by Contributed | Nov 17, 2020 | Technology
This article is contributed. See the original author and article here.
Today, we are excited to announce the public preview of endpoint detection and response (EDR) capabilities in Microsoft Defender for Endpoint on Linux servers.
With the new Linux EDR capabilities, Defender for Endpoint customers will have the ability to detect advanced attacks that involve Linux servers, utilize rich experiences, and quickly remediate threats. This builds on the existing preventative antivirus capabilities and centralized reporting available via the Microsoft Defender Security Center.
Linux EDR preview scope
Microsoft Defender for Endpoint on Linux supports recent versions of the six most common Linux server distributions:
- RHEL 7.2+
- CentOS Linux 7.2+
- Ubuntu 16 LTS, or higher LTS
- SLES 12+
- Debian 9+
- Oracle Linux 7.2
With Defender for Endpoint EDR capabilities for Linux, your security team can immediately start benefiting from:
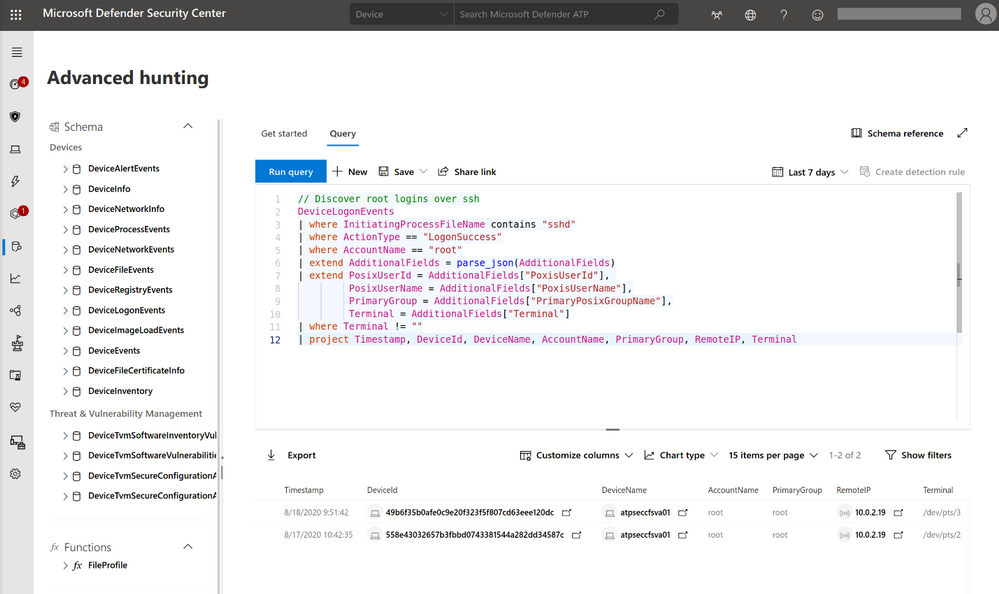
- Rich investigation experience – including machine timeline, process creation, file creation, network connections, login events and, of course, the popular advanced hunting.
- Optimized performance – enhanced CPU utilization in compilation procedures and large software deployments.
- In-context AV detections – just like with Windows, get insight into where a threat came from and how the malicious process or activity was created.
Getting started with Linux EDR preview
To get started with Microsoft Defender for Endpoint public preview capabilities, we encourage customers to turn on preview features in Microsoft Defender Security Center.
If you’re already running Microsoft Defender for Endpoint on Linux, we recommend that you configure some of your Linux servers to Preview mode, by applying the following command on the device:
$ sudo mdatp edr early-preview enable
Please make sure you are running version 101.12.99 or higher. The version can be found in the output of “mdatp health”.
If you are new to Microsoft Defender for Endpoint on Linux, learn how to get started by visiting our documentation and then enable the preview mode as explained above.
