by Contributed | Nov 10, 2020 | Technology
This article is contributed. See the original author and article here.
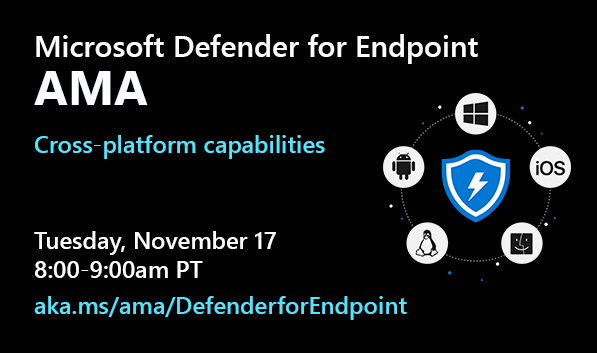
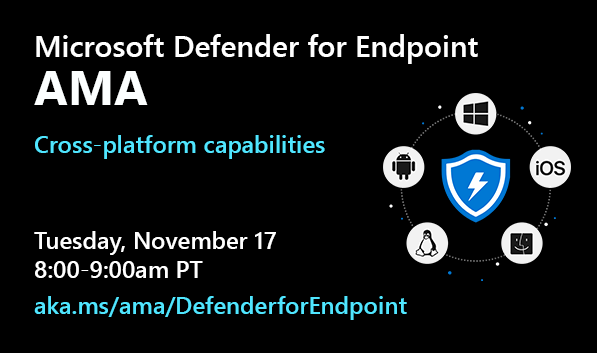
We’re excited to invite you to the first Microsoft Defender for Endpoint Ask Me Anything (AMA) on the Microsoft TechCommunity! The product team has missed meeting customers at security and tech conferences and expo halls through the year and so we’d like to engage with you virtually. Our goal is to do these at least on a quarterly basis and have them focused on specific topics related to Microsoft Defender for Endpoint.
Our first AMA will be on November 17, from 8:00-9:00am PT and it will be focused on Microsoft Defender for Endpoint capabilities for macOS, Linux, Android, and iOS. Bring all your burning questions! Our product team will be there to answer them. :smiling_face_with_smiling_eyes:
Details:
Microsoft Defender for Endpoint AMA – cross platform edition
Date: Tuesday, November 17, 2020
Time: 8-9am PT
Place: https://aka.ms/ama/DefenderforEndpoint
Save the .ics file to ensure you have this on your calendar!
by Contributed | Nov 10, 2020 | Technology
This article is contributed. See the original author and article here.
In my blog Your Pa$$word doesn’t matter, I laid out the key password vulnerabilities, and in response to a gazillion “but other creds can be compromised, too” DMs and emails, I wrote All our creds are belong to us, where I outlined vulnerabilities in credentials other than passwords and highlighted the promise of passwordless, cryptographically protected creds like FIDO, Windows Hello, and the Authenticator App.
Today, I want to do what I can to convince you that it’s time to start your move away from the SMS and voice Multi-Factor Authentication (MFA) mechanisms. These mechanisms are based on publicly switched telephone networks (PSTN), and I believe they’re the least secure of the MFA methods available today. That gap will only widen as MFA adoption increases attackers’ interest in breaking these methods and purpose-built authenticators extend their security and usability advantages. Plan your move to passwordless strong auth now – the authenticator app provides an immediate and evolving option.
It bears repeating, however, that MFA is essential – we are discussing which MFA method to use, not whether to use MFA. Quoting an earlier blog, “Multi-factor Authentication (MFA) is the least you can do if you are at all serious about protecting your accounts. Use of anything beyond the password significantly increases the costs for attackers, which is why the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population.”
The Usual Suspects
It’s worth noting that every mechanism to exploit a credential can be used on PSTN – OTP. Phish? Check. Social? Check. Account takeover? Check. Device theft? Check. Your PSTN account has all the vulnerabilities of every other authenticator and a host of other issues specific to PSTN.
