by Contributed | Sep 30, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Microsoft security workloads, such Microsoft Defender for Endpoint and Microsoft Defender for Office 365 have automated investigation and remediation capabilities that include self-healing of your organization’s devices and mailboxes. However, modern threats are usually running across security workloads. For example, an attack can start with a malicious document in Office 365, continue by compromising a device when a targeted user opens the document, and proceed through lateral movement, attempting to compromise other devices and user accounts in an organization. In such cases, individual workload capabilities are not enough. You need an infrastructure with playbooks that investigate and remediate threats across workloads. This is where self-healing through automated investigation and response capabilities in Microsoft 365 Defender comes into play.
Microsoft 365 Defender
Microsoft 365 Defender stops attacks across Microsoft 365 services and auto-heals affected assets. As threats become more complex and persistent, alerts increase, and security teams are overwhelmed, Microsoft 365 Defender leverages the Microsoft 365 security portfolio to automatically analyze threat data across endpoints, identities, apps and cloud apps, email and docs, building a complete picture of each attack in a single dashboard. With this breadth and depth of clarity defenders can focus on the critical threats and hunting across their data utilizing their unique organizational expertise, trusting that Microsoft 365 Defender’s powerful automation detects and stops attacks anywhere in the kill chain and returns the organization to a secure state.
How does self-healing work?
Self-healing is an integral part of Microsoft 365 Defender that automatically investigates and remediates potentially compromised assets—identities, mailboxes, and devices—by orchestrating signals and remediation actions across workloads.
Currently, self-healing in Microsoft 365 Defender provides the following capabilities:
- Zero-hour auto-purge (ZAP) malware playbook that orchestrates investigation and cleanup of impacted mailboxes and devices as soon as malware is detected after delivery.
- Automated investigation and remediation of potentially compromised devices triggered by Microsoft Defender for Identity alerts.
- The Action center, a single pane of glass experience for reviewing and approving pending actions, and an audit log across security workloads
Example: Emotet threat
Let see an example of the ZAP malware playbook in action. This is an Emotet threat example.
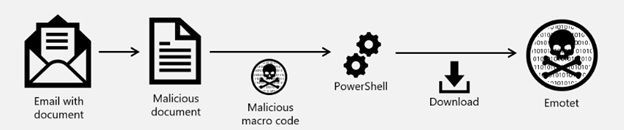
Emotet has evolved from being just a banking trojan to a downloader. It has recently been observed introducing Trickbot to infected systems. The most common attack kill chain for Emotet looks like this:

Emotet uses a malicious document with macro code as its delivery mechanism. Once clicked and running, a PowerShell script downloads additional modules to devices. The malicious document is usually crafted to target specific users, and is highly polymorphic. Within a few minutes, Microsoft Defender for Office 365 can detect the document as malicious, block the file from being delivered to other mailboxes within the organization, and trigger the automated investigation and response playbook that removes all the email messages that have the malicious file (ZAP).
ZAP signal is also sent to Microsoft 365 Defender, and the ZAP malware playbook initiates.
The playbook identifies devices with malicious document (as reported by Microsoft Defender for Office 365) and then quarantines the document. In addition, Microsoft 365 Defender triggers a suspicious host investigation playbook to clean up additional malware from users’ devices and ensure that no more threats remain. Remediation actions across both mailboxes and endpoints are tracked in the Action center, and are listed on the Pending actions or History tabs, based on your tenant configuration.
Speaking of configuration, we recommend configuring Microsoft Defender for Endpoint for full automation. That can help ensure automatic cleanup and self-healing from malware on infected devices.
Want to learn more?
See the following resources:
Let us know what you think! Feel free to leave us a comment.
Microsoft 365 Defender team
by Contributed | Sep 30, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
You can now connect existing sensors to Azure with little to no-code using IoT Plug and Play bridge! For developers who are building IoT solutions with existing hardware attached to a Linux or Windows gateway, the IoT Plug and Play bridge provides you an easy way to connect these devices to IoT Plug and Play compatible services. For supported protocols, the bridge requires modification of a simple JSON. The IoT Plug and Play bridge is open-source and can be easily extended to support additional protocols. It supports the latest version of IoT Plug and Play and Digital Twins Definition Language.
Are you an IoT device developer or IoT solution builder trying to work with existing sensors? Often the code on these sensors can’t be updated to run the latest Azure IoT Device SDK or these sensors are not able to connect directly to the internet. However, many of these sensors can connect to a Windows or Linux gateway with device drivers and support for standard protocols with OS APIs. The IoT Plug and Play bridge enables you to connect these existing sensors without modifying them. It is an open-source application that bridges the gap between the OS APIs and Azure IoT Device SDKs, expanding the reach of devices your IoT solution targets.