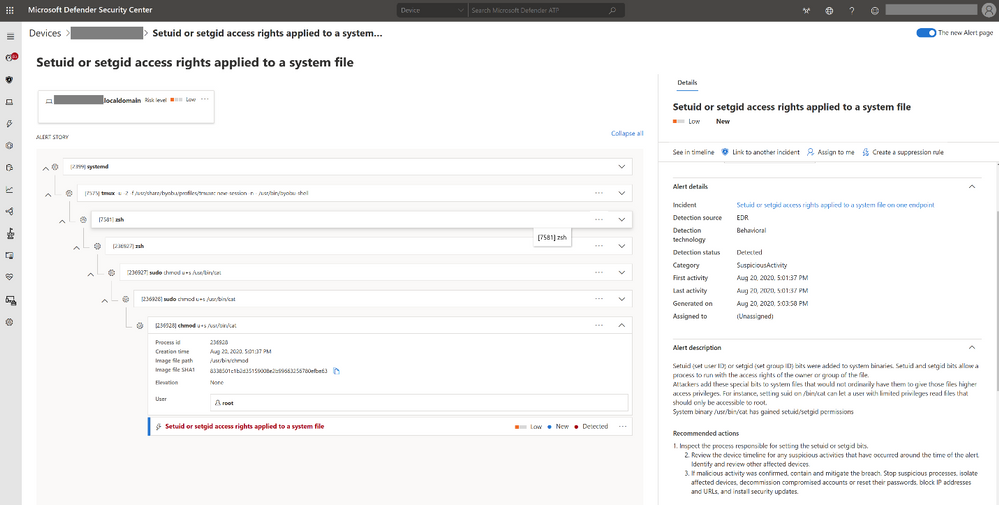
Experience Linux EDR with simulated attack
To test out the functionalities of EDR for Linux, follow the steps below to simulate a detection on your Linux server and investigate the case. Please share your feedback with us!
- Verify that the onboarded Linux server appears in Microsoft Defender Security Center. If this is the first onboarding of the machine, it can take up to 20 minutes until it appears.
- Download and extract the script file from here aka.ms/LinuxDIY to an onboarded Linux server and run the following command: “./mde_linux_edr_diy.sh”
- After a few minutes, should be raised in Microsoft Defender Security Center.
- Look at the alert details, machine timeline, and perform your typical investigation steps.
Help us innovate Microsoft Defender for Endpoint on Linux
We are very excited to share today’s Linux EDR preview news with you and your feedback is highly valuable to us! Join us on the journey to enhance Microsoft Defender for Endpoint on Linux. Try the new Linux EDR capabilities and You can submit feedback by joining the discussion below or by clicking on the ‘send a smile/frown’ icon on the top right corner of the security center.
If you’re not yet taking advantage of Microsoft’s industry leading optics and detection capabilities, sign up for a free trial of Microsoft Defender for Endpoint today.
Tomer Hevlin
Microsoft Defender for Endpoint Team
by Contributed | Nov 17, 2020 | Technology
This article is contributed. See the original author and article here.
Matt Soseman, Senior Security Architect, One Commercial Partner @ Microsoft
History:
As an IT professional of 20 years, I can recall the days of supporting line of business applications hosted in a corporate datacenter, behind a firewall, where IT had complete control. As Software as a Service (SaaS) started becoming the new modern line of business apps, a new challenge presented itself – the infrastructure behind that app is outside IT’s control. Not having controls to govern access (nor the data) in the app posed significant risks to the organization, not to mention a lack of visibility into the compliance and security posture of the app.
Fast forward to present day, SaaS apps are mission critical components to successful operations for an organization – cloud storage, online meetings, customer relationship management, inventory control, payroll and so much more. SaaS provides the organization with the modern technology to meet business needs, without a large infrastructure investment. However, SaaS needs to be trusted by the IT department and be carefully considered as part of a security and compliance strategy.
Matt’s Insight: As I am sure you would agree, reality looks something like:
Business: “I want my SaaS apps now!”