Not Adaptable
Because so many devices rely on receiving PSTN messages, the format of the messages is limited – we can’t make the messages richer, or longer, or do much of anything beyond sending the OTP in a short text message or a phone call. One of the significant advantages of services is that we can adapt to user experience expectations, technical advances, and attacker behavior in real-time. Unfortunately, the SMS and voice formats aren’t adaptable, so the experiences and opportunities for innovations in usability and security are very limited.
Transmitted in the Clear
When SMS and voice protocols were developed, they were designed without encryption. From a practical usability perspective, we can’t overlay encryption onto these protocols because users would be unable to read them (there are other reasons too, like message bloat, which have prevented these from taking hold over the existing protocols). What this means is that signals can be intercepted by anyone who can get access to the switching network or within the radio range of a device. As I said in the earlier “All Your Creds” blog, “an attacker can deploy a software-defined-radio to intercept messages, or a nearby FEMTO, or use an SS7 intercept service to eavesdrop on the phone traffic.” This is a substantial and unique vulnerability in PSTN systems that is available to determined attackers.
Easy to Social Engineer
It’s worth noting that most PSTN systems are backed by online accounts and rich customer support infrastructure. Sadly, customer support agents are vulnerable to charm, coercion, bribery, or extortion. If these social engineering efforts succeed, customer support can provide access to the SMS or voice channel. While social engineering attacks impact email systems as well, the major email systems (e.g. Outlook, Gmail) have a more developed “muscle” for preventing account compromise via their support ecosystems. This leads to everything from message intercept, to call forwarding attacks, to SIM jacking.
Subject to Mobile Operator Performance
Unfortunately, PSTN systems are not 100% reliable, and reporting is not 100% consistent. This is region and carrier dependent, but the path a message takes to you may influence how long it takes to get and whether you get it at all. In some cases, carriers report delivery when delivery has failed, and in others, delivery of messages can take a long enough time that users assume messages have been unable to get through. In some regions, delivery rates can be as low as 50%! Because SMS is “fire and forget,” the MFA provider has no real-time signal to indicate a problem and has to rely on statistical completion rates or helpdesk calls to detect problems. This means signal to users to offer alternatives or warn of an issue is difficult to provide.
Subject to Changing Regulations
Due to the increase in spam in SMS formats, regulators have required regulations on identifying codes, transmit rates, message content, permission to send, and response to messages like “STOP.” Unfortunately, however, these regulations change rapidly and are inconsistent from region to region and can (and have) resulted in major delivery outages. More outages, more user frustration.
Limited Context
In practical terms, the text or voice mediums limit how much information can be communicated to a user – SMS carries 160 characters, 70 if not using GSM, and once we get into languages which require encoding, the practical limit without message splitting is only around half that. Phishing is a serious threat vector, and we want to empower the user with as much context as possible (or, using Windows Hello or FIDO, make phishing impossible) – SMS and voice formats restrict our ability to deliver the context under which authentication is being requested.
Authentication Evolved
Ok, to recap: you’re GOING to use MFA. Which MFA? Well, for most users on their mobile devices, we believe the right answer is app-based authentication. For us, that means the Microsoft Authenticator. The Authenticator uses encrypted communication, allowing bi-directional communication on authentication status, and we’re currently working on adding even more context and control to the app to help users keep themselves safe. In just the last year, we’ve added app lock, hiding notifications from the lock screen, sign-in history in the app, and more – and this list will have grown by the time you plan your deployment, and keep growing while SMS and voice keep sitting still.
Hang up on PSTN and pick up the Microsoft Authenticator – your users will be happier and more secure because you did.
Stay safe out there,
Alex (Twitter: @alex_t_weinert)
by Contributed | Nov 10, 2020 | Technology
This article is contributed. See the original author and article here.
