |
CVE-2020-5633
MISC
MISC
MISC |
nec — univerge_sv9500_and_sv8500_sercies
|
Incorrect implementation of authentication algorithm issue in UNIVERGE SV9500 series from V1 to V7and SV8500 series from S6 to S8 allows an attacker to access the remote system maintenance feature and obtain the information by sending a specially crafted request to a specific URL. |
2021-01-13 |
not yet calculated |
CVE-2020-5686
MISC
MISC |
nec — univerge_sv9500_and_sv8500_sercies
|
UNIVERGE SV9500 series from V1 to V7and SV8500 series from S6 to S8 allows an attacker to execute arbitrary OS commands or cause a denial-of-service (DoS) condition by sending a specially crafted request to a specific URL. |
2021-01-13 |
not yet calculated |
CVE-2020-5685
MISC
MISC |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, there is a critical vulnerability which can lead to pre-auth remote code execution. AttachmentUploadServlet deserializes untrusted data from the `Attachment-Support` header. This Servlet does not enforce any authentication or authorization checks. This issue may lead to pre-auth remote code execution. This issue was fixed in 4.0.3 by removing AttachmentUploadServlet and not using deserialization |
2021-01-15 |
not yet calculated |
CVE-2021-21242
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, a Kubernetes REST endpoint exposes two methods that deserialize untrusted data from the request body. These endpoints do not enforce any authentication or authorization checks. This issue may lead to pre-auth RCE. This issue was fixed in 4.0.3 by not using deserialization at KubernetesResource side. |
2021-01-15 |
not yet calculated |
CVE-2021-21243
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, the REST UserResource endpoint performs a security check to make sure that only administrators can list user details. However for the `/users/{id}` endpoint there are no security checks enforced so it is possible to retrieve arbitrary user details including their Access Tokens! These access tokens can be used to access the API or clone code in the build spec via the HTTP(S) protocol. It has permissions to all projects accessible by the user account. This issue may lead to `Sensitive data leak` and leak the Access Token which can be used to impersonate the administrator or any other users. This issue was addressed in 4.0.3 by removing user info from restful api. |
2021-01-15 |
not yet calculated |
CVE-2021-21246
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, AttachmentUploadServlet also saves user controlled data (`request.getInputStream()`) to a user specified location (`request.getHeader(“File-Name”)`). This issue may lead to arbitrary file upload which can be used to upload a WebShell to OneDev server. This issue is addressed in 4.0.3 by only allowing uploaded file to be in attachments folder. The webshell issue is not possible as OneDev never executes files in attachments folder. |
2021-01-15 |
not yet calculated |
CVE-2021-21245
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, There is a vulnerability that enabled pre-auth server side template injection via Bean validation message tampering. Full details in the reference GHSA. This issue was fixed in 4.0.3 by disabling validation interpolation completely. |
2021-01-15 |
not yet calculated |
CVE-2021-21244
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, the application’s BasePage registers an AJAX event listener (`AbstractPostAjaxBehavior`) in all pages other than the login page. This listener decodes and deserializes the `data` query parameter. We can access this listener by submitting a POST request to any page. This issue may lead to `post-auth RCE` This endpoint is subject to authentication and, therefore, requires a valid user to carry on the attack. This issue was addressed in 4.0.3 by encrypting serialization payload with secrets only known to server. |
2021-01-15 |
not yet calculated |
CVE-2021-21247
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, there is a critical vulnerability involving the build endpoint parameters. InputSpec is used to define parameters of a Build spec. It does so by using dynamically generated Groovy classes. A user able to control job parameters can run arbitrary code on OneDev’s server by injecting arbitrary Groovy code. The ultimate result is in the injection of a static constructor that will run arbitrary code. For a full example refer to the referenced GHSA. This issue was addressed in 4.0.3 by escaping special characters such as quote from user input. |