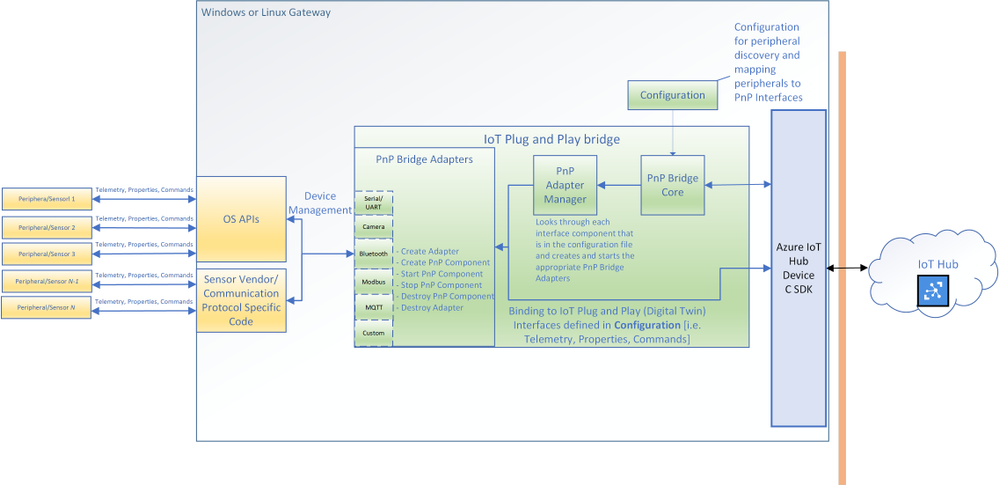
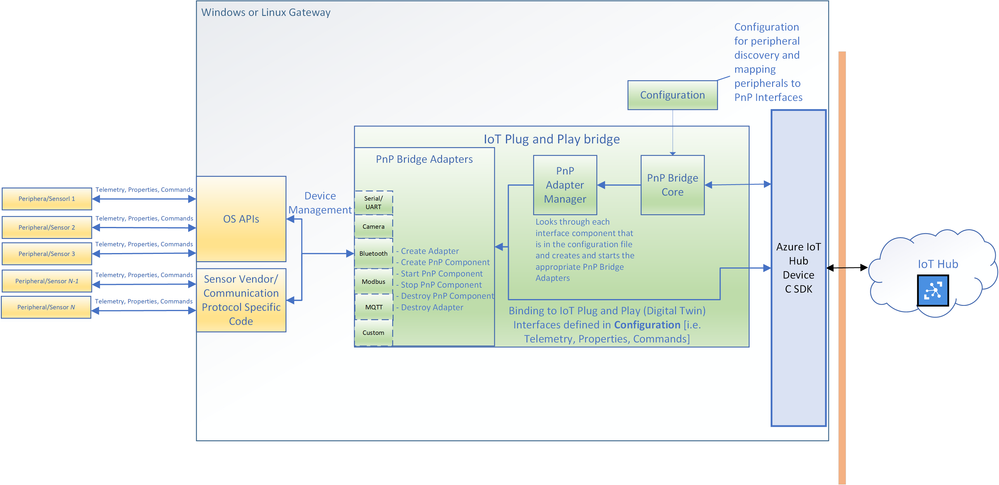 The architecture diagram of the IoT Plug and Play bridge.
The architecture diagram of the IoT Plug and Play bridge.
The IoT Plug and Play supports multiple protocols through a set of existing “PnP Bridge Adapters”. Here’s what’s supported out of the box today:
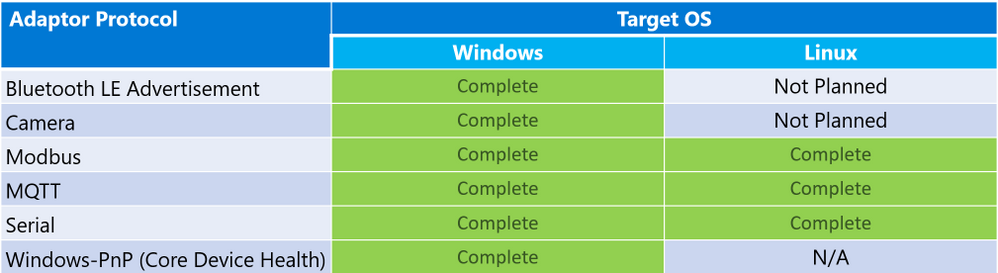 Adaptor protocols currently supported by default for IoT Plug and Play bridge
Adaptor protocols currently supported by default for IoT Plug and Play bridge
For example, there is a Windows Bluetooth adapter that let you connect Bluetooth device advertisements to IoT Plug and Play interfaces. All you need to do is modify a configuration JSON and then compile and run the IoT Plug and Play bridge. If you are only using the supported protocols you can download a pre-compiled version of the bridge from our releases page: www.aka.ms/iot-pnp-bridge-releases
Configuring the IoT Plug and Play bridge
Here’s an example of what that configuration looks like. The first part provides the bridge connection details to the bridge. You can use either a connection string or the IoT Hub Device Provisioning Service. You’ll also specify the device id and IoT Plug and Play model ID:
"$schema": "../../../pnpbridge/src/pnpbridge_config_schema.json",
"pnp_bridge_connection_parameters": {
"connection_type" : "dps",
"root_interface_model_id": "dtmi:com:example:RootPnpBridgeBluetoothDevice;1",
"auth_parameters" : {
"auth_type" : "symmetric_key",
"symmetric_key" : "InNbAialsdfhjlskdflaksdDUMMYSYMETTRICKEY=="
},
"dps_parameters" : {
"global_prov_uri" : "global.azure-devices-provisioning.net",
"id_scope": "0ne00000000",
"device_id": "bluetooth-sensor-3"
}
}
The second part of the configuration maps the hardware parameters of the device to IoT Plug and Play interfaces. Here we map Bluetooth specific addresses and offsets to IoT Plug and Play interfaces. This is done in two parts: a global adapter configuration (think of these as global variables to configure each PnP Bridge Adapter) and interface specific configuration (mappings specific to each Plug and Play interface):
"pnp_bridge_debug_trace": false,
"pnp_bridge_config_source": "local",
"pnp_bridge_interface_components": [
{
"_comment": "Component 1 - Bluetooth Device",
"pnp_bridge_component_name": "Ruuvi",
"pnp_bridge_adapter_id": "bluetooth-sensor-pnp-adapter",
"pnp_bridge_adapter_config": {
"bluetooth_address": "267541100483322",
"blesensor_identity" : "Ruuvi"
}
}
],
"pnp_bridge_adapter_global_configs": {
"bluetooth-sensor-pnp-adapter": {
"Ruuvi" : {
"company_id": "0x499",
"endianness": "big",
"telemetry_descriptor":[
{
"telemetry_name": "humidity",
"data_parse_type": "uint8",
"data_offset": 1,
"conversion_bias": 0,
"conversion_coefficient": 0.5
},
...
]
}
}
}
That’s it! You can now run the bridge with this configuration and start to see telemetry reporting in IoT Hub or IoT Explorer. Each downstream device from the bridge appears as an interface for the root bridge device. In this example you see the BLE sensor exposed a “Ruuvi” interface of the “RootPnpBridgeBluetoothDevice” root device interface:
 The DTDL model content for IoT Plug and Play bridge
The DTDL model content for IoT Plug and Play bridge