IT: “What do you need me to support? Do you have funding and staffing? Will this app touch security, compliance, is governance needed, etc.?”
Business: “I am already using SaaS apps, and you don’t know I am using them”
IT: “…”
More SaaS Apps, More SaaS Problems:
As SaaS becomes more popular and the business is setting expectations of usage, from an IT perspective SaaS presents many challenges. Some of the common challenges that often come up are:
How does your organization discover SaaS apps:
- Discover new and existing SaaS apps in my environment?
- Determine which apps can be used, and which can be blocked?
- Evaluate the security and compliance risks of the app?
- Identify who is using the apps and how much is used?
- Get notified when new apps are discovered?
- Get notified when an app has a public data breach?
How does your organization block SaaS apps:
- Block SaaS apps I do not want users to access?
- Ensure the block is occurring at not only the firewall layer, but also the client layer?
How does your organization approve and provision access to SaaS apps:
- Approve new/existing SaaS apps to be used?
- Consider an automated workflow?
- Provision access to approved apps?
- Remove access to approved apps?
App access:
- Govern access to the app?
- Ensure access encompasses Multi-Factor Authentication and Single Sign On?
- Require/verify the app is only accessed only from a managed device?
Data Loss Prevention:
- Block downloads of sensitive data?
- Block uploads of sensitive data?
- Control the types of data in specific activities? (i.e. printing, instant messaging, copy/paste, etc)
- See if data is being shared externally?
- Monitor for abnormal activities?
- Scan all the data in the app and discover sensitive data, and apply appropriate controls?
Matt’s Insight: The priority is to always strike a balance between productivity and security. There are so many more challenges that come up with SaaS app usage than what is listed above. It starts with gaining visibility to the apps, then using those insights to build a strategy on how to block/govern/control the apps. As I am sure you will agree, this is a journey and not a destination.
How can a Cloud Access Security Broker help?
When I think about how to use a CASB, it comes down to the outcome I am trying to drive. I need to clearly understand what I am trying to accomplish, why it needs to be done and the business outcome it will drive. I cannot stress enough understanding the why as a critical component of your decision-making process: ask yourself if the SaaS app is truly a requirement or a ‘nice to have.’ This helps to ensure it is being used for the right reasons – ultimately helping to transform the business with users who are more productive with proper security in place.
One approach is to address these concerns with each SaaS app individually using the app’s administrative controls. However, the problem with this approach is that SaaS apps are not always centrally managed. This is critical to centralize alerting, activity visibility, common policy, dashboards/reporting, and more. This is where a Cloud Access Security Broker (CASB) comes in. The CASB offers many capabilities to help you address challenges such as:
- Discover new and existing SaaS apps in the environment.
- Identify security and compliance risk for discovered SaaS apps.
- Provide visibility and governance to all user/admin activity within SaaS apps.
- Apply policy controls to govern how an app is accessed and how data in an app can be used (i.e., Data Loss Prevention).
- Robust reporting on SaaS app usage.
- Alerting on policy violations.
- Anomalous behavior detection and mitigation.
- Real-time session controls.
- And more!
Another way to get ideas for how a CASB can be used is to review some common use cases, for example from Microsoft’s Top 20 CASB Use Cases:
1) Discover all cloud apps and services used in your organization
2) Assess the risk and compliance of your cloud apps
3) Govern discovered cloud apps and explore enterprise-ready alternatives
4) Enable continuous monitoring to automatically detect new and risky cloud apps
5) Detect when data is being exfiltrated from your corporate apps
6) Discover OAuth apps that have access to your environment
7) Gain visibility into corporate data stored in the cloud
8) Enforce DLP and compliance policies for sensitive data stored in your cloud apps
9) Ensure safe collaboration and data sharing practices in the cloud
10) Protect your data when it’s downloaded to unmanaged devices
11) Enforce adaptive session controls to manage user actions in real-time
12) Record an audit trail for all user activities across hybrid environments
13) Identify compromised user accounts
14) Detect threats from users inside your organization
15) Detect threats from privileged accounts
16) Identify and revoke access to risky OAuth apps
17) Detect and remediate malware in your cloud apps
18) Audit the configuration of your IaaS environments
19) Monitor user activities to protect against threats in your IaaS environments
20) Capture user activities within custom cloud and on-premises apps
Matt’s Insight: When looking to add a CASB to my toolbox, understanding what business challenges and security objectives I need to meet is critical. Bringing in a subject matter expert from a Microsoft Partner can help me build that business justification by identifying the why and the outcome I need to achieve. It can be helpful to bring in someone who has done this for organizations like mine and who can bring new insights that perhaps I have not thought of. That experience is invaluable and can help me build the business case and a plan of action.
