by Scott Muniz | Jan 28, 2021 | Security, Technology
This article is contributed. See the original author and article here.
January 28 is Data Privacy Day (DPD), an annual effort promoting data privacy awareness and education. This year’s DPD events, sponsored by the National Cyber Security Alliance (NCSA), focus on how to Own Your Privacy.
The NCSA teaches users how to protect valuable data online, while encouraging businesses to Respect Privacy by protecting data they collect. CISA encourages users and businesses to visit NCSA’s website to learn more, including several calls to action:
For Individuals: Own Your Privacy
- Personal info is like money. Your purchase history, IP address, or location has tremendous value. Make informed decisions about whether or not to share such data with certain businesses.
- Keep tabs on your apps. Delete unused ones and keep others secure by performing updates.
- Manage your privacy and security settings. Continuously check them to limit what information you share.
For Businesses: Respect Privacy
- If you collect it, protect it. Make sure any personal data you collect is processed in a fair manner and is only collected for relevant and legitimate purposes.
- Consider adopting a privacy framework to manage risk and secure privacy within your organization.
- Asses data collection practices by evaluating which privacy regulations apply to your organization.
- Transparency builds trust. Be honest with customers about how you collect, use, and share their personal information.
- Maintain oversight of partners and vendors. You are responsible for anyone collecting and using your consumers’ personal information.
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
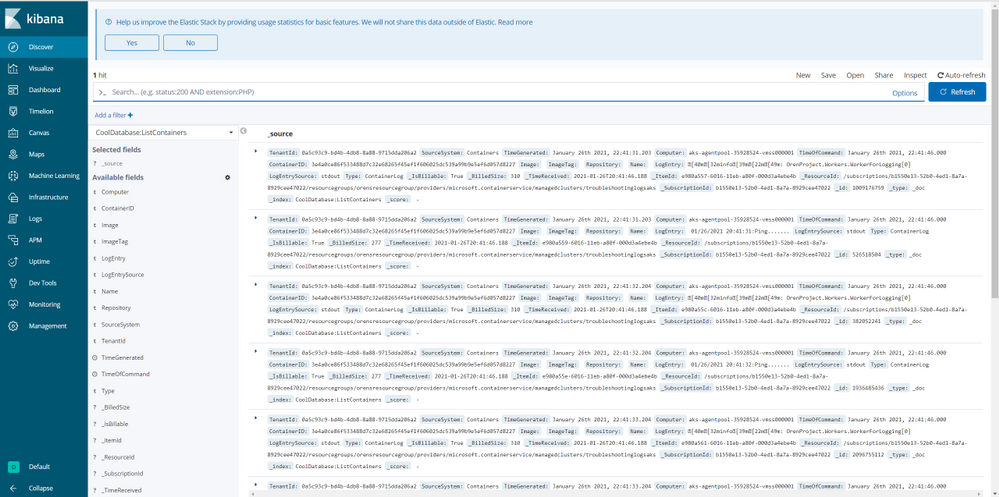
View and Query Log Analytics in Kibana dashboard using Azure Data Explorer
This experience enables you to query Azure Log Analytics in Kibana, using the Azure Data Explorer and Kibana integration and the cross-service query ability between Azure Data Explorer and Azure Log Analytics (see more info here) so you could join and analyze all your data in one place.

Follow the instructions to set up an integration between your Kibana instance and your Azure Data Explorer cluster, than, create a function in Azure Data Explorer with the following pattern:
cluster('https://ade.loganalytics.io/subscriptions/<subscription-id>/resourcegroups/<resource-group-name>/providers/microsoft.operationalinsights/workspaces/<workspace-name>').database('<workspace-name>').<tablename>
Now, the function is in Kibana and you can configure an index pattern and query your Log Analytics data.
Note that the ability to query Log Analytics from Azure Data Explorer is in public preview, for any questions please contact ADXProxy team.
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
I know this not a new feature, but this saved my proverbial behind earlier this week. I was cleaning out demo subscriptions and resource groups that I’m no longer using or that need to be reset for new demos. Well… It did not take long for me to pick one that I needed to keep and hit the “Delete resource group”.

And like any situation where you know you’ve screwed up. I knew the second I saw the notification.