Both the “Ruuvi” and “RootPnpBridgeBluetoothDevice” interface are modeled using Digital Twins Definition Language. You can find more samples of these interfaces for the bridge in the schemas folder. You can author your own models and use them with the bridge. You can use new Visual Studio Code and Visual Studio extensions to help you author these models.
Calls to Action
by Contributed | Sep 30, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Post by Vikas Bhatia (@Vikas Bhatia), Head of Product, Azure Confidential Computing
Microsoft is committed to enabling the industry to move from ‘computing in the clear’ to ‘computing confidentially’. Why? Common scenarios confidential computing have enabled include:
- Multi-party rich and secure data analytics
- Confidential blockchain with secure key management
- Confidential inferencing with client and server measurements & verifications
- Microservices and secure data processing jobs
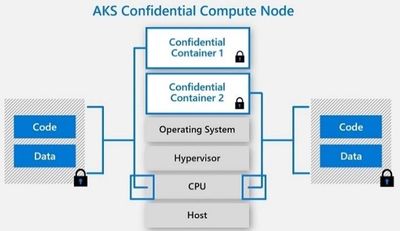
The public preview of confidential computing nodes powered by the Intel SGX DCsv2 SKU with Azure Kubernetes Service brings us one step closer by securing data of cloud native and container workloads. This release extends the data integrity, data confidentiality and code integrity protection of hardware-based isolated Trusted Execution Environments (TEE) to container applications.
Azure confidential computing based on Intel SGX-enabled virtual machines, continues encrypting data while the CPU is processing it—that’s the “in use” part. This is achieved with a hardware-based TEE that provides a protected portion of the hardware’s processor and memory. Users can run software on top of the protected environment to shield portions of code and data from view or modification outside of the TEE.
Expanding Azure confidential computing deployments
Developers can choose different application architectures based on whether they prefer a model with a faster path to confidentiality or a model with more control. The confidential nodes on AKS support both architecture models and will orchestrate confidential application and standard container applications within the same AKS deployment. Also, developers can continue to leverage existing tooling and dev ops practices when designing highly secure end-to-end applications.
During our preview period, we have seen our customers choose different paths towards confidential computing:
- Most developers choose confidential containers by taking an existing unmodified docker container application written in a higher programming language like Python, Java etc. and chose a partner like Scone, Fortanix and Anjuna or Open Source Software (OSS) like Graphene or Occlum in order to “lift and shift” their existing application into a container backed by confidential computing infrastructure. Customers chose this option either because it provides a quicker path to confidentiality or because it provides the ability to achieve container IP protection through encryption and verification of identity in the enclave and client verification of the server thumbprint.
- Other developers choose the path that puts them in full control of the code in the enclave design by developing enclave aware containers with the Open Enclave SDK, Intel SGX SDK or chose a framework such as the Confidential Consortium Framework (CCF). AI/ML developers can also leverage Confidential Inferencing with ONNX to bring a pre-trained ML model and run it confidentially in a hardware isolated trusted execution environment on AKS.