The Basic, Standard, and Premium service tiers fulfill a lot of customers’ needs. For some customers, though, the General Purpose, Business Critical, and Hyperscale service tiers offer additional performance and ability that is required for certain workloads. Even if you don’t require those abilities, the technology and infrastructure behind these are worth learning about! In this episode with Matt Gordon, we’ll discuss those service tiers as well as discussing the differences between Provisioned and Serverless deployments on the General Purpose tier. Come learn how to ramp up your Azure SQL Database experience!
Watch on Data Exposed
Resources:
View/share our latest episodes on Channel 9 and YouTube!
![[Guest Blog] Why We Use Microsoft for Our CMMC Managed Service Customers](https://www.drware.com/wp-content/uploads/2020/11/medium-49)
by Contributed | Nov 10, 2020 | Technology
This article is contributed. See the original author and article here.
In January of this year, the Department of Defense (DoD) released the Cybersecurity Maturity Model Certification or CMMC. This new maturity model defines five levels of increasing maturity and will require all defense contractors, both Primes and Subs, to comply with one of the five levels and attain independent verification of compliance prior to contract award. In an ongoing effort to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), CMMC is a significant change for DoD acquisition, cybersecurity, and policy. For small businesses in the defense industrial base, the challenge is potentially insurmountable.
Having partnered with the DoD as part of the Defense Industrial Base Cybersecurity Initiative since its inception, first as a Chief Information Security Officer with one of the largest DoD contractors and now as CEO of CyberSheath, the foremost Managed CMMC compliance provider, I have seen every side of this compliance problem and understand what works and what doesn’t. Because of this, I am often asked, “How can I meet CMMC requirements?” My answer is always the same, “Hire a great Managed Compliance partner and use Microsoft technologies.” If you only use internal resources, you will inevitably fall short somewhere on the security, technical, or policy expertise required. If you try to use multiple technologies from different vendors, you will have more tools than you can support, possibly achieving compliance and assuredly weakening security. This blog details what Managed Compliance looks like in the context of CMMC.
So, why Microsoft for CMMC?
Microsoft has a deep and long history of supporting government customers and their unique mission requirements; in fact, about a year ago, Richard Wakeman wrote this blog specific to the Microsoft Cloud Service Offerings. Suffice it to say Microsoft uniquely understands the U.S. Government’s mission in a way that only decades of experience working alongside one another will allow. Microsoft understands the required people, processes, and technologies to support the DoD mission from both a compliance and operational perspective so well that it can often be difficult for anyone to lay it all out in one succinct communication. Microsoft has done more for the United States Government than any other cloud provider. Their decades of successful partnership with DoD have enabled them to provide resources that will enable your journey to CMMC compliance.
Here are three resources to get you started on your journey to CMMC compliance:
Shared Responsibility Model
CMMC compliance for many, if not most, companies will undoubtedly rely on the cloud at some point in the journey. When in the cloud, and frankly, on-premise, it is important to understand the concept of shared responsibility. When relying on cloud services, understanding the shared responsibility model is foundational to meeting and maintaining compliance. For an excellent blog on shared responsibility in the cloud start here and as you read think about which CMMC security tasks are handled by your cloud provider and which tasks are handled by you. Now for the many companies that rely on Managed Service Providers, or otherwise defined Third-Party Providers, how are you extending the shared responsibility to those entities?
Very few MSSPs understand CMMC in the context of the shared responsibility model. To my knowledge, CyberSheath is one of the few to build our entire CMMC management platform around Microsoft Azure technology, which is detailed here along with a breakdown of how CMMC has been 13 years in the making.
CMMC compliance isn’t a “go it alone” model and requires an understanding of the shared responsibility model, regardless of your CMMC compliance level. Rare is the company that does everything in-house without exception.
Azure Blueprints
Azure Blueprints enable customers to easily create, deploy, and update compliant environments and leverage the enormous Microsoft investment in data security and privacy. Microsoft invests more than USD 1 billion annually on cybersecurity research and development, employs more than 3,500 security experts entirely dedicated to your data security and privacy and Azure has more certifications than any other cloud provider. View the comprehensive list.