2021-01-15 |
not yet calculated |
CVE-2021-21248
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, there is an issue involving YAML parsing which can lead to post-auth remote code execution. In order to parse and process YAML files, OneDev uses SnakeYaml which by default (when not using `SafeConstructor`) allows the instantiation of arbitrary classes. We can leverage that to run arbitrary code by instantiating classes such as `javax.script.ScriptEngineManager` and using `URLClassLoader` to load the script engine provider, resulting in the instantiation of a user controlled class. For a full example refer to the referenced GHSA. This issue was addressed in 4.0.3 by only allowing certain known classes to be deserialized |
2021-01-15 |
not yet calculated |
CVE-2021-21249
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3, there is a critical vulnerability which may lead to arbitrary file read. When BuildSpec is provided in XML format, the spec is processed by XmlBuildSpecMigrator.migrate(buildSpecString); which processes the XML document without preventing the expansion of external entities. These entities can be configured to read arbitrary files from the file system and dump their contents in the final XML document to be migrated. If the files are dumped in properties included in the YAML file, it will be possible for an attacker to read them. If not, it is possible for an attacker to exfiltrate the contents of these files Out Of Band. This issue was addressed in 4.0.3 by ignoring ENTITY instructions in xml file. |
2021-01-15 |
not yet calculated |
CVE-2021-21250
MISC
CONFIRM |
onedev — onedev
|
OneDev is an all-in-one devops platform. In OneDev before version 4.0.3 there is a critical “zip slip” vulnerability. This issue may lead to arbitrary file write. The KubernetesResource REST endpoint untars user controlled data from the request body using TarUtils. TarUtils is a custom library method leveraging Apache Commons Compress. During the untar process, there are no checks in place to prevent an untarred file from traversing the file system and overriding an existing file. For a successful exploitation, the attacker requires a valid __JobToken__ which may not be possible to get without using any of the other reported vulnerabilities. But this should be considered a vulnerability in `io.onedev.commons.utils.TarUtils` since it lives in a different artifact and can affect other projects using it. This issue was addressed in 4.0.3 by validating paths in tar archive to only allow them to be in specified folder when extracted. |
2021-01-15 |
not yet calculated |
CVE-2021-21251
CONFIRM |
open-iscsi — tcmu-runner
|
In Open-iSCSI tcmu-runner 1.3.x, 1.4.x, and 1.5.x through 1.5.2, xcopy_locate_udev in tcmur_cmd_handler.c lacks a check for transport-layer restrictions, allowing remote attackers to read or write files via directory traversal in an XCOPY request. For example, an attack can occur over a network if the attacker has access to one iSCSI LUN. NOTE: relative to CVE-2020-28374, this is a similar mistake in a different algorithm. |
2021-01-13 |
not yet calculated |
CVE-2021-3139
MLIST
MISC
MISC
CONFIRM
MISC |
| opera — opera_mini_for_android |
Opera Mini for Android below 53.1 displays URL left-aligned in the address field. This allows a malicious attacker to craft a URL with a long domain name, e.g. www.safe.opera.com.attacker.com. With the URL being left-aligned, the user will only see the front part (e.g. www.safe.opera.com…) The exact amount depends on the phone screen size but the attacker can craft a number of different domains and target different phones. Starting with version 53.1 Opera Mini displays long URLs with the top-level domain label aligned to the right of the address field which mitigates the issue. |
2021-01-11 |
not yet calculated |
CVE-2021-23253
CONFIRM |
| owasp — json-sanitizer |
OWASP json-sanitizer before 1.2.2 can output invalid JSON or throw an undeclared exception for crafted input. This may lead to denial of service if the application is not prepared to handle these situations. |
2021-01-13 |
not yet calculated |
CVE-2021-23900
MISC
MISC
MISC |
| owasp — json-sanitizer |