One customer, Magnit, chose the first path. Magnit is one of the largest retail chains in the world and is using confidential containers to pilot a multi-party confidential data analysis solution through Aggregion’s digital marketing platform. The solution focuses on creating insights captured and computed through secured confidential computing to protect customer and partner data within their loyalty program.
We have aggregated more samples of real use cases and continue to expand this sample list here: https://aka.ms/accsamples.
How to get going
- “Lift and shift” your existing application by choosing a partner such as Anjuna, Fortanix, or Scone; or by using Open Source Software such as Graphene or Occlum; or
- Build a new confidential application from scratch using an SDK such as the Open Enclave SDK.
Confidential computing, through its isolated execution environment, has broad potential across use cases and industries; and with the added improvements to the overall security posture of containers with its integration to AKS, we are excited and eager to learn more about what business problems you can solve.
Get started today by learning how to deploy confidential computing nodes via AKS.
by Contributed | Sep 30, 2020 | Uncategorized
This article is contributed. See the original author and article here.
While organizations have long prioritized external cybersecurity risks, many have not paid enough attention to the risks posed by trusted insiders in their organization. This is a mistake. Insiders often already have access to sensitive data, and the risks, whether malicious or inadvertent, can potentially cause greater damage than external cybersecurity risks.
Two years ago, after a conversation with our Chief Information Security Officer (CISO), Bret Arsenault, we embarked upon an incredible journey developing Insider Risk Management in Microsoft 365, which organizations could use to identify and manage insider risks.
Throughout our journey we had the opportunity to speak to a broad set of individuals in different disciplines within organizations across a variety of industries. These conversations helped shape our solution to address the needs of an organization to collaboratively identify and manage insider risks, while maintaining employee privacy and supporting a positive company culture.
Today, we invite you to come along on our journey by listening to Uncovering Hidden Risks, a series of podcasts with top notch insider risk experts!
These experts have a unique and deep understanding of insider risks, the challenges organizations face, and the people, processes and technology being used to address them. We are excited to have you listen in to our conversations as we discuss a range of interesting topics, ranging from hunting for risks using artificial intelligence to collaborating with HR and legal to build an effective insider risk management program.
Get ready to hear some great stories, gain a better understanding of insider risks and in the process learn something new. Listen to our show on the following platforms:
If you like what you hear, we’d love for you to Subscribe, Rate and Review it on iTunes or any other podcast platform you may use.
We look forward to hearing from you!
Thank you,
Raman Kalyan and Talhah Mir
Meet our guests and join us for the discussion!
Dawn Cappelli
VP of Global Security and CISO at Rockwell Automation
Founder of CERT
Dawn is recognized as one of the world’s leaders in insider threat mitigation. She has been working on the insider threat problem for three decades in various roles partnering closely with the Department of Defense, the Department of Homeland Security, the U.S. Secret Service, other federal agencies, the intelligence community, private industry, academia, and the vendor community.
Dan Costa
Technical Manager
CERT National Insider Threat Center, Carnegie Mellon University’s Software Engineering Institute
Dan leads the research and engineering efforts of the CERT National Insider Threat Center, where he and his team conduct empirical research and develop solutions that enable organizations to effectively manage insider risks.
Rob McCann
Principal Applied Researcher
Microsoft
Rob has over 14 years’ experience professional experience in cybersecurity and software engineering and we talk about how new advances in artificial intelligence and machine learning take on the challenge of hunting for insider risks.
Episode 1, “Artificial intelligence hunts for insider risks”
In this podcast we have a wide-ranging discussion with Rob McCann, Principal Applied Researcher at Microsoft. Specifically, about how the power of machine learning and artificial intelligence can uncover hidden risks that would otherwise be impossible to find.
Episode 2, “Predicting your next insider risks”
In this podcast speak with Dan Costa, Technical Manager of the CERT National Insider Threat Center at Carnegie Mellon University’s Software Engineering Institute. We discuss the challenges of addressing insider threats and how organizations can improve their security posture by understanding the conditions and triggers that precede a potentially harmful act. We also explore, how technological advances in prevention and detection can help organizations stay safe and steps ahead of threats from trusted insiders.
Episode 3, “Insider risks aren’t just a security problem”
We are back with Dan Costa to explore how partnering with Human Resources can create a strong insider risk management program, a better workplace and more secure organization.
Episode 4, “Insider risk programs have come a long way”
In this podcast speak with Dawn Cappelli, VP of Global Security and CISO at Rockwell Automation and founder of CERT. We discuss the role of technology, psychology, people, and cross-organizational collaboration to drive an effective insider risk program today and things to consider as we look ahead and across an ever-changing risk landscape.
Episode 5, “Practitioners guide to effectively managing insider risks”
We are back with Dawn Cappelli to discuss about the steps to take to set up and run an insider risk management program. We talk about specific organizations to collaborate with, and top risks to address first.