How does a Cloud App Security Broker Work?
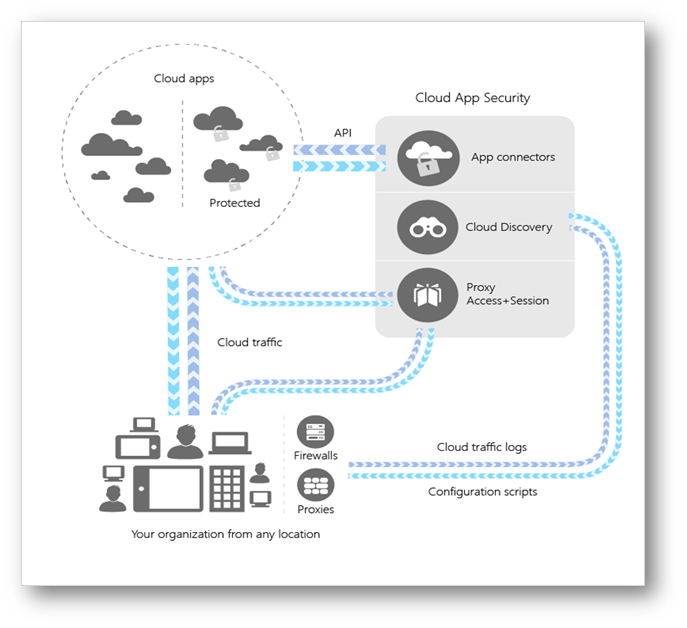
For this, I am going to reference Microsoft’s CASB – Microsoft Cloud App Security (MCAS). The following diagram is a high-level architecture of MCAS to use as a reference in this section:
 MCAS High-Level Architecture
MCAS High-Level Architecture
Microsoft Cloud App Security supports various deployment modes including log collection, API connectors, and reverse proxies. It provides rich visibility, control over data travel, and analytics to identify and combat cyberthreats across your Microsoft and third-party cloud services. Yes, I wrote third-party cloud services (read on)!
I am often asked if MCAS requires a client-side proxy agent to be installed on the user’s device. The answer is no, it does not; the proxy capability with session control is achieved through identity and Single Sign On (supporting both Azure Active Directory and 3rd party identity providers). This flexibility allows governance and protection for users accessing SaaS apps from either a corporate or Bring Your Own Device (BYOD).
If I were to summarize the capabilities of MCAS, it would come down to five main pillars:
1) Shadow IT discovery and control
2) Information Protection
3) Secure Access
4) Threat Protection
5) Cloud Security Posture Management
Matt’s Insight: Microsoft Cloud App Security is a multi-purpose tool, with many capabilities that we will get deeper into with each blog. Afterall, that is the intent of the MCAS Ninja Blog Series, to dive deep into everything MCAS! A key feature is that it does not require a client-side agent making deployment simpler and transparent to end-users. If you are a Microsoft Partner, start thinking about how MCAS can be used with your clients to help them be successful with their SaaS apps. For customers, begin thinking about prioritizing the pillars mentioned above and focus on it within MCAS to start.