OWASP json-sanitizer before 1.2.2 may emit closing SCRIPT tags and CDATA section delimiters for crafted input. This allows an attacker to inject arbitrary HTML or XML into embedding documents. |
2021-01-13 |
not yet calculated |
CVE-2021-23899
MISC
MISC
MISC |
| owncloud — owncloud |
ownCloud (Core) before 10.5 allows XSS in login page ‘forgot password.’ |
2021-01-15 |
not yet calculated |
CVE-2020-16255
MISC
MISC |
| palo_alto_networks — pan-os |
An information exposure through log file vulnerability exists in Palo Alto Networks PAN-OS software where configuration secrets for the “http”, “email”, and “snmptrap” v3 log forwarding server profiles can be logged to the logrcvr.log system log. Logged information may include up to 1024 bytes of the configuration including the username and password in an encrypted form and private keys used in any certificate profiles set for log forwarding server profiles. This issue impacts: PAN-OS 8.1 versions earlier than PAN-OS 8.1.18; PAN-OS 9.0 versions earlier than PAN-OS 9.0.12; PAN-OS 9.1 versions earlier than PAN-OS 9.1.4; PAN-OS 10.0 versions earlier than PAN-OS 10.0.1. |
2021-01-13 |
not yet calculated |
CVE-2021-3032
CONFIRM |
| palo_alto_networks — pan-os |
Padding bytes in Ethernet packets on PA-200, PA-220, PA-500, PA-800, PA-2000 Series, PA-3000 Series, PA-3200 Series, PA-5200 Series, and PA-7000 Series firewalls are not cleared before the data frame is created. This leaks a small amount of random information from the firewall memory into the Ethernet packets. An attacker on the same Ethernet subnet as the PAN-OS firewall is able to collect potentially sensitive information from these packets. This issue is also known as Etherleak and is detected by security scanners as CVE-2003-0001. This issue impacts: PAN-OS 8.1 version earlier than PAN-OS 8.1.18; PAN-OS 9.0 versions earlier than PAN-OS 9.0.12; PAN-OS 9.1 versions earlier than PAN-OS 9.1.5. |
2021-01-13 |
not yet calculated |
CVE-2021-3031
CONFIRM |
| python-cryptography — python-cryptography |
python-cryptography 3.2 is vulnerable to Bleichenbacher timing attacks in the RSA decryption API, via timed processing of valid PKCS#1 v1.5 ciphertext. |
2021-01-11 |
not yet calculated |
CVE-2020-25659
MISC |
r-project — cran
|
The R programming language’s default package manager CRAN is affected by a path traversal vulnerability that can lead to server compromise. This vulnerability affects packages installed via the R CMD install cli command or the install.packages() function from the interpreter. Update to version 4.0.3 |
2021-01-12 |
not yet calculated |
CVE-2020-27637
MISC
MISC |
| red_hat — single_sign_on |
The “Test Connection” available in v7.x of the Red Hat Single Sign On application console can permit an authorized user to cause SMTP connections to be attempted to arbitrary hosts and ports of the user’s choosing, and originating from the RHSSO installation. By observing differences in the timings of these scans, an attacker may glean information about hosts and ports which they do not have access to scan directly. |
2021-01-12 |
not yet calculated |
CVE-2020-14341
CONFIRM |
scalance — multiple_switches
|
A vulnerability has been identified in SCALANCE X-200 switch family (incl. SIPLUS NET variants) (All versions), SCALANCE X-200IRT switch family (incl. SIPLUS NET variants) (All versions), SCALANCE X-300 switch family (incl. X408 and SIPLUS NET variants) (All versions < V4.1.0). The webserver of the affected devices contains a vulnerability that may lead to a heap overflow condition. An attacker could cause this condition on the webserver by sending specially crafted requests. This could stop the webserver temporarily. |
2021-01-12 |
not yet calculated |
CVE-2020-15800
MISC |
| scalance — x-200_and_x-200irt_switches |
A vulnerability has been identified in SCALANCE X-200 switch family (incl. SIPLUS NET variants) (All versions), SCALANCE X-200IRT switch family (incl. SIPLUS NET variants) (All versions). The web server of the affected devices contains a vulnerability that may lead to a buffer overflow condition. An attacker could cause this condition on the webserver by sending a specially crafted request. The webserver could stop and not recover anymore. |
2021-01-12 |
not yet calculated |
CVE-2020-25226
MISC |
scalance — x-200_and_x-200irt_switches
|