by Contributed | Sep 30, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Another month, another round-up of Microsoft Teams for Education updates inspired by you and designed for you. Thank you for sharing your feedback, triumphs, and difficulties with us along the way. We know this is not easy, and we are grateful and humbled that you are choosing Microsoft Teams.
This month there are features that will help make social and emotional learning, online classes, and staying focused easier. We’ve got you covered to:
- Keep learners engaged with social and emotional learning support
- Run engaging classes through online meetings
- Help students stay focused
- Maintain student safety with meeting controls
- Do more with Assignments in Teams
- Build an interactive classroom with SMART Learning Suite
- Train yourself in Teams and support students with additional resources
Let’s dive in! (If you’re just looking for a list without extra description, click here to jump.)
1) Keep students engaged with social and emotional learning support
Social and Emotional Learning (SEL) connections in the digital classroom
Learning is more than just getting homework done. It’s about discovering how to collaborate, regulate your emotions, and engage with others. Now with SEL badges in Praise and new SEL sticker pack for OneNote, educators can encourage the development of these critical life skills while in a remote or hybrid learning environment. Learn how to send Praise, and how IT can make the new SEL Praise badges available.
When: SEL sticker pack for OneNote is available now, SEL badges in Praise coming soon

New badges available in Praise and OneNote built for Social and Emotional Learning
Custom Badges in Praise
Looking to encourage school pride, or a specific class or school curriculum? Now, in the Admin Center you can design up to 25 custom badges to be used throughout school. Create badges with unique names, colors, and images with school mascots, mottos, or core student achievements. Learn how to create and enable custom badges from the Admin Center.