Turns out this Resource Group was where stored all the recorded demos I regularly use…. #Facepalm
This is also when I remembered I had enable blob soft delete on that storage account.
Blob soft delete is available for both new and existing general-purpose v2, general-purpose v1, and Blob storage accounts (standard and premium). But only for unmanaged disks, which are page blobs under the covers, but is not available for managed disks.
If you have not enabled this on storage accounts where you have important data…. DO IT NOW!!
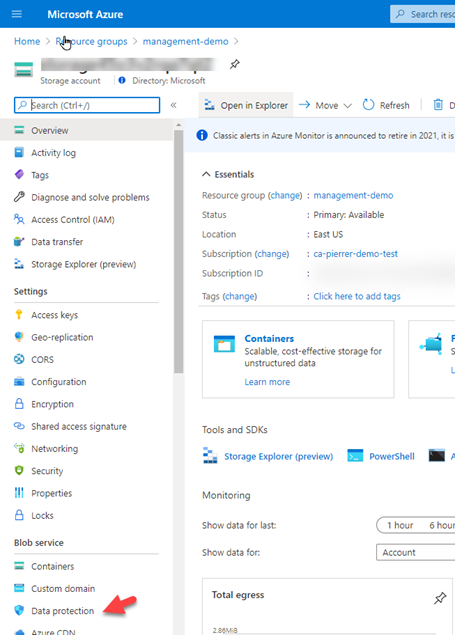
1. In the Azure portal, navigate to your storage account, and in the left-side menu find the “Data Protection” option under the “Blob service” section.
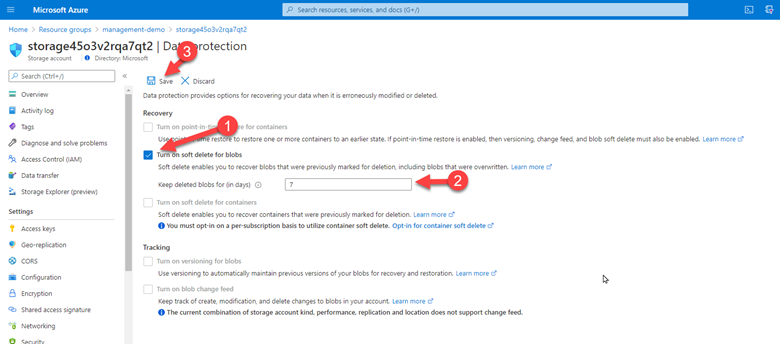
2. Check the box for “Turn on soft delete for blob”, then specify how long soft-deleted blobs are to be retained by Azure Storage, and finally save your configuration.
That’s it! You are now protected. Anyway, I was still looking at how I was going to recover my data. I deleted the Resource Group!! Not just the storage account or just the blob container… started looking for documentation. And found the one I was looking for. Recover a deleted storage account.
I followed the steps that were simple, even when you’re restoring a storage account from a deleted resource group.
1. Create a Resource Group with the EXACT SAME NAME you just deleted. Once it’s created, navigate to the overview page for an existing storage account in the Azure portal. ANY existing storage account. And in the Support + troubleshooting section, select Recover deleted account.
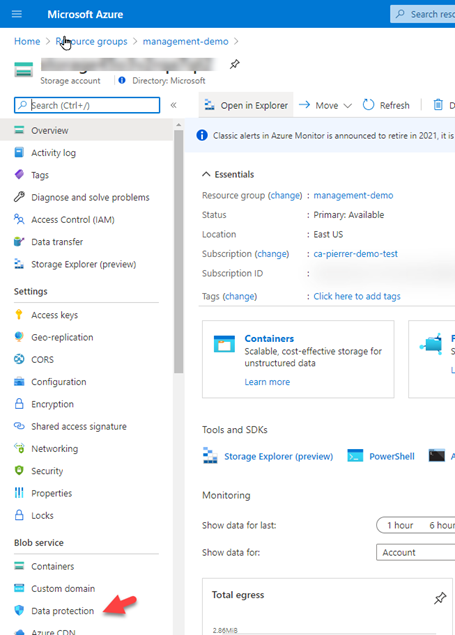
2. From the dropdown, select the account to recover. If the storage account that you want to recover is not in the dropdown, then it cannot be recovered. Once you have selected the account, click on recover button.
Once the process is complete, your storage account will have been restored in its original spot. This really saved my bacon. I know it can potentially save yours.
Hopefully this can potentially save you some grief as well.
Cheeers!
Pierre
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
As announced via the Microsoft Advertising blog, mixed campaigns are now available to all Dynamic Search Ads customers in Microsoft Advertising.
Mixed campaigns are Search campaigns that can include both standard ad groups (with text ads, responsive search ads, and keywords) and dynamic ad groups (with dynamic search ads and auto targets).
Coming soon, campaigns that only support dynamic search ads will be converted to search campaigns. Here are the key dates that you need to know about.
January 8th
As of January 8th, mixed campaigns are supported in all markets where Dynamic search ads are available.
- Dynamic search ads campaign creation is not allowed in the Microsoft advertising UI. Campaigns that only support dynamic search ads can still be viewed and edited.
- There are no changes to the Bing Ads API. All add, edit, and read operations still work without interruption.
- There are no changes to Microsoft Advertising Editor. All add, edit, and read operations still work without interruption.
Q2 calendar year 2021
During early Q2 calendar year 2021, Bing Ads API and Microsoft Advertising Editor clients will not be allowed to add new campaigns with the DynamicSearchAds campaign type. You can still edit and read Dynamic search ads campaigns.
Shortly after the campaign creation calls began to fail, we will convert all dynamic search ads campaigns to search campaigns. The campaign type will be updated from DynamicSearchAds to Search. We anticipate that it could take a couple of weeks to convert DSA campaigns to search campaigns across all accounts.
We will announce more precise dates closer to Q2.
As always please feel free to contact support or post a question in the Microsoft Advertising developer Q&A forum.
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
Final Update: Thursday, 28 January 2021 10:22 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 01/28, 10:00 UTC. Our logs show the incident started on 01/28, 08:00 UTC and that during the 2 Hours that it took to resolve the issue some customers may have experienced issues with missed, delayed and wrongly fired Log Search alerts and may have experienced difficulty accessing data for resources hosted in USGov Arizona region.
Root Cause: We identified the issue was caused by a recent deployment task with a incorrect configuration setting.
- Incident Timeline: 2 Hours – 01/28, 08:00 UTC through 01/28, 10:00 UTC
We understand that customers rely on Log Search Alerts as a critical service and apologize for any impact this incident caused.
-Anmol


Recent Comments