Blueprints simplify largescale Azure deployments by packaging key environment artifacts, such as Azure Resource Manager templates, role-based access controls, and policies, in a single blueprint definition. Customers can easily apply the blueprint to new subscriptions and environments and fine-tune control and management through versioning. Specific to CMMC, blueprints present a tremendous advantage for customers who want to quickly address the majority of the CMMC Maturity Level 3 requirements.
The NIST SP 800-171 R2 blueprint sample provides governance guard-rails using Azure Policy that help you assess specific NIST SP 800-171 R2 requirements or controls. This blueprint helps customers deploy a core set of policies for any Azure-deployed architecture that must implement NIST SP 800-171 R2 requirements or controls. As many readers know, approximately 85% of the CMMC Maturity Level 3 requirements are essentially the NIST SP 800-171 security requirements, so this blueprint can be a force for progress in your CMMC compliance efforts.
Office 365 GCC High and DoD
As many defense contractors already know, CMMC was, in part, created to address the security of CUI, and Microsoft has long been a partner with DoD working to protect this information.
To meet the unique and evolving requirements of DoD and contractors holding or processing DoD controlled CUI or subject to International Traffic in Arms Regulations (ITAR), Microsoft offers GCC High and DoD environments. Microsoft GCC High and DoD meet the compliance requirements for the following certifications and accreditations:
- The Federal Risk and Authorization Management Program at FedRAMP High, including those security controls and control enhancements as outlined in the National Institute of Standards and Technology (NIST) Special Publication 800-53.
- The security controls and control enhancements for the United States Department of Defense Cloud Computing Security Requirements Guide (SRG) for information up to Impact Level 5 (L5).
DoD Office 365 subscribers will receive services provided from the DoD exclusive environment that meets DoD SRG L5. Non-DoD subscribers will receive services from the U.S. Government Defense environment, which is assessed at L5, but has L4 equivalency.
There is much debate and often confusion on whether CMMC requires GCC high, and it is one of many issues that highlight the need for a Managed Compliance Partner, but the point is that Microsoft has long been the partner of choice for the DoD in addressing this challenge.
CMMC mandates minimum cybersecurity standards for 300,000 plus commercial defense contractors around the globe and makes compliance part of the acquisition process, preventing contract award until an independent third-party has verified compliance. Given the magnitude of this change and the revenue impacting consequences of non-compliance, we choose Microsoft for our CMMC Managed Services Customers.
Additional information
For additional information on Microsoft’s CMMC acceleration, join Microsoft’s Richard Wakeman, Senior Director of Aerospace & Defense for Azure Global, on November 18th at CMMC Con 2020. Mr. Wakeman will host a Technology Spotlight session dedicated to discovering how Microsoft solutions are assisting the DIB in government compliance. Visit www.cmmccon2020.com to learn more.
About the Author

Eric is Chief Executive Officer (CEO) for CyberSheath Services International, LLC (CyberSheath) and is a respected cybersecurity expert having testified before the House Armed Services Committee (HASC) Subcommittee on Emerging Threats and Capabilities and served on the Council on Cyber Security expert panel to review and update the Critical Security Controls. Prior to founding CyberSheath, Eric was the Global Chief Information Security Officer for BAE Systems plc, based in London. Concurrently Eric served as Vice President and General Manager of North American IT operations, overseeing engineering, architecture, and IT operations support for approximately 39,000 employees. Eric has an MBA from the University of Maryland and a B.S. with honors in Information Technology Management from Daniel Webster College. He holds numerous technical and professional certifications including Certified Information Systems Security Professional (CISSP) and Project Management Professional (PMP).
by Scott Muniz | Nov 10, 2020 | Security, Technology
This article is contributed. See the original author and article here.
Original release date: November 10, 2020
SAP has released security updates to address vulnerabilities affecting multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system. These include missing authentication check vulnerabilities affecting SAP Solution Manager (JAVA stack).
The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the SAP Security Notes for November 2020 and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.




Recent Comments