To learn more about the benefits of social and emotional learning in child development and some of the research done on SEL, check out this blog from earlier in the month.
When: coming soon
2) Run engaging classes through online meetings
Custom layouts
Custom layouts allow for a more dynamic content viewing experience and enable an educator to customize how content shows up for students during an online class. For example, when an educator is showing a PowerPoint slide, participants will be able to see the presenter’s video feed transposed onto the foreground of the slide they’re showing.
When: expected later this year
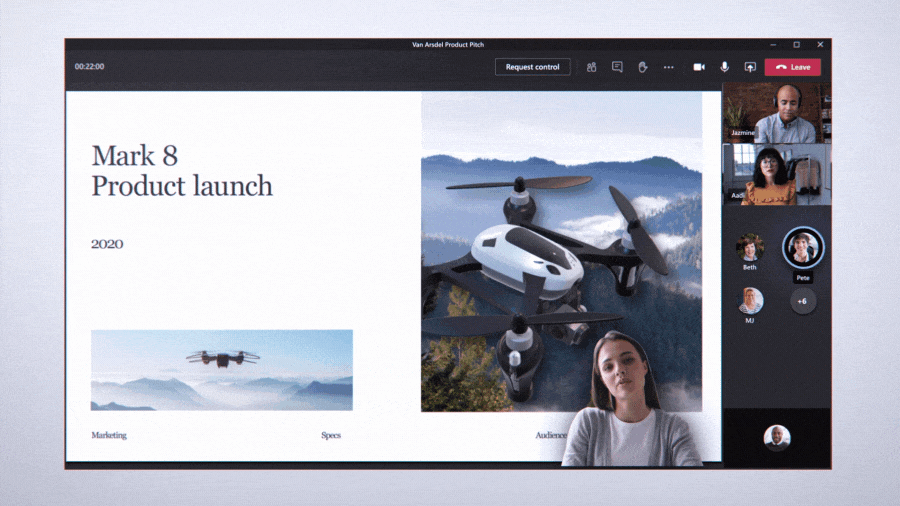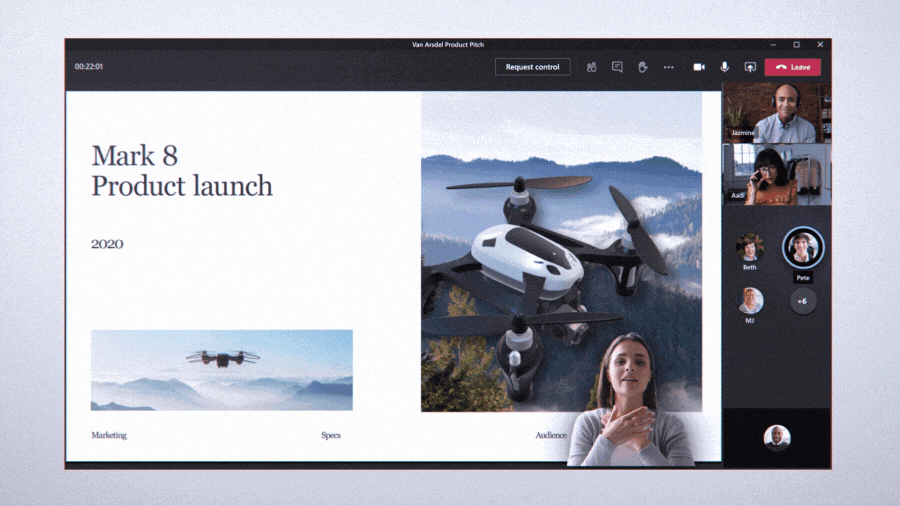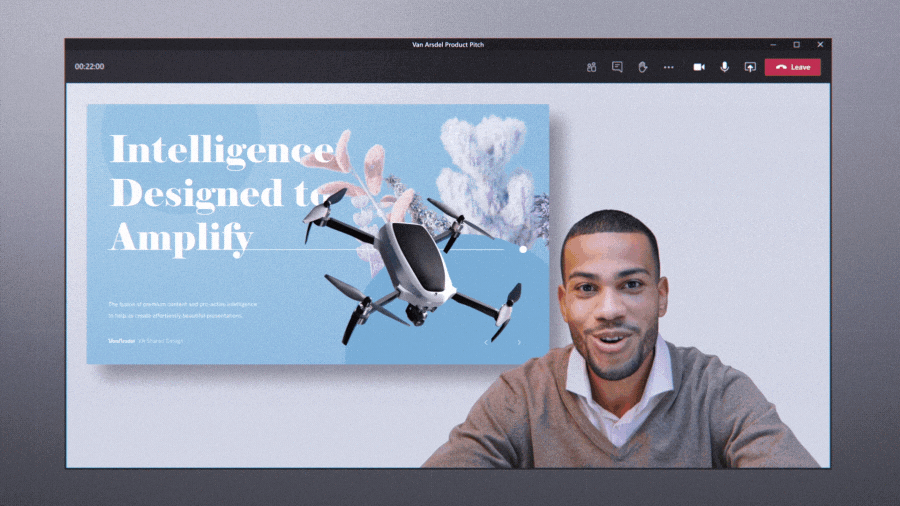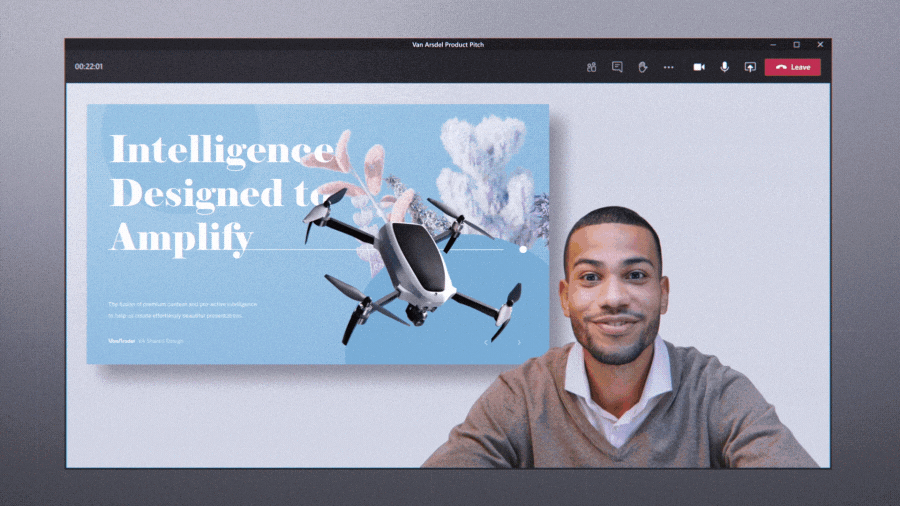
Present along with your presentation, all on the same screen
Request to Speak when Hard Audio Muted
Educators can keep collaboration to the right moments, hard audio mute students when it’s time to present then allow students to unmute themselves. This allows for the flexibility needed in class to help students stay focused, but also gives every student the opportunity to raise their hand and share their voice with the class.
When: coming soon
New Together Mode scenes
Together mode reimagines meeting experiences to help participants feel closer together even when you are apart. With new Together mode scenes coming this calendar year, you can transport your class to a variety of settings that can help set the tone and create the right virtual experience, whether it be an auditorium, a conference room, or a coffee shop.
When: expected later this year

Choose Together Mode scenes for different virtual meeting experiences
Whiteboard “Presenter” Mode
Educators now have the option to choose a presenter mode in Microsoft Whiteboard in Teams. This allows for more flexibility to either present the digital whiteboard with Read-Only access for students, or to allow (or adjust) student access when it’s time to have the whole class collaborate.