A vulnerability has been identified in SCALANCE X-200 switch family (incl. SIPLUS NET variants) (All Versions), SCALANCE X-200IRT switch family (incl. SIPLUS NET variants) (All versions). Devices create a new unique key upon factory reset, except when used with C-PLUG. When used with C-PLUG the devices use the hardcoded private RSA-key shipped with the firmware-image. An attacker could leverage this situation to a man-in-the-middle situation and decrypt previously captured traffic. |
2021-01-12 |
not yet calculated |
CVE-2020-28391
MISC
MISC |
scalance — x-200_and_x200irt_switches
|
A vulnerability has been identified in SCALANCE X-200 switch family (incl. SIPLUS NET variants) (All versions), SCALANCE X-200IRT switch family (incl. SIPLUS NET variants) (All versions). The vulnerability could allow an unauthenticated attacker to reboot the device over the network by using special urls from integrated web server of the affected products. |
2021-01-12 |
not yet calculated |
CVE-2020-15799
MISC |
scalance — x-300_swtiches
|
A vulnerability has been identified in SCALANCE X-300 switch family (incl. X408 and SIPLUS NET variants) (All versions < V4.1.0). Devices do not create a new unique private key after factory reset. An attacker could leverage this situation to a man-in-the-middle situation and decrypt previously captured traffic. |
2021-01-12 |
not yet calculated |
CVE-2020-28395
MISC
MISC
MISC |
| scully — scully |
This affects the package @scullyio/scully before 1.0.9. The transfer state is serialised with the JSON.stringify() function and then written into the HTML page. |
2021-01-14 |
not yet calculated |
CVE-2020-28470
MISC
MISC |
| siemens — opcenter_execution_core |
A vulnerability has been identified in Opcenter Execution Core (V8.2), Opcenter Execution Core (V8.3). The application contains an information leakage vulnerability in the handling of web client sessions. A local attacker who has access to the Web Client Session Storage could disclose the passwords of currently logged-in users. |
2021-01-12 |
not yet calculated |
CVE-2020-28390
MISC
MISC |
simplecommerce — simplecommerce
|
SimplCommerce 1.0.0-rc uses the Bootbox.js library, which allows creation of programmatic dialog boxes using Bootstrap modals. The Bootbox.js library intentionally does not perform any sanitization of user input, which results in a DOM XSS, because it uses the jQuery .html() function to directly append the payload to a dialog. |
2021-01-14 |
not yet calculated |
CVE-2020-29587
MISC |
| sky — skysea_client_view |
Untrusted search path vulnerability in the installer of SKYSEA Client View Ver.1.020.05b to Ver.16.001.01g allows an attacker to gain privileges via a Trojan horse DLL in an unspecified directory. |
2021-01-13 |
not yet calculated |
CVE-2021-20616
MISC
MISC |
| skyworth — gn542vf_boa |
Skyworth GN542VF Boa version 0.94.13 does not set the Secure flag for the session cookie in an HTTPS session, which makes it easier for remote attackers to capture this cookie by intercepting its transmission within an HTTP session. |
2021-01-14 |
not yet calculated |
CVE-2020-26732
MISC |
| skyworth — gn542vf_hardware |
Cross Site Scripting (XSS) in Configuration page in SKYWORTH GN542VF Hardware Version 2.0 and Software Version 2.0.0.16 allows authenticated attacker to inject their own script into the page via DDNS Configuration Section. |
2021-01-14 |
not yet calculated |
CVE-2020-26733
MISC |
solarwinds — web_help_desk
|
SolarWinds Web Help Desk 12.7.0 allows XSS via a Schedule Name. |
2021-01-15 |
not yet calculated |
CVE-2019-16961
MISC
MISC
MISC |
sound_research — dchu
|
The SECOMN service in Sound Research DCHU model software component modules (APO) through 2.0.9.17, delivered on HP Windows 10 computers, may allow escalation of privilege via a fake DLL. (As a resolution, Windows Update is being submitted for all affected products to update to 2.0.9.18 or later.) |
2021-01-13 |
not yet calculated |
CVE-2020-35686
MISC |
sudo — sudo
|
The sudoedit personality of Sudo before 1.9.5 may allow a local unprivileged user to perform arbitrary directory-existence tests by winning a sudo_edit.c race condition in replacing a user-controlled directory by a symlink to an arbitrary path. |
2021-01-12 |
not yet calculated |
CVE-2021-23239
MISC
CONFIRM |
thingworx — multiple_products
|