Wrap Up & Conclusion:
As you can see, a Cloud Access Security Broker wears many hats to perform jobs that help manage SaaS app usage in your organization. I see the CASB as a core solution to enable secure remote work and key to digital transformation. CASBs allows organizations to use the SaaS apps they need while enabling IT to provide the security (and in some cases even compliance) they require.
How are you using a CASB in your organization? What use cases do you find valuable? Let me know in the comments below as I am anxious to hear your insights. More blog posts are on the way in the MCAS Ninja series. The next blog post will focus entirely on architecture and design of Microsoft Cloud App Security.
I am honored to have you on this journey with me, see you soon!
–Matt Soseman
http://aka.ms/SosemanTV
P.S. Stay up to date on all the MCAS Ninja training at http://aka.ms/MCASNinja
by Contributed | Nov 17, 2020 | Technology
This article is contributed. See the original author and article here.
In September 2020, Microsoft announced the new Microsoft Certified: Power Platform Developer Associate certification, providing an opportunity to demonstrate your expertise in implementing Microsoft Power Platform solutions. To earn this certification, you must pass Exam PL-400: Microsoft Power Platform Developer. This is a standalone certification and doesn’t require any prerequisite certifications or exams.
Exam PL-400 is replacing Exam MB-400
Exam MB-400 expires on December 31, 2020. After that date, only PL-400 will be available. If you’re currently preparing to take MB-400, make sure you take and pass the exam before it’s retired. To compare the two exams, check out the PL-400 skills outline document on the exam page or read Power Platform Developer PL-400 Certification, a blog post written by a Microsoft Certified Trainer (MCT). When you pass Exam PL-400, you’ll have earned your Power Platform Developer Associate certification and it will be valid for two years. If you passed Exam MB-400 before it retired and earned the associated certification, Power Apps + Dynamics 365 Developer Associate, that certification will remain valid for two years.
If you’re a professional developer who would like to extend and further customize Microsoft Power Platform capabilities for your current or future employer, you can benefit from this training and certification. The comprehensive training can get you up to speed with the platform and its extensibility points, providing many examples of how it’s done properly. And by validating your skills, certification can help you get noticed and rewarded with a salary increase or promotion. According to the 2020/2021 Nigel Frank Microsoft Dynamics Salary Survey, 61 percent of respondents believe that certifications give you the edge in the job market, 74 percent of Dynamics 365 professionals think that training and certification make you more attractive to employers, and 73 percent of permanent employees reported that their salary increased after certification.
Is this certification right for you?
Are you a developer responsible for developing, securing, and troubleshooting Microsoft Power Platform solutions? Do you implement components of the solution, such as application enhancements, custom user experience, system integrations, data conversions, custom process automation, and custom visualizations? If so, this certification can help you build and validate your skills.
To train for and earn this certification, you must have strong applied knowledge of Microsoft Power Platform, including an in-depth understanding of its capabilities, boundaries, and constraints. You should also have a basic understanding of DevOps practices for Microsoft Power Platform, and your development experience should include Microsoft Power Platform, JavaScript, JSON, TypeScript, C#, HTML, .NET, Azure, Microsoft 365, RESTful web services, ASP.NET, and Power BI.
When you’ve completed the training and passed Exam PL-400, which is a very broad developer-oriented exam, you’ll have demonstrated skills in Common Data Service, Power Apps (canvas, model, and portal), Power Automate, Power BI, and Power Virtual Agents. You’ll also be able to integrate with, and use, Azure with Microsoft Power Platform.
How can you prepare?
To help you plan your journey, check out our infographic, The journey to Microsoft Certified: Power Platform Developer Associate. You can also find it in the resources section on the certification page, which contains other valuable help. There, you’ll also find links to the free online learning paths and paid instructor-led trainings offered by Microsoft Learning Partners that help you prepare for this exam, along with a link to schedule the exam.
Demand for people trained in Microsoft Power Platform is growing, according to job listings on LinkedIn, PricewaterhouseCoopers, and other sites. See whether this new certification can help expand your opportunities for hiring or promotion.




Recent Comments