When: available now
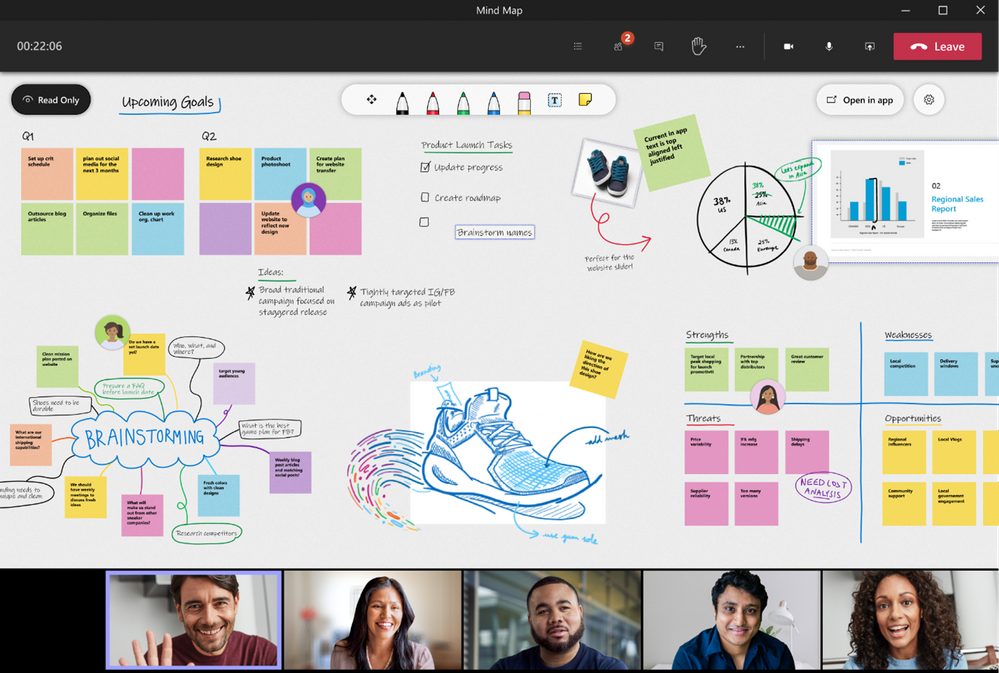
Presenter Mode gives more control, allowing only the educator to edit the whiteboard
3) Help students stay focused
Focus Mode
Now students will be able to hone-in on the materials being presented in their online class. When a teacher is sharing their screen, students can choose “Focus Mode” from the “…” so that only the content shows without any distracting videos.
When: available now
Microsoft Lists in Teams
Track information, coordinate group projects, and share resources with Microsoft Lists. Users can create a list directly in a class team channel – just click “+” and select the Lists app. Lists provides a simple, smart, and flexible way to help groups and classes stay organized. For example, educators can create a list of important articles that tracks the article title, author publisher and date, book recommendations for class, or a “check out of class” list to keep track of classroom assets. Likewise, students can use Lists to keep track of assignments and manage responsibilities for group projects. Learn more from the announcement blog and see it in action with the “Create a list in Microsoft Teams” click-thru demo.
When: available now
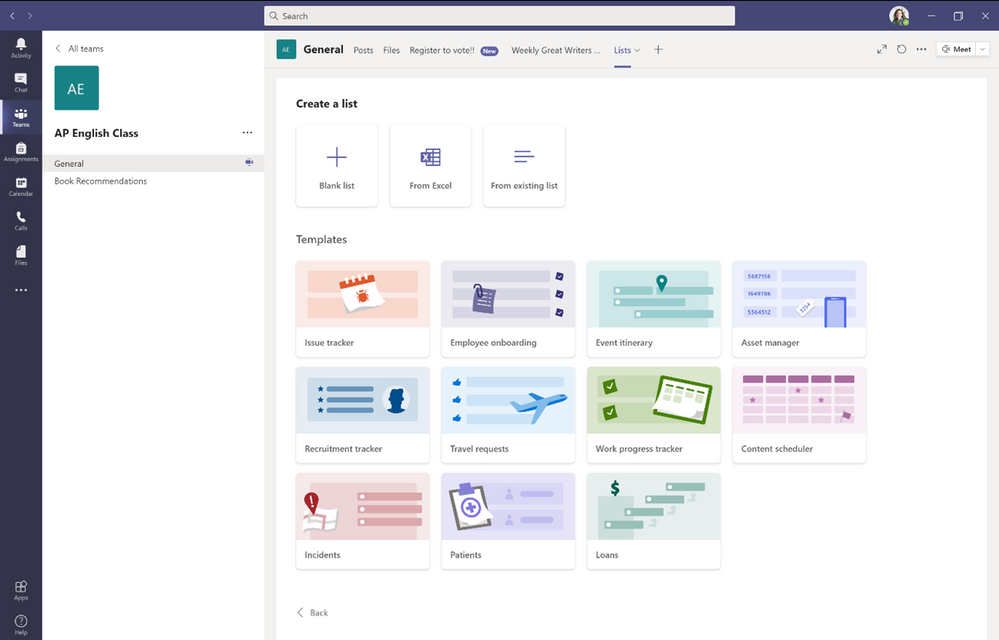
Create a new list from within Microsoft Teams and choose from numerous ready-made templates
4) Maintain student safety with meeting controls
“Only Me” Admin Policy for all Organizer Meeting Options
IT Admins can apply a policy that defaults “Only Me” to allow only educators (or the meeting organizer) to enter the meeting and keep students in the lobby until the educator admits them. This helps maintain student safety and contains student to student interaction in class to the right time when the educator is present. Learn more about this and other recommended Teams for Education policies here.
When: available now
5) Do more with Assignments in Teams
Assignments Grading History
See all of the submission and return history of Assignments in Teams, all in one place. Easily track Assignments over time.