KEPServerEX v6.0 to v6.9, ThingWorx Kepware Server v6.8 and v6.9, ThingWorx Industrial Connectivity (all versions), OPC-Aggregator (all versions), Rockwell Automation KEPServer Enterprise, GE Digital Industrial Gateway Server v7.68.804 and v7.66, and Software Toolbox TOP Server all 6.x versions, are vulnerable to a heap-based buffer overflow. Opening a specifically crafted OPC UA message could allow an attacker to crash the server and potentially leak data. |
2021-01-14 |
not yet calculated |
CVE-2020-27267
MISC |
thingworx — multiple_products
|
KEPServerEX: v6.0 to v6.9, ThingWorx Kepware Server: v6.8 and v6.9, ThingWorx Industrial Connectivity: All versions, OPC-Aggregator: All versions, Rockwell Automation KEPServer Enterprise, GE Digital Industrial Gateway Server: v7.68.804 and v7.66, Software Toolbox TOP Server: All 6.x versions are vulnerable to a stack-based buffer overflow. Opening a specifically crafted OPC UA message could allow an attacker to crash the server and remotely execute code. |
2021-01-14 |
not yet calculated |
CVE-2020-27265
MISC |
thingworx — multiple_products
|
KEPServerEX: v6.0 to v6.9, ThingWorx Kepware Server: v6.8 and v6.9, ThingWorx Industrial Connectivity: All versions, OPC-Aggregator: All versions, Rockwell Automation KEPServer Enterprise, GE Digital Industrial Gateway Server: v7.68.804 and v7.66, Software Toolbox TOP Server: All 6.x versions, are vulnerable to a heap-based buffer overflow. Opening a specifically crafted OPC UA message could allow an attacker to crash the server and potentially leak data. |
2021-01-14 |
not yet calculated |
CVE-2020-27263
MISC |
thinkadmin — thinkadmin
|
An insecure unserialize vulnerability was discovered in ThinkAdmin versions 4.x through 6.x in app/admin/controller/api/Update.php and app/wechat/controller/api/Push.php, which may lead to arbitrary remote code execution. |
2021-01-13 |
not yet calculated |
CVE-2020-23653
MISC |
totolink — a702r_router
|
Directory Indexing in Login Portal of Login Portal of TOTOLINK-A702R-V1.0.0-B20161227.1023 allows attacker to access /icons/ directories via GET Parameter. |
2021-01-14 |
not yet calculated |
CVE-2020-27368
MISC |
| wordpress — wordpress |
The Elementor Contact Form DB plugin before 1.6 for WordPress allows CSRF via backend admin pages. |
2021-01-12 |
not yet calculated |
CVE-2021-3133
MISC
MISC |
wordpress — wordpress
|
Cross-site scripting (XSS) vulnerability in models/list-table.php in the FV Flowplayer Video Player plugin before 7.4.37.727 for WordPress allows remote authenticated users to inject arbitrary web script or HTML via the fv_wp_fvvideoplayer_src JSON field in the data parameter. |
2021-01-15 |
not yet calculated |
CVE-2020-35748
MISC
MISC |
wordpress — wordpress
|
Directory traversal vulnerability in class-simple_job_board_resume_download_handler.php in the Simple Board Job plugin 2.9.3 and earlier for WordPress allows remote attackers to read arbitrary files via the sjb_file parameter to wp-admin/post.php. |
2021-01-15 |
not yet calculated |
CVE-2020-35749
MISC |
| xiaomi — ax1800rom_and_rm1800_routers |
The login verification can be bypassed by using the problem that the time is not synchronized after the router restarts. This affects Xiaomi router AX1800rom version < 1.0.336 and Xiaomi route RM1800 root version < 1.0.26. |
2021-01-13 |
not yet calculated |
CVE-2020-14098
MISC |
xiaomi — ax1800rom_and_rm1800_routers
|
There is command injection when ddns processes the hostname, which causes the administrator user to obtain the root privilege of the router. This affects Xiaomi router AX1800rom version < 1.0.336 and Xiaomi route RM1800 root version < 1.0.26. |
2021-01-13 |
not yet calculated |
CVE-2020-14102
MISC |
xiaomi — ax1800rom_and_rm1800_routers
|
The data collection SDK of the router web management interface caused the leakage of the token. This affects Xiaomi router AX1800rom version < 1.0.336 and Xiaomi route RM1800 root version < 1.0.26. |
2021-01-13 |
not yet calculated |
CVE-2020-14101
MISC |
| xiaomi — ax6_rom_router |
Wrong nginx configuration, causing specific paths to be downloaded without authorization. This affects Xiaomi router AX6 ROM version < 1.0.18. |
2021-01-13 |
not yet calculated |
CVE-2020-14097
MISC |
| zte — smart_stb |
A ZTE Smart STB is impacted by an information leak vulnerability. The device did not fully verify the log, so attackers could use this vulnerability to obtain sensitive user information for further information detection and attacks. This affects: ZXV10 B860A V2.1-T_V0032.1.1.04_jiangsuTelecom. |
2021-01-14 |
not yet calculated |
CVE-2021-21722
MISC |



Recent Comments