When: available now
6) Build an interactive classroom with SMART Learning Suite
The SMART Learning Suite app gives teachers the power to create, edit, deliver, manage and share interactive lessons directly within Microsoft Teams, enhancing instruction from the platform and workflows they already use. It lets students work on lesson activities in class or from home, synchronously or asynchronously, while teachers guide their learning. Teachers can enhance existing lesson material such as PDFs, Power Point and SMART Notebook files with formative assessments, collaborative workspaces, game-based activities, learning manipulatives and more, and easily give feedback to students in real time.
To experience the power SMART Learning Suite can bring to your Teams classroom, sign up for a free 45 day trial and add the app to get started.
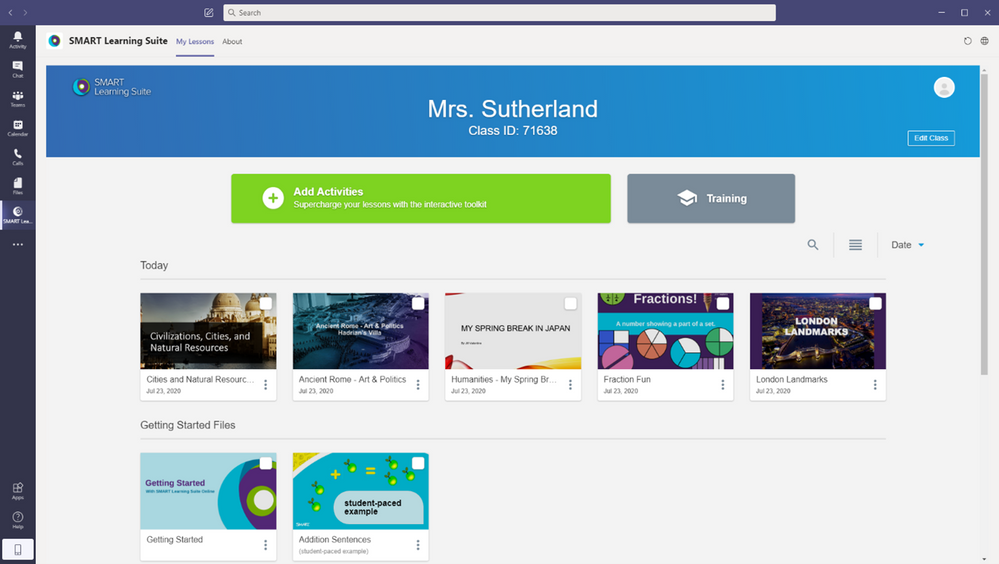
Smart Learning Suite, now available in Microsoft Teams, supports student engagement and learning
Learn about other apps and LMS in Teams
7) Train yourself in Teams and support students with additional resources
For educators
- Find what you need to get started on Teams all in one place at aka.ms/TeamsPP
- Check this quick article about how to have secure online meetings
- Learn more about strategies to promote well-being among children and watch the Microsoft + MindUP webinars at http://aka.ms/MindUpVirtual
For parents
- Learn about Teams and common classroom scenarios with clickable interactive demos (English)
- Find resources to keep kids engaged and learning new skills with family-led learning experiences for children 3-12 and free live or on-demand virtual field trips and learning activities, like Roald Dahl day, Dr Jane Goodall, Global Read Aloud events, and more
For IT
- Check out the Quick Start Guide
-
Watch the recordings from the Microsoft Teams for Edu digital readiness event which dive into common scenarios, use cases to support you this school year at https://aka.ms/TeamsEduEvent
- Learn which policies to enable to keep students safe when using Teams for remote and hybrid learning with this Policy quick guide
You can also check out the Teams help homepage or click Help in your Teams app at any time for extra how-tos and support!
And for those that love lists, here’s a quick review of all the features we shared along with their expected launch dates:
Keep learners engaged with social and emotional learning support
Social and Emotional Learning badges in Praise – coming soon
Social and Emotional Learning sticker pack in OneNote – available now
Custom badges in Praise – coming soon
Run engaging classes through online meetings
New Together Mode scenes – coming this calendar year
Custom layouts – later this year
Request to Speak (as a part of Hard Audio Mute) – coming soon
Whiteboard “Presenter” mode – available now
Help students stay focused
Focus Mode – available now
Microsoft Lists in Teams – available now
Maintain student safety with meeting controls
Only Me Lobby Admin policy – available now
Do more with Assignments in Teams
Assignments Grading History – available now
And in case you missed it, here are features we announced in July and August that are coming soon:
Run engaging classes through online meetings
Attendance Report post-meeting download – expected in October
Teams meetings up to 1,000 interactive participants – coming in the last quarter of 2020 (in Advanced Communications add-on option)
Virtual Breakout rooms – expected October
Do more with Assignments in Teams
View assignments across all classes (again) – expected in October
Link thumbnail preview – expected later this year
Anonymous Grading/Marking – expected in October
Do more with OneNote in Teams
Notification in Teams for OneNote Page Distribution – expected in next few months
You’ve got this. And we’re right here if you need us.








Recent Comments